University Report: Digital Forensics and Incident Response Analysis
VerifiedAdded on 2022/09/12
|6
|962
|17
Report
AI Summary
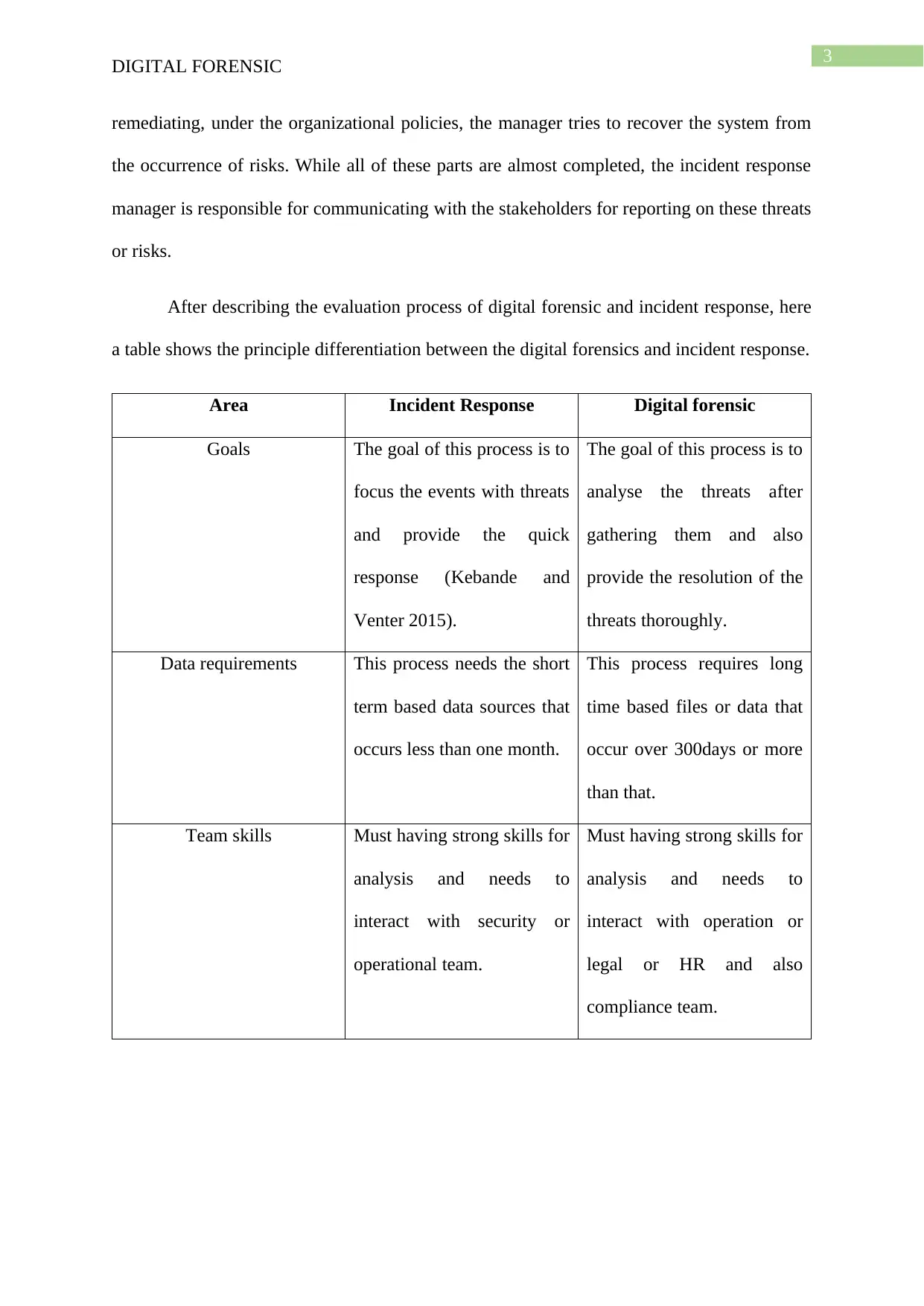
This report delves into the concepts of digital forensics and incident response (DFIR), crucial components of computer security. It defines digital forensics as the process of investigating digital components to identify illegal activities or cyberattacks, emphasizing the skills required of IT professionals to detect threats. Incident response is presented as a structured process for identifying and managing security incidents, involving preparation, identification, containment, remediation, recovery, and reporting. The report evaluates the DFIR process through a six-step framework, highlighting the importance of preparation, identification of risks, containment of threats, remediation, system recovery, and stakeholder communication. A table is included to differentiate between incident response and digital forensics, comparing their goals, data requirements, and team skills. The conclusion emphasizes the importance of these processes for organizational security, recommending the involvement of the incident response team in the operational phase for effective threat assessment and information recovery.
1 out of 6












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)