Data as a Service (DaaS) Cloud offering
VerifiedAdded on 2023/01/05
|46
|18221
|26
AI Summary
This dissertation focuses on analyzing the vulnerabilities associated with Data as a Service (DaaS) Cloud offering in higher education. It explores the importance of cloud computing, different kinds of cloud computing services, and ways to reduce vulnerabilities. The study aims to provide insights for developing a world-class education system using cloud services.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

DISSERTATION
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
CHAPTER 1 INTRODUCTION.....................................................................................................1
1.1 Background............................................................................................................................1
1.2 Aim........................................................................................................................................2
1.3 Objectives..............................................................................................................................2
1.4 Research Questions................................................................................................................2
1.5 Work done and Results..........................................................................................................3
1.6 Conclusion.............................................................................................................................4
1.7 Structure of the Report...........................................................................................................4
CHAPTER 2 LITERATURE REVIEW..........................................................................................4
2.1 Overview................................................................................................................................4
Theme 1 Importance of Cloud Computing and different kinds of cloud computing services....4
Theme 2 Overview of Data as a Service (DaaS) Cloud offering................................................6
Theme 3 Importance of DaaS in Higher education.....................................................................8
Theme 4 Challenges and vulnerabilities associated with Data as a Service cloud offering and
their impact on organizations.....................................................................................................11
Theme 5 Ways in which vulnerabilities associated with Data as a Service (DaaS) Cloud
offering can be reduced.............................................................................................................13
CHAPTER 3 RESEARCH METHODOLOGY............................................................................15
3.1 Overview..............................................................................................................................15
3.2 Research type.......................................................................................................................15
3.3 Research design...................................................................................................................16
3.4 Research approach...............................................................................................................17
3.5 Research philosophy............................................................................................................17
3.6 Data collection.....................................................................................................................18
3.7 Literature search strategy.....................................................................................................18
3.7.1 Inclusion and exclusion criteria........................................................................................18
3.8 Ethical considerations..........................................................................................................20
3.9 Research limitations.............................................................................................................20
3.10 Reliability and validity......................................................................................................21
CHAPTER 1 INTRODUCTION.....................................................................................................1
1.1 Background............................................................................................................................1
1.2 Aim........................................................................................................................................2
1.3 Objectives..............................................................................................................................2
1.4 Research Questions................................................................................................................2
1.5 Work done and Results..........................................................................................................3
1.6 Conclusion.............................................................................................................................4
1.7 Structure of the Report...........................................................................................................4
CHAPTER 2 LITERATURE REVIEW..........................................................................................4
2.1 Overview................................................................................................................................4
Theme 1 Importance of Cloud Computing and different kinds of cloud computing services....4
Theme 2 Overview of Data as a Service (DaaS) Cloud offering................................................6
Theme 3 Importance of DaaS in Higher education.....................................................................8
Theme 4 Challenges and vulnerabilities associated with Data as a Service cloud offering and
their impact on organizations.....................................................................................................11
Theme 5 Ways in which vulnerabilities associated with Data as a Service (DaaS) Cloud
offering can be reduced.............................................................................................................13
CHAPTER 3 RESEARCH METHODOLOGY............................................................................15
3.1 Overview..............................................................................................................................15
3.2 Research type.......................................................................................................................15
3.3 Research design...................................................................................................................16
3.4 Research approach...............................................................................................................17
3.5 Research philosophy............................................................................................................17
3.6 Data collection.....................................................................................................................18
3.7 Literature search strategy.....................................................................................................18
3.7.1 Inclusion and exclusion criteria........................................................................................18
3.8 Ethical considerations..........................................................................................................20
3.9 Research limitations.............................................................................................................20
3.10 Reliability and validity......................................................................................................21

CHAPTER 4 DISCUSSION OF FINDINGS................................................................................21
CHAPTER 5 CONCLUSION AND RECOMMENDATIONS....................................................26
5.1 Conclusion...........................................................................................................................26
5.2 Recommendations................................................................................................................28
REFERENCES..............................................................................................................................31
APPENDIX....................................................................................................................................34
PROPOSAL...................................................................................................................................34
INTRODUCTION.........................................................................................................................34
Background................................................................................................................................34
Aim............................................................................................................................................35
Objectives..................................................................................................................................35
Research questions.....................................................................................................................35
LITERATURE REVIEW..............................................................................................................36
RESEARCH METHODOLOGY..................................................................................................39
PROJECT PLAN (GANTT CHART)...........................................................................................42
CHAPTER 5 CONCLUSION AND RECOMMENDATIONS....................................................26
5.1 Conclusion...........................................................................................................................26
5.2 Recommendations................................................................................................................28
REFERENCES..............................................................................................................................31
APPENDIX....................................................................................................................................34
PROPOSAL...................................................................................................................................34
INTRODUCTION.........................................................................................................................34
Background................................................................................................................................34
Aim............................................................................................................................................35
Objectives..................................................................................................................................35
Research questions.....................................................................................................................35
LITERATURE REVIEW..............................................................................................................36
RESEARCH METHODOLOGY..................................................................................................39
PROJECT PLAN (GANTT CHART)...........................................................................................42

Title- Data as a Service (DaaS) Cloud offering
CHAPTER 1 INTRODUCTION
1.1 introduction
In recently, Cloud computing is one of the modern technology that can consider as
unprecedented pace. There is already use in the various number of organizations moving their
workload to cloud. A various kind of research is being conducted by researcher to examine the
importance of DaaS (Data as a service) cloud application. Cloud computing can be defined as
processes in which consider as model for enabling its ubiquitous convenient, on demand network
which can easily accesses to shared pool. These are already configurable computing resource
includes storage applications, networks, service etc. DaaS appears as computational paradigm
and distribution architecture. Its primary objective is to maintain security aspects in which
quickly storage large amount or data or information. Therefore, it become easier for utilising the
resources as service and delivered over internet. Cloud application is basically enhancing the
collaboration, scalability, availability and ability to adapt as fluctuations on the basis of demand.
Although there are various kind of benefits, advantage to adopt cloud services, also some
significant barriers to adoption. Sometimes, it is representing as relatively new computing model
and deal of uncertainty about security at every levels. As moving the critical applications and
other sensitive information to public cloud environments which become consider as great
concern for corporation that are beyond their actual data centre’s network under their control. It
must ensure that individual people will continue to adopt all kind of security aspects.
1.2 Study rationale
Emerging technologies have brought various kinds of changes within education system.
This technology advancement has helped in bringing transformation within education system
digitally. This digital transformation has brought various kinds of changes of universities or
colleges and for students as well in many different ways (Bond and et. al., 2018). Digital
transformation has introduced various kinds of new technologies and services that can be used by
colleges and students and changed ways in which students and exams were conducted. Cloud
computing is a part of digital transformation that has occurred in higher education. It has worked
as a revolution for higher education. There are various kinds of cloud- based services that are
being frequently used by students because of which today education and learning not limited to
textbooks and notebooks only. One of the most important cloud- based service which is used in
1
CHAPTER 1 INTRODUCTION
1.1 introduction
In recently, Cloud computing is one of the modern technology that can consider as
unprecedented pace. There is already use in the various number of organizations moving their
workload to cloud. A various kind of research is being conducted by researcher to examine the
importance of DaaS (Data as a service) cloud application. Cloud computing can be defined as
processes in which consider as model for enabling its ubiquitous convenient, on demand network
which can easily accesses to shared pool. These are already configurable computing resource
includes storage applications, networks, service etc. DaaS appears as computational paradigm
and distribution architecture. Its primary objective is to maintain security aspects in which
quickly storage large amount or data or information. Therefore, it become easier for utilising the
resources as service and delivered over internet. Cloud application is basically enhancing the
collaboration, scalability, availability and ability to adapt as fluctuations on the basis of demand.
Although there are various kind of benefits, advantage to adopt cloud services, also some
significant barriers to adoption. Sometimes, it is representing as relatively new computing model
and deal of uncertainty about security at every levels. As moving the critical applications and
other sensitive information to public cloud environments which become consider as great
concern for corporation that are beyond their actual data centre’s network under their control. It
must ensure that individual people will continue to adopt all kind of security aspects.
1.2 Study rationale
Emerging technologies have brought various kinds of changes within education system.
This technology advancement has helped in bringing transformation within education system
digitally. This digital transformation has brought various kinds of changes of universities or
colleges and for students as well in many different ways (Bond and et. al., 2018). Digital
transformation has introduced various kinds of new technologies and services that can be used by
colleges and students and changed ways in which students and exams were conducted. Cloud
computing is a part of digital transformation that has occurred in higher education. It has worked
as a revolution for higher education. There are various kinds of cloud- based services that are
being frequently used by students because of which today education and learning not limited to
textbooks and notebooks only. One of the most important cloud- based service which is used in
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

higher education is DaaS Data as a Service (Rof, Bikfalvi and Marquès, 2020). This Data as a
Service is not only used in education industry but it is used by various organizations operating in
different sector. This service has made it much easier for universities and students to store and
share information/ data and knowledge with others easily. But there are various kinds of
vulnerabilities that are associated Data as a Service Cloud offering.
This dissertation will be focusing upon identifying main vulnerabilities associated with
Data as a Service. The Rationale of this study is to identify the importance of DaaS (Data-as-a-
service) within higher education, able to examine the positive aspects which help for developing
as world class education system. In order to provide all kind of essential study materials by using
cloud services.
1.2 Aim
This dissertation has majorly focused upon a specific cloud offering which is Data as a
service (DaaS). Main aim that has been focused upon in this dissertation is “To analyse
vulnerabilities associated with Cloud offering of Data as a Service (DaaS)”.
1.3 Objectives
Major research objectives that have been focused upon in this dissertation are:
To analyse importance of cloud computing
To analyse different kinds of cloud computing services
To evaluate ways in which Data as a Service (DaaS) Cloud offering is used.
To analyse importance of DaaS in Higher education
To evaluate vulnerabilities associated with Data as a Service cloud offering and their impact
on organizations.
To identify ways in which vulnerabilities associated with Data as a Service (DaaS) Cloud
offering can be reduced.
To recommend appropriate ways though which usage of Data as a Service (DaaS) Cloud
offering can be increased and vulnerabilities associated with it can be reduced.
To identify gaps in this research and suggest future results.
1.4 Research Questions
Major research questions that this dissertation has answered are as follows:
What are the importance of cloud computing in higher education system?
What are different kinds of cloud computing services?
2
Service is not only used in education industry but it is used by various organizations operating in
different sector. This service has made it much easier for universities and students to store and
share information/ data and knowledge with others easily. But there are various kinds of
vulnerabilities that are associated Data as a Service Cloud offering.
This dissertation will be focusing upon identifying main vulnerabilities associated with
Data as a Service. The Rationale of this study is to identify the importance of DaaS (Data-as-a-
service) within higher education, able to examine the positive aspects which help for developing
as world class education system. In order to provide all kind of essential study materials by using
cloud services.
1.2 Aim
This dissertation has majorly focused upon a specific cloud offering which is Data as a
service (DaaS). Main aim that has been focused upon in this dissertation is “To analyse
vulnerabilities associated with Cloud offering of Data as a Service (DaaS)”.
1.3 Objectives
Major research objectives that have been focused upon in this dissertation are:
To analyse importance of cloud computing
To analyse different kinds of cloud computing services
To evaluate ways in which Data as a Service (DaaS) Cloud offering is used.
To analyse importance of DaaS in Higher education
To evaluate vulnerabilities associated with Data as a Service cloud offering and their impact
on organizations.
To identify ways in which vulnerabilities associated with Data as a Service (DaaS) Cloud
offering can be reduced.
To recommend appropriate ways though which usage of Data as a Service (DaaS) Cloud
offering can be increased and vulnerabilities associated with it can be reduced.
To identify gaps in this research and suggest future results.
1.4 Research Questions
Major research questions that this dissertation has answered are as follows:
What are the importance of cloud computing in higher education system?
What are different kinds of cloud computing services?
2

How could identify the facilities offers by Data as a Service (DaaS)?
What are various kind of vulnerabilities associated with Data as a Service cloud offering and
impact on organizations?
What are different ways in which vulnerabilities associated with Data as a Service (DaaS)
Cloud offering can be reduced?
What are suggested advice that can help to reduce the vulnerabilities in the cloud computing
(Data as a Service (DaaS) Cloud?
1.5 Work done and Results
In this research secondary data analysis has been done for successfully achieving main
aim and objectives. In this dissertation importance of digital transformation in higher education
has been discussed. Ways in which new and advance digital technology in higher education is
being used and transforming higher education has also been discussed briefly. Then, in this
dissertation a brief overview of importance of cloud computing and different kinds of services
offered by cloud services providers has been discussed.
All the secondary data has been collected from different sources though articles,
journals, books, online portals and many more and using appropriate literature search strategy
data was collected. It help for researcher to get more detailed information regarding DaaS as
cloud service. Sometimes, it acquire all essential information through secondary analysis.
Different articles, books and journals have been given brief idea about the research topic or
subject. The most important thing is that when secondary analysis support to collect, store large
information but needs to be filtered accordingly. Through this way, it can gain more insight view
of research study while identifying relevant information or data. That’s why, it can support for
further doing research analysis. Sometimes, pre-existing theories and other relevant materials
have been included in the data collection, storage. In order to identify vulnerabilities associated
with Cloud offering of Data as a Service using exploratory research design method required data
has been collected and analysed using thematic data analysis method.
Results of this dissertation has further been used to identify and recommend ways in
which vulnerabilities associated with Cloud offering of Data as a Service can be reduced and can
be effectively used in higher education. Moreover, vulnerabilities, threats are associated with
cloud computing at the time of service. Therefore, it should need to collect more information or
data in which help to further generating accurate result or outcome.
3
What are various kind of vulnerabilities associated with Data as a Service cloud offering and
impact on organizations?
What are different ways in which vulnerabilities associated with Data as a Service (DaaS)
Cloud offering can be reduced?
What are suggested advice that can help to reduce the vulnerabilities in the cloud computing
(Data as a Service (DaaS) Cloud?
1.5 Work done and Results
In this research secondary data analysis has been done for successfully achieving main
aim and objectives. In this dissertation importance of digital transformation in higher education
has been discussed. Ways in which new and advance digital technology in higher education is
being used and transforming higher education has also been discussed briefly. Then, in this
dissertation a brief overview of importance of cloud computing and different kinds of services
offered by cloud services providers has been discussed.
All the secondary data has been collected from different sources though articles,
journals, books, online portals and many more and using appropriate literature search strategy
data was collected. It help for researcher to get more detailed information regarding DaaS as
cloud service. Sometimes, it acquire all essential information through secondary analysis.
Different articles, books and journals have been given brief idea about the research topic or
subject. The most important thing is that when secondary analysis support to collect, store large
information but needs to be filtered accordingly. Through this way, it can gain more insight view
of research study while identifying relevant information or data. That’s why, it can support for
further doing research analysis. Sometimes, pre-existing theories and other relevant materials
have been included in the data collection, storage. In order to identify vulnerabilities associated
with Cloud offering of Data as a Service using exploratory research design method required data
has been collected and analysed using thematic data analysis method.
Results of this dissertation has further been used to identify and recommend ways in
which vulnerabilities associated with Cloud offering of Data as a Service can be reduced and can
be effectively used in higher education. Moreover, vulnerabilities, threats are associated with
cloud computing at the time of service. Therefore, it should need to collect more information or
data in which help to further generating accurate result or outcome.
3

From chapter 4- discussion and findings it has bene identified that there are various kinds of
security issues or vulnerabilities that are associated with Cloud offering of Data as a Service in
higher education. Discussion clearly explains that it is important for organizations to focus upon
identifying and implementing ways though which these restrictions can be reduced so that it can
be used in an appropriate manner.
1.7 Structure of the Report
This Dissertation consist of five main chapters.
Chapter 1: Introduction- In this chapter main aim and objectives required to be achieved will be
discussed and a brief background and overview of research topic will also be provided.
Chapter 2: Literature Review- In this chapter various sources of secondary data have been
reviewed in order to develop a base for the research and collect required information to be
analysed in order to answer main research questions.
Chapter 3: Research Methodology- This chapter helps in identifying main research methods that
are used in this dissertation with reason because of which those methods have been used.
Chapter 4: Discussion of Findings- In this chapter analysis of secondary data collected is done
though thematic data analysis method.
Chapter 5: Conclusion and recommendations- This chapter concludes final results of dissertation
that have been identified and then on the basis of those results final recommendations to
overcome those vulnerabilities have been identified.
4
security issues or vulnerabilities that are associated with Cloud offering of Data as a Service in
higher education. Discussion clearly explains that it is important for organizations to focus upon
identifying and implementing ways though which these restrictions can be reduced so that it can
be used in an appropriate manner.
1.7 Structure of the Report
This Dissertation consist of five main chapters.
Chapter 1: Introduction- In this chapter main aim and objectives required to be achieved will be
discussed and a brief background and overview of research topic will also be provided.
Chapter 2: Literature Review- In this chapter various sources of secondary data have been
reviewed in order to develop a base for the research and collect required information to be
analysed in order to answer main research questions.
Chapter 3: Research Methodology- This chapter helps in identifying main research methods that
are used in this dissertation with reason because of which those methods have been used.
Chapter 4: Discussion of Findings- In this chapter analysis of secondary data collected is done
though thematic data analysis method.
Chapter 5: Conclusion and recommendations- This chapter concludes final results of dissertation
that have been identified and then on the basis of those results final recommendations to
overcome those vulnerabilities have been identified.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CHAPTER 2 LITERATURE REVIEW
2.1 Overview
This literature review will focus upon reviewing all the secondary data collected from
different sources in an appropriate manner. This literature review will help in understanding
main research topic in a proper and accurate manner and will further help in gaining
understanding of cloud computing, its services in a proper manner.
It has been summarised about the research gaps related the Data as a Service, ways in
which it is used and different challenges and vulnerabilities associated with this service in a
proper and effective manner.
Theme 1 different kinds of cloud computing services
According to the view of Abdel-Basset, Mohamed and Chang, (2018) Cloud computing
is one of the most commonly used advance digital technology which is being used by
organizations today. It helps in facilitating easy access to data and application any time for users
regardless of their location through internet connectivity. It provides different kinds of scalable
computing resources to organizations at an appropriate cost which makes it much easier for users
to store or access unlimited data or work on applications any time as per their need and
requirement. Today cloud computing has become extremely important for different kinds of
business organizations due to its increasing usage and benefits that it provides to its issuers.
Cloud computing technology has made it much easier for organizations to achieve their main
business objectives in an appropriate manner.
As per the view of He and et. al., (2016) Cloud computing is important in education
industry as well especially for higher education. It has made it much easier for institutes that
provide higher education to students to provide or offer educational services by using different
kinds of cloud services to students easily. They can easily make education resources or study
materials easily available to students regardless of student’s location. These resources and
materials can be accessed by students any time of the day. Now educational institutes can easily
manage large amount of data with higher security in lower or reduced cost. In current pandemic
situation of Coronavirus cloud computing services for higher education institutes have plays a
vital role. Due to these cloud computing services, institutes were easily able to provide required
study material to students, they were able to conduct exams online and save required data on
cloud with higher security. Students were not only able to access required study materials but
5
2.1 Overview
This literature review will focus upon reviewing all the secondary data collected from
different sources in an appropriate manner. This literature review will help in understanding
main research topic in a proper and accurate manner and will further help in gaining
understanding of cloud computing, its services in a proper manner.
It has been summarised about the research gaps related the Data as a Service, ways in
which it is used and different challenges and vulnerabilities associated with this service in a
proper and effective manner.
Theme 1 different kinds of cloud computing services
According to the view of Abdel-Basset, Mohamed and Chang, (2018) Cloud computing
is one of the most commonly used advance digital technology which is being used by
organizations today. It helps in facilitating easy access to data and application any time for users
regardless of their location through internet connectivity. It provides different kinds of scalable
computing resources to organizations at an appropriate cost which makes it much easier for users
to store or access unlimited data or work on applications any time as per their need and
requirement. Today cloud computing has become extremely important for different kinds of
business organizations due to its increasing usage and benefits that it provides to its issuers.
Cloud computing technology has made it much easier for organizations to achieve their main
business objectives in an appropriate manner.
As per the view of He and et. al., (2016) Cloud computing is important in education
industry as well especially for higher education. It has made it much easier for institutes that
provide higher education to students to provide or offer educational services by using different
kinds of cloud services to students easily. They can easily make education resources or study
materials easily available to students regardless of student’s location. These resources and
materials can be accessed by students any time of the day. Now educational institutes can easily
manage large amount of data with higher security in lower or reduced cost. In current pandemic
situation of Coronavirus cloud computing services for higher education institutes have plays a
vital role. Due to these cloud computing services, institutes were easily able to provide required
study material to students, they were able to conduct exams online and save required data on
cloud with higher security. Students were not only able to access required study materials but
5

were able to give their assignments and exams online regardless of their location and time. DaaS
is consider as appropriate modern application in term of cloud computing, which become
considered extremely important role played within educational system. It has already increasing
the major demand of advancement of technology because it can support for handling the
complex business operation and function
In addition to this, Jiang, Ma and Wei, (2016) explains that, there are various kinds of
cloud computing services that are provided by cloud service provers that can be used by higher
education universities or institutes. Some of the main type of services offered by cloud providers
are: infrastructure as a service of IaaS is one of the main clouds offering that offers fundamental
infrastructure of virtual network, servers, data storage drivers and operating systems. This
service helps in fulfilling need of hardware’s in a cost- effective manner. This service focuses
upon pay for services that be used only. Another cloud offering service is platform as a service or
PaaS. This service offers a platform to organizations that can be used by them to deploy, develop
and run their own applications. It helps in providing an environment where more than one
developer can work simultaneously on a same project. Third type of service offered by cloud
providers is Software as a service or SaaS. This service helps in providing deployment of
software over internet to different kinds of businesses as per their usage in a cost- effective
manner. This service runs on pay as per usage model in which business or users pay for
subscription as per their usage. Gohari Moghadam and Åhlgren, (2020) further elaborates that,
Other than this there are many new and advance services that have been developed ad are offered
to business organizations as per their usage to users. One of those advance cloud offering service
is Data as a Service or DaaS. DaaS is enabled by Software as a service. It is majorly used for
data integration, storage and management. Most of the organizations uses this service for
bringing improvement within agility of data workload, reduce time to insight, enhance integrity
of data as well as enhance reliability of data.
Theme 2 Overview of Data as a Service (DaaS) Cloud offering
Søilen, (2016) explains that, DaaS is a data management strategy that can be used by
users of cloud computing for delivering data storage, integration, processing as well as analytical
services. it is enabled by Software as a Service or it can also be said that it is similar to software
as a service. This service has been introduced recently. This service helps in outsourcing
maximum data storage, processing and integration operations to cloud. While SaaS, PaaS, IaaS
6
is consider as appropriate modern application in term of cloud computing, which become
considered extremely important role played within educational system. It has already increasing
the major demand of advancement of technology because it can support for handling the
complex business operation and function
In addition to this, Jiang, Ma and Wei, (2016) explains that, there are various kinds of
cloud computing services that are provided by cloud service provers that can be used by higher
education universities or institutes. Some of the main type of services offered by cloud providers
are: infrastructure as a service of IaaS is one of the main clouds offering that offers fundamental
infrastructure of virtual network, servers, data storage drivers and operating systems. This
service helps in fulfilling need of hardware’s in a cost- effective manner. This service focuses
upon pay for services that be used only. Another cloud offering service is platform as a service or
PaaS. This service offers a platform to organizations that can be used by them to deploy, develop
and run their own applications. It helps in providing an environment where more than one
developer can work simultaneously on a same project. Third type of service offered by cloud
providers is Software as a service or SaaS. This service helps in providing deployment of
software over internet to different kinds of businesses as per their usage in a cost- effective
manner. This service runs on pay as per usage model in which business or users pay for
subscription as per their usage. Gohari Moghadam and Åhlgren, (2020) further elaborates that,
Other than this there are many new and advance services that have been developed ad are offered
to business organizations as per their usage to users. One of those advance cloud offering service
is Data as a Service or DaaS. DaaS is enabled by Software as a service. It is majorly used for
data integration, storage and management. Most of the organizations uses this service for
bringing improvement within agility of data workload, reduce time to insight, enhance integrity
of data as well as enhance reliability of data.
Theme 2 Overview of Data as a Service (DaaS) Cloud offering
Søilen, (2016) explains that, DaaS is a data management strategy that can be used by
users of cloud computing for delivering data storage, integration, processing as well as analytical
services. it is enabled by Software as a Service or it can also be said that it is similar to software
as a service. This service has been introduced recently. This service helps in outsourcing
maximum data storage, processing and integration operations to cloud. While SaaS, PaaS, IaaS
6

services had been introduced a decade ago but DaaS service has recently come into use. This
service has been introduced recently because initially cloud services were not designed to handle
massive workload. Processing of wide or large number of datasets though network was
extremely difficult previously. Due to this limitation, and limited offered bandwidth, this new
DaaS or Data as a service cloud offering was introduced.
As per the view of Abe and Ustundaug, (2018) it has helped in making large scale data
management and processing possible that includes all the benefits of Software as a service. There
are various kinds of benefits which is provided in regards to speed, performance and reliability.
Some of the main benefits of DaaS service are: it requires minimum setup time i.e. organizations
can easily begin storage and processing of data immediately as required. It has helped in bringing
improvement within various functionalities of cloud like downtime or disruption chances has
reduced drastically. It has provided greater amount of flexibility i.e. as per the requirement of
users, cloud resources can be allotted to premises instantaneously as per the workload. DaaS
offering of cloud computing services is extremely cost saving and can be optimized easily.
Organizations can change increase or decrease allocated resources as the need of organization so
that only right number of resources are used and excess cost associated with resource usage can
be reduced. It can also help its users in automatically maintain and keep their data up to date.
Not only this, usage of DaaS require very a smaller number of staff members for management of
this service and data stored in it in a proper and appropriate manner.
According to the view of Fulker, (2019) DaaS is an important service whose importance
is increasing. Today almost every organization require space and platform for data storage and
processing. It helps in resolving storage issue. Most of the organizations use it as a solution to
manage their data, expand and sorter data in different format in a secure manner so that it can be
accessed in an appropriate manner, without degrading overall quality of information stored and
without risking theft or security of information. It is also important for organizations because it
has volume based pricing method and also have data type subscription method because of which
it becomes easier for business organizations to manage their costing as per the size and
complexity of business.
Bastrakova, Kemp and Car, (2016) DaaS is mainly focused on the cloud related offers
whereas service provider can deliver virtual platform to end user by internet connection. This can
provide the different tasks to manage or control overall business processes. In case, educational
7
service has been introduced recently because initially cloud services were not designed to handle
massive workload. Processing of wide or large number of datasets though network was
extremely difficult previously. Due to this limitation, and limited offered bandwidth, this new
DaaS or Data as a service cloud offering was introduced.
As per the view of Abe and Ustundaug, (2018) it has helped in making large scale data
management and processing possible that includes all the benefits of Software as a service. There
are various kinds of benefits which is provided in regards to speed, performance and reliability.
Some of the main benefits of DaaS service are: it requires minimum setup time i.e. organizations
can easily begin storage and processing of data immediately as required. It has helped in bringing
improvement within various functionalities of cloud like downtime or disruption chances has
reduced drastically. It has provided greater amount of flexibility i.e. as per the requirement of
users, cloud resources can be allotted to premises instantaneously as per the workload. DaaS
offering of cloud computing services is extremely cost saving and can be optimized easily.
Organizations can change increase or decrease allocated resources as the need of organization so
that only right number of resources are used and excess cost associated with resource usage can
be reduced. It can also help its users in automatically maintain and keep their data up to date.
Not only this, usage of DaaS require very a smaller number of staff members for management of
this service and data stored in it in a proper and appropriate manner.
According to the view of Fulker, (2019) DaaS is an important service whose importance
is increasing. Today almost every organization require space and platform for data storage and
processing. It helps in resolving storage issue. Most of the organizations use it as a solution to
manage their data, expand and sorter data in different format in a secure manner so that it can be
accessed in an appropriate manner, without degrading overall quality of information stored and
without risking theft or security of information. It is also important for organizations because it
has volume based pricing method and also have data type subscription method because of which
it becomes easier for business organizations to manage their costing as per the size and
complexity of business.
Bastrakova, Kemp and Car, (2016) DaaS is mainly focused on the cloud related offers
whereas service provider can deliver virtual platform to end user by internet connection. This can
provide the different tasks to manage or control overall business processes. In case, educational
7
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

institution is able to find as creating their own cloud infrastructure but it become expensive as
resource consuming. Typically, higher educational institution include essential response
maintenance, backup updates and other kind of data storage. Cloud service provider is handle the
security and privacy so that user can easily manage difficult situation. By using DaaS, Cloud
service are hosting the infrastructure for different institution in order to establish a strong
connection with storage cloud, stream a virtual environment for users. Therefore, they can easily
access sensitive information or data. Enterprises can offer DaaS service that have considered as
necessary infrastructure in which comprising with different areas or fields. In this way, it help to
support for delivered the value added data service. In additional, it could be operating the
enterprise model and ensure that business generated revenue with the help of DaaS. Initially, it
have been spends some money include operational costs of running the entire enterprise. Data as
a service (DaaS) is typically consider as subscription based where everyone can use them but
needs to pay for wide range of services.
Moreover, DaaS can provide great advantage, benefits for creating as virtualization of
data centre activities, which means that enterprise cannot affords with effectively. That’s why, it
is an essentially consider as most advanced analytics, BI solution. DaaS can offer easy data
access facilities in order to collect, store large amount of information or data. Sometimes, it is
convenient of full of data centre facility without including large amount of investment,
operational costs. The concept of DaaS has been completely dissolved the wall of guarding data
or information. afterwards, it would be accessible for other people. Sometimes, it will be
increasing as great opportunities to establish a collaboration with other department in order to
collect, organise, store and label data or information in a user-friendly fashion for potential
revenue benefits. At that point, it should be noted that point in which identify the success of
educational institutional data sharing, team work and other data competition to change mind-sets,
plug or play data service as important solution. DaaS service is helping to share as tenant data
across different student, who wants to access information through cloud network. Its primary
goal is to keep usage of data or information of each or every segregation, while allowing to
interact with share a proper configuration data as per needed.
Theme 3 Importance of DaaS in Higher education
According to the view of Olorunfemi Abe and Berk Ustundaug, (2018) data and analytics
is extremely important in higher education. Today due to advancement in technology it has
8
resource consuming. Typically, higher educational institution include essential response
maintenance, backup updates and other kind of data storage. Cloud service provider is handle the
security and privacy so that user can easily manage difficult situation. By using DaaS, Cloud
service are hosting the infrastructure for different institution in order to establish a strong
connection with storage cloud, stream a virtual environment for users. Therefore, they can easily
access sensitive information or data. Enterprises can offer DaaS service that have considered as
necessary infrastructure in which comprising with different areas or fields. In this way, it help to
support for delivered the value added data service. In additional, it could be operating the
enterprise model and ensure that business generated revenue with the help of DaaS. Initially, it
have been spends some money include operational costs of running the entire enterprise. Data as
a service (DaaS) is typically consider as subscription based where everyone can use them but
needs to pay for wide range of services.
Moreover, DaaS can provide great advantage, benefits for creating as virtualization of
data centre activities, which means that enterprise cannot affords with effectively. That’s why, it
is an essentially consider as most advanced analytics, BI solution. DaaS can offer easy data
access facilities in order to collect, store large amount of information or data. Sometimes, it is
convenient of full of data centre facility without including large amount of investment,
operational costs. The concept of DaaS has been completely dissolved the wall of guarding data
or information. afterwards, it would be accessible for other people. Sometimes, it will be
increasing as great opportunities to establish a collaboration with other department in order to
collect, organise, store and label data or information in a user-friendly fashion for potential
revenue benefits. At that point, it should be noted that point in which identify the success of
educational institutional data sharing, team work and other data competition to change mind-sets,
plug or play data service as important solution. DaaS service is helping to share as tenant data
across different student, who wants to access information through cloud network. Its primary
goal is to keep usage of data or information of each or every segregation, while allowing to
interact with share a proper configuration data as per needed.
Theme 3 Importance of DaaS in Higher education
According to the view of Olorunfemi Abe and Berk Ustundaug, (2018) data and analytics
is extremely important in higher education. Today due to advancement in technology it has
8

become important for organizations that provide higher education to integrate their education
system with information technology. Today higher education institutes focus upon introducing
various kinds of courses and study material to students online in order to enhance their overall
knowledge so that they can implement that knowledge practically. Nowadays many institutes
also providing study material to students online, provide them facility to attempt online exams
online regardless of their location. This facility has helped higher education institutes to enhance
facility of making their students remain updated with education. Not only this, if there is any
kind of changes within educational system or within studies then students can be made aware
with the changes and appropriate material or data can be made available to them easily. Due to
this, data as a service has become important in higher education.
As per the view of Bastrakova, Kemp and Car, (2016) Data as a Service has replaced
traditional ways of providing education for higher education institutes. Today most of the top
universities are using this cloud offering service for management of their data so that it becomes
much easier for students to access required data, process it in a proper manner. It does not
require a storage space i.e. all the data is stored and processed on cloud which makes it much
easier for institutes to manage data of their students, subjects, additional courses, examination
data and store it security on cloud so that it can be processes and accessed whenever it is
required. Initially in order to maintain data and store it additional staff members were required
but now limited number of staff members are required for maintenance of data with higher
security level. Not only this it has also become much easier for organizations to maintain and
easily access data over internet in a much faster speed. Today in current pandemic situation it has
become important for most of the institutes to provide education to students online and make all
the data available online, conduct all the examination online, make students’ work on projects as
well online. In this, data as a service cloud offering has plays a vital role which has made it
much easier for universities to provide education online though data as a service cloud offering
to students and students to access required data online in a much easier and faster manner.
As per Psomakelis and et. al., (2020) for purpose of higher education, DaaS is one of the
consider as good fit in different ways. It can help for reducing the information technology
complexity, fulfil all needs for expensive IT support staff. It allows for institution to deploy its
resource with more effectively. The flexibility of Data as a service that means with end of
update of hardware or computer across campus. Sometimes, it will be updated the information
9
system with information technology. Today higher education institutes focus upon introducing
various kinds of courses and study material to students online in order to enhance their overall
knowledge so that they can implement that knowledge practically. Nowadays many institutes
also providing study material to students online, provide them facility to attempt online exams
online regardless of their location. This facility has helped higher education institutes to enhance
facility of making their students remain updated with education. Not only this, if there is any
kind of changes within educational system or within studies then students can be made aware
with the changes and appropriate material or data can be made available to them easily. Due to
this, data as a service has become important in higher education.
As per the view of Bastrakova, Kemp and Car, (2016) Data as a Service has replaced
traditional ways of providing education for higher education institutes. Today most of the top
universities are using this cloud offering service for management of their data so that it becomes
much easier for students to access required data, process it in a proper manner. It does not
require a storage space i.e. all the data is stored and processed on cloud which makes it much
easier for institutes to manage data of their students, subjects, additional courses, examination
data and store it security on cloud so that it can be processes and accessed whenever it is
required. Initially in order to maintain data and store it additional staff members were required
but now limited number of staff members are required for maintenance of data with higher
security level. Not only this it has also become much easier for organizations to maintain and
easily access data over internet in a much faster speed. Today in current pandemic situation it has
become important for most of the institutes to provide education to students online and make all
the data available online, conduct all the examination online, make students’ work on projects as
well online. In this, data as a service cloud offering has plays a vital role which has made it
much easier for universities to provide education online though data as a service cloud offering
to students and students to access required data online in a much easier and faster manner.
As per Psomakelis and et. al., (2020) for purpose of higher education, DaaS is one of the
consider as good fit in different ways. It can help for reducing the information technology
complexity, fulfil all needs for expensive IT support staff. It allows for institution to deploy its
resource with more effectively. The flexibility of Data as a service that means with end of
update of hardware or computer across campus. Sometimes, it will be updated the information
9

with time at the time of classes session. In this way, DaaS plays important role in which collect,
store large amount or information. in context of security, it has dramatically reduce threat, risks.
Since data or information are securely stored at centrally, not applicable as end user devices.
DaaS can handle the mobile computing and BYOD with ease, since it is running any kind of
hardware device, virtually operating entire system from tablets, smartphones. Nowadays, Data as
a service is becoming important capital expense as they can create virtual environment, gradually
converting gaining desktop. In term of higher education, student can access information with
cloud network, gaining as high quality of computing experience.
The importance of DaaS in term of higher education because of certain reason in order to
handle the complex networks.
Reduce IT complexity- it is concerned about the overall cost or price of experienced staff
members, who will manage or control centralised data centre within properly. Data as a service
(DaaS) can provide the better quality of service that able to handle current large amount or
information. It allows for university or school to deploy experienced employees elsewhere and
also avoid external consultants. Computing services includes software updates, maintenance and
backup for virtual infrastructure. It is not only managing the overall functionality of cloud. Once
the system is being configured, ordered that can help for IT staff to resolve any kind of issues
during class’s session within school. The good thing about the DaaS is that university or school
have do anything on the back end. It was completely change the educational system while
providing the better solution for end-users computing at DaaS, especially when implementing the
desired service level.
Cut purchasing and operating costs- for higher education, it will support for predicating
any kind of fluctuation in term of price or cost over entire school years, beyond its budgetary
challenges. In case, if any server fails in school, a department can suddenly check the current
issues and asked for update new software. In this way, it will automatically increases the demand
beyond expectation for student, faculty and staff members. DaaS brings as predictable utility
based in which eliminate its fluctuations in term of computing. It is one of the key value
proportion of any kind of software computing services. For colleges or universities, it provide the
huge benefits, advantage in order to support seasonality. DaaS has been changing the usage plan
which brings to increase performance of entire cloud computing service.
10
store large amount or information. in context of security, it has dramatically reduce threat, risks.
Since data or information are securely stored at centrally, not applicable as end user devices.
DaaS can handle the mobile computing and BYOD with ease, since it is running any kind of
hardware device, virtually operating entire system from tablets, smartphones. Nowadays, Data as
a service is becoming important capital expense as they can create virtual environment, gradually
converting gaining desktop. In term of higher education, student can access information with
cloud network, gaining as high quality of computing experience.
The importance of DaaS in term of higher education because of certain reason in order to
handle the complex networks.
Reduce IT complexity- it is concerned about the overall cost or price of experienced staff
members, who will manage or control centralised data centre within properly. Data as a service
(DaaS) can provide the better quality of service that able to handle current large amount or
information. It allows for university or school to deploy experienced employees elsewhere and
also avoid external consultants. Computing services includes software updates, maintenance and
backup for virtual infrastructure. It is not only managing the overall functionality of cloud. Once
the system is being configured, ordered that can help for IT staff to resolve any kind of issues
during class’s session within school. The good thing about the DaaS is that university or school
have do anything on the back end. It was completely change the educational system while
providing the better solution for end-users computing at DaaS, especially when implementing the
desired service level.
Cut purchasing and operating costs- for higher education, it will support for predicating
any kind of fluctuation in term of price or cost over entire school years, beyond its budgetary
challenges. In case, if any server fails in school, a department can suddenly check the current
issues and asked for update new software. In this way, it will automatically increases the demand
beyond expectation for student, faculty and staff members. DaaS brings as predictable utility
based in which eliminate its fluctuations in term of computing. It is one of the key value
proportion of any kind of software computing services. For colleges or universities, it provide the
huge benefits, advantage in order to support seasonality. DaaS has been changing the usage plan
which brings to increase performance of entire cloud computing service.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Anytime, anywhere access the information or data- College computing needs have turned
towards upside down instead of education dictating what type of devices student can use. Higher
educational institution must have supports wide range of computing device that can help for
student’s access more information at anywhere. DaaS can provide as more flexibility of student
to establish connect or interact with different departments. In order to resolve any kind of
problem or issues. An educational institution has been setups as hybrid computing that can offers
on premises, virtualization solution. This is creating an effective environment with data centers
for some different areas, outsources service can possible due to computing services.
Theme 4 Challenges and vulnerabilities
According to the view of Badidi, Routaib and El Koutbi, (2016) there are various kinds
of vulnerabilities and challenges that are associated with this data as a service (DaaS) cloud
offering. Due to this many unique security considerations arise. This is mainly because all the
data of organization is stored in cloud and is transferred over network. Due to this various kind
of security risk or issues arises that would not even exist if data is stored locally within firewall
institutes. Another vulnerability associated with DaaS cloud offering is that it increases
unauthorised access risk for data. This is majorly because all the data of organization is stored on
cloud that can be access though a unique username and password. Due to this unauthorized
access to data increases. It is one of the main vulnerabilities associated with this cloud offering.
It is important for organizations to pay attentions to these security issues so that data can be
stored security overcloud and unauthorized access vulnerability security issue can be reduced.
As per the view of Hayat and et. al., (2019) there are many other kinds of vulnerabilities
associated with Data as a Service cloud offering. Compliance vulnerability is another kind of
challenge especially for organizations who risk moving sensitive or confidential data to cloud
environment. This does not mean that special data cannot be stored on cloud but it simply means
that special compliance terms and conditions are required to be developed in order to ensure that
all the important data stored can be security stored through DaaS Service.
In addition to this, Psomakelis and et. al., (2020) explains that, DaaS platform reduces
number of tools available or required for working and users will only be able to work on tools
that are compatible with DaaS platform. Due to this flexibility of this platform reduces. It is one
of the major challenge which is associated with this data as a service cloud offering. It is
11
towards upside down instead of education dictating what type of devices student can use. Higher
educational institution must have supports wide range of computing device that can help for
student’s access more information at anywhere. DaaS can provide as more flexibility of student
to establish connect or interact with different departments. In order to resolve any kind of
problem or issues. An educational institution has been setups as hybrid computing that can offers
on premises, virtualization solution. This is creating an effective environment with data centers
for some different areas, outsources service can possible due to computing services.
Theme 4 Challenges and vulnerabilities
According to the view of Badidi, Routaib and El Koutbi, (2016) there are various kinds
of vulnerabilities and challenges that are associated with this data as a service (DaaS) cloud
offering. Due to this many unique security considerations arise. This is mainly because all the
data of organization is stored in cloud and is transferred over network. Due to this various kind
of security risk or issues arises that would not even exist if data is stored locally within firewall
institutes. Another vulnerability associated with DaaS cloud offering is that it increases
unauthorised access risk for data. This is majorly because all the data of organization is stored on
cloud that can be access though a unique username and password. Due to this unauthorized
access to data increases. It is one of the main vulnerabilities associated with this cloud offering.
It is important for organizations to pay attentions to these security issues so that data can be
stored security overcloud and unauthorized access vulnerability security issue can be reduced.
As per the view of Hayat and et. al., (2019) there are many other kinds of vulnerabilities
associated with Data as a Service cloud offering. Compliance vulnerability is another kind of
challenge especially for organizations who risk moving sensitive or confidential data to cloud
environment. This does not mean that special data cannot be stored on cloud but it simply means
that special compliance terms and conditions are required to be developed in order to ensure that
all the important data stored can be security stored through DaaS Service.
In addition to this, Psomakelis and et. al., (2020) explains that, DaaS platform reduces
number of tools available or required for working and users will only be able to work on tools
that are compatible with DaaS platform. Due to this flexibility of this platform reduces. It is one
of the major challenge which is associated with this data as a service cloud offering. It is
11

important to work on such security issues because due to these issues it can become difficult to
store sensitive, confidential or personal data on cloud in a secure manner.
As per Gohari Moghadam and Åhlgren, (2020) challenges to DaaS which include
concern about the security, privacy and other kind of data governance. It may arise the biggest
challenges in context of privacy resolve around the fact, in case shared the data or information. it
often include as data which pertaining to mission as critical applications. Sometimes, companies
are mainly concerned about the security in DaaS but it is very difficult to ensure data governance
among information between Data as a service environment and enterprises. At that time, they
have a more chances to increase vulnerabilities and challenges in data privacy or security.
Multiple information management specialist can believed that as different enterprise can figure
out the essential data assets. They can rent for competitive advantage. Moreover, DaaS as cloud
computing application will continues to expand their demand. DaaS is basically expected to
launch point in context of business intelligence as well as big data analytics. Higher educational
institution has been giving more priorities of DaaS in order to manage or control their critical
data. DaaS (Data as a service) is primarily closed related to cloud application. It may help to
establish as strong integration with one or more provision models. As per cases, other kind of
cloud computing technologies support, adoption may be hampered by security, proprietary issues
and privacy.
Security is one of the string as weakest link, it could be any staff members working on
the particular machine. But it might have an out of date in case of expired. It has become
consider as enormous tasks for every institution to keep shield their business information.
Usually, new modern technologies, processes are completely emerging to deal with significant
challenges regardless of security. But at certain point, it should include as DaaS application that
trends has been reshaping hardware device over last few years. The primary advantage of DaaS
that are promoted as capital advantage, benefits. In particularly, preserve monthly cash flow of
enterprise. Another advantage include ability to easily swap out certain machine as per demand.
Afterwards, it quickly replace outdated system with French devices. Sometimes, this is where
identifying the challenges regarding security which directly impact on the overall performance of
network. When IT staff members are mitigating to DaaS but it is only depending on the service
provider. Therefore, typically promoted as overall budget of cloud application in which
eliminates as much of overhead of burdening with constant hardware devices. But it also helping
12
store sensitive, confidential or personal data on cloud in a secure manner.
As per Gohari Moghadam and Åhlgren, (2020) challenges to DaaS which include
concern about the security, privacy and other kind of data governance. It may arise the biggest
challenges in context of privacy resolve around the fact, in case shared the data or information. it
often include as data which pertaining to mission as critical applications. Sometimes, companies
are mainly concerned about the security in DaaS but it is very difficult to ensure data governance
among information between Data as a service environment and enterprises. At that time, they
have a more chances to increase vulnerabilities and challenges in data privacy or security.
Multiple information management specialist can believed that as different enterprise can figure
out the essential data assets. They can rent for competitive advantage. Moreover, DaaS as cloud
computing application will continues to expand their demand. DaaS is basically expected to
launch point in context of business intelligence as well as big data analytics. Higher educational
institution has been giving more priorities of DaaS in order to manage or control their critical
data. DaaS (Data as a service) is primarily closed related to cloud application. It may help to
establish as strong integration with one or more provision models. As per cases, other kind of
cloud computing technologies support, adoption may be hampered by security, proprietary issues
and privacy.
Security is one of the string as weakest link, it could be any staff members working on
the particular machine. But it might have an out of date in case of expired. It has become
consider as enormous tasks for every institution to keep shield their business information.
Usually, new modern technologies, processes are completely emerging to deal with significant
challenges regardless of security. But at certain point, it should include as DaaS application that
trends has been reshaping hardware device over last few years. The primary advantage of DaaS
that are promoted as capital advantage, benefits. In particularly, preserve monthly cash flow of
enterprise. Another advantage include ability to easily swap out certain machine as per demand.
Afterwards, it quickly replace outdated system with French devices. Sometimes, this is where
identifying the challenges regarding security which directly impact on the overall performance of
network. When IT staff members are mitigating to DaaS but it is only depending on the service
provider. Therefore, typically promoted as overall budget of cloud application in which
eliminates as much of overhead of burdening with constant hardware devices. But it also helping
12

to manage or control the accountability in term of safeguard with protect against any kind of
vulnerabilities.
Schabacker and et.al. (2019) On demand shelf service that simplifies unauthorised use-
this type of service will enable within cloud without consent of IT. The use of DaaS that is
properly supported by organization and then increasing unauthorised access of cloud services. As
a result, it would be identifying the malware infections so that enterprise unable to protect of
secure resources. Through this, it continuously decreasing overall enterprise visibility and
control of their network.
Separation among different tenants fails- this type of vulnerabilities within software
which may generate failure to maintain large number of separation among tenants. Failure can be
used by unauthorised attacker to gain more information from resources of enterprises.
Theme 5 Ways in which vulnerabilities associated with Data as a Service
As per the view of Naous, Schwarz and Legner, (2017) there are various kinds of security
issues and vulnerabilities associated with data as a service cloud offering. It is important to
identify ways in which these vulnerabilities can be reduced. These vulnerabilities are important
to be reduced because it increases risk of data security. One of the main vulnerabilities associated
with this Data as a Service Cloud offering is unauthorized access vulnerability. In order to reduce
vulnerability of this issue is to save username and password of logging in in encrypted form and
only few of them should be allowed to access the account. Saving password in encrypted form
will reduce theft of username and password and will further help in reducing vulnerabilities of
unauthorised access. This way not only unauthorised access chances can be reduced but privacy
and security of data can also be maintained. This security way can be used by both organizations
and higher education institutes as well. In fact, it is extremely important to be used in higher
education because such institutes store data of their students, their account, academic data,
institute related data and many more. Unauthorised access can put data of all the students as well
as of institute vulnerable.
Gill and et. al., (2018) further explains that, educating employees is another way through
which vulnerability associated with Data as a Service can be reduced. Employees who will be
using data stored in DaaS for storing, analysing or for any other purpose should be educated and
proper training should be provided to them. Employees should be provided training for different
kinds of defensive practises that can be adopted by them while using this Data as a Service cloud
13
vulnerabilities.
Schabacker and et.al. (2019) On demand shelf service that simplifies unauthorised use-
this type of service will enable within cloud without consent of IT. The use of DaaS that is
properly supported by organization and then increasing unauthorised access of cloud services. As
a result, it would be identifying the malware infections so that enterprise unable to protect of
secure resources. Through this, it continuously decreasing overall enterprise visibility and
control of their network.
Separation among different tenants fails- this type of vulnerabilities within software
which may generate failure to maintain large number of separation among tenants. Failure can be
used by unauthorised attacker to gain more information from resources of enterprises.
Theme 5 Ways in which vulnerabilities associated with Data as a Service
As per the view of Naous, Schwarz and Legner, (2017) there are various kinds of security
issues and vulnerabilities associated with data as a service cloud offering. It is important to
identify ways in which these vulnerabilities can be reduced. These vulnerabilities are important
to be reduced because it increases risk of data security. One of the main vulnerabilities associated
with this Data as a Service Cloud offering is unauthorized access vulnerability. In order to reduce
vulnerability of this issue is to save username and password of logging in in encrypted form and
only few of them should be allowed to access the account. Saving password in encrypted form
will reduce theft of username and password and will further help in reducing vulnerabilities of
unauthorised access. This way not only unauthorised access chances can be reduced but privacy
and security of data can also be maintained. This security way can be used by both organizations
and higher education institutes as well. In fact, it is extremely important to be used in higher
education because such institutes store data of their students, their account, academic data,
institute related data and many more. Unauthorised access can put data of all the students as well
as of institute vulnerable.
Gill and et. al., (2018) further explains that, educating employees is another way through
which vulnerability associated with Data as a Service can be reduced. Employees who will be
using data stored in DaaS for storing, analysing or for any other purpose should be educated and
proper training should be provided to them. Employees should be provided training for different
kinds of defensive practises that can be adopted by them while using this Data as a Service cloud
13
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

offering. This can be done by setting up some protocols for employees so that even if they feel
that their data has been compromised. Educating employees about this can directly help
employees in understanding ways in which they can securely use this service, and even if any
unauthorized person access data then some set of protocols can be developed that can be used by
employees for restricting unauthorised access. Employees can also be provided training for
running unannounced security test training. This unannounced training can directly help in
identifying ways in which whether users of DaaS service within organization are aware of the
security threats or not, whether they can identify unauthorised person accessing this service and
data or any kind of phishing emails have been sent to them or not.
According to the view of Piraghaj and et. al., (2017) one of the most important
vulnerability of DaaS service which is created due to risk of unauthorised access is moving
sensitive and confidential data to cloud because due to this risk, it becomes difficult for
organizations to trust these services and directly store such kind of data on cloud. For this there
are two main ways though which security of confidential and sensitive data on cloud can ensure.
First is to develop a secure data backup plan and second is to store data in encrypted manner that
can only be accessed by a person who has correct encryption key. This will help in securely
storing sensitive and confidential data so that even if an unauthorised person access the data they
will not be able to use or understand the data. This method can be used by higher education
institutes as well and they can store of all of their confidential data accordingly. Piraghaj and et.
al., (2017) further elaborates that, all the three identified methods should be used by
organizations if they want to use data as a service cloud computing offering security and store
their data without any issue. Other that this, organizations should continuously test data on DaaS
and ways in which employees use it.
According to Gohari Moghadam and Åhlgren, (2020) when it comes to data security in
cloud computing. It is consider as threat which become potential danger to information or
system. It could be developed as intruder network through different ports on the firewall.
Sometimes, process of accessing data in which consider as violates security policy, procedures. It
is critical for higher education to analyse the certain kind of risks, threat. An important aspects in
the data security which are identifying the potential threat, classify them by each and every
categories. Afterwards, it can support for evaluating damage within educational institution.
14
that their data has been compromised. Educating employees about this can directly help
employees in understanding ways in which they can securely use this service, and even if any
unauthorized person access data then some set of protocols can be developed that can be used by
employees for restricting unauthorised access. Employees can also be provided training for
running unannounced security test training. This unannounced training can directly help in
identifying ways in which whether users of DaaS service within organization are aware of the
security threats or not, whether they can identify unauthorised person accessing this service and
data or any kind of phishing emails have been sent to them or not.
According to the view of Piraghaj and et. al., (2017) one of the most important
vulnerability of DaaS service which is created due to risk of unauthorised access is moving
sensitive and confidential data to cloud because due to this risk, it becomes difficult for
organizations to trust these services and directly store such kind of data on cloud. For this there
are two main ways though which security of confidential and sensitive data on cloud can ensure.
First is to develop a secure data backup plan and second is to store data in encrypted manner that
can only be accessed by a person who has correct encryption key. This will help in securely
storing sensitive and confidential data so that even if an unauthorised person access the data they
will not be able to use or understand the data. This method can be used by higher education
institutes as well and they can store of all of their confidential data accordingly. Piraghaj and et.
al., (2017) further elaborates that, all the three identified methods should be used by
organizations if they want to use data as a service cloud computing offering security and store
their data without any issue. Other that this, organizations should continuously test data on DaaS
and ways in which employees use it.
According to Gohari Moghadam and Åhlgren, (2020) when it comes to data security in
cloud computing. It is consider as threat which become potential danger to information or
system. It could be developed as intruder network through different ports on the firewall.
Sometimes, process of accessing data in which consider as violates security policy, procedures. It
is critical for higher education to analyse the certain kind of risks, threat. An important aspects in
the data security which are identifying the potential threat, classify them by each and every
categories. Afterwards, it can support for evaluating damage within educational institution.
14

There are different ways to vulnerabilities associated with DaaS (Data as a service) cloud
computing application.
Hacking- it is one of the most commonly threat, vulnerability that are directly associated
with cloud computing. A hacker can access the information with cloud network which can
possible when gaining authorised access to network. There are different way that hacker gain
access to cloud network and other as guessing or cracking user’s password, installing a key
loggers. These kind of illegal activities are performed by hackers to target the information or
sensitive data. Sometimes, it become dangerous for users to loss all essential data.
Misuser- when educational institution staff members are taking advantage, benefits of
entrusted resources which give more privileges for malicious or unintended purpose. Typically, it
has been categorised which increases administrative abuse, use of non-approved assets. These
kind of action will directly affecting the malicious and other non-malicious nature.
Cloud computing- there are large amount encrypted information or data stored within
cloud network. Sometimes, it leaves the data stored in cloud vulnerable which become as
improper disclosure. With rapidly growing large amount of organization, people and other staff
member of higher educational institution that can use cloud computers, hardware. At that time, it
should increase the vulnerabilities in DaaS (Data as a service) before protecting the information
against hackers or unauthorised individual people. Moreover, availability attacks are primarily
well structure that can easily extorts to damage the educational institution whose online assets
are majorly source of revenue.
Every passing day can assume as opportunity for hackers to get hand a sensitive
information or data, which can hold the student, staff members within educational institution.
That’s why, it is an essential part to protect or secure cloud computing network in which
implementing appropriate security measurement, prevention to protect the overall entire in
proper manner.
Summarise-
As per analysis Literature, it has been summarised about the concept of Cloud computing
which can be running the business through digital technology. Sometimes, It can utilise to store,
collect large information within cloud based infrastructure. Moreover, it has been analysed
threat, vulnerabilities within cloud service. Afterwards, identifying the importance of DaaS in
term of overall data protection.
15
computing application.
Hacking- it is one of the most commonly threat, vulnerability that are directly associated
with cloud computing. A hacker can access the information with cloud network which can
possible when gaining authorised access to network. There are different way that hacker gain
access to cloud network and other as guessing or cracking user’s password, installing a key
loggers. These kind of illegal activities are performed by hackers to target the information or
sensitive data. Sometimes, it become dangerous for users to loss all essential data.
Misuser- when educational institution staff members are taking advantage, benefits of
entrusted resources which give more privileges for malicious or unintended purpose. Typically, it
has been categorised which increases administrative abuse, use of non-approved assets. These
kind of action will directly affecting the malicious and other non-malicious nature.
Cloud computing- there are large amount encrypted information or data stored within
cloud network. Sometimes, it leaves the data stored in cloud vulnerable which become as
improper disclosure. With rapidly growing large amount of organization, people and other staff
member of higher educational institution that can use cloud computers, hardware. At that time, it
should increase the vulnerabilities in DaaS (Data as a service) before protecting the information
against hackers or unauthorised individual people. Moreover, availability attacks are primarily
well structure that can easily extorts to damage the educational institution whose online assets
are majorly source of revenue.
Every passing day can assume as opportunity for hackers to get hand a sensitive
information or data, which can hold the student, staff members within educational institution.
That’s why, it is an essential part to protect or secure cloud computing network in which
implementing appropriate security measurement, prevention to protect the overall entire in
proper manner.
Summarise-
As per analysis Literature, it has been summarised about the concept of Cloud computing
which can be running the business through digital technology. Sometimes, It can utilise to store,
collect large information within cloud based infrastructure. Moreover, it has been analysed
threat, vulnerabilities within cloud service. Afterwards, identifying the importance of DaaS in
term of overall data protection.
15

CHAPTER 3 RESEARCH METHODOLOGY
3.1 Overview
Research methodology helps in providing a brief overview of methods that are used by
researcher for data collection and analysis in order to answer main research questions related to
the DaaS cloud based application. (Adhabi and Anozie, 2017). It helps in enhancing overall
knowledge of different methods can be used within research for achieving main goals and
objectives of the DaaS based study.
3.2 Research type
It is also known as research method which is a kind of a procedure though which data
collection, analysis and interpretation can be done in a proper and appropriate manner for
resolving main research problem in a systematic manner. Research method or type are mainly of
two types. First research type of qualitative research type or method. Second is quantitative
research type or method. Selection of appropriate research type is done according to the type of
study, need and requirement of study (Adhabi and Anozie, 2017). Qualitative research type is a
type of research study in which non-numerical data is collected and analysed in order to achieve
main research objective with the help of different kinds of theories and framework. Whereas
quantitative research type focuses upon collection and analysis of non-numerical data in which
different kinds of mathematical or statistical methods can be used for analysis of data collected
and for achieving main aim of the research and reaching to the conclusion. It is extremely
important to select appropriate research type on the basis of DaaS cloud based application,
identifying its importance to generate accurate result or outcome can be obtained. In this
dissertation, research had focused upon selecting qualitative type of research method as it will
help in identifying different kinds of vulnerabilities associated with Data as a Service in a proper
and accurate manner. Qualitative type of research will further help in evaluating different sources
so that main vulnerabilities can be identified and ways in which it can impact organizations can
also be identified and analysed.
3.3 Research design
Research design can be defined as a kind of strategy which is selected in order to analyse
different components or elements of a research in a logical and coherent manner, so that main
research questions can be answered in a proper and effective manner. it helps in integrating
different components of a study with each other in a proper and accurate manner. it further helps
16
3.1 Overview
Research methodology helps in providing a brief overview of methods that are used by
researcher for data collection and analysis in order to answer main research questions related to
the DaaS cloud based application. (Adhabi and Anozie, 2017). It helps in enhancing overall
knowledge of different methods can be used within research for achieving main goals and
objectives of the DaaS based study.
3.2 Research type
It is also known as research method which is a kind of a procedure though which data
collection, analysis and interpretation can be done in a proper and appropriate manner for
resolving main research problem in a systematic manner. Research method or type are mainly of
two types. First research type of qualitative research type or method. Second is quantitative
research type or method. Selection of appropriate research type is done according to the type of
study, need and requirement of study (Adhabi and Anozie, 2017). Qualitative research type is a
type of research study in which non-numerical data is collected and analysed in order to achieve
main research objective with the help of different kinds of theories and framework. Whereas
quantitative research type focuses upon collection and analysis of non-numerical data in which
different kinds of mathematical or statistical methods can be used for analysis of data collected
and for achieving main aim of the research and reaching to the conclusion. It is extremely
important to select appropriate research type on the basis of DaaS cloud based application,
identifying its importance to generate accurate result or outcome can be obtained. In this
dissertation, research had focused upon selecting qualitative type of research method as it will
help in identifying different kinds of vulnerabilities associated with Data as a Service in a proper
and accurate manner. Qualitative type of research will further help in evaluating different sources
so that main vulnerabilities can be identified and ways in which it can impact organizations can
also be identified and analysed.
3.3 Research design
Research design can be defined as a kind of strategy which is selected in order to analyse
different components or elements of a research in a logical and coherent manner, so that main
research questions can be answered in a proper and effective manner. it helps in integrating
different components of a study with each other in a proper and accurate manner. it further helps
16
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

in conducting a research in a coherent and accurate manner (Fletcher, 2017). Research design
helps in finding correct and accurate solution to every research problem. Research design is of
three different types that are: exploratory, casual and descriptive research design. Exploratory
research design is used to explore important and specific aspects of research for generation of
proper and correct results. This design does not focus upon conclusive answers to questions
rather it helps in exploring and identifying new aspects and evidence gained during research
process that can be used to achieve main research objectives. Casual research design is
conducted for study main cause and effect relationship within a research, whereas descriptive
research design is used to describe specific elements and phenomenon within a research area. As
it is a qualitative type of research so in this researcher will be using exploratory research design
so that they can perform different task easily by exploring them in a proper manner.
3.4 Research approach
Research approach can be defined as a set of actions that can be used by researcher for
solving scientific problem- based research in a proper manner. it is based upon various
assumptions towards or within research study. It helps in identifying and explaining data
collection, analysis and interpretation methods that can be used by research for achieving main
research objectives. It further helps the researcher in generating current and accurate results
useful for the study (Tiwari, Arya and Bansal, 2017). Research approach is majorly of three
different types that are: abductive, deductive and inductive. Inductive approach majorly focuses
upon implementation of new theories proposed by the end of research process as the result of
main observations. This theory helps research in formulating appropriate research objectives and
questions in a proper manner. Deductive research approach helps in testing existing approaches
in which research design is developed in order to test hypothesis. It is tested against observations
for finding a particular pattern in existing theories. Last type of research is abductive research
approach, this approach is majorly used to address weakness of deductive and inductive
approach when there is lack of clarity for testing and selecting appropriate hypothesis and
research questions. It is based on incomplete observations for best prediction that might be true.
For this dissertation, researcher will be using inductive approach in which researcher will be
focusing upon developing new theories for developing general conclusion for answering main
research questions as it is a qualitative type of research.
17
helps in finding correct and accurate solution to every research problem. Research design is of
three different types that are: exploratory, casual and descriptive research design. Exploratory
research design is used to explore important and specific aspects of research for generation of
proper and correct results. This design does not focus upon conclusive answers to questions
rather it helps in exploring and identifying new aspects and evidence gained during research
process that can be used to achieve main research objectives. Casual research design is
conducted for study main cause and effect relationship within a research, whereas descriptive
research design is used to describe specific elements and phenomenon within a research area. As
it is a qualitative type of research so in this researcher will be using exploratory research design
so that they can perform different task easily by exploring them in a proper manner.
3.4 Research approach
Research approach can be defined as a set of actions that can be used by researcher for
solving scientific problem- based research in a proper manner. it is based upon various
assumptions towards or within research study. It helps in identifying and explaining data
collection, analysis and interpretation methods that can be used by research for achieving main
research objectives. It further helps the researcher in generating current and accurate results
useful for the study (Tiwari, Arya and Bansal, 2017). Research approach is majorly of three
different types that are: abductive, deductive and inductive. Inductive approach majorly focuses
upon implementation of new theories proposed by the end of research process as the result of
main observations. This theory helps research in formulating appropriate research objectives and
questions in a proper manner. Deductive research approach helps in testing existing approaches
in which research design is developed in order to test hypothesis. It is tested against observations
for finding a particular pattern in existing theories. Last type of research is abductive research
approach, this approach is majorly used to address weakness of deductive and inductive
approach when there is lack of clarity for testing and selecting appropriate hypothesis and
research questions. It is based on incomplete observations for best prediction that might be true.
For this dissertation, researcher will be using inductive approach in which researcher will be
focusing upon developing new theories for developing general conclusion for answering main
research questions as it is a qualitative type of research.
17

3.5 Research philosophy
Research philosophy can be defined as a way through which data about a phenomenon
can be gathered and analysed. It helps in describing methods that can be used in qualitative and
quantitative research for collection and analysis of data though appropriate research methods.
There are various kinds of research philosophies but there are two most commonly used research
philosophies that are: positivism and interpretivism (van Hees and et. al., 2016). Interpretivism
research philosophy is a kind of philosophy or phenomenon that focuses upon a fact that research
performs a specific role within a society. This philosophy is mostly used in qualitative type of
research papers. It is majorly used with qualitative type of research studies. Whereas, positivism
research philosophy is a kind of phenomenon that helps in shaping a society as well as an
individual. It further helps in integrating human interest within a study. This philosophy says that
science is the only way through which truth can be learnt. It is mostly used with quantitative type
of research studies. For this dissertation, interpretivism research philosophy has been used as it is
a qualitative type of research so usage of interpretivism research philosophy is used by
researcher.
3.6 Data collection
Data collection focuses upon gathering important and relevant information from different
sources for research so that main research objectives can be achieved. Data collected within
research is of two types: primary and secondary data (Al Kilani and Kobziev, 2016). Primary
data is a kind of data which is collected by the researcher for research study for the first time
though different sources such as survey, interview, questionnaire and many more. Whereas
secondary data is a kind of data that has already been published and is collected by the researcher
from different sources such as books, articles, newspapers, journals, online portal and from many
other sources. Type of data that will be collected for a research completely depends upon type of
research, need and requirement of research. For this dissertation, researcher will lay emphasis
upon collection of secondary data for this qualitative research paper from many sources like
books, online portals, articles, journals etc.
3.7 Literature search strategy
Literature search strategy can be defined as a kind of strategy that can be used by a
researcher for collection of accurate and valid secondary data for research. It is important to
develop an appropriate literature search strategy for collection of secondary data that can be used
18
Research philosophy can be defined as a way through which data about a phenomenon
can be gathered and analysed. It helps in describing methods that can be used in qualitative and
quantitative research for collection and analysis of data though appropriate research methods.
There are various kinds of research philosophies but there are two most commonly used research
philosophies that are: positivism and interpretivism (van Hees and et. al., 2016). Interpretivism
research philosophy is a kind of philosophy or phenomenon that focuses upon a fact that research
performs a specific role within a society. This philosophy is mostly used in qualitative type of
research papers. It is majorly used with qualitative type of research studies. Whereas, positivism
research philosophy is a kind of phenomenon that helps in shaping a society as well as an
individual. It further helps in integrating human interest within a study. This philosophy says that
science is the only way through which truth can be learnt. It is mostly used with quantitative type
of research studies. For this dissertation, interpretivism research philosophy has been used as it is
a qualitative type of research so usage of interpretivism research philosophy is used by
researcher.
3.6 Data collection
Data collection focuses upon gathering important and relevant information from different
sources for research so that main research objectives can be achieved. Data collected within
research is of two types: primary and secondary data (Al Kilani and Kobziev, 2016). Primary
data is a kind of data which is collected by the researcher for research study for the first time
though different sources such as survey, interview, questionnaire and many more. Whereas
secondary data is a kind of data that has already been published and is collected by the researcher
from different sources such as books, articles, newspapers, journals, online portal and from many
other sources. Type of data that will be collected for a research completely depends upon type of
research, need and requirement of research. For this dissertation, researcher will lay emphasis
upon collection of secondary data for this qualitative research paper from many sources like
books, online portals, articles, journals etc.
3.7 Literature search strategy
Literature search strategy can be defined as a kind of strategy that can be used by a
researcher for collection of accurate and valid secondary data for research. It is important to
develop an appropriate literature search strategy for collection of secondary data that can be used
18

by researcher for answering main research questions in an accurate manner (Hay and et. al.,
2019). It further helps in identifying sources from which secondary data can be collected
including online and offline libraries. In order to develop an appropriate literature search
strategy, it is important to identify main key terms using which relevant and valid data for
research will be collected. Main key terms used for searching secondary data for this dissertation
are as follows: Data as a Service, DaaS, Cloud computing, higher education, vulnerabilities, and
security issues. For this research using main key terms secondary data was research from online
libraries and databases and with the help of inclusion and exclusion criteria.
3.7.1 Inclusion and exclusion criteria
Inclusion and exclusion criteria are one of the most important factors for secondary
research (Bairagi and Munot, eds., 2019). As inclusion criteria helps in identifying and selecting
appropriate secondary data from appropriate sources that can be used with a research study and
exclusion criteria helps in identifying secondary data that should not be included within research
studies. Inclusion and exclusion criteria for this research paper are as follows:
Inclusion criteria: All the articles or papers that consist of two or more than two key
terms were selected. Other than this all the articles or papers that were published in or were
available in English language were only selected. Lastly articles or papers published in past few
years were only selected.
Exclusion criteria: All the articles that did not have a proper and verified published were
excluded from the studies. Articles or papers that did not have t least two key terms were also
excluded. Articles or papers that were written or were published in language other than English
were excluded from this dissertation. Lastly articles or papers that were published more than 5
years ago were excluded from this study.
3.8 Ethical considerations
Ethical considerations one of the most important factor which is required to be focused
upon and considered in research studies. These ethical considerations are required to be adhered
within research studies. Some of the main ethical considerations that were consideration’s
adhered in this study are as follows: in order to collect secondary data, it is important for
researcher to adhere data protection act, 2018. It further helps in collecting and using secondary
data in an ethical manner. None of the data of other researcher were used without citing or it can
also be said that data of any researcher used in this dissertation have been cited and referenced
19
2019). It further helps in identifying sources from which secondary data can be collected
including online and offline libraries. In order to develop an appropriate literature search
strategy, it is important to identify main key terms using which relevant and valid data for
research will be collected. Main key terms used for searching secondary data for this dissertation
are as follows: Data as a Service, DaaS, Cloud computing, higher education, vulnerabilities, and
security issues. For this research using main key terms secondary data was research from online
libraries and databases and with the help of inclusion and exclusion criteria.
3.7.1 Inclusion and exclusion criteria
Inclusion and exclusion criteria are one of the most important factors for secondary
research (Bairagi and Munot, eds., 2019). As inclusion criteria helps in identifying and selecting
appropriate secondary data from appropriate sources that can be used with a research study and
exclusion criteria helps in identifying secondary data that should not be included within research
studies. Inclusion and exclusion criteria for this research paper are as follows:
Inclusion criteria: All the articles or papers that consist of two or more than two key
terms were selected. Other than this all the articles or papers that were published in or were
available in English language were only selected. Lastly articles or papers published in past few
years were only selected.
Exclusion criteria: All the articles that did not have a proper and verified published were
excluded from the studies. Articles or papers that did not have t least two key terms were also
excluded. Articles or papers that were written or were published in language other than English
were excluded from this dissertation. Lastly articles or papers that were published more than 5
years ago were excluded from this study.
3.8 Ethical considerations
Ethical considerations one of the most important factor which is required to be focused
upon and considered in research studies. These ethical considerations are required to be adhered
within research studies. Some of the main ethical considerations that were consideration’s
adhered in this study are as follows: in order to collect secondary data, it is important for
researcher to adhere data protection act, 2018. It further helps in collecting and using secondary
data in an ethical manner. None of the data of other researcher were used without citing or it can
also be said that data of any researcher used in this dissertation have been cited and referenced
19
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

properly. None of the secondary data from unauthorised sources have been used within this
research. Proper Harvard referencing style was adopted for referencing and citing sources of
data. It is also been analysed that researcher has been engaged in making sure that ethical code of
conduct is being followed. This has assisted them in making research more reliable because of
this they have been able to achieve the target and mission. This has also assisted them in
enhancing quality of research which is really necessary.
3.9 Research limitations
It is important for a researcher to identify limitations of this research in a proper and
appropriate manner. Some of the main research limitations of this dissertation are as follows:
One of the main limitations that was faced by researcher was in formation of research aim and
objectives as cloud computing is a vast topic it was extremely important to narrow down it. So,
in order to overcome this limitation researcher focused upon Data as a Service cloud offering.
Another limitation faced by researcher was in selection of appropriate research methodology.as it
was a secondary qualitative research it become extremely difficult to select appropriate research
methods that can be used by researcher for achieving main aim and objectives of research.
Secondary data analysis was another limitation of this dissertation as secondary data collection
and analysis limited overall scope of the study. There are various limitations for the present
research, it has been evaluated that as the research was qualitative in nature, casualty of research
was unable to be formed. In the cause and effect relationship has been unable to be identify. It
has also been analysed that because of inadequate internet services and unavailability of
resources, the research was also not being able to complete on time and also it got delayed. This
has also affected decision making of researcher. It has also been analysed that the analysis of
literature review was difficult to be done as there were no adequate resources.
3.10 Reliability and validity
Reliability refers to the extent in which same kind of answer can be identified, using the
instruments more than one time. Another words, investigator will focus on the reliability and
whole research associated with higher level of reliability. Sometimes, it needs to be able to
generate accurate result or outcome. As per consideration of same research method under same
type of condition or situation. Reliability can help for investigator to find particular problem in
which crop up in different forms. in this research study, researcher has gained the reliability
while observation in authenticate data source because they have no certain guard against the
20
research. Proper Harvard referencing style was adopted for referencing and citing sources of
data. It is also been analysed that researcher has been engaged in making sure that ethical code of
conduct is being followed. This has assisted them in making research more reliable because of
this they have been able to achieve the target and mission. This has also assisted them in
enhancing quality of research which is really necessary.
3.9 Research limitations
It is important for a researcher to identify limitations of this research in a proper and
appropriate manner. Some of the main research limitations of this dissertation are as follows:
One of the main limitations that was faced by researcher was in formation of research aim and
objectives as cloud computing is a vast topic it was extremely important to narrow down it. So,
in order to overcome this limitation researcher focused upon Data as a Service cloud offering.
Another limitation faced by researcher was in selection of appropriate research methodology.as it
was a secondary qualitative research it become extremely difficult to select appropriate research
methods that can be used by researcher for achieving main aim and objectives of research.
Secondary data analysis was another limitation of this dissertation as secondary data collection
and analysis limited overall scope of the study. There are various limitations for the present
research, it has been evaluated that as the research was qualitative in nature, casualty of research
was unable to be formed. In the cause and effect relationship has been unable to be identify. It
has also been analysed that because of inadequate internet services and unavailability of
resources, the research was also not being able to complete on time and also it got delayed. This
has also affected decision making of researcher. It has also been analysed that the analysis of
literature review was difficult to be done as there were no adequate resources.
3.10 Reliability and validity
Reliability refers to the extent in which same kind of answer can be identified, using the
instruments more than one time. Another words, investigator will focus on the reliability and
whole research associated with higher level of reliability. Sometimes, it needs to be able to
generate accurate result or outcome. As per consideration of same research method under same
type of condition or situation. Reliability can help for investigator to find particular problem in
which crop up in different forms. in this research study, researcher has gained the reliability
while observation in authenticate data source because they have no certain guard against the
20

significant impact on the particular observer’s subjectively. Afterwards, it associated the issue of
research and adopt suitable subjective approach towards study. In this way, it can help for
maintain the level of reliability within research work and comprised with it.
On the other hand, Validity is another concept that will support for explained as an extent
in which fulfil all essential need or requirement of scientific method. Sometimes, it has been
followed by scholar at the time of generating a proper finding. Sometimes, it can be formed
within different way to check the validity. In this research study, scholar has been considered the
validity of authentic resources where using in the further analysis. In this way, it is considered as
important aspects to handle the overall performance, ensure that measure validity within research
study. It has also been analysed and evaluated that data has been collected from reliable and
authentic websites. This has assisted in making sure that researcher has made use of relevant
data. It has also helped them in achieving the set target as well as objectives.
Summarise-
It is also being recommended that in this researchers can also make use of exploratory
design. It will assist them in achieving the end result and also it will assist in overcoming the
issues which is being faced by researchers during the time of making research. It is also being
recommended that in this researcher can also make use of different software so that the
flexibility increases (Dang P. and et.al., 2019). It is also being recommended that in this
researcher can also make use of thematic analysis and if they are making use of primary sources
then in that sample size can also be selected. It is being recommended that Educating employees
about this can directly help employees in understanding ways in which they can securely use this
service, and even if any unauthorized person access data then some set of protocols can be
developed that can be used by employees for restricting unauthorised access.
21
research and adopt suitable subjective approach towards study. In this way, it can help for
maintain the level of reliability within research work and comprised with it.
On the other hand, Validity is another concept that will support for explained as an extent
in which fulfil all essential need or requirement of scientific method. Sometimes, it has been
followed by scholar at the time of generating a proper finding. Sometimes, it can be formed
within different way to check the validity. In this research study, scholar has been considered the
validity of authentic resources where using in the further analysis. In this way, it is considered as
important aspects to handle the overall performance, ensure that measure validity within research
study. It has also been analysed and evaluated that data has been collected from reliable and
authentic websites. This has assisted in making sure that researcher has made use of relevant
data. It has also helped them in achieving the set target as well as objectives.
Summarise-
It is also being recommended that in this researchers can also make use of exploratory
design. It will assist them in achieving the end result and also it will assist in overcoming the
issues which is being faced by researchers during the time of making research. It is also being
recommended that in this researcher can also make use of different software so that the
flexibility increases (Dang P. and et.al., 2019). It is also being recommended that in this
researcher can also make use of thematic analysis and if they are making use of primary sources
then in that sample size can also be selected. It is being recommended that Educating employees
about this can directly help employees in understanding ways in which they can securely use this
service, and even if any unauthorized person access data then some set of protocols can be
developed that can be used by employees for restricting unauthorised access.
21

22
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CHAPTER 4 DISCUSSION OF FINDINGS
It is also being evaluated that more and more organisations are making use of this updated
technology. It has also been evaluated that the new approach of DaaS in managing large amount
of data or information. It has analysed that delineate a possible framework for handling the tools
and service for application migration on the cloud services. This has assisted so many firms in
achieving their set target as well as objectives. It is also being analysed from research that so
many educational institutes can easily manage large amount of data with higher security in lower
or reduced cost. In current pandemic situation of Coronavirus cloud computing services for
higher education institutes have plays a vital role.
During the time of pandemic situation, the use of DaaS has been increased. This has also
assisted in achieving the set target as well as mission. So many people have enhanced sharing of
their information and this software make sure that the personal data of users are being protected.
This has assisted them in increasing trust of users and also because of it the flexibility of users
has been increased which was really necessary to do. There are also various benefits of DaaS
which has been identified in the report. It has been analysed that minimal set up is been required
when making use of this services. This means that companies can install this on minimum cost
and also it increases productivity of firm. This software also has more functionality; these type of
services is also less likely to fail which means firm can only be able to grow because of making
use of DaaS. It increases greater flexibility; this is because so many data can be stored on one
platform. It also helps organisation in saving time which they can invest in other productive
things. It has also been analysed that some of the main type of services offered by cloud
providers are: infrastructure as a service of IaaS is one of the main clouds offering that offers
fundamental infrastructure of virtual network, servers, data storage drivers and operating
systems. It has also been analysed that there are various challenges which has been found in data
as a service. There are various security considerations which can be faced by firms while making
use of this software. In this then companies have to make use of end to end encryption. This has
supported firm in saving the data from getting leaked. In this some of the company also needs to
follow the additional compliance steps. It is being made for those firms who has the data
compliance requirements. In this the compliance requirements needs to be met with the DaaS
solutions. This has assisted them in making sure that data is being protected and also it has
assisted them in increasing flexibility of firms who have made use of these updated technology.
23
It is also being evaluated that more and more organisations are making use of this updated
technology. It has also been evaluated that the new approach of DaaS in managing large amount
of data or information. It has analysed that delineate a possible framework for handling the tools
and service for application migration on the cloud services. This has assisted so many firms in
achieving their set target as well as objectives. It is also being analysed from research that so
many educational institutes can easily manage large amount of data with higher security in lower
or reduced cost. In current pandemic situation of Coronavirus cloud computing services for
higher education institutes have plays a vital role.
During the time of pandemic situation, the use of DaaS has been increased. This has also
assisted in achieving the set target as well as mission. So many people have enhanced sharing of
their information and this software make sure that the personal data of users are being protected.
This has assisted them in increasing trust of users and also because of it the flexibility of users
has been increased which was really necessary to do. There are also various benefits of DaaS
which has been identified in the report. It has been analysed that minimal set up is been required
when making use of this services. This means that companies can install this on minimum cost
and also it increases productivity of firm. This software also has more functionality; these type of
services is also less likely to fail which means firm can only be able to grow because of making
use of DaaS. It increases greater flexibility; this is because so many data can be stored on one
platform. It also helps organisation in saving time which they can invest in other productive
things. It has also been analysed that some of the main type of services offered by cloud
providers are: infrastructure as a service of IaaS is one of the main clouds offering that offers
fundamental infrastructure of virtual network, servers, data storage drivers and operating
systems. It has also been analysed that there are various challenges which has been found in data
as a service. There are various security considerations which can be faced by firms while making
use of this software. In this then companies have to make use of end to end encryption. This has
supported firm in saving the data from getting leaked. In this some of the company also needs to
follow the additional compliance steps. It is being made for those firms who has the data
compliance requirements. In this the compliance requirements needs to be met with the DaaS
solutions. This has assisted them in making sure that data is being protected and also it has
assisted them in increasing flexibility of firms who have made use of these updated technology.
23

It has also been summarised from the research that The use of DaaS that is properly supported by
organization and then increasing unauthorised access of cloud services. As a result, it would be
identifying the malware infections so that enterprise unable to protect of secure resources. It has
also been analysed that this software assists in making sure that the data is not being leaked or no
such type of spamming is being done. This also assist system in making sure that the data is not
being leaked. It helps in achieving the set target and objectives. It has also been analysed that
Separation among different tenants fails- this type of vulnerabilities within software which may
generate failure to maintain large number of separation among tenants. It is also being analysed
that making use of DaaS software has assisted firm in securing their data which is really
necessary. In this they also make sure that the data is not being leaked and This service helps in
providing deployment of software over internet to different kinds of businesses as per their usage
in a cost- effective manner.
4.1 Analysis the concept of Data-as-a-Service (DaaS)
The discussion has made up on the concept of Data-as-a-service (DaaS) which is mainly
considered the data management strategy or deployment model that focus on the cloud. It is
delivery to variety of data or information related service in term of storage, processing and
analytics. It has proposed the new approach of DaaS in managing large amount of data or
information. It has analysed that delineate a possible framework for handling the tools and
service for application migration on the cloud services. That’s why, it has been processing data
or information by DaaS application. Afterwards, it has been proposed the different steps when
using DaaS and composed by different steps such as finding, storing, processing and moving
data. Within current scenario, it has been changing the current situation or condition of business
due to Coronavirus. In this way, many enterprises can use cloud computing services in order to
collect or gather large amount of information. At certain point, analysis that different higher
education institutes have plays a vital role. Due to these cloud computing services, institutes
were easily able to provide required study material to students, they were able to conduct exams
online and save required data on cloud with higher security.
Another way, it has been focused on the different action of DaaS as data management
application that can support for cloud users while delivering data storage, process and integration
or associated with analytical services. Therefore, it help for managing and handling the large
amount or data within Software as a service. But nowadays, it has been recently use of DaaS
24
organization and then increasing unauthorised access of cloud services. As a result, it would be
identifying the malware infections so that enterprise unable to protect of secure resources. It has
also been analysed that this software assists in making sure that the data is not being leaked or no
such type of spamming is being done. This also assist system in making sure that the data is not
being leaked. It helps in achieving the set target and objectives. It has also been analysed that
Separation among different tenants fails- this type of vulnerabilities within software which may
generate failure to maintain large number of separation among tenants. It is also being analysed
that making use of DaaS software has assisted firm in securing their data which is really
necessary. In this they also make sure that the data is not being leaked and This service helps in
providing deployment of software over internet to different kinds of businesses as per their usage
in a cost- effective manner.
4.1 Analysis the concept of Data-as-a-Service (DaaS)
The discussion has made up on the concept of Data-as-a-service (DaaS) which is mainly
considered the data management strategy or deployment model that focus on the cloud. It is
delivery to variety of data or information related service in term of storage, processing and
analytics. It has proposed the new approach of DaaS in managing large amount of data or
information. It has analysed that delineate a possible framework for handling the tools and
service for application migration on the cloud services. That’s why, it has been processing data
or information by DaaS application. Afterwards, it has been proposed the different steps when
using DaaS and composed by different steps such as finding, storing, processing and moving
data. Within current scenario, it has been changing the current situation or condition of business
due to Coronavirus. In this way, many enterprises can use cloud computing services in order to
collect or gather large amount of information. At certain point, analysis that different higher
education institutes have plays a vital role. Due to these cloud computing services, institutes
were easily able to provide required study material to students, they were able to conduct exams
online and save required data on cloud with higher security.
Another way, it has been focused on the different action of DaaS as data management
application that can support for cloud users while delivering data storage, process and integration
or associated with analytical services. Therefore, it help for managing and handling the large
amount or data within Software as a service. But nowadays, it has been recently use of DaaS
24

application service which are designed to handle large amount of dataset. Afterwards, it will be
processing the information within cloud network system. Sometimes, it is very difficult to
manage due to their complexity and identifying certain limitation in their bandwidth or
frequency. On the other hand, DaaS application is also considered the benefits, advantage that
can support for managing overall business operations. it has performed the operation with full of
higher speed and performance, reliability. These are giving the right direction of enterprise to
improve overall business capability. This can possible when implementing this application
within appropriate manner to acquire large amount of information.
Another way, it has been analysed the importance of DaaS service in which requires a
minimum setup interval time and then start to store, collect and process data with immediately. It
brings more advantage in the improvement of overall functionality of enterprise. Cloud Service
can be disruptive during minimum traffic but it would be handled with its flexibility. That’s why,
it has been increasingly the demand of DaaS service and optimized with essential resources. At
that time, higher educational institution can use DaaS as solution and increase their space areas.
Therefore, they can easily storage large amount of relevant information and accessible by
individual person. Moreover, it will increase the demand of large storage that can expand
accordingly. In this way, DaaS application service is becoming flexible to use by individual
people effectively and efficiently.
4.2 Appropriate use of DaaS in Higher education
Nowadays, higher education institutes is mainly focused on the cloud computing service in
which record, store large amount of data within cloud server by using DaaS application.
Therefore, it become useful for accessing the various kinds of courses and study material to
students online in order to enhance their overall knowledge so that they can implement that
knowledge practically. Moreover, it may consider as digital concepts within educational areas
whereas providing study material to students online, provide them facility to attempt online
exams online regardless of their location.
DaaS is consider as appropriate modern application in term of cloud computing, which
become considered extremely important role played within educational system. It has already
increasing the major demand of advancement of technology because it can support for handling
the complex business operation and function. In context of educational level, DaaS can provide
the better facilities and services to their potential student, who are always learn new things and
25
processing the information within cloud network system. Sometimes, it is very difficult to
manage due to their complexity and identifying certain limitation in their bandwidth or
frequency. On the other hand, DaaS application is also considered the benefits, advantage that
can support for managing overall business operations. it has performed the operation with full of
higher speed and performance, reliability. These are giving the right direction of enterprise to
improve overall business capability. This can possible when implementing this application
within appropriate manner to acquire large amount of information.
Another way, it has been analysed the importance of DaaS service in which requires a
minimum setup interval time and then start to store, collect and process data with immediately. It
brings more advantage in the improvement of overall functionality of enterprise. Cloud Service
can be disruptive during minimum traffic but it would be handled with its flexibility. That’s why,
it has been increasingly the demand of DaaS service and optimized with essential resources. At
that time, higher educational institution can use DaaS as solution and increase their space areas.
Therefore, they can easily storage large amount of relevant information and accessible by
individual person. Moreover, it will increase the demand of large storage that can expand
accordingly. In this way, DaaS application service is becoming flexible to use by individual
people effectively and efficiently.
4.2 Appropriate use of DaaS in Higher education
Nowadays, higher education institutes is mainly focused on the cloud computing service in
which record, store large amount of data within cloud server by using DaaS application.
Therefore, it become useful for accessing the various kinds of courses and study material to
students online in order to enhance their overall knowledge so that they can implement that
knowledge practically. Moreover, it may consider as digital concepts within educational areas
whereas providing study material to students online, provide them facility to attempt online
exams online regardless of their location.
DaaS is consider as appropriate modern application in term of cloud computing, which
become considered extremely important role played within educational system. It has already
increasing the major demand of advancement of technology because it can support for handling
the complex business operation and function. In context of educational level, DaaS can provide
the better facilities and services to their potential student, who are always learn new things and
25
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

improve their own learning ability. At that time, Higher education adopt Cloud computing
services to give online courses and gain more information or data. Sometimes, institution will
upload the large amount of study materials in the cloud centre and give option for their student to
access information at anytime or anywhere. In this way, it has been identified the best way to
improve learning abilities by using DaaS application (Cloud computing). In today’s Scenario, it
has been increasingly the demand of cloud service that’s why, higher education system can help
them for both students, faculty members to create as modern learning system. This can possible
only due to cloud computing technology. Sometimes, it become easier for institutional faculty to
update, delete and modify the large data sets. If in case, any kind of change in the education
system where changing the overall process by DaaS application.
As per analysis, researcher has been examined that Data as a service (DaaS) become
consider as good fit in higher educational institution. It helps for maintain flexibility which
means that can easily update essential information within computers. Moreover, it become easier
for students, other staff members to upload syllabus, study materials. Therefore, student can
access information at any time to done their works. Moreover, security risks are commonly
identified at the time of cloud services. But it would be reduce through effectiveness of DaaS
application. It has been securely stored, collected information centrally, not on end user devices.
The research study has been identified the importance of DaaS within educational institution in
which running the device or virtually operating the entire system. By using DaaS, It provide
huge amount of benefits for both universities, college where they can easily building up as strong
data centre for peak usage. Especially, institution can take more advantage of DaaS during multi-
task executions. It has been completely changing the current usage plan and scaling back at the
time of breaks. Research study has been analysed that cloud service not only eliminate data
centre power and also helping to cool down cost or price. Afterwards, it automatically saving
power for zero client rather than its PCs.
The appropriate use of DaaS with college institution instead for supporting wide range of
devices. Student can bring change accordingly, while accessing suitable information or data.
Cloud application is mainly consider as flexible approach for every department of educational
institution but needs to be create as strong networks. It is important to setups with common
choice in term of higher educational level. Moreover, it would be creating as virtual environment
through DaaS or cloud computing services. Another appropriate use of DaaS where provide the
26
services to give online courses and gain more information or data. Sometimes, institution will
upload the large amount of study materials in the cloud centre and give option for their student to
access information at anytime or anywhere. In this way, it has been identified the best way to
improve learning abilities by using DaaS application (Cloud computing). In today’s Scenario, it
has been increasingly the demand of cloud service that’s why, higher education system can help
them for both students, faculty members to create as modern learning system. This can possible
only due to cloud computing technology. Sometimes, it become easier for institutional faculty to
update, delete and modify the large data sets. If in case, any kind of change in the education
system where changing the overall process by DaaS application.
As per analysis, researcher has been examined that Data as a service (DaaS) become
consider as good fit in higher educational institution. It helps for maintain flexibility which
means that can easily update essential information within computers. Moreover, it become easier
for students, other staff members to upload syllabus, study materials. Therefore, student can
access information at any time to done their works. Moreover, security risks are commonly
identified at the time of cloud services. But it would be reduce through effectiveness of DaaS
application. It has been securely stored, collected information centrally, not on end user devices.
The research study has been identified the importance of DaaS within educational institution in
which running the device or virtually operating the entire system. By using DaaS, It provide
huge amount of benefits for both universities, college where they can easily building up as strong
data centre for peak usage. Especially, institution can take more advantage of DaaS during multi-
task executions. It has been completely changing the current usage plan and scaling back at the
time of breaks. Research study has been analysed that cloud service not only eliminate data
centre power and also helping to cool down cost or price. Afterwards, it automatically saving
power for zero client rather than its PCs.
The appropriate use of DaaS with college institution instead for supporting wide range of
devices. Student can bring change accordingly, while accessing suitable information or data.
Cloud application is mainly consider as flexible approach for every department of educational
institution but needs to be create as strong networks. It is important to setups with common
choice in term of higher educational level. Moreover, it would be creating as virtual environment
through DaaS or cloud computing services. Another appropriate use of DaaS where provide the
26

no other restriction in updating PCs. IT staff members are rolling out with new application
anytime, anywhere. This can possible due to effectiveness of cloud application in which offers
best services to student within premises.
4.3 Examine the Security issue or vulnerabilities
Afterwards, it has been identified the some kind of security issues when institutes can use
DaaS application. In this way, higher educational institution is mainly focused on the
vulnerability, threat associated with DaaS cloud offering in which increasing the various type of
unauthorised access. Sometimes, these are directly affecting on the overall business performance
in term of growth and development. Risk, threat would be generated with cloud computing
service due to lack of IT infrastructure. Therefore, it become easier for unauthorised person that
can directly affecting on the performance. This is majorly because all the data of organization
has been stored large amount of data or information within cloud network. In this way, it is an
essential for creating suitable username, password that help for increasing the accessibility
within cloud network. At that time, it has more chance to increase causes of vulnerability within
cloud Infrastructure. Sometimes, different kind of vulnerabilities associated with this cloud
offering. Therefore, it is important for organizations to pay more attentions to these security
issues so that data can be stored security overcloud and unauthorized access vulnerability
security issue can be reduced. Challenges and issues are considered as part of any modern
technology such as DaaS service. it is important to make an effective plan and handle the
vulnerabilities in proper manner. Cloud computing modern technology is one of powerful service
provider, identifying any kind of vulnerabilities, security risk arise. There are lot of challenges
identified in term of authorized access which may have a chance of data loss. Majorly higher
institution educations have been stored or collected large amount of information with cloud
system. Afterwards, it would easier for accessing sensitive information or data. In this way, it
should include as unique username, password that can protect or secure information. Suddenly, it
has been reduced the chances of security issues but it is only temporary based. Certain
vulnerabilities are associated with cloud network so that it may arise automatically. Afterwards,
higher institution will use the significant security approach to handle or control the overall
business aspects.
As per research study, it has been identified that computing system proves that measures
security as simpler manner. it is primarily depending on the cloud service provider, who are
27
anytime, anywhere. This can possible due to effectiveness of cloud application in which offers
best services to student within premises.
4.3 Examine the Security issue or vulnerabilities
Afterwards, it has been identified the some kind of security issues when institutes can use
DaaS application. In this way, higher educational institution is mainly focused on the
vulnerability, threat associated with DaaS cloud offering in which increasing the various type of
unauthorised access. Sometimes, these are directly affecting on the overall business performance
in term of growth and development. Risk, threat would be generated with cloud computing
service due to lack of IT infrastructure. Therefore, it become easier for unauthorised person that
can directly affecting on the performance. This is majorly because all the data of organization
has been stored large amount of data or information within cloud network. In this way, it is an
essential for creating suitable username, password that help for increasing the accessibility
within cloud network. At that time, it has more chance to increase causes of vulnerability within
cloud Infrastructure. Sometimes, different kind of vulnerabilities associated with this cloud
offering. Therefore, it is important for organizations to pay more attentions to these security
issues so that data can be stored security overcloud and unauthorized access vulnerability
security issue can be reduced. Challenges and issues are considered as part of any modern
technology such as DaaS service. it is important to make an effective plan and handle the
vulnerabilities in proper manner. Cloud computing modern technology is one of powerful service
provider, identifying any kind of vulnerabilities, security risk arise. There are lot of challenges
identified in term of authorized access which may have a chance of data loss. Majorly higher
institution educations have been stored or collected large amount of information with cloud
system. Afterwards, it would easier for accessing sensitive information or data. In this way, it
should include as unique username, password that can protect or secure information. Suddenly, it
has been reduced the chances of security issues but it is only temporary based. Certain
vulnerabilities are associated with cloud network so that it may arise automatically. Afterwards,
higher institution will use the significant security approach to handle or control the overall
business aspects.
As per research study, it has been identified that computing system proves that measures
security as simpler manner. it is primarily depending on the cloud service provider, who are
27

responsible for storing, collecting large amount or information. Based on the analysis, it has been
explained the concept of threat, vulnerabilities within cloud service. When ether, educational
institution can be stored or collected information outside boundaries, that needs to be protected
from vulnerabilities. Majorly, it has found that vulnerabilities or threat such as unauthorised
access of hackers, attackers, malware, and misuse of information by viruses. These are consider
as commonly threat in which associated with DaaS during execution. Different kind of threat or
vulnerabilities are directly targeting the sensitive information or data, which are already stored in
the cloud networks. To protect or secure data from vulnerabilities, Staff members must adopt as
security checks and ensure that sensitive data should protected from malicious attacks. Higher
educational institution can use test to assess or validate, which extent data is properly protected
from malicious users.
By using this study, investigator has been focused on the integrity in term of data security
but there is no specific policy exits for data exchange. In this way, it is important to maintain
security on client side and include suitable resources as possible. Since, few resources are
provided the access users which has been suggested to store or collect personal data through
password. On the other hand, there are already exits of problematic issues where higher
institution face slow down processes. In this way, it can be identified as major issue or problem.
The availability of service is mainly depends on the organization, those who want to use service
for life time.
One of the great way to achieve desirable goal or object in which spreading otherwise, cost
or price of college, university become higher. A DaaS solution can be consider as important
aspects in term of achieving their desirable goal with help of the innovative learning. By giving
more leverage the remote accessibility through DaaS solution, student can access study materials
anywhere, anytime. These are providing the better opportunities in term of educational system.
In today’s world, it has been already increasing the benefits of distant learning program which
can possible through DaaS. It provide the better opportunities for institution to engage with
student and give better session. Another reason for implementing DaaS as solution in higher
educational institution because indeed an uphill tasks to accurately anticipate the various kind of
academic programs. As a result, it can easily fulfil all essential need or requirement for
individual people. For conventional DaaS, it simply empower the hardware and forced to incur
their accompanying price or cost as well.
28
explained the concept of threat, vulnerabilities within cloud service. When ether, educational
institution can be stored or collected information outside boundaries, that needs to be protected
from vulnerabilities. Majorly, it has found that vulnerabilities or threat such as unauthorised
access of hackers, attackers, malware, and misuse of information by viruses. These are consider
as commonly threat in which associated with DaaS during execution. Different kind of threat or
vulnerabilities are directly targeting the sensitive information or data, which are already stored in
the cloud networks. To protect or secure data from vulnerabilities, Staff members must adopt as
security checks and ensure that sensitive data should protected from malicious attacks. Higher
educational institution can use test to assess or validate, which extent data is properly protected
from malicious users.
By using this study, investigator has been focused on the integrity in term of data security
but there is no specific policy exits for data exchange. In this way, it is important to maintain
security on client side and include suitable resources as possible. Since, few resources are
provided the access users which has been suggested to store or collect personal data through
password. On the other hand, there are already exits of problematic issues where higher
institution face slow down processes. In this way, it can be identified as major issue or problem.
The availability of service is mainly depends on the organization, those who want to use service
for life time.
One of the great way to achieve desirable goal or object in which spreading otherwise, cost
or price of college, university become higher. A DaaS solution can be consider as important
aspects in term of achieving their desirable goal with help of the innovative learning. By giving
more leverage the remote accessibility through DaaS solution, student can access study materials
anywhere, anytime. These are providing the better opportunities in term of educational system.
In today’s world, it has been already increasing the benefits of distant learning program which
can possible through DaaS. It provide the better opportunities for institution to engage with
student and give better session. Another reason for implementing DaaS as solution in higher
educational institution because indeed an uphill tasks to accurately anticipate the various kind of
academic programs. As a result, it can easily fulfil all essential need or requirement for
individual people. For conventional DaaS, it simply empower the hardware and forced to incur
their accompanying price or cost as well.
28
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CHAPTER 5 CONCLUSION AND RECOMMENDATIONS
5.1 Conclusion
From the above study it has been summarised that this service has made it much easier for
universities and students to store and share information data and knowledge with others easily.
But there are various kinds of vulnerabilities that are associated Data as a Service Cloud offering.
It has been analysed from the research that data as a service has assisted in keeping the data
secure and also it has assisted in making sure that the security of user data is being maintained.
On the other hand, DaaS application is also considered the benefits, advantage that can support
for managing overall business operations. it has performed the operation with full of higher
speed and performance, reliability (Stergiou and et.al., 2018). These software has been used by
so many organisations to keep their data on track and also updated. It has supported in making
sure that every aspect is being kept separated and segregated. This has assisted in Desktop as a
Service also allows companies to provide remote IT support to their employees, reducing
downtime. It has also been analysed from the research that cost related to IT transactions of so
many organisations have also been reduced as previously they are making use of traditional
methods which has increased the cost. In making use of DaaS, company require less power. It
has also been evaluated that companies to provide support remotely to workers. This has assisted
firms in enhancing the flexibility of workers. Most of the organisations has made use of this
updated technology which is really beneficial for them. For this there are two main ways though
which security of confidential and sensitive data on cloud can be ensured. First is to develop a
secure data back-up plan and second is to store data in encrypted manner that can only be
accessed by a person who has correct encryption key. It has also been evaluated that the data is
end to end encrypted. It means that data is being protected and also it cannot be transferred to
anyone else. This has increased the use of DaaS.
5.2 Recommendations
It is being suggested to organisation to make use of DaaS technology. In this they must
make sure that the data is not been leaked and privacy is being maintained. This has assisted in
enhancing the efficiency of firm and also because of this they have been able to achieve the set
target and objectives (Yang and et.al., 2017). It is also being suggested to companies that they
29
5.1 Conclusion
From the above study it has been summarised that this service has made it much easier for
universities and students to store and share information data and knowledge with others easily.
But there are various kinds of vulnerabilities that are associated Data as a Service Cloud offering.
It has been analysed from the research that data as a service has assisted in keeping the data
secure and also it has assisted in making sure that the security of user data is being maintained.
On the other hand, DaaS application is also considered the benefits, advantage that can support
for managing overall business operations. it has performed the operation with full of higher
speed and performance, reliability (Stergiou and et.al., 2018). These software has been used by
so many organisations to keep their data on track and also updated. It has supported in making
sure that every aspect is being kept separated and segregated. This has assisted in Desktop as a
Service also allows companies to provide remote IT support to their employees, reducing
downtime. It has also been analysed from the research that cost related to IT transactions of so
many organisations have also been reduced as previously they are making use of traditional
methods which has increased the cost. In making use of DaaS, company require less power. It
has also been evaluated that companies to provide support remotely to workers. This has assisted
firms in enhancing the flexibility of workers. Most of the organisations has made use of this
updated technology which is really beneficial for them. For this there are two main ways though
which security of confidential and sensitive data on cloud can be ensured. First is to develop a
secure data back-up plan and second is to store data in encrypted manner that can only be
accessed by a person who has correct encryption key. It has also been evaluated that the data is
end to end encrypted. It means that data is being protected and also it cannot be transferred to
anyone else. This has increased the use of DaaS.
5.2 Recommendations
It is being suggested to organisation to make use of DaaS technology. In this they must
make sure that the data is not been leaked and privacy is being maintained. This has assisted in
enhancing the efficiency of firm and also because of this they have been able to achieve the set
target and objectives (Yang and et.al., 2017). It is also being suggested to companies that they
29

must also be engaged in providing training to workers so that this software can be used by them
easily. This will assist them in enhancing efficiency and also it will assist them in achieving the
goals and objectives. It is also being recommended that DaaS software needs to be used by
various company so that flexibility of workers can also be increased. It is also being suggested
that organisation should also make sure that they are updating with the trends whatever trend is
been going in market, they are being involved in following it. This will assist them in achieving
set target and mission. It will also support firm in growing and achieving the set target as well as
objectives. It is also being recommended to researcher that they need to be involved in following
the exclusion and inclusion criteria (Namasudra and et.al., 2020). It is being suggested that All
the articles or papers that consist of two or more than two key terms were selected. Other than
this all the articles or papers that were published in or were available in English language were
only selected. It is also being recommended that employees also need to have the ability to learn
about the new software related to cloud computing. This will assist them in learning about the
new software which is really necessary. It is also being suggested to researcher that while
collecting the data it is really important that ethical code of conduct is also being followed. It is
being suggested that researchers can be engaged in following the deductive research. Now they
are following inductive research but they can also make use of the deductive research so that
better. and reliable results can be obtained by them. This has assisted them in achieving set target
and mission. This type of research is being used as Deductive research approach helps in testing
existing approaches in which research design is developed in order to test hypothesis. It is also
being recommended that for the present research, researchers can also be engaged in making use
of quantitative research. This will assist researcher in getting end results and also because of this
they have been able to achieve set target and objectives. It is also being suggested that researcher
can also make use of primary data to collect the information. This will assist in collecting
reliable and authentic data (Kumar, Raj and Jelciana, 2018). In this there are various method is
primary data collection method which is used by researcher to collect data for the first time
though survey, questionnaire etc. Investigator has been conducting the research study that needs
to be concerned about the recommendation, implementing the use of DaaS in higher educational
institution. The suggestion has made on the basis of demand regardless modern technology
(Varghese and Buyya, 2018). That’s why, it has been suggested that consider DaaS as cloud
computing application which are quickly turn out to be a great or viable alternative. This had its
30
easily. This will assist them in enhancing efficiency and also it will assist them in achieving the
goals and objectives. It is also being recommended that DaaS software needs to be used by
various company so that flexibility of workers can also be increased. It is also being suggested
that organisation should also make sure that they are updating with the trends whatever trend is
been going in market, they are being involved in following it. This will assist them in achieving
set target and mission. It will also support firm in growing and achieving the set target as well as
objectives. It is also being recommended to researcher that they need to be involved in following
the exclusion and inclusion criteria (Namasudra and et.al., 2020). It is being suggested that All
the articles or papers that consist of two or more than two key terms were selected. Other than
this all the articles or papers that were published in or were available in English language were
only selected. It is also being recommended that employees also need to have the ability to learn
about the new software related to cloud computing. This will assist them in learning about the
new software which is really necessary. It is also being suggested to researcher that while
collecting the data it is really important that ethical code of conduct is also being followed. It is
being suggested that researchers can be engaged in following the deductive research. Now they
are following inductive research but they can also make use of the deductive research so that
better. and reliable results can be obtained by them. This has assisted them in achieving set target
and mission. This type of research is being used as Deductive research approach helps in testing
existing approaches in which research design is developed in order to test hypothesis. It is also
being recommended that for the present research, researchers can also be engaged in making use
of quantitative research. This will assist researcher in getting end results and also because of this
they have been able to achieve set target and objectives. It is also being suggested that researcher
can also make use of primary data to collect the information. This will assist in collecting
reliable and authentic data (Kumar, Raj and Jelciana, 2018). In this there are various method is
primary data collection method which is used by researcher to collect data for the first time
though survey, questionnaire etc. Investigator has been conducting the research study that needs
to be concerned about the recommendation, implementing the use of DaaS in higher educational
institution. The suggestion has made on the basis of demand regardless modern technology
(Varghese and Buyya, 2018). That’s why, it has been suggested that consider DaaS as cloud
computing application which are quickly turn out to be a great or viable alternative. This had its
30

own set of unique benefits, advantage before using as data storage. Nowadays, higher
educational institution is becoming focused on the improved current system that why they needs
to change something innovative. So as they can easily attract potential people.
31
educational institution is becoming focused on the improved current system that why they needs
to change something innovative. So as they can easily attract potential people.
31
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

REFERENCES
Books and Journals
Abdel-Basset, M., Mohamed, M. and Chang, V., 2018. NMCDA: A framework for evaluating
cloud computing services. Future Generation Computer Systems. 86. pp.12-29.
Abe, J.O. and Ustundaug, B.B., 2018. A Data as a Service (DaaS) Model for GPU-based Data
Analytics. arXiv preprint arXiv:1802.01639.
Adhabi, E. and Anozie, C.B., 2017. Literature review for the type of interview in qualitative
research. International Journal of Education. 9(3). pp.86-97.
Al Kilani, M. and Kobziev, V., 2016. An Overview of Research Methodology in Information
System (IS). Open Access Library Journal. 3(11). pp.1-9.
Badidi, E., Routaib, H. and El Koutbi, M., 2016, May. Towards data-as-a-service provisioning
with higher-quality data. In International Symposium on Ubiquitous Networking (pp.
611-623). Springer, Singapore.
Bairagi, V. and Munot, M.V. eds., 2019. Research methodology: A practical and scientific
approach. CRC Press.
Bastrakova, I., Kemp, C. and Car, N.J., 2016. Enabling Data-as-a-Service (DaaS)-Biggest
Challenge of Geoscience Australia. AGUFM. 2016. pp.IN31D-1793.
Bond, M., and et. al., 2018. Digital transformation in German higherer education: student and
teacher perceptions and usage of digital media. International Journal of Educational
Technology in Higherer Education. 15(1). p.48.
Dang, L.M., Pand et.al.,, 2019. A survey on internet of things and cloud computing for
healthcare. Electronics. 8(7). p.768.
Fletcher, A.J., 2017. Applying critical realism in qualitative research: methodology meets
method. International journal of social research methodology. 20(2). pp.181-194.
Fulker, D.W., 2019. Overcoming Challenges of Metadata-Crawling as Foundation for
Discovering Data-as-a-Service (DaaS) Resources. AGUFM. 2019. pp.IN22B-07.
Gill, S.S., and et. al., 2018, August. Fog-based smart healthcare as a big data and cloud service
for heart patients using IoT. In International Conference on Intelligent Data
Communication Technologies and Internet of Things (pp. 1376-1383). Springer, Cham.
Giri, S. and Shakya, S., 2019. Cloud Computing and Data Security Challenges: A Nepal
Case. International Journal of Engineering Trends and Technology. 67 (3). 146, 150.
Gohari Moghadam, S.H.E.R.V.I.N. and Åhlgren, T., 2020. Moving beyond connecting things:
What are the factors telecommunication service providers need to consider when
developing a Data-as-a-Service offering?.
Hay, F.R., and et. al., 2019. Seed longevity phenotyping: recommendations on research
methodology. Journal of experimental botany. 70(2). pp.425-434.
Hayat, R., and et. al., 2019. A signaling game-based approach for Data-as-a-Service provisioning
in IoT-Cloud. Future Generation Computer Systems. 92. pp.1040-1050.
He, D., and et. al., 2016. Efficient privacy-aware authentication scheme for mobile cloud
computing services. IEEE Systems Journal. 12(2). pp.1621-1631.
Jiang, Q., Ma, J. and Wei, F., 2016. On the security of a privacy-aware authentication scheme for
distributed mobile cloud computing services. IEEE systems journal. 12(2). pp.2039-
2042.
Kumar, P.R., Raj, P.H. and Jelciana, P., 2018. Exploring data security issues and solutions in
cloud computing. Procedia Computer Science. 125. pp.691-697.
32
Books and Journals
Abdel-Basset, M., Mohamed, M. and Chang, V., 2018. NMCDA: A framework for evaluating
cloud computing services. Future Generation Computer Systems. 86. pp.12-29.
Abe, J.O. and Ustundaug, B.B., 2018. A Data as a Service (DaaS) Model for GPU-based Data
Analytics. arXiv preprint arXiv:1802.01639.
Adhabi, E. and Anozie, C.B., 2017. Literature review for the type of interview in qualitative
research. International Journal of Education. 9(3). pp.86-97.
Al Kilani, M. and Kobziev, V., 2016. An Overview of Research Methodology in Information
System (IS). Open Access Library Journal. 3(11). pp.1-9.
Badidi, E., Routaib, H. and El Koutbi, M., 2016, May. Towards data-as-a-service provisioning
with higher-quality data. In International Symposium on Ubiquitous Networking (pp.
611-623). Springer, Singapore.
Bairagi, V. and Munot, M.V. eds., 2019. Research methodology: A practical and scientific
approach. CRC Press.
Bastrakova, I., Kemp, C. and Car, N.J., 2016. Enabling Data-as-a-Service (DaaS)-Biggest
Challenge of Geoscience Australia. AGUFM. 2016. pp.IN31D-1793.
Bond, M., and et. al., 2018. Digital transformation in German higherer education: student and
teacher perceptions and usage of digital media. International Journal of Educational
Technology in Higherer Education. 15(1). p.48.
Dang, L.M., Pand et.al.,, 2019. A survey on internet of things and cloud computing for
healthcare. Electronics. 8(7). p.768.
Fletcher, A.J., 2017. Applying critical realism in qualitative research: methodology meets
method. International journal of social research methodology. 20(2). pp.181-194.
Fulker, D.W., 2019. Overcoming Challenges of Metadata-Crawling as Foundation for
Discovering Data-as-a-Service (DaaS) Resources. AGUFM. 2019. pp.IN22B-07.
Gill, S.S., and et. al., 2018, August. Fog-based smart healthcare as a big data and cloud service
for heart patients using IoT. In International Conference on Intelligent Data
Communication Technologies and Internet of Things (pp. 1376-1383). Springer, Cham.
Giri, S. and Shakya, S., 2019. Cloud Computing and Data Security Challenges: A Nepal
Case. International Journal of Engineering Trends and Technology. 67 (3). 146, 150.
Gohari Moghadam, S.H.E.R.V.I.N. and Åhlgren, T., 2020. Moving beyond connecting things:
What are the factors telecommunication service providers need to consider when
developing a Data-as-a-Service offering?.
Hay, F.R., and et. al., 2019. Seed longevity phenotyping: recommendations on research
methodology. Journal of experimental botany. 70(2). pp.425-434.
Hayat, R., and et. al., 2019. A signaling game-based approach for Data-as-a-Service provisioning
in IoT-Cloud. Future Generation Computer Systems. 92. pp.1040-1050.
He, D., and et. al., 2016. Efficient privacy-aware authentication scheme for mobile cloud
computing services. IEEE Systems Journal. 12(2). pp.1621-1631.
Jiang, Q., Ma, J. and Wei, F., 2016. On the security of a privacy-aware authentication scheme for
distributed mobile cloud computing services. IEEE systems journal. 12(2). pp.2039-
2042.
Kumar, P.R., Raj, P.H. and Jelciana, P., 2018. Exploring data security issues and solutions in
cloud computing. Procedia Computer Science. 125. pp.691-697.
32

Mishra, S., Sharma, S.K. and Alowaidi, M.A., 2020. Analysis of security issues of cloud-based
web applications. Journal of Ambient Intelligence and Humanized Computing. pp.1-12.
Namasudra, S., and et.al., 2020. Securing Multimedia by Using DNA-Based Encryption in the
Cloud Computing Environment. ACM Transactions on Multimedia Computing,
Communications, and Applications (TOMM). 16(3s). pp.1-19.
Naous, D., Schwarz, J. and Legner, C., 2017, June. Analytics as a Service: Cloud Computing and
the Trans-formation of Business Analytics Business Models and Ecosystems.
In Proceedings of the 25th European Conference on Information Systems (ECIS 2017).
Olorunfemi Abe, J. and Berk Ustundaug, B., 2018. A Data as a Service (DaaS) Model for GPU-
based Data Analytics. arXiv, pp.arXiv-1802.
Orngreen, R. and Levinsen, K., 2017. Workshops as a Research Methodology. Electronic
Journal of E-learning. 15(1). pp.70-81.
Piraghaj, S.F., and et. al., 2017. A survey and taxonomy of energy efficient resource
management techniques in platform as a service cloud. In Handbook of Research on
End-to-End Cloud Computing Architecture Design (pp. 410-454). IGI Global.
Psomakelis, E. and et.al., 2020. A Scalable and Semantic Data as a Service Marketplace for
Enhancing Cloud-Based Applications. Future Internet. 12(5). p.77.
Rof, A., Bikfalvi, A. and Marquès, P., 2020. Digital Transformation for Business Model
Innovation in Higherer Education: Overcoming the Tensions. Sustainability. 12(12).
p.4980.
Santos, H., Batista, J. and Marques, R.P., 2019. Digital transformation in higherer education: the
use of communication technologies by students. Procedia Computer Science. 164.
pp.123-130.
Schabacker, D.S. and et.al. 2019. Assessing cyberbiosecurity vulnerabilities and infrastructure
resilience. Frontiers in bioengineering and biotechnology. 7. p.61.
Shukur, B.S., Abd Ghani, M.K. and Burhasnuddin, M.A., 2019. A Cloud Computing Framework
for Higherer Education Institutes in Developing Countries (CCF_HEI_DC). In Intelligent
and Interactive Computing (pp. 397-409). Springer, Singapore.
Sileyew, K.J., 2019. Research Design and Methodology. In Text Mining-Analysis, Programming
and Application. IntechOpen.
Singh, P. and et.al., 2020. DaaS: Dew Computing as a Service for Intelligent Intrusion Detection
in Edge-of-Things Ecosystem. IEEE Internet of Things Journal.
Søilen, K.S., 2016. Users’ perceptions of Data as a Service (DaaS). Journal of Intelligence
Studies in Business. 6(2).
Stergiou, C., and et.al., 2018. Secure integration of IoT and cloud computing. Future Generation
Computer Systems. 78. pp.964-975.
Stergiou, C., and et.al., 2018. Secure integration of IoT and cloud computing. Future Generation
Computer Systems. 78. pp.964-975.
Tiwari, R., Arya, R.K. and Bansal, M., 2017. Motivating students for project-based learning for
application of research methodology skills. International Journal of Applied and Basic
Medical Research. 7(Suppl 1), p.S4.
van Hees, V.T., and et. al., 2016. Challenges and opportunities for harmonizing research
methodology: Raw accelerometry. Methods of information in medicine. 55(06). pp.525-
532.
Varghese, B. and Buyya, R., 2018. Next generation cloud computing: New trends and research
directions. Future Generation Computer Systems. 79. pp.849-861.
33
web applications. Journal of Ambient Intelligence and Humanized Computing. pp.1-12.
Namasudra, S., and et.al., 2020. Securing Multimedia by Using DNA-Based Encryption in the
Cloud Computing Environment. ACM Transactions on Multimedia Computing,
Communications, and Applications (TOMM). 16(3s). pp.1-19.
Naous, D., Schwarz, J. and Legner, C., 2017, June. Analytics as a Service: Cloud Computing and
the Trans-formation of Business Analytics Business Models and Ecosystems.
In Proceedings of the 25th European Conference on Information Systems (ECIS 2017).
Olorunfemi Abe, J. and Berk Ustundaug, B., 2018. A Data as a Service (DaaS) Model for GPU-
based Data Analytics. arXiv, pp.arXiv-1802.
Orngreen, R. and Levinsen, K., 2017. Workshops as a Research Methodology. Electronic
Journal of E-learning. 15(1). pp.70-81.
Piraghaj, S.F., and et. al., 2017. A survey and taxonomy of energy efficient resource
management techniques in platform as a service cloud. In Handbook of Research on
End-to-End Cloud Computing Architecture Design (pp. 410-454). IGI Global.
Psomakelis, E. and et.al., 2020. A Scalable and Semantic Data as a Service Marketplace for
Enhancing Cloud-Based Applications. Future Internet. 12(5). p.77.
Rof, A., Bikfalvi, A. and Marquès, P., 2020. Digital Transformation for Business Model
Innovation in Higherer Education: Overcoming the Tensions. Sustainability. 12(12).
p.4980.
Santos, H., Batista, J. and Marques, R.P., 2019. Digital transformation in higherer education: the
use of communication technologies by students. Procedia Computer Science. 164.
pp.123-130.
Schabacker, D.S. and et.al. 2019. Assessing cyberbiosecurity vulnerabilities and infrastructure
resilience. Frontiers in bioengineering and biotechnology. 7. p.61.
Shukur, B.S., Abd Ghani, M.K. and Burhasnuddin, M.A., 2019. A Cloud Computing Framework
for Higherer Education Institutes in Developing Countries (CCF_HEI_DC). In Intelligent
and Interactive Computing (pp. 397-409). Springer, Singapore.
Sileyew, K.J., 2019. Research Design and Methodology. In Text Mining-Analysis, Programming
and Application. IntechOpen.
Singh, P. and et.al., 2020. DaaS: Dew Computing as a Service for Intelligent Intrusion Detection
in Edge-of-Things Ecosystem. IEEE Internet of Things Journal.
Søilen, K.S., 2016. Users’ perceptions of Data as a Service (DaaS). Journal of Intelligence
Studies in Business. 6(2).
Stergiou, C., and et.al., 2018. Secure integration of IoT and cloud computing. Future Generation
Computer Systems. 78. pp.964-975.
Stergiou, C., and et.al., 2018. Secure integration of IoT and cloud computing. Future Generation
Computer Systems. 78. pp.964-975.
Tiwari, R., Arya, R.K. and Bansal, M., 2017. Motivating students for project-based learning for
application of research methodology skills. International Journal of Applied and Basic
Medical Research. 7(Suppl 1), p.S4.
van Hees, V.T., and et. al., 2016. Challenges and opportunities for harmonizing research
methodology: Raw accelerometry. Methods of information in medicine. 55(06). pp.525-
532.
Varghese, B. and Buyya, R., 2018. Next generation cloud computing: New trends and research
directions. Future Generation Computer Systems. 79. pp.849-861.
33

Yang, C., and et.al., 2017. Big Data and cloud computing: innovation opportunities and
challenges. International Journal of Digital Earth. 10(1). pp.13-53.
Yang, C., and et.al., 2017. Big Data and cloud computing: innovation opportunities and
challenges. International Journal of Digital Earth, 10(1), pp.13-53.
34
challenges. International Journal of Digital Earth. 10(1). pp.13-53.
Yang, C., and et.al., 2017. Big Data and cloud computing: innovation opportunities and
challenges. International Journal of Digital Earth, 10(1), pp.13-53.
34
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

APPENDIX
PROPOSAL
INTRODUCTION
Advancement in technology has brought various kinds of changes within education
system as well as in business. Digital transformation has leveraged data and technologies both in
education system. Due to this digital transformation needs and requirements of students or
learners have also changed and in order to fulfil these changes school, universities and colleges
have adopted advance technologies within their system so that learning environment can be
created as per needs and requirement of students (Santos, Batista and Marques, 2019). It has
further made it much easier for students to attend classes, access data or information required by
them on timely basis. It has further increased usage of various kinds of technologies for students
as well for management or staff members of schools, colleges and universities like digital
libraries, cloud computing services etc.
Background
Cloud computing can be defined as kind of on-demand availability of services of
computer resources, data storage service, computing power and many other kinds of service
provision to users (Stergiou and et.al., 2018). Usage of cloud computing services has increased
drastically in education, business as well as for personal use. It is one of the most effective and
most commonly used technology whose usage has increased in education industry, in business as
well as for personal use. There are various kinds of services that are provided by cloud
computing that can be used by organizations in education industry. Cloud computing provides
three different kinds of services: Software as a service, platform as a service and infrastructure as
a service. All the three type of services has their own use and is used in many different ways
within organization. But most commonly in education industry Software as a service Cloud
service is used. Using this service many different kinds of applications over internet can be
delivered to its users. Today in most of the industries including education industry, data has
become one of the most important things which is required to be considered. Data as a Service or
which is provided by cloud offers. This service has recently come into picture which uses all the
three services so it has been categorised as another type of cloud offering or service (Yang and
et.al., 2017). This DaaS service is most commonly used and offered by Cloud service providers
and is used by most of the organizations as well as by individuals. This service is mostly used by
35
PROPOSAL
INTRODUCTION
Advancement in technology has brought various kinds of changes within education
system as well as in business. Digital transformation has leveraged data and technologies both in
education system. Due to this digital transformation needs and requirements of students or
learners have also changed and in order to fulfil these changes school, universities and colleges
have adopted advance technologies within their system so that learning environment can be
created as per needs and requirement of students (Santos, Batista and Marques, 2019). It has
further made it much easier for students to attend classes, access data or information required by
them on timely basis. It has further increased usage of various kinds of technologies for students
as well for management or staff members of schools, colleges and universities like digital
libraries, cloud computing services etc.
Background
Cloud computing can be defined as kind of on-demand availability of services of
computer resources, data storage service, computing power and many other kinds of service
provision to users (Stergiou and et.al., 2018). Usage of cloud computing services has increased
drastically in education, business as well as for personal use. It is one of the most effective and
most commonly used technology whose usage has increased in education industry, in business as
well as for personal use. There are various kinds of services that are provided by cloud
computing that can be used by organizations in education industry. Cloud computing provides
three different kinds of services: Software as a service, platform as a service and infrastructure as
a service. All the three type of services has their own use and is used in many different ways
within organization. But most commonly in education industry Software as a service Cloud
service is used. Using this service many different kinds of applications over internet can be
delivered to its users. Today in most of the industries including education industry, data has
become one of the most important things which is required to be considered. Data as a Service or
which is provided by cloud offers. This service has recently come into picture which uses all the
three services so it has been categorised as another type of cloud offering or service (Yang and
et.al., 2017). This DaaS service is most commonly used and offered by Cloud service providers
and is used by most of the organizations as well as by individuals. This service is mostly used by
35

Universities and colleges that provide higher education to students for storing and sharing their
data or information. But there are various kinds of vulnerabilities associated with this service to
which institutes or individuals using this service are unaware of. It has also been analysed that
Most of the organizations use it as a solution to manage their data, expand and sorter data in
different format in a secure manner so that it can be accessed in an appropriate manner, without
degrading overall quality of information stored and without risking theft or security of
information.
Aim
This project will focus upon analysing different kinds of security issues associated with
Data as a Service Cloud offering. So, the main aim of this dissertation is ‘To analyse
vulnerabilities associated with Cloud offering of Data as a Service (DaaS)’.
Objectives
The main objectives that this project will be achieving are as follows:
To analyse importance of cloud computing
To analyse different kinds of cloud computing services
To evaluate ways in which Data as a Service (DaaS) Cloud offering is used.
To analyse importance of DaaS in Higher education
To evaluate vulnerabilities associated with Data as a Service cloud offering and their impact
on organizations.
To identify ways in which vulnerabilities associated with Data as a Service (DaaS) Cloud
offering can be reduced.
To recommend appropriate ways though which usage of Data as a Service (DaaS) Cloud
offering can be increased and vulnerabilities associated with it can be reduced.
To identify gaps in this research and suggest future results.
Research questions
The main research questions that this project will be answering are as follows:
Why cloud computing is important?
What are different kinds of cloud computing services?
How Data as a Service (DaaS) Cloud offering is used?
Why DaaS is important in Higher education?
36
data or information. But there are various kinds of vulnerabilities associated with this service to
which institutes or individuals using this service are unaware of. It has also been analysed that
Most of the organizations use it as a solution to manage their data, expand and sorter data in
different format in a secure manner so that it can be accessed in an appropriate manner, without
degrading overall quality of information stored and without risking theft or security of
information.
Aim
This project will focus upon analysing different kinds of security issues associated with
Data as a Service Cloud offering. So, the main aim of this dissertation is ‘To analyse
vulnerabilities associated with Cloud offering of Data as a Service (DaaS)’.
Objectives
The main objectives that this project will be achieving are as follows:
To analyse importance of cloud computing
To analyse different kinds of cloud computing services
To evaluate ways in which Data as a Service (DaaS) Cloud offering is used.
To analyse importance of DaaS in Higher education
To evaluate vulnerabilities associated with Data as a Service cloud offering and their impact
on organizations.
To identify ways in which vulnerabilities associated with Data as a Service (DaaS) Cloud
offering can be reduced.
To recommend appropriate ways though which usage of Data as a Service (DaaS) Cloud
offering can be increased and vulnerabilities associated with it can be reduced.
To identify gaps in this research and suggest future results.
Research questions
The main research questions that this project will be answering are as follows:
Why cloud computing is important?
What are different kinds of cloud computing services?
How Data as a Service (DaaS) Cloud offering is used?
Why DaaS is important in Higher education?
36

What are different kinds of vulnerabilities associated with Data as a Service cloud offering
and their impact on organizations?
What are different ways in which vulnerabilities associated with Data as a Service (DaaS)
Cloud offering can be reduced?
Recommend appropriate ways though which usage of Data as a Service (DaaS) Cloud
offering can be increased and vulnerabilities associated with it can be reduced.
What are main gaps in this research and suggest future results.
LITERATURE REVIEW
Different kinds of cloud computing services
According to the view of Abdel-Basset, Mohamed and Chang, (2018) There are many
different kinds of services that are provided by cloud offerors. Due to increasing availability of
services and resources over internet usage and importance of clod computing over internet has
increased drastically. as per its use and important services in cloud computing have bee
categorised into three different categories. Each of these categories and sub categories type of
services. Three main types of cloud computing services that are most commonly used by
individuals and organizations. Three typically used cloud computing service categories used are:
IaaS (Infrastructure as a service), PaaS (Platform as a service) and SaaS (Software as a service).
But now a new type of service have been identified which is DaaS or Data as a service. IaaS
service provide users raw computing resources such as storage capacity, processing power,
networking and many more. Platform as a service or PaaS which provide computing
infrastructure and also a development platform to cloud users. SaaS or Software as a service
provides application- level services to cloud users. This service has been recently categorised and
is the latest service which is offered by cloud providers. This service has been developed to
overcome limitation of approaches in data technology. This service allows storage of data in
repositories whose location is knowledge and is relevant for sharing process. Today cloud
computing has become extremely important for different kinds of business organizations due to
its increasing usage and benefits that it provides to its issuers. Cloud computing technology has
made it much easier for organizations to achieve their main business objectives in an appropriate
manner.
37
and their impact on organizations?
What are different ways in which vulnerabilities associated with Data as a Service (DaaS)
Cloud offering can be reduced?
Recommend appropriate ways though which usage of Data as a Service (DaaS) Cloud
offering can be increased and vulnerabilities associated with it can be reduced.
What are main gaps in this research and suggest future results.
LITERATURE REVIEW
Different kinds of cloud computing services
According to the view of Abdel-Basset, Mohamed and Chang, (2018) There are many
different kinds of services that are provided by cloud offerors. Due to increasing availability of
services and resources over internet usage and importance of clod computing over internet has
increased drastically. as per its use and important services in cloud computing have bee
categorised into three different categories. Each of these categories and sub categories type of
services. Three main types of cloud computing services that are most commonly used by
individuals and organizations. Three typically used cloud computing service categories used are:
IaaS (Infrastructure as a service), PaaS (Platform as a service) and SaaS (Software as a service).
But now a new type of service have been identified which is DaaS or Data as a service. IaaS
service provide users raw computing resources such as storage capacity, processing power,
networking and many more. Platform as a service or PaaS which provide computing
infrastructure and also a development platform to cloud users. SaaS or Software as a service
provides application- level services to cloud users. This service has been recently categorised and
is the latest service which is offered by cloud providers. This service has been developed to
overcome limitation of approaches in data technology. This service allows storage of data in
repositories whose location is knowledge and is relevant for sharing process. Today cloud
computing has become extremely important for different kinds of business organizations due to
its increasing usage and benefits that it provides to its issuers. Cloud computing technology has
made it much easier for organizations to achieve their main business objectives in an appropriate
manner.
37
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Data as a Service (DaaS) Cloud offering and ways in which it is used in Higher education
According to Shukur, Abd Ghani and Burhasnuddin (2019) Data as a service (Daas) is
based on the emerging service on the cloud technology. For large user’s communities in the term
of scientific and industrial context which become consider as serious difficulty for moving data
or information because of time transfer and network link limitations. There is large amount of
data sets which growing constantly and process analysis in large amount or datasets as fulfil all
essential needs of higher computing capacities. DaaS is based on the alternative cloud computing
service model, different from other models where it has made available to users and take more
facilities as well as services. It is one of the largest fundamental that able to process or manage
the largest quantity of heterogeneous information. Higher education institutions are basically
focused on the innovation so that they will consider DaaS which collect or gather large amount
of data within cloud. Afterwards, student can access information from cloud within different
innovative ways. At certain level, different areas that has long utilised data driven practices.
Higher education institution have faced with need to be innovation and try to remain competitive
in global marketplace. The use of DaaS is increasing within higher education which may
consider as important part. Many other institutions have been realised that provide better type of
benefits, advantage. This will help for providing the better quality of service while implementing
software, programming environment databases, antiviruses.
Psomakelis and et.al. (2020) Many higher education have limited resources and unable to
provide the better quality of education service of their student. That’s why, it will be
implementing DaaS (Data as a service) that support for giving the better facilities. As a result, it
is also looking for other ways to acquire more information through software, applications. DaaS
can provide the brief idea about the overall processing of education system and use them various
application at an affordable price or cost. Afterwards, Higher education universities offering the
cloud service with the help of DaaS which making transition to reach their destination. With the
evolution of technology, there are large number of education service migrates from different
traditional forms to their online approach. Various education services that needs to be focused on
the adequate system by using a proper technology. Afterwards, cloud based techniques has been
emerged as viable and promising a better solution to the challenges associated with overall
education system. it became consider as convenient, on demand network access to easily sharing
the configurable computing services.
38
According to Shukur, Abd Ghani and Burhasnuddin (2019) Data as a service (Daas) is
based on the emerging service on the cloud technology. For large user’s communities in the term
of scientific and industrial context which become consider as serious difficulty for moving data
or information because of time transfer and network link limitations. There is large amount of
data sets which growing constantly and process analysis in large amount or datasets as fulfil all
essential needs of higher computing capacities. DaaS is based on the alternative cloud computing
service model, different from other models where it has made available to users and take more
facilities as well as services. It is one of the largest fundamental that able to process or manage
the largest quantity of heterogeneous information. Higher education institutions are basically
focused on the innovation so that they will consider DaaS which collect or gather large amount
of data within cloud. Afterwards, student can access information from cloud within different
innovative ways. At certain level, different areas that has long utilised data driven practices.
Higher education institution have faced with need to be innovation and try to remain competitive
in global marketplace. The use of DaaS is increasing within higher education which may
consider as important part. Many other institutions have been realised that provide better type of
benefits, advantage. This will help for providing the better quality of service while implementing
software, programming environment databases, antiviruses.
Psomakelis and et.al. (2020) Many higher education have limited resources and unable to
provide the better quality of education service of their student. That’s why, it will be
implementing DaaS (Data as a service) that support for giving the better facilities. As a result, it
is also looking for other ways to acquire more information through software, applications. DaaS
can provide the brief idea about the overall processing of education system and use them various
application at an affordable price or cost. Afterwards, Higher education universities offering the
cloud service with the help of DaaS which making transition to reach their destination. With the
evolution of technology, there are large number of education service migrates from different
traditional forms to their online approach. Various education services that needs to be focused on
the adequate system by using a proper technology. Afterwards, cloud based techniques has been
emerged as viable and promising a better solution to the challenges associated with overall
education system. it became consider as convenient, on demand network access to easily sharing
the configurable computing services.
38

Vulnerabilities associated with Data as a Service cloud offering and their impact on
organizations.
According to Mishra, Sharma and Alowaidi (2020) organizations continue to develop or
adopt new applications which can easily migrate with existing applications to cloud based
services. Higher education institution is mainly focused on cloud service whereas they are
adopting DaaS in which providing the best quality of service. At certain level, there are different
kinds of risks, threat and vulnerabilities that organization face when they are moving application
or data towards cloud.
Consumer have reduced the control and visibility- this type of vulnerability occurs due to
the assets or operations to cloud. Through this, enterprise have been lost some visibility or
control towards operations. When using external cloud service, it would be increasing the
chances of privacy or security issues.
Ways in which vulnerabilities associated with Data as a Service (DaaS) Cloud offering can be
reduced.
According to Giri and Shakya (2019) there are different kind of vulnerabilities occurs
because of higher profile breach within cloud platform. Various kind of breach is particularly
increasing so much trouble since all service stored of all users website. Especially when
belonging to other administrator with extensive permission for organization. The primarily scale
of breach is extensive and 90% organization have faced the vulnerabilities which are associated
with failure of system, authorised access of attackers within cloud network. Additionally, there
has been explosion of new applications which help for student to learn or continues higher
education. Afterwards, it is moving forwards to recognise the different advantage, benefits which
brings more cloud movement for enterprise.
Singh and et.al. (2020) said that Vulnerabilities are associated with loss of intellectual
property which is increasingly store sensitive data or information within cloud. There are large
number of sensitive information or data that include as intellectual property. When cloud service
is completely breached, attacker has gained more access to their sensitive data. Certain kind of
service can even pose a risk, if applicable term or condition which claim ownership of data
uploaded.
Compliance violations and regulatory action which become consider cause of
vulnerabilities because companies operate different sort of regulatory control in term of sensitive
39
organizations.
According to Mishra, Sharma and Alowaidi (2020) organizations continue to develop or
adopt new applications which can easily migrate with existing applications to cloud based
services. Higher education institution is mainly focused on cloud service whereas they are
adopting DaaS in which providing the best quality of service. At certain level, there are different
kinds of risks, threat and vulnerabilities that organization face when they are moving application
or data towards cloud.
Consumer have reduced the control and visibility- this type of vulnerability occurs due to
the assets or operations to cloud. Through this, enterprise have been lost some visibility or
control towards operations. When using external cloud service, it would be increasing the
chances of privacy or security issues.
Ways in which vulnerabilities associated with Data as a Service (DaaS) Cloud offering can be
reduced.
According to Giri and Shakya (2019) there are different kind of vulnerabilities occurs
because of higher profile breach within cloud platform. Various kind of breach is particularly
increasing so much trouble since all service stored of all users website. Especially when
belonging to other administrator with extensive permission for organization. The primarily scale
of breach is extensive and 90% organization have faced the vulnerabilities which are associated
with failure of system, authorised access of attackers within cloud network. Additionally, there
has been explosion of new applications which help for student to learn or continues higher
education. Afterwards, it is moving forwards to recognise the different advantage, benefits which
brings more cloud movement for enterprise.
Singh and et.al. (2020) said that Vulnerabilities are associated with loss of intellectual
property which is increasingly store sensitive data or information within cloud. There are large
number of sensitive information or data that include as intellectual property. When cloud service
is completely breached, attacker has gained more access to their sensitive data. Certain kind of
service can even pose a risk, if applicable term or condition which claim ownership of data
uploaded.
Compliance violations and regulatory action which become consider cause of
vulnerabilities because companies operate different sort of regulatory control in term of sensitive
39

data or information. Under circumstances, organization must know about the data where it will
be stored and accessible. It often violates every of these tents which are putting enterprise in the
non-compliance. At certain level, it will be generating a serious causes in the vulnerabilities and
associated within DaaS cloud services.
Giri and Shakya (2019) Loss of control over multiple end user action where organizations
are in dark about using cloud DaaS service. In case, student can down the report which needs to
be stored personal information with cloud storage service and then accessible information or
data. So as it will be developing vulnerabilities of data loss associated with DaaS cloud service.
Sometimes, it would be used as data exfiltration which are uncovered the different technique or
method whereby attackers are encoded sensitive data in the different format.
RESEARCH METHODOLOGY
Research methodology is based on the technique which basically used for collecting and
gathering large amount of information. These are completely relevant to research topic or
subject. Researcher is always focused on the research methodology which help for identifying
large amount of information which makes a better way to decision process. Sometimes, research
methodology is basically consider as important aspect within research study to examine the
previous studies, identifying future needs to research expansion.
Research type
Research type or method is basically defined as systematic and scientific procedures of
data collection, compilation analysis, implication pertaining and interpretation to the enterprise
problem. Research type can be divided into different ways: Qualitative and Quantitative. These
are the most commonly used in accordance to nature or purpose of study (Sileyew, 2019).
Quantitative research method is basically descripting about the infer, resolves any kind of
problem through different theories. It emphasis with the emotions, sound, feeling and other non-
numerical elements. It has been noted that considerable as important information within
qualitative nature but cannot be analysed in the mathematical techniques. On the other hand,
Quantitative research is based on the numerical instruction which gathering or collecting large
amount of numerical data or information. So as it become easier for researcher to find accurate
conclusion and solution.
In this study, researcher will use qualitative research method that help for collecting or
gathering relevant information through different resources such as article and journals. This type
40
be stored and accessible. It often violates every of these tents which are putting enterprise in the
non-compliance. At certain level, it will be generating a serious causes in the vulnerabilities and
associated within DaaS cloud services.
Giri and Shakya (2019) Loss of control over multiple end user action where organizations
are in dark about using cloud DaaS service. In case, student can down the report which needs to
be stored personal information with cloud storage service and then accessible information or
data. So as it will be developing vulnerabilities of data loss associated with DaaS cloud service.
Sometimes, it would be used as data exfiltration which are uncovered the different technique or
method whereby attackers are encoded sensitive data in the different format.
RESEARCH METHODOLOGY
Research methodology is based on the technique which basically used for collecting and
gathering large amount of information. These are completely relevant to research topic or
subject. Researcher is always focused on the research methodology which help for identifying
large amount of information which makes a better way to decision process. Sometimes, research
methodology is basically consider as important aspect within research study to examine the
previous studies, identifying future needs to research expansion.
Research type
Research type or method is basically defined as systematic and scientific procedures of
data collection, compilation analysis, implication pertaining and interpretation to the enterprise
problem. Research type can be divided into different ways: Qualitative and Quantitative. These
are the most commonly used in accordance to nature or purpose of study (Sileyew, 2019).
Quantitative research method is basically descripting about the infer, resolves any kind of
problem through different theories. It emphasis with the emotions, sound, feeling and other non-
numerical elements. It has been noted that considerable as important information within
qualitative nature but cannot be analysed in the mathematical techniques. On the other hand,
Quantitative research is based on the numerical instruction which gathering or collecting large
amount of numerical data or information. So as it become easier for researcher to find accurate
conclusion and solution.
In this study, researcher will use qualitative research method that help for collecting or
gathering relevant information through different resources such as article and journals. This type
40
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

of method is based on theoretical aspect so that it help for investigator to find accurate
information. Investigator will focus on the previous studies and identifying theories which
already used within it.
Research design
It is based on the procedure or plan that help for representing overall strategy where
choosing to integrate with different components of research study. it is become consider as
coherent and logical way. Thereby, it ensuring that will effectively identify the solution of
research problem. Research design can be categorised into different ways: conclusive and
exploratory. These are consider the most commonly used research design which help for
exploring the specific areas of research.
Exploratory research is useful for research where they can explore specific aspect of
research and then generating a proper result. In qualitative, research will choose exploratory
research design that provide the brief idea about the overall operational tasks. Investigator will
focus on the research aim and objective that provide better way to understand the study and
move towards right direction (Orngreen and Levinsen, 2017). Apart from that Conclusive
research design is also used in quantitative approach to find out the accurate solution. Through
this study, researcher have no option to move or change their direction. That’s why, researcher
will focus on exploratory research design to perform different tasks effectively.
Research approach
Research approach is define as process that consist of various phases on the basis of
particular assumption towards research study. Through this, it will be describing the detailed
explanation of data collection and interpretation. It help for researcher to get more solution and
generate accurate result. Research approach can be categorised into different types: Abductive,
Deductive and Inductive.
Investigator will select the inductive approach which focuses upon testing and developing
new theries. Pre-existing theories are basically providing the brief idea about the certain level
which may associated with research problem. Afterwards, investigator will use them to generate
accurate result or outcome.
Research philosophy
It helps in development of phenomenon though which data can be collected, analysed and
used. There are two main type of philosophy approaches: interpretivism and positivism.
41
information. Investigator will focus on the previous studies and identifying theories which
already used within it.
Research design
It is based on the procedure or plan that help for representing overall strategy where
choosing to integrate with different components of research study. it is become consider as
coherent and logical way. Thereby, it ensuring that will effectively identify the solution of
research problem. Research design can be categorised into different ways: conclusive and
exploratory. These are consider the most commonly used research design which help for
exploring the specific areas of research.
Exploratory research is useful for research where they can explore specific aspect of
research and then generating a proper result. In qualitative, research will choose exploratory
research design that provide the brief idea about the overall operational tasks. Investigator will
focus on the research aim and objective that provide better way to understand the study and
move towards right direction (Orngreen and Levinsen, 2017). Apart from that Conclusive
research design is also used in quantitative approach to find out the accurate solution. Through
this study, researcher have no option to move or change their direction. That’s why, researcher
will focus on exploratory research design to perform different tasks effectively.
Research approach
Research approach is define as process that consist of various phases on the basis of
particular assumption towards research study. Through this, it will be describing the detailed
explanation of data collection and interpretation. It help for researcher to get more solution and
generate accurate result. Research approach can be categorised into different types: Abductive,
Deductive and Inductive.
Investigator will select the inductive approach which focuses upon testing and developing
new theries. Pre-existing theories are basically providing the brief idea about the certain level
which may associated with research problem. Afterwards, investigator will use them to generate
accurate result or outcome.
Research philosophy
It helps in development of phenomenon though which data can be collected, analysed and
used. There are two main type of philosophy approaches: interpretivism and positivism.
41

Positivism believes that society trends shape an individual and is mostly used in quantitative
study (Orngreen and Levinsen, 2017). Whereas, interpretivism philosophy focuses upon a fact
that specific role is performed by researcher in society. It is mostly used with qualitative research
studies. For this dissertation, researcher will be using interpretivism philosophy as it is
qualitative study in which in which formulation of beliefs and assumptions will take place.
Data collection
It is one of the most important method that help researcher in collecting appropriate and
required data for the research. It helps in answering main research questions in an appropriate
manner or many times it helps in testing developed hypothesis for reaching to conclusion. There
are two types of data collection methods that helps in collecting reliable and accurate information
(Orngreen and Levinsen, 2017). First type of method is primary data collection method which is
used by researcher to collect data for the first time though survey, questionnaire etc. Second type
of data is secondary data which is already published and is collected though books, journals,
articles etc. for this research, researcher has focused upon collecting secondary data from book,
journals, articles and from many other sources.
Literature search strategy
This strategy helps researcher in collecting appropriate and accurate secondary data from
valid sources. Literature search strategy used for this research is: in order to identify appropriate
secondary key terms will be identified that will be used to identify appropriate secondary data
from online databases and libraries. Then in order to select appropriate data inclusion and
exclusion criteria for the search will be defined. Lastly on the basis of date of publication,
secondary data selected will be selected or rejected.
Key terms for this research are: Data as a Service, DaaS, Cloud computing, higherer education,
vulnerabilities, security issues.
Inclusion criteria: All the articles or papers that consist of two or more than two key terms,
published in English and were not more than 5 years old were selected.
Exclusion criteria: All the articles that were more than 5 years old and were not published in
English were rejected.
PROJECT PLAN (GANTT CHART)
Task Name Duration Start Finish
42
study (Orngreen and Levinsen, 2017). Whereas, interpretivism philosophy focuses upon a fact
that specific role is performed by researcher in society. It is mostly used with qualitative research
studies. For this dissertation, researcher will be using interpretivism philosophy as it is
qualitative study in which in which formulation of beliefs and assumptions will take place.
Data collection
It is one of the most important method that help researcher in collecting appropriate and
required data for the research. It helps in answering main research questions in an appropriate
manner or many times it helps in testing developed hypothesis for reaching to conclusion. There
are two types of data collection methods that helps in collecting reliable and accurate information
(Orngreen and Levinsen, 2017). First type of method is primary data collection method which is
used by researcher to collect data for the first time though survey, questionnaire etc. Second type
of data is secondary data which is already published and is collected though books, journals,
articles etc. for this research, researcher has focused upon collecting secondary data from book,
journals, articles and from many other sources.
Literature search strategy
This strategy helps researcher in collecting appropriate and accurate secondary data from
valid sources. Literature search strategy used for this research is: in order to identify appropriate
secondary key terms will be identified that will be used to identify appropriate secondary data
from online databases and libraries. Then in order to select appropriate data inclusion and
exclusion criteria for the search will be defined. Lastly on the basis of date of publication,
secondary data selected will be selected or rejected.
Key terms for this research are: Data as a Service, DaaS, Cloud computing, higherer education,
vulnerabilities, security issues.
Inclusion criteria: All the articles or papers that consist of two or more than two key terms,
published in English and were not more than 5 years old were selected.
Exclusion criteria: All the articles that were more than 5 years old and were not published in
English were rejected.
PROJECT PLAN (GANTT CHART)
Task Name Duration Start Finish
42
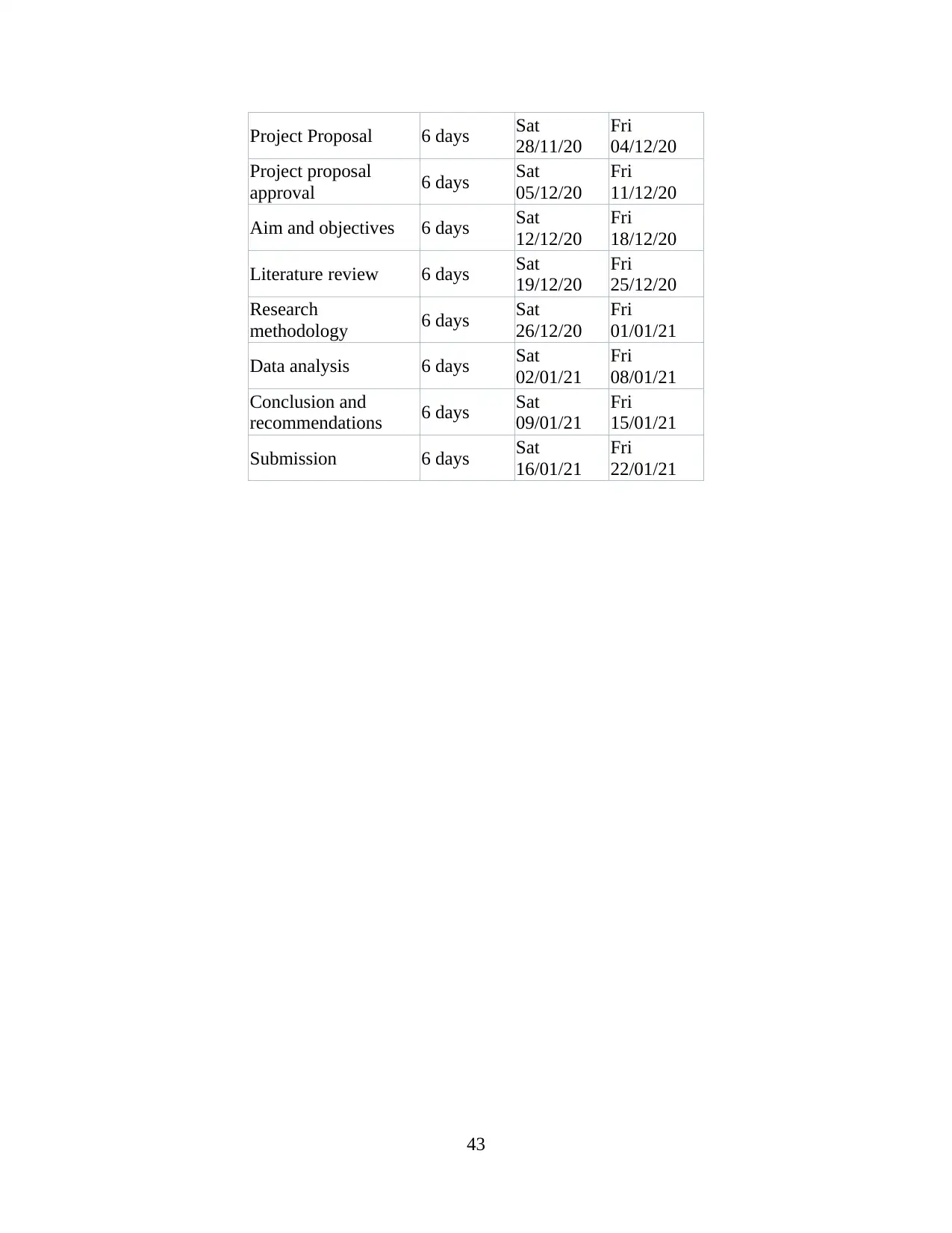
Project Proposal 6 days Sat
28/11/20
Fri
04/12/20
Project proposal
approval 6 days Sat
05/12/20
Fri
11/12/20
Aim and objectives 6 days Sat
12/12/20
Fri
18/12/20
Literature review 6 days Sat
19/12/20
Fri
25/12/20
Research
methodology 6 days Sat
26/12/20
Fri
01/01/21
Data analysis 6 days Sat
02/01/21
Fri
08/01/21
Conclusion and
recommendations 6 days Sat
09/01/21
Fri
15/01/21
Submission 6 days Sat
16/01/21
Fri
22/01/21
43
28/11/20
Fri
04/12/20
Project proposal
approval 6 days Sat
05/12/20
Fri
11/12/20
Aim and objectives 6 days Sat
12/12/20
Fri
18/12/20
Literature review 6 days Sat
19/12/20
Fri
25/12/20
Research
methodology 6 days Sat
26/12/20
Fri
01/01/21
Data analysis 6 days Sat
02/01/21
Fri
08/01/21
Conclusion and
recommendations 6 days Sat
09/01/21
Fri
15/01/21
Submission 6 days Sat
16/01/21
Fri
22/01/21
43
1 out of 46
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





