Desklib Online Library for Study Material with Solved Assignments
VerifiedAdded on 2023/06/11
|8
|3538
|497
AI Summary
Desklib is an online library that provides access to a vast collection of study material for various subjects and courses. It offers solved assignments, essays, dissertations, and more. The platform is designed to help students with their academic needs and provides a one-stop solution for all their study material requirements. Desklib is a reliable source of information and is perfect for students who are looking for high-quality study material.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
COIT 20246 ASSIGNMENT SUBMISSION
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There is a
table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Week 1
The text discusses how modern CPUs function. Recently a critical flaw in microprocessor
design has been discovered that allows two extremely serious security exploits: Spectre and
Meltdown. Find and summarise ONE resource that describes how either of these exploits
work. The resource (and your summary) should focus on what is occurring in the CPU that
allows these exploits to occur.
Title: Exploit of Spectra and Meltdown
Reference: Meltdownattack.com. (2018). Meltdown and Spectre. [online] Available at:
https://meltdownattack.com/ [Accessed 12 May 2018].
Summary:
The main focus point of the article is to take into consideration different aspects which are
related to the meltdown attack.
The main aspect which is related to the attack of the meltdown is the isolation of the operating
system and the application of the user. The main motive behind the attack is that it directly
allows the program to access the memory. The memory access can be related to the access
to the personal data of the user and of the system. The attack is generally initiated in system
which has a vulnerable processor or other system updates are not done properly. If the
system of the user has the above mentioned aspect it can be stated that critical data
processing should be very much avoided in the system. The data which is collected form the
exploit can be used in several of purpose which can directly hamper the system configuration
as well the revelling of the secrets which are stored in the system. Software’s patches can
also be one of the aspects which is related to the mitigation of the attack which is related to
meltdown.
Week 2
Prior to 1985, there were very few Operating Systems (OSes) that used Graphical User
Interfaces (GUIs). Find and summarise ONE resource that describes ONE of these GUI
operating systems. The OS must have been release prior to 1985 so cannot be Microsoft
Windows.
Title: GUI Operating system
Reference: Templates, B. (2018). List of GUI-Based Operating System and Its History.
[online] E-techinnews.blogspot.in. Available at: http://e-techinnews.blogspot.in/2012/06/list-of-
gui-based-operating-system-and.html [Accessed 12 May 2018].
Summary:
The main consideration which is taken into focus selecting the article is that it gives a precise
explanation of the GUI (Graphical user interface) operating system.
The operating system which is selected in the aspect is the Mac OS system 1.0 which was
developed by the Macintosh. The operating system can be considered to be involving all the
important features which should be include into an operating system. The main advantage
which is related to the concept is that the window is accompanied with the help of icons. On
the other hand it can be stated that each of the window can be directly be moved or replaced
There are ten (10) tasks, one for each week: the tasks are detailed below. There is a
table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Week 1
The text discusses how modern CPUs function. Recently a critical flaw in microprocessor
design has been discovered that allows two extremely serious security exploits: Spectre and
Meltdown. Find and summarise ONE resource that describes how either of these exploits
work. The resource (and your summary) should focus on what is occurring in the CPU that
allows these exploits to occur.
Title: Exploit of Spectra and Meltdown
Reference: Meltdownattack.com. (2018). Meltdown and Spectre. [online] Available at:
https://meltdownattack.com/ [Accessed 12 May 2018].
Summary:
The main focus point of the article is to take into consideration different aspects which are
related to the meltdown attack.
The main aspect which is related to the attack of the meltdown is the isolation of the operating
system and the application of the user. The main motive behind the attack is that it directly
allows the program to access the memory. The memory access can be related to the access
to the personal data of the user and of the system. The attack is generally initiated in system
which has a vulnerable processor or other system updates are not done properly. If the
system of the user has the above mentioned aspect it can be stated that critical data
processing should be very much avoided in the system. The data which is collected form the
exploit can be used in several of purpose which can directly hamper the system configuration
as well the revelling of the secrets which are stored in the system. Software’s patches can
also be one of the aspects which is related to the mitigation of the attack which is related to
meltdown.
Week 2
Prior to 1985, there were very few Operating Systems (OSes) that used Graphical User
Interfaces (GUIs). Find and summarise ONE resource that describes ONE of these GUI
operating systems. The OS must have been release prior to 1985 so cannot be Microsoft
Windows.
Title: GUI Operating system
Reference: Templates, B. (2018). List of GUI-Based Operating System and Its History.
[online] E-techinnews.blogspot.in. Available at: http://e-techinnews.blogspot.in/2012/06/list-of-
gui-based-operating-system-and.html [Accessed 12 May 2018].
Summary:
The main consideration which is taken into focus selecting the article is that it gives a precise
explanation of the GUI (Graphical user interface) operating system.
The operating system which is selected in the aspect is the Mac OS system 1.0 which was
developed by the Macintosh. The operating system can be considered to be involving all the
important features which should be include into an operating system. The main advantage
which is related to the concept is that the window is accompanied with the help of icons. On
the other hand it can be stated that each of the window can be directly be moved or replaced
with the help of a mouse. The aspect is not only restricted to the window but is also expanded
to the concept of the folders even. The Mac OS system 1.0 was considered as one of the
most advanced operating system which was dealt with the security aspect of the data. The
concept can be related to the aspect of the MAC very much simple when comparing with
other conecpts which are related to the GUI operating system
Week 3
Low-Powered Wide-Area Networks (LPWANs) are wireless communication networks that are
characterised by linking devices over large distances. Devices (including simple sensors)
typically can only communicate at very low bit rates, however, the communication and
associated electronics consume very little power. As such, LPWAN devices can be battery
powered and operate independently for many months or even years. Find and summarise
ONE resource that describes ONE platform or technology that implements a LPWAN.
Title: Technology that implements a LPWAN
Reference: Bhatia, R. (2018). What is LPWAN and why is it considered critical for IoT?.
[online] IoT India Magazine. Available at: https://www.iotindiamag.com/2017/03/lpwan-
considered-critical-iot/ [Accessed 13 May 2018].
Summary:
The main justification for the selection of the resource is due to the influence that is gives a
direct overview of the concept of the LPWAN and how it can be implemented into different
technology. The main technology which is taken into consideration in the aspect is the
Internet of things.
The concept of the LPWAN directly fuels the direct issue which is related to the internet of
things devices. The basic need which is related to the device is the less bandwidth that would
be required in order to make the internet of things devices very much functional. The main
advantage which can be achieved from the concept is that it makes the aspect of the internet
of things robust “low power blanket” and scalable taking into example devices such as
sensors and lighting. The LPWAN can be considered to be threatening the license which is
related to the cellular network and has a direct focus on the aspect of the redefining the IoT
sector. There are many research which is being conducted which states that in the near
future the technology would be playing a more dominating role and advantage of the
technology can be taken in different stages.
Week 4
Voice over IP (VoIP) is a group of hardware and software technologies that allow users to
communicate via voice and video over the Internet. VoIP uses a number of different software
protocols, depending on the application. Find and summarise ONE resource that describes
ONE of these VoIP protocols.
Title: VoIP Protocols
Reference: Voice over Internet Protocol (VoIP) Based IP PBX System Design. (2016).
International Journal of Science and Research (IJSR), 5(2), pp.1380-1385.
Summary:
The main aspect which is related to the concept is that it gives a simple explanation of the
concept of the protocols which are related to the VoIP. The protocol which is taken into focus
in this aspect is the H.248.
The main functionality which is related to the H. 248 is that it provides a gateway interface
between the control protocols which are related to the VXSM gateway and the PGW 2200. It
can be stated here that the H.248 directly provides a supplement to the protocol which is
related to the MGCP protocol. The functionality interface is related to the ITU-SG16/IETF.
The architecture which is related to the H.248 basically comprise of media gateways (MGs)
and media gateway controller (MGC). The main functionality which is related to the working of
to the concept of the folders even. The Mac OS system 1.0 was considered as one of the
most advanced operating system which was dealt with the security aspect of the data. The
concept can be related to the aspect of the MAC very much simple when comparing with
other conecpts which are related to the GUI operating system
Week 3
Low-Powered Wide-Area Networks (LPWANs) are wireless communication networks that are
characterised by linking devices over large distances. Devices (including simple sensors)
typically can only communicate at very low bit rates, however, the communication and
associated electronics consume very little power. As such, LPWAN devices can be battery
powered and operate independently for many months or even years. Find and summarise
ONE resource that describes ONE platform or technology that implements a LPWAN.
Title: Technology that implements a LPWAN
Reference: Bhatia, R. (2018). What is LPWAN and why is it considered critical for IoT?.
[online] IoT India Magazine. Available at: https://www.iotindiamag.com/2017/03/lpwan-
considered-critical-iot/ [Accessed 13 May 2018].
Summary:
The main justification for the selection of the resource is due to the influence that is gives a
direct overview of the concept of the LPWAN and how it can be implemented into different
technology. The main technology which is taken into consideration in the aspect is the
Internet of things.
The concept of the LPWAN directly fuels the direct issue which is related to the internet of
things devices. The basic need which is related to the device is the less bandwidth that would
be required in order to make the internet of things devices very much functional. The main
advantage which can be achieved from the concept is that it makes the aspect of the internet
of things robust “low power blanket” and scalable taking into example devices such as
sensors and lighting. The LPWAN can be considered to be threatening the license which is
related to the cellular network and has a direct focus on the aspect of the redefining the IoT
sector. There are many research which is being conducted which states that in the near
future the technology would be playing a more dominating role and advantage of the
technology can be taken in different stages.
Week 4
Voice over IP (VoIP) is a group of hardware and software technologies that allow users to
communicate via voice and video over the Internet. VoIP uses a number of different software
protocols, depending on the application. Find and summarise ONE resource that describes
ONE of these VoIP protocols.
Title: VoIP Protocols
Reference: Voice over Internet Protocol (VoIP) Based IP PBX System Design. (2016).
International Journal of Science and Research (IJSR), 5(2), pp.1380-1385.
Summary:
The main aspect which is related to the concept is that it gives a simple explanation of the
concept of the protocols which are related to the VoIP. The protocol which is taken into focus
in this aspect is the H.248.
The main functionality which is related to the H. 248 is that it provides a gateway interface
between the control protocols which are related to the VXSM gateway and the PGW 2200. It
can be stated here that the H.248 directly provides a supplement to the protocol which is
related to the MGCP protocol. The functionality interface is related to the ITU-SG16/IETF.
The architecture which is related to the H.248 basically comprise of media gateways (MGs)
and media gateway controller (MGC). The main functionality which is related to the working of
the H.248 is that it provides an IP telephony network with the PSTN network which directly
passes the voice traffic from one section of the network to another section without any
decrease in the quality of the voice. Although it can be stated that the concept of the H.248 is
designed for the aspect of the generic support but it can be stated that the PSW is directly
designed to act as an MGC and only the interwork with the gateway which is related to
trunking.
Week 5
One of the many uses of cryptography has been the development of the blockchain.
Blockchains are commonly used as the basis for maintaining the data integrity of crypto
currencies, though have many, many more applications. Find and summarise ONE resource
that describes how blockchains work. Note that the resource should focus on the blockchain
mechanism, NOT crypto currencies.
Title: How blockchain works.
Reference: Happiest Minds. (2018). What is Blockchain Technology | Blockchain
Applications. [online] Available at: https://www.happiestminds.com/Insights/blockchain/
[Accessed 13 May 2018].
Summary:
The main reason for the selection of the article is that it gives a direct overview of the concept
of the blockchain and what are the main advantage which is related to the concept and how
they can be implemented.
The blockchain can be considered as a ledger which is distributed in nature across different
platform or application which are not bound in one area or access point. Due to this
advantage sector the technology is implemented widely in the sector the finance and large
amount of benefit are directly achieved from the aspect. The main security aspect which is
related to the data is that each of the data is converted to a hash which keeps the data
secured so that no third person can directly access the data. The data in this concept can be
stated as hash and the family is considered as a block and together they are stated as
blockchain. The concept of the blockchain directly updates themselves and no computer or
software directly instructs them to do the updating.
Week 6
One controversial practical application of network traffic management is in the contravention
of the principle of “net neutrality”. Find and summarise ONE resource that describes what net
neutrality is and how its contravention could impact on individual and business users of the
Internet.
Title: Net neutrality
Reference: Finley, K., Hempel, J., Graff, G., Tiku, N., Matsakis, L., Simonite, T. and
Lapowsky, I. (2018). Net Neutrality: Here's Everything You Need To Know. [online] WIRED.
Available at: https://www.wired.com/story/guide-net-neutrality/ [Accessed 14 May 2018].
Summary:
The justification which is related to the selection of the article is that it provides an overview of
the concept which is related to the net Neutrality and how it can be implemented in recent
times.
Net neutrality can be considered as an idea which is related to the aspect of the internet
service providers such as the Comcast and the Verizon. The main point which is taken into
consideration is the aspect of the content flow which is through the tables and the cell tower
equality aspect. This directly means that the concept should be very much available to slide
some of the data into the fast lanes while the blocking of the user or the unauthorized user
are done. The concept of the Net neutrality is directly implemented in different organization
with the main focus point which is related to the security of the data. Most of the broadband
providers are implementing the technology in order to secure their server from unwanted
traffic so that the net access can be done more properly by authorized user without any type
of discrimency attached to the concept. It can be stated that the concept of the net neutrality
passes the voice traffic from one section of the network to another section without any
decrease in the quality of the voice. Although it can be stated that the concept of the H.248 is
designed for the aspect of the generic support but it can be stated that the PSW is directly
designed to act as an MGC and only the interwork with the gateway which is related to
trunking.
Week 5
One of the many uses of cryptography has been the development of the blockchain.
Blockchains are commonly used as the basis for maintaining the data integrity of crypto
currencies, though have many, many more applications. Find and summarise ONE resource
that describes how blockchains work. Note that the resource should focus on the blockchain
mechanism, NOT crypto currencies.
Title: How blockchain works.
Reference: Happiest Minds. (2018). What is Blockchain Technology | Blockchain
Applications. [online] Available at: https://www.happiestminds.com/Insights/blockchain/
[Accessed 13 May 2018].
Summary:
The main reason for the selection of the article is that it gives a direct overview of the concept
of the blockchain and what are the main advantage which is related to the concept and how
they can be implemented.
The blockchain can be considered as a ledger which is distributed in nature across different
platform or application which are not bound in one area or access point. Due to this
advantage sector the technology is implemented widely in the sector the finance and large
amount of benefit are directly achieved from the aspect. The main security aspect which is
related to the data is that each of the data is converted to a hash which keeps the data
secured so that no third person can directly access the data. The data in this concept can be
stated as hash and the family is considered as a block and together they are stated as
blockchain. The concept of the blockchain directly updates themselves and no computer or
software directly instructs them to do the updating.
Week 6
One controversial practical application of network traffic management is in the contravention
of the principle of “net neutrality”. Find and summarise ONE resource that describes what net
neutrality is and how its contravention could impact on individual and business users of the
Internet.
Title: Net neutrality
Reference: Finley, K., Hempel, J., Graff, G., Tiku, N., Matsakis, L., Simonite, T. and
Lapowsky, I. (2018). Net Neutrality: Here's Everything You Need To Know. [online] WIRED.
Available at: https://www.wired.com/story/guide-net-neutrality/ [Accessed 14 May 2018].
Summary:
The justification which is related to the selection of the article is that it provides an overview of
the concept which is related to the net Neutrality and how it can be implemented in recent
times.
Net neutrality can be considered as an idea which is related to the aspect of the internet
service providers such as the Comcast and the Verizon. The main point which is taken into
consideration is the aspect of the content flow which is through the tables and the cell tower
equality aspect. This directly means that the concept should be very much available to slide
some of the data into the fast lanes while the blocking of the user or the unauthorized user
are done. The concept of the Net neutrality is directly implemented in different organization
with the main focus point which is related to the security of the data. Most of the broadband
providers are implementing the technology in order to secure their server from unwanted
traffic so that the net access can be done more properly by authorized user without any type
of discrimency attached to the concept. It can be stated that the concept of the net neutrality
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
would be playing a dominating role in the near future.
Week 7
Information Systems have led to greater and greater degrees of automation in the workplace.
There is currently extensive speculation on which jobs will cease to be performed by humans
in the near future. Find and summarise ONE resource that discusses jobs that are likely to
not exist in the future due to ICT based automation. Note that the resource must clearly link
the loss of the job(s) to advances in ICT.
Title: Job lost due to ICT automation
Reference: TechCrunch. (2018). Technology is killing jobs, and only technology can save
them. [online] Available at: https://techcrunch.com/2017/03/26/technology-is-killing-jobs-and-
only-technology-can-save-them/ [Accessed 14 May 2018].
Summary:
The main reason for the section of the article is due to the factor that it gives a directly
overview of the concept of the ICT automation and how it would be likely implemented in the
sector of the loss job sector.
In recent times it can be stated that many technology are being automated which directly
means that human intervention would be very much less in the different sectors. The main
advantage which can be related to the concept is that the automation would result in less
error prone activity. On the other hand it can be stated that the most of the technology need
expertise to deal with the system. So it can be stated here that loss of job would be directly
defecting the people who are not so much involved into the working or it can be stated as who
are not so much technology oriented people. The different sectors which the ICT automation
has helped are majorly in the sector of finance, banking and telecom. In the near future it can
be stated be playing a more vital role which would be directly effecting the life of the common
people.
Week 8
With the advent of mass data collection and storage has come the use of these datasets for
machine learning. Find and summarise ONE resource that describes what machine learning
is and how it is being used.
Title: Concept of Machine Learning
Reference: Sas.com. (2018). Machine Learning: What it is and why it matters. [online]
Available at: https://www.sas.com/en_in/insights/analytics/machine-learning.html [Accessed
14 May 2018].
Summary:
The above mentioned article gives a precise overview of the concept which is applicable to
the aspect of the machine learning. One of the important factors which are majorly discussed
in the article is that how the aspect of machine learning is providing an enhancement sector in
the technology oriented field.
The concept of the machine learning can be directly be related to the aspect of the artificial
intelligence. The main functionality which is related to the machine learning is the capability of
the machine to learn from the data which is feed into the system. The system according to the
data which is feed takes necessary decision and provides a framework of decision relating to
the data which is available. The concept of machine learning can also be related to the aspect
of linguistic which directly means that it would be playing a very vital role in the near future.
The concept of machine learning can also be implemented in the sector of fraud detection
which would be directly securing the data of the system as well as the data of the
organization or the user in different manner.
Week 7
Information Systems have led to greater and greater degrees of automation in the workplace.
There is currently extensive speculation on which jobs will cease to be performed by humans
in the near future. Find and summarise ONE resource that discusses jobs that are likely to
not exist in the future due to ICT based automation. Note that the resource must clearly link
the loss of the job(s) to advances in ICT.
Title: Job lost due to ICT automation
Reference: TechCrunch. (2018). Technology is killing jobs, and only technology can save
them. [online] Available at: https://techcrunch.com/2017/03/26/technology-is-killing-jobs-and-
only-technology-can-save-them/ [Accessed 14 May 2018].
Summary:
The main reason for the section of the article is due to the factor that it gives a directly
overview of the concept of the ICT automation and how it would be likely implemented in the
sector of the loss job sector.
In recent times it can be stated that many technology are being automated which directly
means that human intervention would be very much less in the different sectors. The main
advantage which can be related to the concept is that the automation would result in less
error prone activity. On the other hand it can be stated that the most of the technology need
expertise to deal with the system. So it can be stated here that loss of job would be directly
defecting the people who are not so much involved into the working or it can be stated as who
are not so much technology oriented people. The different sectors which the ICT automation
has helped are majorly in the sector of finance, banking and telecom. In the near future it can
be stated be playing a more vital role which would be directly effecting the life of the common
people.
Week 8
With the advent of mass data collection and storage has come the use of these datasets for
machine learning. Find and summarise ONE resource that describes what machine learning
is and how it is being used.
Title: Concept of Machine Learning
Reference: Sas.com. (2018). Machine Learning: What it is and why it matters. [online]
Available at: https://www.sas.com/en_in/insights/analytics/machine-learning.html [Accessed
14 May 2018].
Summary:
The above mentioned article gives a precise overview of the concept which is applicable to
the aspect of the machine learning. One of the important factors which are majorly discussed
in the article is that how the aspect of machine learning is providing an enhancement sector in
the technology oriented field.
The concept of the machine learning can be directly be related to the aspect of the artificial
intelligence. The main functionality which is related to the machine learning is the capability of
the machine to learn from the data which is feed into the system. The system according to the
data which is feed takes necessary decision and provides a framework of decision relating to
the data which is available. The concept of machine learning can also be related to the aspect
of linguistic which directly means that it would be playing a very vital role in the near future.
The concept of machine learning can also be implemented in the sector of fraud detection
which would be directly securing the data of the system as well as the data of the
organization or the user in different manner.

Week 9
Critical to application development are the languages used to implement the specifications.
Find and summarise ONE resource that describes ONE programming language that has
been developed since 2008. The resource (and your summary) should include information
on the principle uses and features of the language.
Title: Pure Programming Language
Reference: Purelang.bitbucket.io. (2018). Pure Programming Language. [online] Available at:
https://purelang.bitbucket.io/ [Accessed 14 May 2018].
Summary:
Programming language are widely used by the developers to develop a scenario which is
related to the aspect of the working which is related to the concept of the technology.
The Pure programming language can be stated to be in existing since 2008. The aspect of
the pure programming language has different level of functionality which can be related to the
normal programming language concept. It can be stated as one of the most used
programming language due to the factor that it involves all the necessary features which can
be very much helpful in different types of functionality to be achieved. It can be stated here
that the pure programming language can be directly be implemented into different
programming environment quite easily so it can be stated as an environmental friendly
programming language. The system support relating to the programming language can range
from Mac OS X, free BSD and windows just to name a few. The allocation of the memory with
regards to the programming language can be considered to be very much appropriately and
within the range so that the execution of the program is done in a proper manner in a proper
framework.
Critical to application development are the languages used to implement the specifications.
Find and summarise ONE resource that describes ONE programming language that has
been developed since 2008. The resource (and your summary) should include information
on the principle uses and features of the language.
Title: Pure Programming Language
Reference: Purelang.bitbucket.io. (2018). Pure Programming Language. [online] Available at:
https://purelang.bitbucket.io/ [Accessed 14 May 2018].
Summary:
Programming language are widely used by the developers to develop a scenario which is
related to the aspect of the working which is related to the concept of the technology.
The Pure programming language can be stated to be in existing since 2008. The aspect of
the pure programming language has different level of functionality which can be related to the
normal programming language concept. It can be stated as one of the most used
programming language due to the factor that it involves all the necessary features which can
be very much helpful in different types of functionality to be achieved. It can be stated here
that the pure programming language can be directly be implemented into different
programming environment quite easily so it can be stated as an environmental friendly
programming language. The system support relating to the programming language can range
from Mac OS X, free BSD and windows just to name a few. The allocation of the memory with
regards to the programming language can be considered to be very much appropriately and
within the range so that the execution of the program is done in a proper manner in a proper
framework.

Week 10
While information systems and technology deliver many benefits to society, they can also
result in negative effects and outcomes. One recent controversy, the propagation of fake
news and its influence on elections, has been linked to a type of software called a “bot”. Find
and summarise ONE resource that describes what bots are and how they can be used for
disseminating misinformation and affecting human behaviour.
Title: Loss of job due to ICT Automation
Reference: Us.norton.com. (2018). What Are Bots?. [online] Available at:
https://us.norton.com/internetsecurity-malware-what-are-bots.html [Accessed 13 May 2018].
Summary:
The bots or the internet bots can be considered as a spider, crawlers and web bots. The main
functionality which is related to the bots is that it directly performs repetitive mapping of the
jobs such as the search engine optimization. There are basically two types of bots mainly the
good bots and the bad bots. The good bots are usually utilized in the sector of the information
gathering, another sector were the bots can be very much beneficial is the interaction sector
which is achieved in concept of the instant messaging.
The bad sector which is related to bots generally include malware activity. These malware
activity can directly impact the normal functionality of the system. The transportation of the
malware activity can be majorly in the area of the access denied aspect. The malware directly
prevents an authorized user to deny the access of a particular area. On the other hand the
bad bots can also be used in the aspect of the information gathering which may include
password and username collection. The bots are usually infected on large number of
computers. These computer directly form a bot network which is related to a system of
networks.
While information systems and technology deliver many benefits to society, they can also
result in negative effects and outcomes. One recent controversy, the propagation of fake
news and its influence on elections, has been linked to a type of software called a “bot”. Find
and summarise ONE resource that describes what bots are and how they can be used for
disseminating misinformation and affecting human behaviour.
Title: Loss of job due to ICT Automation
Reference: Us.norton.com. (2018). What Are Bots?. [online] Available at:
https://us.norton.com/internetsecurity-malware-what-are-bots.html [Accessed 13 May 2018].
Summary:
The bots or the internet bots can be considered as a spider, crawlers and web bots. The main
functionality which is related to the bots is that it directly performs repetitive mapping of the
jobs such as the search engine optimization. There are basically two types of bots mainly the
good bots and the bad bots. The good bots are usually utilized in the sector of the information
gathering, another sector were the bots can be very much beneficial is the interaction sector
which is achieved in concept of the instant messaging.
The bad sector which is related to bots generally include malware activity. These malware
activity can directly impact the normal functionality of the system. The transportation of the
malware activity can be majorly in the area of the access denied aspect. The malware directly
prevents an authorized user to deny the access of a particular area. On the other hand the
bad bots can also be used in the aspect of the information gathering which may include
password and username collection. The bots are usually infected on large number of
computers. These computer directly form a bot network which is related to a system of
networks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
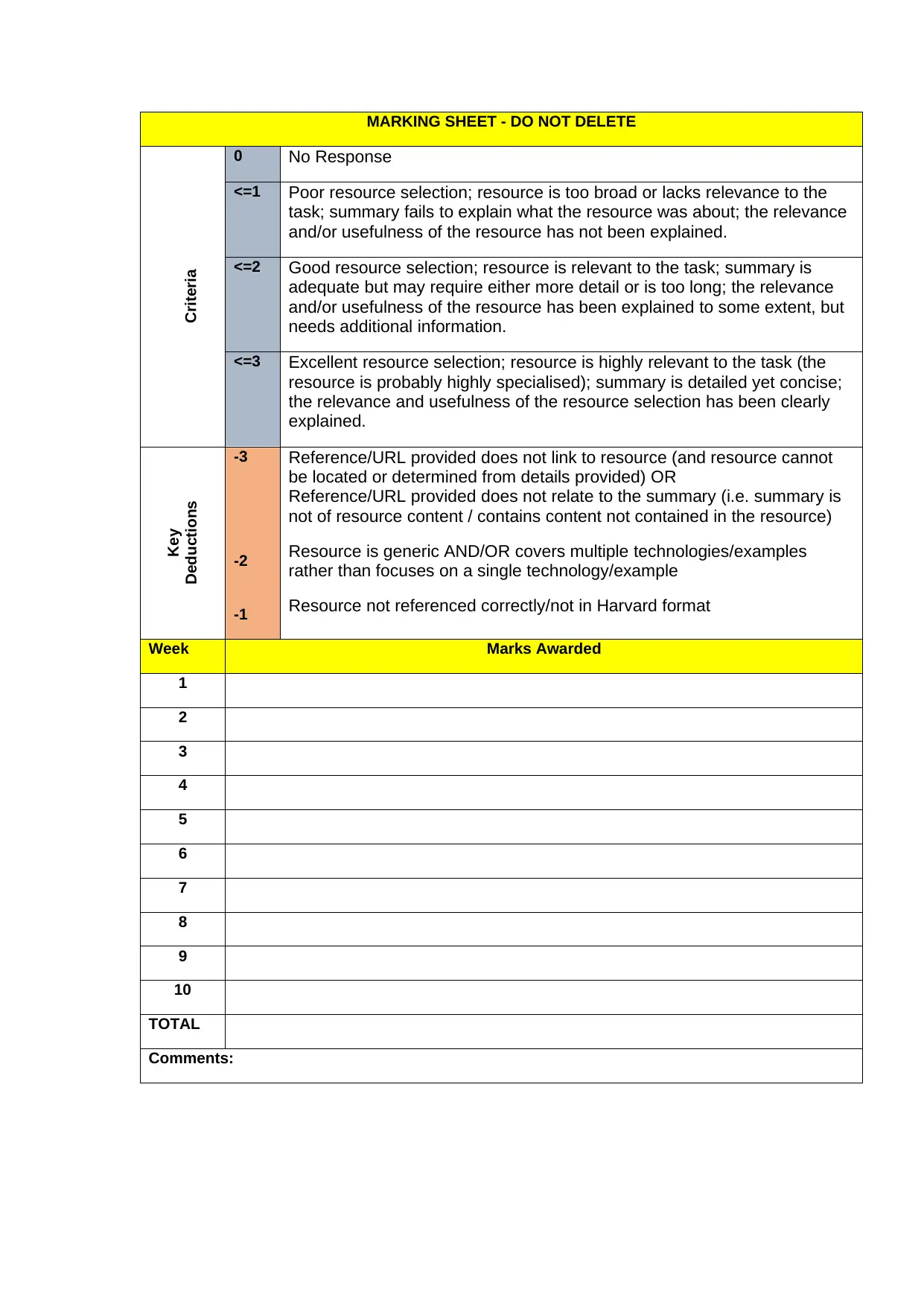
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.


