Digital Forensics: Company A's Investigation of Stolen Files, Report
VerifiedAdded on 2020/03/16
|26
|2413
|62
Report
AI Summary
This report presents a digital forensics investigation conducted for Company A, a construction firm, following the suspected theft of sensitive files. The investigation focused on an employee suspected of data exfiltration and frequent USB drive formatting. The forensic investigator employed various techniques, including USB data recovery, network traffic analysis using Wireshark to identify email spoofing, and password cracking of encrypted files using RainbowCrack. The investigation revealed that the employee had compromised the CEO's computer with Ophcrack, copied files to a USB drive, and sent spoofed emails. The recovered data provided crucial evidence, allowing Company A to inform the approver and prevent misuse of the stolen information. The report outlines the tools used, the analysis performed, the findings, and the conclusions, providing a comprehensive overview of the investigation's methodology and results, with supporting evidence such as camera footage of the employee using email spoofing software. The report also provides information on the methods used in the investigation, like cracking the password for the company admin system, and the recovery of stolen files.
digital forensics
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive summary
Company A is a construction company. The CEO of company A suspects that some files
have been stolen. The CEO also notices that an employee formats his USB drive frequently.
Before the stolen information reaches the approver, the company A has to inform the approver
about the stolen files and file information and has to track the company which submits the same
file. The company A contacts the forensic investigator and asks them to find out the files theft
and the details of the files. The investigator investigates the suspected employee and catches his
USB drive which is in formatted mode. The investigator retrieves the data from the formatted
USB drive and also the suspected employee’s network traffic. By using wire shark traffic
analyzer it is found that the suspected employee has spoofed the company’s mail address using
mail spoofing software. The investigator retrieves the data in USB but it appears to be in
encrypted format and the investigator user rainbow cracker to crack the password of the
encrypted file and the investigator provides the file details to company A. Company A transfers
the information to Approver to decertify the work if submitted by other companies. The
company A provides the investigated details to the approver for proof.
1
Company A is a construction company. The CEO of company A suspects that some files
have been stolen. The CEO also notices that an employee formats his USB drive frequently.
Before the stolen information reaches the approver, the company A has to inform the approver
about the stolen files and file information and has to track the company which submits the same
file. The company A contacts the forensic investigator and asks them to find out the files theft
and the details of the files. The investigator investigates the suspected employee and catches his
USB drive which is in formatted mode. The investigator retrieves the data from the formatted
USB drive and also the suspected employee’s network traffic. By using wire shark traffic
analyzer it is found that the suspected employee has spoofed the company’s mail address using
mail spoofing software. The investigator retrieves the data in USB but it appears to be in
encrypted format and the investigator user rainbow cracker to crack the password of the
encrypted file and the investigator provides the file details to company A. Company A transfers
the information to Approver to decertify the work if submitted by other companies. The
company A provides the investigated details to the approver for proof.
1

Table of Contents
1. Introduction.......................................................................................................................................4
2. Analysis..............................................................................................................................................4
3. Findings............................................................................................................................................14
4. Conclusion........................................................................................................................................17
5. Appendix..........................................................................................................................................17
Reference..................................................................................................................................................25
2
1. Introduction.......................................................................................................................................4
2. Analysis..............................................................................................................................................4
3. Findings............................................................................................................................................14
4. Conclusion........................................................................................................................................17
5. Appendix..........................................................................................................................................17
Reference..................................................................................................................................................25
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Glossary
forensic : Crime investigation science
USB : Universal Serial Bus is an industry standard in digital devices communication
Wireshark : Formerly called as Ethereal , is a network pocket capturing and investigation tool
Spoofing : Identity cheating to get access to others data
rainbow cracker : A hash cracking tool
encrypted file : Format changed file which cannot be read without decrypting
Scam : Illegal way of cheating people
Caller ID : Identification details of the communication initiator
IP Address : Numerical address of a network connected device
Gmail : Email service provider
3
forensic : Crime investigation science
USB : Universal Serial Bus is an industry standard in digital devices communication
Wireshark : Formerly called as Ethereal , is a network pocket capturing and investigation tool
Spoofing : Identity cheating to get access to others data
rainbow cracker : A hash cracking tool
encrypted file : Format changed file which cannot be read without decrypting
Scam : Illegal way of cheating people
Caller ID : Identification details of the communication initiator
IP Address : Numerical address of a network connected device
Gmail : Email service provider
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Introduction
Company A suspects some files have been stolen. It has to provide the details of the stolen files
with the investigation report to stop others from using the file. Company A contacts the forensic
officer. The forensic officer finds out that the attacker has hacked the CEO’s computer using
ophcrack and copied files to the USB drive and sent from his computer using a proofed address
to some other company. The investigator retrieves the formatted USB drive of the suspected
employee and opens the encrypted files using ophcrack. The investigation will be carried based
on the complaints provided by the CEO. The investigation results will be provided which will be
helpful for company A to submit it to the approver
2. Analysis
Tools used by attacker
Ophcrack
Email spoofing software
Tools used by investigator
USB data retrieval (from formatted USB)
Rainbow cracker software(to find password of encrypted file)
Hacking password protected computer by ophcrack
In order to crack password that are very simple and short a tool called ophcrack is used.
Even though the ophcrack tool is an old tool, we can use the tool with some limitations.
The ophcrack tool is downloaded from the website and the ISO image file is burned into
Universal serial bus or compact disc (Ophcrack, 2012).
The locked personal computer is started by ophcrack and select “Ophcrack Graphic Mode –
Automatic”
It takes some time to recover the password of the computer. once the password is recovered it
will be displayed on the user interface of the ophcrack tool (Blackstone & Lewis, 2007).
4
Company A suspects some files have been stolen. It has to provide the details of the stolen files
with the investigation report to stop others from using the file. Company A contacts the forensic
officer. The forensic officer finds out that the attacker has hacked the CEO’s computer using
ophcrack and copied files to the USB drive and sent from his computer using a proofed address
to some other company. The investigator retrieves the formatted USB drive of the suspected
employee and opens the encrypted files using ophcrack. The investigation will be carried based
on the complaints provided by the CEO. The investigation results will be provided which will be
helpful for company A to submit it to the approver
2. Analysis
Tools used by attacker
Ophcrack
Email spoofing software
Tools used by investigator
USB data retrieval (from formatted USB)
Rainbow cracker software(to find password of encrypted file)
Hacking password protected computer by ophcrack
In order to crack password that are very simple and short a tool called ophcrack is used.
Even though the ophcrack tool is an old tool, we can use the tool with some limitations.
The ophcrack tool is downloaded from the website and the ISO image file is burned into
Universal serial bus or compact disc (Ophcrack, 2012).
The locked personal computer is started by ophcrack and select “Ophcrack Graphic Mode –
Automatic”
It takes some time to recover the password of the computer. once the password is recovered it
will be displayed on the user interface of the ophcrack tool (Blackstone & Lewis, 2007).
4
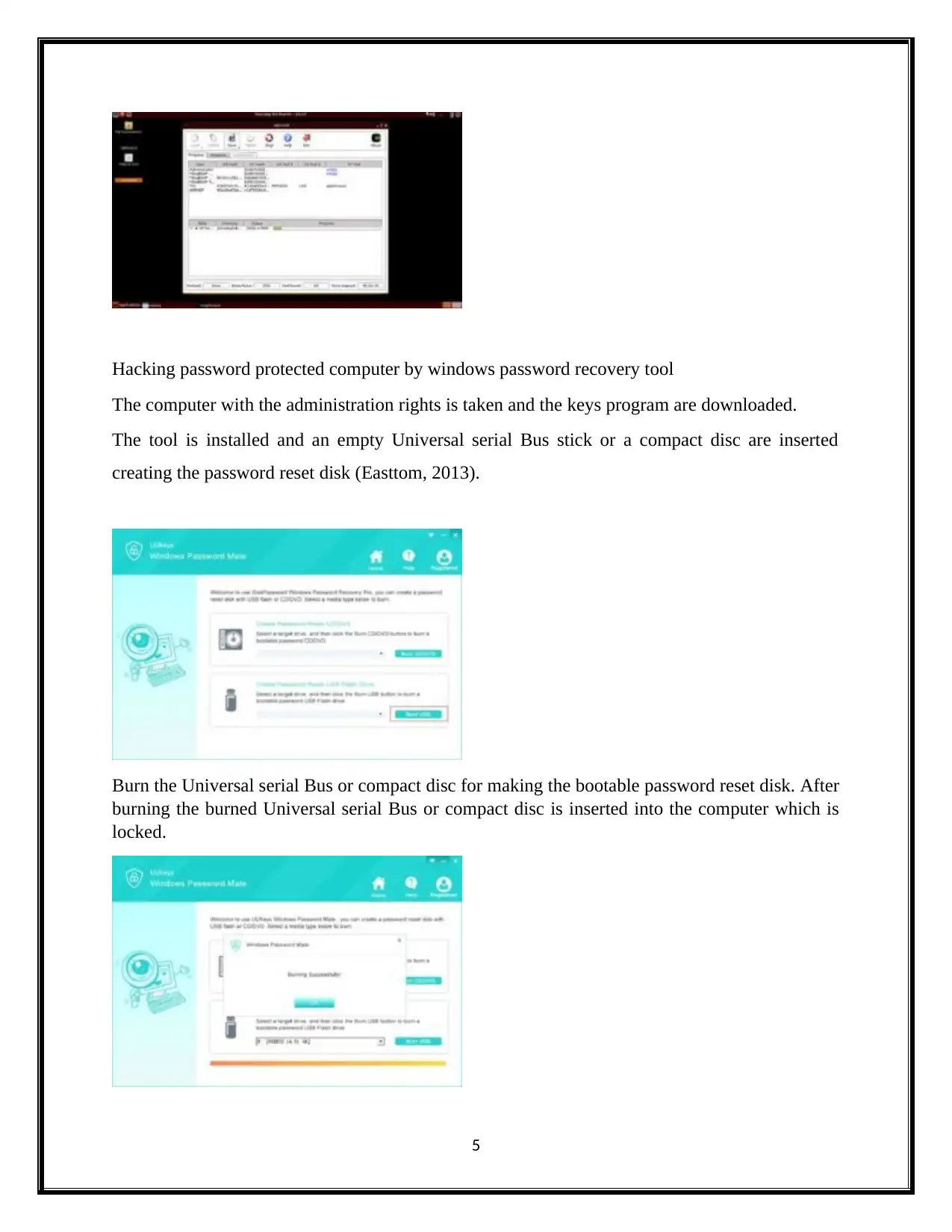
Hacking password protected computer by windows password recovery tool
The computer with the administration rights is taken and the keys program are downloaded.
The tool is installed and an empty Universal serial Bus stick or a compact disc are inserted
creating the password reset disk (Easttom, 2013).
Burn the Universal serial Bus or compact disc for making the bootable password reset disk. After
burning the burned Universal serial Bus or compact disc is inserted into the computer which is
locked.
5
The computer with the administration rights is taken and the keys program are downloaded.
The tool is installed and an empty Universal serial Bus stick or a compact disc are inserted
creating the password reset disk (Easttom, 2013).
Burn the Universal serial Bus or compact disc for making the bootable password reset disk. After
burning the burned Universal serial Bus or compact disc is inserted into the computer which is
locked.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
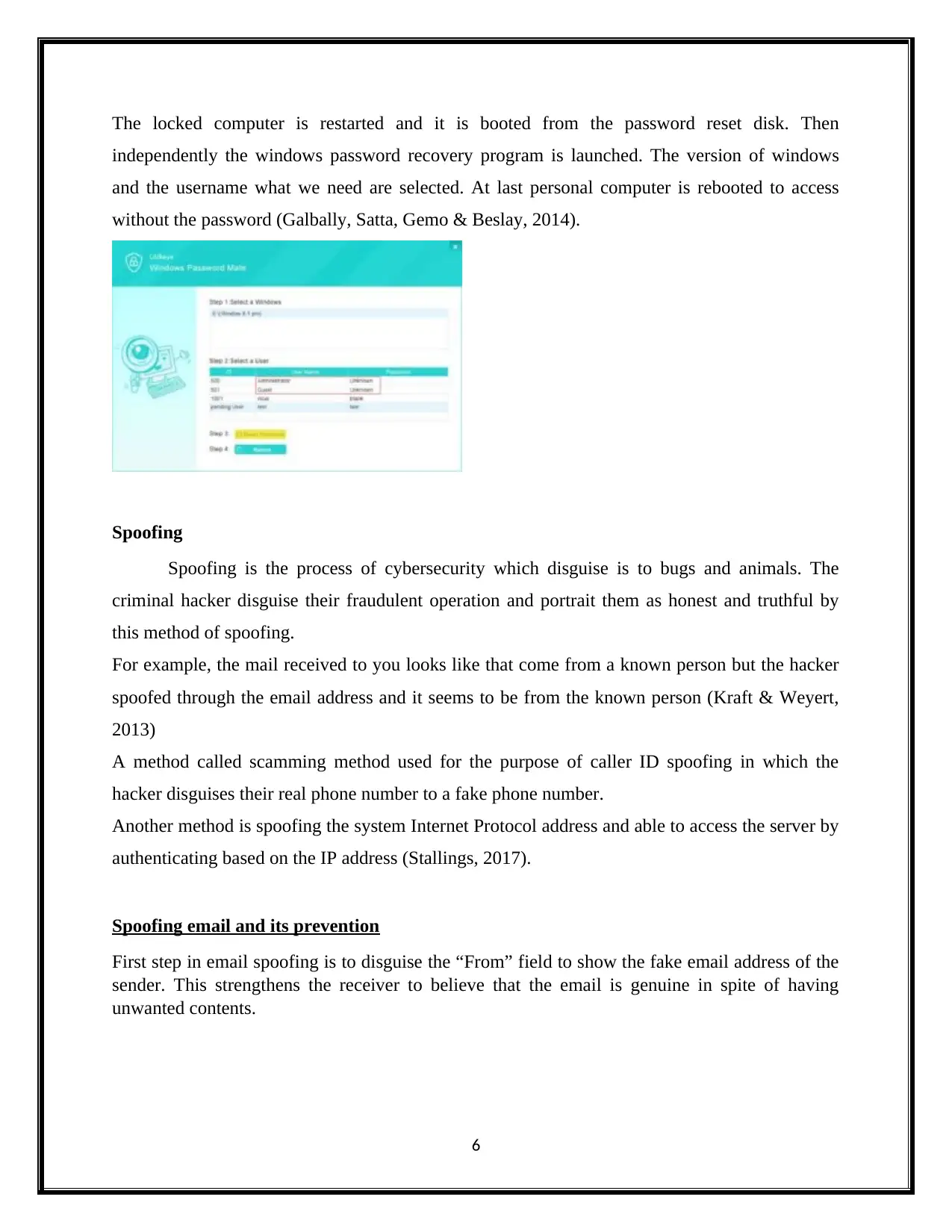
The locked computer is restarted and it is booted from the password reset disk. Then
independently the windows password recovery program is launched. The version of windows
and the username what we need are selected. At last personal computer is rebooted to access
without the password (Galbally, Satta, Gemo & Beslay, 2014).
Spoofing
Spoofing is the process of cybersecurity which disguise is to bugs and animals. The
criminal hacker disguise their fraudulent operation and portrait them as honest and truthful by
this method of spoofing.
For example, the mail received to you looks like that come from a known person but the hacker
spoofed through the email address and it seems to be from the known person (Kraft & Weyert,
2013)
A method called scamming method used for the purpose of caller ID spoofing in which the
hacker disguises their real phone number to a fake phone number.
Another method is spoofing the system Internet Protocol address and able to access the server by
authenticating based on the IP address (Stallings, 2017).
Spoofing email and its prevention
First step in email spoofing is to disguise the “From” field to show the fake email address of the
sender. This strengthens the receiver to believe that the email is genuine in spite of having
unwanted contents.
6
independently the windows password recovery program is launched. The version of windows
and the username what we need are selected. At last personal computer is rebooted to access
without the password (Galbally, Satta, Gemo & Beslay, 2014).
Spoofing
Spoofing is the process of cybersecurity which disguise is to bugs and animals. The
criminal hacker disguise their fraudulent operation and portrait them as honest and truthful by
this method of spoofing.
For example, the mail received to you looks like that come from a known person but the hacker
spoofed through the email address and it seems to be from the known person (Kraft & Weyert,
2013)
A method called scamming method used for the purpose of caller ID spoofing in which the
hacker disguises their real phone number to a fake phone number.
Another method is spoofing the system Internet Protocol address and able to access the server by
authenticating based on the IP address (Stallings, 2017).
Spoofing email and its prevention
First step in email spoofing is to disguise the “From” field to show the fake email address of the
sender. This strengthens the receiver to believe that the email is genuine in spite of having
unwanted contents.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
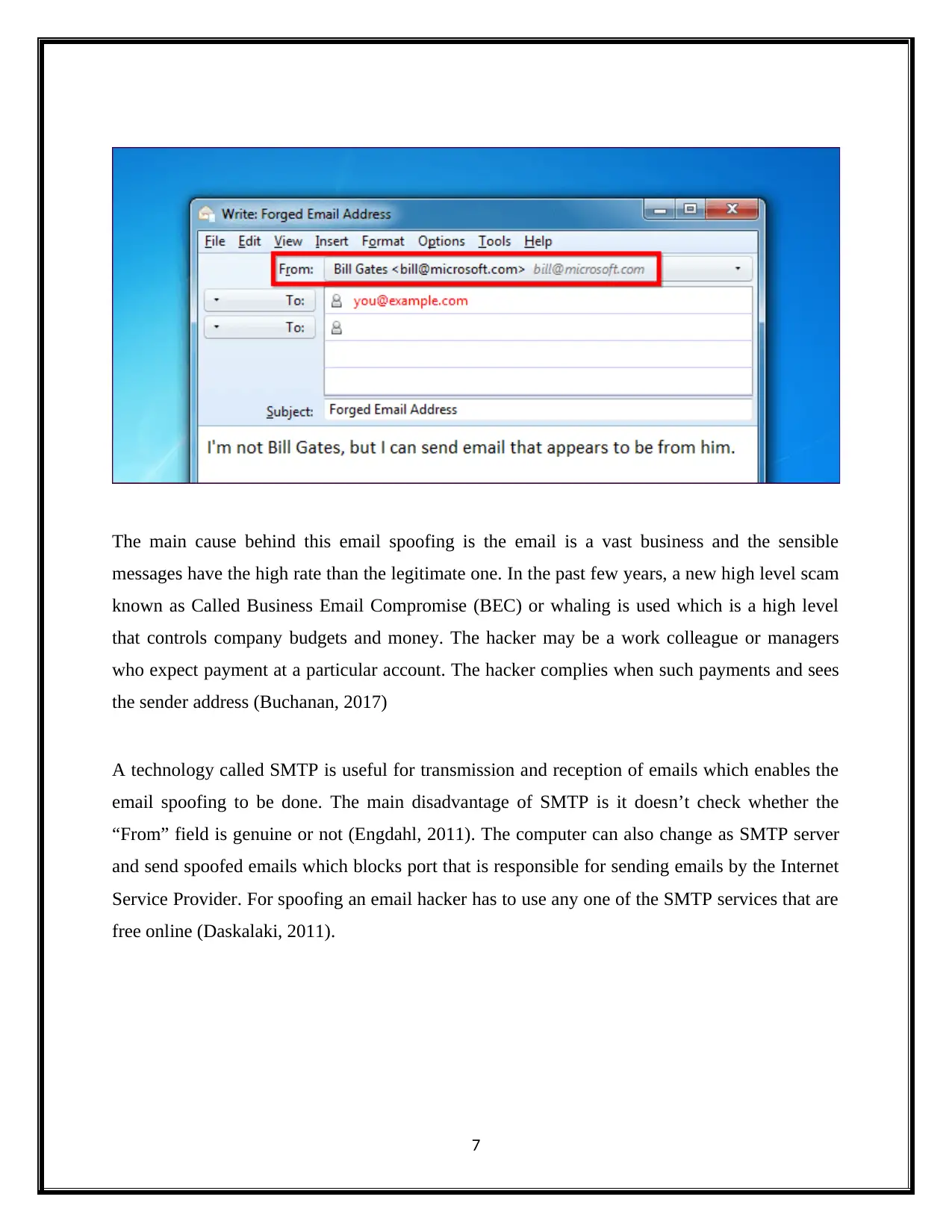
The main cause behind this email spoofing is the email is a vast business and the sensible
messages have the high rate than the legitimate one. In the past few years, a new high level scam
known as Called Business Email Compromise (BEC) or whaling is used which is a high level
that controls company budgets and money. The hacker may be a work colleague or managers
who expect payment at a particular account. The hacker complies when such payments and sees
the sender address (Buchanan, 2017)
A technology called SMTP is useful for transmission and reception of emails which enables the
email spoofing to be done. The main disadvantage of SMTP is it doesn’t check whether the
“From” field is genuine or not (Engdahl, 2011). The computer can also change as SMTP server
and send spoofed emails which blocks port that is responsible for sending emails by the Internet
Service Provider. For spoofing an email hacker has to use any one of the SMTP services that are
free online (Daskalaki, 2011).
7
messages have the high rate than the legitimate one. In the past few years, a new high level scam
known as Called Business Email Compromise (BEC) or whaling is used which is a high level
that controls company budgets and money. The hacker may be a work colleague or managers
who expect payment at a particular account. The hacker complies when such payments and sees
the sender address (Buchanan, 2017)
A technology called SMTP is useful for transmission and reception of emails which enables the
email spoofing to be done. The main disadvantage of SMTP is it doesn’t check whether the
“From” field is genuine or not (Engdahl, 2011). The computer can also change as SMTP server
and send spoofed emails which blocks port that is responsible for sending emails by the Internet
Service Provider. For spoofing an email hacker has to use any one of the SMTP services that are
free online (Daskalaki, 2011).
7
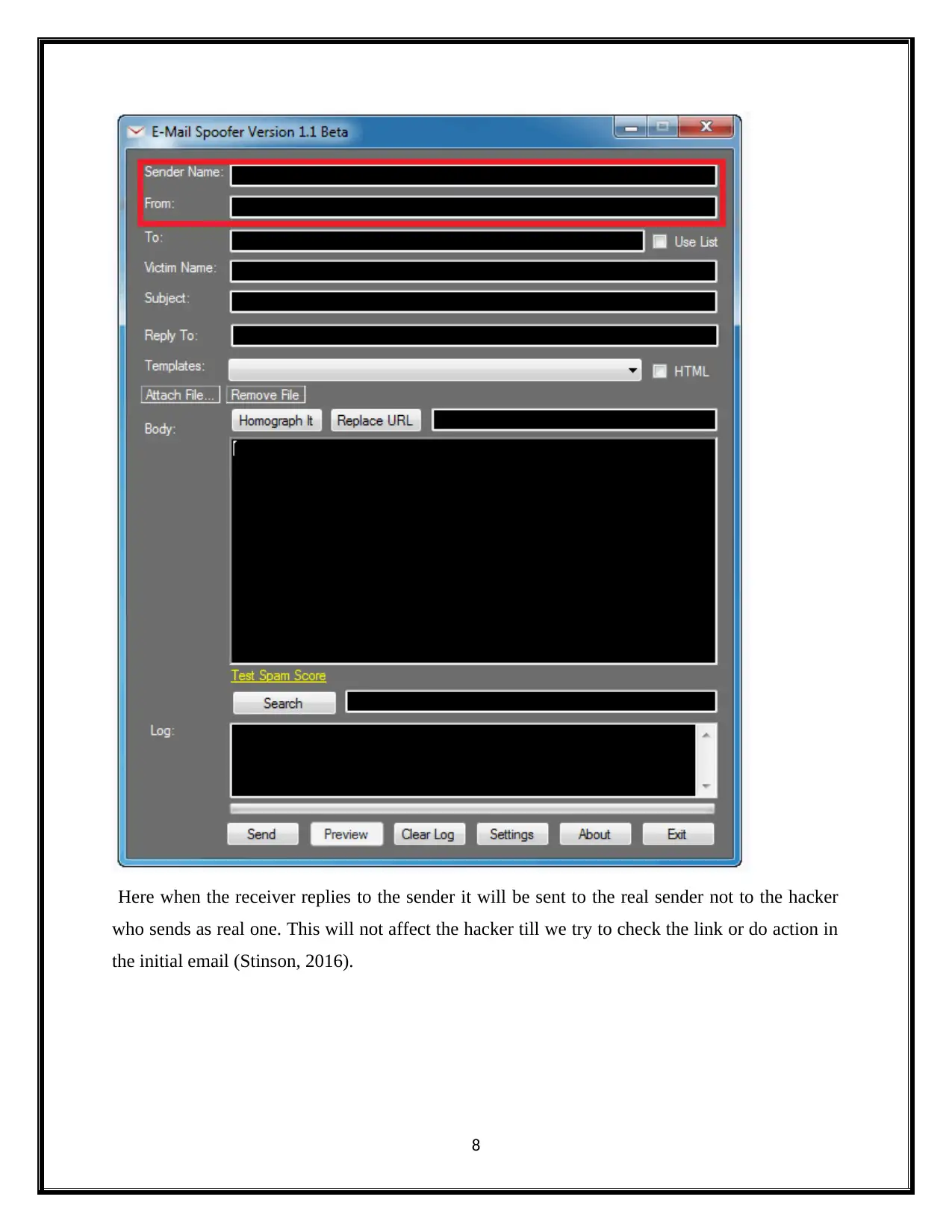
Here when the receiver replies to the sender it will be sent to the real sender not to the hacker
who sends as real one. This will not affect the hacker till we try to check the link or do action in
the initial email (Stinson, 2016).
8
who sends as real one. This will not affect the hacker till we try to check the link or do action in
the initial email (Stinson, 2016).
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
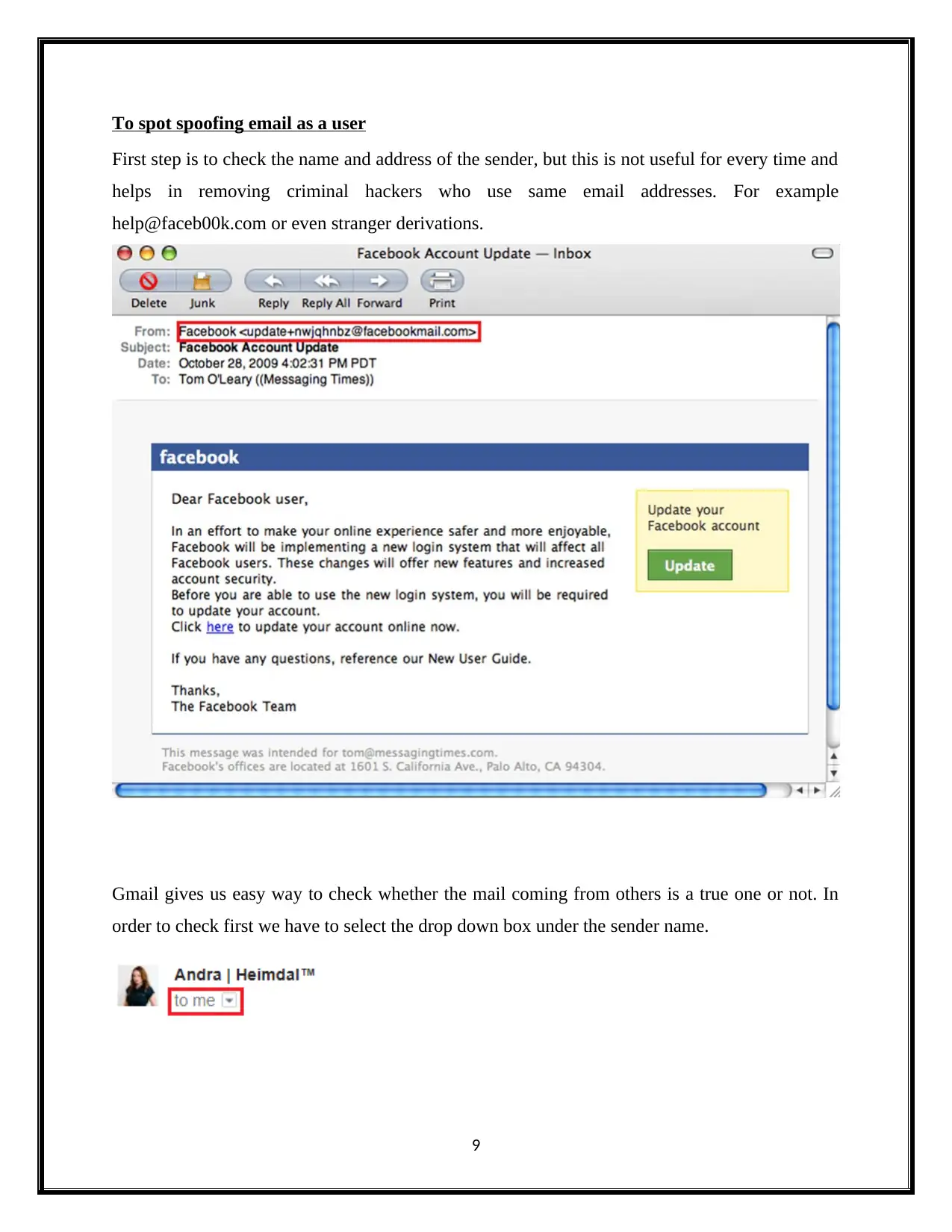
To spot spoofing email as a user
First step is to check the name and address of the sender, but this is not useful for every time and
helps in removing criminal hackers who use same email addresses. For example
help@faceb00k.com or even stranger derivations.
Gmail gives us easy way to check whether the mail coming from others is a true one or not. In
order to check first we have to select the drop down box under the sender name.
9
First step is to check the name and address of the sender, but this is not useful for every time and
helps in removing criminal hackers who use same email addresses. For example
help@faceb00k.com or even stranger derivations.
Gmail gives us easy way to check whether the mail coming from others is a true one or not. In
order to check first we have to select the drop down box under the sender name.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
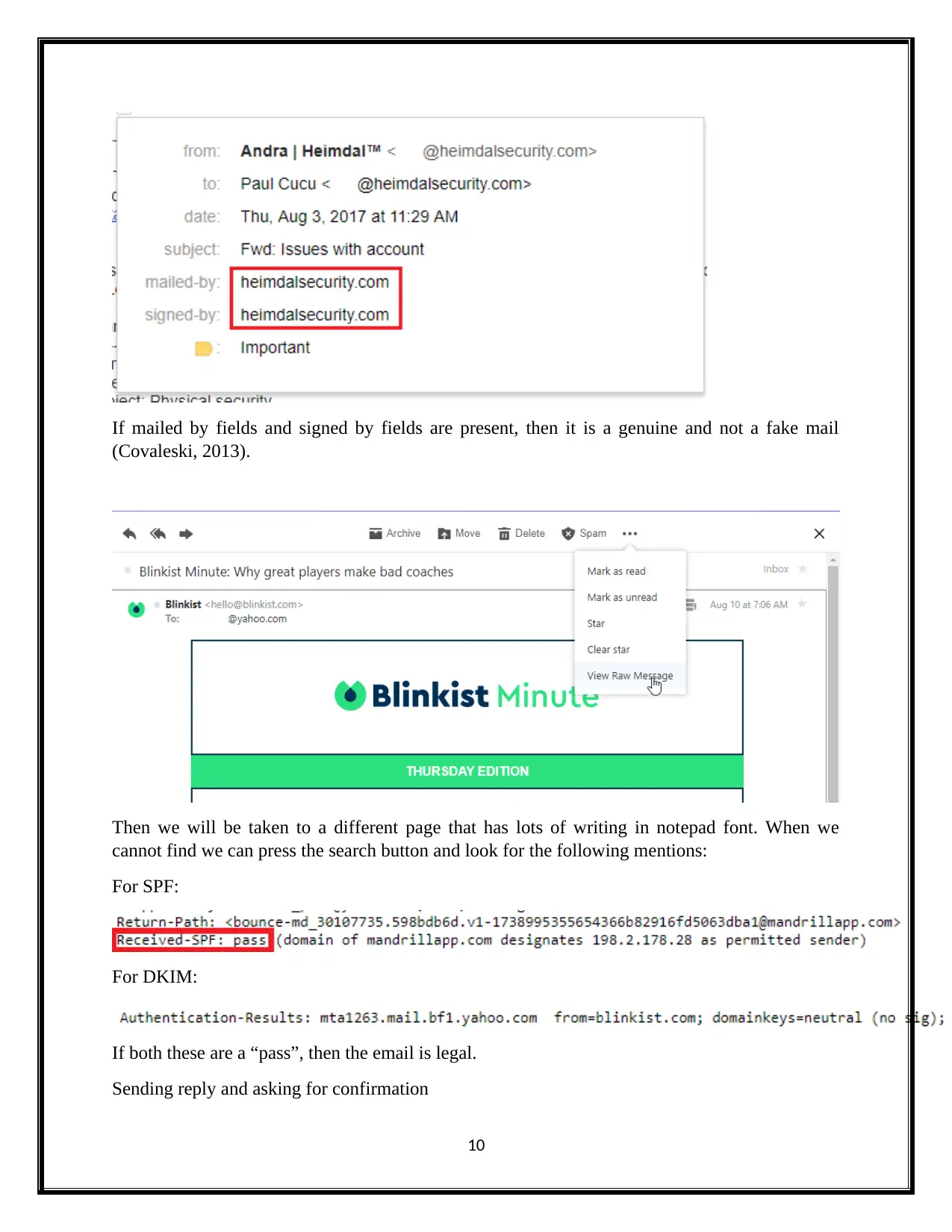
If mailed by fields and signed by fields are present, then it is a genuine and not a fake mail
(Covaleski, 2013).
Then we will be taken to a different page that has lots of writing in notepad font. When we
cannot find we can press the search button and look for the following mentions:
For SPF:
For DKIM:
If both these are a “pass”, then the email is legal.
Sending reply and asking for confirmation
10
(Covaleski, 2013).
Then we will be taken to a different page that has lots of writing in notepad font. When we
cannot find we can press the search button and look for the following mentions:
For SPF:
For DKIM:
If both these are a “pass”, then the email is legal.
Sending reply and asking for confirmation
10

By sending reply for the spoofed email, we can able to identify whether it is a mail from criminal
hacker because when we reply for that spoofing mail it goes to the original owner not to the
spoofer (Marshall, 2009).
Recovering data from formatted or corrupted USB/flash drive
First Windows CMD is used to fix the flash drive.
Select "Run" at start menu and type "cmd" in the input box. A command promote will be opened.
Type the command "CHKDSK [driveletter] /r" in the command promote. For instance flash
drive's drive letter is "E", then type command "CHKDSK E: /r" in command promote.
The command "CHKDSK" checks the specify disk for structure corruption. The paramter "/r"
helps command to repair the issues it finds.
It asks to save lost chains into files when all the above steps are completed. Select "Yes". Chkdsk
will report back what has done and go to my computer and check out the drive.
But sometimes, command "CHKDSK" can't repair logical error on the corrupted flash drive. At
that time, a third part data recovery tool is used to get lost data back.
Recover data from formatted and corrupted USB flash drive, pen drive with M3 data recovery
Free
First step is to connect the flash drive to the computer system and install the M3 data recovery
free. The program is run and select “Data Recovery” module (Gogolin, 2013)
11
hacker because when we reply for that spoofing mail it goes to the original owner not to the
spoofer (Marshall, 2009).
Recovering data from formatted or corrupted USB/flash drive
First Windows CMD is used to fix the flash drive.
Select "Run" at start menu and type "cmd" in the input box. A command promote will be opened.
Type the command "CHKDSK [driveletter] /r" in the command promote. For instance flash
drive's drive letter is "E", then type command "CHKDSK E: /r" in command promote.
The command "CHKDSK" checks the specify disk for structure corruption. The paramter "/r"
helps command to repair the issues it finds.
It asks to save lost chains into files when all the above steps are completed. Select "Yes". Chkdsk
will report back what has done and go to my computer and check out the drive.
But sometimes, command "CHKDSK" can't repair logical error on the corrupted flash drive. At
that time, a third part data recovery tool is used to get lost data back.
Recover data from formatted and corrupted USB flash drive, pen drive with M3 data recovery
Free
First step is to connect the flash drive to the computer system and install the M3 data recovery
free. The program is run and select “Data Recovery” module (Gogolin, 2013)
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

