Digital Security Report: Ruskin City Council, Digital Security Module
VerifiedAdded on 2023/04/21
|16
|3334
|170
Report
AI Summary
This report addresses key aspects of digital security, focusing on the Computer Misuse Act, cryptography, and secure programming techniques within the context of Ruskin City Council. It begins by defining cybercrime, its societal impact, and the role of the Computer Misuse Act in mitigating digital threats. The report then delves into cryptography, exploring different encryption techniques, their applications, and the risks associated with sensitive data. Finally, it examines secure programming practices, emphasizing the importance of complex codes, the OWASP framework, and common security attacks in the hospital industry, offering recommendations for improved security measures. The report aims to provide a comprehensive understanding of digital security principles and their practical application in a real-world scenario, offering insights into safeguarding digital assets and mitigating cyber threats.

Running head: DIGITAL SECURITY
Digital Security
Module Title
Course Code
Student ID
Date of Submission
Digital Security
Module Title
Course Code
Student ID
Date of Submission
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2DIGITAL SECURITY
Table of Contents
Question 1: Digital Security Principles...............................................................................4
1.1 Introduction................................................................................................................4
1.2 Cyber-crime and its impact....................................................................................4
1.3 Description of the Computer Misuse Act..............................................................5
1.4 Consequences of breaking the Act........................................................................6
1.5 Real life examples of misuse of the Act................................................................7
1.6 Conclusion.................................................................................................................7
Question 2: Introduction to Cryptography...........................................................................8
2.1 Introduction................................................................................................................8
2.2 Risk of sensitive data.............................................................................................8
2.3 Security model.......................................................................................................8
2.4 Categories of encryption techniques......................................................................9
2.5 Recommendation and justification of the encryption algorithm...........................9
2.6 Long term impact of encryption..........................................................................10
2.7 Conclusion...............................................................................................................10
Question 3: Secure Programming Techniques..................................................................10
3.1 Introduction..............................................................................................................10
3.2. Importance of complex codes............................................................................11
3.3 Description of OWASP......................................................................................11
3.4 Three attacks which are common in the hospital industry.................................11
3.5 Conclusion...................................................................................................................12
4 Reference........................................................................................................................14
Table of Contents
Question 1: Digital Security Principles...............................................................................4
1.1 Introduction................................................................................................................4
1.2 Cyber-crime and its impact....................................................................................4
1.3 Description of the Computer Misuse Act..............................................................5
1.4 Consequences of breaking the Act........................................................................6
1.5 Real life examples of misuse of the Act................................................................7
1.6 Conclusion.................................................................................................................7
Question 2: Introduction to Cryptography...........................................................................8
2.1 Introduction................................................................................................................8
2.2 Risk of sensitive data.............................................................................................8
2.3 Security model.......................................................................................................8
2.4 Categories of encryption techniques......................................................................9
2.5 Recommendation and justification of the encryption algorithm...........................9
2.6 Long term impact of encryption..........................................................................10
2.7 Conclusion...............................................................................................................10
Question 3: Secure Programming Techniques..................................................................10
3.1 Introduction..............................................................................................................10
3.2. Importance of complex codes............................................................................11
3.3 Description of OWASP......................................................................................11
3.4 Three attacks which are common in the hospital industry.................................11
3.5 Conclusion...................................................................................................................12
4 Reference........................................................................................................................14

3DIGITAL SECURITY
Question 1: Digital Security Principles
1.1 Introduction
The foremost determination of this report is to highlight the importance of the
Computer Misuse Act. The impact and the definition of the cyber crimes will be
highlighted in the paper along with the act which helps in safeguarding the digital
security of Ruskin City Council (Wall 2017). The report will discuss different aspects of
the act such as the consequences of breaking the act and real-life examples of the misuse
of the Act.
1.2 Cyber-crime and its impact
Cyber Crime can be defined as the type of crime in which computer systems are
used to commit a crime. All the illegal internet-based activities can be considered as the
cybercrime and it has a very negative effect on our society. There are different categories
if cyber-crimes such as phishing emails and child pornography. Computers are the object
of the cybercrimes and the cybercriminals uses extensive and innovative methods for
different categories of cybercrimes (Nishchal 2018). Cyberstalking is the other examples
of the cyber-crimes along with that the ransomware attacks also falls under this category.
Severe business loss and loss of reputation are the most negative impact of the
cybercrimes. Apart from the economic impact of the cybercrimes, there are numerous
technological impacts of the cybercrimes as well such as the delay in the implementation
of new technology in a business environment (Hatta et al. 2018). Some of the real-life
examples of cybercrimes are ethical hacking, identity theft and transaction frauds. The
recent online scams also fall under the category of the cyber-crimes along with this the
SQL injections attacks are also considered as one of the deadliest cyber-crimes (Barker
Question 1: Digital Security Principles
1.1 Introduction
The foremost determination of this report is to highlight the importance of the
Computer Misuse Act. The impact and the definition of the cyber crimes will be
highlighted in the paper along with the act which helps in safeguarding the digital
security of Ruskin City Council (Wall 2017). The report will discuss different aspects of
the act such as the consequences of breaking the act and real-life examples of the misuse
of the Act.
1.2 Cyber-crime and its impact
Cyber Crime can be defined as the type of crime in which computer systems are
used to commit a crime. All the illegal internet-based activities can be considered as the
cybercrime and it has a very negative effect on our society. There are different categories
if cyber-crimes such as phishing emails and child pornography. Computers are the object
of the cybercrimes and the cybercriminals uses extensive and innovative methods for
different categories of cybercrimes (Nishchal 2018). Cyberstalking is the other examples
of the cyber-crimes along with that the ransomware attacks also falls under this category.
Severe business loss and loss of reputation are the most negative impact of the
cybercrimes. Apart from the economic impact of the cybercrimes, there are numerous
technological impacts of the cybercrimes as well such as the delay in the implementation
of new technology in a business environment (Hatta et al. 2018). Some of the real-life
examples of cybercrimes are ethical hacking, identity theft and transaction frauds. The
recent online scams also fall under the category of the cyber-crimes along with this the
SQL injections attacks are also considered as one of the deadliest cyber-crimes (Barker
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4DIGITAL SECURITY
2017). DoS or the Denial of Service and MitM attack are the other examples of the
cyber-crimes.
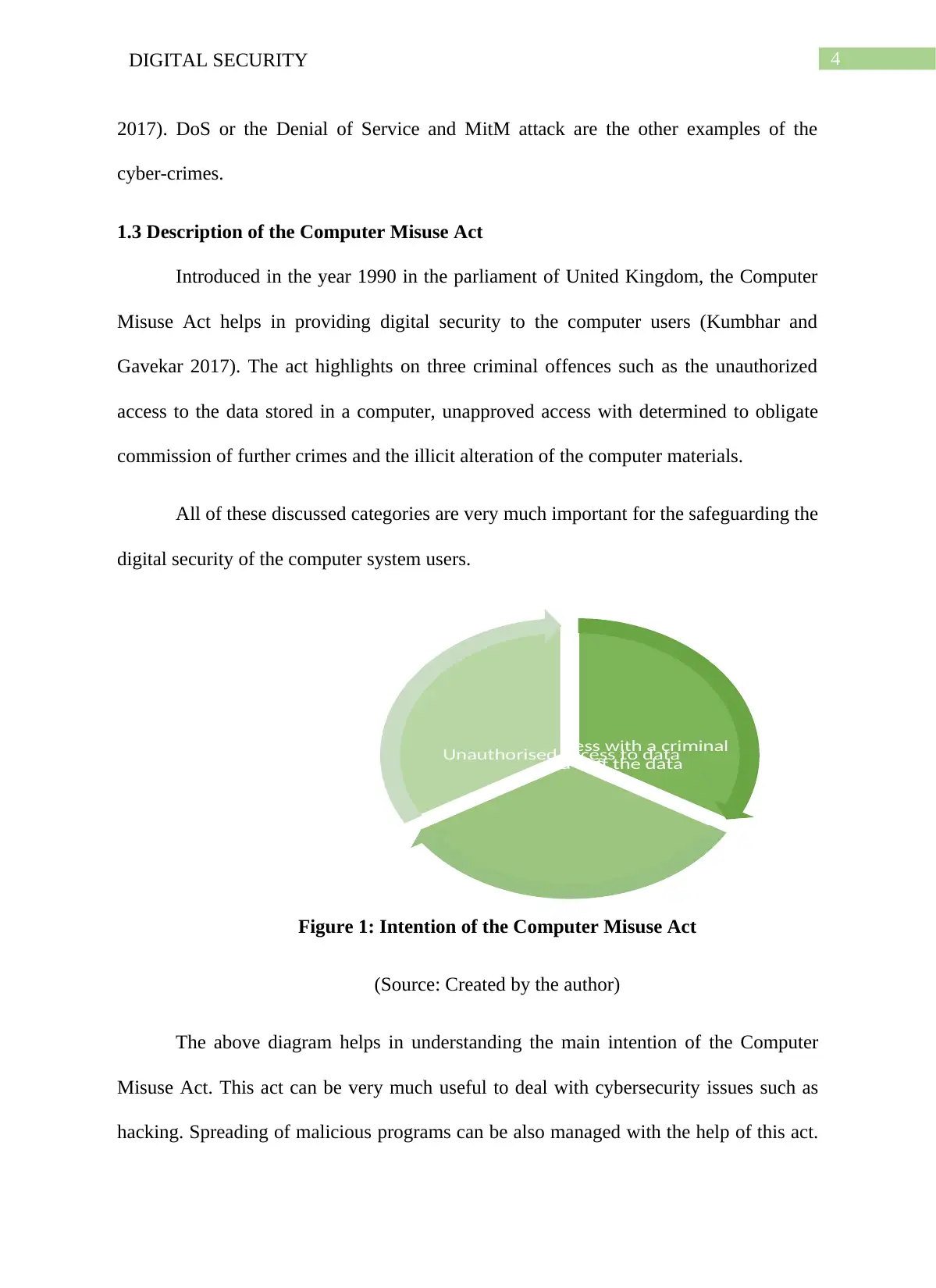
1.3 Description of the Computer Misuse Act
Introduced in the year 1990 in the parliament of United Kingdom, the Computer
Misuse Act helps in providing digital security to the computer users (Kumbhar and
Gavekar 2017). The act highlights on three criminal offences such as the unauthorized
access to the data stored in a computer, unapproved access with determined to obligate
commission of further crimes and the illicit alteration of the computer materials.
All of these discussed categories are very much important for the safeguarding the
digital security of the computer system users.
Figure 1: Intention of the Computer Misuse Act
(Source: Created by the author)
The above diagram helps in understanding the main intention of the Computer
Misuse Act. This act can be very much useful to deal with cybersecurity issues such as
hacking. Spreading of malicious programs can be also managed with the help of this act.
Unauthorized access with a criminal
intentUnauthorised o of the data
Unauthorised access to data
2017). DoS or the Denial of Service and MitM attack are the other examples of the
cyber-crimes.
1.3 Description of the Computer Misuse Act
Introduced in the year 1990 in the parliament of United Kingdom, the Computer
Misuse Act helps in providing digital security to the computer users (Kumbhar and
Gavekar 2017). The act highlights on three criminal offences such as the unauthorized
access to the data stored in a computer, unapproved access with determined to obligate
commission of further crimes and the illicit alteration of the computer materials.
All of these discussed categories are very much important for the safeguarding the
digital security of the computer system users.
Figure 1: Intention of the Computer Misuse Act
(Source: Created by the author)
The above diagram helps in understanding the main intention of the Computer
Misuse Act. This act can be very much useful to deal with cybersecurity issues such as
hacking. Spreading of malicious programs can be also managed with the help of this act.
Unauthorized access with a criminal
intentUnauthorised o of the data
Unauthorised access to data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5DIGITAL SECURITY
The computer-based threats and fraudulent activities can be controlled with the help of
this act. The software viruses can be restricted in a network if this act is followed by all
the users of the network. This act can be also beneficial to deal with the copyrights issues
of the programs (Levi 2016). The Computer Misuse Act was proposed on the in response
to the decision which were taken in R v Gold & Schifreen of 1988. Authorization of the
data which are constantly circulated in the computer systems in business can be managed
and protected with the help of this act. There are different types of sections associated
with this act such as section one and section 2. Each section has its own penalty clauses
and regulations. The activities of the cybercriminals can be identified and contingency
plans for each of the unethical breaching can be created with the help of this act. The
legislative loopholes of the organizations can be mitigated with the help of this act.
1.4 Consequences of breaking the Act
There are different consequences for each of the three intentions of the Computer
Misuse Act. The unauthorized access to the computer materials can lead up to 12 months
of imprisonment along with a fine based on the level of breaching (Yassein et al. 2017).
The unauthorized access to a computer system with criminal intent can lead up to 12
months and 5 years of imprisonment and the unauthorized modification of the computer
materials can lead up to 6 months and 10 years of imprisonment (Ngo and Jaishankar
2017). The consequences of breaking the act is directly depended on the level of the
breach it causes.
The computer-based threats and fraudulent activities can be controlled with the help of
this act. The software viruses can be restricted in a network if this act is followed by all
the users of the network. This act can be also beneficial to deal with the copyrights issues
of the programs (Levi 2016). The Computer Misuse Act was proposed on the in response
to the decision which were taken in R v Gold & Schifreen of 1988. Authorization of the
data which are constantly circulated in the computer systems in business can be managed
and protected with the help of this act. There are different types of sections associated
with this act such as section one and section 2. Each section has its own penalty clauses
and regulations. The activities of the cybercriminals can be identified and contingency
plans for each of the unethical breaching can be created with the help of this act. The
legislative loopholes of the organizations can be mitigated with the help of this act.
1.4 Consequences of breaking the Act
There are different consequences for each of the three intentions of the Computer
Misuse Act. The unauthorized access to the computer materials can lead up to 12 months
of imprisonment along with a fine based on the level of breaching (Yassein et al. 2017).
The unauthorized access to a computer system with criminal intent can lead up to 12
months and 5 years of imprisonment and the unauthorized modification of the computer
materials can lead up to 6 months and 10 years of imprisonment (Ngo and Jaishankar
2017). The consequences of breaking the act is directly depended on the level of the
breach it causes.

6DIGITAL SECURITY
1.5 Real life examples of misuse of the Act.
There are numerous examples of the misuse of this act. Based on an investigation
report it was found that a 21 years old Gareth Cross of West Sussex was penalized for 12
months after hacking into a private Facebook account.
Breaching occurred when James and McCormick and James Marks were found to
break the Sony Music servers, and an un released version of a Michael Jackson video is
leaked. More than 7900 files were downloaded from the Sony Music server.
More cases of miss use of the Computer Misuse Act was found all around
Europe, a 15-year-old boy from Ireland alleged the attack on the talk website where the
details of the customer data were hacked by him.
1.6 Conclusion
The report is much important to understand the cyber crimes which ate having a
direct negative impact on our society. The impact of the cyber-crimes was concluded for
this report. Detailed description of the computer misuse act can be also concluded from
the report along with the charges and penalties for each of the categories of the act.
Consequences of breaking the act can be also determined from this report. Real life
examples of the misuse of the act can be also determined with the help of this act.
1.5 Real life examples of misuse of the Act.
There are numerous examples of the misuse of this act. Based on an investigation
report it was found that a 21 years old Gareth Cross of West Sussex was penalized for 12
months after hacking into a private Facebook account.
Breaching occurred when James and McCormick and James Marks were found to
break the Sony Music servers, and an un released version of a Michael Jackson video is
leaked. More than 7900 files were downloaded from the Sony Music server.
More cases of miss use of the Computer Misuse Act was found all around
Europe, a 15-year-old boy from Ireland alleged the attack on the talk website where the
details of the customer data were hacked by him.
1.6 Conclusion
The report is much important to understand the cyber crimes which ate having a
direct negative impact on our society. The impact of the cyber-crimes was concluded for
this report. Detailed description of the computer misuse act can be also concluded from
the report along with the charges and penalties for each of the categories of the act.
Consequences of breaking the act can be also determined from this report. Real life
examples of the misuse of the act can be also determined with the help of this act.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7DIGITAL SECURITY
Question 2: Introduction to Cryptography
2.1 Introduction
The prime determination of the paper is to focus on the protection of personal and the
sensitive information of the Lord Ruskin hospital (Karali, Panda and Panda 2015). This
report will be evaluating all the probable use of encryption techniques in the working
environment.
2.2 Risk of sensitive data
The data which are circulated in the business environment of the Lord Ruskin
hospital have different types of risk such as the risks coming from the loss of reputation
for the business organizations and the risks of customer dissatisfaction. The alteration of
sensitive business data can lead to huge financial loss for the organization.
2.3 Security model
Maintaining the security of the data which are circulated with in the hospital as
well as the data which are circulated outside the organization is important.
Confidentiality Integrity and Availability is a security model which are widely followed
in most of the global healthcare industries as it helps to maintain the integrity, availability
of the data and confidentiality. Authorization of the data can be maintained with the help
of this security model at the same time the accuracy of the data can be maintained with
the help of CIA.
Question 2: Introduction to Cryptography
2.1 Introduction
The prime determination of the paper is to focus on the protection of personal and the
sensitive information of the Lord Ruskin hospital (Karali, Panda and Panda 2015). This
report will be evaluating all the probable use of encryption techniques in the working
environment.
2.2 Risk of sensitive data
The data which are circulated in the business environment of the Lord Ruskin
hospital have different types of risk such as the risks coming from the loss of reputation
for the business organizations and the risks of customer dissatisfaction. The alteration of
sensitive business data can lead to huge financial loss for the organization.
2.3 Security model
Maintaining the security of the data which are circulated with in the hospital as
well as the data which are circulated outside the organization is important.
Confidentiality Integrity and Availability is a security model which are widely followed
in most of the global healthcare industries as it helps to maintain the integrity, availability
of the data and confidentiality. Authorization of the data can be maintained with the help
of this security model at the same time the accuracy of the data can be maintained with
the help of CIA.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8DIGITAL SECURITY
2.4 Categories of encryption techniques
There are different categories of encryptions techniques such as the symmetric
encryption and asymmetric encryption which are widely used all over the world for the
protection of the data.
As stated by Khurana and Singh (2017), the asymmetric encryption is defined as
the type of encryption technique which involves the use of both private and public key.
Whereas the symmetric encryption technique can be used in the business organization
which involves the use of the secret key which is present for both the sender and the
receiver of the encrypted message. The security of the data can be maintained with the
help of the symmetric and asymmetric encryption procedures as mentioned by the
researchers of the paper.
However, there are lots of issues associated with the symmetric and the
asymmetric encryption procedures such as the server issue, trust between the sender and
the receiver of the data are the other significant issue of the encryption procedures. The
researchers of this paper stated that the encryption procedure should be very carefully
conducted.
2.5 Recommendation and justification of the encryption algorithm
The encryption algorism which can be used for transferring the student
assignment report to an examiner over the internet is the Advanced encryption method.
The advanced encryption method is a type of symmetric encryption algorithm is
used by the government of United States for the protection of the classified information,
2.4 Categories of encryption techniques
There are different categories of encryptions techniques such as the symmetric
encryption and asymmetric encryption which are widely used all over the world for the
protection of the data.
As stated by Khurana and Singh (2017), the asymmetric encryption is defined as
the type of encryption technique which involves the use of both private and public key.
Whereas the symmetric encryption technique can be used in the business organization
which involves the use of the secret key which is present for both the sender and the
receiver of the encrypted message. The security of the data can be maintained with the
help of the symmetric and asymmetric encryption procedures as mentioned by the
researchers of the paper.
However, there are lots of issues associated with the symmetric and the
asymmetric encryption procedures such as the server issue, trust between the sender and
the receiver of the data are the other significant issue of the encryption procedures. The
researchers of this paper stated that the encryption procedure should be very carefully
conducted.
2.5 Recommendation and justification of the encryption algorithm
The encryption algorism which can be used for transferring the student
assignment report to an examiner over the internet is the Advanced encryption method.
The advanced encryption method is a type of symmetric encryption algorithm is
used by the government of United States for the protection of the classified information,

9DIGITAL SECURITY
this type of encryption technique is hugely reliable so it can be effectively used in the
education industry as well.
2.6 Long term impact of encryption
Cryptographic techniques are increasingly used in the education industry. Lots of
sensitive and confidential data are circulated in the business environments with reliability
which is given by the encryption techniques (Ishai et al. 2016). The symmetric
cryptography is much slower than the asymmetric cryptography. The long-term impact
of the encryption can be seen in the business organizations due to its enhanced security
measures.
2.7 Conclusion
This report is very much useful to understand the impact of the two different
categories of encryption techniques such as the symmetric and the asymmetric encryption
techniques. The risks associated with the sensitive data and the security models such as
CIA which are used for the protection and integrity of the data. Compare and contrast of
the two different types of encryption techniques can be also be concluded from this
report. The long term impacts of the encryption techniques which are widely followed in
the education industry can be also concluded from the paper.
Question 3: Secure Programming Techniques
3.1 Introduction
The main objective of the report focuses on the importance of secure
programming for the software developers of Ruskin University as recommended by the
this type of encryption technique is hugely reliable so it can be effectively used in the
education industry as well.
2.6 Long term impact of encryption
Cryptographic techniques are increasingly used in the education industry. Lots of
sensitive and confidential data are circulated in the business environments with reliability
which is given by the encryption techniques (Ishai et al. 2016). The symmetric
cryptography is much slower than the asymmetric cryptography. The long-term impact
of the encryption can be seen in the business organizations due to its enhanced security
measures.
2.7 Conclusion
This report is very much useful to understand the impact of the two different
categories of encryption techniques such as the symmetric and the asymmetric encryption
techniques. The risks associated with the sensitive data and the security models such as
CIA which are used for the protection and integrity of the data. Compare and contrast of
the two different types of encryption techniques can be also be concluded from this
report. The long term impacts of the encryption techniques which are widely followed in
the education industry can be also concluded from the paper.
Question 3: Secure Programming Techniques
3.1 Introduction
The main objective of the report focuses on the importance of secure
programming for the software developers of Ruskin University as recommended by the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10DIGITAL SECURITY
OWASP. This report will be having numerous units, each unit having it sown
significance.
OWASP. This report will be having numerous units, each unit having it sown
significance.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11DIGITAL SECURITY
3.2. Importance of complex codes
The length of the source codes which are used by the software developers can be
huge factors regarding the unethical practices of this industry such as ethical hacking.
The length of the complex codes is generally bigger in size as compared with the simple
codes and the length of the codes gives the opportunity for the hackers to exploit the
backend functionalities (McAndrew 2016). There are lots of back door codes present in
the complex codes which are responsible for the exploitation of the codes, thus it can be
understood that the application of the complex source code can be vulnerable to the
security attacks.
3.3 Description of OWASP
The Open Web Application security Project is defined as the type of organization
which provides the unbiased and cost-effective information about the application of
internet and computer systems (Bellare, Kane and Rogaway 2016). Security knowledge
framework of the OWASP is very much useful for verifying the security of the software.
The software developers can be trained with the help of this network (Mehra 2016). The
entire software development life cycle can be managed with the help of this framework.
3.4 Three attacks which are common in the hospital industry
Among the different types of security attacks of the top 10 website application of
OWASP the selected risks for this paper are the Cross-Site Request Forgery CSRF,
Cross-Site Scripting (XSS) and injection attacks (Poh et al. 2017). These attacks are the
most vulnerable regarding the data which are circulated in the healthcare industry.
Vulnerabilities Reason behind
existence
Impact on the
hospital industry
Mitigation Plan
3.2. Importance of complex codes
The length of the source codes which are used by the software developers can be
huge factors regarding the unethical practices of this industry such as ethical hacking.
The length of the complex codes is generally bigger in size as compared with the simple
codes and the length of the codes gives the opportunity for the hackers to exploit the
backend functionalities (McAndrew 2016). There are lots of back door codes present in
the complex codes which are responsible for the exploitation of the codes, thus it can be
understood that the application of the complex source code can be vulnerable to the
security attacks.
3.3 Description of OWASP
The Open Web Application security Project is defined as the type of organization
which provides the unbiased and cost-effective information about the application of
internet and computer systems (Bellare, Kane and Rogaway 2016). Security knowledge
framework of the OWASP is very much useful for verifying the security of the software.
The software developers can be trained with the help of this network (Mehra 2016). The
entire software development life cycle can be managed with the help of this framework.
3.4 Three attacks which are common in the hospital industry
Among the different types of security attacks of the top 10 website application of
OWASP the selected risks for this paper are the Cross-Site Request Forgery CSRF,
Cross-Site Scripting (XSS) and injection attacks (Poh et al. 2017). These attacks are the
most vulnerable regarding the data which are circulated in the healthcare industry.
Vulnerabilities Reason behind
existence
Impact on the
hospital industry
Mitigation Plan
12DIGITAL SECURITY
Cross-Site Scripting
(XSS)
The reason behind
this vulnerability is
to get the accesses
of the websites
(Kamara and
Moataz 2017). The
contents of the
websites can be
altered with the
help of this attack
This vulnerability
can have a very
negative impact on
the hospital
industry as the
sensitive data can
be altered which
can lead to loss of
life as well as loss
of money for the
patients.
The mitigation plan
for this attack is
contextual
encoding. HTML
sanitization is the
other technique to
avoid this
vulnerability.
Cross-Site Request
Forgery CSRF
Getting
unauthorized access
to any website or
application is the
prime intention of
this attack.
This vulnerability
can decrease the
reputation of the
hospital industry
and electronic
records of the
patients and the
equipment’s can be
altered with the
help of this
vulnerability.
Anti-forgery token
can be successfully
used to deal with
the threat coming
from the CSRF.
Those anti-forgery
token must be
unique as user
session.
Injection attacks The main reason
behind the
occurrence of this
attack are spoofing
of the identity,
tampering with the
data, destruction of
the data or hiding
valuable contents of
the website or
application.
The advanced
systems which are
connected in the
network can be
controlled with the
help of the injection
attacks.
Compliance issue
and the extra
investment required
from the
management team
of the hospital
industry are the
main concern
regarding the SQL
injection attacks.
The application of
the static SQL and
updating the
internal security
systems such as the
firewall can be the
contingency plan to
tackle with this
issue. Management
of the database
issue with
minimum admin
level facilities is the
other way to deal
with this cyber
security issue.
Table 1: Three attacks which are vulnerable to the hospital software application
(Source: Created by the author)
Cross-Site Scripting
(XSS)
The reason behind
this vulnerability is
to get the accesses
of the websites
(Kamara and
Moataz 2017). The
contents of the
websites can be
altered with the
help of this attack
This vulnerability
can have a very
negative impact on
the hospital
industry as the
sensitive data can
be altered which
can lead to loss of
life as well as loss
of money for the
patients.
The mitigation plan
for this attack is
contextual
encoding. HTML
sanitization is the
other technique to
avoid this
vulnerability.
Cross-Site Request
Forgery CSRF
Getting
unauthorized access
to any website or
application is the
prime intention of
this attack.
This vulnerability
can decrease the
reputation of the
hospital industry
and electronic
records of the
patients and the
equipment’s can be
altered with the
help of this
vulnerability.
Anti-forgery token
can be successfully
used to deal with
the threat coming
from the CSRF.
Those anti-forgery
token must be
unique as user
session.
Injection attacks The main reason
behind the
occurrence of this
attack are spoofing
of the identity,
tampering with the
data, destruction of
the data or hiding
valuable contents of
the website or
application.
The advanced
systems which are
connected in the
network can be
controlled with the
help of the injection
attacks.
Compliance issue
and the extra
investment required
from the
management team
of the hospital
industry are the
main concern
regarding the SQL
injection attacks.
The application of
the static SQL and
updating the
internal security
systems such as the
firewall can be the
contingency plan to
tackle with this
issue. Management
of the database
issue with
minimum admin
level facilities is the
other way to deal
with this cyber
security issue.
Table 1: Three attacks which are vulnerable to the hospital software application
(Source: Created by the author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

13DIGITAL SECURITY
3.5 Conclusion
The report was very much successful to understand the importance of the long
and complex source codes, along with that the report also discusses the detailed
description of the OWASP. The most common attacks which are found in the hospital
software applications such as the CSS attacks and injection attacks can be also concluded
from the paper. The detailed description of three vulnerabilities is the most striking
feature of this report as it helps us to understand the reasons behind the attack, its impact
on the healthcare industry and their mitigation plan.
3.5 Conclusion
The report was very much successful to understand the importance of the long
and complex source codes, along with that the report also discusses the detailed
description of the OWASP. The most common attacks which are found in the hospital
software applications such as the CSS attacks and injection attacks can be also concluded
from the paper. The detailed description of three vulnerabilities is the most striking
feature of this report as it helps us to understand the reasons behind the attack, its impact
on the healthcare industry and their mitigation plan.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

14DIGITAL SECURITY
4 Reference
Barker, E., 2017. SP 800-67 Rev. 2, Recommendation for Triple Data Encryption
Algorithm (TDEA) Block Cipher. NIST special publication, 800, p.67.
Bellare, M., Kane, D. and Rogaway, P., 2016, August. Big-key symmetric encryption:
Resisting key exfiltration. In Annual Cryptology Conference (pp. 373-402). Springer,
Berlin, Heidelberg.
Hatta, M., Rajamanickam, R., Abdullah, D., Hartono, H., Bunga, M., Adji, H.S.,
Djanggih, H., Hipan, N., Salle, S., Salmawati, S. and Azis, A., 2018, November. Efforts
to Overcome Cyber Crime Actions in Indonesia. In Journal of Physics: Conference
Series (Vol. 1114, No. 1, p. 012081). IOP Publishing.
Ishai, Y., Kushilevitz, E., Lu, S. and Ostrovsky, R., 2016, February. Private large-scale
databases with distributed searchable symmetric encryption. In Cryptographers’ Track at
the RSA Conference (pp. 90-107). Springer, Cham.
Kamara, S. and Moataz, T., 2017, April. Boolean searchable symmetric encryption with
worst-case sub-linear complexity. In Annual International Conference on the Theory and
Applications of Cryptographic Techniques (pp. 94-124). Springer, Cham.
Karali, Y., Panda, S. and Panda, C.S., 2015. Analysis of cyber crime and its impact in
India. International Journal of Management, IT and Engineering, 5(6), pp.119-127.
Khurana, M. and Singh, H., 2017, October. Asymmetric optical image encryption using
random Hilbert mask based on fast walsh hadamard transform. In Computing and
4 Reference
Barker, E., 2017. SP 800-67 Rev. 2, Recommendation for Triple Data Encryption
Algorithm (TDEA) Block Cipher. NIST special publication, 800, p.67.
Bellare, M., Kane, D. and Rogaway, P., 2016, August. Big-key symmetric encryption:
Resisting key exfiltration. In Annual Cryptology Conference (pp. 373-402). Springer,
Berlin, Heidelberg.
Hatta, M., Rajamanickam, R., Abdullah, D., Hartono, H., Bunga, M., Adji, H.S.,
Djanggih, H., Hipan, N., Salle, S., Salmawati, S. and Azis, A., 2018, November. Efforts
to Overcome Cyber Crime Actions in Indonesia. In Journal of Physics: Conference
Series (Vol. 1114, No. 1, p. 012081). IOP Publishing.
Ishai, Y., Kushilevitz, E., Lu, S. and Ostrovsky, R., 2016, February. Private large-scale
databases with distributed searchable symmetric encryption. In Cryptographers’ Track at
the RSA Conference (pp. 90-107). Springer, Cham.
Kamara, S. and Moataz, T., 2017, April. Boolean searchable symmetric encryption with
worst-case sub-linear complexity. In Annual International Conference on the Theory and
Applications of Cryptographic Techniques (pp. 94-124). Springer, Cham.
Karali, Y., Panda, S. and Panda, C.S., 2015. Analysis of cyber crime and its impact in
India. International Journal of Management, IT and Engineering, 5(6), pp.119-127.
Khurana, M. and Singh, H., 2017, October. Asymmetric optical image encryption using
random Hilbert mask based on fast walsh hadamard transform. In Computing and

15DIGITAL SECURITY
Communication Technologies for Smart Nation (IC3TSN), 2017 International
Conference on (pp. 374-377). IEEE.
Kumbhar, M. and Gavekar, V., 2017. A study of cyber crime awareness for prevention
and its impact. International Journal of Recent Trends in Engineering & Research
Review, 3, pp.241-242.
Levi, M., 2016. The impacts of organised crime in the EU: some preliminary thoughts on
measurement difficulties. Contemporary Social Science, 11(4), pp.392-402.
McAndrew, A., 2016. Introduction to Cryptography with open-source software. CRC
Press.
Mehra, I., 2016. Investigations on Asymmetric Image Encryption Schemes using Optical
Transforms (Doctoral dissertation, IIT Patna).
Ngo, F. and Jaishankar, K., 2017. Commemorating a Decade in Existence of the
International Journal of Cyber Criminology: A Research Agenda to Advance the
Scholarship on Cyber Crime. International Journal of Cyber Criminology, 11(1).
Nishchal, N.K., 2018, October. Optical asymmetric encryption schemes and attack
analysis. In Electro-Optical and Infrared Systems: Technology and Applications XV (Vol.
10795, p. 107950A). International Society for Optics and Photonics.
Poh, G.S., Chin, J.J., Yau, W.C., Choo, K.K.R. and Mohamad, M.S., 2017. Searchable
symmetric encryption: designs and challenges. ACM Computing Surveys (CSUR), 50(3),
p.40.
Communication Technologies for Smart Nation (IC3TSN), 2017 International
Conference on (pp. 374-377). IEEE.
Kumbhar, M. and Gavekar, V., 2017. A study of cyber crime awareness for prevention
and its impact. International Journal of Recent Trends in Engineering & Research
Review, 3, pp.241-242.
Levi, M., 2016. The impacts of organised crime in the EU: some preliminary thoughts on
measurement difficulties. Contemporary Social Science, 11(4), pp.392-402.
McAndrew, A., 2016. Introduction to Cryptography with open-source software. CRC
Press.
Mehra, I., 2016. Investigations on Asymmetric Image Encryption Schemes using Optical
Transforms (Doctoral dissertation, IIT Patna).
Ngo, F. and Jaishankar, K., 2017. Commemorating a Decade in Existence of the
International Journal of Cyber Criminology: A Research Agenda to Advance the
Scholarship on Cyber Crime. International Journal of Cyber Criminology, 11(1).
Nishchal, N.K., 2018, October. Optical asymmetric encryption schemes and attack
analysis. In Electro-Optical and Infrared Systems: Technology and Applications XV (Vol.
10795, p. 107950A). International Society for Optics and Photonics.
Poh, G.S., Chin, J.J., Yau, W.C., Choo, K.K.R. and Mohamad, M.S., 2017. Searchable
symmetric encryption: designs and challenges. ACM Computing Surveys (CSUR), 50(3),
p.40.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

16DIGITAL SECURITY
Wall, D.S., 2017, July. Towards a conceptualisation of cloud (Cyber) crime. In
International Conference on Human Aspects of Information Security, Privacy, and Trust
(pp. 529-538). Springer, Cham.
Yassein, M.B., Aljawarneh, S., Qawasmeh, E., Mardini, W. and Khamayseh, Y., 2017,
August. Comprehensive study of symmetric key and asymmetric key encryption
algorithms. In Engineering and Technology (ICET), 2017 International Conference on
(pp. 1-7). IEEE.
Wall, D.S., 2017, July. Towards a conceptualisation of cloud (Cyber) crime. In
International Conference on Human Aspects of Information Security, Privacy, and Trust
(pp. 529-538). Springer, Cham.
Yassein, M.B., Aljawarneh, S., Qawasmeh, E., Mardini, W. and Khamayseh, Y., 2017,
August. Comprehensive study of symmetric key and asymmetric key encryption
algorithms. In Engineering and Technology (ICET), 2017 International Conference on
(pp. 1-7). IEEE.
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





