Digital Forensics: Recovering Scrambled Bits and Suspicious Data
Added on 2023-06-08
25 Pages2901 Words132 Views
DIGITAL FORENSICS

Table of Contents
Task – 1..................................................................................................................................................2
Recover the Scrambled Bits...................................................................................................................2
Task – 2..................................................................................................................................................6
Introduction...........................................................................................................................................6
1.1 Background............................................................................................................................6
1.2 Scope.....................................................................................................................................6
1.3 System Requirement..............................................................................................................6
1.4 Forensic tool..........................................................................................................................7
Analysis..................................................................................................................................................7
1.5 Winhex..................................................................................................................................7
1.6 Steganography.......................................................................................................................8
1.7 Pro Discover Tool..................................................................................................................8
Finding and Evidence.............................................................................................................................9
1.8 Recovering the deleted image from the USB with the help of Winhex..................................9
1.9 From Image recovering the hidden text with the help of Steganography Tool.....................16
1.10 Recovering the Files from the USB with the help of Pro Discover Tool..............................19
Conclusion...........................................................................................................................................23
References...........................................................................................................................................24
1
Task – 1..................................................................................................................................................2
Recover the Scrambled Bits...................................................................................................................2
Task – 2..................................................................................................................................................6
Introduction...........................................................................................................................................6
1.1 Background............................................................................................................................6
1.2 Scope.....................................................................................................................................6
1.3 System Requirement..............................................................................................................6
1.4 Forensic tool..........................................................................................................................7
Analysis..................................................................................................................................................7
1.5 Winhex..................................................................................................................................7
1.6 Steganography.......................................................................................................................8
1.7 Pro Discover Tool..................................................................................................................8
Finding and Evidence.............................................................................................................................9
1.8 Recovering the deleted image from the USB with the help of Winhex..................................9
1.9 From Image recovering the hidden text with the help of Steganography Tool.....................16
1.10 Recovering the Files from the USB with the help of Pro Discover Tool..............................19
Conclusion...........................................................................................................................................23
References...........................................................................................................................................24
1

Task – 1
Recover the Scrambled Bits
Here, the scrambled bits will be recovered by using Winhex digital forensics tool.
This tools is used for data recovery and it gives the effective data recovery for digital
forensics analysis. The recovery of scrambled bit follows the below steps to recovery the
scrambled bits.
First user needs to open the Winhex forensic Tool. It is shown below (Advances in Digital
Forensics 9, 2016).
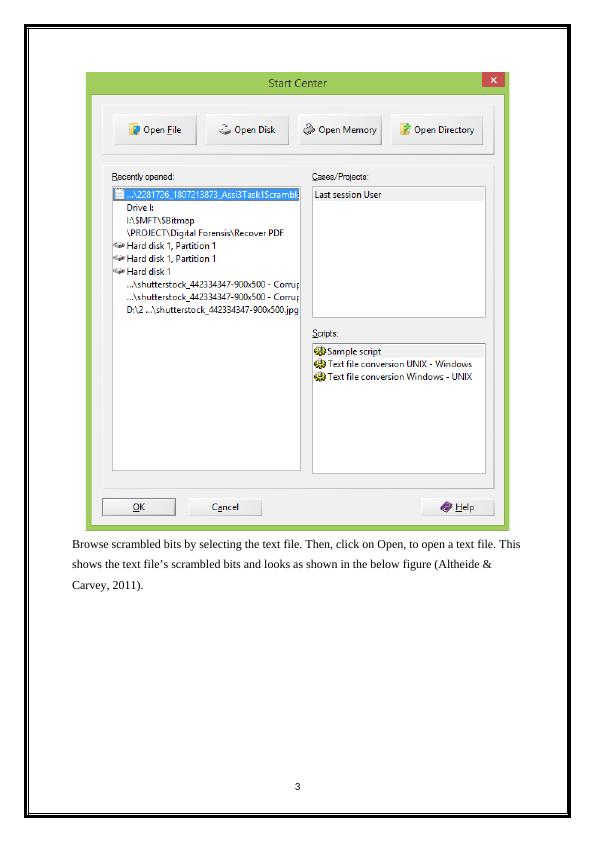
Then, choose “Start center” for opening the scrambled bits. To select start center click on the
tools option and choose, Start center. Once the scrambled bits opens. This process is
represented in the below figure.
2
Recover the Scrambled Bits
Here, the scrambled bits will be recovered by using Winhex digital forensics tool.
This tools is used for data recovery and it gives the effective data recovery for digital
forensics analysis. The recovery of scrambled bit follows the below steps to recovery the
scrambled bits.
First user needs to open the Winhex forensic Tool. It is shown below (Advances in Digital
Forensics 9, 2016).
Then, choose “Start center” for opening the scrambled bits. To select start center click on the
tools option and choose, Start center. Once the scrambled bits opens. This process is
represented in the below figure.
2

Browse scrambled bits by selecting the text file. Then, click on Open, to open a text file. This
shows the text file’s scrambled bits and looks as shown in the below figure (Altheide &
Carvey, 2011).
3
shows the text file’s scrambled bits and looks as shown in the below figure (Altheide &
Carvey, 2011).
3
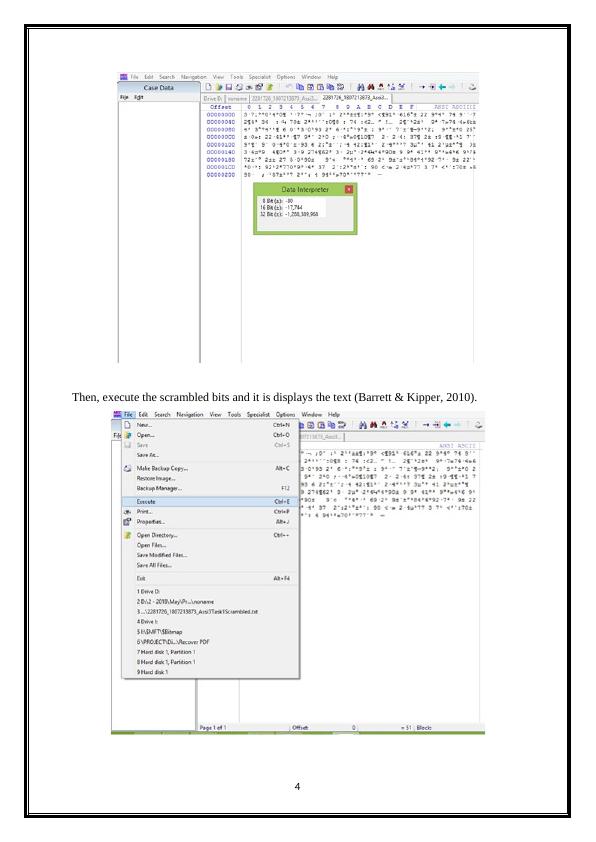
Then, execute the scrambled bits and it is displays the text (Barrett & Kipper, 2010).
4
4
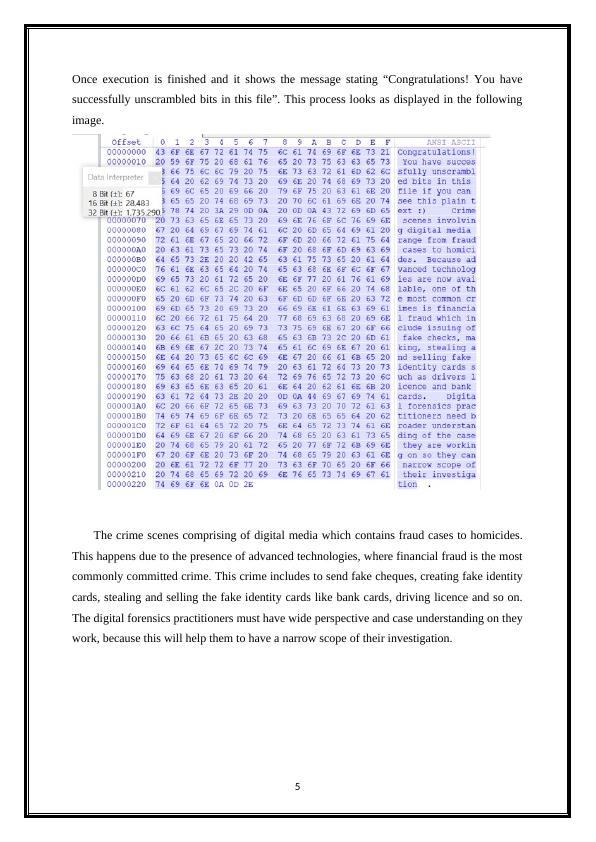
Once execution is finished and it shows the message stating “Congratulations! You have
successfully unscrambled bits in this file”. This process looks as displayed in the following
image.
The crime scenes comprising of digital media which contains fraud cases to homicides.
This happens due to the presence of advanced technologies, where financial fraud is the most
commonly committed crime. This crime includes to send fake cheques, creating fake identity
cards, stealing and selling the fake identity cards like bank cards, driving licence and so on.
The digital forensics practitioners must have wide perspective and case understanding on they
work, because this will help them to have a narrow scope of their investigation.
5
successfully unscrambled bits in this file”. This process looks as displayed in the following
image.
The crime scenes comprising of digital media which contains fraud cases to homicides.
This happens due to the presence of advanced technologies, where financial fraud is the most
commonly committed crime. This crime includes to send fake cheques, creating fake identity
cards, stealing and selling the fake identity cards like bank cards, driving licence and so on.
The digital forensics practitioners must have wide perspective and case understanding on they
work, because this will help them to have a narrow scope of their investigation.
5
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Digital Forensics Report for EMTS Organizationlg...
|28
|2503
|371
University Semester.lg...
|25
|2602
|55
Digital Theft and Recovery Procedureslg...
|23
|1494
|138
Digital Forensics: Investigation and Recovery of Lost Datalg...
|21
|2379
|235
University Semester.lg...
|7
|184
|285
Digital Forensics Report for Exotic Mountain Tour Servicelg...
|24
|2567
|203
