Digital Forensics Report: Scrambled Bits, USB Image & Data Security
VerifiedAdded on 2023/03/30
|18
|3209
|347
Report
AI Summary
This report delves into the realm of digital forensics, addressing two primary tasks. The first task involves recovering scrambled bits from a text file using the Winhex tool, detailing the process of converting these bits back to plain text through logical and arithmetic shift operations. The second task presents a digital forensics investigation scenario concerning potential intellectual property theft, employing the Autopsy tool to analyze a USB image file and uncover hidden information. Furthermore, the report explores methods for securing sensitive files, including the use of VeraCrypt for encryption and secure storage, alongside strategies for hiding user information to prevent unauthorized access and data breaches. The report emphasizes the importance of multi-layered security measures to protect against both remote and physical threats to digital data.

Running head: DIGITAL FORENSIC
DIGITAL FORENSIC
Name of the Student
Name of the University
Author Note
DIGITAL FORENSIC
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DIGITAL FORENSIC 1
Abstract:
The purpose of this paper is to discuss the digital forensic. This paper will discuss scrambled
buts, usb image file and will also provide the information bout securing the files.
Abstract:
The purpose of this paper is to discuss the digital forensic. This paper will discuss scrambled
buts, usb image file and will also provide the information bout securing the files.

2DIGITAL FORENSIC
Table of Contents
Task 1:........................................................................................................................................3
Scrambled bit:........................................................................................................................3
Table:..........................................................................................................................................3
Plain text:...................................................................................................................................5
Process:......................................................................................................................................5
Task 2:........................................................................................................................................5
Process:....................................................................................................................................10
Introduction:.............................................................................................................................11
Secure file storage:...................................................................................................................11
VeraCrypt for Windows - Secure File Storage:.......................................................................12
Using file encryption safely:....................................................................................................12
Hiding user information:..........................................................................................................14
Conclusion:..............................................................................................................................15
Table of Contents
Task 1:........................................................................................................................................3
Scrambled bit:........................................................................................................................3
Table:..........................................................................................................................................3
Plain text:...................................................................................................................................5
Process:......................................................................................................................................5
Task 2:........................................................................................................................................5
Process:....................................................................................................................................10
Introduction:.............................................................................................................................11
Secure file storage:...................................................................................................................11
VeraCrypt for Windows - Secure File Storage:.......................................................................12
Using file encryption safely:....................................................................................................12
Hiding user information:..........................................................................................................14
Conclusion:..............................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DIGITAL FORENSIC
Task 1:
Scrambled bit:
3·7¡ºº0¹4º0¶¹·7º·¬ ;0´:¹ 2¹²±±¶:³9º<¶91¹·616°±229º4º749´´2¶4³34:·¼ 70± 2²¹¹´´:0¶8:74:<2…” !
…2¶´¹2±¹ 9²·7»74·4»64²3°º4³²¶60´²3·0¹932³6·²:°¹9°± :9²·´7´±´¶—
9²²2¡9º°±²0 2±·0»:22·41²³·¶79²´ 2¹0;··4°»0¶10¶72· 2·4:37¶ 2± :9·¶¶·¹179²¶´ 9´ 0·4³0´±·9362:°±
´´;·442:¶1¹
´ 2·4º¹³73μ°³412¹μ±²°¶ 3·4μº94¶0²° 3·9274¶62³3·2μ°·2²4¼º4º90± 99²41º²9°²»4¹69¹72±´° 2±
±275·0²90± 9´¢°º4³·³69·2¹9±´±°¹84º4º92·7²·9±22²0·¹: 92¹2²770º9³·4²372´:2¹°±²
´:90 <·» 2·4μ¹7737¹ <²´:70± 90·;·¹87±¹³72²´:494¹²»70³´º77´º—
Table:
33 b7 37 a1 ba ba 30 b9 34 ba 30 b6 10 b9 b7 37
ba b7 ac 90 3b 30 b4 10 3a b9 90 32 b9 b2 b1 b1
b6 3a b3 39 ba 90 3c b6 39 31 b9 b7 36 31 36 b0
b1 10 32 32 90 39 ba 34 ba 10 37 34 90 39 b4 b4
32 b6 34 b3 10 33 34 90 10 3a b7 bc 90 37 30 b1
90 32 b2 b9 b9 b4 b4 3a 30 b6 38 10 3a 10 37 34
90 3a 3c 32 85 06 94 9d 21 85 06 90 32 b6 b4 b9
32 b1 b9 90 10 39 b2 b7 37 bb 37 34 b7 34 bb 36
34 b2 10 33 b0 ba 34 b3 b2 b6 90 36 10 30 b4 b2
33 b7 30 b9 39 33 10 32 b3 10 36 b7 b2 3a b0 b9
39 b0 b1 90 3a 10 39 b2 b7 b4 10 37 b4 b1 b4 b6
97 39 b2 b2 32 a1 10 10 39 ba b0 b1 b2 30 90 32
Task 1:
Scrambled bit:
3·7¡ºº0¹4º0¶¹·7º·¬ ;0´:¹ 2¹²±±¶:³9º<¶91¹·616°±229º4º749´´2¶4³34:·¼ 70± 2²¹¹´´:0¶8:74:<2…” !
…2¶´¹2±¹ 9²·7»74·4»64²3°º4³²¶60´²3·0¹932³6·²:°¹9°± :9²·´7´±´¶—
9²²2¡9º°±²0 2±·0»:22·41²³·¶79²´ 2¹0;··4°»0¶10¶72· 2·4:37¶ 2± :9·¶¶·¹179²¶´ 9´ 0·4³0´±·9362:°±
´´;·442:¶1¹
´ 2·4º¹³73μ°³412¹μ±²°¶ 3·4μº94¶0²° 3·9274¶62³3·2μ°·2²4¼º4º90± 99²41º²9°²»4¹69¹72±´° 2±
±275·0²90± 9´¢°º4³·³69·2¹9±´±°¹84º4º92·7²·9±22²0·¹: 92¹2²770º9³·4²372´:2¹°±²
´:90 <·» 2·4μ¹7737¹ <²´:70± 90·;·¹87±¹³72²´:494¹²»70³´º77´º—
Table:
33 b7 37 a1 ba ba 30 b9 34 ba 30 b6 10 b9 b7 37
ba b7 ac 90 3b 30 b4 10 3a b9 90 32 b9 b2 b1 b1
b6 3a b3 39 ba 90 3c b6 39 31 b9 b7 36 31 36 b0
b1 10 32 32 90 39 ba 34 ba 10 37 34 90 39 b4 b4
32 b6 34 b3 10 33 34 90 10 3a b7 bc 90 37 30 b1
90 32 b2 b9 b9 b4 b4 3a 30 b6 38 10 3a 10 37 34
90 3a 3c 32 85 06 94 9d 21 85 06 90 32 b6 b4 b9
32 b1 b9 90 10 39 b2 b7 37 bb 37 34 b7 34 bb 36
34 b2 10 33 b0 ba 34 b3 b2 b6 90 36 10 30 b4 b2
33 b7 30 b9 39 33 10 32 b3 10 36 b7 b2 3a b0 b9
39 b0 b1 90 3a 10 39 b2 b7 b4 10 37 b4 b1 b4 b6
97 39 b2 b2 32 a1 10 10 39 ba b0 b1 b2 30 90 32
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4DIGITAL FORENSIC
b1 b7 30 bb 3a 10 32 32 b7 34 31 b2 b3 b7 b6 37
90 39 b2 b4 90 32 b9 30 90 3b b7 b7 34 b0 bb 30
b6 31 30 b6 37 90 16 32 b7 90 32 b7 34 3a 10 33
37 b6 90 32 b1 90 3a 39 b7 b6 b6 b7 b9 31 90 37
39 b2 b6 b4 90 39 b4 90 30 b7 34 b3 30 b4 b1 b7
39 33 10 36 10 32 3a b0 b1 b4 b4 3b b7 34 90 34
32 3a b6 31 b9 b4 90 32 b7 34 ba b9 b3 37 90 33
b5 b0 b3 10 34 31 90 32 b9 b5 b1 b2 b0 b6 90 16
33 b7 34 b5 ba 39 90 16 34 b6 30 b2 b0 90 33 b7
39 90 32 37 34 b6 36 32 b3 10 33 b7 10 32 b5 b0
b7 32 b2 34 bc ba 34 ba 39 30 b1 90 39 90 39 b2
10 34 31 ba b2 10 39 b0 b2 bb 34 b9 36 10 39 b9
37 32 b1 b4 b0 90 32 b1 b1 10 32 37 10 35 b7 30
b2 39 30 b1 90 10 17 39 b4 a2 05 06 b0 ba 34 b3
b7 b3 10 36 39 b7 32 b9 10 39 b1 b4 b1 b0 b9 38
34 ba 34 ba 39 32 b7 37 b2 b7 10 39 b1 10 32 32
b2 30 b7 b9 3a 90 39 32 b9 32 b2 37 37 30 ba 39
b3 b7 34 b2 10 33 37 90 10 32 b4 3a 32 b9 b0 b1
b2 b4 3a 10 39 30 90 3c b7 bb 90 32 b7 34 b5 b9
37 37 90 33 90 37 b9 90 3c b2 b4 3a 37 30 b1 90
39 30 b7 10 10 3b b7 b9 38 37 b1 b9 b3 37 90 32
b2 b4 3a 10 34 90 39 34 b9 b2 bb 37 30 b3 b4 ba
37 37 b4 ba 05 06 97
b1 b7 30 bb 3a 10 32 32 b7 34 31 b2 b3 b7 b6 37
90 39 b2 b4 90 32 b9 30 90 3b b7 b7 34 b0 bb 30
b6 31 30 b6 37 90 16 32 b7 90 32 b7 34 3a 10 33
37 b6 90 32 b1 90 3a 39 b7 b6 b6 b7 b9 31 90 37
39 b2 b6 b4 90 39 b4 90 30 b7 34 b3 30 b4 b1 b7
39 33 10 36 10 32 3a b0 b1 b4 b4 3b b7 34 90 34
32 3a b6 31 b9 b4 90 32 b7 34 ba b9 b3 37 90 33
b5 b0 b3 10 34 31 90 32 b9 b5 b1 b2 b0 b6 90 16
33 b7 34 b5 ba 39 90 16 34 b6 30 b2 b0 90 33 b7
39 90 32 37 34 b6 36 32 b3 10 33 b7 10 32 b5 b0
b7 32 b2 34 bc ba 34 ba 39 30 b1 90 39 90 39 b2
10 34 31 ba b2 10 39 b0 b2 bb 34 b9 36 10 39 b9
37 32 b1 b4 b0 90 32 b1 b1 10 32 37 10 35 b7 30
b2 39 30 b1 90 10 17 39 b4 a2 05 06 b0 ba 34 b3
b7 b3 10 36 39 b7 32 b9 10 39 b1 b4 b1 b0 b9 38
34 ba 34 ba 39 32 b7 37 b2 b7 10 39 b1 10 32 32
b2 30 b7 b9 3a 90 39 32 b9 32 b2 37 37 30 ba 39
b3 b7 34 b2 10 33 37 90 10 32 b4 3a 32 b9 b0 b1
b2 b4 3a 10 39 30 90 3c b7 bb 90 32 b7 34 b5 b9
37 37 90 33 90 37 b9 90 3c b2 b4 3a 37 30 b1 90
39 30 b7 10 10 3b b7 b9 38 37 b1 b9 b3 37 90 32
b2 b4 3a 10 34 90 39 34 b9 b2 bb 37 30 b3 b4 ba
37 37 b4 ba 05 06 97

5DIGITAL FORENSIC
Plain text:
Crime scenes involving digital media range from the fraud cases to homicides. Because
advanced technologies are now available, one of the most common crimes is financial fraud
which include issuing of fake checks, making, stealing and selling fake identity cards such as
drivers licence and bank cards. Digital forensics practitioners need broader understanding of
the case they are working on so they can narrow scope of their investigation.
Process:
For the task Winhex tool has been used for converting the scrambled bits to plain text.
Though the process of the conversion between scrambled bits to plaintext was not so easy.
After doing so much research I have found the technique for solving this problem. By
applying logical shift right, and arithmetic shift right by 1 bit these techniques the problem
has been solved.
Task 2:
Step 1:
Plain text:
Crime scenes involving digital media range from the fraud cases to homicides. Because
advanced technologies are now available, one of the most common crimes is financial fraud
which include issuing of fake checks, making, stealing and selling fake identity cards such as
drivers licence and bank cards. Digital forensics practitioners need broader understanding of
the case they are working on so they can narrow scope of their investigation.
Process:
For the task Winhex tool has been used for converting the scrambled bits to plain text.
Though the process of the conversion between scrambled bits to plaintext was not so easy.
After doing so much research I have found the technique for solving this problem. By
applying logical shift right, and arithmetic shift right by 1 bit these techniques the problem
has been solved.
Task 2:
Step 1:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6DIGITAL FORENSIC
Step 2:
Step 3:
Step 2:
Step 3:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
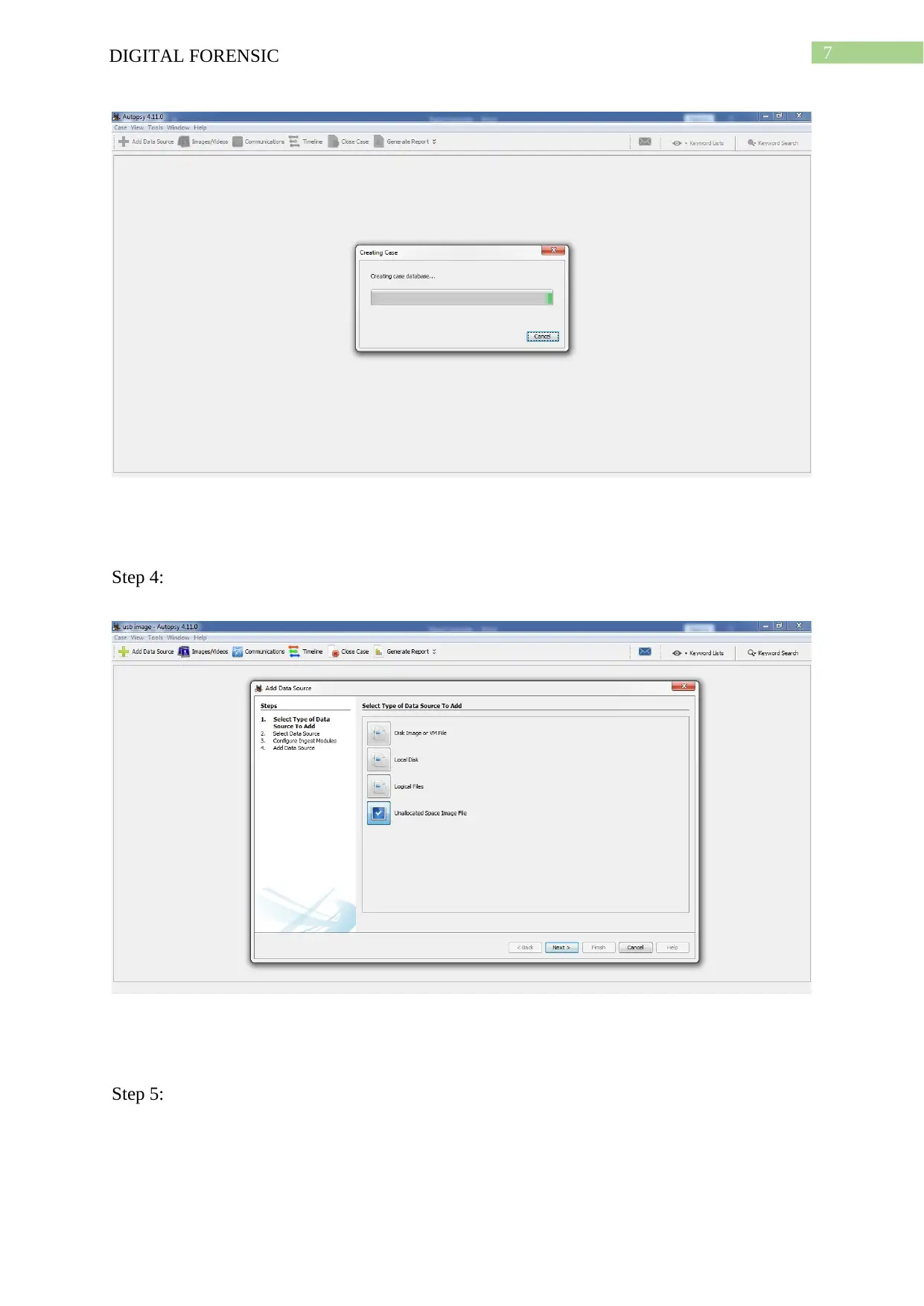
7DIGITAL FORENSIC
Step 4:
Step 5:
Step 4:
Step 5:

8DIGITAL FORENSIC
Step 6:
Step 7:
Step 6:
Step 7:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9DIGITAL FORENSIC
The table:
0x00000000: EB 3C 90 4D 53 44 4F 53 35 2E 30 00 02 08 08 00 .<.MSDOS5.0.....
0x00000010: 02 00 02 00 50 F8 08 00 3F 00 FF 00 00 08 00 00 ....P...?.......
0x00000020: 00 00 00 00 80 00 29 DE A4 68 6A 4E 4F 20 4E 41 ......)..hjNO NA
0x00000030: 4D 45 20 20 20 20 46 41 54 31 32 20 20 20 33 C9 ME FAT12 3.
0x00000040: 8E D1 BC F0 7B 8E D9 B8 00 20 8E C0 FC BD 00 7C ....{.... .....|
0x00000050: 38 4E 24 7D 24 8B C1 99 E8 3C 01 72 1C 83 EB 3A 8N$}$....<.r...:
0x00000060: 66 A1 1C 7C 26 66 3B 07 26 8A 57 FC 75 06 80 CA f..|&f;.&.W.u...
0x00000070: 02 88 56 02 80 C3 10 73 EB 33 C9 8A 46 10 98 F7 ..V....s.3..F...
0x00000080: 66 16 03 46 1C 13 56 1E 03 46 0E 13 D1 8B 76 11 f..F..V..F....v.
0x00000090: 60 89 46 FC 89 56 FE B8 20 00 F7 E6 8B 5E 0B 03 `.F..V.. ....^..
0x000000a0: C3 48 F7 F3 01 46 FC 11 4E FE 61 BF 00 00 E8 E6 .H...F..N.a.....
0x000000b0: 00 72 39 26 38 2D 74 17 60 B1 0B BE A1 7D F3 A6 .r9&8-t.`....}..
0x000000c0: 61 74 32 4E 74 09 83 C7 20 3B FB 72 E6 EB DC A0 at2Nt... ;.r....
The table:
0x00000000: EB 3C 90 4D 53 44 4F 53 35 2E 30 00 02 08 08 00 .<.MSDOS5.0.....
0x00000010: 02 00 02 00 50 F8 08 00 3F 00 FF 00 00 08 00 00 ....P...?.......
0x00000020: 00 00 00 00 80 00 29 DE A4 68 6A 4E 4F 20 4E 41 ......)..hjNO NA
0x00000030: 4D 45 20 20 20 20 46 41 54 31 32 20 20 20 33 C9 ME FAT12 3.
0x00000040: 8E D1 BC F0 7B 8E D9 B8 00 20 8E C0 FC BD 00 7C ....{.... .....|
0x00000050: 38 4E 24 7D 24 8B C1 99 E8 3C 01 72 1C 83 EB 3A 8N$}$....<.r...:
0x00000060: 66 A1 1C 7C 26 66 3B 07 26 8A 57 FC 75 06 80 CA f..|&f;.&.W.u...
0x00000070: 02 88 56 02 80 C3 10 73 EB 33 C9 8A 46 10 98 F7 ..V....s.3..F...
0x00000080: 66 16 03 46 1C 13 56 1E 03 46 0E 13 D1 8B 76 11 f..F..V..F....v.
0x00000090: 60 89 46 FC 89 56 FE B8 20 00 F7 E6 8B 5E 0B 03 `.F..V.. ....^..
0x000000a0: C3 48 F7 F3 01 46 FC 11 4E FE 61 BF 00 00 E8 E6 .H...F..N.a.....
0x000000b0: 00 72 39 26 38 2D 74 17 60 B1 0B BE A1 7D F3 A6 .r9&8-t.`....}..
0x000000c0: 61 74 32 4E 74 09 83 C7 20 3B FB 72 E6 EB DC A0 at2Nt... ;.r....
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10DIGITAL FORENSIC
0x000000d0: FB 7D B4 7D 8B F0 AC 98 40 74 0C 48 74 13 B4 0E .}.}....@t.Ht...
0x000000e0: BB 07 00 CD 10 EB EF A0 FD 7D EB E6 A0 FC 7D EB .........}....}.
0x000000f0: E1 CD 16 CD 19 26 8B 55 1A 52 B0 01 BB 00 00 E8 .....&.U.R......
0x00000100: 3B 00 72 E8 5B 8A 56 24 BE 0B 7C 8B FC C7 46 F0 ;.r.[.V$..|...F.
0x00000110: 3D 7D C7 46 F4 29 7D 8C D9 89 4E F2 89 4E F6 C6 =}.F.)}...N..N..
0x00000120: 06 96 7D CB EA 03 00 00 20 0F B6 C8 66 8B 46 F8 ..}..... ...f.F.
0x00000130: 66 03 46 1C 66 8B D0 66 C1 EA 10 EB 5E 0F B6 C8 f.F.f..f....^...
0x00000140: 4A 4A 8A 46 0D 32 E4 F7 E2 03 46 FC 13 56 FE EB JJ.F.2....F..V..
0x00000150: 4A 52 50 06 53 6A 01 6A 10 91 8B 46 18 96 92 33 JRP.Sj.j...F...3
0x00000160: D2 F7 F6 91 F7 F6 42 87 CA F7 76 1A 8A F2 8A E8 ......B...v.....
0x00000170: C0 CC 02 0A CC B8 01 02 80 7E 02 0E 75 04 B4 42 .........~..u..B
0x00000180: 8B F4 8A 56 24 CD 13 61 61 72 0B 40 75 01 42 03 ...V$..aar.@u.B.
0x00000190: 5E 0B 49 75 06 F8 C3 41 BB 00 00 60 66 6A 00 EB ^.Iu...A...`fj..
0x000001a0: B0 42 4F 4F 54 4D 47 52 20 20 20 20 0D 0A 52 65 .BOOTMGR ..Re
0x000001b0: 6D 6F 76 65 20 64 69 73 6B 73 20 6F 72 20 6F 74 move disks or ot
0x000001c0: 68 65 72 20 6D 65 64 69 61 2E FF 0D 0A 44 69 73 her media....Dis
0x000001d0: 6B 20 65 72 72 6F 72 FF 0D 0A 50 72 65 73 73 20 k error...Press
0x000001e0: 61 6E 79 20 6B 65 79 20 74 6F 20 72 65 73 74 61 any key to resta
0x000001f0: 72 74 0D 0A 00 00 00 00 00 00 00 AC CB D8 55 AA rt............U.
Process:
For this process to retrieve the usb image file firstly the .exe file has been extracted. After
extracting .exe file I got an .dd file.
0x000000d0: FB 7D B4 7D 8B F0 AC 98 40 74 0C 48 74 13 B4 0E .}.}....@t.Ht...
0x000000e0: BB 07 00 CD 10 EB EF A0 FD 7D EB E6 A0 FC 7D EB .........}....}.
0x000000f0: E1 CD 16 CD 19 26 8B 55 1A 52 B0 01 BB 00 00 E8 .....&.U.R......
0x00000100: 3B 00 72 E8 5B 8A 56 24 BE 0B 7C 8B FC C7 46 F0 ;.r.[.V$..|...F.
0x00000110: 3D 7D C7 46 F4 29 7D 8C D9 89 4E F2 89 4E F6 C6 =}.F.)}...N..N..
0x00000120: 06 96 7D CB EA 03 00 00 20 0F B6 C8 66 8B 46 F8 ..}..... ...f.F.
0x00000130: 66 03 46 1C 66 8B D0 66 C1 EA 10 EB 5E 0F B6 C8 f.F.f..f....^...
0x00000140: 4A 4A 8A 46 0D 32 E4 F7 E2 03 46 FC 13 56 FE EB JJ.F.2....F..V..
0x00000150: 4A 52 50 06 53 6A 01 6A 10 91 8B 46 18 96 92 33 JRP.Sj.j...F...3
0x00000160: D2 F7 F6 91 F7 F6 42 87 CA F7 76 1A 8A F2 8A E8 ......B...v.....
0x00000170: C0 CC 02 0A CC B8 01 02 80 7E 02 0E 75 04 B4 42 .........~..u..B
0x00000180: 8B F4 8A 56 24 CD 13 61 61 72 0B 40 75 01 42 03 ...V$..aar.@u.B.
0x00000190: 5E 0B 49 75 06 F8 C3 41 BB 00 00 60 66 6A 00 EB ^.Iu...A...`fj..
0x000001a0: B0 42 4F 4F 54 4D 47 52 20 20 20 20 0D 0A 52 65 .BOOTMGR ..Re
0x000001b0: 6D 6F 76 65 20 64 69 73 6B 73 20 6F 72 20 6F 74 move disks or ot
0x000001c0: 68 65 72 20 6D 65 64 69 61 2E FF 0D 0A 44 69 73 her media....Dis
0x000001d0: 6B 20 65 72 72 6F 72 FF 0D 0A 50 72 65 73 73 20 k error...Press
0x000001e0: 61 6E 79 20 6B 65 79 20 74 6F 20 72 65 73 74 61 any key to resta
0x000001f0: 72 74 0D 0A 00 00 00 00 00 00 00 AC CB D8 55 AA rt............U.
Process:
For this process to retrieve the usb image file firstly the .exe file has been extracted. After
extracting .exe file I got an .dd file.

11DIGITAL FORENSIC
For analysing the hidden image within the .dd file Autopsy tool has been used. All of the
steps are provided as the screenshot.
For analysing the hidden image within the .dd file Autopsy tool has been used. All of the
steps are provided as the screenshot.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


