Detailed Report: DDoS Attacks with Operation Ababil Case Study
VerifiedAdded on 2023/06/07
|10
|2158
|245
Report
AI Summary
This report provides a comprehensive analysis of Distributed Denial of Service (DDoS) attacks, detailing their operational mechanisms and real-world impact, with a specific focus on the Operation Ababil incident. The report begins with an overview of computer security and the increasing need for it due to rising cybercrimes. It explains how DDoS attacks work, including the roles of master computers, victim servers, and botnets, and how attackers exploit vulnerabilities to flood networks with traffic, rendering services unavailable to legitimate users. The report then delves into Operation Ababil, a series of cyber-attacks targeting American banks in 2012 and 2013, discussing its motivations, impact on financial institutions, and the breaches in security principles, particularly availability. Finally, it touches on mitigation strategies, such as monitoring internet traffic, using firewalls and anti-viruses, implementing disaster recovery plans, and encrypting sensitive data, to safeguard against such attacks.

[Type the company name]
Computer security
Computer security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 | P a g e
Table of Contents
Introduction................................................................................................................................1
An overview on DDoS...............................................................................................................1
Working of the attack.............................................................................................................2
One real world example.............................................................................................................4
Conclusion..................................................................................................................................6
References..................................................................................................................................7
Table of Contents
Introduction................................................................................................................................1
An overview on DDoS...............................................................................................................1
Working of the attack.............................................................................................................2
One real world example.............................................................................................................4
Conclusion..................................................................................................................................6
References..................................................................................................................................7

2 | P a g e
Introduction
Computer security is a protection that safeguards the system, hardware, software and
networks from all the malicious attacks. The need of computer security is increasing day by
day because cyber-crimes are also increasing. Thus, it is necessary to protect all the
information as organisations and enterprises completely rely over network for keeping their
information private (Schwartz, 2017). The role of computer security is to maintain
confidentiality, availability and integrity of information. The vulnerabilities and attacks are
increasing day by day. One such attack that is considered in this report is distributed denial
of service. It is an attack that makes the resources and services unavailable from the valid
user. DDoS attack is difficult to detect as in this system is fooled from the attacker by
sending huge amount of traffic to the victims computer. In this report, one real life example
of DDoS that is operation ababil is discussed.
An overview on DDoS
Distributed denial of service is an attack that has penetrated in the real world. It
makes many web applications and services unavailable from the user for a time slot. It is
caused due to many infected computers on the internet that are under the control of hackers
(Alieyan, Kadhum, Anbar, Rehman & Alajmi, 2016). It basically targets servers and do not
allow legitimate users to access the information. Theses attacks take place silently as even
the owners of computer are not aware that their system is being access by third party
(Alieyan, Kadhum, Anbar, Rehman & Alajmi, 2016). This attack is carried by increasing
eth traffic over the web or flooding it with many requests in order to degrade the service.
Introduction
Computer security is a protection that safeguards the system, hardware, software and
networks from all the malicious attacks. The need of computer security is increasing day by
day because cyber-crimes are also increasing. Thus, it is necessary to protect all the
information as organisations and enterprises completely rely over network for keeping their
information private (Schwartz, 2017). The role of computer security is to maintain
confidentiality, availability and integrity of information. The vulnerabilities and attacks are
increasing day by day. One such attack that is considered in this report is distributed denial
of service. It is an attack that makes the resources and services unavailable from the valid
user. DDoS attack is difficult to detect as in this system is fooled from the attacker by
sending huge amount of traffic to the victims computer. In this report, one real life example
of DDoS that is operation ababil is discussed.
An overview on DDoS
Distributed denial of service is an attack that has penetrated in the real world. It
makes many web applications and services unavailable from the user for a time slot. It is
caused due to many infected computers on the internet that are under the control of hackers
(Alieyan, Kadhum, Anbar, Rehman & Alajmi, 2016). It basically targets servers and do not
allow legitimate users to access the information. Theses attacks take place silently as even
the owners of computer are not aware that their system is being access by third party
(Alieyan, Kadhum, Anbar, Rehman & Alajmi, 2016). This attack is carried by increasing
eth traffic over the web or flooding it with many requests in order to degrade the service.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
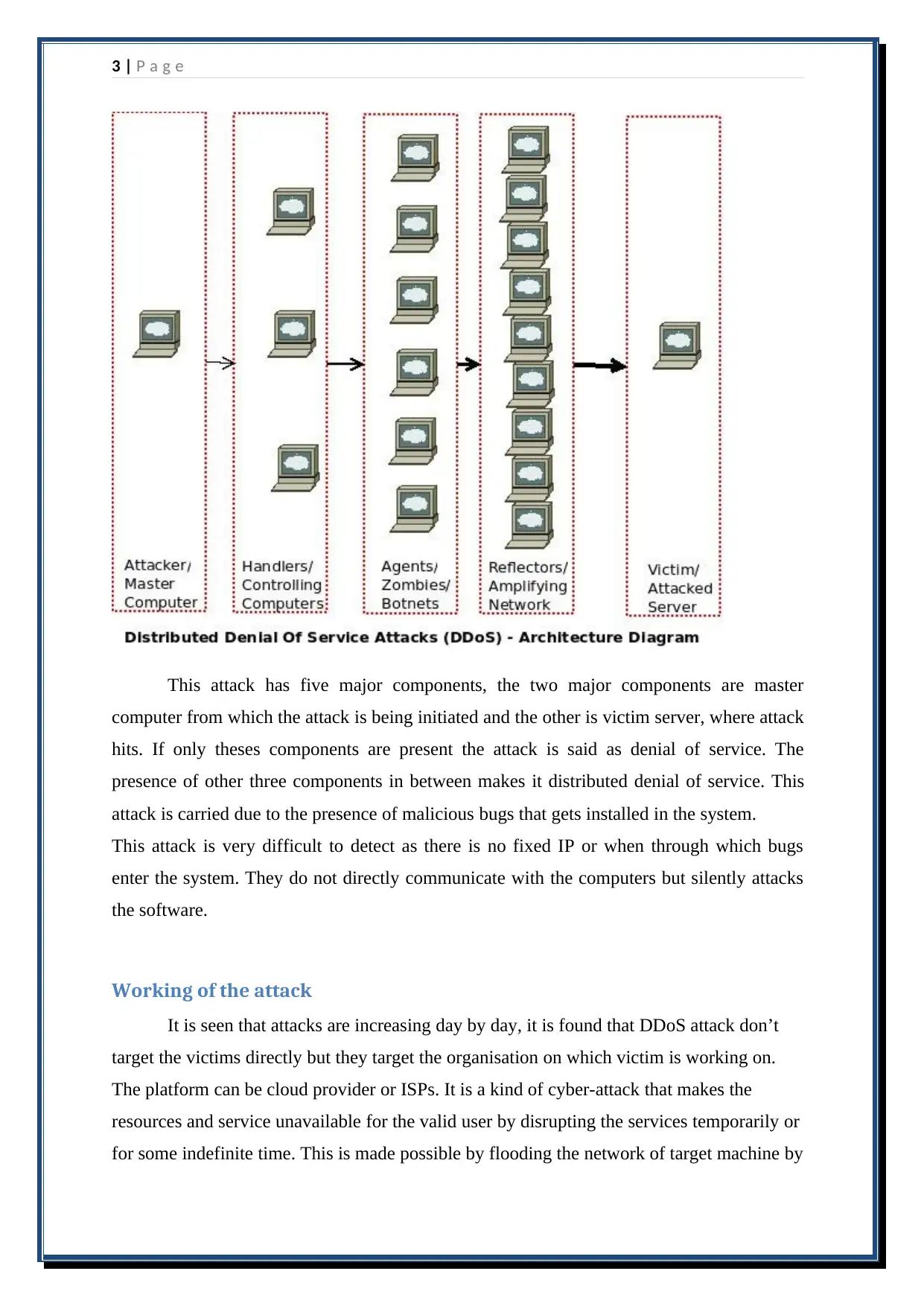
3 | P a g e
This attack has five major components, the two major components are master
computer from which the attack is being initiated and the other is victim server, where attack
hits. If only theses components are present the attack is said as denial of service. The
presence of other three components in between makes it distributed denial of service. This
attack is carried due to the presence of malicious bugs that gets installed in the system.
This attack is very difficult to detect as there is no fixed IP or when through which bugs
enter the system. They do not directly communicate with the computers but silently attacks
the software.
Working of the attack
It is seen that attacks are increasing day by day, it is found that DDoS attack don’t
target the victims directly but they target the organisation on which victim is working on.
The platform can be cloud provider or ISPs. It is a kind of cyber-attack that makes the
resources and service unavailable for the valid user by disrupting the services temporarily or
for some indefinite time. This is made possible by flooding the network of target machine by
This attack has five major components, the two major components are master
computer from which the attack is being initiated and the other is victim server, where attack
hits. If only theses components are present the attack is said as denial of service. The
presence of other three components in between makes it distributed denial of service. This
attack is carried due to the presence of malicious bugs that gets installed in the system.
This attack is very difficult to detect as there is no fixed IP or when through which bugs
enter the system. They do not directly communicate with the computers but silently attacks
the software.
Working of the attack
It is seen that attacks are increasing day by day, it is found that DDoS attack don’t
target the victims directly but they target the organisation on which victim is working on.
The platform can be cloud provider or ISPs. It is a kind of cyber-attack that makes the
resources and service unavailable for the valid user by disrupting the services temporarily or
for some indefinite time. This is made possible by flooding the network of target machine by
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
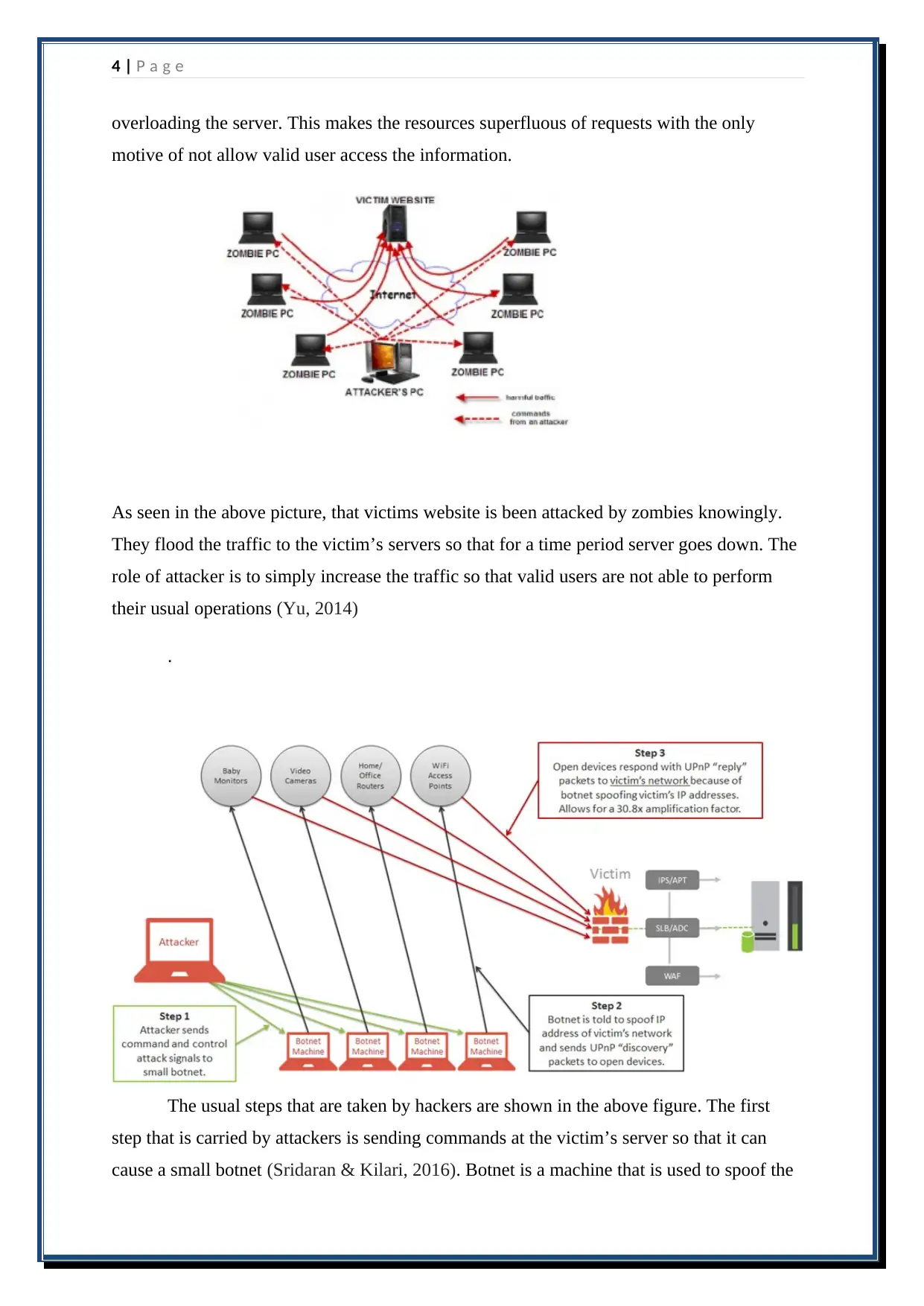
4 | P a g e
overloading the server. This makes the resources superfluous of requests with the only
motive of not allow valid user access the information.
As seen in the above picture, that victims website is been attacked by zombies knowingly.
They flood the traffic to the victim’s servers so that for a time period server goes down. The
role of attacker is to simply increase the traffic so that valid users are not able to perform
their usual operations (Yu, 2014)
.
The usual steps that are taken by hackers are shown in the above figure. The first
step that is carried by attackers is sending commands at the victim’s server so that it can
cause a small botnet (Sridaran & Kilari, 2016). Botnet is a machine that is used to spoof the
overloading the server. This makes the resources superfluous of requests with the only
motive of not allow valid user access the information.
As seen in the above picture, that victims website is been attacked by zombies knowingly.
They flood the traffic to the victim’s servers so that for a time period server goes down. The
role of attacker is to simply increase the traffic so that valid users are not able to perform
their usual operations (Yu, 2014)
.
The usual steps that are taken by hackers are shown in the above figure. The first
step that is carried by attackers is sending commands at the victim’s server so that it can
cause a small botnet (Sridaran & Kilari, 2016). Botnet is a machine that is used to spoof the

5 | P a g e
IP address of the actual user by sending UPnP packets that are said as a discovery packets
used to open the devices. Thus, victim computers are not aware about such network so that
allow botnet packets t hit the system and access the system. These botnet directly access the
victim’s computer by increasing the traffic on the site (Yu, 2014). This does not allow valid
user to access the information.
Once this botnet has been set up successful, the attacker gets the right to have direct
communication with the machine so that they send all the false instructions (McGregor,
Charters, Holliday & Roesner, 2015). The IP address is targeted by the botnet which cause
the server to overflow from its actual capacity. The overflowing of the capacity results in
increasing the traffic which in turn causes distributed denial of service (Sridaran & Kilari,
2016). It is very difficult to identify as each bot is a real device that separates the attacker
traffic from normal traffic can be difficult. The goal of this attack is to create traffic or
congestion by making all bandwidth available between target and internet (Kau & Kaur,
2015).
One real world example
Distributed denial of service attack is very dangerous and it increased in these recent
years. The attack that is discussed over is operation ababil that targeted many banks in
America with the motive of disallowing valid users to access the information. The real world
example of Distributed denial of service was operation ababil that occurred in the tear 2012
and 2013 (McGregor, Charters, Holliday & Roesner, 2015). It generally impacted the
nation and state cyber-attacks by making at least 26 victims. In this attack mostly the loss
was face by banks of U.S., as they were hit with it.
This attack was given a name that is “Operation ababil” and it occurred in December
2012 and January 2013 (Mallikarjunan, Muthupriya & Shalinie, 2016). It was a
series of cyber-attack that hit various financial institutes of America. The name of
this attack came from Izz as-Din al-Qassam, he was a muslin preacher that once fight
against British people (Gillman, Lin, Maggs & Sitaraman, 2015).
The outcome of this incident was very negative as this attack affected the retaliation
on U.S. sanctions on Iran. This attack was majorly on the bank of America, capital
one, chase, Citibank, ONC bank and many others. These banks went completely
offline after this attack (Gillman, Lin, Maggs & Sitaraman, 2015). This attack
IP address of the actual user by sending UPnP packets that are said as a discovery packets
used to open the devices. Thus, victim computers are not aware about such network so that
allow botnet packets t hit the system and access the system. These botnet directly access the
victim’s computer by increasing the traffic on the site (Yu, 2014). This does not allow valid
user to access the information.
Once this botnet has been set up successful, the attacker gets the right to have direct
communication with the machine so that they send all the false instructions (McGregor,
Charters, Holliday & Roesner, 2015). The IP address is targeted by the botnet which cause
the server to overflow from its actual capacity. The overflowing of the capacity results in
increasing the traffic which in turn causes distributed denial of service (Sridaran & Kilari,
2016). It is very difficult to identify as each bot is a real device that separates the attacker
traffic from normal traffic can be difficult. The goal of this attack is to create traffic or
congestion by making all bandwidth available between target and internet (Kau & Kaur,
2015).
One real world example
Distributed denial of service attack is very dangerous and it increased in these recent
years. The attack that is discussed over is operation ababil that targeted many banks in
America with the motive of disallowing valid users to access the information. The real world
example of Distributed denial of service was operation ababil that occurred in the tear 2012
and 2013 (McGregor, Charters, Holliday & Roesner, 2015). It generally impacted the
nation and state cyber-attacks by making at least 26 victims. In this attack mostly the loss
was face by banks of U.S., as they were hit with it.
This attack was given a name that is “Operation ababil” and it occurred in December
2012 and January 2013 (Mallikarjunan, Muthupriya & Shalinie, 2016). It was a
series of cyber-attack that hit various financial institutes of America. The name of
this attack came from Izz as-Din al-Qassam, he was a muslin preacher that once fight
against British people (Gillman, Lin, Maggs & Sitaraman, 2015).
The outcome of this incident was very negative as this attack affected the retaliation
on U.S. sanctions on Iran. This attack was majorly on the bank of America, capital
one, chase, Citibank, ONC bank and many others. These banks went completely
offline after this attack (Gillman, Lin, Maggs & Sitaraman, 2015). This attack
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6 | P a g e
disturbed the operations of many banks for approximately six months. The online
security of banks was also affected as this attack tried to capture encryption keys and
tries to breach the security by reading or accessing the confidential data (Stavrou,
Fleck & Kolias, 2016). The result of this attack was that online servers of banks were
flooded with traffic and the legitimate and valid users were not able to access the
information.
The impact of this attack caused security breach and also lost the customers trust.
Due to this attack the working condition of many financial institutes were affected
and many government authorities were dismissed for having poor security
protections.
The aim of security is to maintain availability, confidentiality and integrity.
Confidentiality assures that all the information remains private and is accessed only
by valid user. Integrity assures that data is received and delivered to authenticated
user and availability states that services and information will remain available all the
time to valid user (Stavrou, Fleck & Kolias, 2016). In this attack, availability was
breached as attackers flood the network which do not allow valid user to access step
information. It is just a way of blocking the access of valid user, thus the goal of
DDoS defence is to maintain availability (Dev, 2015).
The attack can be mitigated by protected your assets from all the malicious attacks
this can be done by monitoring the internet 24/7 and blocking the sites through which
bugs can penetrate in the system (Geers, Kindlund, Moran & Rachwald, 2014).
Apart from, that it is also recommended that firewalls and anti-viruses should be
used so that viruses can be detecting. Once the virus is detected it becomes easy to
safeguard the network (Schwartz, 2017) .It is also stated that every organisation
should have a disaster recovery plan so that security of the website is maintained
(Adminhacks, 2017). It is suggested that data should be encrypted so that all the
sensitive information remains private and is not leaked to any other organisation.
disturbed the operations of many banks for approximately six months. The online
security of banks was also affected as this attack tried to capture encryption keys and
tries to breach the security by reading or accessing the confidential data (Stavrou,
Fleck & Kolias, 2016). The result of this attack was that online servers of banks were
flooded with traffic and the legitimate and valid users were not able to access the
information.
The impact of this attack caused security breach and also lost the customers trust.
Due to this attack the working condition of many financial institutes were affected
and many government authorities were dismissed for having poor security
protections.
The aim of security is to maintain availability, confidentiality and integrity.
Confidentiality assures that all the information remains private and is accessed only
by valid user. Integrity assures that data is received and delivered to authenticated
user and availability states that services and information will remain available all the
time to valid user (Stavrou, Fleck & Kolias, 2016). In this attack, availability was
breached as attackers flood the network which do not allow valid user to access step
information. It is just a way of blocking the access of valid user, thus the goal of
DDoS defence is to maintain availability (Dev, 2015).
The attack can be mitigated by protected your assets from all the malicious attacks
this can be done by monitoring the internet 24/7 and blocking the sites through which
bugs can penetrate in the system (Geers, Kindlund, Moran & Rachwald, 2014).
Apart from, that it is also recommended that firewalls and anti-viruses should be
used so that viruses can be detecting. Once the virus is detected it becomes easy to
safeguard the network (Schwartz, 2017) .It is also stated that every organisation
should have a disaster recovery plan so that security of the website is maintained
(Adminhacks, 2017). It is suggested that data should be encrypted so that all the
sensitive information remains private and is not leaked to any other organisation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7 | P a g e
Conclusion
Computer security is as important term that is used to maintain confidentiality,
integrity and availability of all the information. In this report, the attack that is discussed in
distributed denial of service that breaches the availability of data. It do not allow valid user
to access computer assets and services. This denial of service affect the brand image thus it
is necessary to maintain integrity, confidentiality and availability. The second part of the
report covers discussion about the attack named as operation ababil that was a DDoS attack.
It captured various American banks and breached security.
Conclusion
Computer security is as important term that is used to maintain confidentiality,
integrity and availability of all the information. In this report, the attack that is discussed in
distributed denial of service that breaches the availability of data. It do not allow valid user
to access computer assets and services. This denial of service affect the brand image thus it
is necessary to maintain integrity, confidentiality and availability. The second part of the
report covers discussion about the attack named as operation ababil that was a DDoS attack.
It captured various American banks and breached security.

8 | P a g e
References
Adminhacks. (2017). How Does a DDOS Attack Happen?. Retrieved from
https://adminhacks.com/ddos-attacks.html.
Alieyan, K., Kadhum, M. M., Anbar, M., Rehman, S. U., & Alajmi, N. K. (2016, October).
An overview of DDoS attacks based on DNS. In Information and Communication
Technology Convergence (ICTC), 2016 International Conference on (pp. 276-280).
IEEE.
Dev, P. R. (2015). Use of Force and Armed Attack Thresholds in Cyber Conflict: The
Looming Definitional Gaps and the Growing Need for Formal UN Response. Tex.
Int'l LJ, 50, 381.
Geers, K., Kindlund, D., Moran, N., & Rachwald, R. (2014). World War C: Understanding
nation-state motives behind today’s advanced cyber attacks. FireEye, Milpitas, CA,
USA, Tech. Rep., Sep.
Gillman, D., Lin, Y., Maggs, B., & Sitaraman, R. K. (2015). Protecting websites from attack
with secure delivery networks. Computer, 48(4), 26-34.
Kaur, R., & Kaur, R. (2015). AN OVERVIEW OF CLASSIFICATION OF DDOS
ATTACKS AND DEFENCE MECHANISMS FOR DDOS ATTACKS. Int J Adv
Engg Tech/Vol. VI/Issue II/April-June, 12, 14.
Mallikarjunan, K. N., Muthupriya, K., & Shalinie, S. M. (2016, January). A survey of
distributed denial of service attack. In Intelligent Systems and Control (ISCO), 2016
10th International Conference on (pp. 1-6). Ieee.
McGregor, S. E., Charters, P., Holliday, T., & Roesner, F. (2015, August). Investigating the
Computer Security Practices and Needs of Journalists. In USENIX Security
Symposium(pp. 399-414).
Schwartz. M. (2017). Banks Hit Downtime Milestone In DDoS Attacks. Retrieved from
https://www.darkreading.com/attacks-and-breaches/banks-hit-downtime-milestone-
in-ddos-attacks/d/d-id/1109390.
References
Adminhacks. (2017). How Does a DDOS Attack Happen?. Retrieved from
https://adminhacks.com/ddos-attacks.html.
Alieyan, K., Kadhum, M. M., Anbar, M., Rehman, S. U., & Alajmi, N. K. (2016, October).
An overview of DDoS attacks based on DNS. In Information and Communication
Technology Convergence (ICTC), 2016 International Conference on (pp. 276-280).
IEEE.
Dev, P. R. (2015). Use of Force and Armed Attack Thresholds in Cyber Conflict: The
Looming Definitional Gaps and the Growing Need for Formal UN Response. Tex.
Int'l LJ, 50, 381.
Geers, K., Kindlund, D., Moran, N., & Rachwald, R. (2014). World War C: Understanding
nation-state motives behind today’s advanced cyber attacks. FireEye, Milpitas, CA,
USA, Tech. Rep., Sep.
Gillman, D., Lin, Y., Maggs, B., & Sitaraman, R. K. (2015). Protecting websites from attack
with secure delivery networks. Computer, 48(4), 26-34.
Kaur, R., & Kaur, R. (2015). AN OVERVIEW OF CLASSIFICATION OF DDOS
ATTACKS AND DEFENCE MECHANISMS FOR DDOS ATTACKS. Int J Adv
Engg Tech/Vol. VI/Issue II/April-June, 12, 14.
Mallikarjunan, K. N., Muthupriya, K., & Shalinie, S. M. (2016, January). A survey of
distributed denial of service attack. In Intelligent Systems and Control (ISCO), 2016
10th International Conference on (pp. 1-6). Ieee.
McGregor, S. E., Charters, P., Holliday, T., & Roesner, F. (2015, August). Investigating the
Computer Security Practices and Needs of Journalists. In USENIX Security
Symposium(pp. 399-414).
Schwartz. M. (2017). Banks Hit Downtime Milestone In DDoS Attacks. Retrieved from
https://www.darkreading.com/attacks-and-breaches/banks-hit-downtime-milestone-
in-ddos-attacks/d/d-id/1109390.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9 | P a g e
Sridaran, R., & Kilari, N. (2016, March). The performance analysis of NS architecture to
mitigate DDoS attack in cloud environment. In Computing for Sustainable Global
Development (INDIACom), 2016 3rd International Conference on (pp. 3460-3463).
IEEE.
Stavrou, A., Fleck, D., & Kolias, C. (2016). On the Move: Evading Distributed Denial-of-
Service Attacks. IEEE Computer, 49(3), 104-107.
Yu, S. (2014). An overview of DDoS attacks. In Distributed Denial of Service Attack and
Defense (pp. 1-14). Springer, New York, NY.
Sridaran, R., & Kilari, N. (2016, March). The performance analysis of NS architecture to
mitigate DDoS attack in cloud environment. In Computing for Sustainable Global
Development (INDIACom), 2016 3rd International Conference on (pp. 3460-3463).
IEEE.
Stavrou, A., Fleck, D., & Kolias, C. (2016). On the Move: Evading Distributed Denial-of-
Service Attacks. IEEE Computer, 49(3), 104-107.
Yu, S. (2014). An overview of DDoS attacks. In Distributed Denial of Service Attack and
Defense (pp. 1-14). Springer, New York, NY.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




