Digital Forensic Investigation: USB Drive Data Recovery and Analysis
VerifiedAdded on 2021/05/27
|30
|2353
|206
Practical Assignment
AI Summary
This assignment details a digital forensic investigation involving a USB drive suspected of containing evidence related to the sale of counterfeit ISIC cards. The process begins with obtaining a forensic image of the USB drive and using tools like Autopsy and WinMD5 for analysis. The investigation includes creating a case file, conducting an initial survey using keyword searches, and analyzing unallocated space and carved files to recover potential evidence. Documentation is meticulously maintained, and the assignment explores the evidence suggesting the counterfeiting of ISIC cards, potential knowledge of illegal activities, and the identification of customers. The analysis aims to reconstruct activities and uncover hidden data, providing a comprehensive overview of the digital forensic process.

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DIGITAL FORENSIC
TECHNOLOGY
1
TECHNOLOGY
1

Table of Contents
1 Introduction.......................................................................................................................2
2 Analysis Tool.....................................................................................................................2
3 Investigation......................................................................................................................2
3.1 Creating a case file using Autopsy tool....................................................................3
3.2 Initial Survey..............................................................................................................7
3.3 Documentation Phase..............................................................................................14
3.4 Search for evidence..................................................................................................20
4 Conclusion.......................................................................................................................25
References...............................................................................................................................26
2
1 Introduction.......................................................................................................................2
2 Analysis Tool.....................................................................................................................2
3 Investigation......................................................................................................................2
3.1 Creating a case file using Autopsy tool....................................................................3
3.2 Initial Survey..............................................................................................................7
3.3 Documentation Phase..............................................................................................14
3.4 Search for evidence..................................................................................................20
4 Conclusion.......................................................................................................................25
References...............................................................................................................................26
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1 Introduction
The main objective of this project is to retrieve a forensic image of the USB data
storage device. Farayi is suspected of selling counterfeit International Student Identity Cards
to people who are not entitled to claim the discounts this card brings. An undercover sting
operation was setup to catch Farayi in the act of selling his counterfeit goods. Farayi
attempted to sell a counterfeit ISIC card to an undercover officer who was part of the sting
operation. After being arrested and questioned at the local police station, Farayi provided a
USB data stick to be further examined. Under questioning Farayi has stated that all the
evidence that can be found is on this USB data stick. This USB storage device has been
processed by a forensic imaging technician and the forensic image has been obtained. So I
have to recover the forensic image of the USB data storage device. Then the copied Data in
USB will be determined. The investigation will be carried out to determine that the hidden
data in USB, the reasons and facts behind the theft.
2 Analysis Tool
This analysis using two main tool to retrieve a forensic image of the USB data storage device.
Autopsy
WinMD5
3 Investigation
Data recovery is might be helpful for examination in a wide range of ways. A few Data
stay introduce even after Data erasure or USB repartitioning (Gogolin et al., 2013). Also,
there are numerous alternatives for offenders with specialized know how to shroud Data, for
the most part utilizing a USB supervisor, stenography, encryption and so forth. Discovering,
recuperation and remaking of concealed Data can be an extremely tedious and dreary process,
however sometimes it might create prove that will split the case. So as to completely see how
and why Data stay on a plate, one ought to find out about the idea of putting away Data on a
USB. A USB part is a unit of settled size characterized when record framework is made
(generally 512 bits). More seasoned hard USBs may have some 'squandered' storage room
outwardly tracks, as intelligently each track is partitioned into break even with number of
divisions. It is conceivable sometimes to shroud Data in the space between areas on the
bigger outside tracks. This is known as the division hole. A few Data recuperation
administrations might have the capacity to find and recover Data that is covered up in this
hole. Erased records and slack space When a working framework composes a document to
3
The main objective of this project is to retrieve a forensic image of the USB data
storage device. Farayi is suspected of selling counterfeit International Student Identity Cards
to people who are not entitled to claim the discounts this card brings. An undercover sting
operation was setup to catch Farayi in the act of selling his counterfeit goods. Farayi
attempted to sell a counterfeit ISIC card to an undercover officer who was part of the sting
operation. After being arrested and questioned at the local police station, Farayi provided a
USB data stick to be further examined. Under questioning Farayi has stated that all the
evidence that can be found is on this USB data stick. This USB storage device has been
processed by a forensic imaging technician and the forensic image has been obtained. So I
have to recover the forensic image of the USB data storage device. Then the copied Data in
USB will be determined. The investigation will be carried out to determine that the hidden
data in USB, the reasons and facts behind the theft.
2 Analysis Tool
This analysis using two main tool to retrieve a forensic image of the USB data storage device.
Autopsy
WinMD5
3 Investigation
Data recovery is might be helpful for examination in a wide range of ways. A few Data
stay introduce even after Data erasure or USB repartitioning (Gogolin et al., 2013). Also,
there are numerous alternatives for offenders with specialized know how to shroud Data, for
the most part utilizing a USB supervisor, stenography, encryption and so forth. Discovering,
recuperation and remaking of concealed Data can be an extremely tedious and dreary process,
however sometimes it might create prove that will split the case. So as to completely see how
and why Data stay on a plate, one ought to find out about the idea of putting away Data on a
USB. A USB part is a unit of settled size characterized when record framework is made
(generally 512 bits). More seasoned hard USBs may have some 'squandered' storage room
outwardly tracks, as intelligently each track is partitioned into break even with number of
divisions. It is conceivable sometimes to shroud Data in the space between areas on the
bigger outside tracks. This is known as the division hole. A few Data recuperation
administrations might have the capacity to find and recover Data that is covered up in this
hole. Erased records and slack space When a working framework composes a document to
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
USB, it dispenses a specific number of segments. The quantity of areas designated relies
upon the restrictions of the working framework and setup choices made by the framework
overseer. The areas allotted and their area on the plate are recorded in a registry table for later
access. At the point when the record is erased, the space initially dispensed to it is essentially
set apart as unallocated. The genuine Data stays on the USB (Larson, 2014).
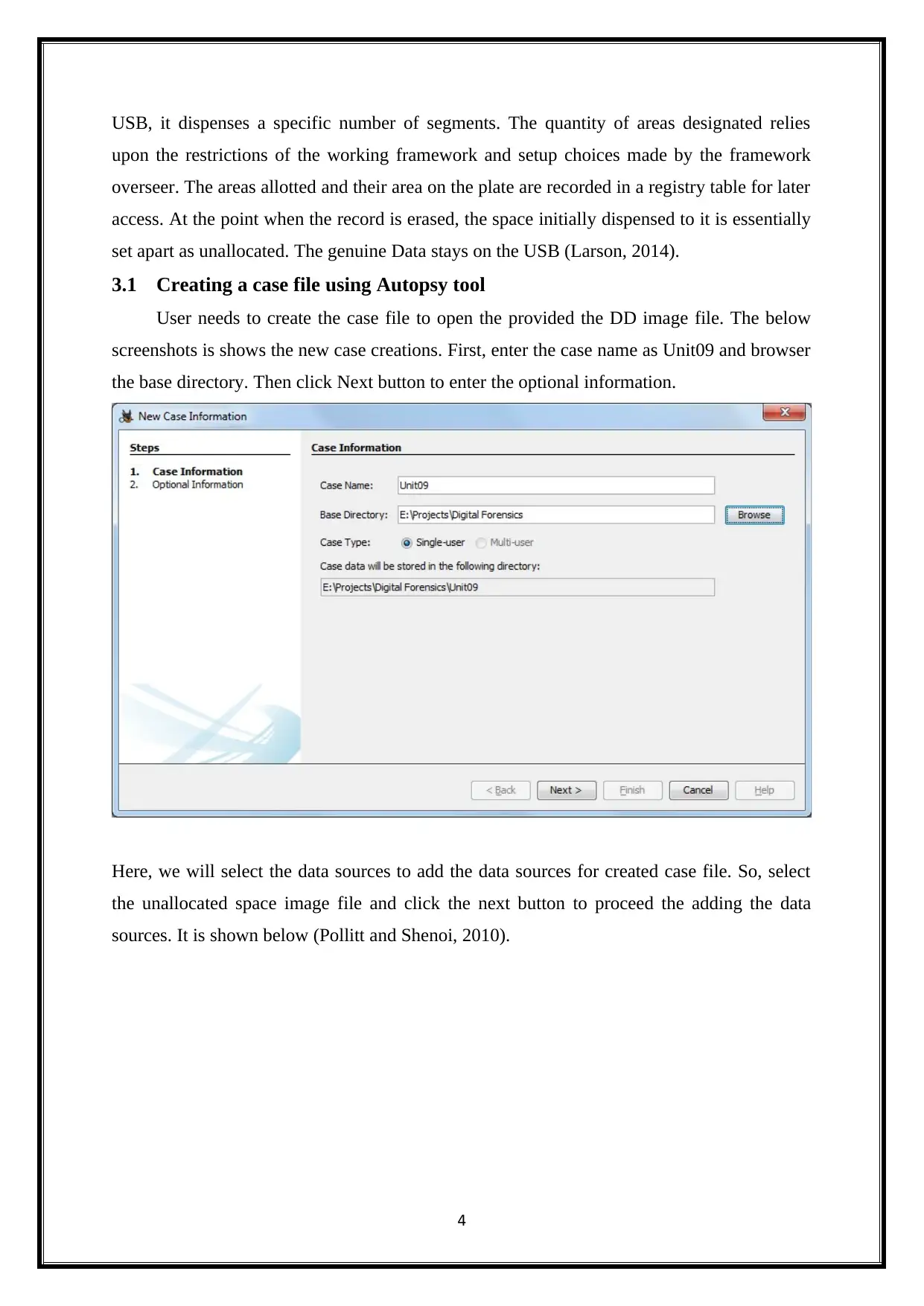
3.1 Creating a case file using Autopsy tool
User needs to create the case file to open the provided the DD image file. The below
screenshots is shows the new case creations. First, enter the case name as Unit09 and browser
the base directory. Then click Next button to enter the optional information.
Here, we will select the data sources to add the data sources for created case file. So, select
the unallocated space image file and click the next button to proceed the adding the data
sources. It is shown below (Pollitt and Shenoi, 2010).
4
upon the restrictions of the working framework and setup choices made by the framework
overseer. The areas allotted and their area on the plate are recorded in a registry table for later
access. At the point when the record is erased, the space initially dispensed to it is essentially
set apart as unallocated. The genuine Data stays on the USB (Larson, 2014).
3.1 Creating a case file using Autopsy tool
User needs to create the case file to open the provided the DD image file. The below
screenshots is shows the new case creations. First, enter the case name as Unit09 and browser
the base directory. Then click Next button to enter the optional information.
Here, we will select the data sources to add the data sources for created case file. So, select
the unallocated space image file and click the next button to proceed the adding the data
sources. It is shown below (Pollitt and Shenoi, 2010).
4
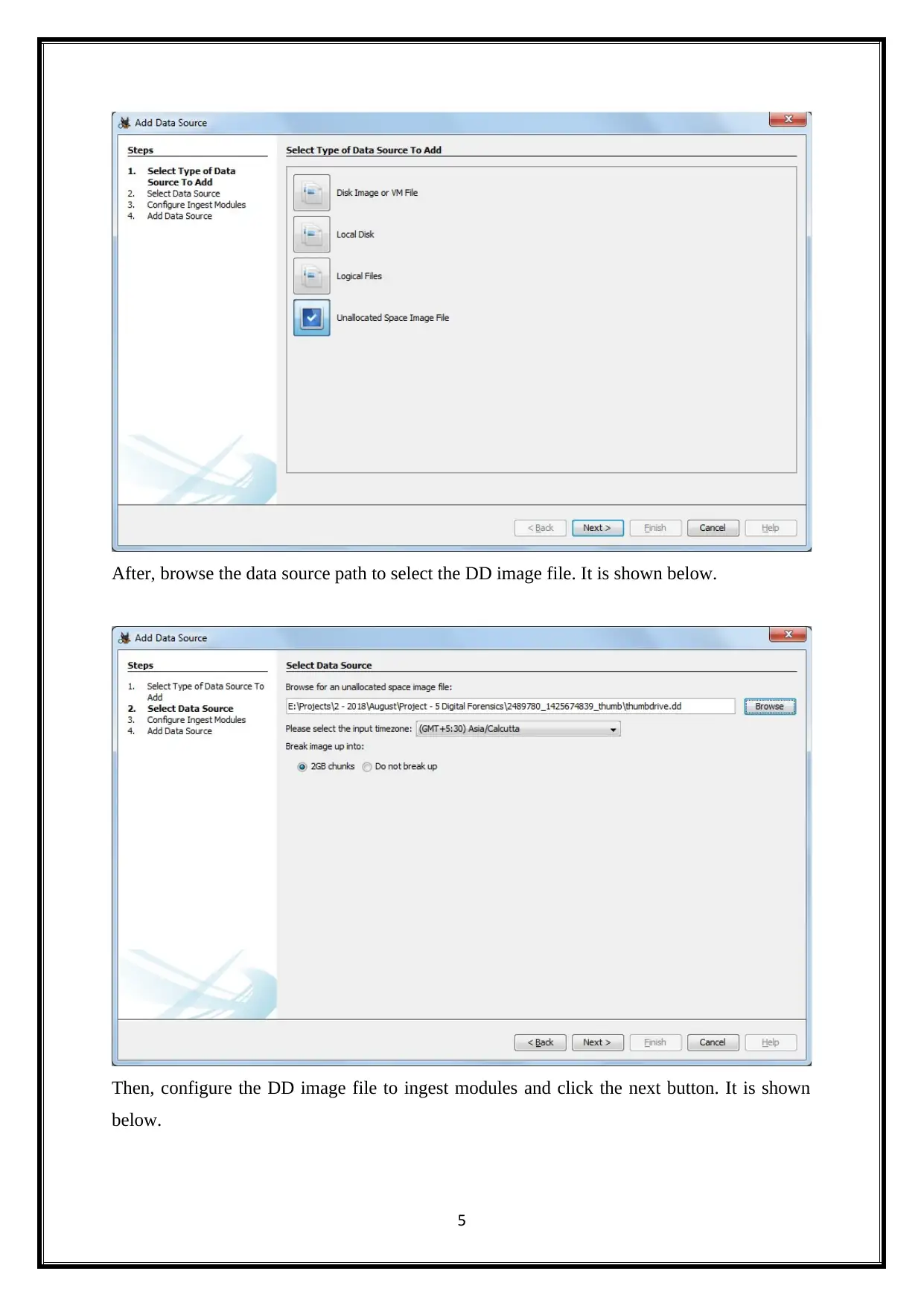
After, browse the data source path to select the DD image file. It is shown below.
Then, configure the DD image file to ingest modules and click the next button. It is shown
below.
5
Then, configure the DD image file to ingest modules and click the next button. It is shown
below.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
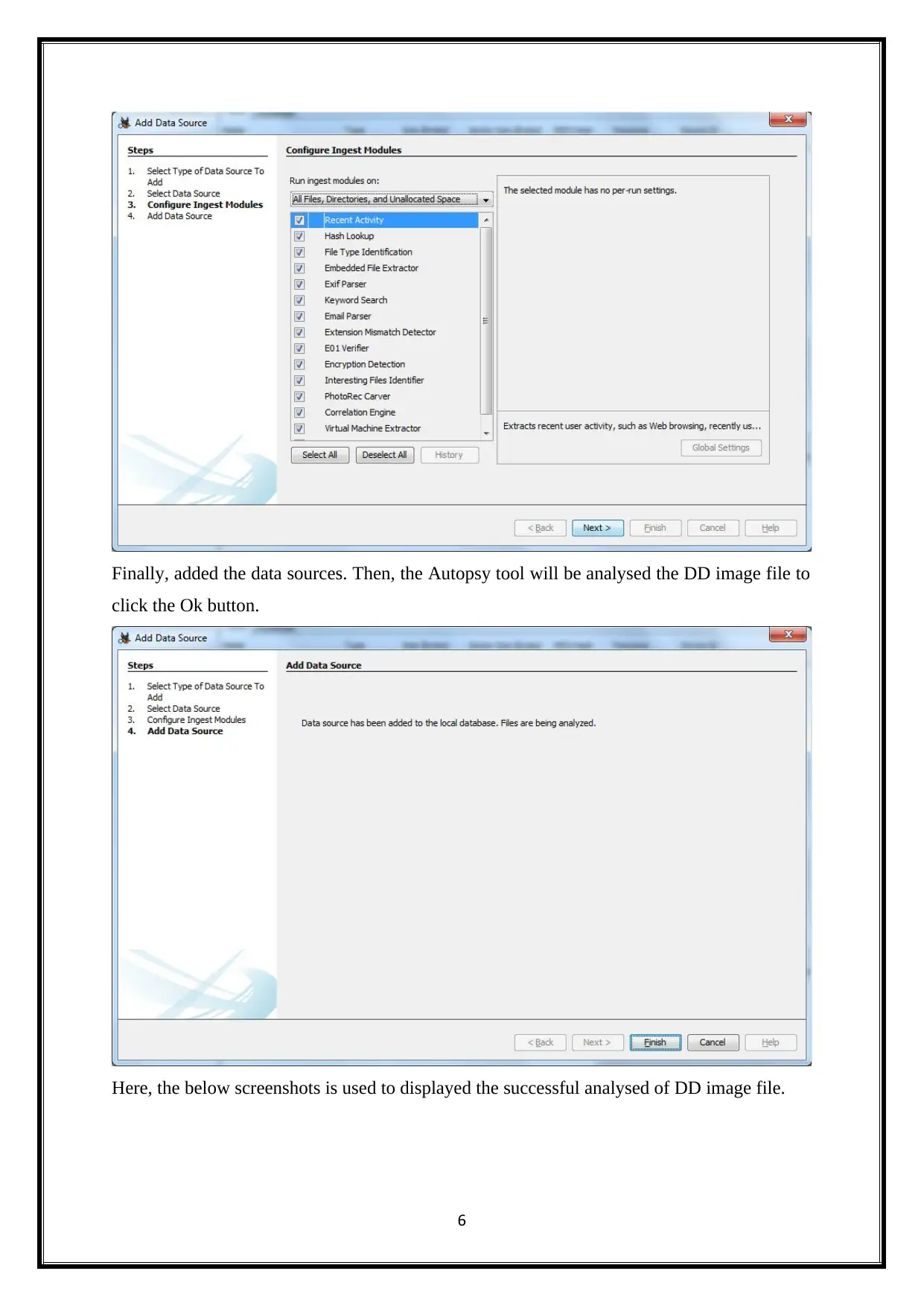
Finally, added the data sources. Then, the Autopsy tool will be analysed the DD image file to
click the Ok button.
Here, the below screenshots is used to displayed the successful analysed of DD image file.
6
click the Ok button.
Here, the below screenshots is used to displayed the successful analysed of DD image file.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
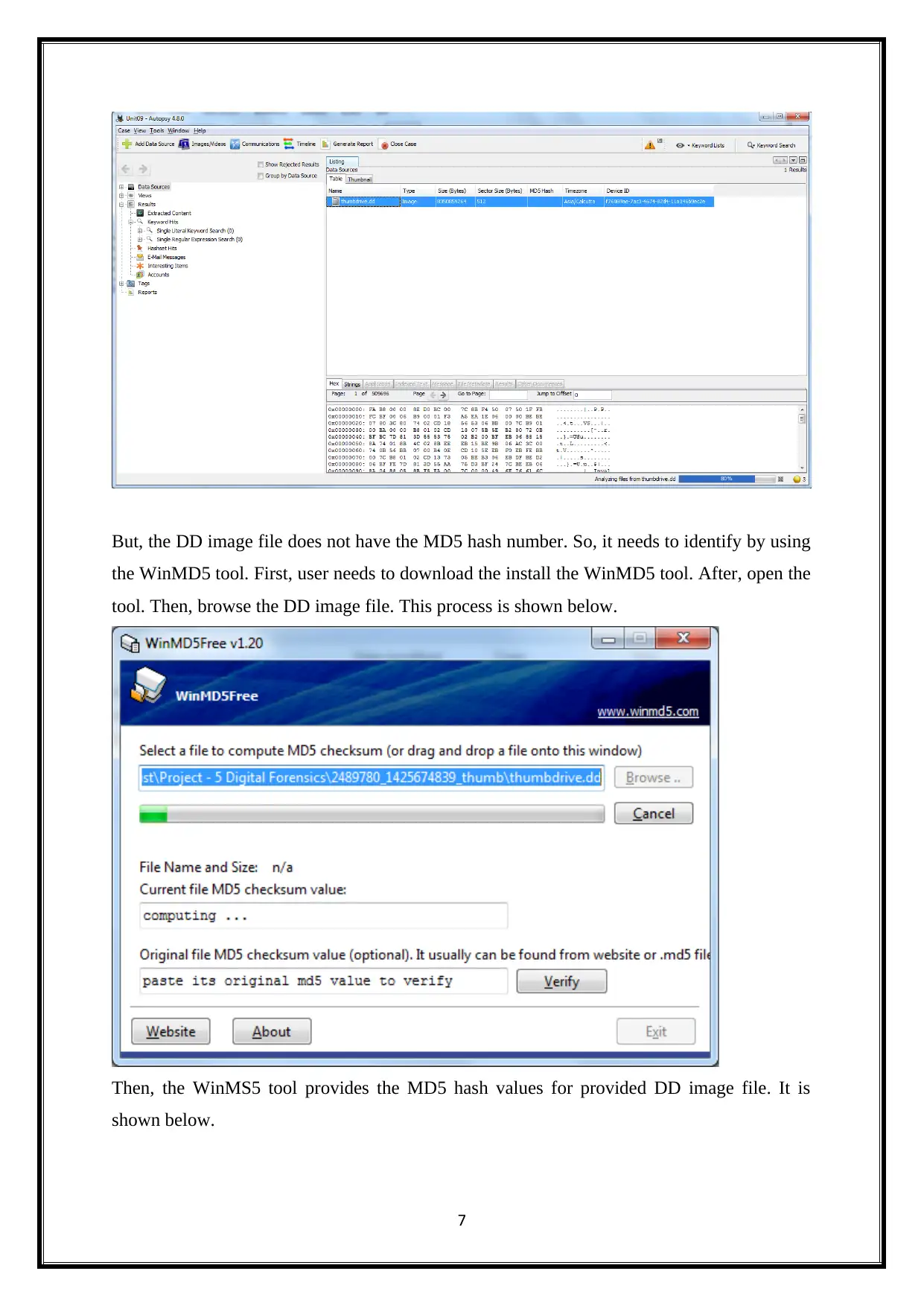
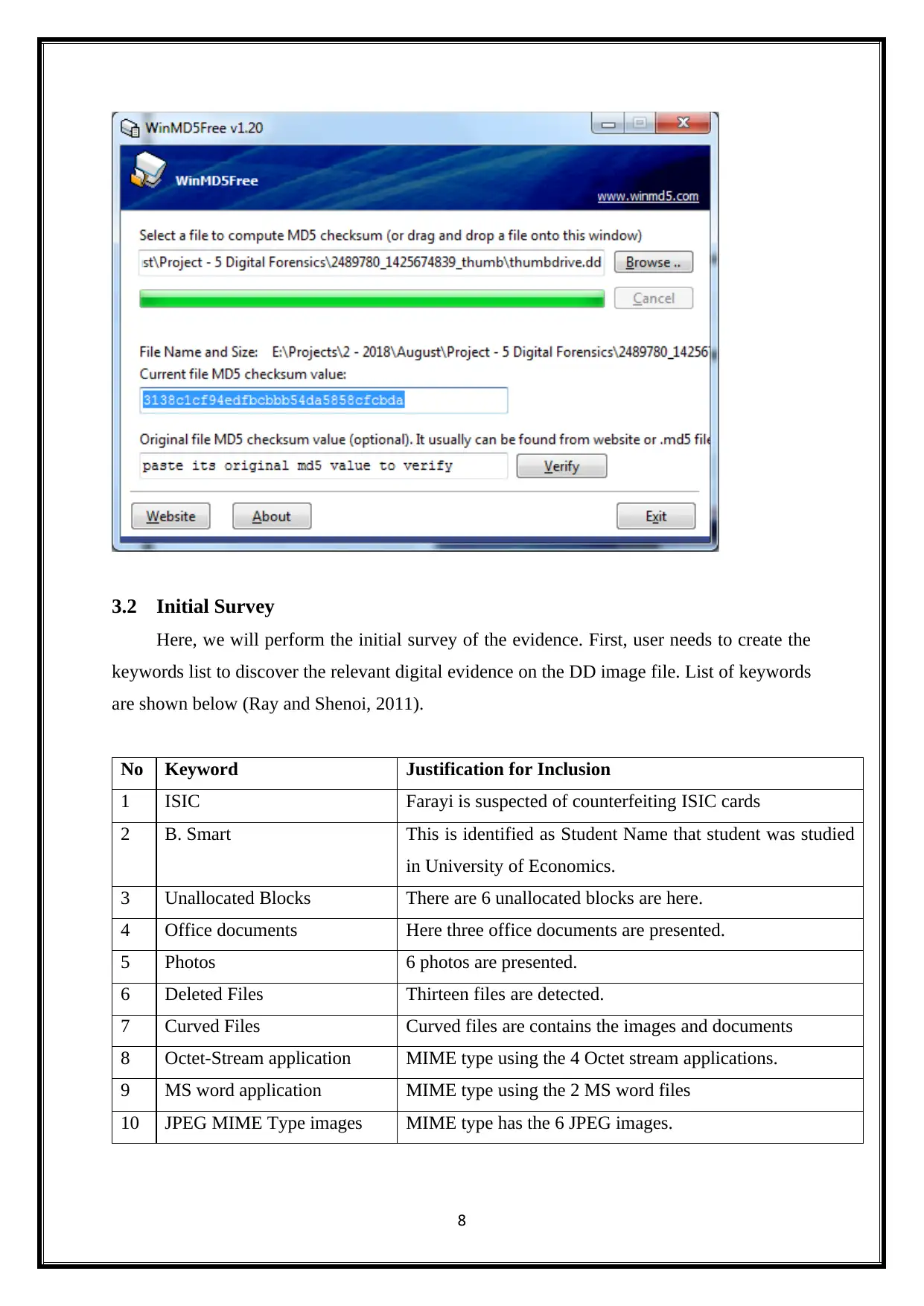
But, the DD image file does not have the MD5 hash number. So, it needs to identify by using
the WinMD5 tool. First, user needs to download the install the WinMD5 tool. After, open the
tool. Then, browse the DD image file. This process is shown below.
Then, the WinMS5 tool provides the MD5 hash values for provided DD image file. It is
shown below.
7
the WinMD5 tool. First, user needs to download the install the WinMD5 tool. After, open the
tool. Then, browse the DD image file. This process is shown below.
Then, the WinMS5 tool provides the MD5 hash values for provided DD image file. It is
shown below.
7
3.2 Initial Survey
Here, we will perform the initial survey of the evidence. First, user needs to create the
keywords list to discover the relevant digital evidence on the DD image file. List of keywords
are shown below (Ray and Shenoi, 2011).
No Keyword Justification for Inclusion
1 ISIC Farayi is suspected of counterfeiting ISIC cards
2 B. Smart This is identified as Student Name that student was studied
in University of Economics.
3 Unallocated Blocks There are 6 unallocated blocks are here.
4 Office documents Here three office documents are presented.
5 Photos 6 photos are presented.
6 Deleted Files Thirteen files are detected.
7 Curved Files Curved files are contains the images and documents
8 Octet-Stream application MIME type using the 4 Octet stream applications.
9 MS word application MIME type using the 2 MS word files
10 JPEG MIME Type images MIME type has the 6 JPEG images.
8
Here, we will perform the initial survey of the evidence. First, user needs to create the
keywords list to discover the relevant digital evidence on the DD image file. List of keywords
are shown below (Ray and Shenoi, 2011).
No Keyword Justification for Inclusion
1 ISIC Farayi is suspected of counterfeiting ISIC cards
2 B. Smart This is identified as Student Name that student was studied
in University of Economics.
3 Unallocated Blocks There are 6 unallocated blocks are here.
4 Office documents Here three office documents are presented.
5 Photos 6 photos are presented.
6 Deleted Files Thirteen files are detected.
7 Curved Files Curved files are contains the images and documents
8 Octet-Stream application MIME type using the 4 Octet stream applications.
9 MS word application MIME type using the 2 MS word files
10 JPEG MIME Type images MIME type has the 6 JPEG images.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
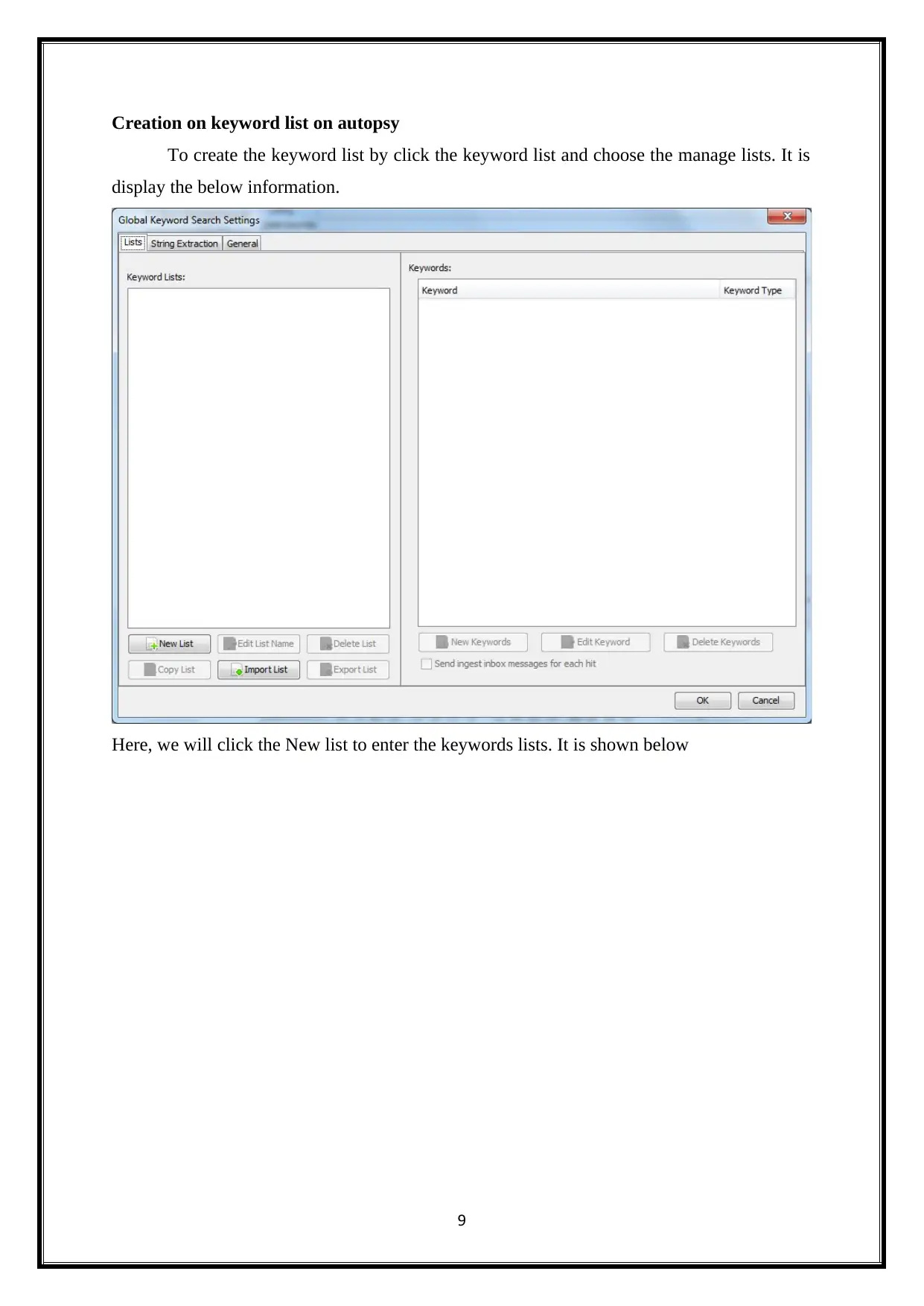
Creation on keyword list on autopsy
To create the keyword list by click the keyword list and choose the manage lists. It is
display the below information.
Here, we will click the New list to enter the keywords lists. It is shown below
9
To create the keyword list by click the keyword list and choose the manage lists. It is
display the below information.
Here, we will click the New list to enter the keywords lists. It is shown below
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
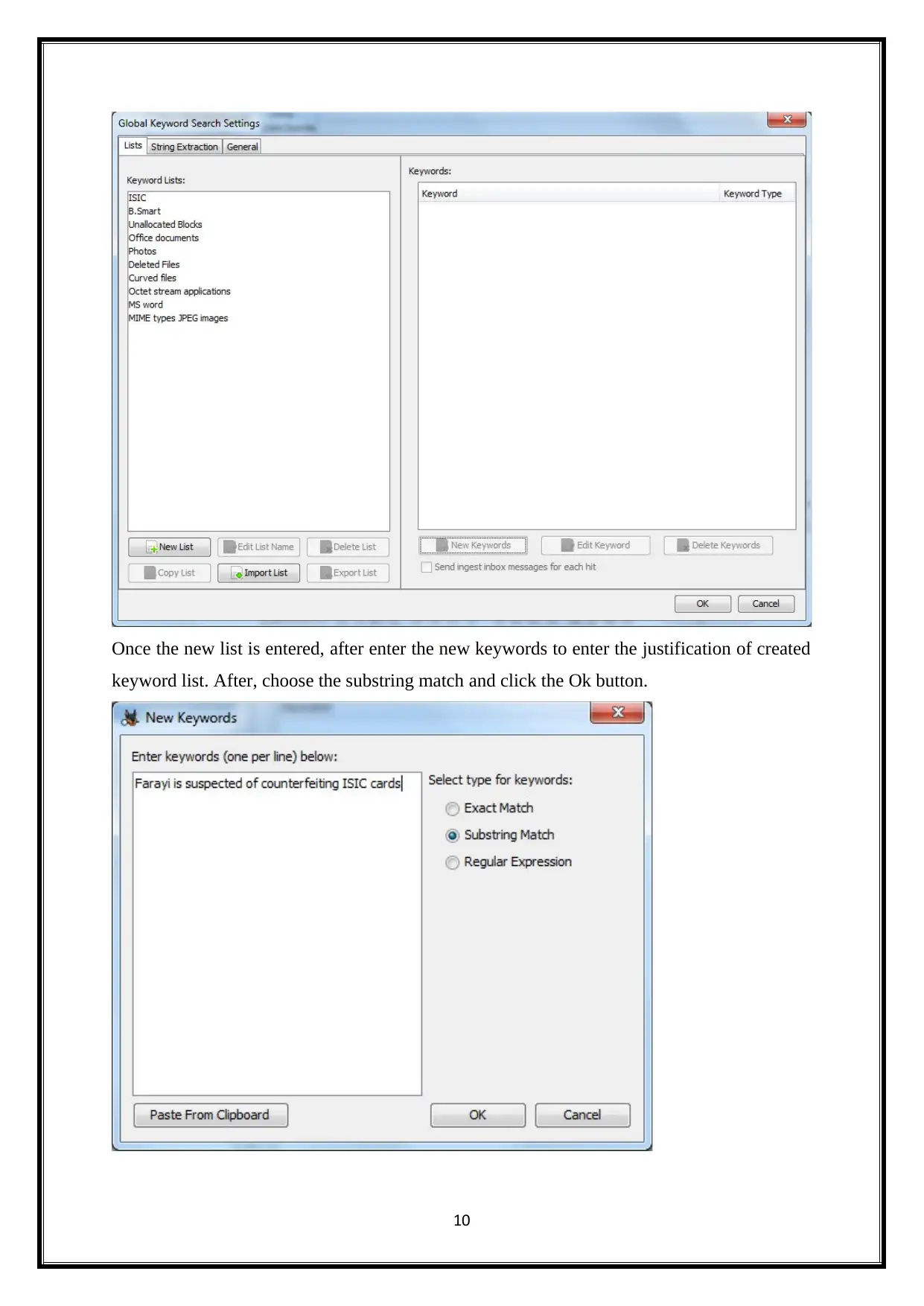
Once the new list is entered, after enter the new keywords to enter the justification of created
keyword list. After, choose the substring match and click the Ok button.
10
keyword list. After, choose the substring match and click the Ok button.
10
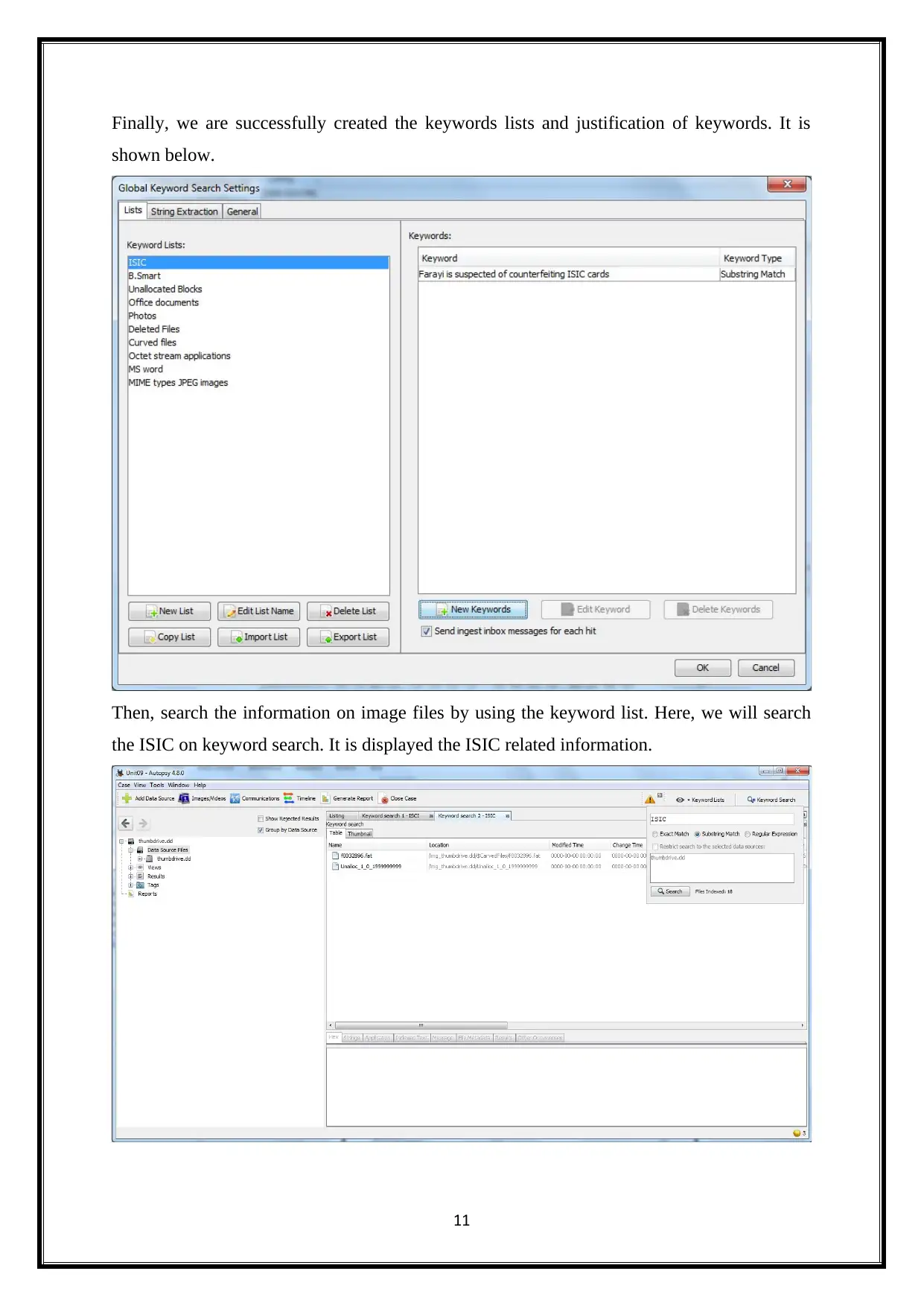
Finally, we are successfully created the keywords lists and justification of keywords. It is
shown below.
Then, search the information on image files by using the keyword list. Here, we will search
the ISIC on keyword search. It is displayed the ISIC related information.
11
shown below.
Then, search the information on image files by using the keyword list. Here, we will search
the ISIC on keyword search. It is displayed the ISIC related information.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 30
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
