Design and Security Challenges in Open Banking Applications Deployed in Mobile Devices
VerifiedAdded on 2022/09/07
|43
|12544
|24
AI Summary
.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Design and Security Challenges in Open Banking Applications Deployed in Mobile devices
Name
Institution
Professor
Course
Date
Name
Institution
Professor
Course
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Abstract
Open banking has been adopted by financial institutions to increase the efficiency of the banking
processes. To facilitate open banking, financial institutions provide their APIs which other third
parties use to access and share customer data. Customer grants mobile applications data access
privileges and users can access a unified bank account information at once. Open banking
application has made it easier for customers to manage their funds from different banking
institutions effectively. Despite operational efficiency, open banking mobile application poses
security challenges to financial institutions. Through the sharing of data, confidentiality and
integrity of data may be lost. The security challenges of financial institutions are posed by
mobile applications and operating system vulnerabilities. Security challenges that open mobile
banking applications face are hacking, malware infection, identity theft and loss of data. Open
banking security challenges are mainly caused by poor interfaces, the use of weak encryption
algorithms, and poor implementation of the strong encryption algorithm. System design is an
essential aspect of open banking because developers are required to define system requirements
such as input, output, processing, and data storage. The security of the open banking mobile
application increases if system design and requirements are fully implemented. From the study, it
was observable that PSD2 which was adopted by EU countries to facilitate data sharing needs
some changes. By addressing security issues that are faced by open banking and mobile
applications, it is believed that the security of the data in financial institutions become reliable.
Open banking has been adopted by financial institutions to increase the efficiency of the banking
processes. To facilitate open banking, financial institutions provide their APIs which other third
parties use to access and share customer data. Customer grants mobile applications data access
privileges and users can access a unified bank account information at once. Open banking
application has made it easier for customers to manage their funds from different banking
institutions effectively. Despite operational efficiency, open banking mobile application poses
security challenges to financial institutions. Through the sharing of data, confidentiality and
integrity of data may be lost. The security challenges of financial institutions are posed by
mobile applications and operating system vulnerabilities. Security challenges that open mobile
banking applications face are hacking, malware infection, identity theft and loss of data. Open
banking security challenges are mainly caused by poor interfaces, the use of weak encryption
algorithms, and poor implementation of the strong encryption algorithm. System design is an
essential aspect of open banking because developers are required to define system requirements
such as input, output, processing, and data storage. The security of the open banking mobile
application increases if system design and requirements are fully implemented. From the study, it
was observable that PSD2 which was adopted by EU countries to facilitate data sharing needs
some changes. By addressing security issues that are faced by open banking and mobile
applications, it is believed that the security of the data in financial institutions become reliable.

Contents
Abstract......................................................................................................................................................2
1. Introduction.......................................................................................................................................4
1.1. Motivation..................................................................................................................................5
1.2. Overview of the dissertation chapters......................................................................................5
2. Study Background.............................................................................................................................7
2.1. Problem domain.........................................................................................................................7
3. Literature review...............................................................................................................................9
3.1. What is open banking?............................................................................................................10
3.2. Open Banking Architecture and Mobile Banking at a Glance.............................................10
3.3. Security Challenges in Mobile Application Banking.............................................................12
3.4. IOS security challenges...........................................................................................................12
3.5. Android Security Challenges..................................................................................................15
3.6. Mobile Application Banking Security Challenges.................................................................16
4. Experimental /System Design.........................................................................................................19
4.1. Fundamentals of Open banking application design..............................................................21
4.2. Open Banking Architecture and Design................................................................................22
4.3. Open Banking API’s................................................................................................................25
5. Evaluation........................................................................................................................................28
5.1. Threat Analysis........................................................................................................................28
5.2. Assets........................................................................................................................................28
5.3. Threat agents............................................................................................................................29
5.4. Security threats........................................................................................................................30
5.5. Vulnerabilities..........................................................................................................................31
6. Discussions of findings.....................................................................................................................34
7. Conclusion........................................................................................................................................37
8. Bibliography.....................................................................................................................................38
Abstract......................................................................................................................................................2
1. Introduction.......................................................................................................................................4
1.1. Motivation..................................................................................................................................5
1.2. Overview of the dissertation chapters......................................................................................5
2. Study Background.............................................................................................................................7
2.1. Problem domain.........................................................................................................................7
3. Literature review...............................................................................................................................9
3.1. What is open banking?............................................................................................................10
3.2. Open Banking Architecture and Mobile Banking at a Glance.............................................10
3.3. Security Challenges in Mobile Application Banking.............................................................12
3.4. IOS security challenges...........................................................................................................12
3.5. Android Security Challenges..................................................................................................15
3.6. Mobile Application Banking Security Challenges.................................................................16
4. Experimental /System Design.........................................................................................................19
4.1. Fundamentals of Open banking application design..............................................................21
4.2. Open Banking Architecture and Design................................................................................22
4.3. Open Banking API’s................................................................................................................25
5. Evaluation........................................................................................................................................28
5.1. Threat Analysis........................................................................................................................28
5.2. Assets........................................................................................................................................28
5.3. Threat agents............................................................................................................................29
5.4. Security threats........................................................................................................................30
5.5. Vulnerabilities..........................................................................................................................31
6. Discussions of findings.....................................................................................................................34
7. Conclusion........................................................................................................................................37
8. Bibliography.....................................................................................................................................38

1. Introduction
Open banking is the process of allowing providers to have direct access to financial
information. With open banking, it is possible to have new products or services that are
consumed by users to offer greater value. Customers' are also able to have a better understanding
of their accounts, which makes it possible to benefit more from their money. The power of
fintech, open banking can change how both technologies and consumers interact with each other.
Developers have been using application programming interfaces (APIs) to create a connection to
any payment network and make a display of all billing details. With the adoption of open
banking in the financial sector, cybersecurity remains a fundamental aspect that all stakeholders
should consider. Its deployment in mobile devices creates an environment that poses security
risks to financial institutions. Formulation of strict rules and regulations play a key role in
establishing a strong foundation under which opening banking operates. The implementation of
PSD2 with open banking has affected the global market and regulators are keenly watching its
adoption in the European Union (EU) (Elkhodr, Shahrestani, & Kourouche 2012, pp. 260). To
build and run secure open banking applications, protection measures such as data encryption,
authentication and creating standard operational guidelines make stakeholders stronger. Unless
all stakeholders in the industry come together to create resilient cybersecurity policies,
developing and maintaining secure open banking APIs remain impossible. Customers of the
financial institution should be able to monitor and control their financial spending from mobile
phones. To offer robust services, open banking should be able to offer a strong legislative
framework that helps financial organizations share data securely.
Open banking is the process of allowing providers to have direct access to financial
information. With open banking, it is possible to have new products or services that are
consumed by users to offer greater value. Customers' are also able to have a better understanding
of their accounts, which makes it possible to benefit more from their money. The power of
fintech, open banking can change how both technologies and consumers interact with each other.
Developers have been using application programming interfaces (APIs) to create a connection to
any payment network and make a display of all billing details. With the adoption of open
banking in the financial sector, cybersecurity remains a fundamental aspect that all stakeholders
should consider. Its deployment in mobile devices creates an environment that poses security
risks to financial institutions. Formulation of strict rules and regulations play a key role in
establishing a strong foundation under which opening banking operates. The implementation of
PSD2 with open banking has affected the global market and regulators are keenly watching its
adoption in the European Union (EU) (Elkhodr, Shahrestani, & Kourouche 2012, pp. 260). To
build and run secure open banking applications, protection measures such as data encryption,
authentication and creating standard operational guidelines make stakeholders stronger. Unless
all stakeholders in the industry come together to create resilient cybersecurity policies,
developing and maintaining secure open banking APIs remain impossible. Customers of the
financial institution should be able to monitor and control their financial spending from mobile
phones. To offer robust services, open banking should be able to offer a strong legislative
framework that helps financial organizations share data securely.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1.1. Motivation
In this case, the rationale behind the study has been motivated by the need to understand
open banking security design and challenges deployed in mobile devices. Consumers embrace
the technology without understanding the security challenges associated with it. To understand
open banking security challenges, the study evaluate all stakeholder interactions and required
security standards that all APIs should meet. In this study, several contributions have been
integrated as part of the rationale behind the study.
1. What security challenges does mobile banking application pose on financial institutions?
2. Is open banking applications safe?
3. Was security all concern considered during the design of the PSD2 on data access and
sharing between entities?
4. What security challenges are faced by open banking applications through device
operating systems (OS) such as IOS and Android?
1.2. Overview of the dissertation chapters
The goal of the study is to evaluate open banking on mobile applications to foster a
robust and manageable security framework. The thesis covers different subsections that helped
the researcher to consolidate important pieces of valuable information. The introduction of the
paper starts with a definition of open banking and fundamental aspects that facilitates data
sharing. The architectural overview of open banking (PSD2) presented showcase interactions
between different application programming interfaces (APIs). It highlights different APIs and
technologies which support open banking. The next section presents a rationale and background
of the study. The background of the study is an important section of the thesis because it forms
the basis of the study. It is at this point where the problem of the study is explained in detail.
Technology has posed so many challenges in the banking industry and through the use of open
In this case, the rationale behind the study has been motivated by the need to understand
open banking security design and challenges deployed in mobile devices. Consumers embrace
the technology without understanding the security challenges associated with it. To understand
open banking security challenges, the study evaluate all stakeholder interactions and required
security standards that all APIs should meet. In this study, several contributions have been
integrated as part of the rationale behind the study.
1. What security challenges does mobile banking application pose on financial institutions?
2. Is open banking applications safe?
3. Was security all concern considered during the design of the PSD2 on data access and
sharing between entities?
4. What security challenges are faced by open banking applications through device
operating systems (OS) such as IOS and Android?
1.2. Overview of the dissertation chapters
The goal of the study is to evaluate open banking on mobile applications to foster a
robust and manageable security framework. The thesis covers different subsections that helped
the researcher to consolidate important pieces of valuable information. The introduction of the
paper starts with a definition of open banking and fundamental aspects that facilitates data
sharing. The architectural overview of open banking (PSD2) presented showcase interactions
between different application programming interfaces (APIs). It highlights different APIs and
technologies which support open banking. The next section presents a rationale and background
of the study. The background of the study is an important section of the thesis because it forms
the basis of the study. It is at this point where the problem of the study is explained in detail.
Technology has posed so many challenges in the banking industry and through the use of open

banking practices, security should be addressed effectively. The security concerns should focus
on android security challenges, open banking APIs, security challenges that face IOS, mobile
application banking security challenges and the use of open banking architecture and design. The
fourth section of the thesis evaluate the entire open banking case study and its application in the
financial sector. It presents a consolidated overview of open banking, its application in the
industry, benefits, and success in the market. Threat analysis section evaluate different types of
threats and threat agents, open banking architecture security threats and vulnerabilities that
should be sealed. Security requirements is a major area considering various APIs that connect to
access customers’ financial data. There should be standard security requirements that every API
should meet to start operating in open banking platforms. The next section focuses on a detailed
open banking mobile security analysis. Several aspects such as mobile security threshold and
individual customer precautions are evaluated intensively. Security controls are also analyzed to
provide recommendations to customers and third-party data users on appropriate security
measures.
on android security challenges, open banking APIs, security challenges that face IOS, mobile
application banking security challenges and the use of open banking architecture and design. The
fourth section of the thesis evaluate the entire open banking case study and its application in the
financial sector. It presents a consolidated overview of open banking, its application in the
industry, benefits, and success in the market. Threat analysis section evaluate different types of
threats and threat agents, open banking architecture security threats and vulnerabilities that
should be sealed. Security requirements is a major area considering various APIs that connect to
access customers’ financial data. There should be standard security requirements that every API
should meet to start operating in open banking platforms. The next section focuses on a detailed
open banking mobile security analysis. Several aspects such as mobile security threshold and
individual customer precautions are evaluated intensively. Security controls are also analyzed to
provide recommendations to customers and third-party data users on appropriate security
measures.

2. Study Background
The focus of the study on the security challenges in open banking applications deployed
on mobile has been of great concern in the financial sector. Notably, technology has been greatly
adopted in the banking industry to efficient access to information to customers’. In the banking
industry, data and access to the data remain a key factor because it is used to make financial
decisions. Both customers and banking institutions need to access financial data which is held by
different banking institutions (Elkhodr, Shahrestani, & Kourouche 2012, pp. 260). For banks and
other financial institutions, it has beeen difficult to determine customer creditworthiness in cases
where an individual has more than one account in different banks. On the same note, customers
with money in different accounts from more than one bank have some challenges to have a
consolidated financial overview of all the accounts. With open banking, both customers and
financial institutions are able to eliminate these challenges by having a unified view of financial
status from all individual customers' accounts. The adoption of open banking in the industry is
expected to change both business policies and operating strategies. As organizations embrace
open banking. It is important to evaluate security concerns that should be addressed.
2.1. Problem domain
Mobile application security in financial institutions remains a fundamental aspect that
requires a concerted effort from all stakeholders. To resolve mobile application challenges in the
banking industry, application users' challenges, organizational processes, and software
development security flaws should be addressed. Precisely, financial institutions make use of
different mobile banking applications that have different security vulnerabilities. To address
security flaws associated with different mobile banking applications, financial institutions should
The focus of the study on the security challenges in open banking applications deployed
on mobile has been of great concern in the financial sector. Notably, technology has been greatly
adopted in the banking industry to efficient access to information to customers’. In the banking
industry, data and access to the data remain a key factor because it is used to make financial
decisions. Both customers and banking institutions need to access financial data which is held by
different banking institutions (Elkhodr, Shahrestani, & Kourouche 2012, pp. 260). For banks and
other financial institutions, it has beeen difficult to determine customer creditworthiness in cases
where an individual has more than one account in different banks. On the same note, customers
with money in different accounts from more than one bank have some challenges to have a
consolidated financial overview of all the accounts. With open banking, both customers and
financial institutions are able to eliminate these challenges by having a unified view of financial
status from all individual customers' accounts. The adoption of open banking in the industry is
expected to change both business policies and operating strategies. As organizations embrace
open banking. It is important to evaluate security concerns that should be addressed.
2.1. Problem domain
Mobile application security in financial institutions remains a fundamental aspect that
requires a concerted effort from all stakeholders. To resolve mobile application challenges in the
banking industry, application users' challenges, organizational processes, and software
development security flaws should be addressed. Precisely, financial institutions make use of
different mobile banking applications that have different security vulnerabilities. To address
security flaws associated with different mobile banking applications, financial institutions should
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

outline some security measures that each mobile application should meet for a secure connection
to core banking solutions. On the same note, application developers should make sure mobile
applications meet the minimum security threshold before attempting any connection to banking
solutions.
to core banking solutions. On the same note, application developers should make sure mobile
applications meet the minimum security threshold before attempting any connection to banking
solutions.

3. Literature review
A review of previous studies in mobile banking application security involves the
evaluation of other scholarly articles. The study focuses mainly on security and mobile banking
applications in the banking industry (Elkhodr, Shahrestani, & Kourouche 2012, pp. 260). The use
of mobile banking applications has been on the rise and according to studies, mobile application
usage as surpassed desktop-based applications. Every business requires to reach out to its
customers conveniently and at all times. With the desktop application being unpotable, the
mobile application has dominated the market because it can be accessed conveniently. In the
case of financial institutions that want to offer their services effectively and competitively,
customer satisfaction is the key. To satisfy customers’ in the banking industry, access and use of
their funds from mobile applications should be availed. The review help banking industry
stakeholders to internalize the meaning of mobile banking application, and the meaning and use
of open banking. It also focus on the security challenges in open mobile banking applications,
analyze and design open mobile baking application architecture (He, Tian, & Shen 2015, pp.
104). The security of mobile applications from the mobile operating system (OS) such as the
android and IOS perspective has been done. The review is done from the scholarly articles that
are less than 10 years old since publication. The study evaluates security challenges that are
faced in the banking industry and measures required to control the menace. It brings together
different stakeholders and highlights their respective responsibilities. Finally, threats, threat
agents, and threat control procedures wraps up the study. The study fits the research gap because
it addresses open mobile banking security challenges, which form part of current industrial
problem that need urgent intervention.
A review of previous studies in mobile banking application security involves the
evaluation of other scholarly articles. The study focuses mainly on security and mobile banking
applications in the banking industry (Elkhodr, Shahrestani, & Kourouche 2012, pp. 260). The use
of mobile banking applications has been on the rise and according to studies, mobile application
usage as surpassed desktop-based applications. Every business requires to reach out to its
customers conveniently and at all times. With the desktop application being unpotable, the
mobile application has dominated the market because it can be accessed conveniently. In the
case of financial institutions that want to offer their services effectively and competitively,
customer satisfaction is the key. To satisfy customers’ in the banking industry, access and use of
their funds from mobile applications should be availed. The review help banking industry
stakeholders to internalize the meaning of mobile banking application, and the meaning and use
of open banking. It also focus on the security challenges in open mobile banking applications,
analyze and design open mobile baking application architecture (He, Tian, & Shen 2015, pp.
104). The security of mobile applications from the mobile operating system (OS) such as the
android and IOS perspective has been done. The review is done from the scholarly articles that
are less than 10 years old since publication. The study evaluates security challenges that are
faced in the banking industry and measures required to control the menace. It brings together
different stakeholders and highlights their respective responsibilities. Finally, threats, threat
agents, and threat control procedures wraps up the study. The study fits the research gap because
it addresses open mobile banking security challenges, which form part of current industrial
problem that need urgent intervention.

3.1. What is open banking?
Open banking (PSD2) is a new and secure way through which consumers share
information to allow both new and other existing companies to provide efficient payment
methods and innovative products in the industry (Bharti 2016, pp. 13). It is also known to be
“open bank data”, and a practice used by banking institutions to provide data access to third
parties. The data exposed to third parties include transaction data, consumer banking, and
financial which is exposed through APIs. In an open banking environment, all stakeholders can
access and share data for use by other service providers, consumers, and financial institutions. To
facilitate open banking, banks are required to get customer consent to allow the sharing of
financial data. Customer consent can be in the form of a checkbox with appropriate terms of the
agreement in a mobile online banking application. In open banking, electronic sharing of
financial data should be secure and governed by terms of service approved by the consumer. In
current banking scenarios, it is not possible to manage two different accounts at the same time
from different banks due to the incompatibility of the systems (Hadad 2019, pp. 343). With the
introduction and use of open banking, consumers are able to access and manage their money
from all accounts at once. It is expected to centralize all customer's banking data for ease of
money management, lending, and payment processes. Therefore, Open banking has been
categorized as an innovation expected to change the nature and operations of the banking
industry.
3.2. Open Banking Architecture and Mobile Banking at a Glance
Open banking architecture involves the integration of different entities and stakeholders
into a single business process. With the innovation and acceptance of PSD2 by European Union
(EU) countries, the architecture was compressed to eliminate mobile banking applications for
Open banking (PSD2) is a new and secure way through which consumers share
information to allow both new and other existing companies to provide efficient payment
methods and innovative products in the industry (Bharti 2016, pp. 13). It is also known to be
“open bank data”, and a practice used by banking institutions to provide data access to third
parties. The data exposed to third parties include transaction data, consumer banking, and
financial which is exposed through APIs. In an open banking environment, all stakeholders can
access and share data for use by other service providers, consumers, and financial institutions. To
facilitate open banking, banks are required to get customer consent to allow the sharing of
financial data. Customer consent can be in the form of a checkbox with appropriate terms of the
agreement in a mobile online banking application. In open banking, electronic sharing of
financial data should be secure and governed by terms of service approved by the consumer. In
current banking scenarios, it is not possible to manage two different accounts at the same time
from different banks due to the incompatibility of the systems (Hadad 2019, pp. 343). With the
introduction and use of open banking, consumers are able to access and manage their money
from all accounts at once. It is expected to centralize all customer's banking data for ease of
money management, lending, and payment processes. Therefore, Open banking has been
categorized as an innovation expected to change the nature and operations of the banking
industry.
3.2. Open Banking Architecture and Mobile Banking at a Glance
Open banking architecture involves the integration of different entities and stakeholders
into a single business process. With the innovation and acceptance of PSD2 by European Union
(EU) countries, the architecture was compressed to eliminate mobile banking applications for
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
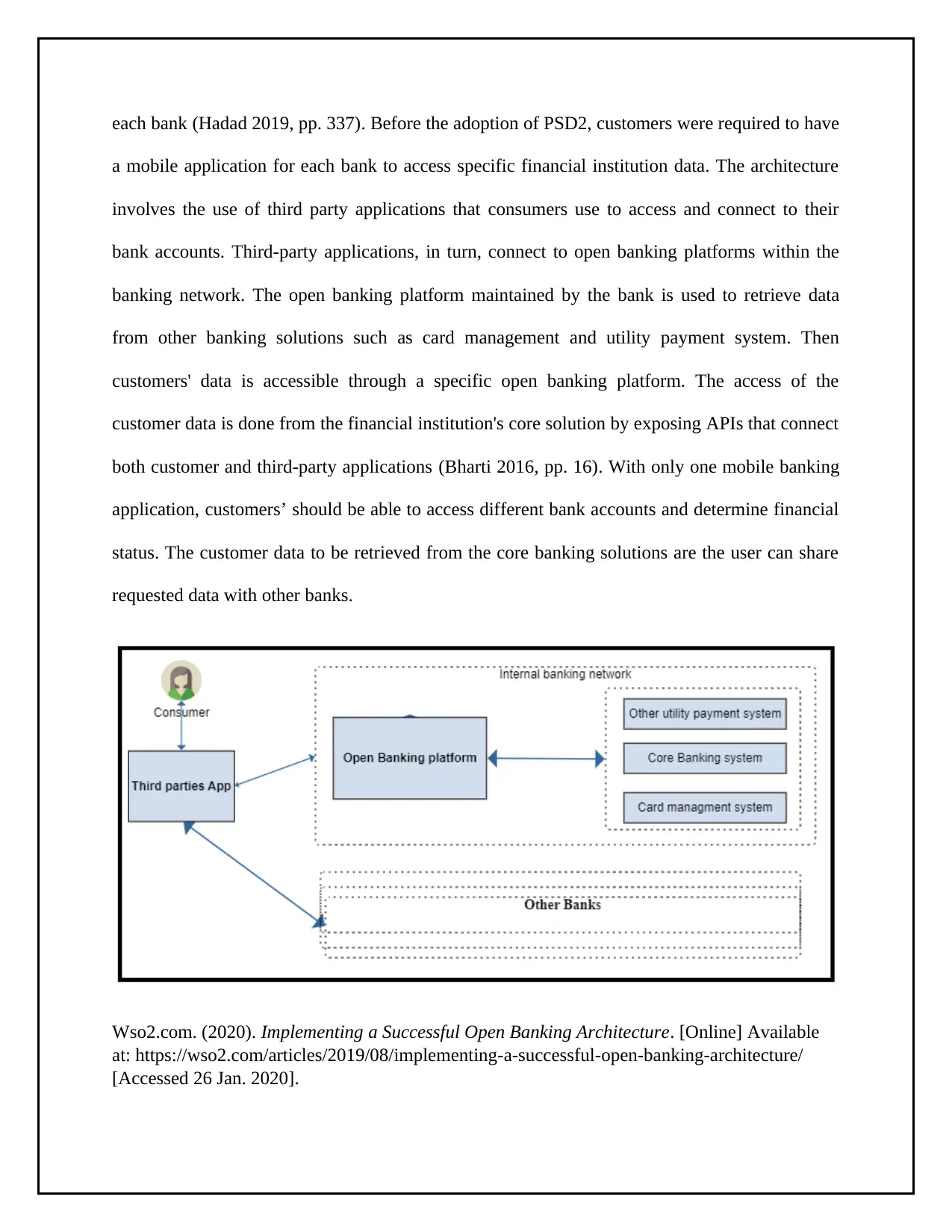
each bank (Hadad 2019, pp. 337). Before the adoption of PSD2, customers were required to have
a mobile application for each bank to access specific financial institution data. The architecture
involves the use of third party applications that consumers use to access and connect to their
bank accounts. Third-party applications, in turn, connect to open banking platforms within the
banking network. The open banking platform maintained by the bank is used to retrieve data
from other banking solutions such as card management and utility payment system. Then
customers' data is accessible through a specific open banking platform. The access of the
customer data is done from the financial institution's core solution by exposing APIs that connect
both customer and third-party applications (Bharti 2016, pp. 16). With only one mobile banking
application, customers’ should be able to access different bank accounts and determine financial
status. The customer data to be retrieved from the core banking solutions are the user can share
requested data with other banks.
Wso2.com. (2020). Implementing a Successful Open Banking Architecture. [Online] Available
at: https://wso2.com/articles/2019/08/implementing-a-successful-open-banking-architecture/
[Accessed 26 Jan. 2020].
a mobile application for each bank to access specific financial institution data. The architecture
involves the use of third party applications that consumers use to access and connect to their
bank accounts. Third-party applications, in turn, connect to open banking platforms within the
banking network. The open banking platform maintained by the bank is used to retrieve data
from other banking solutions such as card management and utility payment system. Then
customers' data is accessible through a specific open banking platform. The access of the
customer data is done from the financial institution's core solution by exposing APIs that connect
both customer and third-party applications (Bharti 2016, pp. 16). With only one mobile banking
application, customers’ should be able to access different bank accounts and determine financial
status. The customer data to be retrieved from the core banking solutions are the user can share
requested data with other banks.
Wso2.com. (2020). Implementing a Successful Open Banking Architecture. [Online] Available
at: https://wso2.com/articles/2019/08/implementing-a-successful-open-banking-architecture/
[Accessed 26 Jan. 2020].

3.3. Security Challenges in Mobile Application Banking
Mobile banking is regarded as one of the most important innovations in the banking
sector. Despite its advantages, it has been linked to the number of risks. Mobile application
developers need to uphold the highest standards of security (Sharma 2016, pp. 304). Data
security in mobile banking remains complex due to; organizational employee behavior.
Application users' in the banking industry form a key component of security challenges that
financial institutions should address. The behavior of the users should be controlled by creating
specific privileges for application users within banking institutions. Next, specific organizational
business procedures have been identified as a security problem that organizations should
implement to minimize security challenges that are associated with a mobile application in the
banking sector. On the same note, flaws related to software are quite common and financial
institutions should be held mobile application developers accountable for security flaws that
associated wit code bugs. All stakeholders in the banking sector should understand that a single
security flaw cannot be corrected by other security measures (Solanki 2012, pp. 2277). In this
case, it is important to evaluate and test all security flaws in mobile application banking
frequently.
3.4. IOS security challenges
Applications are believed to have some security flaws despite the effort that system
developers implement as security measures. Apple Inc. has implemented strong security
measures but different types of security issues have been faced by IOS users. Some of the IOS
security issues that the banking industry should address are mainly categorized as Open Web
Application Security Project (OWASP). The first IOS security challenge that should be
addressed is the improper use of mobile banking applications by different stakeholders (He,
Mobile banking is regarded as one of the most important innovations in the banking
sector. Despite its advantages, it has been linked to the number of risks. Mobile application
developers need to uphold the highest standards of security (Sharma 2016, pp. 304). Data
security in mobile banking remains complex due to; organizational employee behavior.
Application users' in the banking industry form a key component of security challenges that
financial institutions should address. The behavior of the users should be controlled by creating
specific privileges for application users within banking institutions. Next, specific organizational
business procedures have been identified as a security problem that organizations should
implement to minimize security challenges that are associated with a mobile application in the
banking sector. On the same note, flaws related to software are quite common and financial
institutions should be held mobile application developers accountable for security flaws that
associated wit code bugs. All stakeholders in the banking sector should understand that a single
security flaw cannot be corrected by other security measures (Solanki 2012, pp. 2277). In this
case, it is important to evaluate and test all security flaws in mobile application banking
frequently.
3.4. IOS security challenges
Applications are believed to have some security flaws despite the effort that system
developers implement as security measures. Apple Inc. has implemented strong security
measures but different types of security issues have been faced by IOS users. Some of the IOS
security issues that the banking industry should address are mainly categorized as Open Web
Application Security Project (OWASP). The first IOS security challenge that should be
addressed is the improper use of mobile banking applications by different stakeholders (He,

Tian, & Shen 2015, pp. 104). IOS provides users with unique security parameters such as
permission systems and failure by users to make use of them is considered a security flaw. As a
development platform, IOS offers specific guidelines to be followed by developers if secure
mobile applications are to be accorded a top priority. Failing to uphold proper implementation
features by application developers can result in sensitive data being corrupted. The next IOS
security challenge that mobile application developers should be concerned about is the insecure
storage of data. Every mobile application in the banking industry stores and use data (Al-Sabri,
& Al-Saleem 2013, pp. 259). To store sensitive data required by financial institutions, data
storage solutions such as internal storage features should be very secure. In most cases, securing
internal data storage is recommended as a means of preventing data leak. Failure to protect
confidential data leads to data access by unauthorized users who can use the data for illegal
activities such as money laundering.
Additionally, insecure communication between data applications and other data sources
including servers and Bluetooth enabled devices is a security challenge in IOS devices. It is
inevitable for mobile applications to communicate and share data because they majorly work
through data sharing. Considering each mobile application has its security flaws, adequate data
protection measures while on the transmission is important to prevent potential data leaks
(Handa, & Singh 2015, pp. 786). With readily available tools to access external data while on
transmission, insecure data sharing results in data breaches such as identity theft. The next IOS
security challenge is insecure authentication when accessing the internal functionality of mobile
banking applications (Hanafizadeh et al 2014, pp. 62). Applications provide users with various
authentication measures such as PINs, specific user ids, strong passwords, and fingerprint
scanning. It is important to note that strong authentication measures allow mobile application
permission systems and failure by users to make use of them is considered a security flaw. As a
development platform, IOS offers specific guidelines to be followed by developers if secure
mobile applications are to be accorded a top priority. Failing to uphold proper implementation
features by application developers can result in sensitive data being corrupted. The next IOS
security challenge that mobile application developers should be concerned about is the insecure
storage of data. Every mobile application in the banking industry stores and use data (Al-Sabri,
& Al-Saleem 2013, pp. 259). To store sensitive data required by financial institutions, data
storage solutions such as internal storage features should be very secure. In most cases, securing
internal data storage is recommended as a means of preventing data leak. Failure to protect
confidential data leads to data access by unauthorized users who can use the data for illegal
activities such as money laundering.
Additionally, insecure communication between data applications and other data sources
including servers and Bluetooth enabled devices is a security challenge in IOS devices. It is
inevitable for mobile applications to communicate and share data because they majorly work
through data sharing. Considering each mobile application has its security flaws, adequate data
protection measures while on the transmission is important to prevent potential data leaks
(Handa, & Singh 2015, pp. 786). With readily available tools to access external data while on
transmission, insecure data sharing results in data breaches such as identity theft. The next IOS
security challenge is insecure authentication when accessing the internal functionality of mobile
banking applications (Hanafizadeh et al 2014, pp. 62). Applications provide users with various
authentication measures such as PINs, specific user ids, strong passwords, and fingerprint
scanning. It is important to note that strong authentication measures allow mobile application
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

users to secure manage all assets within the application. Mobile application developers and users
should make sure strong authentication and validation measures are implemented in applications.
Weak authentication security measures are easier to bypass and expose sensitive data to
unauthorized users (Goyal, Pandey, & Batra 2012, pp. 87). It is the responsibility of the
developers to enforce the use of strong authentication measures such as the use of strong
passwords and change of passwords expiry dates. On the other hand, mobile application users are
expected to adhere to secure authentication measures provided by mobile application developers.
Similarly, insufficient data cryptography has proved to be a great challenge in mobile
banking applications. Cryptography with a strong transformation algorithm is required to
transform mobile application raw data into secure data packages (Islam 2014, pp. 114).
Encryption is regarded as a secure means of protecting data because it is impossible to either
read the data. Encrypted data is useless as it requires high processing power and too much time
to break encrypted data. Despite encryption being a secure means of protecting data, weak
encryption algorithms expose sensitive data to attackers (Das, & Debbarma 2011, pp. 162). Code
quality is an important aspect that should be observed by mobile application developers. It is not
simple to measure code quality, but some coding quality parameters such as proper code layering
and consistency in coding style must be enforced. The use of poor coding techniques makes it
difficult to use and maintain an application for a long period. Change in a block of code when
adding new features may introduce the subjected application to vulnerabilities. In most cases,
attackers make use of complex code analysis tools to evaluate code vulnerabilities and extract
required data without knowledge of the application user (Xavier, & Pati 2012, pp. 219). Finally,
code tempering is believed to be a complex security challenge in mobile application banking.
Hackers with code development skills can change some blocks of code or replicate some binary
should make sure strong authentication and validation measures are implemented in applications.
Weak authentication security measures are easier to bypass and expose sensitive data to
unauthorized users (Goyal, Pandey, & Batra 2012, pp. 87). It is the responsibility of the
developers to enforce the use of strong authentication measures such as the use of strong
passwords and change of passwords expiry dates. On the other hand, mobile application users are
expected to adhere to secure authentication measures provided by mobile application developers.
Similarly, insufficient data cryptography has proved to be a great challenge in mobile
banking applications. Cryptography with a strong transformation algorithm is required to
transform mobile application raw data into secure data packages (Islam 2014, pp. 114).
Encryption is regarded as a secure means of protecting data because it is impossible to either
read the data. Encrypted data is useless as it requires high processing power and too much time
to break encrypted data. Despite encryption being a secure means of protecting data, weak
encryption algorithms expose sensitive data to attackers (Das, & Debbarma 2011, pp. 162). Code
quality is an important aspect that should be observed by mobile application developers. It is not
simple to measure code quality, but some coding quality parameters such as proper code layering
and consistency in coding style must be enforced. The use of poor coding techniques makes it
difficult to use and maintain an application for a long period. Change in a block of code when
adding new features may introduce the subjected application to vulnerabilities. In most cases,
attackers make use of complex code analysis tools to evaluate code vulnerabilities and extract
required data without knowledge of the application user (Xavier, & Pati 2012, pp. 219). Finally,
code tempering is believed to be a complex security challenge in mobile application banking.
Hackers with code development skills can change some blocks of code or replicate some binary

codes. Once the code is changed, attackers can execute code and affect application programming
interfaces (API) calls and affect application functionality by running some malicious codes
(Devadevan 2013, pp. 518). In most cases, attackers are known to distribute malicious codes
through phishing. By tampering with the code, attackers can intercept any form of
communication between IOS applications and steal data. It is also possible to gain authorized
access to either part of an entire mobile application such as internal data storage.
3.5. Android Security Challenges
Most of the devices such as smartphones and tablets are running on the Android
Operating System (OS). Cybercriminals have been targeting devices that run on Android because
their users use them to conduct online transactions from their bank accounts. With an increase in
online purchases from Android devices, security challenges should be of great concern to both
user and application developers (Handa, & Singh 2015, pp. 787). The first security concern with
Android devices is application-focused due to an increase in instant messaging and music mobile
applications. Considering one Android device can support several applications, attackers do not
focus on financial related applications. To gain access to mobile banking applications without
knowledge of the user, attackers gain access to the Android device through less suspicious
Applications. Once backdoor access is available, it is possible to extract logs related to mobile
banking applications and analyze them to get its related authentication sensitive data. It is a
common problem with application users to allow other mobile applications to access data within
the device. The vulnerable mobile application allows some data to be collected by malicious
actors and use it for social engineering attacks (Singh 2013, pp. 97). As a result, mobile
application users are convinced to provide sensitive data to untrusted entities. On the same note,
interfaces (API) calls and affect application functionality by running some malicious codes
(Devadevan 2013, pp. 518). In most cases, attackers are known to distribute malicious codes
through phishing. By tampering with the code, attackers can intercept any form of
communication between IOS applications and steal data. It is also possible to gain authorized
access to either part of an entire mobile application such as internal data storage.
3.5. Android Security Challenges
Most of the devices such as smartphones and tablets are running on the Android
Operating System (OS). Cybercriminals have been targeting devices that run on Android because
their users use them to conduct online transactions from their bank accounts. With an increase in
online purchases from Android devices, security challenges should be of great concern to both
user and application developers (Handa, & Singh 2015, pp. 787). The first security concern with
Android devices is application-focused due to an increase in instant messaging and music mobile
applications. Considering one Android device can support several applications, attackers do not
focus on financial related applications. To gain access to mobile banking applications without
knowledge of the user, attackers gain access to the Android device through less suspicious
Applications. Once backdoor access is available, it is possible to extract logs related to mobile
banking applications and analyze them to get its related authentication sensitive data. It is a
common problem with application users to allow other mobile applications to access data within
the device. The vulnerable mobile application allows some data to be collected by malicious
actors and use it for social engineering attacks (Singh 2013, pp. 97). As a result, mobile
application users are convinced to provide sensitive data to untrusted entities. On the same note,

mobile application users running on Android should be very careful with application installation
because viruses and worms can be hidden from some mobile applications.
The next Android security challenge is component-based threats that focus on both
hardware and software components with the android device. Some of the components that
attackers have been focusing on include Wi-Fi and Bluetooth which can be used to exploit
devices without user’s knowledge (Islam 2014, pp. 109). Both Wi-Fi and Bluetooth enabled
devices can provide an attacker with remote access to the specific mobile device and use it to
perform unauthorized activities. Attackers can also use such devices to install malware and
viruses on such devices. The installed malware can be used to extract sensitive data and monitor
specific transactions that can be used against the target user. Threats from cheap and old Android
versions of phones pose major security threats because most of the versions are not upgradable.
Old versions of technology both in hardware and software are vulnerable to security threats such
as malware and hackers (Bamoriya, & Singh P., 2011, pp. 116). New technologies are usually
incorporated into the newer versions of Android phones making it more secure. As developers
design and come up with new versions of Android, new security threats are considered and the
existing loopholes are sealed. Finally, Android instant application security has been a great
challenge in mobile banking applications. The effects of instant Applications on Android phones
are not clear and it can cause serious security challenges to financial institutions.
3.6. Mobile Application Banking Security Challenges
The banking industry remains a robust and sensitive sector in today's business and there
is a need to embrace mobile technology with caution. Despite mobile banking application is very
convenient, they are believed to pose serious security threats due to some vulnerabilities
associated channels. Some of the security challenges associated with mobile applications in the
because viruses and worms can be hidden from some mobile applications.
The next Android security challenge is component-based threats that focus on both
hardware and software components with the android device. Some of the components that
attackers have been focusing on include Wi-Fi and Bluetooth which can be used to exploit
devices without user’s knowledge (Islam 2014, pp. 109). Both Wi-Fi and Bluetooth enabled
devices can provide an attacker with remote access to the specific mobile device and use it to
perform unauthorized activities. Attackers can also use such devices to install malware and
viruses on such devices. The installed malware can be used to extract sensitive data and monitor
specific transactions that can be used against the target user. Threats from cheap and old Android
versions of phones pose major security threats because most of the versions are not upgradable.
Old versions of technology both in hardware and software are vulnerable to security threats such
as malware and hackers (Bamoriya, & Singh P., 2011, pp. 116). New technologies are usually
incorporated into the newer versions of Android phones making it more secure. As developers
design and come up with new versions of Android, new security threats are considered and the
existing loopholes are sealed. Finally, Android instant application security has been a great
challenge in mobile banking applications. The effects of instant Applications on Android phones
are not clear and it can cause serious security challenges to financial institutions.
3.6. Mobile Application Banking Security Challenges
The banking industry remains a robust and sensitive sector in today's business and there
is a need to embrace mobile technology with caution. Despite mobile banking application is very
convenient, they are believed to pose serious security threats due to some vulnerabilities
associated channels. Some of the security challenges associated with mobile applications in the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

banking industry are; poor mobile application design and configurations which make stored data
vulnerable to attacks (Driga, & Isac 2014, pp. 49-50). Banking mobile applications are regarded
as safe than banking practices on a mobile browser. However, with the ever-increasing number
of data breaches in financial institutions, security lapses have been directly linked to poor coding
practices and code quality. It is important for mobile developers and particularly in the banking
industry to understand each mobile platform has its unique requirements. By understanding
specific mobile security parameters, it is possible for developers to mitigate most of the security
challenges. It is of great concern that most of the mobile application developers lack skills and
knowledge on current security risks. This leaves the security of data at risk of being
compromised by hackers and other untrusted third parties. Next, the operating system (OS)
cryptographic vulnerabilities due to lack of adequate secure socket layer (SSL) implementation.
In mobile applications, application developers need to implement certificate validation in the
transport layer of the network (Bamoriya, & Singh P., 2011, pp. 118). Cryptographic in mobile
banking applications can be implemented by the application developers in every digital security
protocol to facilitate the establishment of encrypted communication links. Secure communication
links between applications and external data sources help to validate all communicating entities
to prevent threats such as man-in-middle and phishing attacks.
Moreover, there has been an explosive rise in malware attacks on mobile devices.
Malware attacks are usually propagated through software bugs and hackers are exploiting
vulnerabilities in mobile application banking for possibilities of launching attacks (Driga, & Isac
2014, pp. 49). Malicious programs are developed and executed on a target program to exploit the
possibilities of attacks. Both application developers and users should enforce security measures
due to the rise in malware and virus attacks. Flawed authentication is another security challenge
vulnerable to attacks (Driga, & Isac 2014, pp. 49-50). Banking mobile applications are regarded
as safe than banking practices on a mobile browser. However, with the ever-increasing number
of data breaches in financial institutions, security lapses have been directly linked to poor coding
practices and code quality. It is important for mobile developers and particularly in the banking
industry to understand each mobile platform has its unique requirements. By understanding
specific mobile security parameters, it is possible for developers to mitigate most of the security
challenges. It is of great concern that most of the mobile application developers lack skills and
knowledge on current security risks. This leaves the security of data at risk of being
compromised by hackers and other untrusted third parties. Next, the operating system (OS)
cryptographic vulnerabilities due to lack of adequate secure socket layer (SSL) implementation.
In mobile applications, application developers need to implement certificate validation in the
transport layer of the network (Bamoriya, & Singh P., 2011, pp. 118). Cryptographic in mobile
banking applications can be implemented by the application developers in every digital security
protocol to facilitate the establishment of encrypted communication links. Secure communication
links between applications and external data sources help to validate all communicating entities
to prevent threats such as man-in-middle and phishing attacks.
Moreover, there has been an explosive rise in malware attacks on mobile devices.
Malware attacks are usually propagated through software bugs and hackers are exploiting
vulnerabilities in mobile application banking for possibilities of launching attacks (Driga, & Isac
2014, pp. 49). Malicious programs are developed and executed on a target program to exploit the
possibilities of attacks. Both application developers and users should enforce security measures
due to the rise in malware and virus attacks. Flawed authentication is another security challenge

in mobile banking applications as fraudsters try to exploit exiting application weaknesses to
collect sensitive data. Financial institutions fail to provide mobile application users with secure
authentication measures results in security flaws. Banks have been relying on two-factor
authentication and one-time password (OTP) which has turned to be obsolete due to
technological innovation. Finally, the lack of sufficient oversight in a fast-growing technological
ecosystem by the government has created security flaws in the mobile application banking
industry. Federal Financial Institution Examination Council (FFIEC) has published some
guidelines that mobile banking applications should meet. However, the same council has failed
to address standard controls on mobile banking application regarding identification and
authentication controls (Bamoriya, & Singh P., 2011, pp. 118). The greatest challenge on
authentication and identification is that other bodies have tried to provide guidelines, but it has
not been substantive to solve financial institutions' mobile banking security challenges. Financial
institutions must establish a high level of trust on mobile channels if they have to remain
competitive.
collect sensitive data. Financial institutions fail to provide mobile application users with secure
authentication measures results in security flaws. Banks have been relying on two-factor
authentication and one-time password (OTP) which has turned to be obsolete due to
technological innovation. Finally, the lack of sufficient oversight in a fast-growing technological
ecosystem by the government has created security flaws in the mobile application banking
industry. Federal Financial Institution Examination Council (FFIEC) has published some
guidelines that mobile banking applications should meet. However, the same council has failed
to address standard controls on mobile banking application regarding identification and
authentication controls (Bamoriya, & Singh P., 2011, pp. 118). The greatest challenge on
authentication and identification is that other bodies have tried to provide guidelines, but it has
not been substantive to solve financial institutions' mobile banking security challenges. Financial
institutions must establish a high level of trust on mobile channels if they have to remain
competitive.

4. Experimental /System Design
The design of the system involves the processes of defining open banking architecture,
working interfaces, different modules, and required data to meet specific banking requirements.
System design is used by banking institutions to provide comprehensive data about open banking
and its components to facilitate architectural design consistency. The open banking institutions
have different requirements that each mobile banking application should meet before accessing
the required data (Asfaw 2015, pp. 101). The system design context can be sub-divided into
various modules which include; process, interface and working data design. The design of the
system should consider different aspects such as input requirements. In open banking, the input
requirements define the customer data used to access the mobile banking application. Once
validation and authentication of the data are performed the open banking platforms provide
access to the customers' data (Omar et al 2011, pp. 56-57). The input requirements should meet
minimum security aspects such as data encryption and character hiding during data input. The
other security parameter that open banking applications should meet is user validation through
One Time Pin (OTP). It is one of the modern data validation technique which is highly reliable
and convenient. During the system design process, output requirements should conform to the
standard banking specifications. Data retrieval and transmission should not interfere with
confidentiality and integrity (Tiwari, Agarwal, & Goyal 2014, pp. 271). To make sure security
requirements are met, the design processes should be guided by data security principles. Before
The design of the system involves the processes of defining open banking architecture,
working interfaces, different modules, and required data to meet specific banking requirements.
System design is used by banking institutions to provide comprehensive data about open banking
and its components to facilitate architectural design consistency. The open banking institutions
have different requirements that each mobile banking application should meet before accessing
the required data (Asfaw 2015, pp. 101). The system design context can be sub-divided into
various modules which include; process, interface and working data design. The design of the
system should consider different aspects such as input requirements. In open banking, the input
requirements define the customer data used to access the mobile banking application. Once
validation and authentication of the data are performed the open banking platforms provide
access to the customers' data (Omar et al 2011, pp. 56-57). The input requirements should meet
minimum security aspects such as data encryption and character hiding during data input. The
other security parameter that open banking applications should meet is user validation through
One Time Pin (OTP). It is one of the modern data validation technique which is highly reliable
and convenient. During the system design process, output requirements should conform to the
standard banking specifications. Data retrieval and transmission should not interfere with
confidentiality and integrity (Tiwari, Agarwal, & Goyal 2014, pp. 271). To make sure security
requirements are met, the design processes should be guided by data security principles. Before
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

exposing customer data to third parties, all applications should prompt the customer to grant
access to the data.
The next type of system design requirement is storage which focuses mainly on the data
storage security requirements. Data storage is very critical because it requires data to be
protected from unauthorized access by third parties. The design should be enforced to make sure
data is stored securely and only accessible to authorized users (Prasad, Gyani, & Murti 2012, pp.
8). Mobile banking applications that access data should be designed with the highest security
requirements that conform to current banking standards. Any data storage within the mobile
banking applications should not be allowed because it can be accessed and used fraudulently by
unauthorized persons. The design should make sure that all data stored by the financial
institutions be encrypted for security purposes. Data encryption is a fundamental security
concern that every organization should use to protected data from fraudulent use even after
unauthorized data access. Encryption makes data unusable and it is the security mechanism that
guarantees the security of the data if the encryption algorithm is strong. System control and
backup for recovery during IT infrastructure disaster is very important system design aspect.
Organizations should be prepared for any eventuality because IT infrastructure is prone to failure
(Bamoriya, & Singh P., 2011, pp. 112). Data backup should be done frequently to make sure
recovery options are readily available to avoid data loss and business process interruption. To
avoid data loss, the system design should be automated to facilitate data backup without user
interventions. The final system design requirement that mobile banking applications should meet
is data processing criteria. To process data requests from any application user, open banking
platforms should be enforced to make sure the processing of data is specific to the user request.
Some mobile banking applications are designed with capabilities of accessing data from backed
access to the data.
The next type of system design requirement is storage which focuses mainly on the data
storage security requirements. Data storage is very critical because it requires data to be
protected from unauthorized access by third parties. The design should be enforced to make sure
data is stored securely and only accessible to authorized users (Prasad, Gyani, & Murti 2012, pp.
8). Mobile banking applications that access data should be designed with the highest security
requirements that conform to current banking standards. Any data storage within the mobile
banking applications should not be allowed because it can be accessed and used fraudulently by
unauthorized persons. The design should make sure that all data stored by the financial
institutions be encrypted for security purposes. Data encryption is a fundamental security
concern that every organization should use to protected data from fraudulent use even after
unauthorized data access. Encryption makes data unusable and it is the security mechanism that
guarantees the security of the data if the encryption algorithm is strong. System control and
backup for recovery during IT infrastructure disaster is very important system design aspect.
Organizations should be prepared for any eventuality because IT infrastructure is prone to failure
(Bamoriya, & Singh P., 2011, pp. 112). Data backup should be done frequently to make sure
recovery options are readily available to avoid data loss and business process interruption. To
avoid data loss, the system design should be automated to facilitate data backup without user
interventions. The final system design requirement that mobile banking applications should meet
is data processing criteria. To process data requests from any application user, open banking
platforms should be enforced to make sure the processing of data is specific to the user request.
Some mobile banking applications are designed with capabilities of accessing data from backed

without application user permissions (Gupta, Bagoria, & Bagoria 2013, pp. 4-5). Backed data
access is regarded as fraudulent activity and financial institutions should strictly define
requirements that each mobile application should meet. To avoid backed data access, financial
institutions should put in place strict measures that prohibit data protection.
4.1. Fundamentals of Open banking application design
System design is quite specific on what each stakeholder is expected to do in product
design. In the design of the system, system designers should address some concerns that are
mainly used to evaluate system quality. System reliability is a fundamental aspect that measures
system ability to withstand fault tolerance to make sure the system does not fail (Tiwari,
Agarwal, & Goyal 2014, pp. 271). System developers need to build large systems through the
use of components that are fault intolerance in nature. When systems are developed with fault
intolerance components, the subjected system is expected to be reliable because it does not fail
frequently. Open banking applications should be fault tolerance to make them reliable at all
times and when required by users. Faults can either be hardware or software but the main focus,
in this case, is software fault tolerance. Software faults can be caused by a variety of reasons
such as bug, malware and code compromise. Important to note is that a runaway system process
can over-utilize system resources and cause application failure across various nodes that are
running the Application. It is only through the understanding of the business requirements that
mobile application faults can be resiliently handled. System developers should implement
application communication features that can support user interaction to support application
monitoring (Bhuiyan, & Rahman 2013, pp. 54-55). Better application unit testing and the use of
abstraction in the design processes can be easily used to isolate faults in mobile banking
applications.
access is regarded as fraudulent activity and financial institutions should strictly define
requirements that each mobile application should meet. To avoid backed data access, financial
institutions should put in place strict measures that prohibit data protection.
4.1. Fundamentals of Open banking application design
System design is quite specific on what each stakeholder is expected to do in product
design. In the design of the system, system designers should address some concerns that are
mainly used to evaluate system quality. System reliability is a fundamental aspect that measures
system ability to withstand fault tolerance to make sure the system does not fail (Tiwari,
Agarwal, & Goyal 2014, pp. 271). System developers need to build large systems through the
use of components that are fault intolerance in nature. When systems are developed with fault
intolerance components, the subjected system is expected to be reliable because it does not fail
frequently. Open banking applications should be fault tolerance to make them reliable at all
times and when required by users. Faults can either be hardware or software but the main focus,
in this case, is software fault tolerance. Software faults can be caused by a variety of reasons
such as bug, malware and code compromise. Important to note is that a runaway system process
can over-utilize system resources and cause application failure across various nodes that are
running the Application. It is only through the understanding of the business requirements that
mobile application faults can be resiliently handled. System developers should implement
application communication features that can support user interaction to support application
monitoring (Bhuiyan, & Rahman 2013, pp. 54-55). Better application unit testing and the use of
abstraction in the design processes can be easily used to isolate faults in mobile banking
applications.

The next application development fundamental is the scalability which is the mobile
banking application ability to offer required performance. The performance of the subjected
application should remain the same despite the increase in any form of system load. The
application load is used to describe operational characteristics concerning changing application
load parameters. In open mobile applications, performance can be measured regarding its
response time (Bahl 2012, pp. 229). The time is taken for a mobile application to submit a
request or process a request presents an ideal measure of the performance. It is the responsibility
of the system developers to make sure the system is scalable and can offer the required
functionality effectively. Finally, system maintainability is meant to understand code layout
during application development. System developers need to adopt modularity in the application
design for ease of understanding the code, refactoring and upgrading. Original system designers
might not be available for upgrade and there is a need to have a code that can be understood by
others. For any application to have maintainability characteristics, it should be readable and
easily understood by other developers (Driga, & Isac 2014, pp. 49). The code should have a high
level of system abstraction so that users do not understand the internal functionality of the
system. Considering open mobile banking applications rely on APIs, interfaces and clean APIs
are requirement to make it possible to upgrade the system in the future. System upgrade is
unavoidable and application developers should be aware of the future user requirements.
4.2. Open Banking Architecture and Design
It is important for banking institutions to establish successful open mobile banking
architecture if they need to benefit from open banking technology. The nature of the open
banking chosen by any financial institution is the key determinant of the effectiveness of the
chosen APIs. The effectiveness of the APIs help banks to provide third parties with a seamless
experience to customers than competitors. The design of open banking should allow banks to
banking application ability to offer required performance. The performance of the subjected
application should remain the same despite the increase in any form of system load. The
application load is used to describe operational characteristics concerning changing application
load parameters. In open mobile applications, performance can be measured regarding its
response time (Bahl 2012, pp. 229). The time is taken for a mobile application to submit a
request or process a request presents an ideal measure of the performance. It is the responsibility
of the system developers to make sure the system is scalable and can offer the required
functionality effectively. Finally, system maintainability is meant to understand code layout
during application development. System developers need to adopt modularity in the application
design for ease of understanding the code, refactoring and upgrading. Original system designers
might not be available for upgrade and there is a need to have a code that can be understood by
others. For any application to have maintainability characteristics, it should be readable and
easily understood by other developers (Driga, & Isac 2014, pp. 49). The code should have a high
level of system abstraction so that users do not understand the internal functionality of the
system. Considering open mobile banking applications rely on APIs, interfaces and clean APIs
are requirement to make it possible to upgrade the system in the future. System upgrade is
unavoidable and application developers should be aware of the future user requirements.
4.2. Open Banking Architecture and Design
It is important for banking institutions to establish successful open mobile banking
architecture if they need to benefit from open banking technology. The nature of the open
banking chosen by any financial institution is the key determinant of the effectiveness of the
chosen APIs. The effectiveness of the APIs help banks to provide third parties with a seamless
experience to customers than competitors. The design of open banking should allow banks to
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

expose their internal data to external data sources (Kujur, & Shah 2015, pp. 209). To securely
and successfully implement APIs, a set of key requirements, both functional and non-functional
should be established. The first requirement that banks should consider when designing open
banking architecture is an API specification. Proper API specification in open banking help
financial institutions to expose both internal data and required services to other parties in a well-
defined standard manner. The nature of the data that the bank wants to expose determines how
such sensitive information is be exposed. Open APIs are used to expose bank details such as
ATMs, exchange rates and branches. On the same note, customer sensitive information such as
account number and payment services should be exposed over secure APIs (Hayikader, Hadi, &
Ibrahim 2016, pp. 38). The next open banking design requirement is API security which is used
to restrict APIs access to only authorized third parties. After exposing APIs, it is the
responsibility of the banks to implement the security layer, which is used as a third-party
authorization certificate-based mechanism. Strong customer authentication and consent are
required from the customer when sensitive data is to be shared. Customer identification is a
fundamental aspect as OPT authentication cannot be used as a guarantee that the customer is a
genuine one. Banks are highly encouraged to apply a combination of more than two mechanisms
such as knowledge, ownership, and inheritance to validate the customer (Conti et al 2018, pp.
3416). To make customer identification secure and reliable, banks have resulted to use of a
redirect and decoupled approach.
Similarly, third-party onboarding is used by banks to provide external entities an
opportunity to explore available APIs and use them to develop different applications. For third
parties to use specific bank’s API, it is mandatory to subscribe for on-boarding for it to be
registered as a recognized third-party with the bank (Hartono et al 2014, pp. 14). To make use of
and successfully implement APIs, a set of key requirements, both functional and non-functional
should be established. The first requirement that banks should consider when designing open
banking architecture is an API specification. Proper API specification in open banking help
financial institutions to expose both internal data and required services to other parties in a well-
defined standard manner. The nature of the data that the bank wants to expose determines how
such sensitive information is be exposed. Open APIs are used to expose bank details such as
ATMs, exchange rates and branches. On the same note, customer sensitive information such as
account number and payment services should be exposed over secure APIs (Hayikader, Hadi, &
Ibrahim 2016, pp. 38). The next open banking design requirement is API security which is used
to restrict APIs access to only authorized third parties. After exposing APIs, it is the
responsibility of the banks to implement the security layer, which is used as a third-party
authorization certificate-based mechanism. Strong customer authentication and consent are
required from the customer when sensitive data is to be shared. Customer identification is a
fundamental aspect as OPT authentication cannot be used as a guarantee that the customer is a
genuine one. Banks are highly encouraged to apply a combination of more than two mechanisms
such as knowledge, ownership, and inheritance to validate the customer (Conti et al 2018, pp.
3416). To make customer identification secure and reliable, banks have resulted to use of a
redirect and decoupled approach.
Similarly, third-party onboarding is used by banks to provide external entities an
opportunity to explore available APIs and use them to develop different applications. For third
parties to use specific bank’s API, it is mandatory to subscribe for on-boarding for it to be
registered as a recognized third-party with the bank (Hartono et al 2014, pp. 14). To make use of

the open banking applications, once third-party onboarding is done, integration into the core
banking solution is required. Exposing APIs requires third parties to connect to existing banking
solutions through HTTPS, JSON, and XML. The next open banking requirement is user store
integration which brings together different stakeholders such as banks, third party users, bank
staff and services to be consumed. In this regard, product integration brings different users
together by providing a common platform through which service providers and consumers
interact. Finally, when planning and designing open banking architecture, it is important to
consider all stakeholder's operational requirements (Yang et al 2015, pp. 19). In the case of third-
party providers, it is a requirement they rely on available and dedicated APIs which are provided
by account servicing payment service provider (ASPSPs). In turn, third parties can offer reliable
and efficient services to their customers. Bank, on the other hand, should have a well-tested and
verified platform before taking it to production. Different types of testing should be done to
make sure the subjected platform provides a convenient and efficient solution to customers. To
reduce their workload and increase testing accuracy, banks are required to provide third-parties
with testing facilities before taking applications to productions (Zahoor, Ud-din, & Sunami 2016,
pp. 32-33). By engaging third-parties, banks benefit through feedback which can be used to
improve core banking solutions. Important to note is that any core banking problem can affect
the quality of service provided by third-party APIs, which can affect enter banking business
operations.
Once the open banking requirements are defined and design is done, the focus turns to
open banking system architecture. The system works seamlessly of how data is approved for
access by third-party mobile applications (Elkhodr, Shahrestani, & Kourouche 2012, pp. 262).
Once the user installs an application, the application require access to the data in order to offer
banking solution is required. Exposing APIs requires third parties to connect to existing banking
solutions through HTTPS, JSON, and XML. The next open banking requirement is user store
integration which brings together different stakeholders such as banks, third party users, bank
staff and services to be consumed. In this regard, product integration brings different users
together by providing a common platform through which service providers and consumers
interact. Finally, when planning and designing open banking architecture, it is important to
consider all stakeholder's operational requirements (Yang et al 2015, pp. 19). In the case of third-
party providers, it is a requirement they rely on available and dedicated APIs which are provided
by account servicing payment service provider (ASPSPs). In turn, third parties can offer reliable
and efficient services to their customers. Bank, on the other hand, should have a well-tested and
verified platform before taking it to production. Different types of testing should be done to
make sure the subjected platform provides a convenient and efficient solution to customers. To
reduce their workload and increase testing accuracy, banks are required to provide third-parties
with testing facilities before taking applications to productions (Zahoor, Ud-din, & Sunami 2016,
pp. 32-33). By engaging third-parties, banks benefit through feedback which can be used to
improve core banking solutions. Important to note is that any core banking problem can affect
the quality of service provided by third-party APIs, which can affect enter banking business
operations.
Once the open banking requirements are defined and design is done, the focus turns to
open banking system architecture. The system works seamlessly of how data is approved for
access by third-party mobile applications (Elkhodr, Shahrestani, & Kourouche 2012, pp. 262).
Once the user installs an application, the application require access to the data in order to offer

some services. To access the data, the subjected application request the user to approve data
access for specific banks. Once the application user provided the required details, it is the
responsibility of the bank to authenticate the provided information and sent confirmation through
a short message. The requested data is provided to the user’s third-party application through a
protocol such as OAuth, an authorization protocol that helps the user to provide access to the
required information. The third-party application can consume either private or public REST
APIs provided by the bank to access the required data (Swacha-Lech 2017, pp. 97). Important to
note is that different open source APIs are readily available and they are written in different
programming languages such as Java and JavaScript (Bhatt, & Bhatt 2016, pp. 81). A sample of
opening banking architecture is presented depicting sharing of data from bank A to bank B
through a third-party application. Through open banking APIs, bank A can get information from
a customer from bank B. This has to be done through by customer allowing an application to
retrieve data from an external source to the requestor bank through a third-party application. In
this regard, the customer can have a unified view of banking information from all banks at a
glance.
access for specific banks. Once the application user provided the required details, it is the
responsibility of the bank to authenticate the provided information and sent confirmation through
a short message. The requested data is provided to the user’s third-party application through a
protocol such as OAuth, an authorization protocol that helps the user to provide access to the
required information. The third-party application can consume either private or public REST
APIs provided by the bank to access the required data (Swacha-Lech 2017, pp. 97). Important to
note is that different open source APIs are readily available and they are written in different
programming languages such as Java and JavaScript (Bhatt, & Bhatt 2016, pp. 81). A sample of
opening banking architecture is presented depicting sharing of data from bank A to bank B
through a third-party application. Through open banking APIs, bank A can get information from
a customer from bank B. This has to be done through by customer allowing an application to
retrieve data from an external source to the requestor bank through a third-party application. In
this regard, the customer can have a unified view of banking information from all banks at a
glance.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
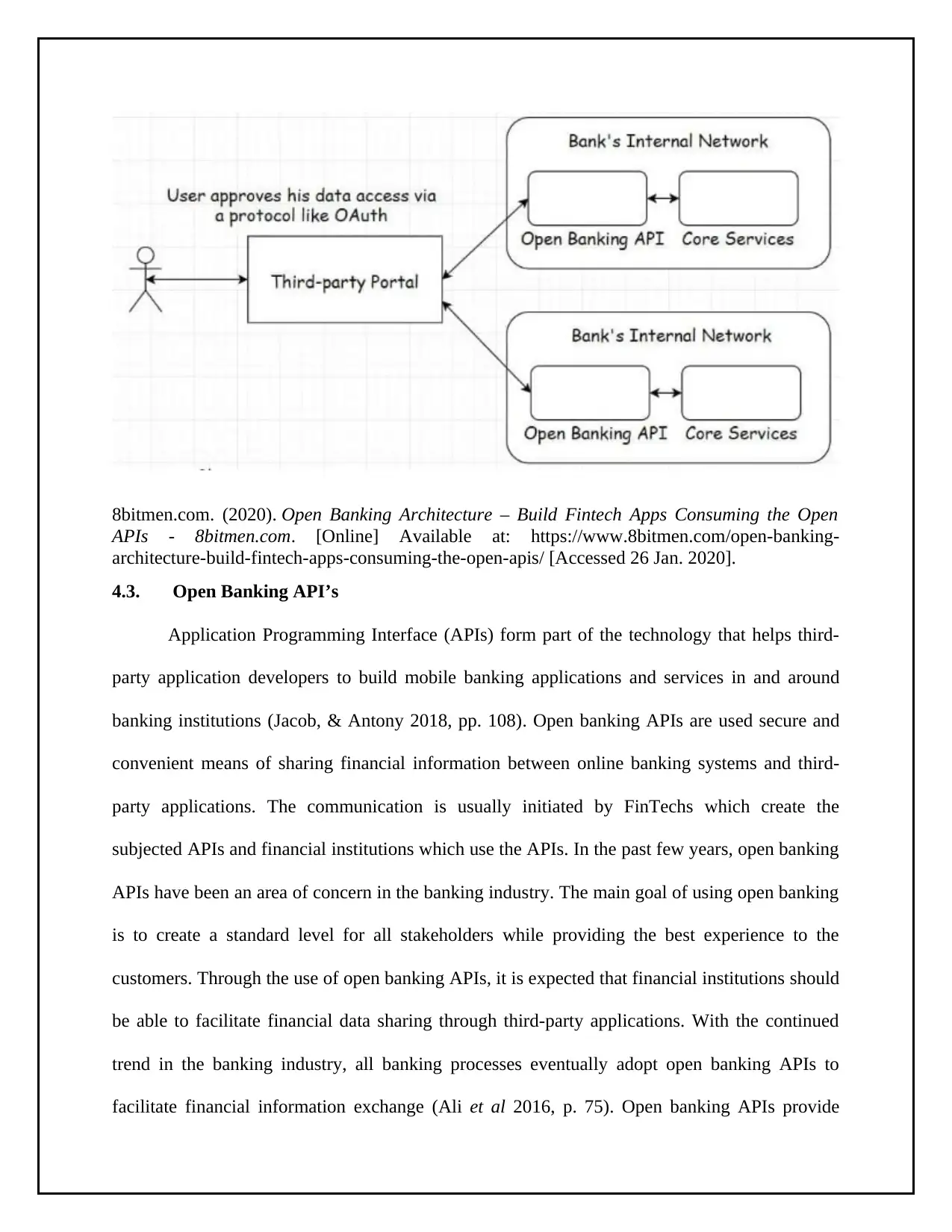
8bitmen.com. (2020). Open Banking Architecture – Build Fintech Apps Consuming the Open
APIs - 8bitmen.com. [Online] Available at: https://www.8bitmen.com/open-banking-
architecture-build-fintech-apps-consuming-the-open-apis/ [Accessed 26 Jan. 2020].
4.3. Open Banking API’s
Application Programming Interface (APIs) form part of the technology that helps third-
party application developers to build mobile banking applications and services in and around
banking institutions (Jacob, & Antony 2018, pp. 108). Open banking APIs are used secure and
convenient means of sharing financial information between online banking systems and third-
party applications. The communication is usually initiated by FinTechs which create the
subjected APIs and financial institutions which use the APIs. In the past few years, open banking
APIs have been an area of concern in the banking industry. The main goal of using open banking
is to create a standard level for all stakeholders while providing the best experience to the
customers. Through the use of open banking APIs, it is expected that financial institutions should
be able to facilitate financial data sharing through third-party applications. With the continued
trend in the banking industry, all banking processes eventually adopt open banking APIs to
facilitate financial information exchange (Ali et al 2016, p. 75). Open banking APIs provide
APIs - 8bitmen.com. [Online] Available at: https://www.8bitmen.com/open-banking-
architecture-build-fintech-apps-consuming-the-open-apis/ [Accessed 26 Jan. 2020].
4.3. Open Banking API’s
Application Programming Interface (APIs) form part of the technology that helps third-
party application developers to build mobile banking applications and services in and around
banking institutions (Jacob, & Antony 2018, pp. 108). Open banking APIs are used secure and
convenient means of sharing financial information between online banking systems and third-
party applications. The communication is usually initiated by FinTechs which create the
subjected APIs and financial institutions which use the APIs. In the past few years, open banking
APIs have been an area of concern in the banking industry. The main goal of using open banking
is to create a standard level for all stakeholders while providing the best experience to the
customers. Through the use of open banking APIs, it is expected that financial institutions should
be able to facilitate financial data sharing through third-party applications. With the continued
trend in the banking industry, all banking processes eventually adopt open banking APIs to
facilitate financial information exchange (Ali et al 2016, p. 75). Open banking APIs provide

financial institutions and their customers a secure mechanism to share sensitive information such
as customer's account data, balances and transaction flow on request. Despite making financial
institution processes efficient and effective, it is important to understand the flip-side of using
open banking APIs in a technological ecosystem coupled with cybersecurity threats.
Open banking APIs have created a security challenge for both providers and consumers
in the banking industry. Most of the organizations that have been championing the adoption of
the opine banking APIs are small technology companies. Giant technology organizations such as
Apple, Amazon, and Google have been objecting to the ideology considering they have built
their business on customer data. In this case, sharing its data with third-parties exposes their
customer data to fraudulent activities. The giant in technologies believes that creating APIs that
access data at any time and without proper authentication make it difficult to determine that fault
after a data breach. Another issue associated with open banking and which most of the
stakeholders are wary about is its reliability. It is imperative that providing access to third-party
applications poses serious security risks to financial institutions. Unless there are clear legal
boundaries on data sharing between banks and third-parties, any loss of customer data by banks
makes it possible to pass the blame to third-parties. The issue of responsibility after data breach
should be clearly outlined within the laws of the banking industry to avoid unnecessary blames
among stakeholders. The last challenge is the lack of knowledge in open banking APIs, which
has made applications users unwilling to authorize data sharing. Lack of data sharing which is
the main aspect in open banking makes it impossible for both banks and Fintechs to initiate
necessary innovations in the banking industry. A research done by Accenture showed that only a
third of the consumers were unwilling to share their financial data and 92% of them had no
as customer's account data, balances and transaction flow on request. Despite making financial
institution processes efficient and effective, it is important to understand the flip-side of using
open banking APIs in a technological ecosystem coupled with cybersecurity threats.
Open banking APIs have created a security challenge for both providers and consumers
in the banking industry. Most of the organizations that have been championing the adoption of
the opine banking APIs are small technology companies. Giant technology organizations such as
Apple, Amazon, and Google have been objecting to the ideology considering they have built
their business on customer data. In this case, sharing its data with third-parties exposes their
customer data to fraudulent activities. The giant in technologies believes that creating APIs that
access data at any time and without proper authentication make it difficult to determine that fault
after a data breach. Another issue associated with open banking and which most of the
stakeholders are wary about is its reliability. It is imperative that providing access to third-party
applications poses serious security risks to financial institutions. Unless there are clear legal
boundaries on data sharing between banks and third-parties, any loss of customer data by banks
makes it possible to pass the blame to third-parties. The issue of responsibility after data breach
should be clearly outlined within the laws of the banking industry to avoid unnecessary blames
among stakeholders. The last challenge is the lack of knowledge in open banking APIs, which
has made applications users unwilling to authorize data sharing. Lack of data sharing which is
the main aspect in open banking makes it impossible for both banks and Fintechs to initiate
necessary innovations in the banking industry. A research done by Accenture showed that only a
third of the consumers were unwilling to share their financial data and 92% of them had no

information on open banking. Therefore, the use of APIs in the banking industry requires a
proper security framework and security setup to guide both providers and consumers.
5. Evaluation
5.1. Threat Analysis
Financial institutions have been facing various cybersecurity threats from different
agents. The goal of the threat analysis is to evaluate, determine, and quantify the potentiality of
the subjected treat. The focus of the agents has been to gain unauthorized access to banking
assets, mainly customer data and money. The success of the threat agents is determined by the
vulnerabilities that exist in an open banking mobile application (Ahmad et al 2010, pp. 268). A
proper security framework and security setup to guide both providers and consumers.
5. Evaluation
5.1. Threat Analysis
Financial institutions have been facing various cybersecurity threats from different
agents. The goal of the threat analysis is to evaluate, determine, and quantify the potentiality of
the subjected treat. The focus of the agents has been to gain unauthorized access to banking
assets, mainly customer data and money. The success of the threat agents is determined by the
vulnerabilities that exist in an open banking mobile application (Ahmad et al 2010, pp. 268). A
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

threat model has been created to present the nature of threats that open mobile banking
application stakeholders should prioritize while protecting organizational assets.
5.2. Assets
In a banking industry setup, assets are classified into different categories such as income-
generating processes and physical assets such as a building. However, in the cybersecurity
context, assets are mainly organizational data and any other technological equipment that can be
of value to the institution (Arockiam, & Monikandan 2013, pp. 30654). In an open banking
mobile application, customer data is an important asset that all stakeholders should strive to
secure. Considering customer data is shared with many stakeholders and in different banking
entities, it is accessed by different users. Through some of the data, users are authorized, others
are access and use the banking institutions data illegally. By accessing and sharing customer data
with many users, its integrity, availability, and confidentiality are lost. The nature of the data
shared with other stakeholders is very sensitive and in most cases is used against the customer.
An example can be deduced from the loss of customer open banking mobile application
credentials (Marwaha, & Bedi 2013, pp. 367). Attackers can gain access to the banking
institution and understand its functional mechanism by masking behind the actual customer. In
this case, attackers can use customer data to compromise organizational assets such as network,
servers and customer's financial privacy.
The next asset in the banking industry is any digital document that is prone to access and
compromise by attackers. Financial institution documents must be protected from unauthorized
access and be corrupted by malware. Through the use of customer data from open banking
mobile applications, attackers can infect the server's hard disk which in turn leads to disk failure
(Kumar, Pandey, & Punia 2014, pp. 129). Digital content is also prone to unauthorized access
application stakeholders should prioritize while protecting organizational assets.
5.2. Assets
In a banking industry setup, assets are classified into different categories such as income-
generating processes and physical assets such as a building. However, in the cybersecurity
context, assets are mainly organizational data and any other technological equipment that can be
of value to the institution (Arockiam, & Monikandan 2013, pp. 30654). In an open banking
mobile application, customer data is an important asset that all stakeholders should strive to
secure. Considering customer data is shared with many stakeholders and in different banking
entities, it is accessed by different users. Through some of the data, users are authorized, others
are access and use the banking institutions data illegally. By accessing and sharing customer data
with many users, its integrity, availability, and confidentiality are lost. The nature of the data
shared with other stakeholders is very sensitive and in most cases is used against the customer.
An example can be deduced from the loss of customer open banking mobile application
credentials (Marwaha, & Bedi 2013, pp. 367). Attackers can gain access to the banking
institution and understand its functional mechanism by masking behind the actual customer. In
this case, attackers can use customer data to compromise organizational assets such as network,
servers and customer's financial privacy.
The next asset in the banking industry is any digital document that is prone to access and
compromise by attackers. Financial institution documents must be protected from unauthorized
access and be corrupted by malware. Through the use of customer data from open banking
mobile applications, attackers can infect the server's hard disk which in turn leads to disk failure
(Kumar, Pandey, & Punia 2014, pp. 129). Digital content is also prone to unauthorized access

through which untheorized parties can access sensitive organizational information such as
Information Technology (IT) infrastructure. Finally, the system administrator is a very important
organizational asset that should be protected to avoid cases of unavailability. It is the
responsibility of system administrators to configure and keep organizational data such as
customer data secure and safe. Administrators have at their disposal all organizational sensitive
information such as passwords of the core IT infrastructure. Since it is not possible to replace a
system administrator, it is the responsibility of any financial institution to keep system
administrators secure (Sun et al 2014, pp. 190). In most cases, organizations invest highly in
their system administrators by organizing pieces of training and workshops. With a reliable and
experienced system administrator, financial institutions can keep their data secure from free from
interruption by third parties. Therefore, as an asset, a well trained and experienced system
administrator can encrypt both passwords and customer data and maintain data backups
effectively.
5.3. Threat agents
In open mobile banking applications, threat agents involve a group of people or an
individual with the ability to initiate a threat to systems. In the technology world, it is important
to identify and evaluate threat agents and the capability of threats affecting organizational assets
(Padmapriya, & Subhasri 2013, pp. 78). Considering open mobile banking applications have
direct access to financial institution data, different application users and third parties try to
compromise the data. Some of the threat agents in the mobile banking application include
financial institution employees. Employees have manifested some form of complex security risks
because they have a clear understanding of organizational IT infrastructure. Organizational
employees have been classified as a threat agent because most of the cybersecurity crimes
Information Technology (IT) infrastructure. Finally, the system administrator is a very important
organizational asset that should be protected to avoid cases of unavailability. It is the
responsibility of system administrators to configure and keep organizational data such as
customer data secure and safe. Administrators have at their disposal all organizational sensitive
information such as passwords of the core IT infrastructure. Since it is not possible to replace a
system administrator, it is the responsibility of any financial institution to keep system
administrators secure (Sun et al 2014, pp. 190). In most cases, organizations invest highly in
their system administrators by organizing pieces of training and workshops. With a reliable and
experienced system administrator, financial institutions can keep their data secure from free from
interruption by third parties. Therefore, as an asset, a well trained and experienced system
administrator can encrypt both passwords and customer data and maintain data backups
effectively.
5.3. Threat agents
In open mobile banking applications, threat agents involve a group of people or an
individual with the ability to initiate a threat to systems. In the technology world, it is important
to identify and evaluate threat agents and the capability of threats affecting organizational assets
(Padmapriya, & Subhasri 2013, pp. 78). Considering open mobile banking applications have
direct access to financial institution data, different application users and third parties try to
compromise the data. Some of the threat agents in the mobile banking application include
financial institution employees. Employees have manifested some form of complex security risks
because they have a clear understanding of organizational IT infrastructure. Organizational
employees have been classified as a threat agent because most of the cybersecurity crimes

committed are assisted by internal agents. Banking institution employees can access sensitive
information that can be used fraudulently by insiders or external entities. Insiders collaborate
with external entities and share required organizational data that can be used to commit
cybercrime. The next threat agent in the mobile banking application is hackers who compromise
application to extract sensitive information without the user's knowledge. Hackers as threat
agents can gain access to the mobile application through the backdoor and extract sensitive
information such as login credentials (Asfaw 2015, pp. 102). Once hackers get such information,
they use it to access the system as if it is the actual user and access data or perform transactions
fraudulently. Malware is another form of threat agent that has been posing security risks to
financial institutions. Financial institutions have been targeted through ransomware which locks
organizational data or devices and bringing the entire business process at a standstill.
5.4. Security threats
Security threats are unavoidable due to the growing technology and evolving nature of
security threats. Financial institutions have been facing various types of security threats like web
application attacks. It is apparent that most of the applications in use are web-based and are
vulnerable to different types of attacks. Since these applications rely on user input to process the
required request, SQL injections and distributed denial of service (DDoS) attacks are common
(Marium et al 2012, pp. 178). The next security threat is backdoor and supply-chain attacks
which target data extraction from the backend of the applications. Hackers can exploit existing
backdoor vulnerability from code and open ports and gain access to user devices and applications
without the user's knowledge. In recent data security breaches, hackers have proved very
sophisticated by hijacking DNS request while the user is processing some online financial
transactions. Through supply-chain attacks, the backdoor is opened and customers' data is
information that can be used fraudulently by insiders or external entities. Insiders collaborate
with external entities and share required organizational data that can be used to commit
cybercrime. The next threat agent in the mobile banking application is hackers who compromise
application to extract sensitive information without the user's knowledge. Hackers as threat
agents can gain access to the mobile application through the backdoor and extract sensitive
information such as login credentials (Asfaw 2015, pp. 102). Once hackers get such information,
they use it to access the system as if it is the actual user and access data or perform transactions
fraudulently. Malware is another form of threat agent that has been posing security risks to
financial institutions. Financial institutions have been targeted through ransomware which locks
organizational data or devices and bringing the entire business process at a standstill.
5.4. Security threats
Security threats are unavoidable due to the growing technology and evolving nature of
security threats. Financial institutions have been facing various types of security threats like web
application attacks. It is apparent that most of the applications in use are web-based and are
vulnerable to different types of attacks. Since these applications rely on user input to process the
required request, SQL injections and distributed denial of service (DDoS) attacks are common
(Marium et al 2012, pp. 178). The next security threat is backdoor and supply-chain attacks
which target data extraction from the backend of the applications. Hackers can exploit existing
backdoor vulnerability from code and open ports and gain access to user devices and applications
without the user's knowledge. In recent data security breaches, hackers have proved very
sophisticated by hijacking DNS request while the user is processing some online financial
transactions. Through supply-chain attacks, the backdoor is opened and customers' data is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

exposed to serious security threats. Security threats have also been posed by having several
vendors using similar applications. Contracting applications that are integrated with core banking
solutions, though within the organizational network, vulnerabilities from third parties are
complex (Pancholi, & Patel 2016, pp. 19). A good example is when a third party is attacked by
ransomware, chances are high that all institutions and customers using the service can be
affected. Therefore, organizations contacting external services and applications must test the
security matrix used to protect the contracted services.
5.5. Vulnerabilities
Mobile open banking application is immune to a different type of security risks and
financial institution should provide secure and reliable applications. The mobile application
vulnerabilities are mainly caused by poor application development practices (Chou 2013, pp.
79). Vulnerabilities that are associated with mobile application development are; lack of binary
protection which is commonly known as hardening of the applications. Once an application is
developed and put in use, it is important to protect and make it difficult to reverse engineer
(Jansen 2011, pp. 10). The application security is hardened by source code obfuscation which
financial institutions should enforce to secure its operations. Failure to harden mobile application
makes it easier for threat agents to decompile mobile banking application. The next form of
mobile application vulnerability is unpreceded data leakage which is caused by banking
application sharing of services. Mobile application users should be aware that data storage data
access by other applications through sharing of service has been a major security threat by
exposing sensitive data to other applications. Notably, client-side injection is one of the
vulnerabilities that make it possible for malicious codes to be executed on mobile applications
(Abomhara 2015, pp. 67-68). Through malicious code execution, threat agents can access
vendors using similar applications. Contracting applications that are integrated with core banking
solutions, though within the organizational network, vulnerabilities from third parties are
complex (Pancholi, & Patel 2016, pp. 19). A good example is when a third party is attacked by
ransomware, chances are high that all institutions and customers using the service can be
affected. Therefore, organizations contacting external services and applications must test the
security matrix used to protect the contracted services.
5.5. Vulnerabilities
Mobile open banking application is immune to a different type of security risks and
financial institution should provide secure and reliable applications. The mobile application
vulnerabilities are mainly caused by poor application development practices (Chou 2013, pp.
79). Vulnerabilities that are associated with mobile application development are; lack of binary
protection which is commonly known as hardening of the applications. Once an application is
developed and put in use, it is important to protect and make it difficult to reverse engineer
(Jansen 2011, pp. 10). The application security is hardened by source code obfuscation which
financial institutions should enforce to secure its operations. Failure to harden mobile application
makes it easier for threat agents to decompile mobile banking application. The next form of
mobile application vulnerability is unpreceded data leakage which is caused by banking
application sharing of services. Mobile application users should be aware that data storage data
access by other applications through sharing of service has been a major security threat by
exposing sensitive data to other applications. Notably, client-side injection is one of the
vulnerabilities that make it possible for malicious codes to be executed on mobile applications
(Abomhara 2015, pp. 67-68). Through malicious code execution, threat agents can access

different functionalities of the mobile application, make changes on application settings and
break sandbox security device user has it for security reasons. Insecure data storage is a
vulnerability that mobile application users should be aware of. Financial mobile applications are
not secure in storing users’ data because they store very sensitive data locally. By having internal
storage within the device or storing data outside of the sandbox provide an easy target to third
party users to exploit the data.
Similarly, most of the mobile banking applications use weak encryption algorithms or
strong cipher have been implemented wrongly. The use of a weak encryption algorithm makes it
easier for hackers to break the encryption algorithm and access the encrypted data. Implicit trust
in application certificates in financial institutions is a major security threat because most of the
institutions do not implement required security checks (Kalpana, & Singaraju 2012, pp. 2278).
As a result, mobile applications are susceptible to attacks such as man-in-the-middle due to the
use of invalid certificates. Notably, attackers can use different techniques to intercept data
exchanged between financial institutions and the application. On the same note, execution of
activities using root is a security breach that most of the mobile banking applications can
perform with the highest possible privileges. Criminals can compromise a mobile banking
application and perform different tasks with the highest level of privileges possible.
Consequently, some mobile banking applications have their security private key and certificates
hardcoded or saved in mobile devices or component files. Such sensitive data can be easily
retrieved due to mobile application lack of binary security protection and attackers can make use
of such data to crack encryption algorithms. Finally, exposure to database SQL queries and
parameters cause major security threats to mobile applications and financial institutions. If
mobile applications show readable codes in the decompiled state, attackers can trace sensitive
break sandbox security device user has it for security reasons. Insecure data storage is a
vulnerability that mobile application users should be aware of. Financial mobile applications are
not secure in storing users’ data because they store very sensitive data locally. By having internal
storage within the device or storing data outside of the sandbox provide an easy target to third
party users to exploit the data.
Similarly, most of the mobile banking applications use weak encryption algorithms or
strong cipher have been implemented wrongly. The use of a weak encryption algorithm makes it
easier for hackers to break the encryption algorithm and access the encrypted data. Implicit trust
in application certificates in financial institutions is a major security threat because most of the
institutions do not implement required security checks (Kalpana, & Singaraju 2012, pp. 2278).
As a result, mobile applications are susceptible to attacks such as man-in-the-middle due to the
use of invalid certificates. Notably, attackers can use different techniques to intercept data
exchanged between financial institutions and the application. On the same note, execution of
activities using root is a security breach that most of the mobile banking applications can
perform with the highest possible privileges. Criminals can compromise a mobile banking
application and perform different tasks with the highest level of privileges possible.
Consequently, some mobile banking applications have their security private key and certificates
hardcoded or saved in mobile devices or component files. Such sensitive data can be easily
retrieved due to mobile application lack of binary security protection and attackers can make use
of such data to crack encryption algorithms. Finally, exposure to database SQL queries and
parameters cause major security threats to mobile applications and financial institutions. If
mobile applications show readable codes in the decompiled state, attackers can trace sensitive

database parameters and configurations (Chou 2013, pp. 79). In return, attackers can perform
SQL injections and perform unauthorized database manipulations.
6. Discussions of findings
The study focused on the design and security challenges that are faced by open banking
applications that are deployed in mobile applications. The open banking approach dictates that
financial institutions and third-party application can share data, but with customer consent. Data
sharing has been given concerted efforts due to an increase in data breaches from the banking
industry. The security has been given a substantive approach in financial institutions because
SQL injections and perform unauthorized database manipulations.
6. Discussions of findings
The study focused on the design and security challenges that are faced by open banking
applications that are deployed in mobile applications. The open banking approach dictates that
financial institutions and third-party application can share data, but with customer consent. Data
sharing has been given concerted efforts due to an increase in data breaches from the banking
industry. The security has been given a substantive approach in financial institutions because
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

they hold quite sensitive customers’ data. The study found out that from the year 2018, the EU
adopted PSD2 to facilitate data sharing among financial entities and third-party applications
(Takabi, Joshi, & Ahn 2010, pp. 26). With PSD2 adoption, third party applications and financial
institutions should share customer data with necessary approvals. It is only the customer who
should grant access to sharing bank details data to other entities by allowing access to specific
mobile banking applications. Though PSD2 has provides users with guidelines on data sharing, it
was notable that it does not dictate both authorization and authentication. Authorization is the
process of granting application users privileges to access mobile banking applications.
Authentication in open mobile banking application is the process that customer goes through to
grant various applications to both access and share data. By failing to address authorization and
authentication, PSD2 leaves financial institutions with no guidelines on the best practices to
follow when accessing financial data. It is the responsibility of the financial institutions to decide
how to address access and granting of privileges.
The architecture of the open banking application and its interaction with third parties
changed after the adoption of PSD2 in 2018. Before its adoption, each bank that had to share
data was required to have a different mobile banking application. Through the adoption of open
banking, financial institutions are required to expose APIs that third parties use to either access
or share data (Kong, Lei, & Ma 2016, pp. 512). With open banking, customers can access
different bank accounts and financial transactions by use of only one application. With a unified
view of customer data and transactions, customers can manage their finds effectively. Banks
have also benefited from open banking because they can access customer financial status
conveniently. With the customer's financial status, financial institutions can determine the
customer's creditworthiness. The use of one mobile application to access and manage financial
adopted PSD2 to facilitate data sharing among financial entities and third-party applications
(Takabi, Joshi, & Ahn 2010, pp. 26). With PSD2 adoption, third party applications and financial
institutions should share customer data with necessary approvals. It is only the customer who
should grant access to sharing bank details data to other entities by allowing access to specific
mobile banking applications. Though PSD2 has provides users with guidelines on data sharing, it
was notable that it does not dictate both authorization and authentication. Authorization is the
process of granting application users privileges to access mobile banking applications.
Authentication in open mobile banking application is the process that customer goes through to
grant various applications to both access and share data. By failing to address authorization and
authentication, PSD2 leaves financial institutions with no guidelines on the best practices to
follow when accessing financial data. It is the responsibility of the financial institutions to decide
how to address access and granting of privileges.
The architecture of the open banking application and its interaction with third parties
changed after the adoption of PSD2 in 2018. Before its adoption, each bank that had to share
data was required to have a different mobile banking application. Through the adoption of open
banking, financial institutions are required to expose APIs that third parties use to either access
or share data (Kong, Lei, & Ma 2016, pp. 512). With open banking, customers can access
different bank accounts and financial transactions by use of only one application. With a unified
view of customer data and transactions, customers can manage their finds effectively. Banks
have also benefited from open banking because they can access customer financial status
conveniently. With the customer's financial status, financial institutions can determine the
customer's creditworthiness. The use of one mobile application to access and manage financial

transactions has proved to be effective and convenient for both customers and financial
institutions.
Financial institutions have accepted the sharing of data through open banking
applications, but some security concerns need to be addressed. There is a lack of rules that
defines how to determine security lapse once data breaches happen. Data sharing between
entities makes it difficult to evaluate which entity exposed customer data without consent and
this leaves organizations in a blame game. PSD2 should evaluate and present different entities
with guidelines on how to determine stakeholder’s lapses during the data breach. Failure to
provide required guidelines leaves financial institutions unwilling to share customer data with
other entities that do not guarantee the required security. Data security in open banking cannot be
placed on mobile applications only because hackers have changed techniques. Hackers have
changed their techniques after realizing mobile banking applications security is strong and not
easy to bypass. It is apparent that by gaining access to the user's device, it is possible to
manipulate other applications and extract sensitive data. The hackers gain access to the device
through other mobile applications that do not put much emphasis on security.
Open banking mobile applications are faced with several security challenges that are
consequently passed to financial institutions. By granting permission to mobile banking
applications to access and share customer data, it is possible that hackers can use such an
opportunity to access financial transactions. Sharing of data without proper control by the
government leaves the banking sector open to fraudulent activities that result in a legal battle on
the privacy of data. Open banking is safe but due to the nature of the changing technological
environment, financial institutions face serious security challenges from other entities.
Categorizing open banking as unsafe make customers fear the use of the innovation which
institutions.
Financial institutions have accepted the sharing of data through open banking
applications, but some security concerns need to be addressed. There is a lack of rules that
defines how to determine security lapse once data breaches happen. Data sharing between
entities makes it difficult to evaluate which entity exposed customer data without consent and
this leaves organizations in a blame game. PSD2 should evaluate and present different entities
with guidelines on how to determine stakeholder’s lapses during the data breach. Failure to
provide required guidelines leaves financial institutions unwilling to share customer data with
other entities that do not guarantee the required security. Data security in open banking cannot be
placed on mobile applications only because hackers have changed techniques. Hackers have
changed their techniques after realizing mobile banking applications security is strong and not
easy to bypass. It is apparent that by gaining access to the user's device, it is possible to
manipulate other applications and extract sensitive data. The hackers gain access to the device
through other mobile applications that do not put much emphasis on security.
Open banking mobile applications are faced with several security challenges that are
consequently passed to financial institutions. By granting permission to mobile banking
applications to access and share customer data, it is possible that hackers can use such an
opportunity to access financial transactions. Sharing of data without proper control by the
government leaves the banking sector open to fraudulent activities that result in a legal battle on
the privacy of data. Open banking is safe but due to the nature of the changing technological
environment, financial institutions face serious security challenges from other entities.
Categorizing open banking as unsafe make customers fear the use of the innovation which

cannot be avoided because it is convenient for customers (Arora, Raja, & Bahl 2018, pp. 26-27).
During the formulation and implementation of PSD2, security concerns were not fully addressed.
Instead, the focus was mainly on data sharing between third parties and financial institutions. For
big organizations like amazon and google, data sharing is quite devastating because they mainly
rely on customer data for business operations. Sharing of data without proper guidelines poses
both security and operational risks to big players in the financial industry. Open banking
applications face serious security challenges from device OS level and other applications
installed in mobile phones. Some applications and OS codes have vulnerabilities that pose
security concerns to open banking mobile applications. All operating systems have some security
challenges which should be addressed to protect financial institutions from data breaches.
7. Conclusion
Open banking involves the sharing of data between financial institutions and other third
parties through mobile applications. Mobile banking applications deployed in mobile devices
have been facing serious security challenges that should be addressed by all stakeholders. The
design of the open mobile banking applications should meet minimum security requirements that
can guarantee financial institutions its data is secure. The main goal of the study is to analyze and
evaluate open banking and security challenges posed by mobile banking applications to financial
During the formulation and implementation of PSD2, security concerns were not fully addressed.
Instead, the focus was mainly on data sharing between third parties and financial institutions. For
big organizations like amazon and google, data sharing is quite devastating because they mainly
rely on customer data for business operations. Sharing of data without proper guidelines poses
both security and operational risks to big players in the financial industry. Open banking
applications face serious security challenges from device OS level and other applications
installed in mobile phones. Some applications and OS codes have vulnerabilities that pose
security concerns to open banking mobile applications. All operating systems have some security
challenges which should be addressed to protect financial institutions from data breaches.
7. Conclusion
Open banking involves the sharing of data between financial institutions and other third
parties through mobile applications. Mobile banking applications deployed in mobile devices
have been facing serious security challenges that should be addressed by all stakeholders. The
design of the open mobile banking applications should meet minimum security requirements that
can guarantee financial institutions its data is secure. The main goal of the study is to analyze and
evaluate open banking and security challenges posed by mobile banking applications to financial
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

institutions. The open banking explanation offered an insight into the study and the efficiency
that it offers to customers and banking institutions. The evaluation of the open banking mobile
banking applications at a glance was meant to provide users with the new architecture of open
banking after the adoption of PSD2. In the year 2018, EU countries adopted PSD2 intending to
push all financial institutions to share data with third parties. Mobile banking application security
challenges provided an opportunity to discuss security challenges, threats and security agents and
vulnerabilities. Finally, system design evaluation presented an opportunity to discuss open
banking mobile application system design requirements. Both open banking platforms and
mobile banking applications design requirements evaluation considered security concerns. Poor
system design and failure to meet the required application specification pose a security challenge
to open banking and mobile applications. Security of the open mobile banking applications
require concerted effort to provide high-security measures
8. Bibliography
Abomhara, M., 2015. Cybersecurity and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Ahmad, M.K.A., Rosalim, R.V., Beng, L.Y. and Fun, T.S., 2010. Security issues on banking
systems. International Journal of Computer Science and Information Technologies, 1(4), pp.268-
272.
Ali, L., Ali, F., Surendran, P. and Thomas, B., 2016. The effects of cyber threats on customer’s
behaviour in e-banking services. International Journal of e-education, e-business, e-
management and e-learning, 7(1), pp.70-78.
that it offers to customers and banking institutions. The evaluation of the open banking mobile
banking applications at a glance was meant to provide users with the new architecture of open
banking after the adoption of PSD2. In the year 2018, EU countries adopted PSD2 intending to
push all financial institutions to share data with third parties. Mobile banking application security
challenges provided an opportunity to discuss security challenges, threats and security agents and
vulnerabilities. Finally, system design evaluation presented an opportunity to discuss open
banking mobile application system design requirements. Both open banking platforms and
mobile banking applications design requirements evaluation considered security concerns. Poor
system design and failure to meet the required application specification pose a security challenge
to open banking and mobile applications. Security of the open mobile banking applications
require concerted effort to provide high-security measures
8. Bibliography
Abomhara, M., 2015. Cybersecurity and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Ahmad, M.K.A., Rosalim, R.V., Beng, L.Y. and Fun, T.S., 2010. Security issues on banking
systems. International Journal of Computer Science and Information Technologies, 1(4), pp.268-
272.
Ali, L., Ali, F., Surendran, P. and Thomas, B., 2016. The effects of cyber threats on customer’s
behaviour in e-banking services. International Journal of e-education, e-business, e-
management and e-learning, 7(1), pp.70-78.

Al-Sabri, H.M., and Al-Saleem, S.M., 2013. Building a cloud storage encryption (CSE)
architecture for enhancing cloud security. International Journal of Computer Science Issues
(IJCSI), 10(2 Part 1), p.259.
Arockiam, L. and Monikandan, S., 2013. Data security and privacy in cloud storage using hybrid
symmetric encryption algorithm. International Journal of Advanced Research in Computer and
Communication Engineering, 2(8), pp.3064-3070.
Arora, A.S., Raja, L. and Bahl, B., 2018. Data centric security approach: A way to achieve
security & privacy in cloud computing. In Proceedings of 3rd International Conference on
Internet of Things and Connected Technologies (ICIoTCT) (pp. 26-27).
Asfaw, H.A., 2015. Financial Inclusion through Mobile Banking: Challenges and
Prospects. Research Journal of Finance and Accounting, 6(5), pp.98-104.
Bahl, S., 2012. E-banking: Challenges & policy implications. International Journal of
Computing & Business Research, pp.229-616.
Bamoriya, P.S. and Singh, P., 2011. Issues & Challenges in Mobile Banking In India: A
Customers’ Perspective. Research Journal of finance and accounting, 2(2), pp.112-120.
Bharti, M., 2016. Impact of dimensions of mobile banking on user satisfaction. The Journal of
Internet Banking and Commerce, 21(1), pp. 1-22.
Bhatt, A. and Bhatt, S., 2016. Factors affecting customers’ adoption of mobile banking
services. The Journal of Internet Banking and Commerce, 21(1), pp. 77-96.
Bhuiyan, M.S.R., and Rahman, M.M., 2013. Implementation of mobile banking in Bangladesh:
opportunities and challenges. IOSR Journal of Electronics Communication Engineering, 15(4),
pp.53-58.
Chou, T.S., 2013. Security threats on cloud computing vulnerabilities. International Journal of
Computer Science & Information Technology, 5(3), p.79.
Conti, M., Kumar, E.S., Lal, C. and Ruj, S., 2018. A survey on security and privacy issues of
bitcoin. IEEE Communications Surveys & Tutorials, 20(4), pp.3416-3452.
architecture for enhancing cloud security. International Journal of Computer Science Issues
(IJCSI), 10(2 Part 1), p.259.
Arockiam, L. and Monikandan, S., 2013. Data security and privacy in cloud storage using hybrid
symmetric encryption algorithm. International Journal of Advanced Research in Computer and
Communication Engineering, 2(8), pp.3064-3070.
Arora, A.S., Raja, L. and Bahl, B., 2018. Data centric security approach: A way to achieve
security & privacy in cloud computing. In Proceedings of 3rd International Conference on
Internet of Things and Connected Technologies (ICIoTCT) (pp. 26-27).
Asfaw, H.A., 2015. Financial Inclusion through Mobile Banking: Challenges and
Prospects. Research Journal of Finance and Accounting, 6(5), pp.98-104.
Bahl, S., 2012. E-banking: Challenges & policy implications. International Journal of
Computing & Business Research, pp.229-616.
Bamoriya, P.S. and Singh, P., 2011. Issues & Challenges in Mobile Banking In India: A
Customers’ Perspective. Research Journal of finance and accounting, 2(2), pp.112-120.
Bharti, M., 2016. Impact of dimensions of mobile banking on user satisfaction. The Journal of
Internet Banking and Commerce, 21(1), pp. 1-22.
Bhatt, A. and Bhatt, S., 2016. Factors affecting customers’ adoption of mobile banking
services. The Journal of Internet Banking and Commerce, 21(1), pp. 77-96.
Bhuiyan, M.S.R., and Rahman, M.M., 2013. Implementation of mobile banking in Bangladesh:
opportunities and challenges. IOSR Journal of Electronics Communication Engineering, 15(4),
pp.53-58.
Chou, T.S., 2013. Security threats on cloud computing vulnerabilities. International Journal of
Computer Science & Information Technology, 5(3), p.79.
Conti, M., Kumar, E.S., Lal, C. and Ruj, S., 2018. A survey on security and privacy issues of
bitcoin. IEEE Communications Surveys & Tutorials, 20(4), pp.3416-3452.

Das, S. and Debbarma, J., 2011. Designing a biometric strategy (fingerprint) measure for
enhancing atm security in indian e-banking system. International Journal of Information and
Communication Technology Research, 1(5), pp.156-189.
Devadevan, V., 2013. Mobile Banking in India–Issues & Challenges. International Journal of
Emerging Technology and Advanced Engineering, 3(6), pp.516-520.
Driga, I. and Isac, C., 2014. E-banking services–features, challenges, and benefits. Annals of the
University of Petroşani. Economics , 14, pp.49-58.
Elkhodr, M., Shahrestani, S. and Kourouche, K., 2012. A proposal to improve the security of
mobile banking applications. In 2012 Tenth International Conference on ICT and Knowledge
Engineering (pp. 260-265).
Elkhodr, M., Shahrestani, S. and Kourouche, K., 2012. A proposal to improve the security of
mobile banking applications. In 2012 Tenth International Conference on ICT and Knowledge
Engineering (pp. 260-265).
Goyal, V., Pandey, U.S. and Batra, S., 2012. Mobile banking in India: Practices, challenges and
security issues. International Journal of Advanced Trends in Computer Science and
Engineering, 1(2), pp. 56-89.
Gupta, V.K., Bagoria, R. and Bagoria, N., 2013. Mobile Banking Services as Adoption and
Challenges: A Case of M-Banking in India (Positive and Negative Impact, Mobile Growth in
India, Adoption Models and Mobile Technology). International Journal of Scientific and
Research Publications, 3(1), pp.1-6.
Hadad, S., 2019. Challenges for Banking Services in the Knowledge Economy. Management
Dynamics in the Knowledge Economy, 7(3), pp.337-352.
Hanafizadeh, P., Behboudi, M., Koshksaray, A.A. and Tabar, M.J.S., 2014. Mobile-banking
adoption by Iranian bank clients. Telematics and Informatics, 31(1), pp.62-78.
Handa, K. and Singh, U., 2015. Data security in cloud computing using encryption and
steganography. International Journal of Computer Science and Mobile Computing, 4(5), pp.786-
791.
enhancing atm security in indian e-banking system. International Journal of Information and
Communication Technology Research, 1(5), pp.156-189.
Devadevan, V., 2013. Mobile Banking in India–Issues & Challenges. International Journal of
Emerging Technology and Advanced Engineering, 3(6), pp.516-520.
Driga, I. and Isac, C., 2014. E-banking services–features, challenges, and benefits. Annals of the
University of Petroşani. Economics , 14, pp.49-58.
Elkhodr, M., Shahrestani, S. and Kourouche, K., 2012. A proposal to improve the security of
mobile banking applications. In 2012 Tenth International Conference on ICT and Knowledge
Engineering (pp. 260-265).
Elkhodr, M., Shahrestani, S. and Kourouche, K., 2012. A proposal to improve the security of
mobile banking applications. In 2012 Tenth International Conference on ICT and Knowledge
Engineering (pp. 260-265).
Goyal, V., Pandey, U.S. and Batra, S., 2012. Mobile banking in India: Practices, challenges and
security issues. International Journal of Advanced Trends in Computer Science and
Engineering, 1(2), pp. 56-89.
Gupta, V.K., Bagoria, R. and Bagoria, N., 2013. Mobile Banking Services as Adoption and
Challenges: A Case of M-Banking in India (Positive and Negative Impact, Mobile Growth in
India, Adoption Models and Mobile Technology). International Journal of Scientific and
Research Publications, 3(1), pp.1-6.
Hadad, S., 2019. Challenges for Banking Services in the Knowledge Economy. Management
Dynamics in the Knowledge Economy, 7(3), pp.337-352.
Hanafizadeh, P., Behboudi, M., Koshksaray, A.A. and Tabar, M.J.S., 2014. Mobile-banking
adoption by Iranian bank clients. Telematics and Informatics, 31(1), pp.62-78.
Handa, K. and Singh, U., 2015. Data security in cloud computing using encryption and
steganography. International Journal of Computer Science and Mobile Computing, 4(5), pp.786-
791.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Hartono, E., Holsapple, C.W., Kim, K.Y., Na, K.S. and Simpson, J.T., 2014. Measuring
perceived security in B2C electronic commerce website usage: A respecification and
validation. Decision Support Systems, 62, pp.11-21.
Hayikader, S., Hadi, F.N. and Ibrahim, J., 2016. Issues and security measures of mobile banking
Apps. International Journal of Scientific and Research Publications, 6(1), pp.36-41.
He, W., Tian, X. and Shen, J., 2015. Examining Security Risks of Mobile Banking Applications
through Blog Mining. In MAICS (pp. 103-108).
Islam, S., 2014. Systematic literature review: Security challenges of mobile banking and
payments system. International Journal of u-and e-Service, Science and Technology, 7(6),
pp.107-116.
Jacob, N.A. and Antony, G.V., 2018. Information Security Threats Faced by the Indian Banks-
An Exploratory Study. Sumedha Journal of Management, 7(2), pp.108-114.
Jansen, W.A., 2011. Cloud hooks: Security and privacy issues in cloud computing. In 2011 44th
Hawaii International Conference on System Sciences (pp. 1-10).
Kalpana, P. and Singaraju, S., 2012. Data security in cloud computing using the RSA algorithm.
International Journal of research in computer and communication technology, IJRCCT, ISSN,
pp.2278-5841.
Kong, W., Lei, Y. and Ma, J., 2016. Data security and privacy information challenges in cloud
computing. In 2016 International Conference on Intelligent Networking and Collaborative
Systems (INCoS) (pp. 512-514).
Kujur, T. and Shah, M.A., 2015. Electronic banking: Impact, risk and security
issues. International Journal of Engineering and Management Research (IJEMR), 5(5), pp.207-
212.
Kumar, V.A., Pandey, K.K. and Punia, D.K., 2014. Cyber security threats in the power sector:
Need for a domain specific regulatory framework in India. Energy policy, 65, pp.126-133.
perceived security in B2C electronic commerce website usage: A respecification and
validation. Decision Support Systems, 62, pp.11-21.
Hayikader, S., Hadi, F.N. and Ibrahim, J., 2016. Issues and security measures of mobile banking
Apps. International Journal of Scientific and Research Publications, 6(1), pp.36-41.
He, W., Tian, X. and Shen, J., 2015. Examining Security Risks of Mobile Banking Applications
through Blog Mining. In MAICS (pp. 103-108).
Islam, S., 2014. Systematic literature review: Security challenges of mobile banking and
payments system. International Journal of u-and e-Service, Science and Technology, 7(6),
pp.107-116.
Jacob, N.A. and Antony, G.V., 2018. Information Security Threats Faced by the Indian Banks-
An Exploratory Study. Sumedha Journal of Management, 7(2), pp.108-114.
Jansen, W.A., 2011. Cloud hooks: Security and privacy issues in cloud computing. In 2011 44th
Hawaii International Conference on System Sciences (pp. 1-10).
Kalpana, P. and Singaraju, S., 2012. Data security in cloud computing using the RSA algorithm.
International Journal of research in computer and communication technology, IJRCCT, ISSN,
pp.2278-5841.
Kong, W., Lei, Y. and Ma, J., 2016. Data security and privacy information challenges in cloud
computing. In 2016 International Conference on Intelligent Networking and Collaborative
Systems (INCoS) (pp. 512-514).
Kujur, T. and Shah, M.A., 2015. Electronic banking: Impact, risk and security
issues. International Journal of Engineering and Management Research (IJEMR), 5(5), pp.207-
212.
Kumar, V.A., Pandey, K.K. and Punia, D.K., 2014. Cyber security threats in the power sector:
Need for a domain specific regulatory framework in India. Energy policy, 65, pp.126-133.

Marium, S., Nazir, Q., Ahmed, A., Ahthasham, S. and Mirza, A.M., 2012. Implementation of
EAP with RSA for enhancing the security of cloud computing. International Journal of Basic
and Applied Science, 1(3), pp.177-183.
Marwaha, M. and Bedi, R., 2013. Applying encryption algorithm for data security and privacy in
cloud computing. International Journal of Computer Science Issues (IJCSI), 10(1), p.367.
Omar, A., Sultan, N., Zaman, K., Bibi, N., Wajid, A. and Khan, K., 2011. Customer perception
towards online banking services: Empirical evidence from Pakistan. Journal of Internet Banking
and Commerce, 16(2), pp. 45-79.
Padmapriya, A. and Subhasri, P., 2013. Cloud computing: security challenges and encryption
practices. International Journal of Advanced Research in Computer Science and Software
Engineering, 3(3), pp. 56-98.
Pancholi, V.R. and Patel, B.P., 2016. Enhancement of cloud computing security with secure data
storage using AES. International Journal for Innovative Research in Science and
Technology, 2(9), pp.18-21.
Prasad, M.R., Gyani, J. and Murti, P.R.K., 2012. Mobile cloud computing: Implications and
challenges. Journal of Information Engineering and Applications, 2(7), pp.7-15.
Sharma, S., 2016. A detail comparative study on e-banking VS traditional banking. International
Journal of Advanced Research, 2, pp.302-307.
Singh, G., 2013. A study of encryption algorithms (RSA, DES, 3DES, and AES) for information
security. International Journal of Computer Applications, 67(19), pp. 12-36.
Solanki, V.S., 2012. Risks in e-banking and their management. International Journal of
Marketing, Financial Services & Management Research, 1(9), pp.2277-3622.
Sun, Y., Zhang, J., Xiong, Y. and Zhu, G., 2014. Data security and privacy in cloud
computing. International Journal of Distributed Sensor Networks, 10(7), p.190.
Swacha-Lech, M., 2017. The main challenges facing the retail banking industry in the era of
digitalisation. Rozprawy Ubezpieczeniowe. Konsument na rynku usług finansowych, 4(26),
pp.94-116.
EAP with RSA for enhancing the security of cloud computing. International Journal of Basic
and Applied Science, 1(3), pp.177-183.
Marwaha, M. and Bedi, R., 2013. Applying encryption algorithm for data security and privacy in
cloud computing. International Journal of Computer Science Issues (IJCSI), 10(1), p.367.
Omar, A., Sultan, N., Zaman, K., Bibi, N., Wajid, A. and Khan, K., 2011. Customer perception
towards online banking services: Empirical evidence from Pakistan. Journal of Internet Banking
and Commerce, 16(2), pp. 45-79.
Padmapriya, A. and Subhasri, P., 2013. Cloud computing: security challenges and encryption
practices. International Journal of Advanced Research in Computer Science and Software
Engineering, 3(3), pp. 56-98.
Pancholi, V.R. and Patel, B.P., 2016. Enhancement of cloud computing security with secure data
storage using AES. International Journal for Innovative Research in Science and
Technology, 2(9), pp.18-21.
Prasad, M.R., Gyani, J. and Murti, P.R.K., 2012. Mobile cloud computing: Implications and
challenges. Journal of Information Engineering and Applications, 2(7), pp.7-15.
Sharma, S., 2016. A detail comparative study on e-banking VS traditional banking. International
Journal of Advanced Research, 2, pp.302-307.
Singh, G., 2013. A study of encryption algorithms (RSA, DES, 3DES, and AES) for information
security. International Journal of Computer Applications, 67(19), pp. 12-36.
Solanki, V.S., 2012. Risks in e-banking and their management. International Journal of
Marketing, Financial Services & Management Research, 1(9), pp.2277-3622.
Sun, Y., Zhang, J., Xiong, Y. and Zhu, G., 2014. Data security and privacy in cloud
computing. International Journal of Distributed Sensor Networks, 10(7), p.190.
Swacha-Lech, M., 2017. The main challenges facing the retail banking industry in the era of
digitalisation. Rozprawy Ubezpieczeniowe. Konsument na rynku usług finansowych, 4(26),
pp.94-116.

Takabi, H., Joshi, J.B. and Ahn, G.J., 2010. Security and privacy challenges in cloud computing
environments. IEEE Security & Privacy, 8(6), pp.24-31.
Tiwari, A.K., Agarwal, R. and Goyal, S., 2014. Imperative & challenges of mobile banking in
India. International Journal of Computer Science and Engineering Technology, 5(3,271-274).
Xavier, U.H.R. and Pati, B.P., 2012. Study of internet security threats among home users.
In 2012 Fourth International Conference on Computational Aspects of Social Networks
(CASoN) (pp. 217-221).
Yang, Q., Pang, C., Liu, L., Yen, D.C. and Tarn, J.M., 2015. Exploring consumer perceived risk
and trust for online payments: An empirical study in China’s younger generation. Computers in
Human Behavior, 50, pp.9-24.
Zahoor, Z., Ud-din, M. and Sunami, K., 2016. Challenges in privacy and security in banking
sector and related countermeasures. International Journal of Computer Applications, 144(3),
pp.24-35.
environments. IEEE Security & Privacy, 8(6), pp.24-31.
Tiwari, A.K., Agarwal, R. and Goyal, S., 2014. Imperative & challenges of mobile banking in
India. International Journal of Computer Science and Engineering Technology, 5(3,271-274).
Xavier, U.H.R. and Pati, B.P., 2012. Study of internet security threats among home users.
In 2012 Fourth International Conference on Computational Aspects of Social Networks
(CASoN) (pp. 217-221).
Yang, Q., Pang, C., Liu, L., Yen, D.C. and Tarn, J.M., 2015. Exploring consumer perceived risk
and trust for online payments: An empirical study in China’s younger generation. Computers in
Human Behavior, 50, pp.9-24.
Zahoor, Z., Ud-din, M. and Sunami, K., 2016. Challenges in privacy and security in banking
sector and related countermeasures. International Journal of Computer Applications, 144(3),
pp.24-35.
1 out of 43
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





