Comparing Digital Forensic Frameworks in the Public Cloud Environment
VerifiedAdded on 2022/11/07
|7
|1381
|494
Report
AI Summary
This document provides a comparative analysis of digital forensic investigation frameworks within public cloud environments. It explores and contrasts various frameworks, including an integrated conceptual digital forensic framework, the Digital Forensic Hyper-model, cloud forensic investigation, and the Live Digital Forensic Framework for a cloud (LDF2C). The report delves into the stages of each framework, such as evidence identification, collection, examination, analysis, and reporting. The integrated conceptual framework, in particular, is highlighted for its iterative nature, allowing investigators to revisit earlier phases to gather more evidence. The report also discusses the procedural steps involved in cloud forensic investigations, including evidence source identification, data collection, and analysis. The conclusion emphasizes the differences and similarities among the frameworks, highlighting the effectiveness of the conceptual framework while also acknowledging its limitations in terms of storage and data recovery. The assignment concludes with a discussion of the limitations of the framework and the need for clarifications for data recovery.

DIGITAL FORENSIC INVESTIGATION FRAMEWORKS IN PUBLIC CLOUD
Student
Tutor
Institutional Affiliations
Date
Student
Tutor
Institutional Affiliations
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Digital Forensic Investigation Frameworks in Public Cloud
The digital forensic involves the use of the methods that are scientifically derived and
proven to collect, validate, identify, interpret and present digital evidence that are derived from
digital sources to facilitate or further reconstruction of unauthorized events. Various digital
forensic frameworks have evolved since its innovation. In this document we explore and
compare different digital forensic frameworks.
Digital forensic has suffered a significant advances since its innovation. This is
exemplified by the available digital forensic investigation tools. As a consequence, various
frameworks have evolved. However, for this assignment, we compare only four frameworks for
public cloud environment including: an integrated conceptual digital forensic framework, Digital
Forensic Hyper-model, the cloud forensic investigation and Live Digital Forensic Framework for
a cloud LDF2C [1].
The integrated conceptual digital forensic framework for cloud conducts a cloud forensic
investigations in four stages. These include evidence identification, collection, evidence
examination and evidence analysis and reporting. The Digital Forensic Hyper-model, on the
other hand involves three stages including preparative phase, investigation phase and
presentation stage.
The cloud forensic investigation, however, involves three main stages including
preparation, acquisition as well as evidence analysis both on the client and cloud service provider
side. In the Live Digital Forensic Framework for a cloud LDF2C, the approach on the other hand
is concerned with evidence identification and evidence acquisition stages for real-time forensic
investigation [2], [3]. Some of the frameworks above differ in terms investigation phases. But,
The digital forensic involves the use of the methods that are scientifically derived and
proven to collect, validate, identify, interpret and present digital evidence that are derived from
digital sources to facilitate or further reconstruction of unauthorized events. Various digital
forensic frameworks have evolved since its innovation. In this document we explore and
compare different digital forensic frameworks.
Digital forensic has suffered a significant advances since its innovation. This is
exemplified by the available digital forensic investigation tools. As a consequence, various
frameworks have evolved. However, for this assignment, we compare only four frameworks for
public cloud environment including: an integrated conceptual digital forensic framework, Digital
Forensic Hyper-model, the cloud forensic investigation and Live Digital Forensic Framework for
a cloud LDF2C [1].
The integrated conceptual digital forensic framework for cloud conducts a cloud forensic
investigations in four stages. These include evidence identification, collection, evidence
examination and evidence analysis and reporting. The Digital Forensic Hyper-model, on the
other hand involves three stages including preparative phase, investigation phase and
presentation stage.
The cloud forensic investigation, however, involves three main stages including
preparation, acquisition as well as evidence analysis both on the client and cloud service provider
side. In the Live Digital Forensic Framework for a cloud LDF2C, the approach on the other hand
is concerned with evidence identification and evidence acquisition stages for real-time forensic
investigation [2], [3]. Some of the frameworks above differ in terms investigation phases. But,

both of them are the same based on of the technical dimensions of the forensic investigation in
cloud.
Conceptual digital forensic framework
The preceding parts compared various digital forensic frameworks for the cloud. This
section however propose one framework. The framework proposed here is a four steps including
evidence identification, collection, evidence examination and evidence analysis and reporting
[4]. The framework is integrated conceptual digital forensic framework. The framework is
represented in the following UML model diagram.
This framework is an improvement NIST framework to an integrated conceptual digital
framework to offer digital forensic investigation in the cloud environment. Besides the fact that
the framework is an improvement of another framework, it has one distinction that makes it
outstanding from other frameworks regarding iteration. This unique properties provide
investigators with an opportunity to return back to initial phases during forensic investigation in
order to gather more evidence.
cloud.
Conceptual digital forensic framework
The preceding parts compared various digital forensic frameworks for the cloud. This
section however propose one framework. The framework proposed here is a four steps including
evidence identification, collection, evidence examination and evidence analysis and reporting
[4]. The framework is integrated conceptual digital forensic framework. The framework is
represented in the following UML model diagram.
This framework is an improvement NIST framework to an integrated conceptual digital
framework to offer digital forensic investigation in the cloud environment. Besides the fact that
the framework is an improvement of another framework, it has one distinction that makes it
outstanding from other frameworks regarding iteration. This unique properties provide
investigators with an opportunity to return back to initial phases during forensic investigation in
order to gather more evidence.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
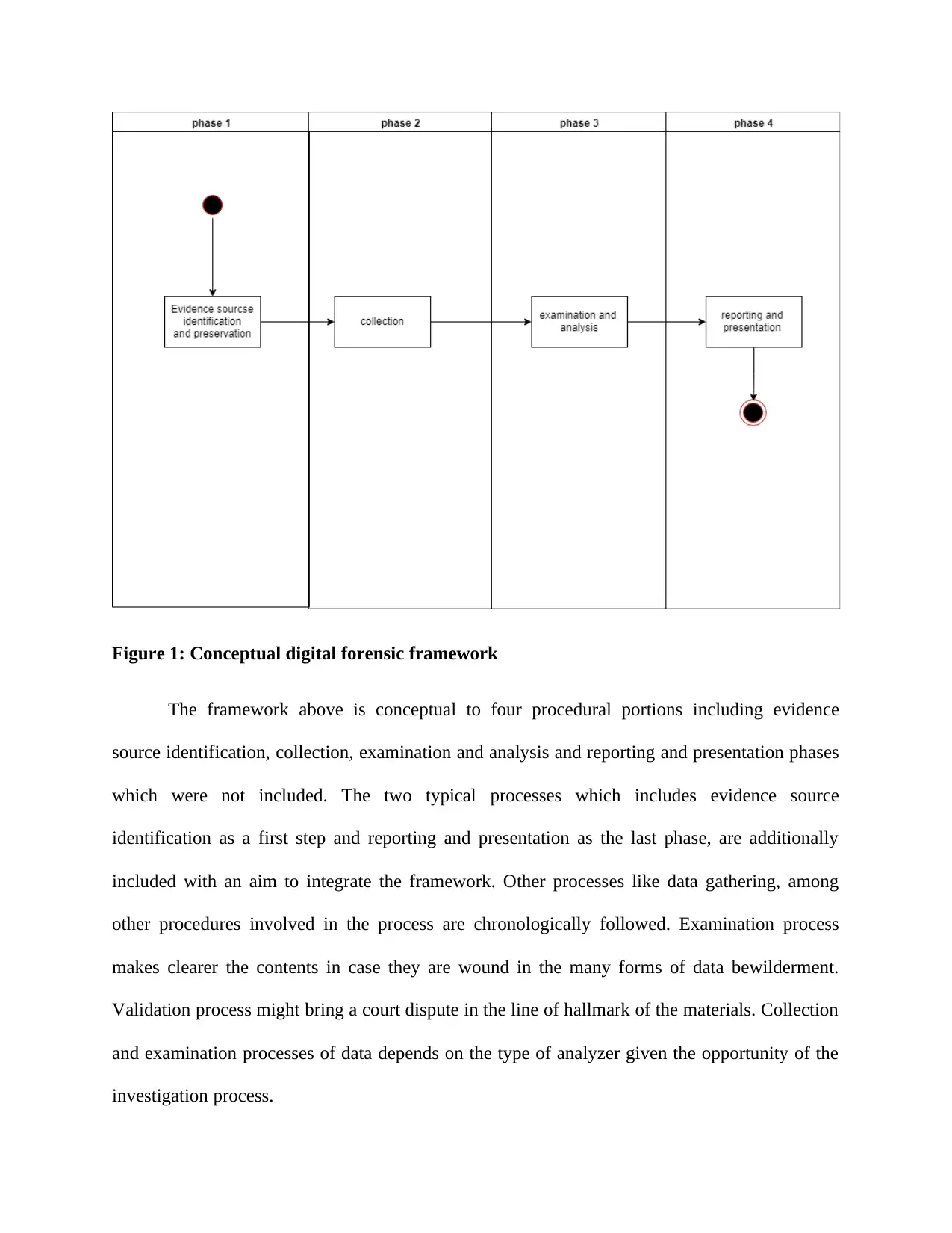
Figure 1: Conceptual digital forensic framework
The framework above is conceptual to four procedural portions including evidence
source identification, collection, examination and analysis and reporting and presentation phases
which were not included. The two typical processes which includes evidence source
identification as a first step and reporting and presentation as the last phase, are additionally
included with an aim to integrate the framework. Other processes like data gathering, among
other procedures involved in the process are chronologically followed. Examination process
makes clearer the contents in case they are wound in the many forms of data bewilderment.
Validation process might bring a court dispute in the line of hallmark of the materials. Collection
and examination processes of data depends on the type of analyzer given the opportunity of the
investigation process.
The framework above is conceptual to four procedural portions including evidence
source identification, collection, examination and analysis and reporting and presentation phases
which were not included. The two typical processes which includes evidence source
identification as a first step and reporting and presentation as the last phase, are additionally
included with an aim to integrate the framework. Other processes like data gathering, among
other procedures involved in the process are chronologically followed. Examination process
makes clearer the contents in case they are wound in the many forms of data bewilderment.
Validation process might bring a court dispute in the line of hallmark of the materials. Collection
and examination processes of data depends on the type of analyzer given the opportunity of the
investigation process.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

At a point where decision making is reached, report compilation is much vital. It requires
resourced evidence supporting the report with properly arranged and validated documents
majorly obtained in the prior phase of investigation. The report will at long last have greater
impact on the filed report ready for presentation. What if enough and supportive evidence is not
obtained? The process will be worth to get excluded and the court will employ the use of its
findings for proper and further investigations with an aim of helping the individuals in the
process to be ready for the unforeseen previously unknown factors.
As far as the cloud forensic investigation is concerned, the procedures for investigations
experiences various steps to concentrate and dissect confirmations relying upon a given criminal
case. In each scientific system, distinguishing proof source is the initial step that ought to be
directed to locate a speculated gadget to seize for examination reason [5]. While holding onto
suspected gadget, agents must guarantee honesty of information by protecting proof and forestall
any change on information. If there should arise an occurrence of cloud criminal activity, the
device that is suspected must get seized and the cloud account that is compromised has to be
stopped to guarantee so as to ensure data integrity. Gathering and accessing the required
confirmations from the held onto gadget comes as a second step during the investigation process.
Various procedures can be utilized to procure information during this stage. In any case,
live scientific is the main procedure that can be utilized to gather information from cloud where
gathering information from disk images isn't sufficient to settle on any cloud's criminal case.
Various antiquities can be examined on the customer gadgets like cloud Synced Folder, cloud
web customer Interface and system. Additionally, some potential confirmations can be gathered
from network captures, memory captures as well as artifacts of a browser. In the investigation
process, breaking down the sources of the gathered information is considered as a significant
resourced evidence supporting the report with properly arranged and validated documents
majorly obtained in the prior phase of investigation. The report will at long last have greater
impact on the filed report ready for presentation. What if enough and supportive evidence is not
obtained? The process will be worth to get excluded and the court will employ the use of its
findings for proper and further investigations with an aim of helping the individuals in the
process to be ready for the unforeseen previously unknown factors.
As far as the cloud forensic investigation is concerned, the procedures for investigations
experiences various steps to concentrate and dissect confirmations relying upon a given criminal
case. In each scientific system, distinguishing proof source is the initial step that ought to be
directed to locate a speculated gadget to seize for examination reason [5]. While holding onto
suspected gadget, agents must guarantee honesty of information by protecting proof and forestall
any change on information. If there should arise an occurrence of cloud criminal activity, the
device that is suspected must get seized and the cloud account that is compromised has to be
stopped to guarantee so as to ensure data integrity. Gathering and accessing the required
confirmations from the held onto gadget comes as a second step during the investigation process.
Various procedures can be utilized to procure information during this stage. In any case,
live scientific is the main procedure that can be utilized to gather information from cloud where
gathering information from disk images isn't sufficient to settle on any cloud's criminal case.
Various antiquities can be examined on the customer gadgets like cloud Synced Folder, cloud
web customer Interface and system. Additionally, some potential confirmations can be gathered
from network captures, memory captures as well as artifacts of a browser. In the investigation
process, breaking down the sources of the gathered information is considered as a significant

stage to locate the precise evidence regarding the investigation. A relevant forensic toolbox is
required in this stage must match the digital forensic techniques used. The results produced in
this stage is to check and guarantee the event of any criminal case on cloud accounts by looking
at all accessible cloud segments on customer gadget.
In conclusion, this document has presented an overview on digital forensic investigation.
In doing so, the article has compared various frameworks of digital forensic investigation in
public cloud. It has been found that the frameworks differ in their investigation phases but they
also show some similarity in terms of the technical dimensions of the cloud based digital
forensic. We selected one framework including conceptual digital forensic framework for cloud
which is consist of four stages. Based on the analysis, it can be concluded that this framework
provide one of the most effective strategies for investigations. However, it provide clients with a
limited storage infrastructure [6]. As a result, it only allow a limited collection of evidence
during investigation of criminal cases. Additionally, the framework require clarifications for data
recovery if the data got lost in the cloud.
required in this stage must match the digital forensic techniques used. The results produced in
this stage is to check and guarantee the event of any criminal case on cloud accounts by looking
at all accessible cloud segments on customer gadget.
In conclusion, this document has presented an overview on digital forensic investigation.
In doing so, the article has compared various frameworks of digital forensic investigation in
public cloud. It has been found that the frameworks differ in their investigation phases but they
also show some similarity in terms of the technical dimensions of the cloud based digital
forensic. We selected one framework including conceptual digital forensic framework for cloud
which is consist of four stages. Based on the analysis, it can be concluded that this framework
provide one of the most effective strategies for investigations. However, it provide clients with a
limited storage infrastructure [6]. As a result, it only allow a limited collection of evidence
during investigation of criminal cases. Additionally, the framework require clarifications for data
recovery if the data got lost in the cloud.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
[1] Sibiya G, Venter HS, Fogwill T. Digital forensic framework for a cloud environment.
[2] Du X, Le-Khac NA, Scanlon M. Evaluation of digital forensic process models with respect to
digital forensics as a service. arXiv preprint arXiv:1708.01730. 2017 Aug 5.
[3] Simou S, Kalloniatis C, Kavakli E, Gritzalis S. Cloud forensics: identifying the major issues
and challenges. InInternational conference on advanced information systems engineering 2014
Jun 16 (pp. 271-284). Springer, Cham.
[4] Martini B, Choo KK. An integrated conceptual digital forensic framework for cloud
computing. Digital Investigation. 2012 Nov 1;9(2):71-80.
[5] Daryabar F, Dehghantanha A, Udzir NI, Sani NF, Shamsuddin S, Norouzizadeh F. A survey
about impacts of cloud computing on digital forensics. International Journal of Cyber-Security
and Digital Forensics. 2013 Apr 1;2(2):77-94.
[6] Thethi N, Keane A. Digital forensics investigations in the cloud. In2014 IEEE international
advance computing conference (IACC) 2014 Feb 21 (pp. 1475-1480). IEEE.
[1] Sibiya G, Venter HS, Fogwill T. Digital forensic framework for a cloud environment.
[2] Du X, Le-Khac NA, Scanlon M. Evaluation of digital forensic process models with respect to
digital forensics as a service. arXiv preprint arXiv:1708.01730. 2017 Aug 5.
[3] Simou S, Kalloniatis C, Kavakli E, Gritzalis S. Cloud forensics: identifying the major issues
and challenges. InInternational conference on advanced information systems engineering 2014
Jun 16 (pp. 271-284). Springer, Cham.
[4] Martini B, Choo KK. An integrated conceptual digital forensic framework for cloud
computing. Digital Investigation. 2012 Nov 1;9(2):71-80.
[5] Daryabar F, Dehghantanha A, Udzir NI, Sani NF, Shamsuddin S, Norouzizadeh F. A survey
about impacts of cloud computing on digital forensics. International Journal of Cyber-Security
and Digital Forensics. 2013 Apr 1;2(2):77-94.
[6] Thethi N, Keane A. Digital forensics investigations in the cloud. In2014 IEEE international
advance computing conference (IACC) 2014 Feb 21 (pp. 1475-1480). IEEE.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





