Digital Forensics (Doc) | Assignment
Added on 2020-03-16
26 Pages2413 Words62 Views
DIGITAL FORENSICS

Executive summaryCompany A is a construction company. The CEO of company A suspects that some fileshave been stolen. The CEO also notices that an employee formats his USB drive frequently.Before the stolen information reaches the approver, the company A has to inform the approverabout the stolen files and file information and has to track the company which submits the samefile. The company A contacts the forensic investigator and asks them to find out the files theftand the details of the files. The investigator investigates the suspected employee and catches hisUSB drive which is in formatted mode. The investigator retrieves the data from the formattedUSB drive and also the suspected employee’s network traffic. By using wire shark trafficanalyzer it is found that the suspected employee has spoofed the company’s mail address usingmail spoofing software. The investigator retrieves the data in USB but it appears to be inencrypted format and the investigator user rainbow cracker to crack the password of theencrypted file and the investigator provides the file details to company A. Company A transfersthe information to Approver to decertify the work if submitted by other companies. Thecompany A provides the investigated details to the approver for proof.1

Table of Contents1.Introduction.......................................................................................................................................42.Analysis..............................................................................................................................................43.Findings............................................................................................................................................144.Conclusion........................................................................................................................................175.Appendix..........................................................................................................................................17Reference..................................................................................................................................................252

Glossaryforensic : Crime investigation scienceUSB : Universal Serial Bus is an industry standard in digital devices communicationWireshark : Formerly called as Ethereal , is a network pocket capturing and investigation toolSpoofing : Identity cheating to get access to others datarainbow cracker : A hash cracking toolencrypted file : Format changed file which cannot be read without decryptingScam : Illegal way of cheating peopleCaller ID : Identification details of the communication initiatorIP Address : Numerical address of a network connected deviceGmail : Email service provider3

1.IntroductionCompany A suspects some files have been stolen. It has to provide the details of the stolen fileswith the investigation report to stop others from using the file. Company A contacts the forensicofficer. The forensic officer finds out that the attacker has hacked the CEO’s computer usingophcrack and copied files to the USB drive and sent from his computer using a proofed addressto some other company. The investigator retrieves the formatted USB drive of the suspectedemployee and opens the encrypted files using ophcrack. The investigation will be carried basedon the complaints provided by the CEO. The investigation results will be provided which will behelpful for company A to submit it to the approver2.AnalysisTools used by attackerOphcrackEmail spoofing softwareTools used by investigatorUSB data retrieval (from formatted USB)Rainbow cracker software(to find password of encrypted file)Hacking password protected computer by ophcrackIn order to crack password that are very simple and short a tool called ophcrack is used.Even though the ophcrack tool is an old tool, we can use the tool with some limitations.The ophcrack tool is downloaded from the website and the ISO image file is burned intoUniversal serial bus or compact disc (Ophcrack, 2012). The locked personal computer is started by ophcrack and select “Ophcrack Graphic Mode –Automatic”It takes some time to recover the password of the computer. once the password is recovered itwill be displayed on the user interface of the ophcrack tool (Blackstone & Lewis, 2007).4

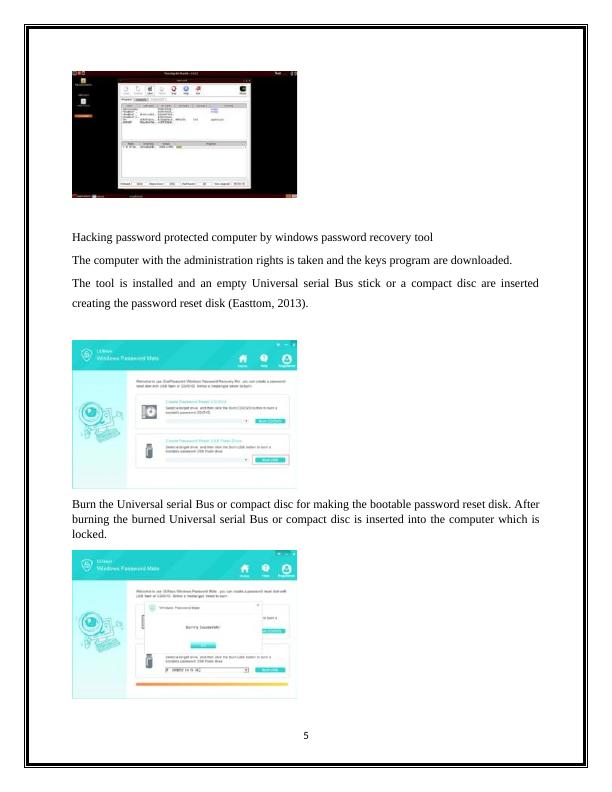
Hacking password protected computer by windows password recovery toolThe computer with the administration rights is taken and the keys program are downloaded.The tool is installed and an empty Universal serial Bus stick or a compact disc are insertedcreating the password reset disk (Easttom, 2013).Burn the Universal serial Bus or compact disc for making the bootable password reset disk. Afterburning the burned Universal serial Bus or compact disc is inserted into the computer which islocked.5
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Assignment of Digital Forensicslg...
|18
|1528
|292
Digital Forensic Investigation of Recovering Corrupted Image Fileslg...
|19
|2319
|447
