Database Management System Report: Cloud Implementation and Security
VerifiedAdded on 2023/06/04
|5
|767
|285
Report
AI Summary
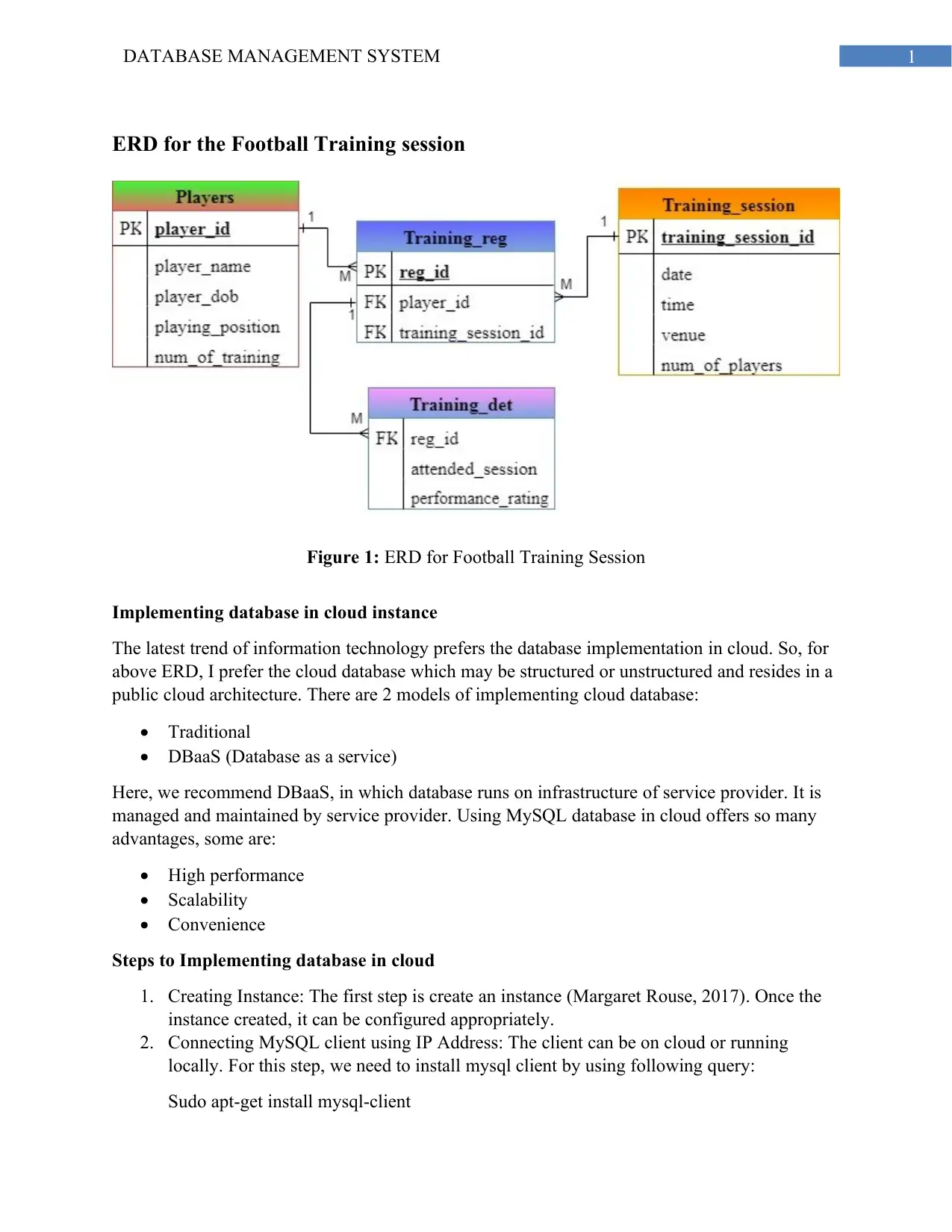
This report delves into the practical aspects of database management systems (DBMS), specifically focusing on the implementation of a cloud-based database for a football training session. It begins by presenting an Entity-Relationship Diagram (ERD) to model the data structure, followed by a discussion on the advantages of cloud database implementation, including high performance and scalability. The report then outlines the steps involved in creating a cloud database instance using MySQL, establishing connections, and creating tables such as Players, Training_session, Training_reg, and Training_det. Furthermore, it addresses user management, including registration and access control using GRANT and REVOKE statements, while emphasizing the importance of database security in a cloud environment. The report concludes by exploring security measures like cryptography, digital signatures, and access control methods (MAC, LBAC, RBAC) to ensure data confidentiality, availability, and integrity.
1 out of 5









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)