Digital Forensics Report: Investigating Patent Leakage with FTK Imager
VerifiedAdded on 2023/06/01
|26
|2973
|408
Report
AI Summary
This digital forensic report investigates a case of suspected patent information leakage from m57.biz, a patent search company. The report details the methodology used, which includes forensic procurement, investigation, and reporting, with a focus on using FTK Imager to analyze a forensic image of the suspect's (Jo's) computer. The analysis identifies various files, including orphan files, root files, unallocated space files, and hidden files, with a particular focus on the contents of Jo's folder, which contains potentially sensitive patent information. The report aims to determine if Jo leaked design information to a third-party organization, Asian Entertainment Corporation, and the potential consequences based on the evidence found. The report concludes by highlighting the security issues faced by data frameworks and the importance of digital forensics in identifying deleted files and security breaches.

Forensic Computing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
The main objective of this project is to create the digital forensic report for the provided
case. The m57.biz organization refers to a company of patent search which intends to
researche the patent information for its clients. This organization generally verifies the
novelty of patent for the business of patent searches and for invalidating the a available
patents by determining it priorly. This organization has four employees such as, two patent
researchers, IT administrator and CEO. This firm is planning to hire additional employees at
a later date, once the further clients are booked. The employees of this organization strictly
work onsite and perform the most of the business exchanges through email. Also the
employees work in windows operating system, despite tat their preference varies with
software such as, Thunderbird or outlook. The information of the design is very sensitive and
has great potential value. So, the clients are assigned to only one research staff for one case
and the data copy is not allowed. Moreover, no sharing of contacts is allowed. The contact
and data are strictly forbidden to take data offsite. The information of the pre-patent design is
only on the hard drive of the employee assigned to the clients. Such information’s backup is
performed weekly, by Terry. But, one of the researcher staff (Jo) was leaking the suspicion of
the details for certain patents to the third party organization. So, our cyber security
organization required to identify the leaking design information, by using the forensics tool.
Here, we are using the FTK imager tool to identify the leaking design information. The cyber
security organization was contacted by Mr Pat McGoo, to identifying the concern, where one
of their patent researcher is under suspicion of leaking the design information, for certain
patents to the third party organization. So, the user need to prepare digital forensic report for
this above case and analysis the provided forensic image file.
1
The main objective of this project is to create the digital forensic report for the provided
case. The m57.biz organization refers to a company of patent search which intends to
researche the patent information for its clients. This organization generally verifies the
novelty of patent for the business of patent searches and for invalidating the a available
patents by determining it priorly. This organization has four employees such as, two patent
researchers, IT administrator and CEO. This firm is planning to hire additional employees at
a later date, once the further clients are booked. The employees of this organization strictly
work onsite and perform the most of the business exchanges through email. Also the
employees work in windows operating system, despite tat their preference varies with
software such as, Thunderbird or outlook. The information of the design is very sensitive and
has great potential value. So, the clients are assigned to only one research staff for one case
and the data copy is not allowed. Moreover, no sharing of contacts is allowed. The contact
and data are strictly forbidden to take data offsite. The information of the pre-patent design is
only on the hard drive of the employee assigned to the clients. Such information’s backup is
performed weekly, by Terry. But, one of the researcher staff (Jo) was leaking the suspicion of
the details for certain patents to the third party organization. So, our cyber security
organization required to identify the leaking design information, by using the forensics tool.
Here, we are using the FTK imager tool to identify the leaking design information. The cyber
security organization was contacted by Mr Pat McGoo, to identifying the concern, where one
of their patent researcher is under suspicion of leaking the design information, for certain
patents to the third party organization. So, the user need to prepare digital forensic report for
this above case and analysis the provided forensic image file.
1

Table of Contents
Introduction.........................................................................................................................................3
Methodology Details............................................................................................................................4
Analysis and Findings.........................................................................................................................5
Summary and Conclusion.................................................................................................................23
References..........................................................................................................................................25
2
Introduction.........................................................................................................................................3
Methodology Details............................................................................................................................4
Analysis and Findings.........................................................................................................................5
Summary and Conclusion.................................................................................................................23
References..........................................................................................................................................25
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
In this report, the primary objective is to create the digital forensics report for provided
case. The m57.biz organization is a patent search company that, researches the patent
information for their clients. This organization generally verifies the novelty of patent for the
business of patent searches and to invalidate the existing patents by determining it priorly.
This organization has four employees such as, two patent researchers, IT administrator and
CEO. This firm is planning to hire additional employees at a later date, once the further
clients are booked. The employees of this organization strictly work onsite and perform the
most of the business exchanges through email. Also the employees work in windows
operating system, despite tat their preference varies with software such as, Thunderbird or
outlook. The information of the design is very sensitive and has great potential value. So, the
clients are assigned to only one research staff for one case and the data copy is not allowed.
Moreover, no sharing of contacts is allowed. The contact and data are strictly forbidden to
take data offsite. The information of the pre-patent design is only on the hard drive of the
employee assigned to the clients. Such information’s backup is performed weekly, by Terry.
But, one of the researcher staff (Jo) was leaking the suspicion of the details for certain patents
to the third party organization. So, our cyber security organization required to identify the
leaking design information, by using the forensics tool. Here, we are using the FTK imager
tool to identify the leaking design information. The cyber security organization was contacted
by Mr Pat McGoo, to identifying the concern, where one of their patent researcher is under
suspicion of leaking the design information, for certain patents to the third party organization.
Mr. Pat McGoo provides the below information.
Firstly, Jo has become the suspect, so Jo’s work computer was temporarily seized and
the computer hard disk was removed. The forensics image was created by Terry on
December 21st 2009. Jo's subject matter is on PC recreations, there have been no issues with
these licenses until this point. Amusement structure materials would be typical to discover on
the plate. The Wuzbro Toy Company (m57.biz customer and proprietor of toy plans and
licenses) has whined that three ongoing toy structures have had relatively indistinguishable
plans protected by their rivals, Asian Entertainment Corporation. No part of these three plans
must be found on Jo's system and, contingent on the degree of evidence found on Jo's plate,
the accompanying outcomes are conceivable such as, Cautioning and Probation, End of
Employment, Common Lawsuit for Damages and Giving over the case to the nearby police
3
In this report, the primary objective is to create the digital forensics report for provided
case. The m57.biz organization is a patent search company that, researches the patent
information for their clients. This organization generally verifies the novelty of patent for the
business of patent searches and to invalidate the existing patents by determining it priorly.
This organization has four employees such as, two patent researchers, IT administrator and
CEO. This firm is planning to hire additional employees at a later date, once the further
clients are booked. The employees of this organization strictly work onsite and perform the
most of the business exchanges through email. Also the employees work in windows
operating system, despite tat their preference varies with software such as, Thunderbird or
outlook. The information of the design is very sensitive and has great potential value. So, the
clients are assigned to only one research staff for one case and the data copy is not allowed.
Moreover, no sharing of contacts is allowed. The contact and data are strictly forbidden to
take data offsite. The information of the pre-patent design is only on the hard drive of the
employee assigned to the clients. Such information’s backup is performed weekly, by Terry.
But, one of the researcher staff (Jo) was leaking the suspicion of the details for certain patents
to the third party organization. So, our cyber security organization required to identify the
leaking design information, by using the forensics tool. Here, we are using the FTK imager
tool to identify the leaking design information. The cyber security organization was contacted
by Mr Pat McGoo, to identifying the concern, where one of their patent researcher is under
suspicion of leaking the design information, for certain patents to the third party organization.
Mr. Pat McGoo provides the below information.
Firstly, Jo has become the suspect, so Jo’s work computer was temporarily seized and
the computer hard disk was removed. The forensics image was created by Terry on
December 21st 2009. Jo's subject matter is on PC recreations, there have been no issues with
these licenses until this point. Amusement structure materials would be typical to discover on
the plate. The Wuzbro Toy Company (m57.biz customer and proprietor of toy plans and
licenses) has whined that three ongoing toy structures have had relatively indistinguishable
plans protected by their rivals, Asian Entertainment Corporation. No part of these three plans
must be found on Jo's system and, contingent on the degree of evidence found on Jo's plate,
the accompanying outcomes are conceivable such as, Cautioning and Probation, End of
Employment, Common Lawsuit for Damages and Giving over the case to the nearby police
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

office for indictment. So, the user need to prepare a digital forensics report for this case and
analyze the provided forensic image file.
Methodology Details
The security of the created and gathered data is considered as the most multi-dimensional
order, in the present day time of data innovation. The organizations and government on the
whole performs the exercises of data security with the help of computerized measurable
frameworks. The advanced measurable frameworks give administration of principles, rules
and best practices, which are created to keep up data security, in any organization. The
obligations and jobs of people, occurred correspondence among these created jobs, duties of
best administration and utilization of data security is likewise characterized by the assistance
of advanced criminological framework. The entire structure of data security inside any
organization is guaranteed by the actualized computerized measurable framework. Along
these lines, the computerized criminological framework is like, administration framework
which is utilized to keep up and set up the anchored condition for any data framework
(Boddington, 2016).
The required methodology and related procedures for compelling administration of data
security are being set up by these computerized 5 criminological frameworks. The essential
point of all and related procedures for the powerful administration of data security built up by
the computerized legal framework are, to give legitimate security to all the data resources of
any organization. This likewise, intends to make constant upgrades in security of any
organization. These worldwide measures give a methodology of hazard administration and
administration control on generally speaking framework by observing, foundation, activities,
execution, enhancements and support of data security in the advanced scientific framework.
The strategies, structure of organization, obligations, exercises of arranging, techniques,
related practices and utilized assets are characterized by these principles for helping
computerized criminological framework. As it is a legal and logical procedure of
examination, thus the Forensic procurement as a piece of computerized measurable
framework requires execution of the following advances:
Procurement: In this progression, the seized procedure for any show is finished. The
confirmation of the obtained picture is finished by making use of MD5 hash
capacities or SHA-1. By utilizing these MD5 hash capacities or SHA-1, the first
4
analyze the provided forensic image file.
Methodology Details
The security of the created and gathered data is considered as the most multi-dimensional
order, in the present day time of data innovation. The organizations and government on the
whole performs the exercises of data security with the help of computerized measurable
frameworks. The advanced measurable frameworks give administration of principles, rules
and best practices, which are created to keep up data security, in any organization. The
obligations and jobs of people, occurred correspondence among these created jobs, duties of
best administration and utilization of data security is likewise characterized by the assistance
of advanced criminological framework. The entire structure of data security inside any
organization is guaranteed by the actualized computerized measurable framework. Along
these lines, the computerized criminological framework is like, administration framework
which is utilized to keep up and set up the anchored condition for any data framework
(Boddington, 2016).
The required methodology and related procedures for compelling administration of data
security are being set up by these computerized 5 criminological frameworks. The essential
point of all and related procedures for the powerful administration of data security built up by
the computerized legal framework are, to give legitimate security to all the data resources of
any organization. This likewise, intends to make constant upgrades in security of any
organization. These worldwide measures give a methodology of hazard administration and
administration control on generally speaking framework by observing, foundation, activities,
execution, enhancements and support of data security in the advanced scientific framework.
The strategies, structure of organization, obligations, exercises of arranging, techniques,
related practices and utilized assets are characterized by these principles for helping
computerized criminological framework. As it is a legal and logical procedure of
examination, thus the Forensic procurement as a piece of computerized measurable
framework requires execution of the following advances:
Procurement: In this progression, the seized procedure for any show is finished. The
confirmation of the obtained picture is finished by making use of MD5 hash
capacities or SHA-1. By utilizing these MD5 hash capacities or SHA-1, the first
4

condition of the gathered proof is again guaranteed, confirmed and is known as
hashing. If there is close down of framework for the criminological examination
which isn't conceivable, at that point, blend of e-revelation forms and advanced
scientific obtaining is being conveyed for finding the confirmations in huge picture
drives. The e-disclosure procedures can likewise make proof gathering for the
computerized scientific through record servers or cloud assets (CYBERCRIME AND
DIGITAL FORENSICS, 2018).
Investigation: While securing process is completed, the proof distinguishing proof via
a created speculation of tempered information is directed. In the following
investigation, the natural systems are pursued that makes the ID of proof hardening
records by making a comprehensive pursuit by filling the document gaps. This
examination uses the quantity of tools dependent on various philosophies for making
recuperation of temper material to start. The tool such as FTK is used here by the
legal inspectors for seeing and recuperating the temper information records. The
examination of these information recuperation typically changes for pictures,
archives, messages and web history or for the visit logs. The recuperation of
information is characterized with the space that is available from the used plate,
erased spaces and the reserve documents of the working system. Catchphrase seeking
is the most ordinarily utilized strategy for proof recuperation from procured picture
records. A particular byte set of picture documents are additionally utilized for
characterizing the start and completion of any investigation process of the advanced
measurable. When the ID process is completed, rebuilding of the deleted information
document starts. The hash marks are the parts which are used by the scientific
analysts via, various tools to contrast the DRS and the deleted documents.
Revealing: Once the examination procedure is completed, the gathered specialized
individuals and the non-specialized confirmations are accounted for the organization,
for the ID of deleted documents and for the occured misfortunes (Pollitt & Shenoi,
2010).
Analysis and Findings
There are such significant number of open source tools accessible in the market, to make
usage of advanced measurable erased documents, where the FTK Imager 3.2.0.0 is one of
5
hashing. If there is close down of framework for the criminological examination
which isn't conceivable, at that point, blend of e-revelation forms and advanced
scientific obtaining is being conveyed for finding the confirmations in huge picture
drives. The e-disclosure procedures can likewise make proof gathering for the
computerized scientific through record servers or cloud assets (CYBERCRIME AND
DIGITAL FORENSICS, 2018).
Investigation: While securing process is completed, the proof distinguishing proof via
a created speculation of tempered information is directed. In the following
investigation, the natural systems are pursued that makes the ID of proof hardening
records by making a comprehensive pursuit by filling the document gaps. This
examination uses the quantity of tools dependent on various philosophies for making
recuperation of temper material to start. The tool such as FTK is used here by the
legal inspectors for seeing and recuperating the temper information records. The
examination of these information recuperation typically changes for pictures,
archives, messages and web history or for the visit logs. The recuperation of
information is characterized with the space that is available from the used plate,
erased spaces and the reserve documents of the working system. Catchphrase seeking
is the most ordinarily utilized strategy for proof recuperation from procured picture
records. A particular byte set of picture documents are additionally utilized for
characterizing the start and completion of any investigation process of the advanced
measurable. When the ID process is completed, rebuilding of the deleted information
document starts. The hash marks are the parts which are used by the scientific
analysts via, various tools to contrast the DRS and the deleted documents.
Revealing: Once the examination procedure is completed, the gathered specialized
individuals and the non-specialized confirmations are accounted for the organization,
for the ID of deleted documents and for the occured misfortunes (Pollitt & Shenoi,
2010).
Analysis and Findings
There are such significant number of open source tools accessible in the market, to make
usage of advanced measurable erased documents, where the FTK Imager 3.2.0.0 is one of
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
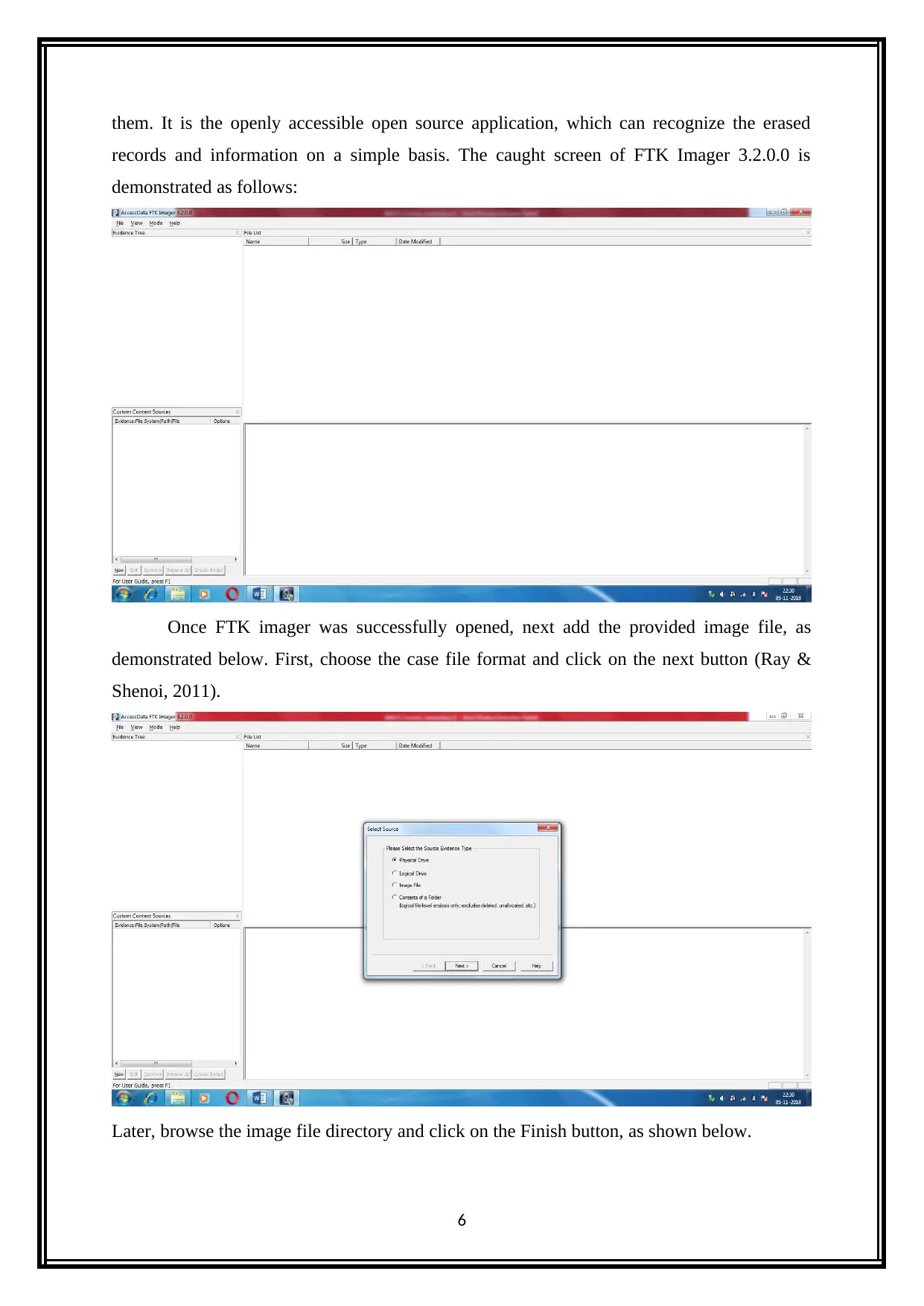
them. It is the openly accessible open source application, which can recognize the erased
records and information on a simple basis. The caught screen of FTK Imager 3.2.0.0 is
demonstrated as follows:
Once FTK imager was successfully opened, next add the provided image file, as
demonstrated below. First, choose the case file format and click on the next button (Ray &
Shenoi, 2011).
Later, browse the image file directory and click on the Finish button, as shown below.
6
records and information on a simple basis. The caught screen of FTK Imager 3.2.0.0 is
demonstrated as follows:
Once FTK imager was successfully opened, next add the provided image file, as
demonstrated below. First, choose the case file format and click on the next button (Ray &
Shenoi, 2011).
Later, browse the image file directory and click on the Finish button, as shown below.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
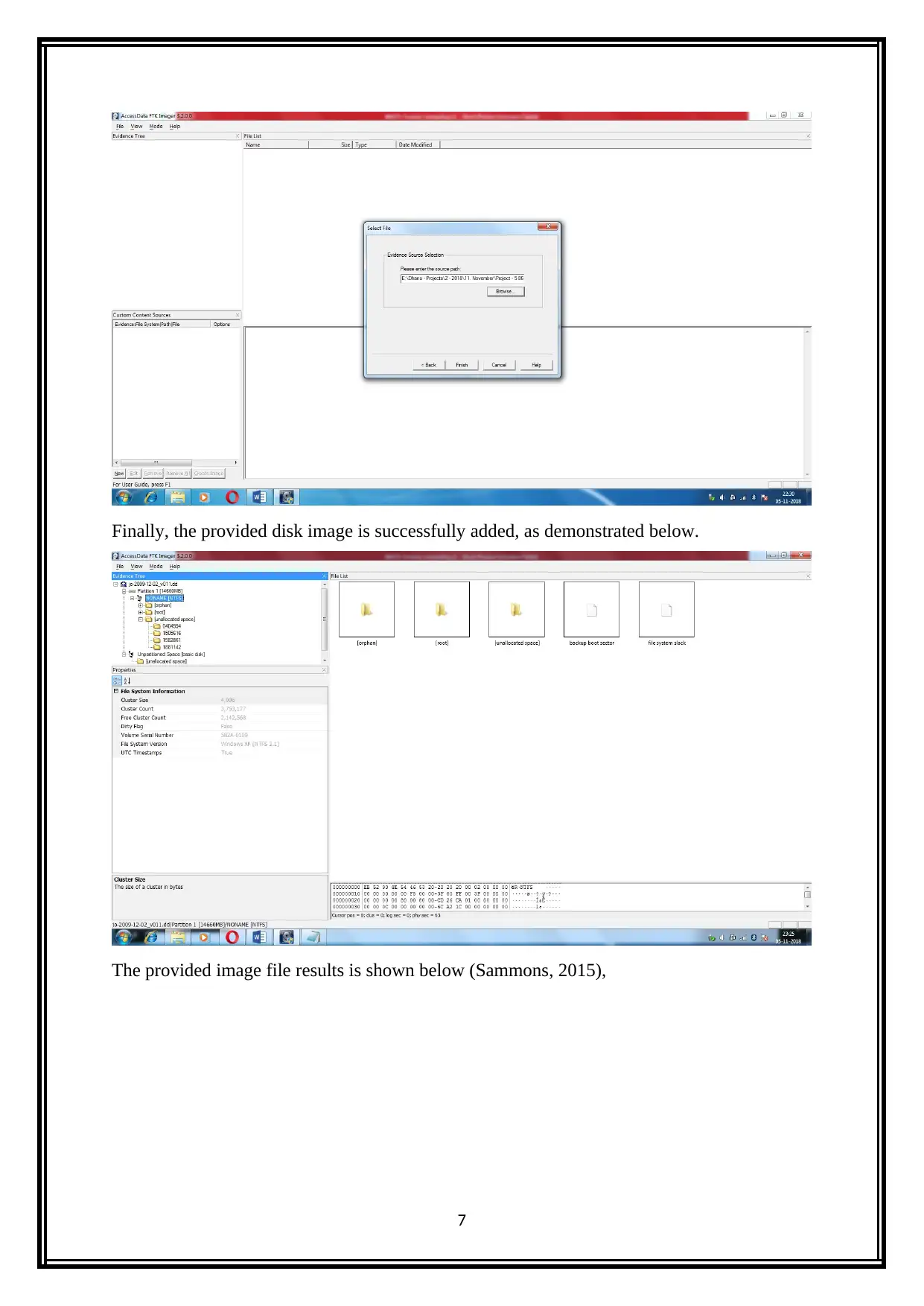
Finally, the provided disk image is successfully added, as demonstrated below.
The provided image file results is shown below (Sammons, 2015),
7
The provided image file results is shown below (Sammons, 2015),
7
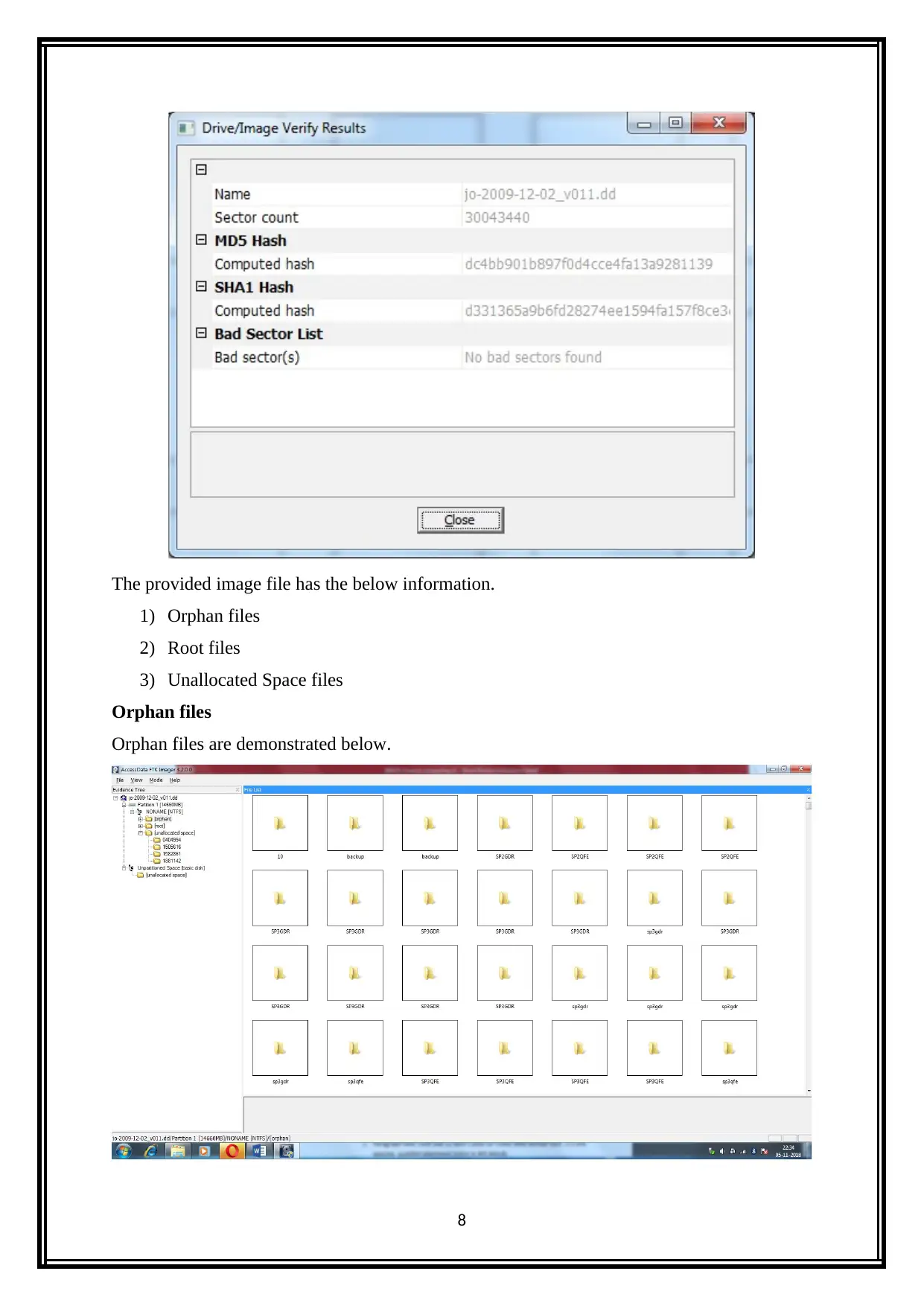
The provided image file has the below information.
1) Orphan files
2) Root files
3) Unallocated Space files
Orphan files
Orphan files are demonstrated below.
8
1) Orphan files
2) Root files
3) Unallocated Space files
Orphan files
Orphan files are demonstrated below.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
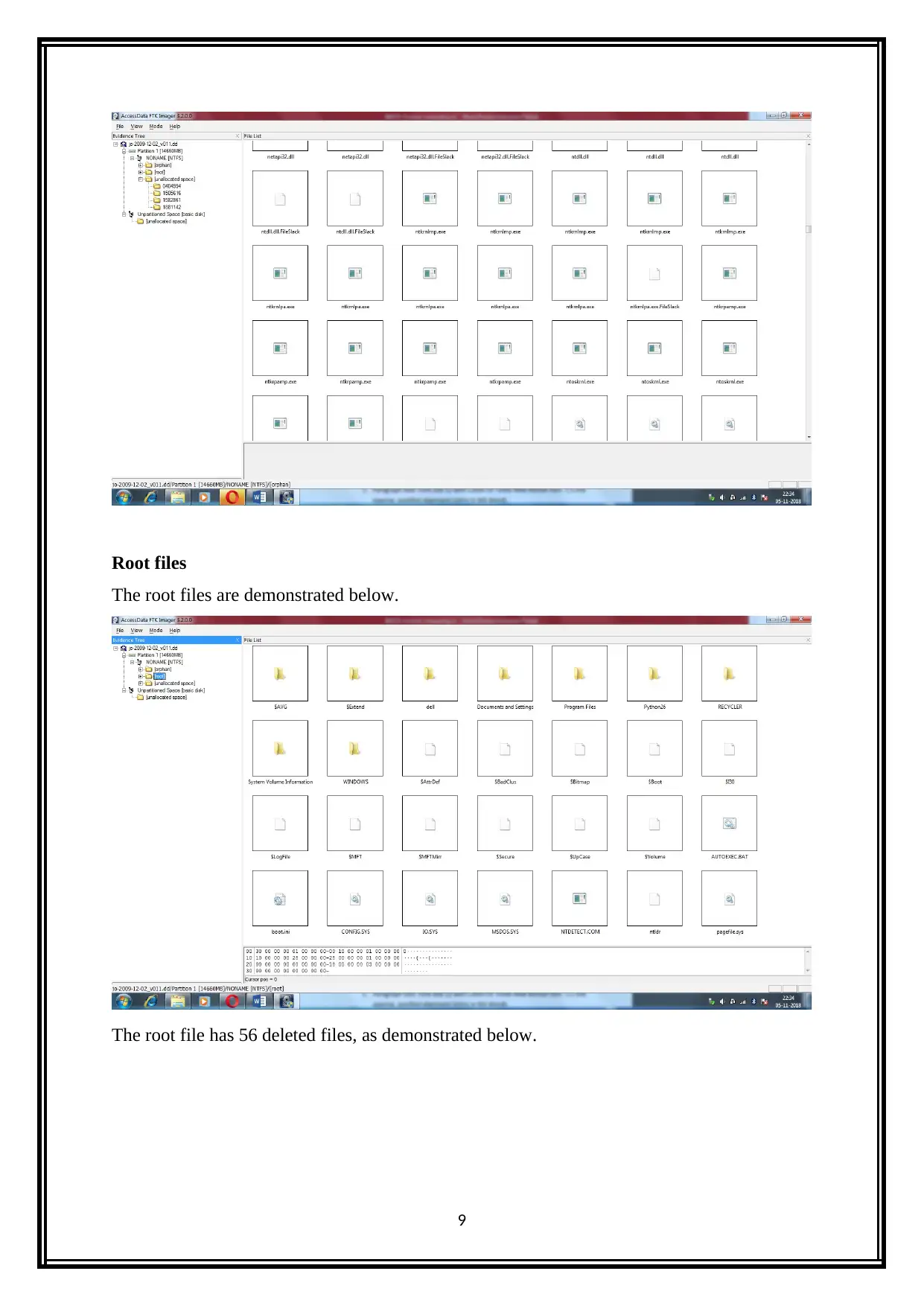
Root files
The root files are demonstrated below.
The root file has 56 deleted files, as demonstrated below.
9
The root files are demonstrated below.
The root file has 56 deleted files, as demonstrated below.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
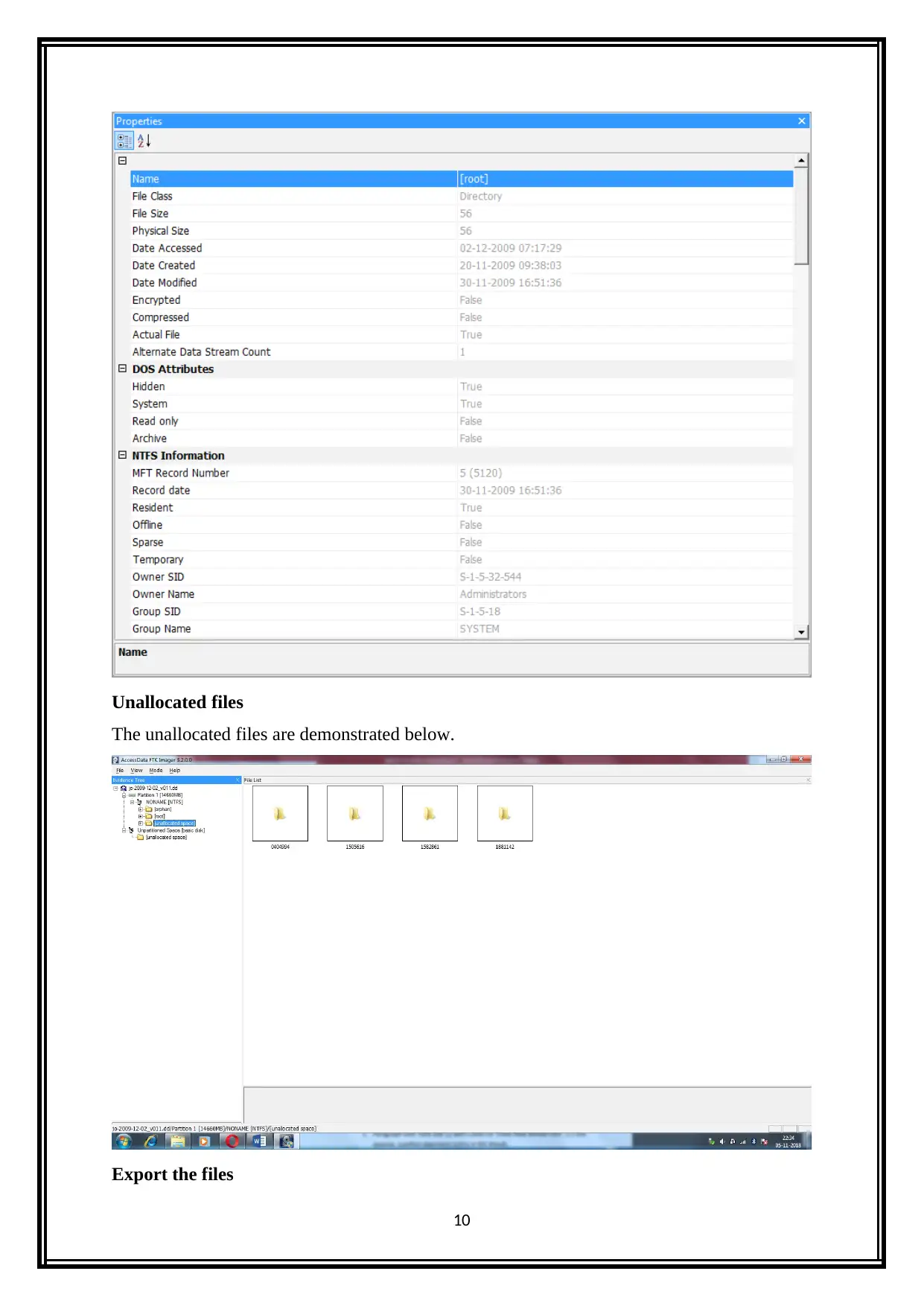
Unallocated files
The unallocated files are demonstrated below.
Export the files
10
The unallocated files are demonstrated below.
Export the files
10
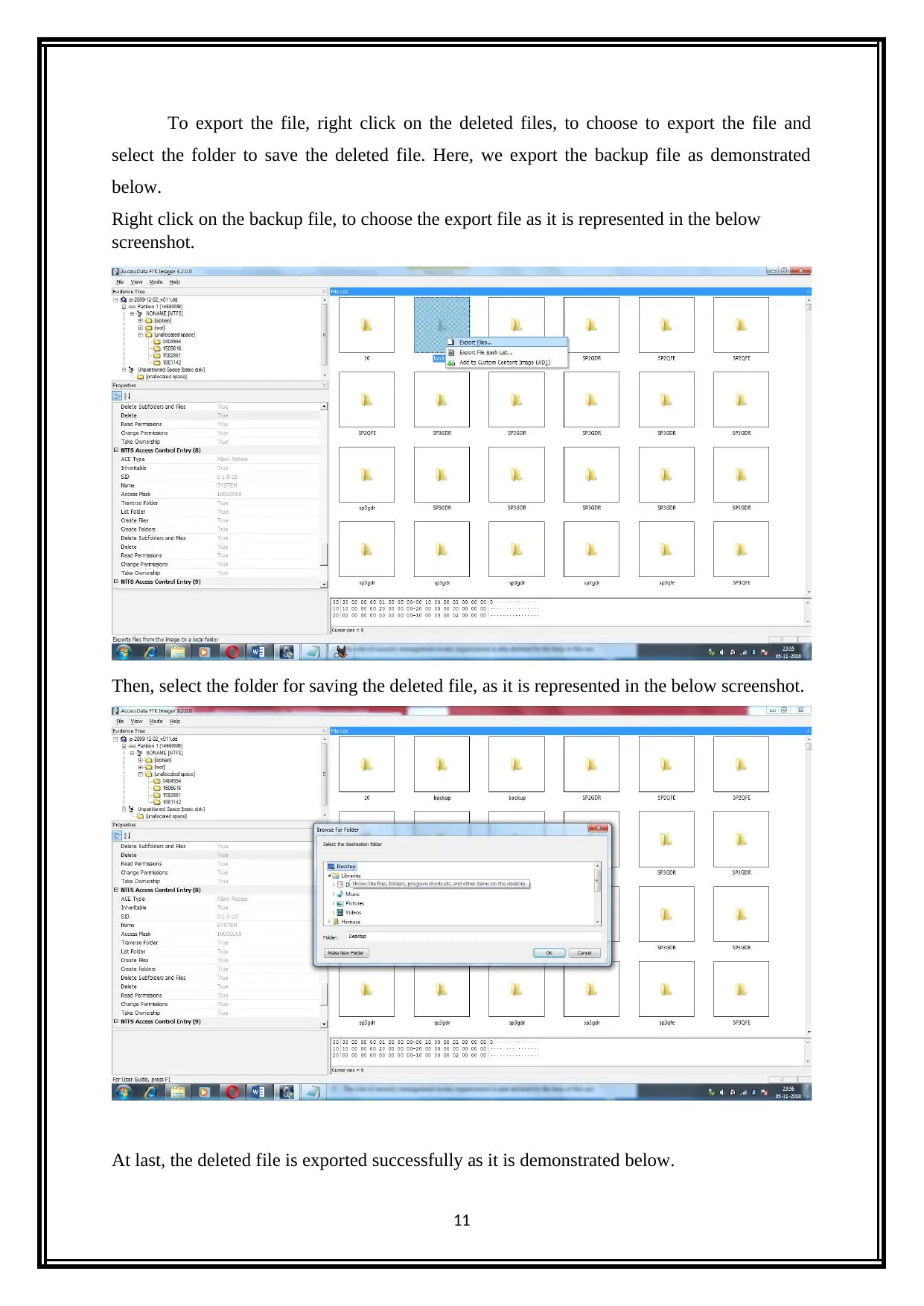
To export the file, right click on the deleted files, to choose to export the file and
select the folder to save the deleted file. Here, we export the backup file as demonstrated
below.
Right click on the backup file, to choose the export file as it is represented in the below
screenshot.
Then, select the folder for saving the deleted file, as it is represented in the below screenshot.
At last, the deleted file is exported successfully as it is demonstrated below.
11
select the folder to save the deleted file. Here, we export the backup file as demonstrated
below.
Right click on the backup file, to choose the export file as it is represented in the below
screenshot.
Then, select the folder for saving the deleted file, as it is represented in the below screenshot.
At last, the deleted file is exported successfully as it is demonstrated below.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.