Digital Forensic Investigation of Recovering Corrupted Image Files
VerifiedAdded on 2023/06/12
|19
|2319
|447
AI Summary
This report discusses the forensic investigation of recovering corrupted image files using ProDiscover and Hex Workshop software. The report covers the analysis conducted, search for and recovering digital photography evidence, rebuilding file header, reconstructing file fragments, and findings. The report also mentions the tools used and references.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
[Document title]
[Document subtitle]
[DATE]
[Company name]
[Company address]
[Document subtitle]
[DATE]
[Company name]
[Company address]
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Task 2.........................................................................................................................................2
Abstract..................................................................................................................................2
Introduction............................................................................................................................2
Analysis conducted................................................................................................................3
Search for and Recovering Digital photography Evidence....................................................3
Rebuilding File Header........................................................................................................10
Reconstructing File Fragments............................................................................................11
Findings................................................................................................................................14
References............................................................................................................................16
Task 2.........................................................................................................................................2
Abstract..................................................................................................................................2
Introduction............................................................................................................................2
Analysis conducted................................................................................................................3
Search for and Recovering Digital photography Evidence....................................................3
Rebuilding File Header........................................................................................................10
Reconstructing File Fragments............................................................................................11
Findings................................................................................................................................14
References............................................................................................................................16

Task 2
Abstract
The case at hand is about the possible theft of Intellectual Property by a contract employee in
company Exotic Mountain Tour Services (ETMS). The company has just finished an
extensive market analysis and customer service along with Superior Bicycles, LLC. The
reason for the investigation are the two emails that were captured and raises questions about
the data that have been communicated using the email to a competitor. The USB drive was
also found at the workstation on which the contract employee used to operate, the forensic
investigation is about the email and USB drive image and trying to recover as much as data
for the possible recovery of data that have been stolen.
Introduction
ProDiscover is the forensic tool that is used to analyze the disk images, it is windows based
forensic tool that can acquire and analyze the disk partitions. Though the features available
are quite large but only few of them are being used for the forensic purposes.
One of the most important aspect of the ProDiscover is that it can make the remote client
images while rest of the work can continue to work as ever. The forensic images created are
intact though the original disk being continuously being changed or manipulated. Though
ProDiscover is a paid software but available for trail based and student reporting non-
profitable purposes.
Another tool that is being used for this workshop is the Hex Workshop, it is Hex editor that is
developed by BreakPoint Company, it is Windows based utility and being used in several
forensic reporting by forensic experts around the world. The Hex Workshop allows the
feature of binary editing and interpretation of data along with the visualization of the same
like a flexibility of any modern-based word processor. With the help of WinHex forensic
expert can cut, copy, edit, paste, insert, delete any binary data. With the data in this native
structure can be worked upon using the WinHex as well as the data types with integrated
structure and smart bookmark option also being made available. The other useful operations
that are available are find or replace the data, sector location jump, performing various
arithmetic operations, logical operations over the data, generating the checksums and digests
Abstract
The case at hand is about the possible theft of Intellectual Property by a contract employee in
company Exotic Mountain Tour Services (ETMS). The company has just finished an
extensive market analysis and customer service along with Superior Bicycles, LLC. The
reason for the investigation are the two emails that were captured and raises questions about
the data that have been communicated using the email to a competitor. The USB drive was
also found at the workstation on which the contract employee used to operate, the forensic
investigation is about the email and USB drive image and trying to recover as much as data
for the possible recovery of data that have been stolen.
Introduction
ProDiscover is the forensic tool that is used to analyze the disk images, it is windows based
forensic tool that can acquire and analyze the disk partitions. Though the features available
are quite large but only few of them are being used for the forensic purposes.
One of the most important aspect of the ProDiscover is that it can make the remote client
images while rest of the work can continue to work as ever. The forensic images created are
intact though the original disk being continuously being changed or manipulated. Though
ProDiscover is a paid software but available for trail based and student reporting non-
profitable purposes.
Another tool that is being used for this workshop is the Hex Workshop, it is Hex editor that is
developed by BreakPoint Company, it is Windows based utility and being used in several
forensic reporting by forensic experts around the world. The Hex Workshop allows the
feature of binary editing and interpretation of data along with the visualization of the same
like a flexibility of any modern-based word processor. With the help of WinHex forensic
expert can cut, copy, edit, paste, insert, delete any binary data. With the data in this native
structure can be worked upon using the WinHex as well as the data types with integrated
structure and smart bookmark option also being made available. The other useful operations
that are available are find or replace the data, sector location jump, performing various
arithmetic operations, logical operations over the data, generating the checksums and digests

based on data and view character distributions, all of this report can be exported to HTML or
RTF for detailed publishing of the reports.
Analysis conducted
At the current moment a very little is known of the information on the USB drive of the
suspect intern. We need to ask yourself some basic questions as well as some important
assumptions that are made available in order to proceed in search of any information. There
were two emails that were being forwarded to the terrysadler@groowy.com and
baspen@aol.com, that matches the contract employee credentials and name. Next we need to
check the timestamp and date of the message that have been sent: 4 Feb 2007 9:21 PM, and
the 2007, 5:17 AM -08:00.
As the Jim Shu email sent to the terrysadler@groowy.com account that had been forwarded
to the baspen@aol.com account, the time stamp of the Jim Shu mail is later than the time
stamp used for the terrysadler@groowy.com that means the Jim Shu must be from the
western region with different time zone as the two email server’s time values have been off
due to the fact the time stamp are being provided by the server not the users.
With the next email asking the bob to alter all the data sent in image format to have their
extensions changed to .jpg to .txt and these files are about kayaks. Last message that have the
last line that is responded to the terrysadler@groowy.com that says that Bob cannot be
receive this message.
Search for and Recovering Digital photography Evidence
In this part we are going to recover the corrupted image file that might be there on the image
file provided by the EMTS, the examination would be about finding the “FIF” string, the
reason of using the “FIF” is because using JFIF and JPEG might lead to several other
previous image files that might be present over the USB drive. These false hits that are also
known as false hits needs to be examined and as a forensic investigator needs to verify each
and every file that we are actually looking for.
In order to examine the image C10InChp.eve following are the steps are being used in order
to observe it using the ProDiscover software:
1. Run ProDiscover Basic as Administrator on the Windows based PC and create a new
project named C10InChp, and numbered (1).
RTF for detailed publishing of the reports.
Analysis conducted
At the current moment a very little is known of the information on the USB drive of the
suspect intern. We need to ask yourself some basic questions as well as some important
assumptions that are made available in order to proceed in search of any information. There
were two emails that were being forwarded to the terrysadler@groowy.com and
baspen@aol.com, that matches the contract employee credentials and name. Next we need to
check the timestamp and date of the message that have been sent: 4 Feb 2007 9:21 PM, and
the 2007, 5:17 AM -08:00.
As the Jim Shu email sent to the terrysadler@groowy.com account that had been forwarded
to the baspen@aol.com account, the time stamp of the Jim Shu mail is later than the time
stamp used for the terrysadler@groowy.com that means the Jim Shu must be from the
western region with different time zone as the two email server’s time values have been off
due to the fact the time stamp are being provided by the server not the users.
With the next email asking the bob to alter all the data sent in image format to have their
extensions changed to .jpg to .txt and these files are about kayaks. Last message that have the
last line that is responded to the terrysadler@groowy.com that says that Bob cannot be
receive this message.
Search for and Recovering Digital photography Evidence
In this part we are going to recover the corrupted image file that might be there on the image
file provided by the EMTS, the examination would be about finding the “FIF” string, the
reason of using the “FIF” is because using JFIF and JPEG might lead to several other
previous image files that might be present over the USB drive. These false hits that are also
known as false hits needs to be examined and as a forensic investigator needs to verify each
and every file that we are actually looking for.
In order to examine the image C10InChp.eve following are the steps are being used in order
to observe it using the ProDiscover software:
1. Run ProDiscover Basic as Administrator on the Windows based PC and create a new
project named C10InChp, and numbered (1).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
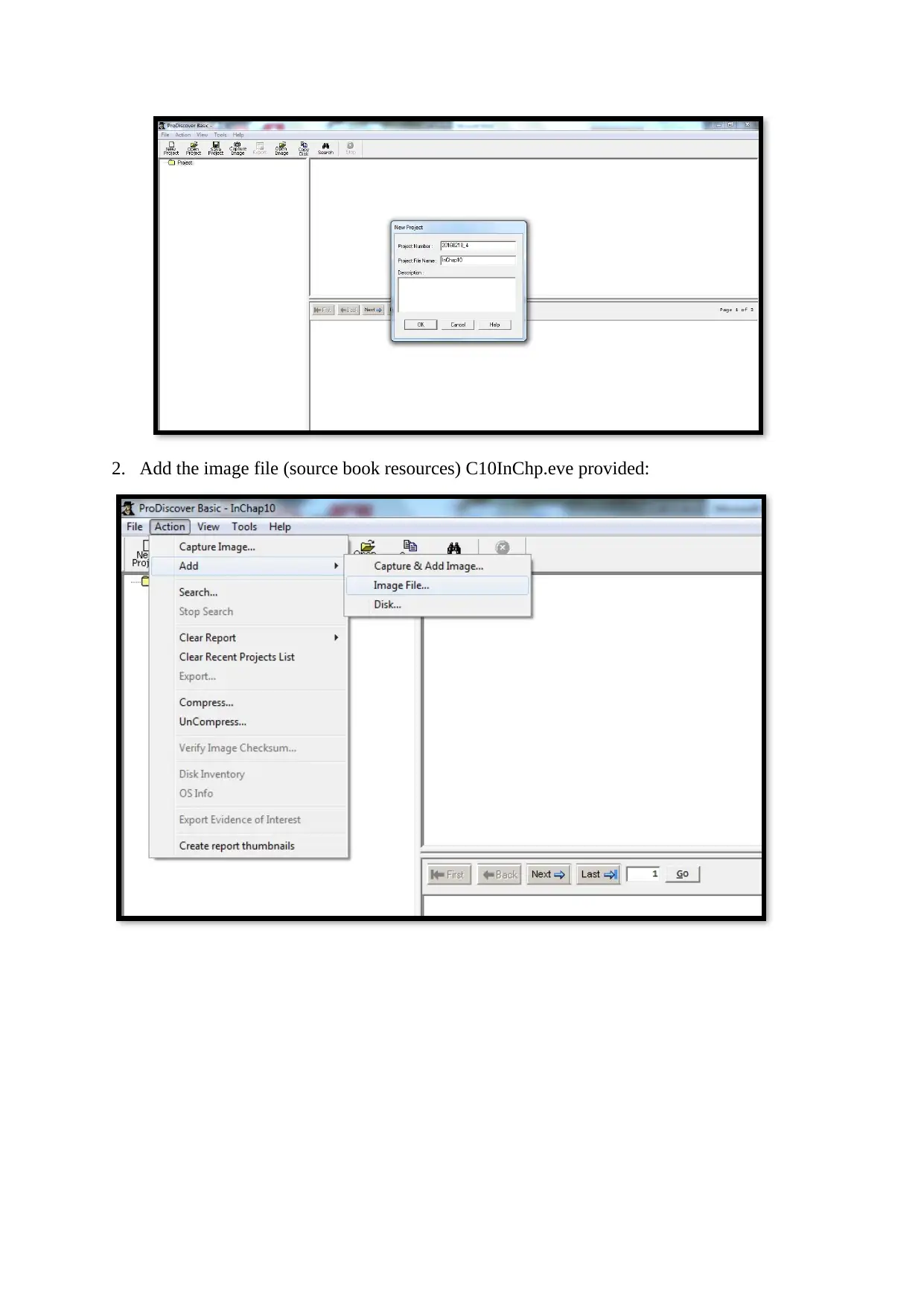
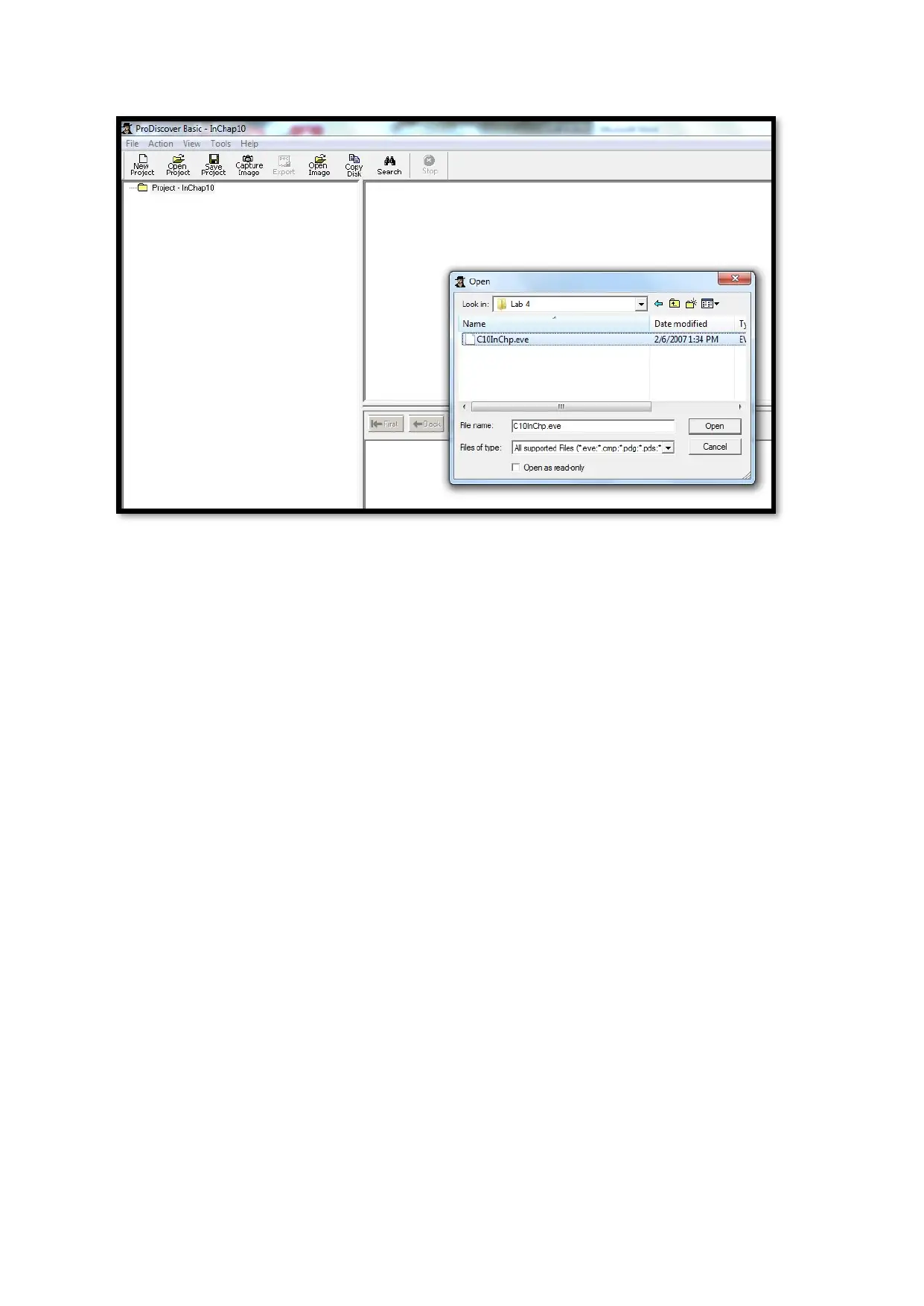
2. Add the image file (source book resources) C10InChp.eve provided:
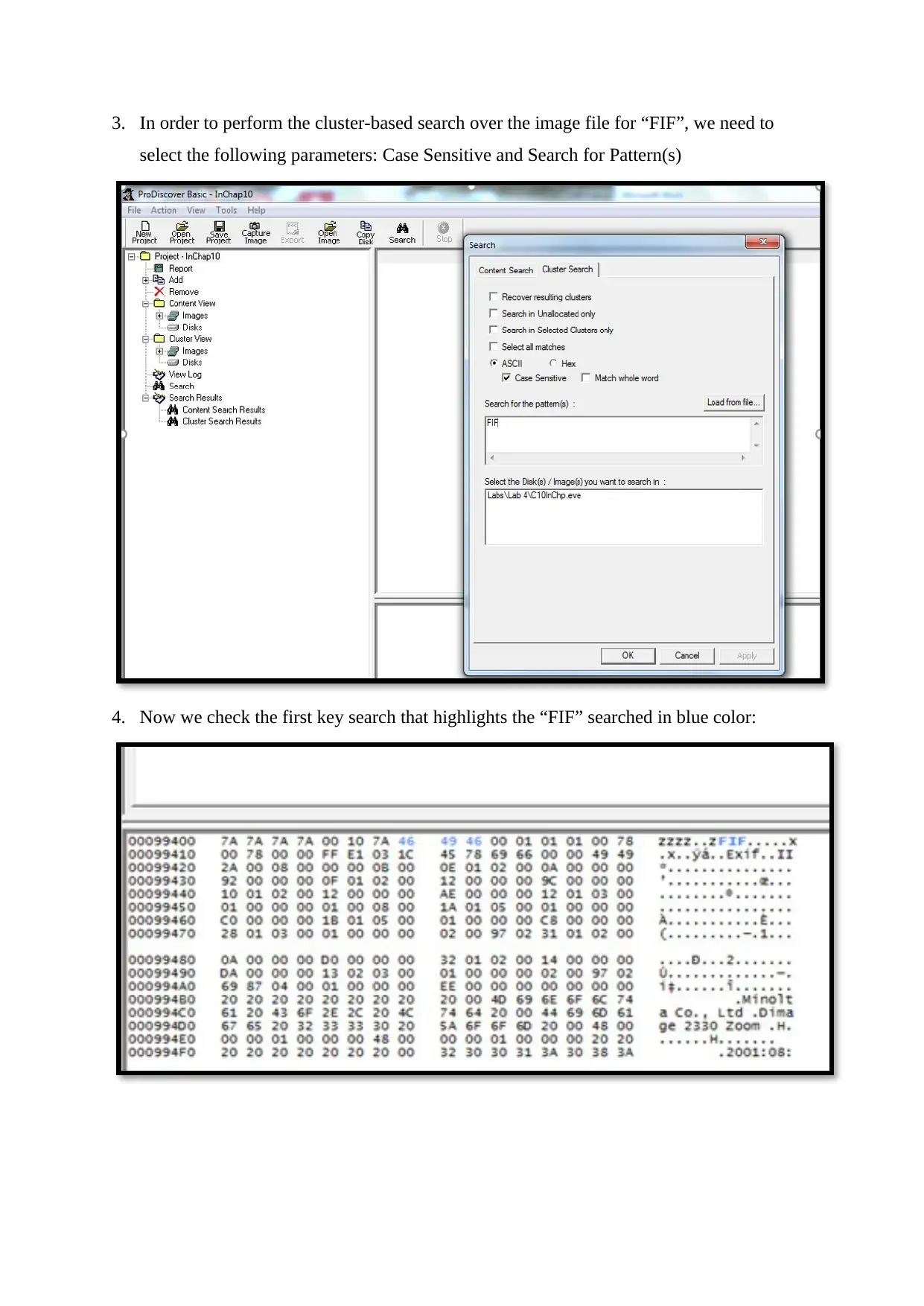
3. In order to perform the cluster-based search over the image file for “FIF”, we need to
select the following parameters: Case Sensitive and Search for Pattern(s)
4. Now we check the first key search that highlights the “FIF” searched in blue color:
select the following parameters: Case Sensitive and Search for Pattern(s)
4. Now we check the first key search that highlights the “FIF” searched in blue color:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
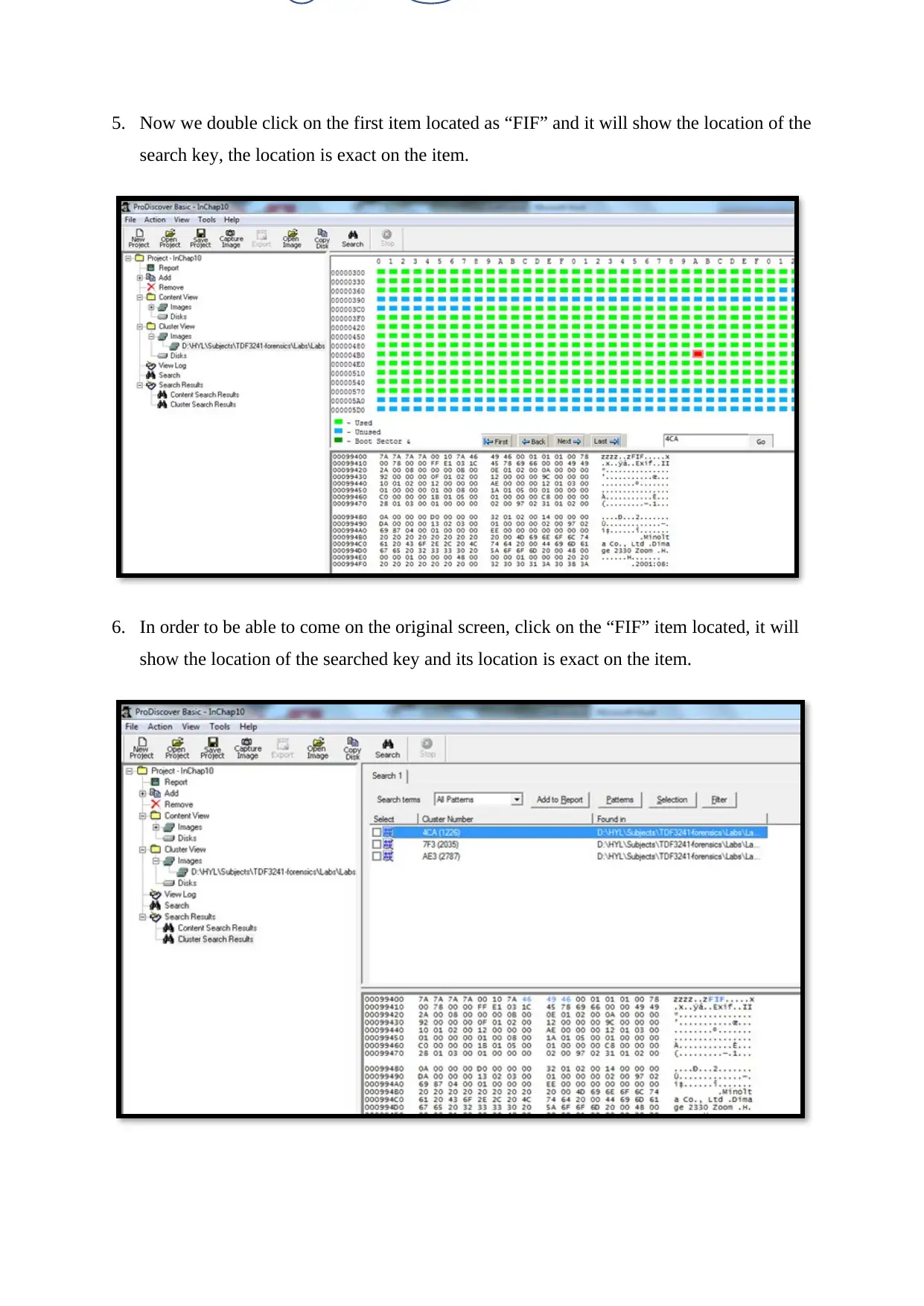
5. Now we double click on the first item located as “FIF” and it will show the location of the
search key, the location is exact on the item.
6. In order to be able to come on the original screen, click on the “FIF” item located, it will
show the location of the searched key and its location is exact on the item.
search key, the location is exact on the item.
6. In order to be able to come on the original screen, click on the “FIF” item located, it will
show the location of the searched key and its location is exact on the item.
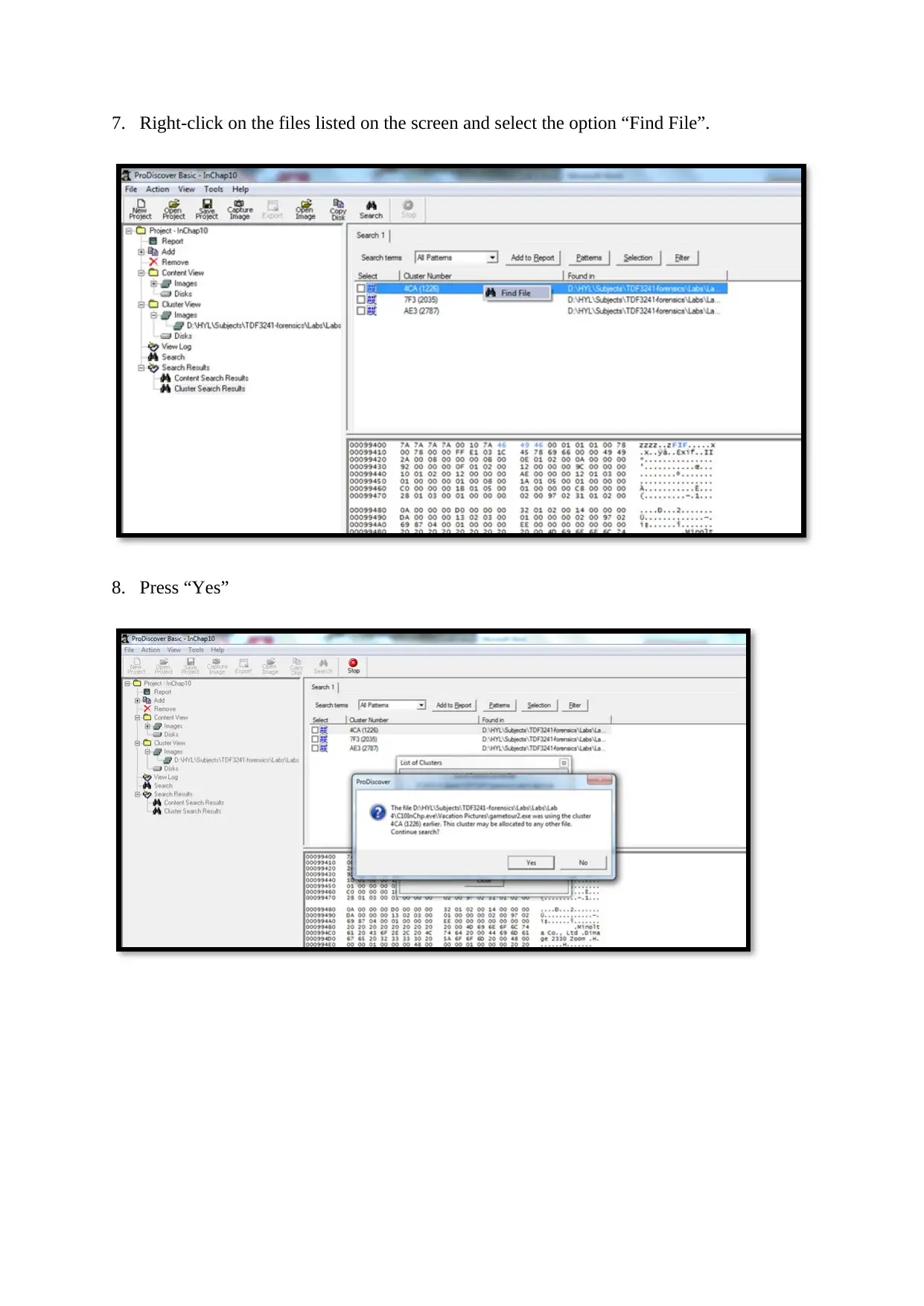
7. Right-click on the files listed on the screen and select the option “Find File”.
8. Press “Yes”
8. Press “Yes”
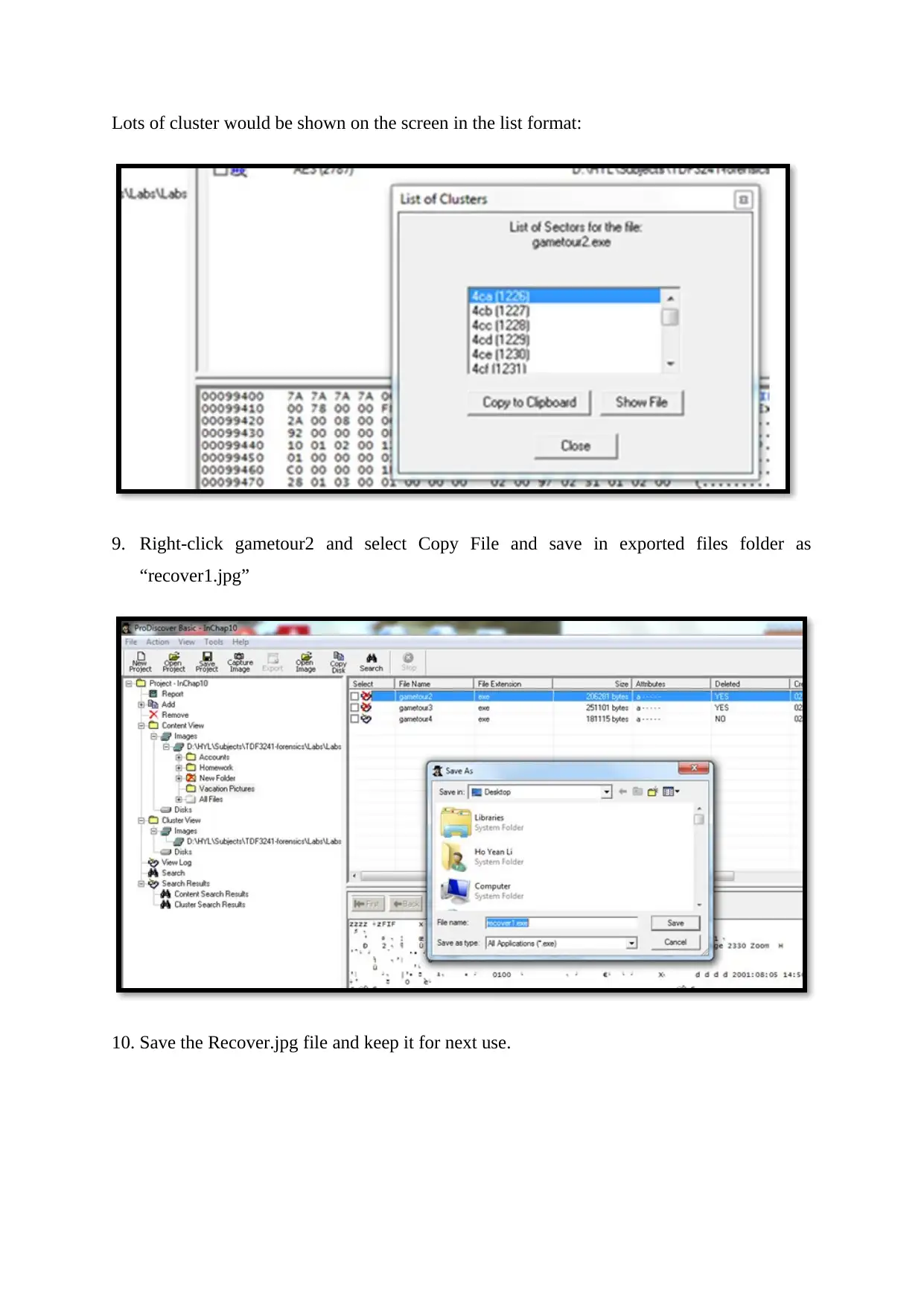
Lots of cluster would be shown on the screen in the list format:
9. Right-click gametour2 and select Copy File and save in exported files folder as
“recover1.jpg”
10. Save the Recover.jpg file and keep it for next use.
9. Right-click gametour2 and select Copy File and save in exported files folder as
“recover1.jpg”
10. Save the Recover.jpg file and keep it for next use.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
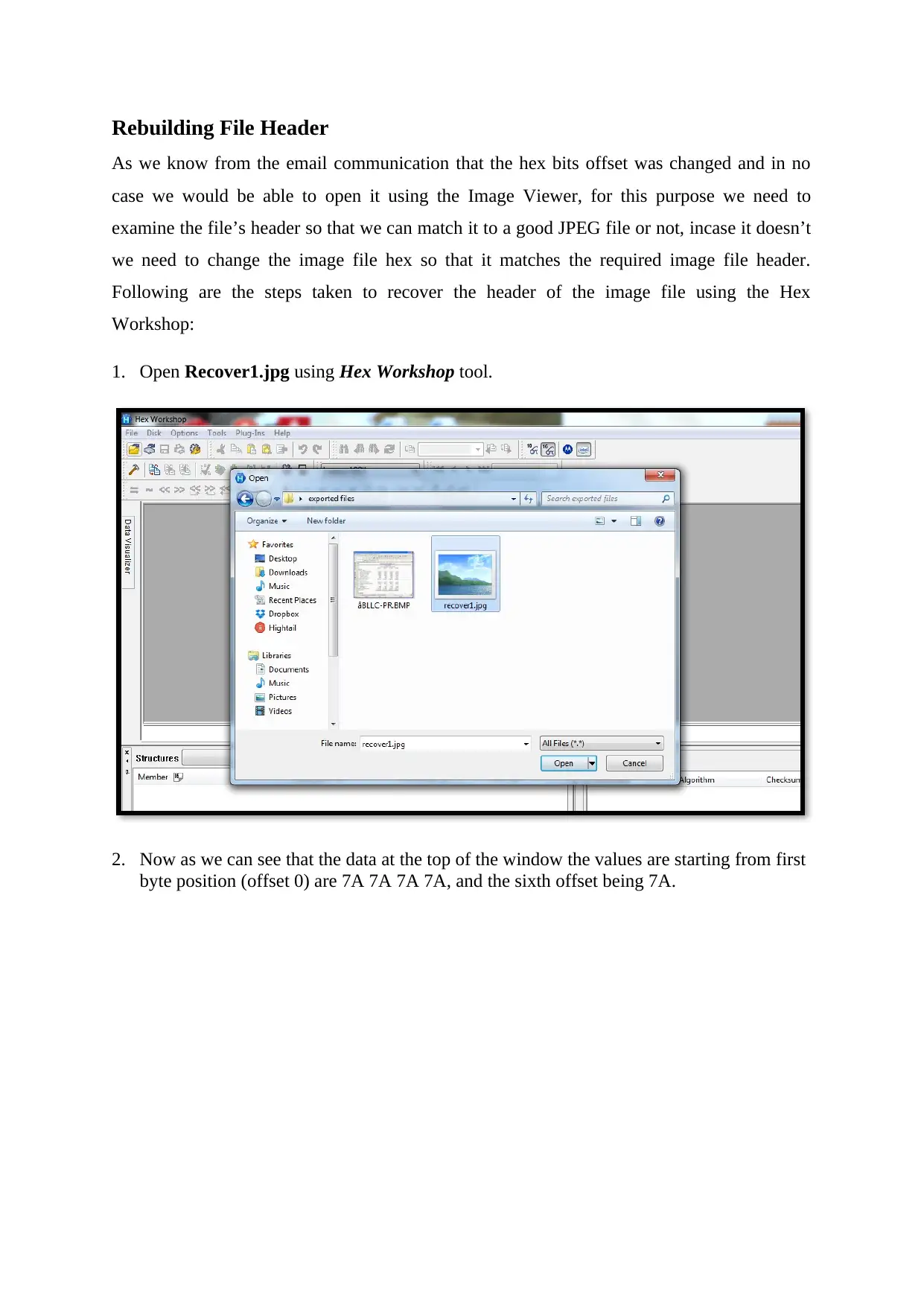
Rebuilding File Header
As we know from the email communication that the hex bits offset was changed and in no
case we would be able to open it using the Image Viewer, for this purpose we need to
examine the file’s header so that we can match it to a good JPEG file or not, incase it doesn’t
we need to change the image file hex so that it matches the required image file header.
Following are the steps taken to recover the header of the image file using the Hex
Workshop:
1. Open Recover1.jpg using Hex Workshop tool.
2. Now as we can see that the data at the top of the window the values are starting from first
byte position (offset 0) are 7A 7A 7A 7A, and the sixth offset being 7A.
As we know from the email communication that the hex bits offset was changed and in no
case we would be able to open it using the Image Viewer, for this purpose we need to
examine the file’s header so that we can match it to a good JPEG file or not, incase it doesn’t
we need to change the image file hex so that it matches the required image file header.
Following are the steps taken to recover the header of the image file using the Hex
Workshop:
1. Open Recover1.jpg using Hex Workshop tool.
2. Now as we can see that the data at the top of the window the values are starting from first
byte position (offset 0) are 7A 7A 7A 7A, and the sixth offset being 7A.
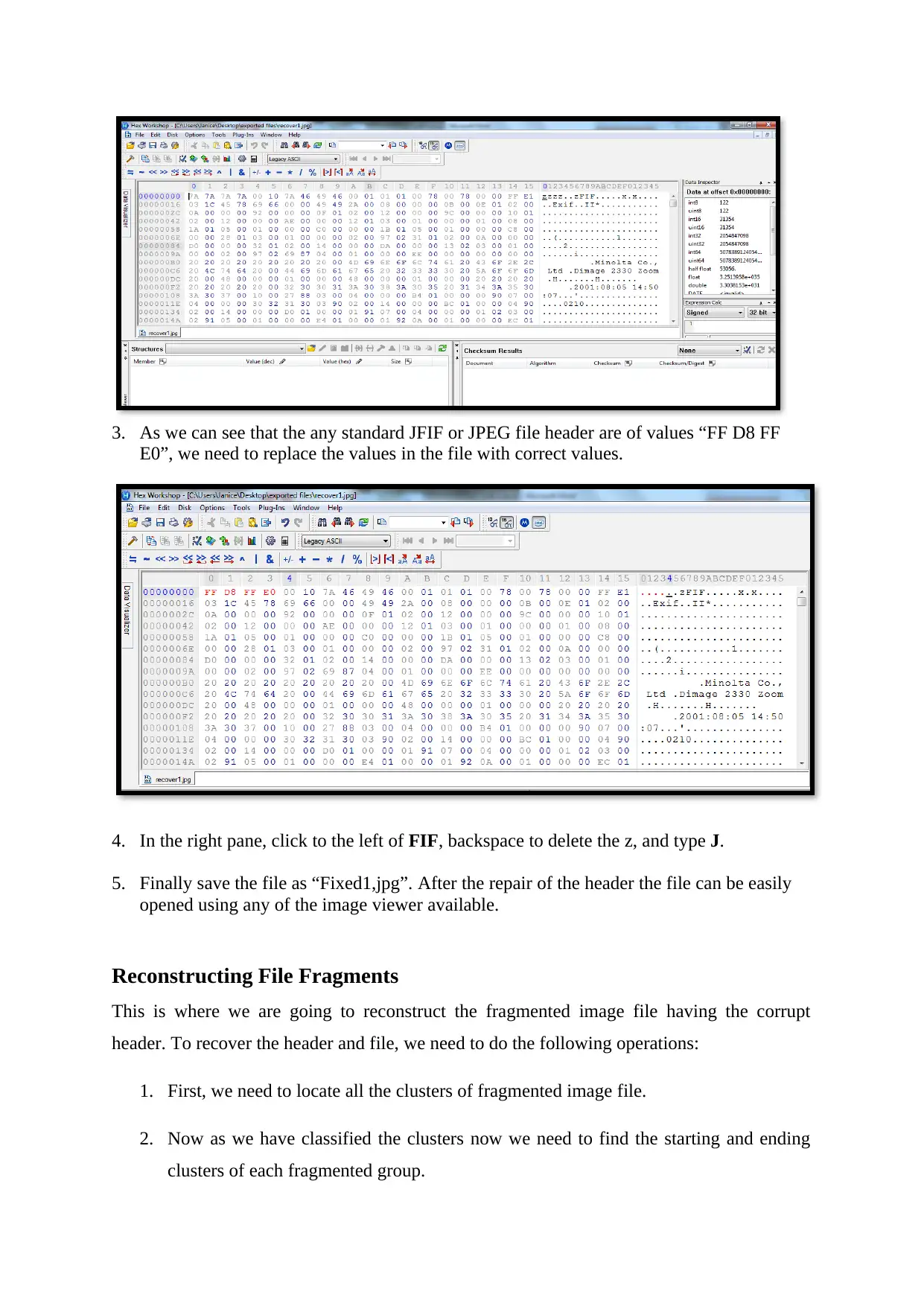
3. As we can see that the any standard JFIF or JPEG file header are of values “FF D8 FF
E0”, we need to replace the values in the file with correct values.
4. In the right pane, click to the left of FIF, backspace to delete the z, and type J.
5. Finally save the file as “Fixed1,jpg”. After the repair of the header the file can be easily
opened using any of the image viewer available.
Reconstructing File Fragments
This is where we are going to reconstruct the fragmented image file having the corrupt
header. To recover the header and file, we need to do the following operations:
1. First, we need to locate all the clusters of fragmented image file.
2. Now as we have classified the clusters now we need to find the starting and ending
clusters of each fragmented group.
E0”, we need to replace the values in the file with correct values.
4. In the right pane, click to the left of FIF, backspace to delete the z, and type J.
5. Finally save the file as “Fixed1,jpg”. After the repair of the header the file can be easily
opened using any of the image viewer available.
Reconstructing File Fragments
This is where we are going to reconstruct the fragmented image file having the corrupt
header. To recover the header and file, we need to do the following operations:
1. First, we need to locate all the clusters of fragmented image file.
2. Now as we have classified the clusters now we need to find the starting and ending
clusters of each fragmented group.

3. Copy the fragments in correct order in order to recover the file
4. Rebuild the entire header of the fragmented file in order to be able to view in any
image viewer.
4. Rebuild the entire header of the fragmented file in order to be able to view in any
image viewer.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
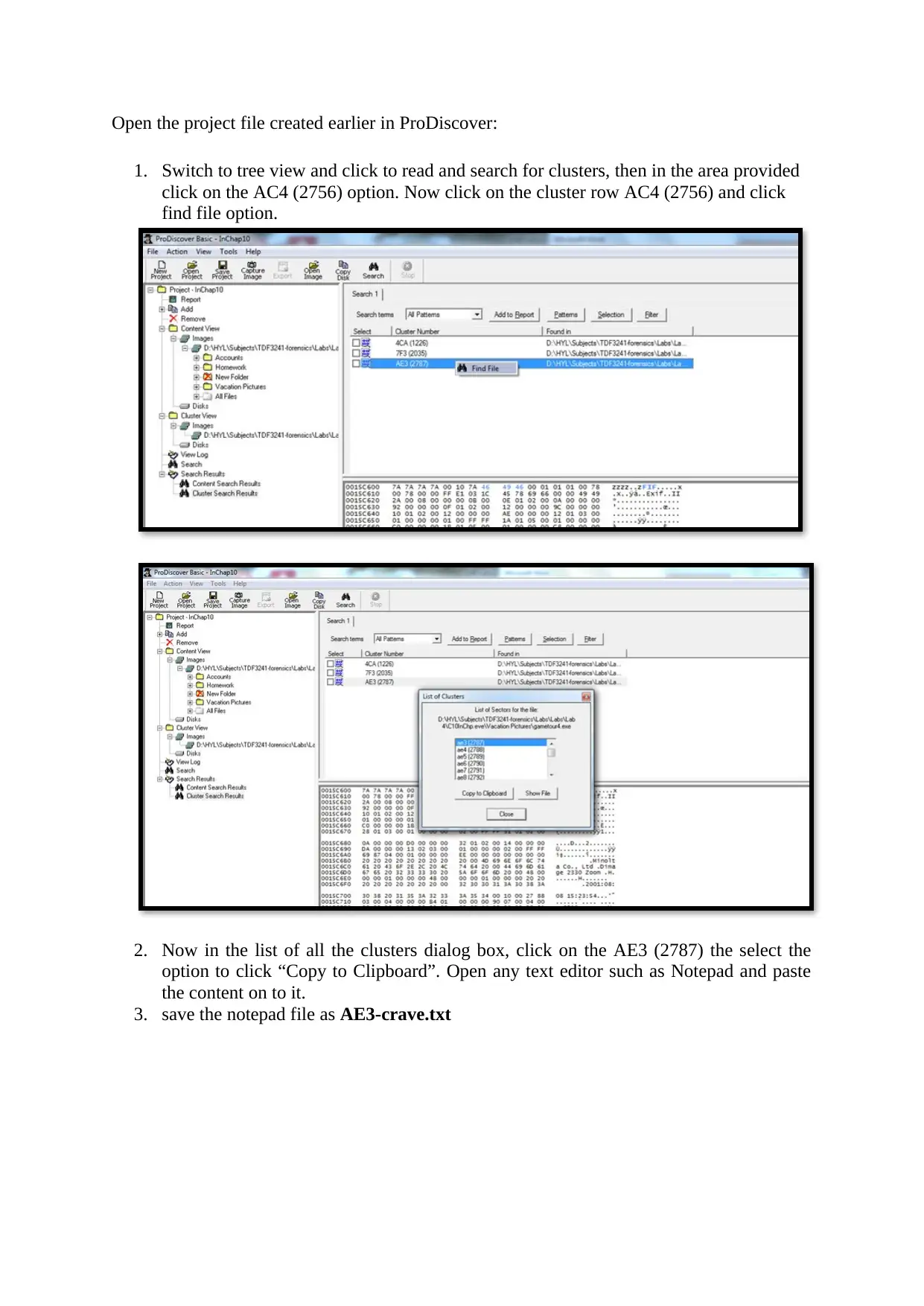
Open the project file created earlier in ProDiscover:
1. Switch to tree view and click to read and search for clusters, then in the area provided
click on the AC4 (2756) option. Now click on the cluster row AC4 (2756) and click
find file option.
2. Now in the list of all the clusters dialog box, click on the AE3 (2787) the select the
option to click “Copy to Clipboard”. Open any text editor such as Notepad and paste
the content on to it.
3. save the notepad file as AE3-crave.txt
1. Switch to tree view and click to read and search for clusters, then in the area provided
click on the AC4 (2756) option. Now click on the cluster row AC4 (2756) and click
find file option.
2. Now in the list of all the clusters dialog box, click on the AE3 (2787) the select the
option to click “Copy to Clipboard”. Open any text editor such as Notepad and paste
the content on to it.
3. save the notepad file as AE3-crave.txt
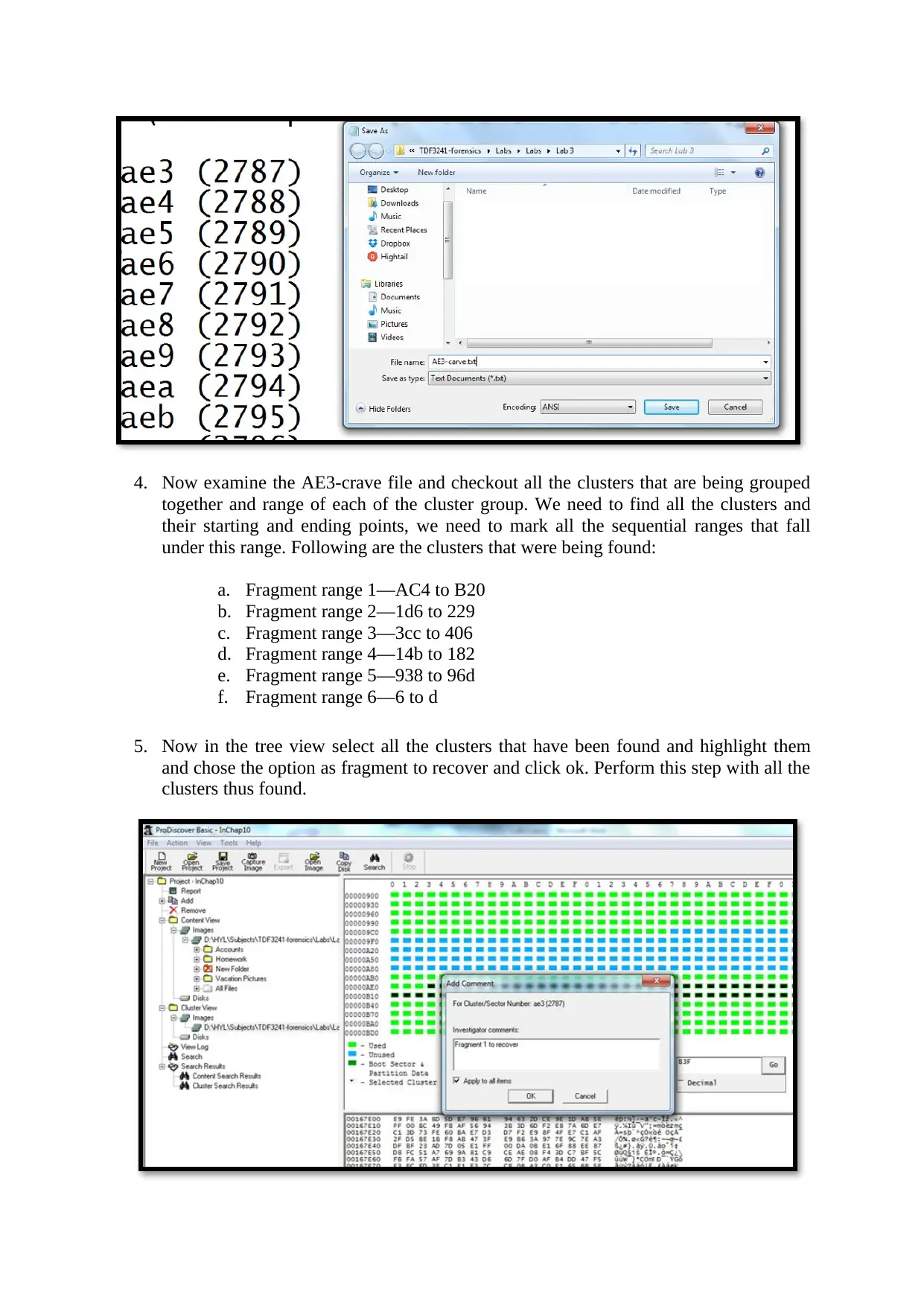
4. Now examine the AE3-crave file and checkout all the clusters that are being grouped
together and range of each of the cluster group. We need to find all the clusters and
their starting and ending points, we need to mark all the sequential ranges that fall
under this range. Following are the clusters that were being found:
a. Fragment range 1—AC4 to B20
b. Fragment range 2—1d6 to 229
c. Fragment range 3—3cc to 406
d. Fragment range 4—14b to 182
e. Fragment range 5—938 to 96d
f. Fragment range 6—6 to d
5. Now in the tree view select all the clusters that have been found and highlight them
and chose the option as fragment to recover and click ok. Perform this step with all the
clusters thus found.
together and range of each of the cluster group. We need to find all the clusters and
their starting and ending points, we need to mark all the sequential ranges that fall
under this range. Following are the clusters that were being found:
a. Fragment range 1—AC4 to B20
b. Fragment range 2—1d6 to 229
c. Fragment range 3—3cc to 406
d. Fragment range 4—14b to 182
e. Fragment range 5—938 to 96d
f. Fragment range 6—6 to d
5. Now in the tree view select all the clusters that have been found and highlight them
and chose the option as fragment to recover and click ok. Perform this step with all the
clusters thus found.
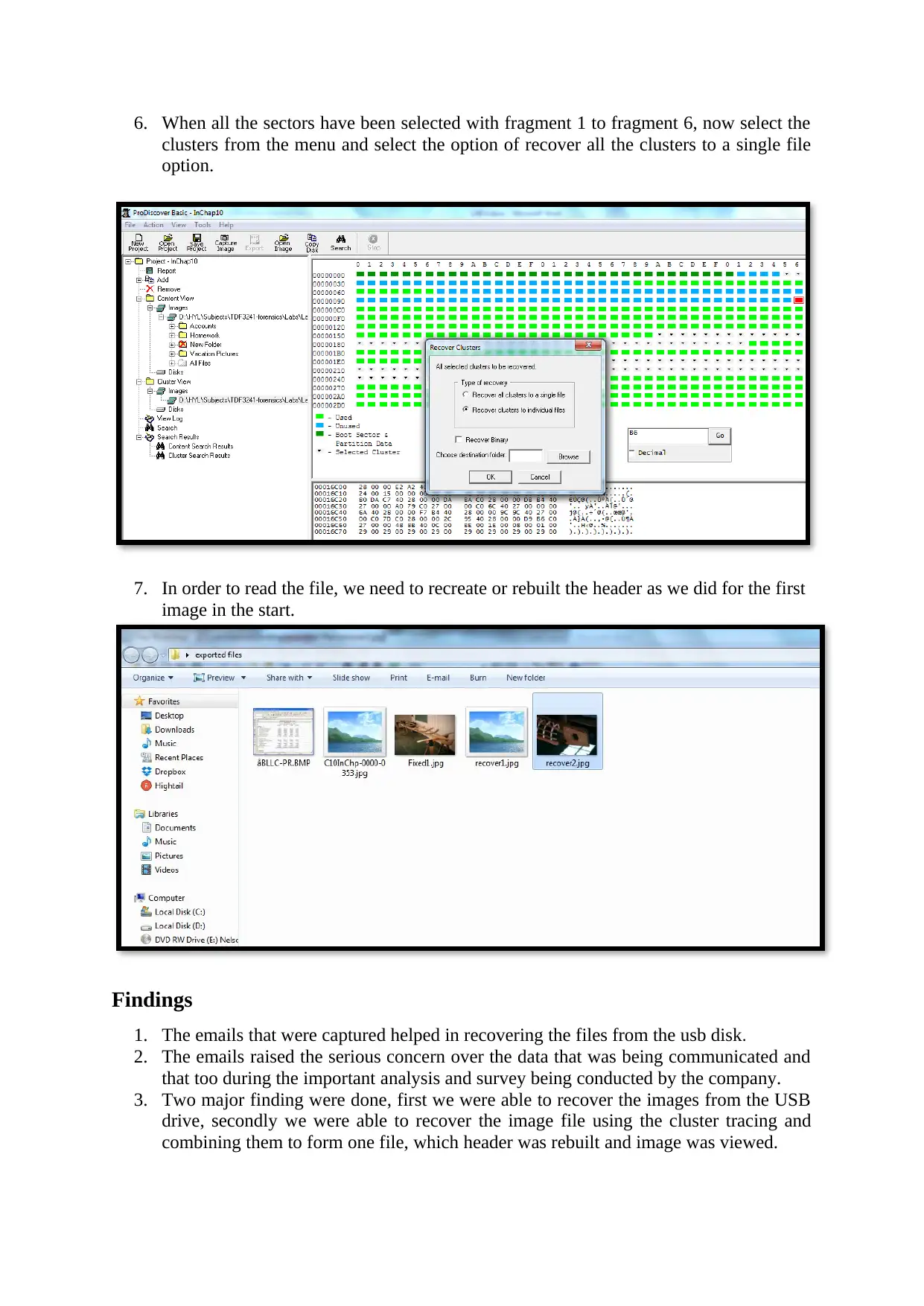
6. When all the sectors have been selected with fragment 1 to fragment 6, now select the
clusters from the menu and select the option of recover all the clusters to a single file
option.
7. In order to read the file, we need to recreate or rebuilt the header as we did for the first
image in the start.
Findings
1. The emails that were captured helped in recovering the files from the usb disk.
2. The emails raised the serious concern over the data that was being communicated and
that too during the important analysis and survey being conducted by the company.
3. Two major finding were done, first we were able to recover the images from the USB
drive, secondly we were able to recover the image file using the cluster tracing and
combining them to form one file, which header was rebuilt and image was viewed.
clusters from the menu and select the option of recover all the clusters to a single file
option.
7. In order to read the file, we need to recreate or rebuilt the header as we did for the first
image in the start.
Findings
1. The emails that were captured helped in recovering the files from the usb disk.
2. The emails raised the serious concern over the data that was being communicated and
that too during the important analysis and survey being conducted by the company.
3. Two major finding were done, first we were able to recover the images from the USB
drive, secondly we were able to recover the image file using the cluster tracing and
combining them to form one file, which header was rebuilt and image was viewed.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4. The two major Forensic tools that were used were ProDiscover and Hex WinHex
software, ProDiscover was used to recover the data from the image and clusters as well
whereas the WinHex was used to replace the hex values of the data recovered to
manage them and view the originally intended files.
software, ProDiscover was used to recover the data from the image and clusters as well
whereas the WinHex was used to replace the hex values of the data recovered to
manage them and view the originally intended files.

References
Carrier, B. (2006). Risks of live digital forensic analysis. Communications Of The
ACM, 49(2), 56. doi: 10.1145/1113034.1113069
Mayer, F., & Steinebach, M. (2017). Forensic Image Inspection Assisted by Deep
Learning. Proceedings Of The 12Th International Conference On Availability,
Reliability And Security - ARES '17. doi: 10.1145/3098954.3104051
Mazurczyk, W., Caviglione, L., & Wendzel, S. (2017). Recent Advancements in Digital
Forensics. IEEE Security & Privacy, 15(6), 10-11. doi: 10.1109/msp.2017.4251106
Mire, A., Dhok, S., Porey, P., & Mistry, N. (2014). Digital Forensic of JPEG Images. 2014
Fifth International Conference On Signal And Image Processing. doi:
10.1109/icsip.2014.26
Morioka, E., & Sharbaf, M. (2016). Digital forensics research on cloud computing: An
investigation of cloud forensics solutions. 2016 IEEE Symposium On Technologies For
Homeland Security (HST). doi: 10.1109/ths.2016.7568909
Quick, D., & Choo, K. (2016). Big forensic data reduction: digital forensic images and
electronic evidence. Cluster Computing, 19(2), 723-740. doi: 10.1007/s10586-016-0553-
1
Redi, J., Taktak, W., & Dugelay, J. (2010). Digital image forensics: a booklet for
beginners. Multimedia Tools And Applications, 51(1), 133-162. doi: 10.1007/s11042-
010-0620-1
Richard, G., & Roussev, V. (2006). Next-generation digital forensics. Communications Of
The ACM, 49(2), 76. doi: 10.1145/1113034.1113074
Shrivastava, A., Payal, N., Rastogi, A., & Tiwari, A. (2013). Digital Forensic Investigation
Development Model. 2013 5Th International Conference On Computational Intelligence
And Communication Networks. doi: 10.1109/cicn.2013.115
van Beek, H., van Eijk, E., van Baar, R., Ugen, M., Bodde, J., & Siemelink, A. (2015).
Digital forensics as a service: Game on. Digital Investigation, 15, 20-38. doi:
10.1016/j.diin.2015.07.004
Carrier, B. (2006). Risks of live digital forensic analysis. Communications Of The
ACM, 49(2), 56. doi: 10.1145/1113034.1113069
Mayer, F., & Steinebach, M. (2017). Forensic Image Inspection Assisted by Deep
Learning. Proceedings Of The 12Th International Conference On Availability,
Reliability And Security - ARES '17. doi: 10.1145/3098954.3104051
Mazurczyk, W., Caviglione, L., & Wendzel, S. (2017). Recent Advancements in Digital
Forensics. IEEE Security & Privacy, 15(6), 10-11. doi: 10.1109/msp.2017.4251106
Mire, A., Dhok, S., Porey, P., & Mistry, N. (2014). Digital Forensic of JPEG Images. 2014
Fifth International Conference On Signal And Image Processing. doi:
10.1109/icsip.2014.26
Morioka, E., & Sharbaf, M. (2016). Digital forensics research on cloud computing: An
investigation of cloud forensics solutions. 2016 IEEE Symposium On Technologies For
Homeland Security (HST). doi: 10.1109/ths.2016.7568909
Quick, D., & Choo, K. (2016). Big forensic data reduction: digital forensic images and
electronic evidence. Cluster Computing, 19(2), 723-740. doi: 10.1007/s10586-016-0553-
1
Redi, J., Taktak, W., & Dugelay, J. (2010). Digital image forensics: a booklet for
beginners. Multimedia Tools And Applications, 51(1), 133-162. doi: 10.1007/s11042-
010-0620-1
Richard, G., & Roussev, V. (2006). Next-generation digital forensics. Communications Of
The ACM, 49(2), 76. doi: 10.1145/1113034.1113074
Shrivastava, A., Payal, N., Rastogi, A., & Tiwari, A. (2013). Digital Forensic Investigation
Development Model. 2013 5Th International Conference On Computational Intelligence
And Communication Networks. doi: 10.1109/cicn.2013.115
van Beek, H., van Eijk, E., van Baar, R., Ugen, M., Bodde, J., & Siemelink, A. (2015).
Digital forensics as a service: Game on. Digital Investigation, 15, 20-38. doi:
10.1016/j.diin.2015.07.004

1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



