Digital Forensics (ITC 597) Assessment No. 2
VerifiedAdded on 2023/06/14
|15
|1809
|111
AI Summary
This report covers hands-on projects, case project, and research report on digital forensics. It includes tasks such as creating projects, adding image files, searching for keywords, indexing, and validating forensic data.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Digital Forensics (ITC 597)
Assessment No. 2
Name
Adm NO
Lecturer’s Name:
Date of submission
Couse Code
Table of Contents
1.0 Task 1: REFLECTION OF HANDS ON PROJECT..............................................................2
0 | P a g e
Assessment No. 2
Name
Adm NO
Lecturer’s Name:
Date of submission
Couse Code
Table of Contents
1.0 Task 1: REFLECTION OF HANDS ON PROJECT..............................................................2
0 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1.1 Hands-On Project 1-1................................................................................................................2
1.2 Hands-On Project 1-2................................................................................................................3
1.3 Hands-On Project 1-3................................................................................................................4
1.4 Hands-On Project 1-4................................................................................................................4
1.5 Hands-On Project 1-5................................................................................................................5
2.0 Task 2: Case Project......................................................................................................................6
3. 0 Task 3: Research Report............................................................................................................12
References...........................................................................................................................................14
1 | P a g e
1.2 Hands-On Project 1-2................................................................................................................3
1.3 Hands-On Project 1-3................................................................................................................4
1.4 Hands-On Project 1-4................................................................................................................4
1.5 Hands-On Project 1-5................................................................................................................5
2.0 Task 2: Case Project......................................................................................................................6
3. 0 Task 3: Research Report............................................................................................................12
References...........................................................................................................................................14
1 | P a g e

1.0 Task 1: REFLECTION OF HANDS ON PROJECT
1.1 Hands-On Project 1-1
Step 1 - 3: Create project C1Prj01 in ProDiscover Basic with project number, and a brief
description about the project.
Step 4: Adding the image File to our C1Prj01 Project. This is done by expanding the Add
item in the Action Menu.
Step 5: Selecting the C1Prj01.eve image to be added to C1Prj01.
Step 6: Viewing the content of C1Prj01.eve by Expanding the Content View for the
C1Prj01.eve image.
Step 7: Viewing the Content of the Files in C1Prj01.eve image with associated programs.
Step 8: Generating C1Prj01 Evidence Report.
Report:
From the Tasks Carried out, an image of the USB Drive was backed-up bit-to-bit before
being analysed. Both a text file and excel document were found indicating the possibility of
an incidence of suicide as a result of tough financial times as seen in suicide1.txt located in
the C1Prj01.eve image. Using associated programs, the suicide1.txt could be read in a note
pad thus allowing us to view its content.
2 | P a g e
1.1 Hands-On Project 1-1
Step 1 - 3: Create project C1Prj01 in ProDiscover Basic with project number, and a brief
description about the project.
Step 4: Adding the image File to our C1Prj01 Project. This is done by expanding the Add
item in the Action Menu.
Step 5: Selecting the C1Prj01.eve image to be added to C1Prj01.
Step 6: Viewing the content of C1Prj01.eve by Expanding the Content View for the
C1Prj01.eve image.
Step 7: Viewing the Content of the Files in C1Prj01.eve image with associated programs.
Step 8: Generating C1Prj01 Evidence Report.
Report:
From the Tasks Carried out, an image of the USB Drive was backed-up bit-to-bit before
being analysed. Both a text file and excel document were found indicating the possibility of
an incidence of suicide as a result of tough financial times as seen in suicide1.txt located in
the C1Prj01.eve image. Using associated programs, the suicide1.txt could be read in a note
pad thus allowing us to view its content.
2 | P a g e

1.2 Hands-On Project 1-2
Step 1: Create a project called C1Prj02 with a project number and a brief description of what
it is about.
Step 2: Adding the image File to our C1Prj02 Project. This is done by expanding the Add
item in the Action Menu.
Step 3: Viewing the content of C1Prj02.eve by Expanding the Content View for the
C1Prj02.eve image.
Step 4: Searching for the keyword “book,” by clicking the Search Menu Button to open the
Search dialog box.
Step 5: Viewing Cluster Search Results after the “Book” Search.
Report:
The purpose of this report is to find out a word “book” out of twenty-four very personal files.
ProDiscover tool provides us with means of searching for specified keywords. This simple
feature helps us find keywords of interest through a search dialog thus reducing on time taken
to carry out an investigation as one does not need to manually look for them.
3 | P a g e
Step 1: Create a project called C1Prj02 with a project number and a brief description of what
it is about.
Step 2: Adding the image File to our C1Prj02 Project. This is done by expanding the Add
item in the Action Menu.
Step 3: Viewing the content of C1Prj02.eve by Expanding the Content View for the
C1Prj02.eve image.
Step 4: Searching for the keyword “book,” by clicking the Search Menu Button to open the
Search dialog box.
Step 5: Viewing Cluster Search Results after the “Book” Search.
Report:
The purpose of this report is to find out a word “book” out of twenty-four very personal files.
ProDiscover tool provides us with means of searching for specified keywords. This simple
feature helps us find keywords of interest through a search dialog thus reducing on time taken
to carry out an investigation as one does not need to manually look for them.
3 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.3 Hands-On Project 1-3
Step 1: Create a new project C1Prj03 with a project number and a brief description of what it
is about.
Step 2-3: Adding C1Prj03.dd, Navigating to Content and Sorting by “Deleted”
Step 4: Searching for 461562 as the search keyword and any other Interesting picture.
Report:
From searching through the gallery view, I came across a COUNT.GIF with an account
number 461562 which we were looking in the first place. It is possible to search for keywords
not only in documents but also in not text files such as images.
1.4 Hands-On Project 1-4
Step 1: C1Prj04 project with a project number and a brief description
Step 2-3: Adding the C1Prj04.eve to Our Project & Navigating to Content
Step 5: Sorting files by “Deleted” Column into YES-NO groups.
Step 6: Extracting files not deleted from image.
Report:
In this project, content which was not deleted on the backed-up image could easily be
retrieved. Retrieval of these allocated files gives us clues for further investigations. Also, files
that had been deleted were shown by their names, sizes along other attributes. Files from the
image being investigated can be saved or exported to other places for further investigation or
safe keeping as evidence. It is possible to search for occurrences of the specified keywords in
an image. A detailed report is also generated. This report has details of the findings and is
termed as an Evidence Report.
4 | P a g e
Step 1: Create a new project C1Prj03 with a project number and a brief description of what it
is about.
Step 2-3: Adding C1Prj03.dd, Navigating to Content and Sorting by “Deleted”
Step 4: Searching for 461562 as the search keyword and any other Interesting picture.
Report:
From searching through the gallery view, I came across a COUNT.GIF with an account
number 461562 which we were looking in the first place. It is possible to search for keywords
not only in documents but also in not text files such as images.
1.4 Hands-On Project 1-4
Step 1: C1Prj04 project with a project number and a brief description
Step 2-3: Adding the C1Prj04.eve to Our Project & Navigating to Content
Step 5: Sorting files by “Deleted” Column into YES-NO groups.
Step 6: Extracting files not deleted from image.
Report:
In this project, content which was not deleted on the backed-up image could easily be
retrieved. Retrieval of these allocated files gives us clues for further investigations. Also, files
that had been deleted were shown by their names, sizes along other attributes. Files from the
image being investigated can be saved or exported to other places for further investigation or
safe keeping as evidence. It is possible to search for occurrences of the specified keywords in
an image. A detailed report is also generated. This report has details of the findings and is
termed as an Evidence Report.
4 | P a g e

1.5 Hands-On Project 1-5
Step 1: All the steps from project 4 are repeated.
Step 2: Write a comment in the investigator text box.
Step 3: Export the report by typing C1Prj05Report and exit.
Report:
Documentation of the investigations and the findings is an important practice that
distinguishes forensic experts. In this project, we have final file to be saved in a word
document or an image by giving a comment. That is, we name them in a meaningful way so
as to prioritize them during examination.
5 | P a g e
Step 1: All the steps from project 4 are repeated.
Step 2: Write a comment in the investigator text box.
Step 3: Export the report by typing C1Prj05Report and exit.
Report:
Documentation of the investigations and the findings is an important practice that
distinguishes forensic experts. In this project, we have final file to be saved in a word
document or an image by giving a comment. That is, we name them in a meaningful way so
as to prioritize them during examination.
5 | P a g e
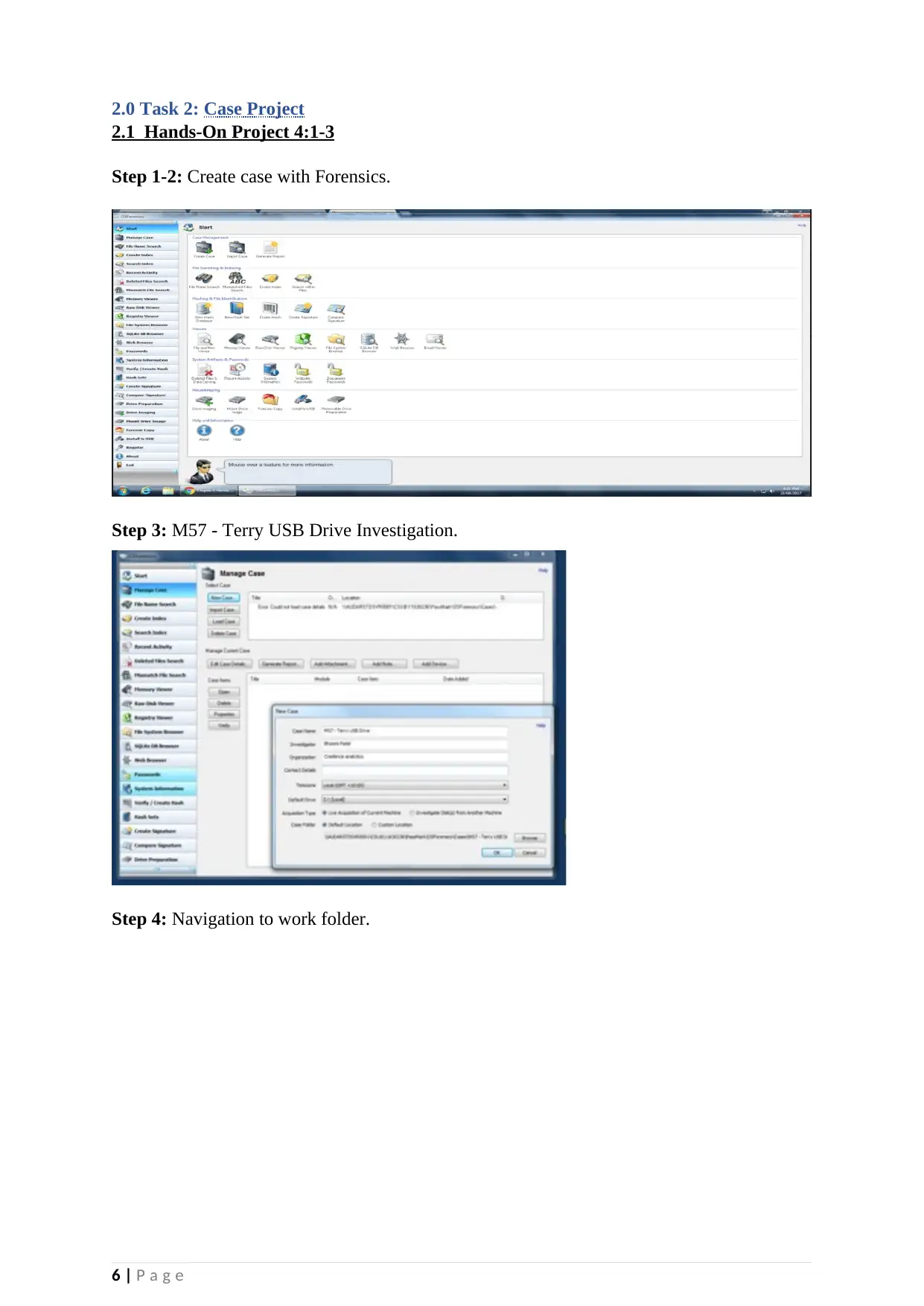
2.0 Task 2: Case Project
2.1 Hands-On Project 4:1-3
Step 1-2: Create case with Forensics.
Step 3: M57 - Terry USB Drive Investigation.
Step 4: Navigation to work folder.
6 | P a g e
2.1 Hands-On Project 4:1-3
Step 1-2: Create case with Forensics.
Step 3: M57 - Terry USB Drive Investigation.
Step 4: Navigation to work folder.
6 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
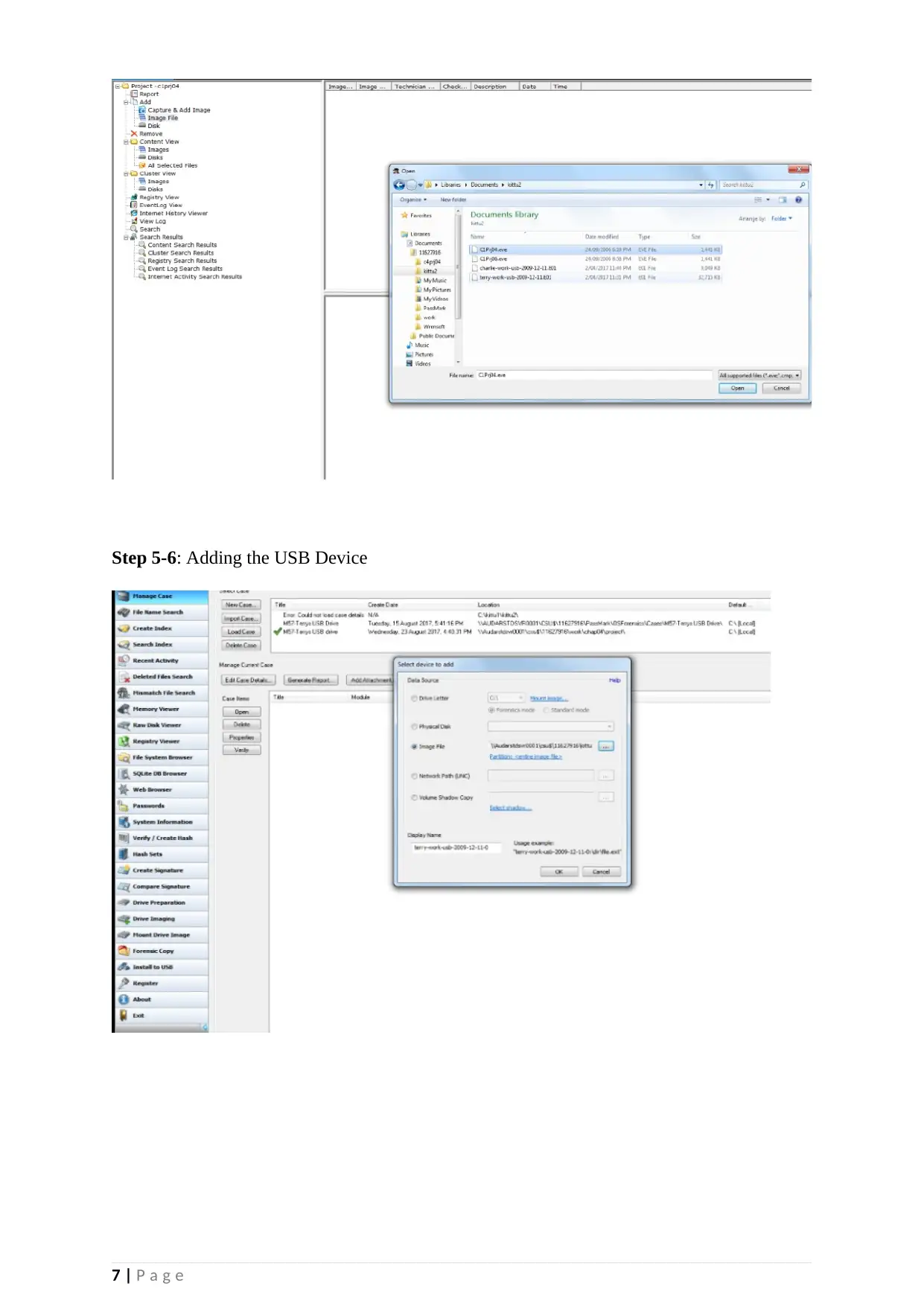
Step 5-6: Adding the USB Device
7 | P a g e
7 | P a g e
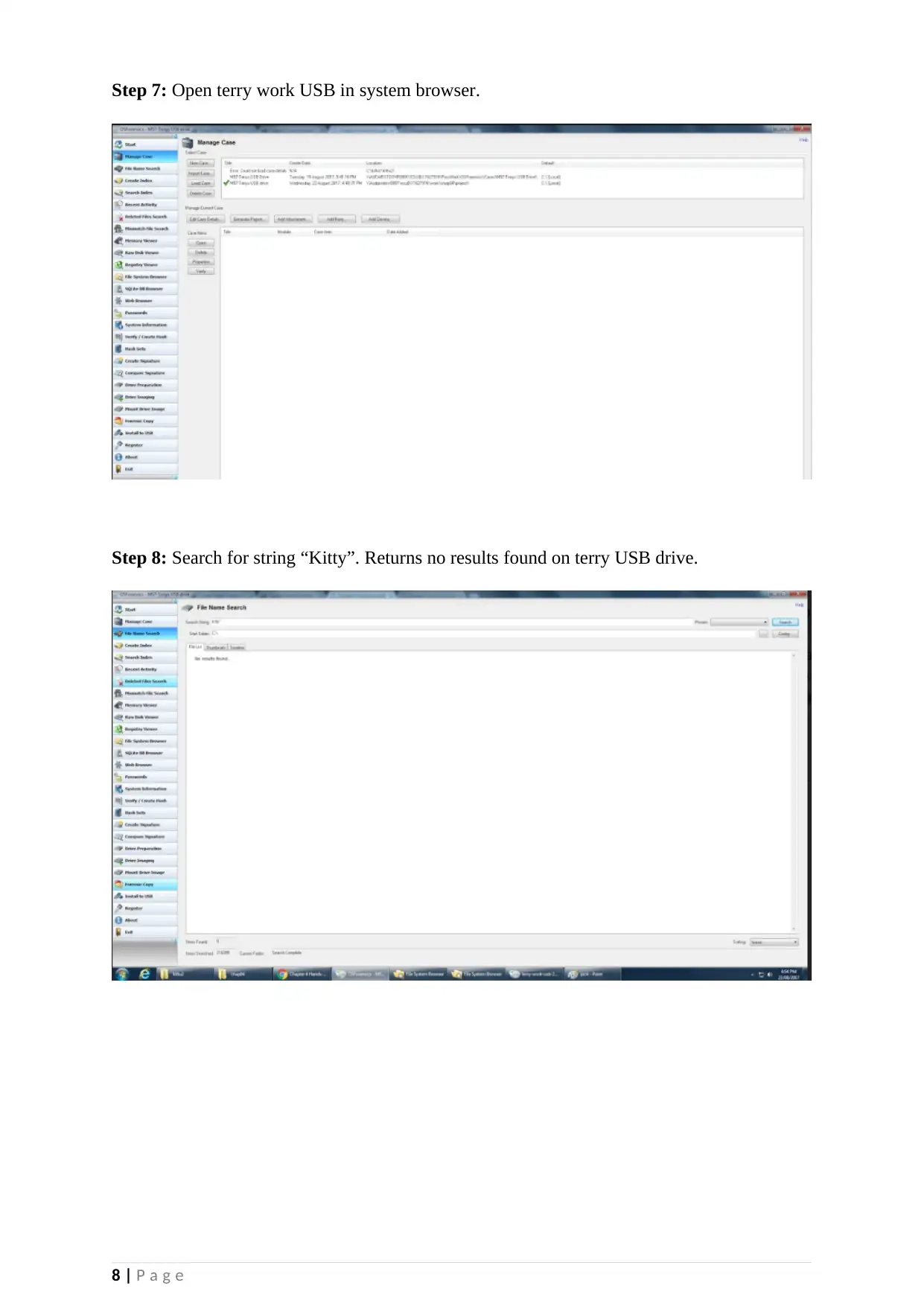
Step 7: Open terry work USB in system browser.
Step 8: Search for string “Kitty”. Returns no results found on terry USB drive.
8 | P a g e
Step 8: Search for string “Kitty”. Returns no results found on terry USB drive.
8 | P a g e
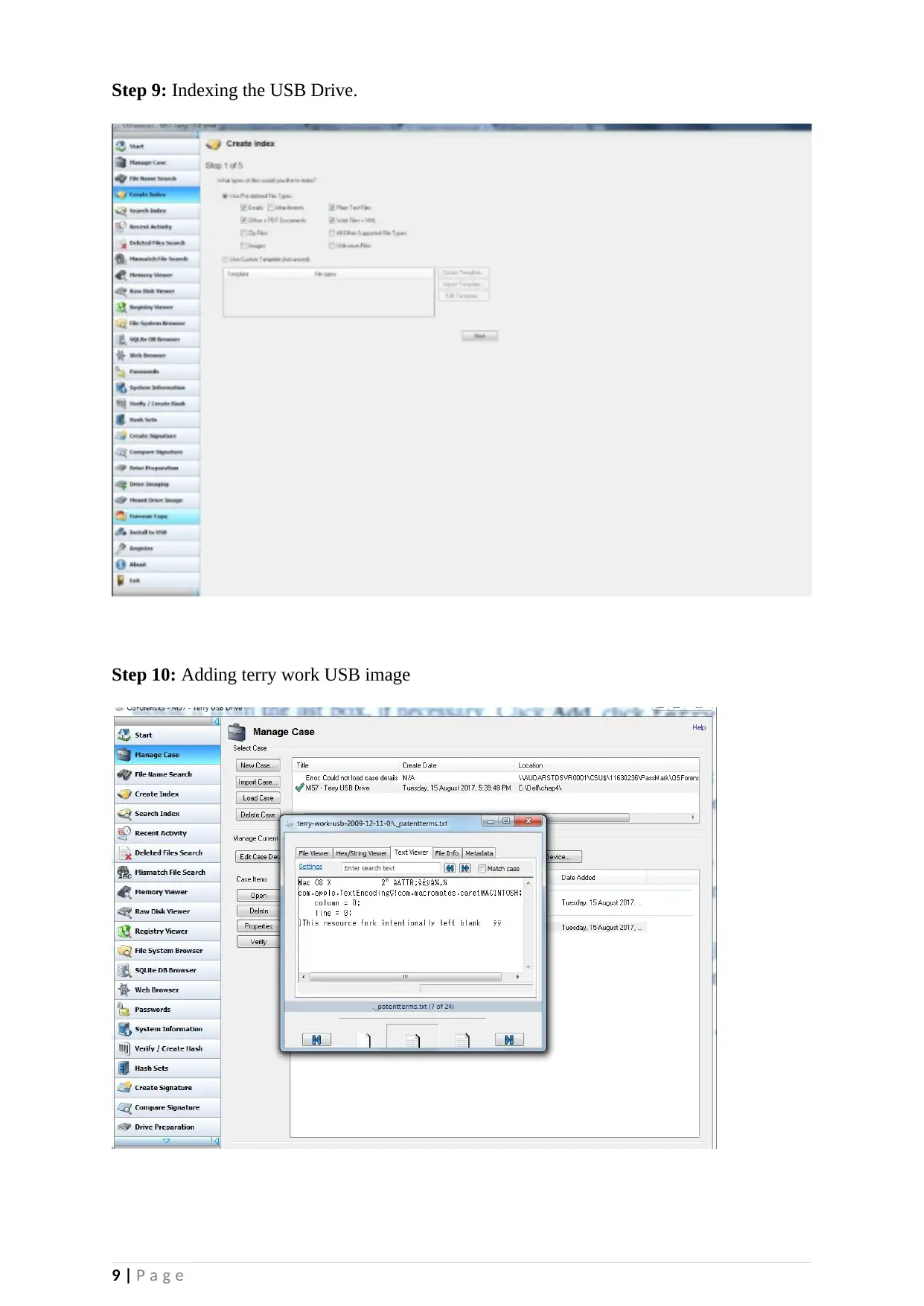
Step 9: Indexing the USB Drive.
Step 10: Adding terry work USB image
9 | P a g e
Step 10: Adding terry work USB image
9 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
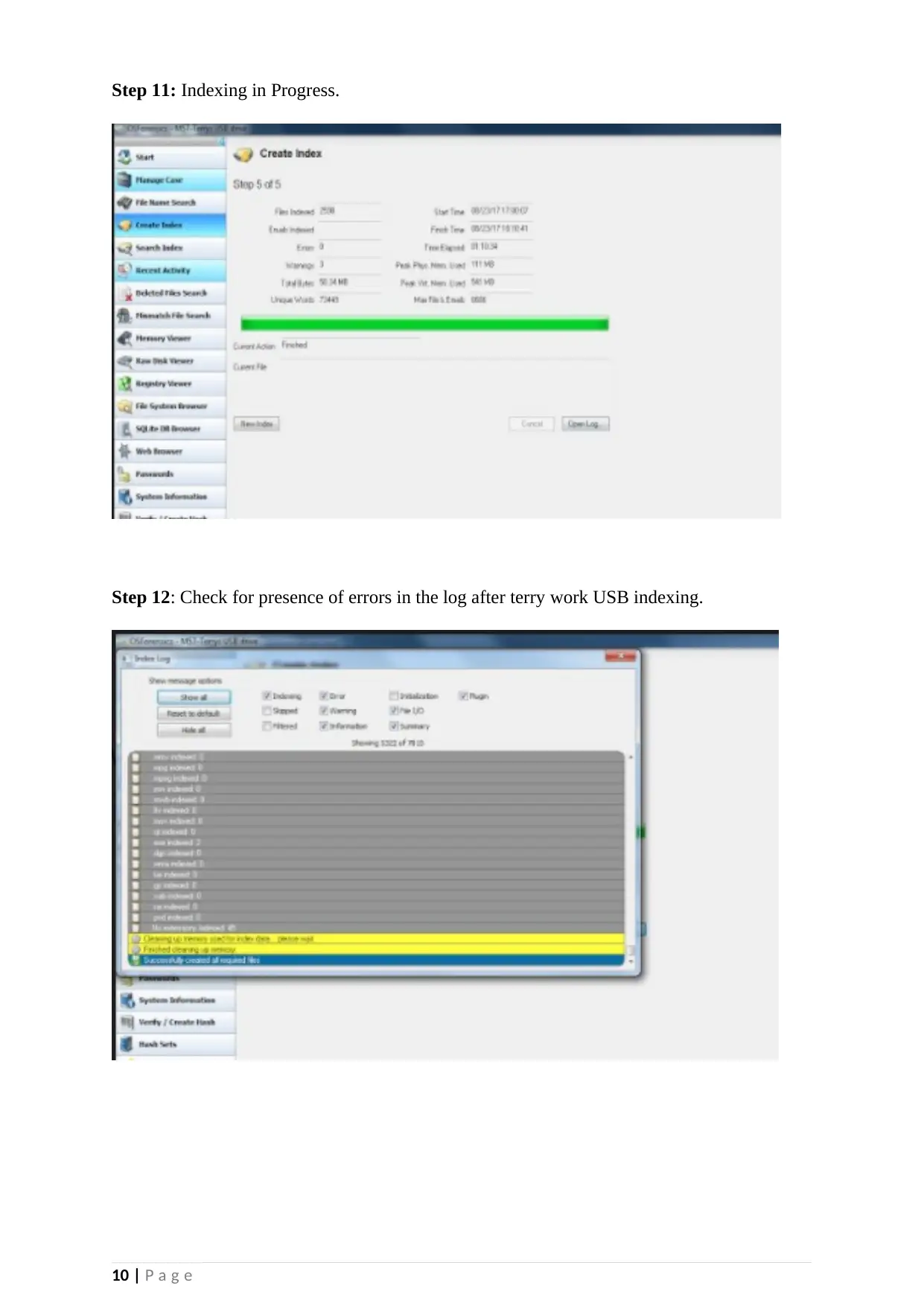
Step 11: Indexing in Progress.
Step 12: Check for presence of errors in the log after terry work USB indexing.
10 | P a g e
Step 12: Check for presence of errors in the log after terry work USB indexing.
10 | P a g e
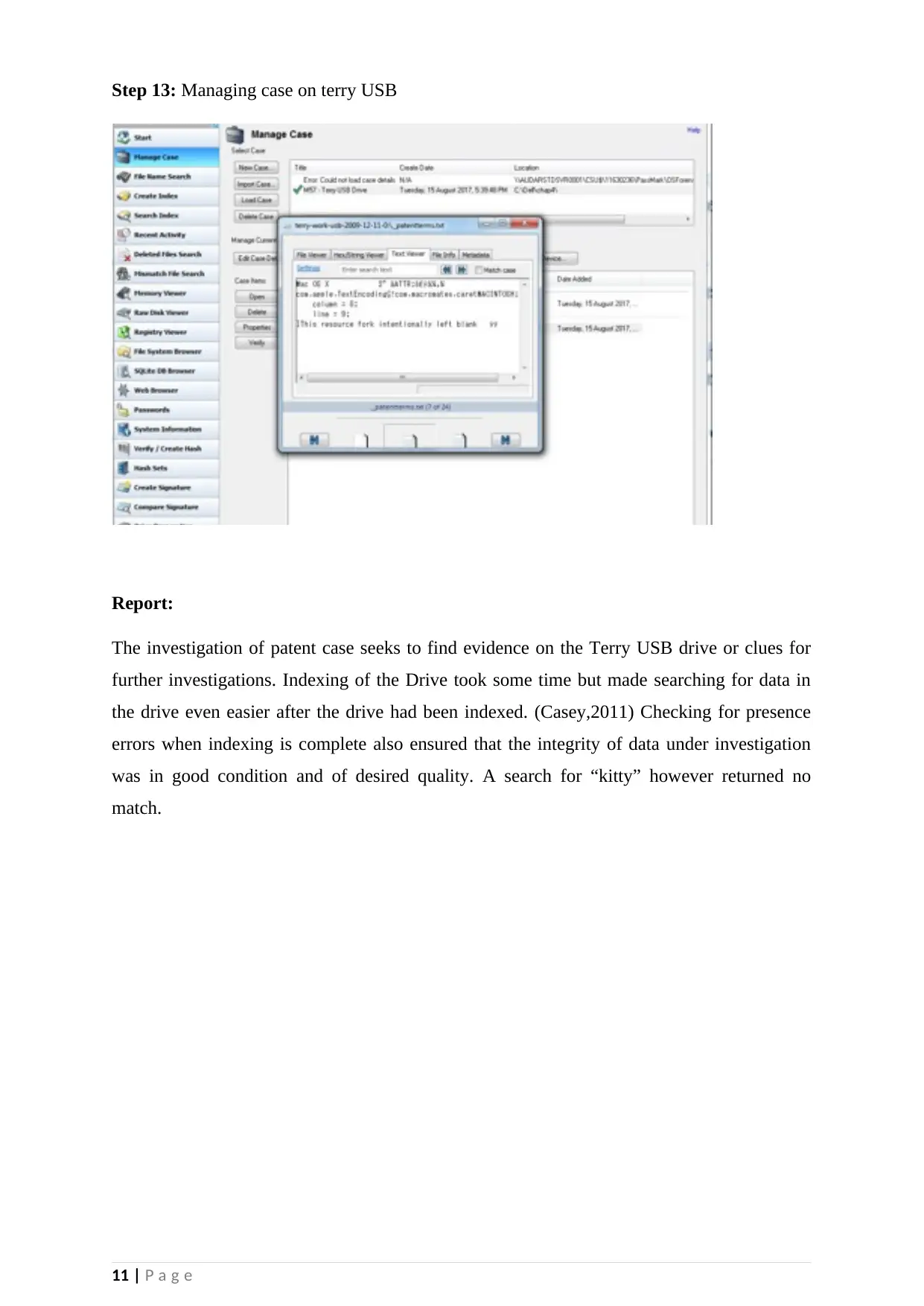
Step 13: Managing case on terry USB
Report:
The investigation of patent case seeks to find evidence on the Terry USB drive or clues for
further investigations. Indexing of the Drive took some time but made searching for data in
the drive even easier after the drive had been indexed. (Casey,2011) Checking for presence
errors when indexing is complete also ensured that the integrity of data under investigation
was in good condition and of desired quality. A search for “kitty” however returned no
match.
11 | P a g e
Report:
The investigation of patent case seeks to find evidence on the Terry USB drive or clues for
further investigations. Indexing of the Drive took some time but made searching for data in
the drive even easier after the drive had been indexed. (Casey,2011) Checking for presence
errors when indexing is complete also ensured that the integrity of data under investigation
was in good condition and of desired quality. A search for “kitty” however returned no
match.
11 | P a g e

3. 0 Task 3: Research Report
As a rule, an investigation is arranged by characterizing the objectives, scope, materials
required and duties to perform. The field of examination ought to be resolved. That is, the
gathering of the potential trick or scam:
Criminal: inclined information clarified in court order
Common: insufficient to court orders for revelation
Corporate: amplifies up to when the point when the potential outcomes of organization
approach infringement are discovered bringing about Scope crawl.
At display the Scope crawl is extremely normal as resolved to find as much as devastations
which regularly are outside the first portrayal. Obviously its intensive procedure guarantees
higher request of information, henceforth requires more opportunity to remove or dissect the
information. (Farid,2011) Along these lines, archives must be set up with additional time and
development of extension. Because an interior examination, proofs or some other necessities
goes under a similar zone with the goal that it is anything but difficult to get to while for
outside connections a few issues because of authorization or intermittent auto-expulsion of
conceivable confirmations may happen.
For advanced crime scene investigation there are numerous recommendations accessible
which incorporates open strides of approval utilizing hashes like MDS or SHA-l, investigate
every one’s document/indexes, under roots and files, evacuation infection and keeping up
control of all verifications and finding through examination. As indicated by the past
documents, examination designs may require the screening and changes. An exceptionally
huge advance is to approve scientific information for instance utilizing Hash esteems or
computerized devices. Examining the scrambled records and files by using graphical
techniques are thought about.
Approving the crime scene investigation information is intense piece of PC legal sciences as
it ensures the uprightness of information gathered for showing in the court. Although most
PC crime scene investigation instruments give computerized hashing of picture record, it has
a few restrictions in performing hashing thus the progressed hexadecimal editors are liked to
work with hash esteems to isolate the information.
Utilizing hash esteems and the Known File Filter, the program documents from view, for
example, MSWord.exe or Excel is found and after that the illicit records can be resolved.
Known File Filter contrasts the known document hash esteems and the record on prove drive
or separated picture and it refreshes itself on known document hash esteems. Some business
12 | P a g e
As a rule, an investigation is arranged by characterizing the objectives, scope, materials
required and duties to perform. The field of examination ought to be resolved. That is, the
gathering of the potential trick or scam:
Criminal: inclined information clarified in court order
Common: insufficient to court orders for revelation
Corporate: amplifies up to when the point when the potential outcomes of organization
approach infringement are discovered bringing about Scope crawl.
At display the Scope crawl is extremely normal as resolved to find as much as devastations
which regularly are outside the first portrayal. Obviously its intensive procedure guarantees
higher request of information, henceforth requires more opportunity to remove or dissect the
information. (Farid,2011) Along these lines, archives must be set up with additional time and
development of extension. Because an interior examination, proofs or some other necessities
goes under a similar zone with the goal that it is anything but difficult to get to while for
outside connections a few issues because of authorization or intermittent auto-expulsion of
conceivable confirmations may happen.
For advanced crime scene investigation there are numerous recommendations accessible
which incorporates open strides of approval utilizing hashes like MDS or SHA-l, investigate
every one’s document/indexes, under roots and files, evacuation infection and keeping up
control of all verifications and finding through examination. As indicated by the past
documents, examination designs may require the screening and changes. An exceptionally
huge advance is to approve scientific information for instance utilizing Hash esteems or
computerized devices. Examining the scrambled records and files by using graphical
techniques are thought about.
Approving the crime scene investigation information is intense piece of PC legal sciences as
it ensures the uprightness of information gathered for showing in the court. Although most
PC crime scene investigation instruments give computerized hashing of picture record, it has
a few restrictions in performing hashing thus the progressed hexadecimal editors are liked to
work with hash esteems to isolate the information.
Utilizing hash esteems and the Known File Filter, the program documents from view, for
example, MSWord.exe or Excel is found and after that the illicit records can be resolved.
Known File Filter contrasts the known document hash esteems and the record on prove drive
or separated picture and it refreshes itself on known document hash esteems. Some business
12 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

PC crime scene investigation programs exists with worked in approval highlights, for
example, pro find and numerous other, still Raw configuration picture documents say, *gg
records which does not contain the metadata which must be approved physically to guarantee
the trustworthiness.
Legal sciences basically make use of MDS and SHA-l hash streams, where MD implies
Message process and SHA implies Secure hashing calculation which utilizes cryptographic
strategies.
13 | P a g e
example, pro find and numerous other, still Raw configuration picture documents say, *gg
records which does not contain the metadata which must be approved physically to guarantee
the trustworthiness.
Legal sciences basically make use of MDS and SHA-l hash streams, where MD implies
Message process and SHA implies Secure hashing calculation which utilizes cryptographic
strategies.
13 | P a g e

References
There are no sources in the current document
Carrier, B. (2002). Open source digital forensics tools: The legal argument (pp. 1-11). stake.
Casey, E. (2011). Digital evidence and computer crime: Forensic science, computers, and
the internet. Academic press.
Freeling, F., & Schwittay, B. (2007). A common process model for incident response and
digital forensics. Proceedings of the IMF2007.
Farid, H., & Lyu, S. (2003, June). Higher-order wavelet statistics and their application to
digital forensics. In Computer Vision and Pattern Recognition Workshop, 2003. CVPRW'03.
Conference on (Vol. 8, pp. 94-94). IEEE.
Garfinkel, S. L. (2010). Digital forensics research: The next 10 years. digital investigation, 7,
S64-S73.
Jones, K. J., Bejtlich, R., & Rose, C. W. (2006). Real digital forensics: computer security
and incident response (pp. 3-4). Addison-Wesley
Popescu, A. C., & Farid, H. (2004, May). Statistical tools for digital forensics.
In International Workshop on Information Hiding (pp. 128-147). Springer, Berlin,
Heidelberg.
14 | P a g e
There are no sources in the current document
Carrier, B. (2002). Open source digital forensics tools: The legal argument (pp. 1-11). stake.
Casey, E. (2011). Digital evidence and computer crime: Forensic science, computers, and
the internet. Academic press.
Freeling, F., & Schwittay, B. (2007). A common process model for incident response and
digital forensics. Proceedings of the IMF2007.
Farid, H., & Lyu, S. (2003, June). Higher-order wavelet statistics and their application to
digital forensics. In Computer Vision and Pattern Recognition Workshop, 2003. CVPRW'03.
Conference on (Vol. 8, pp. 94-94). IEEE.
Garfinkel, S. L. (2010). Digital forensics research: The next 10 years. digital investigation, 7,
S64-S73.
Jones, K. J., Bejtlich, R., & Rose, C. W. (2006). Real digital forensics: computer security
and incident response (pp. 3-4). Addison-Wesley
Popescu, A. C., & Farid, H. (2004, May). Statistical tools for digital forensics.
In International Workshop on Information Hiding (pp. 128-147). Springer, Berlin,
Heidelberg.
14 | P a g e
1 out of 15
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)





