Digital Forensics Report: Data Recovery and Analysis of USB Drive Data
VerifiedAdded on 2023/06/12
|19
|2633
|66
Report
AI Summary
This digital forensics report outlines an investigation into potential intellectual property theft by an employee of Exotic Mountain Tour Services (EMTS). The investigation focuses on a USB drive found at the employee's workstation to determine if it contains proprietary data belonging to EMTS or Superior Bicycle, LLC. The report details the use of various digital forensics tools, including Stenography software to uncover hidden text within images, ProDiscover to recover deleted files, and WinHex to retrieve a corrupted image. The methodologies, results, and findings of using these tools are presented with supporting evidence, demonstrating the process of recovering and analyzing potentially stolen data. The report also covers the background of the case, the scope of the project, and the analysis of the tools and techniques used in the investigation.

Digital Forensics
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
This undertaking intends to set up a digital forensics report the given situation. We have to
examine the plausible licensed innovation stolen by the Bob Apsen who is functioning as an
agreement worker of the Exotic Mountain Tour Services (EMTS). The EMTS Company has
completed an extremely costly showcasing marketing report investigation on client benefit gave
by the Superior Bicycle, LLC Company. The arrangement of the EMTS Company is to complete
a proficient promotion for a joint item arrangement of Superior Bicycles with their visit
administrations. EMTS is under nondisclosure simultaneousness with Superior Bicycles and
should guarantee this advancing exertion material. The manager of EMTS determined that the
USB drive on the work place of Bob Aspen. This investigation is to choose if the drive contains
restrictive EMTS or Superior Bicycles data. The EMTS boss also gives you some interesting
information he collected from the Web server official. EMTS channels all Web-based email
action experiencing its framework and recognizes suspicious associations. When a Web-based
email with associations is gotten, the Web channel is enacted. So we recovered the erased record
which has suspicious information that pertinent to the case documents from USB. It is finished
by utilizing Prodiscover essential. At that point the erased picture in USB is recovered and
furthermore this document was tainted while opening this record in Winhex. The fitting
advanced criminology apparatuses were utilized to achieve Recover process. For our situation
contemplate, we will utilize Winhex to recover the erased picture in the USB. The Stenography
instrument is utilized for recuperating the concealed content in Image. At that point utilizing the
Pro Discover, we recover the all the files. So these recovering strategies should be examined
before we continue to determination of results with appropriate evidences.
1
This undertaking intends to set up a digital forensics report the given situation. We have to
examine the plausible licensed innovation stolen by the Bob Apsen who is functioning as an
agreement worker of the Exotic Mountain Tour Services (EMTS). The EMTS Company has
completed an extremely costly showcasing marketing report investigation on client benefit gave
by the Superior Bicycle, LLC Company. The arrangement of the EMTS Company is to complete
a proficient promotion for a joint item arrangement of Superior Bicycles with their visit
administrations. EMTS is under nondisclosure simultaneousness with Superior Bicycles and
should guarantee this advancing exertion material. The manager of EMTS determined that the
USB drive on the work place of Bob Aspen. This investigation is to choose if the drive contains
restrictive EMTS or Superior Bicycles data. The EMTS boss also gives you some interesting
information he collected from the Web server official. EMTS channels all Web-based email
action experiencing its framework and recognizes suspicious associations. When a Web-based
email with associations is gotten, the Web channel is enacted. So we recovered the erased record
which has suspicious information that pertinent to the case documents from USB. It is finished
by utilizing Prodiscover essential. At that point the erased picture in USB is recovered and
furthermore this document was tainted while opening this record in Winhex. The fitting
advanced criminology apparatuses were utilized to achieve Recover process. For our situation
contemplate, we will utilize Winhex to recover the erased picture in the USB. The Stenography
instrument is utilized for recuperating the concealed content in Image. At that point utilizing the
Pro Discover, we recover the all the files. So these recovering strategies should be examined
before we continue to determination of results with appropriate evidences.
1

Table of Contents
Abstract......................................................................................................................................................1
1. Introduction.......................................................................................................................................3
1.1 Background Study of Given Case.............................................................................................3
1.2 Scope of Project.........................................................................................................................3
1.3 Tools and Techniques to be Used..............................................................................................3
2. Analysis of Tools and Techniques.....................................................................................................4
2.1 Stenography...............................................................................................................................4
2.2 WinHex.......................................................................................................................................4
2.3 Pro Discover...............................................................................................................................5
3. Results and Findings with the Evidences.........................................................................................5
3.1 Recover the hidden text in Image using Stenography tool......................................................5
3.2 Recover the file using Pro Discover..........................................................................................9
3.3 Recover the deleted image in the USB Using Winhex...........................................................10
4. Conclusion........................................................................................................................................16
References................................................................................................................................................17
2
Abstract......................................................................................................................................................1
1. Introduction.......................................................................................................................................3
1.1 Background Study of Given Case.............................................................................................3
1.2 Scope of Project.........................................................................................................................3
1.3 Tools and Techniques to be Used..............................................................................................3
2. Analysis of Tools and Techniques.....................................................................................................4
2.1 Stenography...............................................................................................................................4
2.2 WinHex.......................................................................................................................................4
2.3 Pro Discover...............................................................................................................................5
3. Results and Findings with the Evidences.........................................................................................5
3.1 Recover the hidden text in Image using Stenography tool......................................................5
3.2 Recover the file using Pro Discover..........................................................................................9
3.3 Recover the deleted image in the USB Using Winhex...........................................................10
4. Conclusion........................................................................................................................................16
References................................................................................................................................................17
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Introduction
1.1 Background Study of Given Case
The report will explore the probable intellectual innovation which is stolen by the Bob
Apsen who is filling in as an agreement worker of the Exotic Mountain Tour Services. The
EMTS Organization has been completed an exceptionally expensive advertising procedure and
examination on client benefit gave by the Superior Bicycle, LLC Company. The EMTS
Company has arranged to do an effective ad for a joint item arrangement of Superior Bicycles
with their administrations. EMTS is under nondisclosure simultaneousness with Superior
Bicycles and should guarantee this advancing agreement material. The manager of EMTS
determined that the USB drive on the work place of Bob Aspen.
This investigation is to choose if the drive contains restrictive EMTS or Superior
Bicycles data. The EMTS boss also gives you some interesting information he collected from the
Web server official. EMTS channels all Web-based email action experiencing its framework and
recognizes suspicious associations. When a Web-based email with associations is gotten, the
Web channel is enacted.
1.2 Scope of Project
This project focuses on to provide a digital forensic report for given case study. The
proper digital forensics tools have been used to perform recover system. So we will recover the
deleted report which has suspicious records that applicable to the case files from USB. The
Stenography device can be used for convalescing the hidden textual content in picture. Then
using the Pro Discover, we are able to recover the all the files from USB. In our case examine,
we're going to use Winhex to get better the deleted photograph in the USB. The study of these
techniques will be carried out in analysis section.
1.3 Tools and Techniques to be Used
The following tools will be used in this case study.
1. Stenography
2. Pro Discover
3. Winhex
3
1.1 Background Study of Given Case
The report will explore the probable intellectual innovation which is stolen by the Bob
Apsen who is filling in as an agreement worker of the Exotic Mountain Tour Services. The
EMTS Organization has been completed an exceptionally expensive advertising procedure and
examination on client benefit gave by the Superior Bicycle, LLC Company. The EMTS
Company has arranged to do an effective ad for a joint item arrangement of Superior Bicycles
with their administrations. EMTS is under nondisclosure simultaneousness with Superior
Bicycles and should guarantee this advancing agreement material. The manager of EMTS
determined that the USB drive on the work place of Bob Aspen.
This investigation is to choose if the drive contains restrictive EMTS or Superior
Bicycles data. The EMTS boss also gives you some interesting information he collected from the
Web server official. EMTS channels all Web-based email action experiencing its framework and
recognizes suspicious associations. When a Web-based email with associations is gotten, the
Web channel is enacted.
1.2 Scope of Project
This project focuses on to provide a digital forensic report for given case study. The
proper digital forensics tools have been used to perform recover system. So we will recover the
deleted report which has suspicious records that applicable to the case files from USB. The
Stenography device can be used for convalescing the hidden textual content in picture. Then
using the Pro Discover, we are able to recover the all the files from USB. In our case examine,
we're going to use Winhex to get better the deleted photograph in the USB. The study of these
techniques will be carried out in analysis section.
1.3 Tools and Techniques to be Used
The following tools will be used in this case study.
1. Stenography
2. Pro Discover
3. Winhex
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2. Analysis of Tools and Techniques
Based on the case study, we will analyse which tools are required to provide the best
solution for the given case and we should investigate about how they will be applied.In our case
study, we're going to use The Stenography device is used for getting better the hidden text in
image. We will be using the Remo recovery, to recover the pdf document. The Winhex tool will
be used to recover the deleted photograph within the USB. So those healing techniques need to
be analysed before finding outcomes.
2.1 Stenography
Steganography is the art of hiding a puzzle message at the back of the normal message. It
has the capacity to grasp what the licensed message which we predicted to pass on changed into.
This power of disguising puzzle messages has been used for a huge time span, the whole thing
taken into consideration, correspondences("Best Tools to Perform Steganography", 2018).
Because the evolvement of automatic correspondence, it has moreover been used as a bit of
cutting part talks. In computer, it's far talented via supplanting the unused or worthless
information of a general computer file with the bit of our puzzle message. This secret included
information can be a plain text, figure substance, or photo. You'll be able to conceal statistics in
any kind of record. Mostly picture, video and sound information are used to hide plain text or
image message. Barely any units by and by using empower one to cover reports inner a picture
or sound document.
Through using Steganography, we are able to reduce the probability of statistics spillage.
Not with standing whether or not the attacker selections up induction to our report or email, he'll
don't comprehend where the personal archive in our document is. There are numerous strategies
for achieving the steganography in reducing edge correspondence. Regardless, we don't want to
carry out coding to reap this. There are special programming gadgets are open for
Steganography. This item can cowl the secret message at the back of the image report, HTML
fil, doc report or a few different kind of report (Flandrin, 2018). The steganography of computer
forensics tool is useful for scientific knowledge for analysing, presenting and collecting the
evidence to the court. It is very helpful to ensure the overall survivability and integrity of
network infrastructure. It may provide the result in destroying the vital evidences. Basically this
tool have the various software and it is used to hide the secret text from the HTML files, Docx
4
Based on the case study, we will analyse which tools are required to provide the best
solution for the given case and we should investigate about how they will be applied.In our case
study, we're going to use The Stenography device is used for getting better the hidden text in
image. We will be using the Remo recovery, to recover the pdf document. The Winhex tool will
be used to recover the deleted photograph within the USB. So those healing techniques need to
be analysed before finding outcomes.
2.1 Stenography
Steganography is the art of hiding a puzzle message at the back of the normal message. It
has the capacity to grasp what the licensed message which we predicted to pass on changed into.
This power of disguising puzzle messages has been used for a huge time span, the whole thing
taken into consideration, correspondences("Best Tools to Perform Steganography", 2018).
Because the evolvement of automatic correspondence, it has moreover been used as a bit of
cutting part talks. In computer, it's far talented via supplanting the unused or worthless
information of a general computer file with the bit of our puzzle message. This secret included
information can be a plain text, figure substance, or photo. You'll be able to conceal statistics in
any kind of record. Mostly picture, video and sound information are used to hide plain text or
image message. Barely any units by and by using empower one to cover reports inner a picture
or sound document.
Through using Steganography, we are able to reduce the probability of statistics spillage.
Not with standing whether or not the attacker selections up induction to our report or email, he'll
don't comprehend where the personal archive in our document is. There are numerous strategies
for achieving the steganography in reducing edge correspondence. Regardless, we don't want to
carry out coding to reap this. There are special programming gadgets are open for
Steganography. This item can cowl the secret message at the back of the image report, HTML
fil, doc report or a few different kind of report (Flandrin, 2018). The steganography of computer
forensics tool is useful for scientific knowledge for analysing, presenting and collecting the
evidence to the court. It is very helpful to ensure the overall survivability and integrity of
network infrastructure. It may provide the result in destroying the vital evidences. Basically this
tool have the various software and it is used to hide the secret text from the HTML files, Docx
4

file, Image files and any kind of the file. In our case study, we are using the image steganography
tool because we will the recover the hidden text in the images. So, this tool is very useful tool to
recover the hidden text and it is also hiding the user information in the image file.
2.2 WinHex
For mistakenly erased documents or by and large after an accomplished loss of
information. Should be possible physically (see undeleting documents) or naturally. There is a
programmed recuperation mode for FAT12, FAT16, FAT32, and NTFS drives called "Document
Recovery by Name" that basically expects you to determine at least one record covers (like *.gif,
John*.doc, and so forth.). WinHex will wrap up. Through the Access catch menu, a recuperation
component is accessible for FAT drives which re-makes whole settled catalogue structures
(points of interest here).
Another component ("File Recovery by Type", once in the past "document recovery")
can be utilized on any record framework and recuperates all documents of a specific kind at any
given moment. Upheld document writes: jpg, png, gif, tif, bmp, dwg, psd, rtf, xml, html, eml,
dbx, xls/doc, mdb, wpd, eps/ps, pdf, qdf, pwl, zip, rar, wav, avi, slam, rm, mpg, mpg, mov, asf,
mid. Specifically proprietors of computerized cameras regularly experience issues with their
media. WinHex is probably going to help with this mechanized capacity that makes great
utilization of the presence of record headers (trademark marks toward the start of a document),
("WinHex: A powerful data recovery and forensics tool", 2018).
2.3 Pro Discover
The pro discover tool is a very powerful tool for computer security and it enables the
professional to determine the all the data on the computer disk. It is used to protecting the
evidence and creating the quality reports for use in legal proceedings. It creates the bit stream
copy of disk to analyse and it maintains the multi tool compatibility by writing and reading
images. It has various features such as,
Examine the Linux file systems
Automated report generation
Integrated and GUI interface function is used to assure the ease of use and quick start.
Integrated thumbnail graphics
Utilize the Perl scripts
Utilize the user provide and national Drug intelligence
5
tool because we will the recover the hidden text in the images. So, this tool is very useful tool to
recover the hidden text and it is also hiding the user information in the image file.
2.2 WinHex
For mistakenly erased documents or by and large after an accomplished loss of
information. Should be possible physically (see undeleting documents) or naturally. There is a
programmed recuperation mode for FAT12, FAT16, FAT32, and NTFS drives called "Document
Recovery by Name" that basically expects you to determine at least one record covers (like *.gif,
John*.doc, and so forth.). WinHex will wrap up. Through the Access catch menu, a recuperation
component is accessible for FAT drives which re-makes whole settled catalogue structures
(points of interest here).
Another component ("File Recovery by Type", once in the past "document recovery")
can be utilized on any record framework and recuperates all documents of a specific kind at any
given moment. Upheld document writes: jpg, png, gif, tif, bmp, dwg, psd, rtf, xml, html, eml,
dbx, xls/doc, mdb, wpd, eps/ps, pdf, qdf, pwl, zip, rar, wav, avi, slam, rm, mpg, mpg, mov, asf,
mid. Specifically proprietors of computerized cameras regularly experience issues with their
media. WinHex is probably going to help with this mechanized capacity that makes great
utilization of the presence of record headers (trademark marks toward the start of a document),
("WinHex: A powerful data recovery and forensics tool", 2018).
2.3 Pro Discover
The pro discover tool is a very powerful tool for computer security and it enables the
professional to determine the all the data on the computer disk. It is used to protecting the
evidence and creating the quality reports for use in legal proceedings. It creates the bit stream
copy of disk to analyse and it maintains the multi tool compatibility by writing and reading
images. It has various features such as,
Examine the Linux file systems
Automated report generation
Integrated and GUI interface function is used to assure the ease of use and quick start.
Integrated thumbnail graphics
Utilize the Perl scripts
Utilize the user provide and national Drug intelligence
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Prove the data integrity
Search the entire disk
Internet history
Event log file
Integrated viewer to examine the files
Ensure high quality
Extracts the EXIF information
Examine the sun Solaris UFS file
The pro discover tool is used to handle the organization security concerns. It basically designed
to NIST disk imaging tool and it insure the high quality. It supports the VM ware to run the
captured images. It is used to provide the power search capability is flexible and fast. It creates
the bit stream the copy of hard drive and disk to analyse to maintain the original evidence safe. It
uses the lease destructive methodology and industry best practices to allow the examination of
files without altering the valuable Meta data such as last time accessed. It is used to hide the data
and reads the disk at the sector level.
3. Results and Findings with the Evidences
3.1 Recover the hidden text in Image using Stenography tool
To recover the concealed content in picture utilizing the stenography device and it used to
give the powerful and effective information recuperation for windows. It is most generally
utilized programming for information recuperation and concealed content recuperation. The
beneath pictures has shrouded content and it needs to recouped by utilizing the stenography
device. It is demonstrated as follows.
6
Search the entire disk
Internet history
Event log file
Integrated viewer to examine the files
Ensure high quality
Extracts the EXIF information
Examine the sun Solaris UFS file
The pro discover tool is used to handle the organization security concerns. It basically designed
to NIST disk imaging tool and it insure the high quality. It supports the VM ware to run the
captured images. It is used to provide the power search capability is flexible and fast. It creates
the bit stream the copy of hard drive and disk to analyse to maintain the original evidence safe. It
uses the lease destructive methodology and industry best practices to allow the examination of
files without altering the valuable Meta data such as last time accessed. It is used to hide the data
and reads the disk at the sector level.
3. Results and Findings with the Evidences
3.1 Recover the hidden text in Image using Stenography tool
To recover the concealed content in picture utilizing the stenography device and it used to
give the powerful and effective information recuperation for windows. It is most generally
utilized programming for information recuperation and concealed content recuperation. The
beneath pictures has shrouded content and it needs to recouped by utilizing the stenography
device. It is demonstrated as follows.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
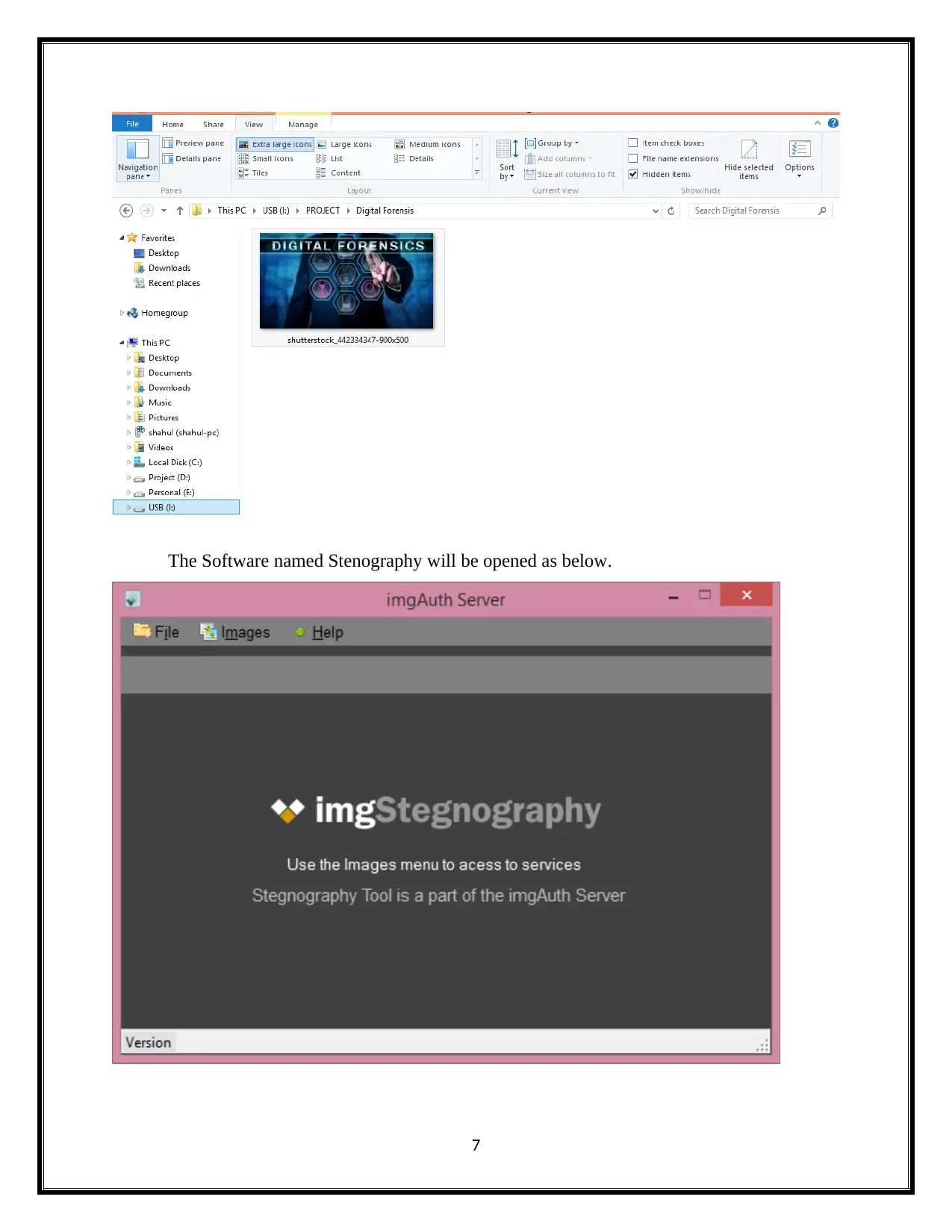
The Software named Stenography will be opened as below.
7
7
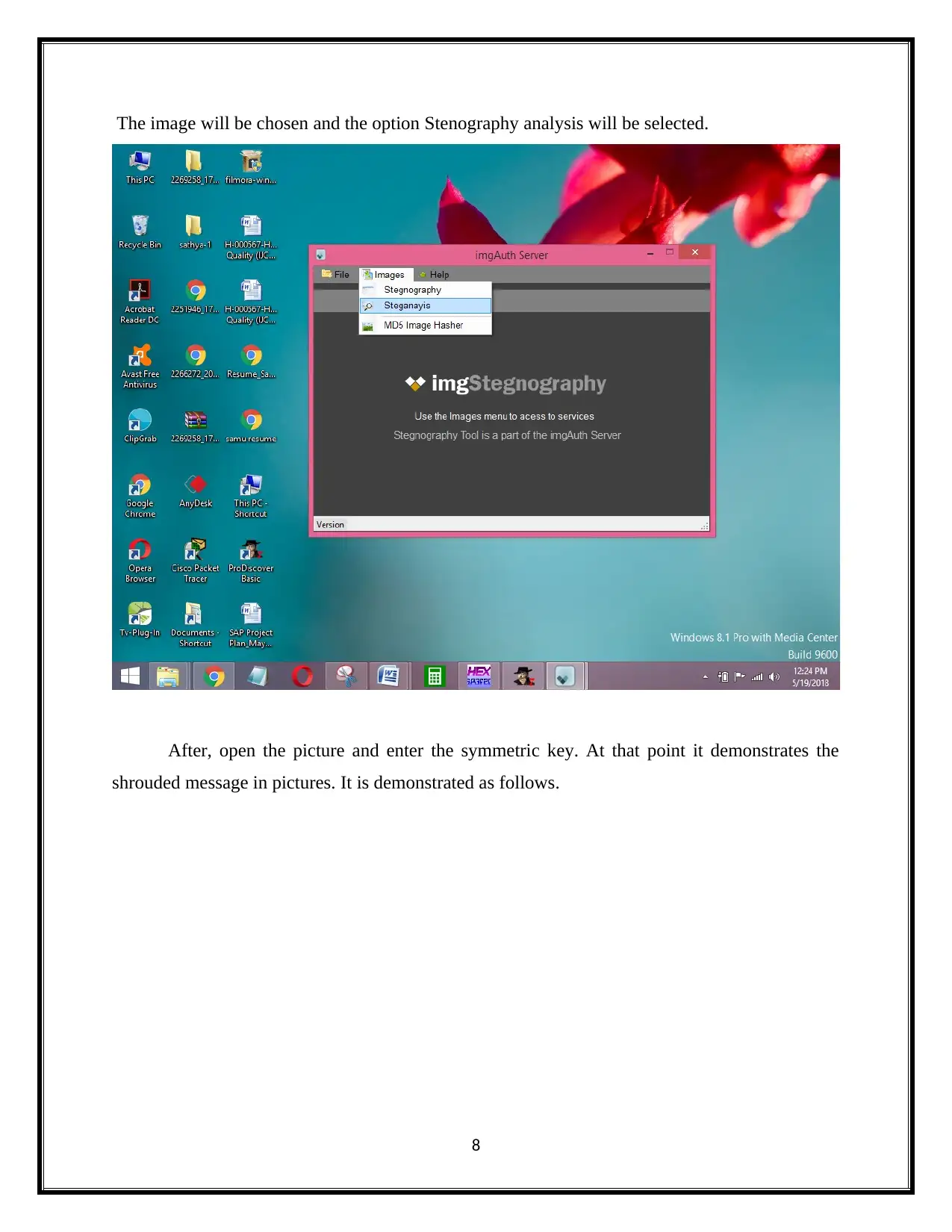
The image will be chosen and the option Stenography analysis will be selected.
After, open the picture and enter the symmetric key. At that point it demonstrates the
shrouded message in pictures. It is demonstrated as follows.
8
After, open the picture and enter the symmetric key. At that point it demonstrates the
shrouded message in pictures. It is demonstrated as follows.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
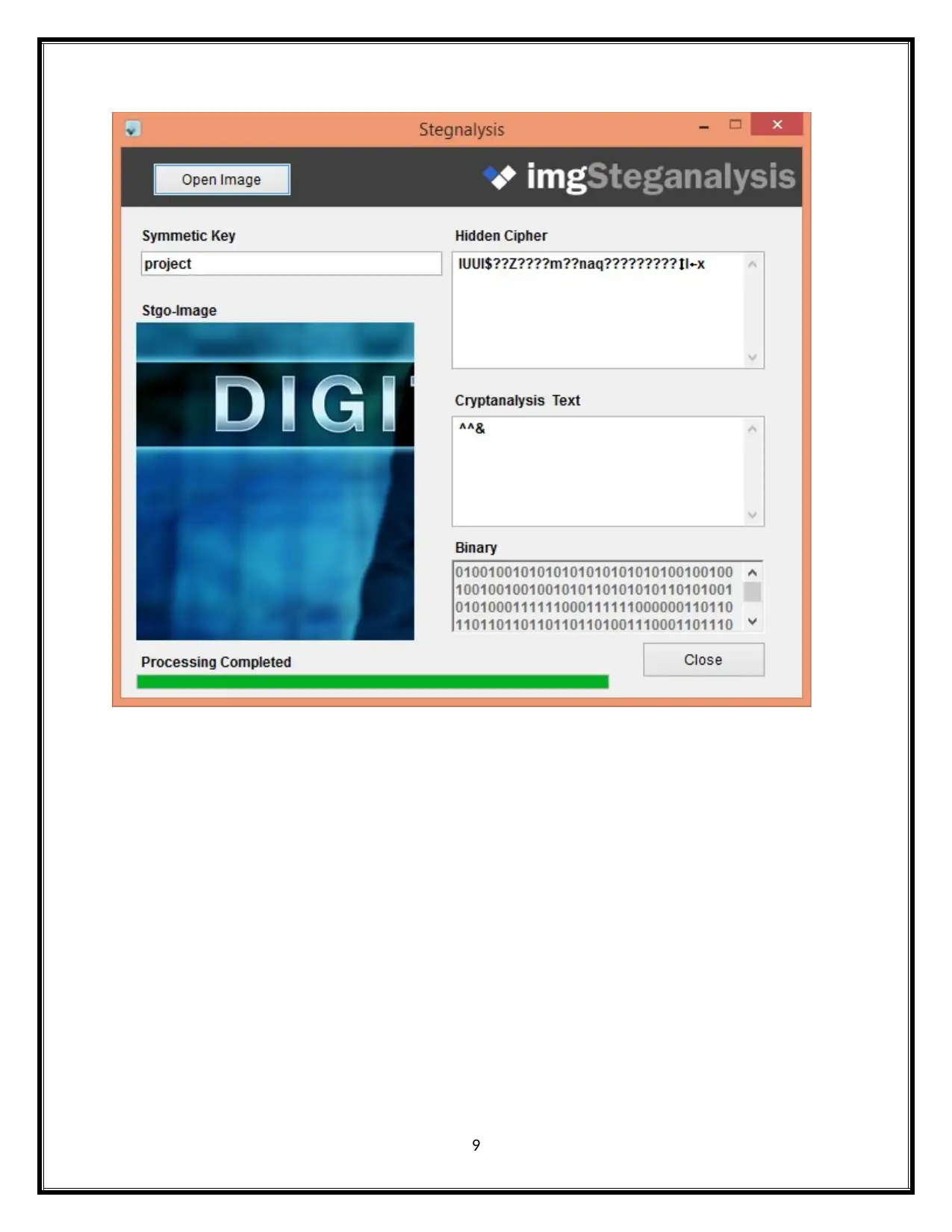
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
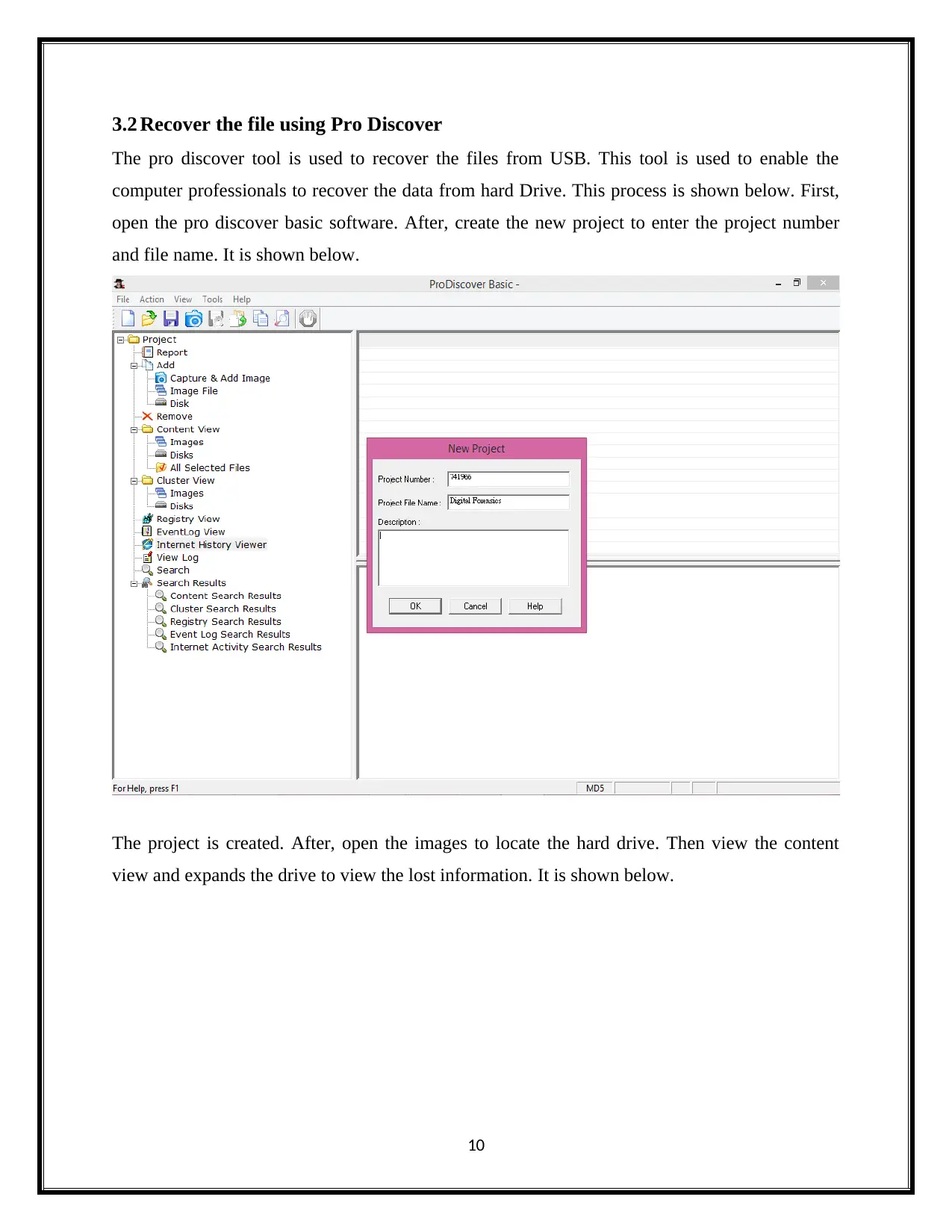
3.2 Recover the file using Pro Discover
The pro discover tool is used to recover the files from USB. This tool is used to enable the
computer professionals to recover the data from hard Drive. This process is shown below. First,
open the pro discover basic software. After, create the new project to enter the project number
and file name. It is shown below.
The project is created. After, open the images to locate the hard drive. Then view the content
view and expands the drive to view the lost information. It is shown below.
10
The pro discover tool is used to recover the files from USB. This tool is used to enable the
computer professionals to recover the data from hard Drive. This process is shown below. First,
open the pro discover basic software. After, create the new project to enter the project number
and file name. It is shown below.
The project is created. After, open the images to locate the hard drive. Then view the content
view and expands the drive to view the lost information. It is shown below.
10
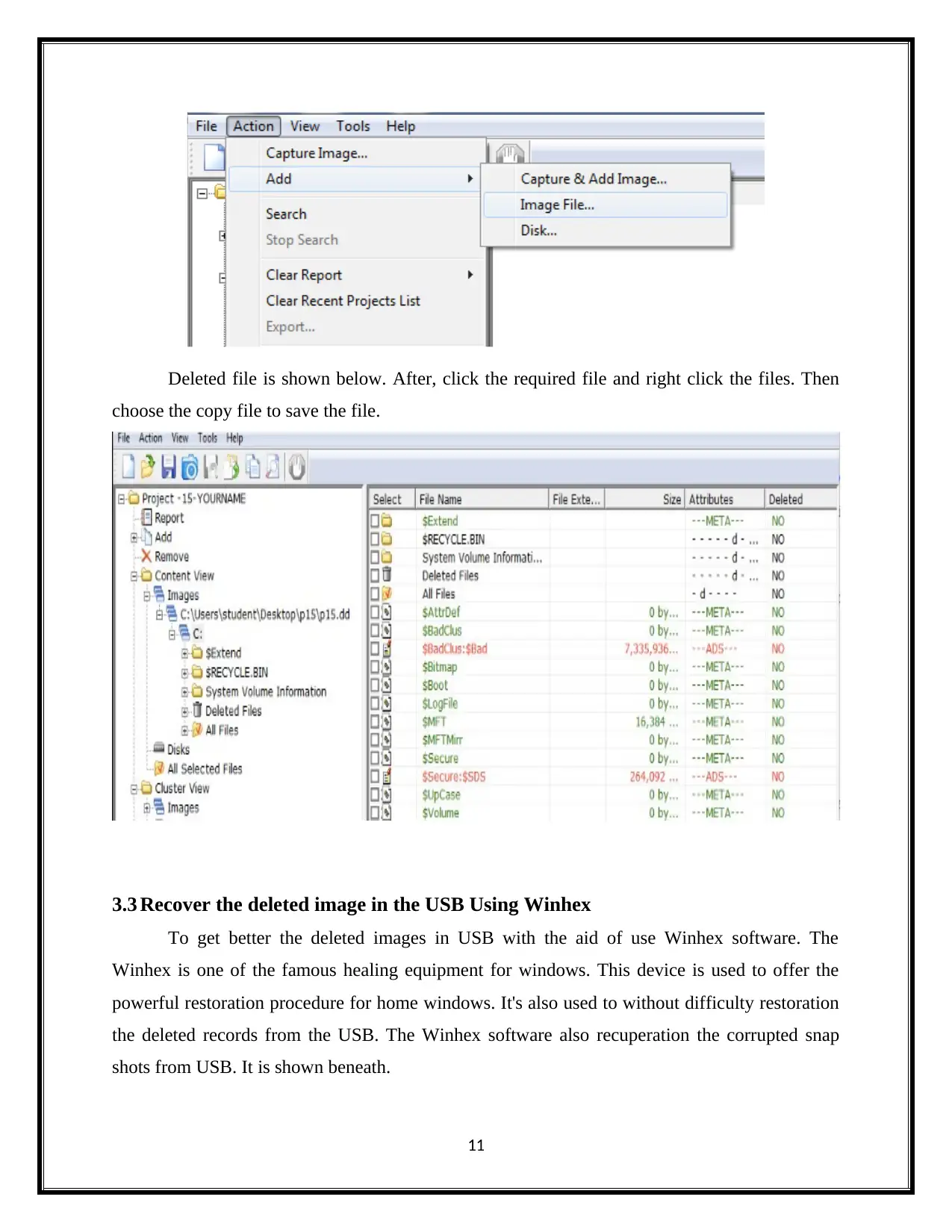
Deleted file is shown below. After, click the required file and right click the files. Then
choose the copy file to save the file.
3.3 Recover the deleted image in the USB Using Winhex
To get better the deleted images in USB with the aid of use Winhex software. The
Winhex is one of the famous healing equipment for windows. This device is used to offer the
powerful restoration procedure for home windows. It's also used to without difficulty restoration
the deleted records from the USB. The Winhex software also recuperation the corrupted snap
shots from USB. It is shown beneath.
11
choose the copy file to save the file.
3.3 Recover the deleted image in the USB Using Winhex
To get better the deleted images in USB with the aid of use Winhex software. The
Winhex is one of the famous healing equipment for windows. This device is used to offer the
powerful restoration procedure for home windows. It's also used to without difficulty restoration
the deleted records from the USB. The Winhex software also recuperation the corrupted snap
shots from USB. It is shown beneath.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



