Development of Network Solution for uSoft.com
VerifiedAdded on 2023/04/23
|14
|3389
|393
AI Summary
This report evaluates the current network framework used by uSoft.com and develops a new network solution to connect two of its branch offices for enabling communication with each other. The number of department comprising the head quarter and plan of the company for increasing the ...
Read More
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Data Communication and Networks
Name of the Student
Name of the University
Author
Date
Name of the Student
Name of the University
Author
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Summary
uSoft.com have the requirement of development of a network solution to connect two of its branch
offices for enabling communication with each other. The current network framework used by the
organization is evaluated for identification of the issues with the network and the new network
solution is developed that would help in meeting the business and technical goals of the
organization. The number of department comprising the head quarter and plan of the company for
increasing the employees is evaluated for the calculation of subnet for each of the department. The
security requirement of the organization is also evaluated for protecting the IT assets of the
company from the internal and external agents. The structure of the HQ is analysed for proposing
the logical and physical network framework and documenting in the report. The building plan of the
company headquarter is evaluated for identification of the placement of the network device and
develop the physical network topology to ensure that the network solution meets the need of the
organization.
uSoft.com have the requirement of development of a network solution to connect two of its branch
offices for enabling communication with each other. The current network framework used by the
organization is evaluated for identification of the issues with the network and the new network
solution is developed that would help in meeting the business and technical goals of the
organization. The number of department comprising the head quarter and plan of the company for
increasing the employees is evaluated for the calculation of subnet for each of the department. The
security requirement of the organization is also evaluated for protecting the IT assets of the
company from the internal and external agents. The structure of the HQ is analysed for proposing
the logical and physical network framework and documenting in the report. The building plan of the
company headquarter is evaluated for identification of the placement of the network device and
develop the physical network topology to ensure that the network solution meets the need of the
organization.

Table of Contents
Summary...............................................................................................................................................2
1. Introduction.......................................................................................................................................4
1.1 Goals............................................................................................................................................4
1.2 Purpose........................................................................................................................................4
1.3. Background and Scope...............................................................................................................4
2. Organisational Description................................................................................................................4
3. Analysis of User Requirements (Requirement engineering)..............................................................5
3.1 Mobility Requirements................................................................................................................5
3.2 Security requirements.................................................................................................................5
3.3 Bandwidth requirement..............................................................................................................5
3.4 Application requirement.............................................................................................................5
3.5 Remote access requirement........................................................................................................5
3.6 Quality of service requirement....................................................................................................6
3.7 VoIP Service Requirement...........................................................................................................6
4. Logical Design....................................................................................................................................6
4.1 Security:.......................................................................................................................................6
4.2 Wireless Networks:....................................................................................................................6
4.3 Virtual LANs:...............................................................................................................................6
4.4 Organisational Structure..............................................................................................................7
5. IP Address Allocation Plan:................................................................................................................7
6. Logical Network Diagram:................................................................................................................10
7. Physical Network Diagram:..............................................................................................................10
7. Conclusions......................................................................................................................................12
List of References................................................................................................................................13
Summary...............................................................................................................................................2
1. Introduction.......................................................................................................................................4
1.1 Goals............................................................................................................................................4
1.2 Purpose........................................................................................................................................4
1.3. Background and Scope...............................................................................................................4
2. Organisational Description................................................................................................................4
3. Analysis of User Requirements (Requirement engineering)..............................................................5
3.1 Mobility Requirements................................................................................................................5
3.2 Security requirements.................................................................................................................5
3.3 Bandwidth requirement..............................................................................................................5
3.4 Application requirement.............................................................................................................5
3.5 Remote access requirement........................................................................................................5
3.6 Quality of service requirement....................................................................................................6
3.7 VoIP Service Requirement...........................................................................................................6
4. Logical Design....................................................................................................................................6
4.1 Security:.......................................................................................................................................6
4.2 Wireless Networks:....................................................................................................................6
4.3 Virtual LANs:...............................................................................................................................6
4.4 Organisational Structure..............................................................................................................7
5. IP Address Allocation Plan:................................................................................................................7
6. Logical Network Diagram:................................................................................................................10
7. Physical Network Diagram:..............................................................................................................10
7. Conclusions......................................................................................................................................12
List of References................................................................................................................................13

1. Introduction
1.1 Goals
The main goals for the development of the network for usoft.com are listed below:
Improvement of VoIP, wireless and communication between each of the department for
improving the performance of the employees
Protecting the sensitive information of the organization and configuring access control list
for managing the access of the user to the servers installed in different departments
Improvement of scalability of the network and allow more number of users to connect and
support the growth of the company
The performance of the network should not decrease with the increase in the number of
users and different risk such as congestion, packet loss, jitter should be eliminated.
Access control list should be configured for the management of communication of the user
to access the servers of different departments
Connecting the wireless access point in different subnet such that it can not be used by the
intruder to gain access of the local network.
1.2 Purpose
The purpose of the development of the network solution is to have a centralized
management on the data traffic flowing from different sources and destination addresses in the
network. The successfully send and receive data packet from the headquarter to the branches and
reduce the response time of the network. The network is needed to be configured such the
employees of the organization can connect with the organizational network from remote location
for improvement of their productivity. The network is needed to be develop such that its
performance is high and there should not be any error in the configuration of the network device
such that failure occur in the system. A DMZ, firewall and network security policy is needed to be
configured such that the access of the user is monitored and the resources are secured.
1.3. Background and Scope
The network solution is developed for usoft.com which is a private biomedical software
development company having 6 departments in the companies headquarter. The network solution is
developed for supporting the expansion of the company and meeting its business and technical
goals. Currently the company have 102 number of employees in the software development
department, 92 employees in solution design, 62 in customer support, 52 in sales, 32 in finance and
22 in human resource department. Sales finance and human resource department have 1 server,
software development have 3 servers and solution design have 2 servers installed in its subnet.
Some extra number of Ip address are kept in reserve for supporting the expansion of the
organization and connect more employees in each of the subnet created for the department.
1.1 Goals
The main goals for the development of the network for usoft.com are listed below:
Improvement of VoIP, wireless and communication between each of the department for
improving the performance of the employees
Protecting the sensitive information of the organization and configuring access control list
for managing the access of the user to the servers installed in different departments
Improvement of scalability of the network and allow more number of users to connect and
support the growth of the company
The performance of the network should not decrease with the increase in the number of
users and different risk such as congestion, packet loss, jitter should be eliminated.
Access control list should be configured for the management of communication of the user
to access the servers of different departments
Connecting the wireless access point in different subnet such that it can not be used by the
intruder to gain access of the local network.
1.2 Purpose
The purpose of the development of the network solution is to have a centralized
management on the data traffic flowing from different sources and destination addresses in the
network. The successfully send and receive data packet from the headquarter to the branches and
reduce the response time of the network. The network is needed to be configured such the
employees of the organization can connect with the organizational network from remote location
for improvement of their productivity. The network is needed to be develop such that its
performance is high and there should not be any error in the configuration of the network device
such that failure occur in the system. A DMZ, firewall and network security policy is needed to be
configured such that the access of the user is monitored and the resources are secured.
1.3. Background and Scope
The network solution is developed for usoft.com which is a private biomedical software
development company having 6 departments in the companies headquarter. The network solution is
developed for supporting the expansion of the company and meeting its business and technical
goals. Currently the company have 102 number of employees in the software development
department, 92 employees in solution design, 62 in customer support, 52 in sales, 32 in finance and
22 in human resource department. Sales finance and human resource department have 1 server,
software development have 3 servers and solution design have 2 servers installed in its subnet.
Some extra number of Ip address are kept in reserve for supporting the expansion of the
organization and connect more employees in each of the subnet created for the department.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2. Organisational Description
The company named usoft.com currently have two branches located in different areas of
Gold Coast region. For expansion of the companies network the current network topology of the
headquarter is needed to be redesigned following the business and technical goals of the
organization. The headquarter of the company has 6 departments and each of the department are
allocated with separate floors of a six stories building. The organization have a option to allocate two
of the floors to solution design and thus the network is needed to be designed to meet the option.
3. Analysis of User Requirements (Requirement engineering)
The requirement of the user is analysed for developing the solution for usoft.com after analysing the
technical and business goals of the organization. The mobility, security, bandwidth, application and
remote access requirement is
3.1 Mobility Requirements
The wireless access point should be installed in the workplace area such that the people
working in the organization can connect their wireless device. The servers deployed in the network is
needed to be configured as RADIUS server such that the users can access the organisational network
from remote location for increasing the efficiency and access the resources residing in the server.
3.2 Security requirements
The wireless access point is needed to be secured from the external agents with the application of
encryption and creating different subnet for each of the department. The router used for
transmission of data packet to different sources in the network is needed to be configured with
access control list for management of access of the inter departmental server and secure the
information residing in the server.
3.3 Bandwidth requirement
The application that are used by the employees of different department are analysed for
calculating the bandwidth needed for running the application. For ensuring that each of the subnet
have sufficient bandwidth for its operation the interface is needed to be divided and a proper
cabling plan should be followed to interconnect the network devices.
3.4 Application requirement
The solution design would require to run different web development tools and software for
designing the interface. A standard antivirus software should be installed in each of the host
connected in the network for eliminating the risk of spyware, malware and other viruses that can
affect the performance of the network.
3.5 Remote access requirement
Configuration of the server with RADUIS protocol helps in enabling the user to gain access of
the network from remote geographical location. The users are needed to access the internal
network of the organization such that they can improve their productivity and help the organisation
to gain competitive advantage in the marketplace.
The company named usoft.com currently have two branches located in different areas of
Gold Coast region. For expansion of the companies network the current network topology of the
headquarter is needed to be redesigned following the business and technical goals of the
organization. The headquarter of the company has 6 departments and each of the department are
allocated with separate floors of a six stories building. The organization have a option to allocate two
of the floors to solution design and thus the network is needed to be designed to meet the option.
3. Analysis of User Requirements (Requirement engineering)
The requirement of the user is analysed for developing the solution for usoft.com after analysing the
technical and business goals of the organization. The mobility, security, bandwidth, application and
remote access requirement is
3.1 Mobility Requirements
The wireless access point should be installed in the workplace area such that the people
working in the organization can connect their wireless device. The servers deployed in the network is
needed to be configured as RADIUS server such that the users can access the organisational network
from remote location for increasing the efficiency and access the resources residing in the server.
3.2 Security requirements
The wireless access point is needed to be secured from the external agents with the application of
encryption and creating different subnet for each of the department. The router used for
transmission of data packet to different sources in the network is needed to be configured with
access control list for management of access of the inter departmental server and secure the
information residing in the server.
3.3 Bandwidth requirement
The application that are used by the employees of different department are analysed for
calculating the bandwidth needed for running the application. For ensuring that each of the subnet
have sufficient bandwidth for its operation the interface is needed to be divided and a proper
cabling plan should be followed to interconnect the network devices.
3.4 Application requirement
The solution design would require to run different web development tools and software for
designing the interface. A standard antivirus software should be installed in each of the host
connected in the network for eliminating the risk of spyware, malware and other viruses that can
affect the performance of the network.
3.5 Remote access requirement
Configuration of the server with RADUIS protocol helps in enabling the user to gain access of
the network from remote geographical location. The users are needed to access the internal
network of the organization such that they can improve their productivity and help the organisation
to gain competitive advantage in the marketplace.

3.6 Quality of service requirement
The switches installed in the network is needed to be configured with MPLS for directing the
data from one node to another based on the shortest path label and the long network address are
avoided since it have complex lookups in the routing table. It helps in maintaining quality of service
and speeds up the traffic flow in the network.
3.7 VoIP Service Requirement
A reliable internet connection is needed for the configuration of the network with VoIP
service and the network should be free from latency, jitter, packet loss and burstiness. This delay in
the network can cause echo and delay in the conversation. QoS should be maintained for the
network because 1% packet loss can significantly degrade the VOIP.
4. Logical Design
4.1 Security:
The network is needed to be secured from the external agents and a DMZ zone should be configured
for installing the core network device in this zone and restricting the access of the device to the
users to increase the security. A firewall should be deployed in the network for the management of
incoming and outgoing data packets and enabling access control of the user. A VPN server can be
used for establishing a secure connection with the remote branch and eliminating the risk of man in
the middle attack.
4.2 Wireless Networks:
Separate wireless access point should be configured for each of the department and it should be
installed in an open space such that the coverage area of the wireless signal is not affected by
different obstruction. The access point is also needed to be secured with proper encryption
algorithm for the improvement of the security of the network.
4.3 Virtual LANs:
A virtual LAN should be created for each of the department such that less number of packet is
broadcasted and there is no congestion in the network. Configuration of then network with VLAN
helps in reducing the complexity of management and enforcing the security policy for the different
department following the business rules of the organization.
The switches installed in the network is needed to be configured with MPLS for directing the
data from one node to another based on the shortest path label and the long network address are
avoided since it have complex lookups in the routing table. It helps in maintaining quality of service
and speeds up the traffic flow in the network.
3.7 VoIP Service Requirement
A reliable internet connection is needed for the configuration of the network with VoIP
service and the network should be free from latency, jitter, packet loss and burstiness. This delay in
the network can cause echo and delay in the conversation. QoS should be maintained for the
network because 1% packet loss can significantly degrade the VOIP.
4. Logical Design
4.1 Security:
The network is needed to be secured from the external agents and a DMZ zone should be configured
for installing the core network device in this zone and restricting the access of the device to the
users to increase the security. A firewall should be deployed in the network for the management of
incoming and outgoing data packets and enabling access control of the user. A VPN server can be
used for establishing a secure connection with the remote branch and eliminating the risk of man in
the middle attack.
4.2 Wireless Networks:
Separate wireless access point should be configured for each of the department and it should be
installed in an open space such that the coverage area of the wireless signal is not affected by
different obstruction. The access point is also needed to be secured with proper encryption
algorithm for the improvement of the security of the network.
4.3 Virtual LANs:
A virtual LAN should be created for each of the department such that less number of packet is
broadcasted and there is no congestion in the network. Configuration of then network with VLAN
helps in reducing the complexity of management and enforcing the security policy for the different
department following the business rules of the organization.
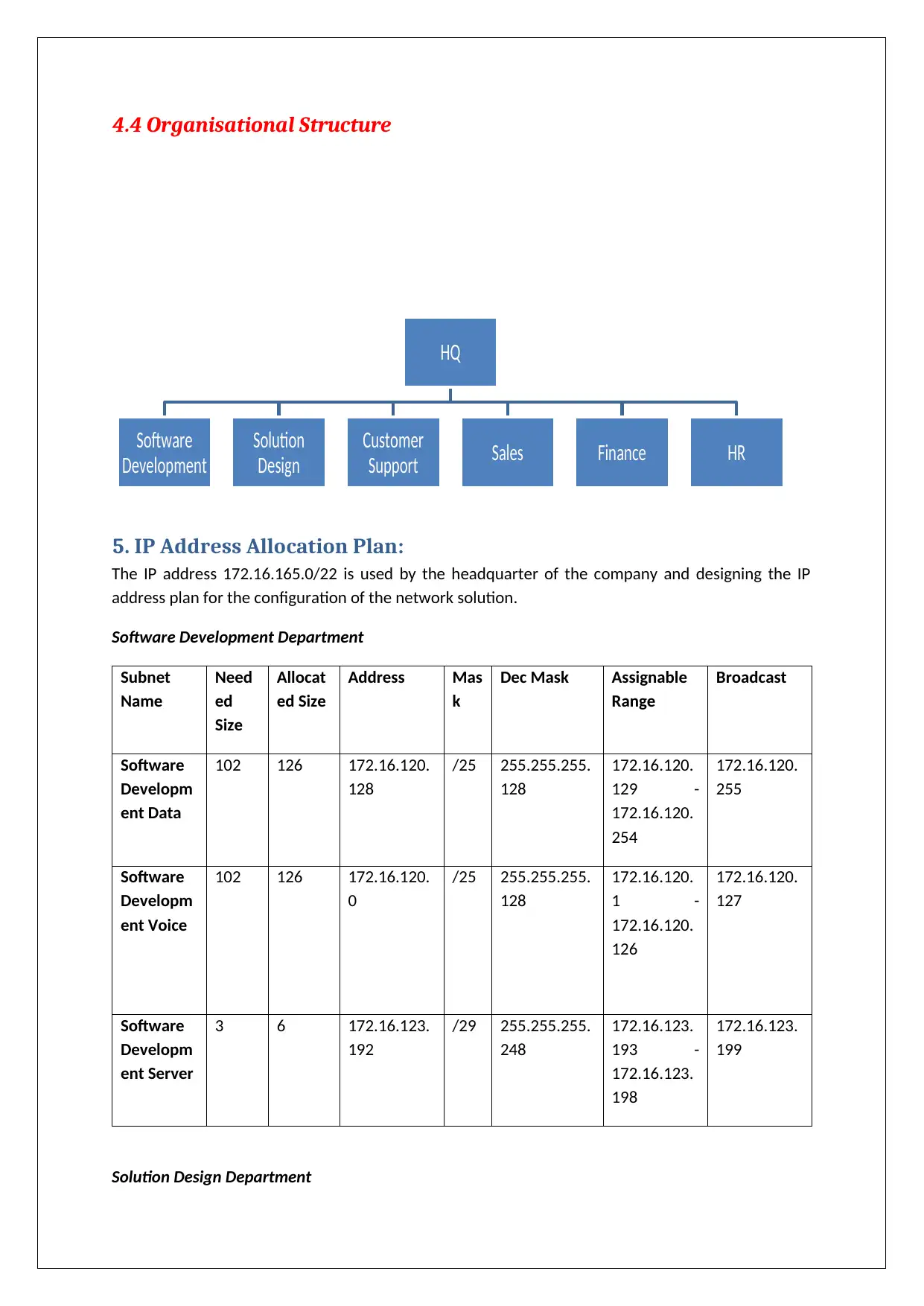
4.4 Organisational Structure
5. IP Address Allocation Plan:
The IP address 172.16.165.0/22 is used by the headquarter of the company and designing the IP
address plan for the configuration of the network solution.
Software Development Department
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Software
Developm
ent Data
102 126 172.16.120.
128
/25 255.255.255.
128
172.16.120.
129 -
172.16.120.
254
172.16.120.
255
Software
Developm
ent Voice
102 126 172.16.120.
0
/25 255.255.255.
128
172.16.120.
1 -
172.16.120.
126
172.16.120.
127
Software
Developm
ent Server
3 6 172.16.123.
192
/29 255.255.255.
248
172.16.123.
193 -
172.16.123.
198
172.16.123.
199
Solution Design Department
HQ
Software
Development
Solution
Design
Customer
Support Sales Finance HR
5. IP Address Allocation Plan:
The IP address 172.16.165.0/22 is used by the headquarter of the company and designing the IP
address plan for the configuration of the network solution.
Software Development Department
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Software
Developm
ent Data
102 126 172.16.120.
128
/25 255.255.255.
128
172.16.120.
129 -
172.16.120.
254
172.16.120.
255
Software
Developm
ent Voice
102 126 172.16.120.
0
/25 255.255.255.
128
172.16.120.
1 -
172.16.120.
126
172.16.120.
127
Software
Developm
ent Server
3 6 172.16.123.
192
/29 255.255.255.
248
172.16.123.
193 -
172.16.123.
198
172.16.123.
199
Solution Design Department
HQ
Software
Development
Solution
Design
Customer
Support Sales Finance HR
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Subnet
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Solutio
n
Design
Data
92 126 172.16.121.1
28
/25 255.255.255.1
28
172.16.121.1
29 -
172.16.121.2
54
172.16.121.2
55
Solutio
n
Design
Voice
92 126 172.16.121.0 /25 255.255.255.1
28
172.16.121.1
-
172.16.121.1
26
172.16.121.1
27
Solutio
n
Design
Server
2 2 172.16.123.2
00
/30 255.255.255.2
52
172.16.123.2
01 -
172.16.123.2
02
172.16.123.2
03
Customer Support
Subnet
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Custom
er
Support
Data
62 62 172.16.122.6
4
/26 255.255.255.
192
172.16.122.6
5 -
172.16.122.1
26
172.16.122.1
27
Custom
er
Support
Voice
62 62 172.16.122.0 /26 255.255.255.
192
172.16.122.1
-
172.16.122.6
2
172.16.122.6
3
Custom
er
Support
Server
1 2 172.16.123.2
04
/30 255.255.255.
252
172.16.123.2
05 -
172.16.123.2
06
172.16.123.2
07
Sales Department
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Solutio
n
Design
Data
92 126 172.16.121.1
28
/25 255.255.255.1
28
172.16.121.1
29 -
172.16.121.2
54
172.16.121.2
55
Solutio
n
Design
Voice
92 126 172.16.121.0 /25 255.255.255.1
28
172.16.121.1
-
172.16.121.1
26
172.16.121.1
27
Solutio
n
Design
Server
2 2 172.16.123.2
00
/30 255.255.255.2
52
172.16.123.2
01 -
172.16.123.2
02
172.16.123.2
03
Customer Support
Subnet
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Custom
er
Support
Data
62 62 172.16.122.6
4
/26 255.255.255.
192
172.16.122.6
5 -
172.16.122.1
26
172.16.122.1
27
Custom
er
Support
Voice
62 62 172.16.122.0 /26 255.255.255.
192
172.16.122.1
-
172.16.122.6
2
172.16.122.6
3
Custom
er
Support
Server
1 2 172.16.123.2
04
/30 255.255.255.
252
172.16.123.2
05 -
172.16.123.2
06
172.16.123.2
07
Sales Department
Subn
et
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Sales
Data
52 62 172.16.122.1
92
/26 255.255.255.1
92
172.16.122.1
93 -
172.16.122.2
54
172.16.122.2
55
Sales
Voice
52 62 172.16.122.1
28
/26 255.255.255.1
92
172.16.122.1
29 -
172.16.122.1
90
172.16.122.1
91
Sales
Serve
r
1 2 172.16.123.2
16
/30 255.255.255.2
52
172.16.123.2
17 -
172.16.123.2
18
172.16.123.2
19
Finance Department
Subne
t
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Financ
e Data
32 62 172.16.123.6
4
/26 255.255.255.1
92
172.16.123.6
5 -
172.16.123.1
26
172.16.123.1
27
Financ
e
Voice
32 62 172.16.123.0 /26 255.255.255.1
92
172.16.123.1
-
172.16.123.6
2
172.16.123.6
3
Financ
e
Server
1 2 172.16.123.2
08
/30 255.255.255.2
52
172.16.123.2
09 -
172.16.123.2
10
172.16.123.2
11
HR Department
et
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Sales
Data
52 62 172.16.122.1
92
/26 255.255.255.1
92
172.16.122.1
93 -
172.16.122.2
54
172.16.122.2
55
Sales
Voice
52 62 172.16.122.1
28
/26 255.255.255.1
92
172.16.122.1
29 -
172.16.122.1
90
172.16.122.1
91
Sales
Serve
r
1 2 172.16.123.2
16
/30 255.255.255.2
52
172.16.123.2
17 -
172.16.123.2
18
172.16.123.2
19
Finance Department
Subne
t
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Financ
e Data
32 62 172.16.123.6
4
/26 255.255.255.1
92
172.16.123.6
5 -
172.16.123.1
26
172.16.123.1
27
Financ
e
Voice
32 62 172.16.123.0 /26 255.255.255.1
92
172.16.123.1
-
172.16.123.6
2
172.16.123.6
3
Financ
e
Server
1 2 172.16.123.2
08
/30 255.255.255.2
52
172.16.123.2
09 -
172.16.123.2
10
172.16.123.2
11
HR Department
Subnet
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Human
Resour
ce Data
22 30 172.16.123.1
60
/27 255.255.255.
224
172.16.123.1
61 -
172.16.123.1
90
172.16.123.1
91
Human
Resour
ce
Voice
22 30 172.16.123.1
28
/27 255.255.255.
224
172.16.123.1
29 -
172.16.123.1
58
172.16.123.1
59
Human
Resour
ce
Server
1 2 172.16.123.2
12
/30 255.255.255.
252
172.16.123.2
13 -
172.16.123.2
14
172.16.123.2
15
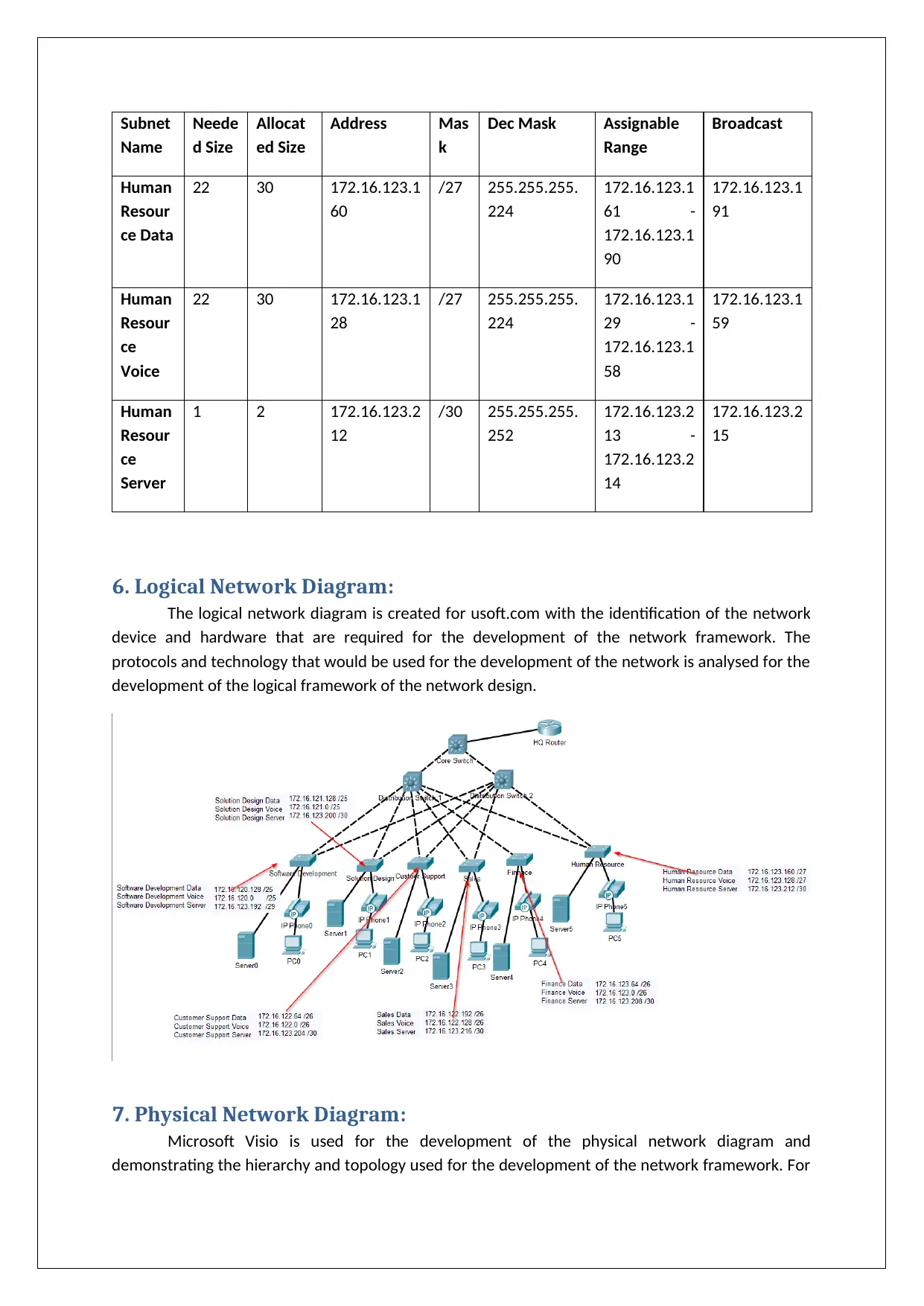
6. Logical Network Diagram:
The logical network diagram is created for usoft.com with the identification of the network
device and hardware that are required for the development of the network framework. The
protocols and technology that would be used for the development of the network is analysed for the
development of the logical framework of the network design.
7. Physical Network Diagram:
Microsoft Visio is used for the development of the physical network diagram and
demonstrating the hierarchy and topology used for the development of the network framework. For
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Human
Resour
ce Data
22 30 172.16.123.1
60
/27 255.255.255.
224
172.16.123.1
61 -
172.16.123.1
90
172.16.123.1
91
Human
Resour
ce
Voice
22 30 172.16.123.1
28
/27 255.255.255.
224
172.16.123.1
29 -
172.16.123.1
58
172.16.123.1
59
Human
Resour
ce
Server
1 2 172.16.123.2
12
/30 255.255.255.
252
172.16.123.2
13 -
172.16.123.2
14
172.16.123.2
15
6. Logical Network Diagram:
The logical network diagram is created for usoft.com with the identification of the network
device and hardware that are required for the development of the network framework. The
protocols and technology that would be used for the development of the network is analysed for the
development of the logical framework of the network design.
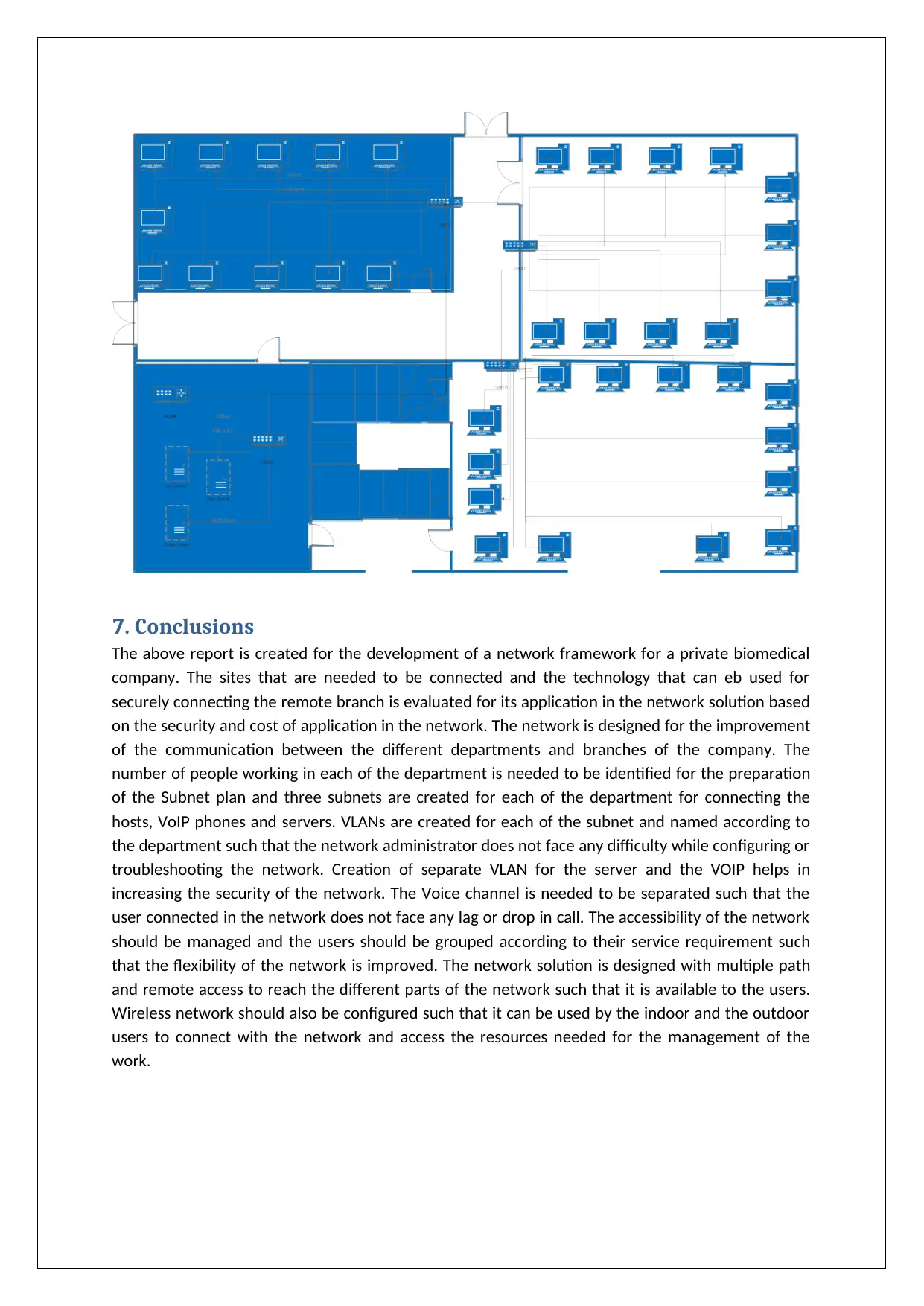
7. Physical Network Diagram:
Microsoft Visio is used for the development of the physical network diagram and
demonstrating the hierarchy and topology used for the development of the network framework. For
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

the development of the physical network design the current floor plan and organizational structure
is evaluated with the business and technical needs of the company. Separate switches are used for
each of the department and since the solution design department would be located in two of the
floors two switches are used for solution design. Three layer hierarchical model is used for the
development of the network framework and the devices are grouped into core, access and
distribution device for increasing the redundancy, scalability and availability of then network. The
network designed would support the future growth of the organisation and reduce the management
cost needed for maintaining the network device. The core device have router and firewall that are
used for the management of data traffic in the network and a DMZ zone is created for securing the
accessibility of the server for the internal and external users associated with the company.
Diagram of each of the floor
is evaluated with the business and technical needs of the company. Separate switches are used for
each of the department and since the solution design department would be located in two of the
floors two switches are used for solution design. Three layer hierarchical model is used for the
development of the network framework and the devices are grouped into core, access and
distribution device for increasing the redundancy, scalability and availability of then network. The
network designed would support the future growth of the organisation and reduce the management
cost needed for maintaining the network device. The core device have router and firewall that are
used for the management of data traffic in the network and a DMZ zone is created for securing the
accessibility of the server for the internal and external users associated with the company.
Diagram of each of the floor
7. Conclusions
The above report is created for the development of a network framework for a private biomedical
company. The sites that are needed to be connected and the technology that can eb used for
securely connecting the remote branch is evaluated for its application in the network solution based
on the security and cost of application in the network. The network is designed for the improvement
of the communication between the different departments and branches of the company. The
number of people working in each of the department is needed to be identified for the preparation
of the Subnet plan and three subnets are created for each of the department for connecting the
hosts, VoIP phones and servers. VLANs are created for each of the subnet and named according to
the department such that the network administrator does not face any difficulty while configuring or
troubleshooting the network. Creation of separate VLAN for the server and the VOIP helps in
increasing the security of the network. The Voice channel is needed to be separated such that the
user connected in the network does not face any lag or drop in call. The accessibility of the network
should be managed and the users should be grouped according to their service requirement such
that the flexibility of the network is improved. The network solution is designed with multiple path
and remote access to reach the different parts of the network such that it is available to the users.
Wireless network should also be configured such that it can be used by the indoor and the outdoor
users to connect with the network and access the resources needed for the management of the
work.
The above report is created for the development of a network framework for a private biomedical
company. The sites that are needed to be connected and the technology that can eb used for
securely connecting the remote branch is evaluated for its application in the network solution based
on the security and cost of application in the network. The network is designed for the improvement
of the communication between the different departments and branches of the company. The
number of people working in each of the department is needed to be identified for the preparation
of the Subnet plan and three subnets are created for each of the department for connecting the
hosts, VoIP phones and servers. VLANs are created for each of the subnet and named according to
the department such that the network administrator does not face any difficulty while configuring or
troubleshooting the network. Creation of separate VLAN for the server and the VOIP helps in
increasing the security of the network. The Voice channel is needed to be separated such that the
user connected in the network does not face any lag or drop in call. The accessibility of the network
should be managed and the users should be grouped according to their service requirement such
that the flexibility of the network is improved. The network solution is designed with multiple path
and remote access to reach the different parts of the network such that it is available to the users.
Wireless network should also be configured such that it can be used by the indoor and the outdoor
users to connect with the network and access the resources needed for the management of the
work.

List of References
Cunha, F., Villas, L., Boukerche, A., Maia, G., Viana, A., Mini, R.A. and Loureiro, A.A., 2016. Data
communication in VANETs: Protocols, applications and challenges. Ad Hoc Networks, 44, pp.90-103.
Hail, M.A., Amadeo, M., Molinaro, A. and Fischer, S., 2015, April. Caching in named data networking
for the wireless internet of things. In Recent Advances in Internet of Things (RIoT), 2015 International
Conference on (pp. 1-6). IEEE.
Li, Z., Chen, Y., Shi, H. and Liu, K., 2016. NDN-GSM-R: a novel high-speed railway communication
system via named data networking. EURASIP Journal on Wireless Communications and
Networking, 2016(1), p.48.
Lu, X., Niyato, D., Wang, P., Kim, D.I. and Han, Z., 2015. Wireless charger networking for mobile
devices: Fundamentals, standards, and applications. IEEE Wireless Communications, 22(2), pp.126-
135.
Lu, Z., Cao, G. and La Porta, T., 2016, March. Networking smartphones for disaster recovery.
In Pervasive Computing and Communications (PerCom), 2016 IEEE International Conference on (pp.
1-9). IEEE.
Pathak, P.H., Feng, X., Hu, P. and Mohapatra, P., 2015. Visible light communication, networking, and
sensing: A survey, potential and challenges. IEEE communications surveys & tutorials, 17(4), pp.2047-
2077.
Perez, G.M., Mishra, K.K., Tiwari, S. and Trivedi, M.C. eds., 2018. Networking Communication and
Data Knowledge Engineering. Springer Singapore.
Puiu, D., Barnaghi, P., Tönjes, R., Kümper, D., Ali, M.I., Mileo, A., Parreira, J.X., Fischer, M., Kolozali,
S., Farajidavar, N. and Gao, F., 2016. Citypulse: Large scale data analytics framework for smart
cities. IEEE Access, 4, pp.1086-1108.
Puthal, D., Nepal, S., Ranjan, R. and Chen, J., 2016. Threats to networking cloud and edge
datacenters in the internet of things. IEEE Cloud Computing, 3(3), pp.64-71.
Saxena, D., Raychoudhury, V., Suri, N., Becker, C. and Cao, J., 2016. Named data networking: a
survey. Computer Science Review, 19, pp.15-55.
Shang, W., Afanasyev, A., Li, Y., Burke, J. and Zhang, L., 2017, September. Device-to-device
communication with named data networking. In Proceedings of the 4th ACM Conference on
Information-Centric Networking (pp. 184-185). ACM.
Shang, W., Bannis, A., Liang, T., Wang, Z., Yu, Y., Afanasyev, A., Thompson, J., Burke, J., Zhang, B. and
Zhang, L., 2016, April. Named data networking of things. In Internet-of-Things Design and
Implementation (IoTDI), 2016 IEEE First International Conference on (pp. 117-128). IEEE.
Shang, W., Yu, Y., Droms, R. and Zhang, L., 2016. Challenges in IoT networking via TCP/IP
architecture. Technical Report NDN-0038. NDN Project.
Cunha, F., Villas, L., Boukerche, A., Maia, G., Viana, A., Mini, R.A. and Loureiro, A.A., 2016. Data
communication in VANETs: Protocols, applications and challenges. Ad Hoc Networks, 44, pp.90-103.
Hail, M.A., Amadeo, M., Molinaro, A. and Fischer, S., 2015, April. Caching in named data networking
for the wireless internet of things. In Recent Advances in Internet of Things (RIoT), 2015 International
Conference on (pp. 1-6). IEEE.
Li, Z., Chen, Y., Shi, H. and Liu, K., 2016. NDN-GSM-R: a novel high-speed railway communication
system via named data networking. EURASIP Journal on Wireless Communications and
Networking, 2016(1), p.48.
Lu, X., Niyato, D., Wang, P., Kim, D.I. and Han, Z., 2015. Wireless charger networking for mobile
devices: Fundamentals, standards, and applications. IEEE Wireless Communications, 22(2), pp.126-
135.
Lu, Z., Cao, G. and La Porta, T., 2016, March. Networking smartphones for disaster recovery.
In Pervasive Computing and Communications (PerCom), 2016 IEEE International Conference on (pp.
1-9). IEEE.
Pathak, P.H., Feng, X., Hu, P. and Mohapatra, P., 2015. Visible light communication, networking, and
sensing: A survey, potential and challenges. IEEE communications surveys & tutorials, 17(4), pp.2047-
2077.
Perez, G.M., Mishra, K.K., Tiwari, S. and Trivedi, M.C. eds., 2018. Networking Communication and
Data Knowledge Engineering. Springer Singapore.
Puiu, D., Barnaghi, P., Tönjes, R., Kümper, D., Ali, M.I., Mileo, A., Parreira, J.X., Fischer, M., Kolozali,
S., Farajidavar, N. and Gao, F., 2016. Citypulse: Large scale data analytics framework for smart
cities. IEEE Access, 4, pp.1086-1108.
Puthal, D., Nepal, S., Ranjan, R. and Chen, J., 2016. Threats to networking cloud and edge
datacenters in the internet of things. IEEE Cloud Computing, 3(3), pp.64-71.
Saxena, D., Raychoudhury, V., Suri, N., Becker, C. and Cao, J., 2016. Named data networking: a
survey. Computer Science Review, 19, pp.15-55.
Shang, W., Afanasyev, A., Li, Y., Burke, J. and Zhang, L., 2017, September. Device-to-device
communication with named data networking. In Proceedings of the 4th ACM Conference on
Information-Centric Networking (pp. 184-185). ACM.
Shang, W., Bannis, A., Liang, T., Wang, Z., Yu, Y., Afanasyev, A., Thompson, J., Burke, J., Zhang, B. and
Zhang, L., 2016, April. Named data networking of things. In Internet-of-Things Design and
Implementation (IoTDI), 2016 IEEE First International Conference on (pp. 117-128). IEEE.
Shang, W., Yu, Y., Droms, R. and Zhang, L., 2016. Challenges in IoT networking via TCP/IP
architecture. Technical Report NDN-0038. NDN Project.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Wang, W., Chen, Y., Zhang, Q. and Jiang, T., 2016. A software-defined wireless networking enabled
spectrum management architecture. IEEE Communications Magazine, 54(1), pp.33-39.
Widmer, J., 2015. Efficient Networking in Millimeter Wave Bands.
Zhang, Z., Zhang, H., Newberry, E., Mastorakis, S., Li, Y., Afanasyev, A. and Zhang, L., 2018. Security
support in named data networking. Technical Report. Available online: https://named-data. net/wp-
content/uploads/2018/03/ndn-0057-1-ndn-security. pdf (accessed on 18 March 2018).
spectrum management architecture. IEEE Communications Magazine, 54(1), pp.33-39.
Widmer, J., 2015. Efficient Networking in Millimeter Wave Bands.
Zhang, Z., Zhang, H., Newberry, E., Mastorakis, S., Li, Y., Afanasyev, A. and Zhang, L., 2018. Security
support in named data networking. Technical Report. Available online: https://named-data. net/wp-
content/uploads/2018/03/ndn-0057-1-ndn-security. pdf (accessed on 18 March 2018).
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





