Developments in Mobile Device Evidence and Investigation
VerifiedAdded on 2023/03/21
|16
|3343
|98
AI Summary
This document discusses the developments in mobile device evidence and investigation methods. It covers logical extraction, file system extraction, and physical extraction. The role of proportionality in selecting evidence extraction methods is also explored. The document provides an overview of the data collected from mobile devices and the Windows mobile device forensic process model. Subject: Mobile Device Forensics, Course Code: N/A, Course Name: N/A, College/University: N/A
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Developments in mobile device evidence and investigation
Student’s Name:
Institution Affiliation:
Student’s Name:
Institution Affiliation:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1. Executive summary ……………………………………………………………………………. 2
2. Introduction ……………………………………………………………………………………. 2
3. Logical extraction………………………………………………………………………………. 2
4. File system extraction …………………………………………………………………………. 3
5. Physical extraction …………………………………………………………………………….. 3
6. Data collected ………………………………………………………………………………….. 4
7. Role of proportionality ………………………………………………………………………… 6
8. Windows mobile device forensic process model……………………………………………… 7
9. Conclusion …………………………………………………………………………………….. 11
10. Reference …………………………………………………………………………………… 12
11. Appendix …………………………………………………………………………………….. 13
2. Introduction ……………………………………………………………………………………. 2
3. Logical extraction………………………………………………………………………………. 2
4. File system extraction …………………………………………………………………………. 3
5. Physical extraction …………………………………………………………………………….. 3
6. Data collected ………………………………………………………………………………….. 4
7. Role of proportionality ………………………………………………………………………… 6
8. Windows mobile device forensic process model……………………………………………… 7
9. Conclusion …………………………………………………………………………………….. 11
10. Reference …………………………………………………………………………………… 12
11. Appendix …………………………………………………………………………………….. 13

Page 1
Executive summary
The scientific instruments utilize these API's to speak with the cell phone's working framework and
solicitation the information from the framework(Daryabar, Dehghantanha, Eterovic-Soric, & Choo,
2016). This procedure takes into account the procurement of the greater part of the live information
on the gadget, much like that of a live focused on gathering of PC(Quick, Choo, 2017). A physical
extraction from a cell phone has a similar essential idea as the physical scientific imaging of a PC
hard drive. A physical extraction plays out an a tiny bit at a time duplicate of the whole substance of
the glimmer memory of a cell phone. This extraction takes into account the accumulation of every
live datum and furthermore information that has been erased or is covered up(Teing, Dehghantanha,
Choo, & Yang, 2017).
Introduction
Advanced gadgets and media ought not be caught in light of the fact that they are there. The
individual responsible for the inquiry must have sensible grounds to evacuate property and there
must be legitimate reasons for doing as such. The hunt arrangements of PACE Legislation Codes of
Practice similarly apply to advanced gadgets and media in England, Wales and Northern Ireland. In
Scotland, officers ought to guarantee they are acting inside the terms of the court order. Due respect
ought to likewise be given to the utilization of the European Convention of Human
Rights(Saferstein, 2015).
Logical extraction
The quickest and most upheld extraction technique, yet additionally the most constrained, is an
intelligent extraction. In an intelligent extraction, the measurable apparatuses speak with the
working arrangement of the cell phone utilizing an API (Application Programming Interface),
which determines how programming parts collaborate.
Strengths
Executive summary
The scientific instruments utilize these API's to speak with the cell phone's working framework and
solicitation the information from the framework(Daryabar, Dehghantanha, Eterovic-Soric, & Choo,
2016). This procedure takes into account the procurement of the greater part of the live information
on the gadget, much like that of a live focused on gathering of PC(Quick, Choo, 2017). A physical
extraction from a cell phone has a similar essential idea as the physical scientific imaging of a PC
hard drive. A physical extraction plays out an a tiny bit at a time duplicate of the whole substance of
the glimmer memory of a cell phone. This extraction takes into account the accumulation of every
live datum and furthermore information that has been erased or is covered up(Teing, Dehghantanha,
Choo, & Yang, 2017).
Introduction
Advanced gadgets and media ought not be caught in light of the fact that they are there. The
individual responsible for the inquiry must have sensible grounds to evacuate property and there
must be legitimate reasons for doing as such. The hunt arrangements of PACE Legislation Codes of
Practice similarly apply to advanced gadgets and media in England, Wales and Northern Ireland. In
Scotland, officers ought to guarantee they are acting inside the terms of the court order. Due respect
ought to likewise be given to the utilization of the European Convention of Human
Rights(Saferstein, 2015).
Logical extraction
The quickest and most upheld extraction technique, yet additionally the most constrained, is an
intelligent extraction. In an intelligent extraction, the measurable apparatuses speak with the
working arrangement of the cell phone utilizing an API (Application Programming Interface),
which determines how programming parts collaborate.
Strengths

Page 2
Utilizing a consistent strategy enables one to acquire information in an intelligible structure
right away.
Weaknesses
The measure of gained information is much lower. This is on the grounds that the API given
by the telephone were not produced for scientific reason but rather to work the telephone as
a modem, just as to synchronize information with work area PIM(Lillis, Becker, O'Sullivan, &
Scanlon, 2016).
File system extraction
The next step up in extraction capacities is a filesystem extraction. The essential differentiator
between consistent extractions and filesystem extractions is the capacity for the legal instruments to
get to the documents on the cell phone's inward memory legitimately as opposed to imparting
through API's for each kind of information. This immediate access enables the measurable
instruments to remove all records present in the inward memory including database documents,
framework documents and logs(Kebande, Ray, 2016, August).
Strengths
Less complex than physical acquisition
Through this technique, it is conceivable to recuperate certain erased data since some
working frameworks, for example, Android and iOS utilize a structure that utilizes SQLite
databases to store a significant part of the data
Weaknesses
It has limit on the number of information to be gathered
Physical extraction
The most broad however least bolstered extraction strategy is the physical extraction.
Utilizing a consistent strategy enables one to acquire information in an intelligible structure
right away.
Weaknesses
The measure of gained information is much lower. This is on the grounds that the API given
by the telephone were not produced for scientific reason but rather to work the telephone as
a modem, just as to synchronize information with work area PIM(Lillis, Becker, O'Sullivan, &
Scanlon, 2016).
File system extraction
The next step up in extraction capacities is a filesystem extraction. The essential differentiator
between consistent extractions and filesystem extractions is the capacity for the legal instruments to
get to the documents on the cell phone's inward memory legitimately as opposed to imparting
through API's for each kind of information. This immediate access enables the measurable
instruments to remove all records present in the inward memory including database documents,
framework documents and logs(Kebande, Ray, 2016, August).
Strengths
Less complex than physical acquisition
Through this technique, it is conceivable to recuperate certain erased data since some
working frameworks, for example, Android and iOS utilize a structure that utilizes SQLite
databases to store a significant part of the data
Weaknesses
It has limit on the number of information to be gathered
Physical extraction
The most broad however least bolstered extraction strategy is the physical extraction.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Page 3
Physical extraction is least bolstered on the grounds that getting full access to the interior memory
of a cell phone is totally needy upon the working framework and safety efforts utilized by the maker
like Apple and Samsung.
Strengths
The physical extraction enables one to acquire the substance of the whole telephone memory
in its present condition(Martini, Do, & Choo, 2015).
Weaknesses
It is time consuming and requires unpredictable and costly hardware. Therefore one gets a
"crude" picture, which, much of the time, is scrambled. Regardless of whether one is
sufficiently fortunate to decode a picture (no one has had the option to do this with
BlackBerry, f.ex.), further examination can be made by methods for exceptional modern
programming devices as it were(Hitchcock, Le-Khac, & Scanlon, 2016).
Data collected
Call Detail Records (CDRs): Service suppliers as often as possible use CDRs to improve organize
execution. Be that as it may, they can give helpful data to agents, also. CDRs can appear:
Call began and finished date/time
The ending and beginning towers
Regardless of whether the call was active or approaching
Call time length
Global Positioning System (GPS): GPS information is a great wellspring of observational proof.
In the event that the presume has a functioning cell phone at the wrongdoing scene,
Physical extraction is least bolstered on the grounds that getting full access to the interior memory
of a cell phone is totally needy upon the working framework and safety efforts utilized by the maker
like Apple and Samsung.
Strengths
The physical extraction enables one to acquire the substance of the whole telephone memory
in its present condition(Martini, Do, & Choo, 2015).
Weaknesses
It is time consuming and requires unpredictable and costly hardware. Therefore one gets a
"crude" picture, which, much of the time, is scrambled. Regardless of whether one is
sufficiently fortunate to decode a picture (no one has had the option to do this with
BlackBerry, f.ex.), further examination can be made by methods for exceptional modern
programming devices as it were(Hitchcock, Le-Khac, & Scanlon, 2016).
Data collected
Call Detail Records (CDRs): Service suppliers as often as possible use CDRs to improve organize
execution. Be that as it may, they can give helpful data to agents, also. CDRs can appear:
Call began and finished date/time
The ending and beginning towers
Regardless of whether the call was active or approaching
Call time length
Global Positioning System (GPS): GPS information is a great wellspring of observational proof.
In the event that the presume has a functioning cell phone at the wrongdoing scene,

Page 4
GPS can pinpoint his area just as his criminal demonstrations. GPS additionally finds the
developments of the suspect from a wrongdoing scene to the alcove. Besides, it helps in discovering
telephone call logs, pictures, and SMS messages. By and by, a GPS framework incorporates 27
satellites in task.
Application Data: Many applications store and access information the client doesn't know about.
Truth be told, numerous applications look for authorization amid the establishment procedure to get
to these information. For instance, photograph or video altering applications demand consent to get
to media records, camera, and GPS for route. This information can be an essential wellspring of
proof to the court.
SMS: Text informing is a broadly utilized method for correspondence. Instant messages leave
electronic records of exchange that can be exhibited in the court as proof. They incorporate the
applicable data.
Photographs and Videos as Evidence: They can be an enormous wellspring of proof, however
their significance to wrongdoing and confirmation is critical(Underwood, Birdsall, & Kay, 2015).
Role of proportionality in selecting evidence method of extraction for mobile devices
Think about that proof might be put away on the web, or on a network access supplier's
frameworks, and end-client gadgets may just be expected to acquire the subtleties important to
demand this proof from the specialist co-op. Assuming this is the case, it is ideal to catch things in
current use, for example PCs associated with the web.
People in charge of the seizure of advanced gadgets, or for on-scene catch of information, ought to
guarantee:
They have the vital hardware. (Allude to the First Responder's Guide for a point by point
breakdown);
GPS can pinpoint his area just as his criminal demonstrations. GPS additionally finds the
developments of the suspect from a wrongdoing scene to the alcove. Besides, it helps in discovering
telephone call logs, pictures, and SMS messages. By and by, a GPS framework incorporates 27
satellites in task.
Application Data: Many applications store and access information the client doesn't know about.
Truth be told, numerous applications look for authorization amid the establishment procedure to get
to these information. For instance, photograph or video altering applications demand consent to get
to media records, camera, and GPS for route. This information can be an essential wellspring of
proof to the court.
SMS: Text informing is a broadly utilized method for correspondence. Instant messages leave
electronic records of exchange that can be exhibited in the court as proof. They incorporate the
applicable data.
Photographs and Videos as Evidence: They can be an enormous wellspring of proof, however
their significance to wrongdoing and confirmation is critical(Underwood, Birdsall, & Kay, 2015).
Role of proportionality in selecting evidence method of extraction for mobile devices
Think about that proof might be put away on the web, or on a network access supplier's
frameworks, and end-client gadgets may just be expected to acquire the subtleties important to
demand this proof from the specialist co-op. Assuming this is the case, it is ideal to catch things in
current use, for example PCs associated with the web.
People in charge of the seizure of advanced gadgets, or for on-scene catch of information, ought to
guarantee:
They have the vital hardware. (Allude to the First Responder's Guide for a point by point
breakdown);

Page 5
They have thought about potential wellsprings of proof and comprehend what is probably
going to be applicable,
where conceivable(Phonthanukitithaworn, Sellitto, & Fong, 2016).
Where an examination is probably going to include the examination of client made
computerized pictures, thought ought to be given to the subject of seizing of cameras and
different gadgets able to do taking computerized photos(Montag, Błaszkiewicz, Lachmann,
Sariyska, Andone, Trendafilov, & Markowetz, 2015). For instance, in situations where a suspect
is accepted to have taken obscene photos of kids, seizure of gadgets equipped for
taking advanced photographs could be helpful not just for the information they store, yet in
addition to interface these gadgets to recently recognized obscene photos by the examination
of advanced metadata (EXIF information). Where vital, pro exhortation from a power's
Digital Forensic Unit ought to be looked for ahead of time.
Whenever given adequate data about the examination, DFUs will almost certainly prompt on which
things are well on the way to give the proof looked for(Land, Zimmerman, 2015).
They have thought about potential wellsprings of proof and comprehend what is probably
going to be applicable,
where conceivable(Phonthanukitithaworn, Sellitto, & Fong, 2016).
Where an examination is probably going to include the examination of client made
computerized pictures, thought ought to be given to the subject of seizing of cameras and
different gadgets able to do taking computerized photos(Montag, Błaszkiewicz, Lachmann,
Sariyska, Andone, Trendafilov, & Markowetz, 2015). For instance, in situations where a suspect
is accepted to have taken obscene photos of kids, seizure of gadgets equipped for
taking advanced photographs could be helpful not just for the information they store, yet in
addition to interface these gadgets to recently recognized obscene photos by the examination
of advanced metadata (EXIF information). Where vital, pro exhortation from a power's
Digital Forensic Unit ought to be looked for ahead of time.
Whenever given adequate data about the examination, DFUs will almost certainly prompt on which
things are well on the way to give the proof looked for(Land, Zimmerman, 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Page 6
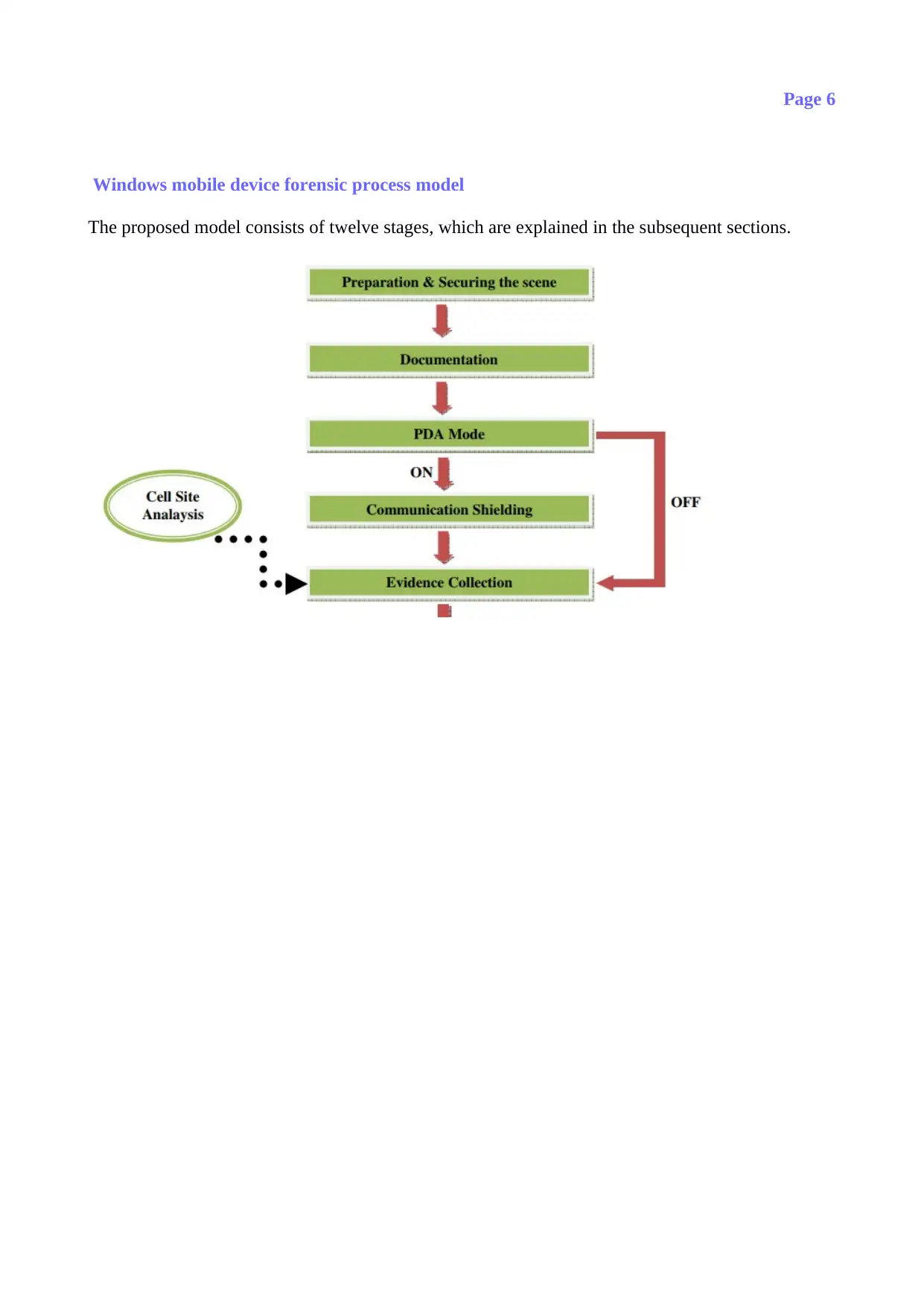
Windows mobile device forensic process model
The proposed model consists of twelve stages, which are explained in the subsequent sections.
Windows mobile device forensic process model
The proposed model consists of twelve stages, which are explained in the subsequent sections.
Page 7
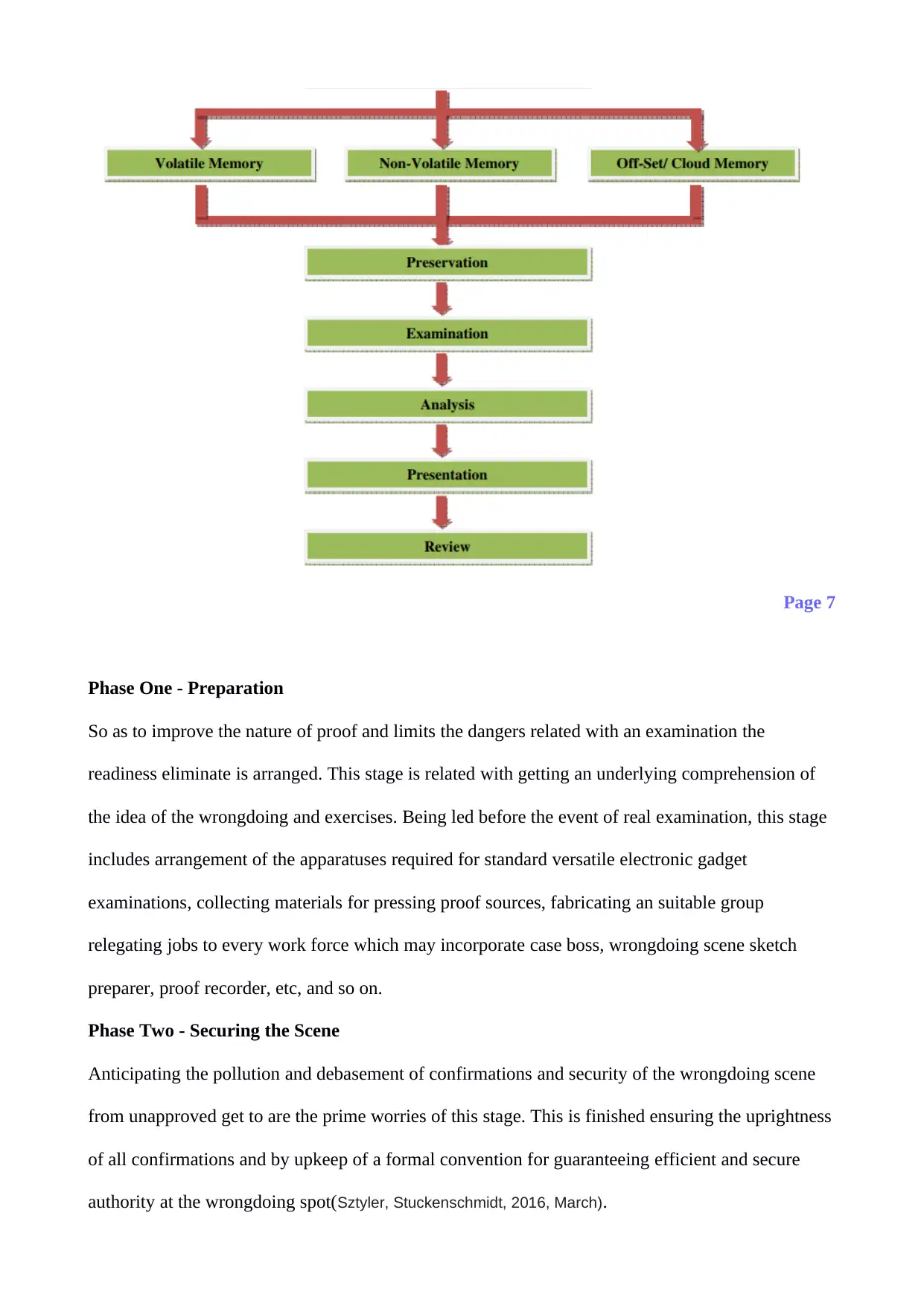
Phase One - Preparation
So as to improve the nature of proof and limits the dangers related with an examination the
readiness eliminate is arranged. This stage is related with getting an underlying comprehension of
the idea of the wrongdoing and exercises. Being led before the event of real examination, this stage
includes arrangement of the apparatuses required for standard versatile electronic gadget
examinations, collecting materials for pressing proof sources, fabricating an suitable group
relegating jobs to every work force which may incorporate case boss, wrongdoing scene sketch
preparer, proof recorder, etc, and so on.
Phase Two - Securing the Scene
Anticipating the pollution and debasement of confirmations and security of the wrongdoing scene
from unapproved get to are the prime worries of this stage. This is finished ensuring the uprightness
of all confirmations and by upkeep of a formal convention for guaranteeing efficient and secure
authority at the wrongdoing spot(Sztyler, Stuckenschmidt, 2016, March).
Phase One - Preparation
So as to improve the nature of proof and limits the dangers related with an examination the
readiness eliminate is arranged. This stage is related with getting an underlying comprehension of
the idea of the wrongdoing and exercises. Being led before the event of real examination, this stage
includes arrangement of the apparatuses required for standard versatile electronic gadget
examinations, collecting materials for pressing proof sources, fabricating an suitable group
relegating jobs to every work force which may incorporate case boss, wrongdoing scene sketch
preparer, proof recorder, etc, and so on.
Phase Two - Securing the Scene
Anticipating the pollution and debasement of confirmations and security of the wrongdoing scene
from unapproved get to are the prime worries of this stage. This is finished ensuring the uprightness
of all confirmations and by upkeep of a formal convention for guaranteeing efficient and secure
authority at the wrongdoing spot(Sztyler, Stuckenschmidt, 2016, March).
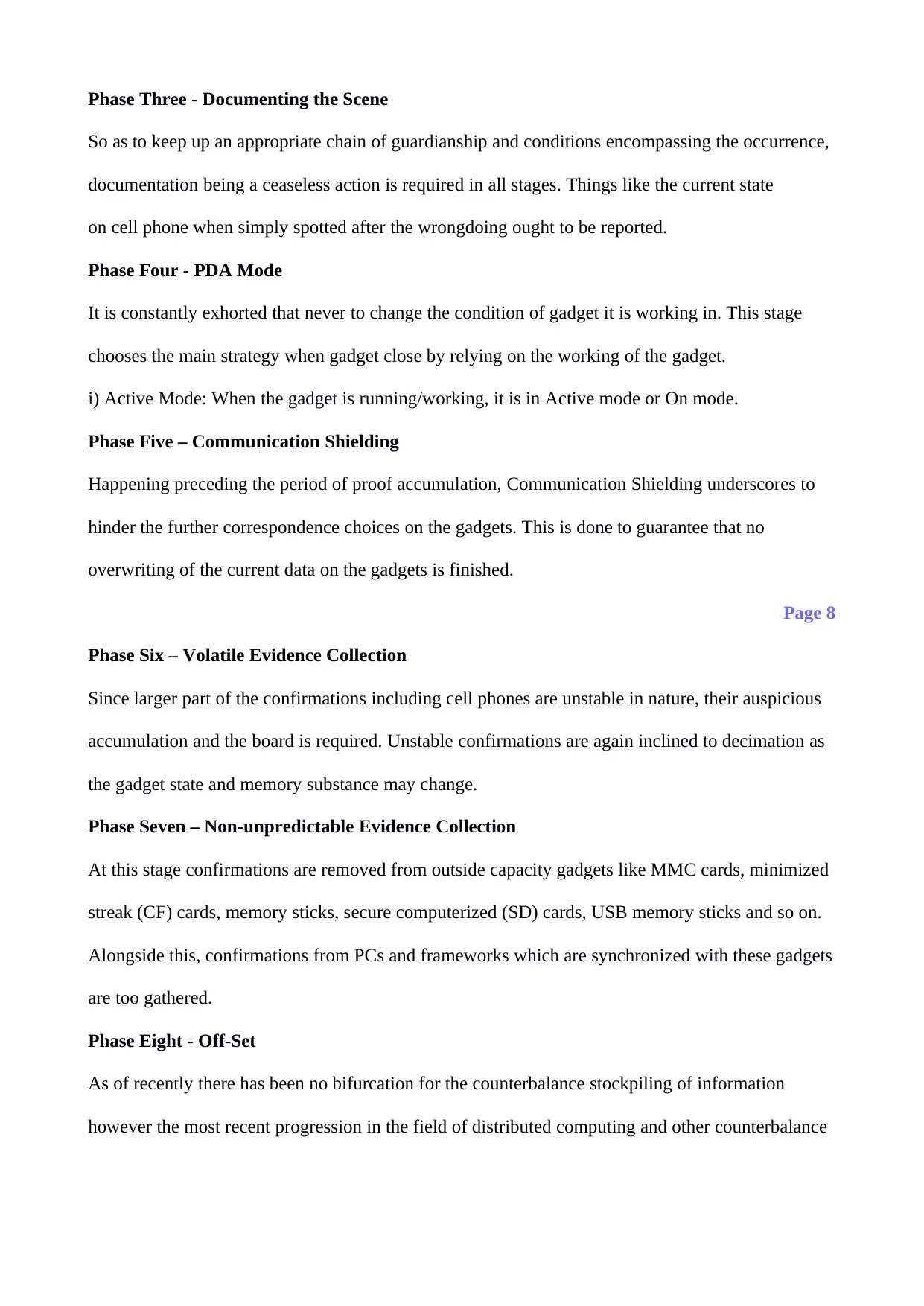
Phase Three - Documenting the Scene
So as to keep up an appropriate chain of guardianship and conditions encompassing the occurrence,
documentation being a ceaseless action is required in all stages. Things like the current state
on cell phone when simply spotted after the wrongdoing ought to be reported.
Phase Four - PDA Mode
It is constantly exhorted that never to change the condition of gadget it is working in. This stage
chooses the main strategy when gadget close by relying on the working of the gadget.
i) Active Mode: When the gadget is running/working, it is in Active mode or On mode.
Phase Five – Communication Shielding
Happening preceding the period of proof accumulation, Communication Shielding underscores to
hinder the further correspondence choices on the gadgets. This is done to guarantee that no
overwriting of the current data on the gadgets is finished.
Page 8
Phase Six – Volatile Evidence Collection
Since larger part of the confirmations including cell phones are unstable in nature, their auspicious
accumulation and the board is required. Unstable confirmations are again inclined to decimation as
the gadget state and memory substance may change.
Phase Seven – Non-unpredictable Evidence Collection
At this stage confirmations are removed from outside capacity gadgets like MMC cards, minimized
streak (CF) cards, memory sticks, secure computerized (SD) cards, USB memory sticks and so on.
Alongside this, confirmations from PCs and frameworks which are synchronized with these gadgets
are too gathered.
Phase Eight - Off-Set
As of recently there has been no bifurcation for the counterbalance stockpiling of information
however the most recent progression in the field of distributed computing and other counterbalance
So as to keep up an appropriate chain of guardianship and conditions encompassing the occurrence,
documentation being a ceaseless action is required in all stages. Things like the current state
on cell phone when simply spotted after the wrongdoing ought to be reported.
Phase Four - PDA Mode
It is constantly exhorted that never to change the condition of gadget it is working in. This stage
chooses the main strategy when gadget close by relying on the working of the gadget.
i) Active Mode: When the gadget is running/working, it is in Active mode or On mode.
Phase Five – Communication Shielding
Happening preceding the period of proof accumulation, Communication Shielding underscores to
hinder the further correspondence choices on the gadgets. This is done to guarantee that no
overwriting of the current data on the gadgets is finished.
Page 8
Phase Six – Volatile Evidence Collection
Since larger part of the confirmations including cell phones are unstable in nature, their auspicious
accumulation and the board is required. Unstable confirmations are again inclined to decimation as
the gadget state and memory substance may change.
Phase Seven – Non-unpredictable Evidence Collection
At this stage confirmations are removed from outside capacity gadgets like MMC cards, minimized
streak (CF) cards, memory sticks, secure computerized (SD) cards, USB memory sticks and so on.
Alongside this, confirmations from PCs and frameworks which are synchronized with these gadgets
are too gathered.
Phase Eight - Off-Set
As of recently there has been no bifurcation for the counterbalance stockpiling of information
however the most recent progression in the field of distributed computing and other counterbalance
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
stockpiling advancements has prompted genuine thought of this stage for the inquiry of potential
proof.
Phase Nine - Cell Site Analysis
Cell site examination is the exploration of having the option to pinpoint a particular position, or
positions where a cell phone was or is. In the event that a call is produced using a cell phone or a
call is gotten from another telephone to the cell phone being referred to, or on the off chance that a
SMS is either sent or gotten, at that point there will be records of this specific occasion.
Phase Ten – Preservation
To guarantee the wellbeing of confirmations accumulated their bundling, transportation and
capacity is conveyed out in this stage. Recognizable proof and their naming are done before
bundling. Plastic sacks cause friction based electricity and subsequently may harm the
confirmations.
Page 9
Phase Eleven – Examination
To determine and deal with the case, basic examination of the information gathered from the
research
Phase Twelve – Analysis
Distinguishing connections between parts of information, and analyzing the data received from
investigation
Phase Thirteen - Presentation
After the entire examination of the outcomes introduction of results to the wide assortment of
gathering of people counting law implementation authorities, specialized specialists, lawful
specialists, corporate administration and so on. is finished(Cahyani, Martini, Choo, & Al‐Azhar, 2017).
Phase Fourteen - Review
proof.
Phase Nine - Cell Site Analysis
Cell site examination is the exploration of having the option to pinpoint a particular position, or
positions where a cell phone was or is. In the event that a call is produced using a cell phone or a
call is gotten from another telephone to the cell phone being referred to, or on the off chance that a
SMS is either sent or gotten, at that point there will be records of this specific occasion.
Phase Ten – Preservation
To guarantee the wellbeing of confirmations accumulated their bundling, transportation and
capacity is conveyed out in this stage. Recognizable proof and their naming are done before
bundling. Plastic sacks cause friction based electricity and subsequently may harm the
confirmations.
Page 9
Phase Eleven – Examination
To determine and deal with the case, basic examination of the information gathered from the
research
Phase Twelve – Analysis
Distinguishing connections between parts of information, and analyzing the data received from
investigation
Phase Thirteen - Presentation
After the entire examination of the outcomes introduction of results to the wide assortment of
gathering of people counting law implementation authorities, specialized specialists, lawful
specialists, corporate administration and so on. is finished(Cahyani, Martini, Choo, & Al‐Azhar, 2017).
Phase Fourteen - Review
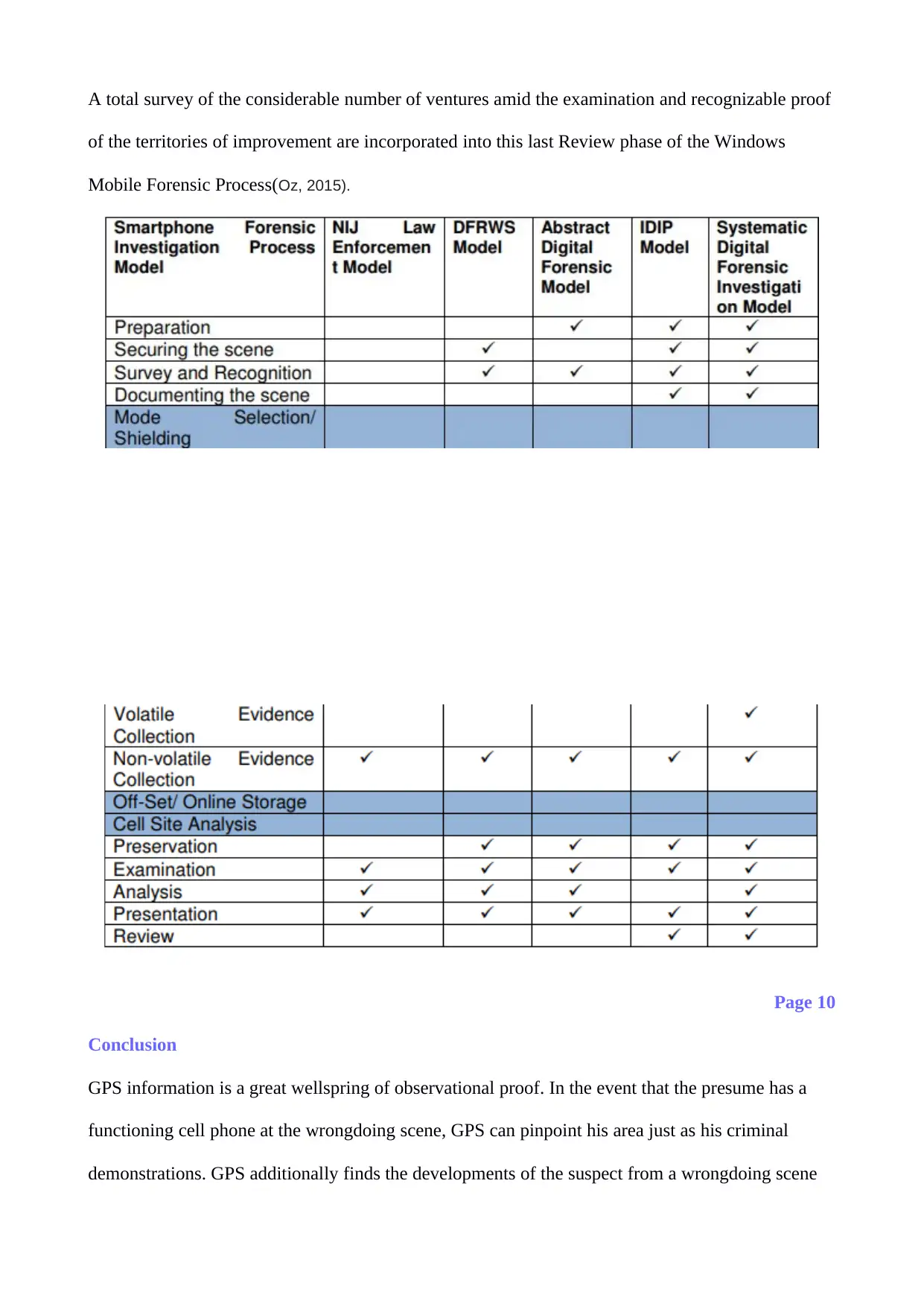
A total survey of the considerable number of ventures amid the examination and recognizable proof
of the territories of improvement are incorporated into this last Review phase of the Windows
Mobile Forensic Process(Oz, 2015).
Page 10
Conclusion
GPS information is a great wellspring of observational proof. In the event that the presume has a
functioning cell phone at the wrongdoing scene, GPS can pinpoint his area just as his criminal
demonstrations. GPS additionally finds the developments of the suspect from a wrongdoing scene
of the territories of improvement are incorporated into this last Review phase of the Windows
Mobile Forensic Process(Oz, 2015).
Page 10
Conclusion
GPS information is a great wellspring of observational proof. In the event that the presume has a
functioning cell phone at the wrongdoing scene, GPS can pinpoint his area just as his criminal
demonstrations. GPS additionally finds the developments of the suspect from a wrongdoing scene

to the alcove. Besides, it helps in discovering telephone call logs, pictures, and SMS messages. By
and by, a GPS framework incorporates 27 satellites in task.
Page 11
Reference
Quick, D., & Choo, K. K. R. (2017). Pervasive social networking forensics: intelligence and evidence from
Daryabar, F., Dehghantanha, A., Eterovic-Soric, B., & Choo, K. K. R. (2016). Forensic investigation of
OneDrive, Box, GoogleDrive and Dropbox applications on Android and iOS devices. Australian Journal of
Forensic Sciences, 48(6), 615-642.
Underwood, B., Birdsall, J., & Kay, E. (2015). The use of a mobile app to motivate evidence-based oral
hygiene behaviour. British dental journal, 219(4), E2.
Lillis, D., Becker, B., O'Sullivan, T., & Scanlon, M. (2016). Current challenges and future research areas for
digital forensic investigation. arXiv preprint arXiv:1604.03850.
Hitchcock, B., Le-Khac, N. A., & Scanlon, M. (2016). Tiered forensic methodology model for Digital Field
Triage by non-digital evidence specialists. Digital investigation, 16, S75-S85.
and by, a GPS framework incorporates 27 satellites in task.
Page 11
Reference
Quick, D., & Choo, K. K. R. (2017). Pervasive social networking forensics: intelligence and evidence from
Daryabar, F., Dehghantanha, A., Eterovic-Soric, B., & Choo, K. K. R. (2016). Forensic investigation of
OneDrive, Box, GoogleDrive and Dropbox applications on Android and iOS devices. Australian Journal of
Forensic Sciences, 48(6), 615-642.
Underwood, B., Birdsall, J., & Kay, E. (2015). The use of a mobile app to motivate evidence-based oral
hygiene behaviour. British dental journal, 219(4), E2.
Lillis, D., Becker, B., O'Sullivan, T., & Scanlon, M. (2016). Current challenges and future research areas for
digital forensic investigation. arXiv preprint arXiv:1604.03850.
Hitchcock, B., Le-Khac, N. A., & Scanlon, M. (2016). Tiered forensic methodology model for Digital Field
Triage by non-digital evidence specialists. Digital investigation, 16, S75-S85.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Martini, B., Do, Q., & Choo, K. K. R. (2015). Conceptual evidence collection and analysis methodology for
Android devices. arXiv preprint arXiv:1506.05527.
Teing, Y. Y., Dehghantanha, A., Choo, K. K. R., & Yang, L. T. (2017). Forensic investigation of P2P cloud
storage services and backbone for IoT networks: BitTorrent Sync as a case study. Computers & Electrical
Engineering, 58, 350-363.
Kebande, V. R., & Ray, I. (2016, August). A generic digital forensic investigation framework for internet of
things (iot). In 2016 IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud) (pp.
356-362). IEEE.
Saferstein, R. (2015). Criminalistics: An introduction to forensic science. Pearson Higher Ed.
Phonthanukitithaworn, C., Sellitto, C., & Fong, M. W. (2016). An investigation of mobile payment (m-
payment) services in Thailand. Asia-Pacific Journal of Business Administration, 8(1), 37-54.
Sztyler, T., & Stuckenschmidt, H. (2016, March). On-body localization of wearable devices: An investigation
of position-aware activity recognition. In 2016 IEEE International Conference on Pervasive Computing and
Communications (PerCom) (pp. 1-9). IEEE.
Land, S. M., & Zimmerman, H. T. (2015). Socio-technical dimensions of an outdoor mobile learning
environment: a three-phase design-based research investigation. Educational Technology Research and
Development, 63(2), 229-255.
Page 12
Montag, C., Błaszkiewicz, K., Lachmann, B., Sariyska, R., Andone, I., Trendafilov, B., & Markowetz, A.
(2015). Recorded behavior as a valuable resource for diagnostics in mobile phone addiction: evidence from
psychoinformatics. Behavioral Sciences, 5(4), 434-442.
Cahyani, N. D. W., Martini, B., Choo, K. K. R., & Al‐Azhar, A. M. N. (2017). Forensic data acquisition from
cloud‐of‐things devices: windows Smartphones as a case study. Concurrency and Computation: Practice
and Experience, 29(14), e3855.
Oz, H. (2015). An Investigation of Preservice English Teachers' Perceptions of Mobile Assisted Language
Learning. English Language Teaching, 8(2), 22-34.
Appendix
Security Testing Test Cases
Android devices. arXiv preprint arXiv:1506.05527.
Teing, Y. Y., Dehghantanha, A., Choo, K. K. R., & Yang, L. T. (2017). Forensic investigation of P2P cloud
storage services and backbone for IoT networks: BitTorrent Sync as a case study. Computers & Electrical
Engineering, 58, 350-363.
Kebande, V. R., & Ray, I. (2016, August). A generic digital forensic investigation framework for internet of
things (iot). In 2016 IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud) (pp.
356-362). IEEE.
Saferstein, R. (2015). Criminalistics: An introduction to forensic science. Pearson Higher Ed.
Phonthanukitithaworn, C., Sellitto, C., & Fong, M. W. (2016). An investigation of mobile payment (m-
payment) services in Thailand. Asia-Pacific Journal of Business Administration, 8(1), 37-54.
Sztyler, T., & Stuckenschmidt, H. (2016, March). On-body localization of wearable devices: An investigation
of position-aware activity recognition. In 2016 IEEE International Conference on Pervasive Computing and
Communications (PerCom) (pp. 1-9). IEEE.
Land, S. M., & Zimmerman, H. T. (2015). Socio-technical dimensions of an outdoor mobile learning
environment: a three-phase design-based research investigation. Educational Technology Research and
Development, 63(2), 229-255.
Page 12
Montag, C., Błaszkiewicz, K., Lachmann, B., Sariyska, R., Andone, I., Trendafilov, B., & Markowetz, A.
(2015). Recorded behavior as a valuable resource for diagnostics in mobile phone addiction: evidence from
psychoinformatics. Behavioral Sciences, 5(4), 434-442.
Cahyani, N. D. W., Martini, B., Choo, K. K. R., & Al‐Azhar, A. M. N. (2017). Forensic data acquisition from
cloud‐of‐things devices: windows Smartphones as a case study. Concurrency and Computation: Practice
and Experience, 29(14), e3855.
Oz, H. (2015). An Investigation of Preservice English Teachers' Perceptions of Mobile Assisted Language
Learning. English Language Teaching, 8(2), 22-34.
Appendix
Security Testing Test Cases

The major goal of security testing is to guarantee that the application's information and systems
administration security necessities are met according to rules. Coming up next are the most critical regions
for checking the security of Mobile applications.
To approve that the application can withstand any savage power assault which is a mechanized
procedure of experimentation used to figure an individual's username, secret phrase or Mastercard
number.
To approve whether an application isn't allowing an aggressor to get to delicate substance or
usefulness without legitimate confirmation.
To approve that the application has a solid secret word assurance framework and it doesn't allow an
aggressor to get, change or recuperate another client's secret word.
To approve that the application does not experience the ill effects of lacking session lapse.
To recognize the dynamic conditions and take measures to forestall any aggressor for getting to
these vulnerabilities.
To keep from SQL infusion related assaults.
To distinguish and recuperate from any unmanaged code situations.
To guarantee whether the testaments are approved, does the application actualize Certificate
Pinning or not.
Page 13
To shield the application and the system from the refusal of administration assaults.
To investigate the information stockpiling and information approval necessities.
To empower the session the executives for averting unapproved clients to get to spontaneous data.
Significant Checklist
Establishment testing (regardless of whether the application can be introduced in a sensible
measure of time and with required standard)
Uninstallation testing (regardless of whether the application can be uninstalled in a sensible measure
of time and with required standard)
System experiments (approval of whether the system is performing under required burden or not,
regardless of whether the system can bolster all the important applications amid the testing
strategies)
administration security necessities are met according to rules. Coming up next are the most critical regions
for checking the security of Mobile applications.
To approve that the application can withstand any savage power assault which is a mechanized
procedure of experimentation used to figure an individual's username, secret phrase or Mastercard
number.
To approve whether an application isn't allowing an aggressor to get to delicate substance or
usefulness without legitimate confirmation.
To approve that the application has a solid secret word assurance framework and it doesn't allow an
aggressor to get, change or recuperate another client's secret word.
To approve that the application does not experience the ill effects of lacking session lapse.
To recognize the dynamic conditions and take measures to forestall any aggressor for getting to
these vulnerabilities.
To keep from SQL infusion related assaults.
To distinguish and recuperate from any unmanaged code situations.
To guarantee whether the testaments are approved, does the application actualize Certificate
Pinning or not.
Page 13
To shield the application and the system from the refusal of administration assaults.
To investigate the information stockpiling and information approval necessities.
To empower the session the executives for averting unapproved clients to get to spontaneous data.
Significant Checklist
Establishment testing (regardless of whether the application can be introduced in a sensible
measure of time and with required standard)
Uninstallation testing (regardless of whether the application can be uninstalled in a sensible measure
of time and with required standard)
System experiments (approval of whether the system is performing under required burden or not,
regardless of whether the system can bolster all the important applications amid the testing
strategies)
Check Unmapped keys
Check application sprinkle screen
Proceeded with keypad section amid hinders and different occasions such as system issues
Techniques which manage leaving the application
Charger impact while an application is running out of sight
Low battery and superior interest
Evacuation of battery while an application is being performed
Utilization of battery by application
Check Application reactions
Page 14
Check application sprinkle screen
Proceeded with keypad section amid hinders and different occasions such as system issues
Techniques which manage leaving the application
Charger impact while an application is running out of sight
Low battery and superior interest
Evacuation of battery while an application is being performed
Utilization of battery by application
Check Application reactions
Page 14
1 out of 16
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.

