Disaster Recovery Plan Report
VerifiedAdded on 2020/03/01
|8
|1988
|188
Report
AI Summary
The report outlines a comprehensive disaster recovery plan for organizations, detailing strategies to protect IT infrastructure and data from various disruptive events. It discusses the importance of maintaining business continuity, identifies potential threats, and suggests effective backup solutions. The report emphasizes the necessity of contingency planning and risk mitigation strategies to ensure organizational resilience in the face of disasters.

RUNNING HEAD: Disaster Recovery Plan
Skillage I.T.
Disaster Recovery Plan for an Organization
Recovery Plans
Skillage I.T.
Disaster Recovery Plan for an Organization
Recovery Plans
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Disaster Recovery Plan
Table of Contents
Introduction..............................................................................................................................................2
Answer 1..........................................................................................................................................2
Answer 2..........................................................................................................................................2
Answer 3..........................................................................................................................................3
Answer 4..........................................................................................................................................4
Answer 5..........................................................................................................................................5
Answer 6..........................................................................................................................................5
References................................................................................................................................................7
Introduction
Disaster Recovery Plan can be expressed as a document process or set of procedures to
recover and to protect the details of business organization and its IT infrastructure to be
aware of tending a disaster or disruptive events. Disaster can be arising in any situation i.e.
1
Table of Contents
Introduction..............................................................................................................................................2
Answer 1..........................................................................................................................................2
Answer 2..........................................................................................................................................2
Answer 3..........................................................................................................................................3
Answer 4..........................................................................................................................................4
Answer 5..........................................................................................................................................5
Answer 6..........................................................................................................................................5
References................................................................................................................................................7
Introduction
Disaster Recovery Plan can be expressed as a document process or set of procedures to
recover and to protect the details of business organization and its IT infrastructure to be
aware of tending a disaster or disruptive events. Disaster can be arising in any situation i.e.
1

Disaster Recovery Plan
power failures, IT system crashes, supply chain problems or it can be a natural calamity.
Organizations sometimes ignore or avoid the disruptive event but it cannot be ignored for
long term. In an organisation to avoid the disasters careful planning and strategies should
be planned to get it minimized from the disaster. The main object to avoid the disaster is
the data loss of an organisation and downtime (Phillips, 2015).
Alternatives of Disaster Recovery Plan-
It is necessary to maintain the business continuity plan which is generally falls within the
several issues regarding costs constraints. It generally arises where business lack in
achieving the targets and the requirements regarding to the main objects which need to be
fulfilled. An organization need to set the objectives and the strategies to avoid the disaster.
The best solution making in consideration is to keep the initial cost, transferring of data
cost and the cost of data. To identify the type of risk occurred and to evaluate need to be
identified the cost failures and how to identify the profitability from the occurrence of a
disaster. In the given time it is essential to restore the services and to recover the valuable
data.
Contingency Plan-
It plays a vital role to perform an action so as to avoid the disaster occurred. A well
designed format should be created so that significant future event or problems may not
arise in future. It is also known as Plan B, as it is an alternative action being taken if the
expected targets generally fails to materialize. It has become the necessity to make the
contingency plan as the main priority.
Answer 1: Threats that could impact any of the important data are:
Misuse of staff details
Organization database
Information regarding customer records and billing information
Progress report or dashboards of individual user.
Unwanted files from access to an internet usability
Department of Finance which is affected because of its billing information and their
financial reports.
Answer 2:The applications and files that you will backup:
2
power failures, IT system crashes, supply chain problems or it can be a natural calamity.
Organizations sometimes ignore or avoid the disruptive event but it cannot be ignored for
long term. In an organisation to avoid the disasters careful planning and strategies should
be planned to get it minimized from the disaster. The main object to avoid the disaster is
the data loss of an organisation and downtime (Phillips, 2015).
Alternatives of Disaster Recovery Plan-
It is necessary to maintain the business continuity plan which is generally falls within the
several issues regarding costs constraints. It generally arises where business lack in
achieving the targets and the requirements regarding to the main objects which need to be
fulfilled. An organization need to set the objectives and the strategies to avoid the disaster.
The best solution making in consideration is to keep the initial cost, transferring of data
cost and the cost of data. To identify the type of risk occurred and to evaluate need to be
identified the cost failures and how to identify the profitability from the occurrence of a
disaster. In the given time it is essential to restore the services and to recover the valuable
data.
Contingency Plan-
It plays a vital role to perform an action so as to avoid the disaster occurred. A well
designed format should be created so that significant future event or problems may not
arise in future. It is also known as Plan B, as it is an alternative action being taken if the
expected targets generally fails to materialize. It has become the necessity to make the
contingency plan as the main priority.
Answer 1: Threats that could impact any of the important data are:
Misuse of staff details
Organization database
Information regarding customer records and billing information
Progress report or dashboards of individual user.
Unwanted files from access to an internet usability
Department of Finance which is affected because of its billing information and their
financial reports.
Answer 2:The applications and files that you will backup:
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Disaster Recovery Plan
Recovery of Database- It is also termed as Application- aware backups. It is
necessary and good for backing up of applications and databases. It usually includes
various features like independent retention schedules and automated maintenance.
Tape Drives- These are the most commonly used, because of the most common
backup devices. It basically uses magnetic tape cartridges to store data, but it has one
disadvantage that these are not highly reliable. Tape drivers are fairly slow, and eve
its selling price is low in cost (Cook, 2015).
System Imaging-It captures everything that is placed on server’s disk like files,
programs, operating system, etc. The best suitable way of restoring the system images
is when it is capable before is shut down and restore the whole data on daily basis.
Recovery of Desktop security- The protection of business security offers simple and
affordable desktop security which usually aims to protect against the malicious
activities and dangerous threats. It basically shields desktops and servers from virus
attacks and quickly recovers desktops from the event of failures (Haddow, Bullock, and
Coppola, 2017).
Backup of Dashboards- When you are logged out from the web; you can directly log
in and can recover the files present on the dashboard like document file or report. This
allows you to recover all the work and allow you to analyse and editing to a file.
Backup of Storage Location-It keeps the copy of disinfected or those files who are
not harmed from any threat or malicious activities. Its main feature is to restore all the
possible data to process the objects at any time.
Answer 3:Which, if any, data listed as important may be subject to legislative or
regulatory constraints
All organization has some data collection and release activities that are followed by
some legal rules, regulations and legislative authorizations. Some of these are:
1. Administrative Barriers- They are basically bounded with the limited data sharing.
Security concerns and regulations required to use the specific software for circulating of
information so that these requirements can secure data and computer systems.
2. Data Incompatibilities- Various resources are needed for the manipulation, coding and
transmitting of data within the organization. It can be limited because of user friendly data
information tools or it can be detailed documentation.
3
Recovery of Database- It is also termed as Application- aware backups. It is
necessary and good for backing up of applications and databases. It usually includes
various features like independent retention schedules and automated maintenance.
Tape Drives- These are the most commonly used, because of the most common
backup devices. It basically uses magnetic tape cartridges to store data, but it has one
disadvantage that these are not highly reliable. Tape drivers are fairly slow, and eve
its selling price is low in cost (Cook, 2015).
System Imaging-It captures everything that is placed on server’s disk like files,
programs, operating system, etc. The best suitable way of restoring the system images
is when it is capable before is shut down and restore the whole data on daily basis.
Recovery of Desktop security- The protection of business security offers simple and
affordable desktop security which usually aims to protect against the malicious
activities and dangerous threats. It basically shields desktops and servers from virus
attacks and quickly recovers desktops from the event of failures (Haddow, Bullock, and
Coppola, 2017).
Backup of Dashboards- When you are logged out from the web; you can directly log
in and can recover the files present on the dashboard like document file or report. This
allows you to recover all the work and allow you to analyse and editing to a file.
Backup of Storage Location-It keeps the copy of disinfected or those files who are
not harmed from any threat or malicious activities. Its main feature is to restore all the
possible data to process the objects at any time.
Answer 3:Which, if any, data listed as important may be subject to legislative or
regulatory constraints
All organization has some data collection and release activities that are followed by
some legal rules, regulations and legislative authorizations. Some of these are:
1. Administrative Barriers- They are basically bounded with the limited data sharing.
Security concerns and regulations required to use the specific software for circulating of
information so that these requirements can secure data and computer systems.
2. Data Incompatibilities- Various resources are needed for the manipulation, coding and
transmitting of data within the organization. It can be limited because of user friendly data
information tools or it can be detailed documentation.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Disaster Recovery Plan
3. Data Sharing Guidance- Lack of standard languages are processed related to the
sharing of the data. It has legally served the data policies and procedures within the
organizations because of its inconsistent data researched by the policy community. Its
main roles is to provide the data to its partners for the public purposes because of
balancing of privacy concerns but some are not familiar with it so Experts and resources
have the knowledge for creating the agreements with then but are not easily shared
(Snedaker, 2013).
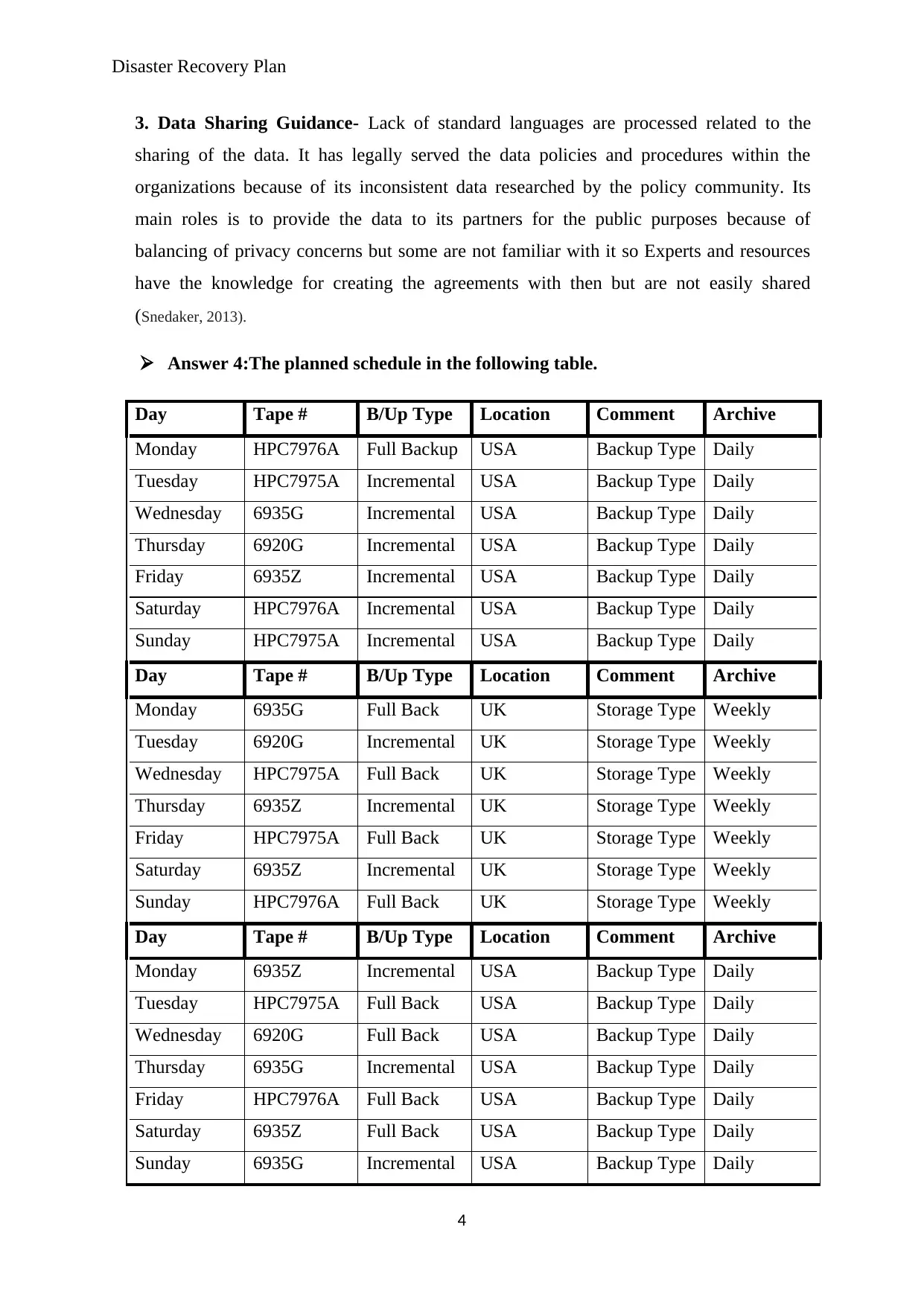
Answer 4:The planned schedule in the following table.
Day Tape # B/Up Type Location Comment Archive
Monday HPC7976A Full Backup USA Backup Type Daily
Tuesday HPC7975A Incremental USA Backup Type Daily
Wednesday 6935G Incremental USA Backup Type Daily
Thursday 6920G Incremental USA Backup Type Daily
Friday 6935Z Incremental USA Backup Type Daily
Saturday HPC7976A Incremental USA Backup Type Daily
Sunday HPC7975A Incremental USA Backup Type Daily
Day Tape # B/Up Type Location Comment Archive
Monday 6935G Full Back UK Storage Type Weekly
Tuesday 6920G Incremental UK Storage Type Weekly
Wednesday HPC7975A Full Back UK Storage Type Weekly
Thursday 6935Z Incremental UK Storage Type Weekly
Friday HPC7975A Full Back UK Storage Type Weekly
Saturday 6935Z Incremental UK Storage Type Weekly
Sunday HPC7976A Full Back UK Storage Type Weekly
Day Tape # B/Up Type Location Comment Archive
Monday 6935Z Incremental USA Backup Type Daily
Tuesday HPC7975A Full Back USA Backup Type Daily
Wednesday 6920G Full Back USA Backup Type Daily
Thursday 6935G Incremental USA Backup Type Daily
Friday HPC7976A Full Back USA Backup Type Daily
Saturday 6935Z Full Back USA Backup Type Daily
Sunday 6935G Incremental USA Backup Type Daily
4
3. Data Sharing Guidance- Lack of standard languages are processed related to the
sharing of the data. It has legally served the data policies and procedures within the
organizations because of its inconsistent data researched by the policy community. Its
main roles is to provide the data to its partners for the public purposes because of
balancing of privacy concerns but some are not familiar with it so Experts and resources
have the knowledge for creating the agreements with then but are not easily shared
(Snedaker, 2013).
Answer 4:The planned schedule in the following table.
Day Tape # B/Up Type Location Comment Archive
Monday HPC7976A Full Backup USA Backup Type Daily
Tuesday HPC7975A Incremental USA Backup Type Daily
Wednesday 6935G Incremental USA Backup Type Daily
Thursday 6920G Incremental USA Backup Type Daily
Friday 6935Z Incremental USA Backup Type Daily
Saturday HPC7976A Incremental USA Backup Type Daily
Sunday HPC7975A Incremental USA Backup Type Daily
Day Tape # B/Up Type Location Comment Archive
Monday 6935G Full Back UK Storage Type Weekly
Tuesday 6920G Incremental UK Storage Type Weekly
Wednesday HPC7975A Full Back UK Storage Type Weekly
Thursday 6935Z Incremental UK Storage Type Weekly
Friday HPC7975A Full Back UK Storage Type Weekly
Saturday 6935Z Incremental UK Storage Type Weekly
Sunday HPC7976A Full Back UK Storage Type Weekly
Day Tape # B/Up Type Location Comment Archive
Monday 6935Z Incremental USA Backup Type Daily
Tuesday HPC7975A Full Back USA Backup Type Daily
Wednesday 6920G Full Back USA Backup Type Daily
Thursday 6935G Incremental USA Backup Type Daily
Friday HPC7976A Full Back USA Backup Type Daily
Saturday 6935Z Full Back USA Backup Type Daily
Sunday 6935G Incremental USA Backup Type Daily
4
Disaster Recovery Plan
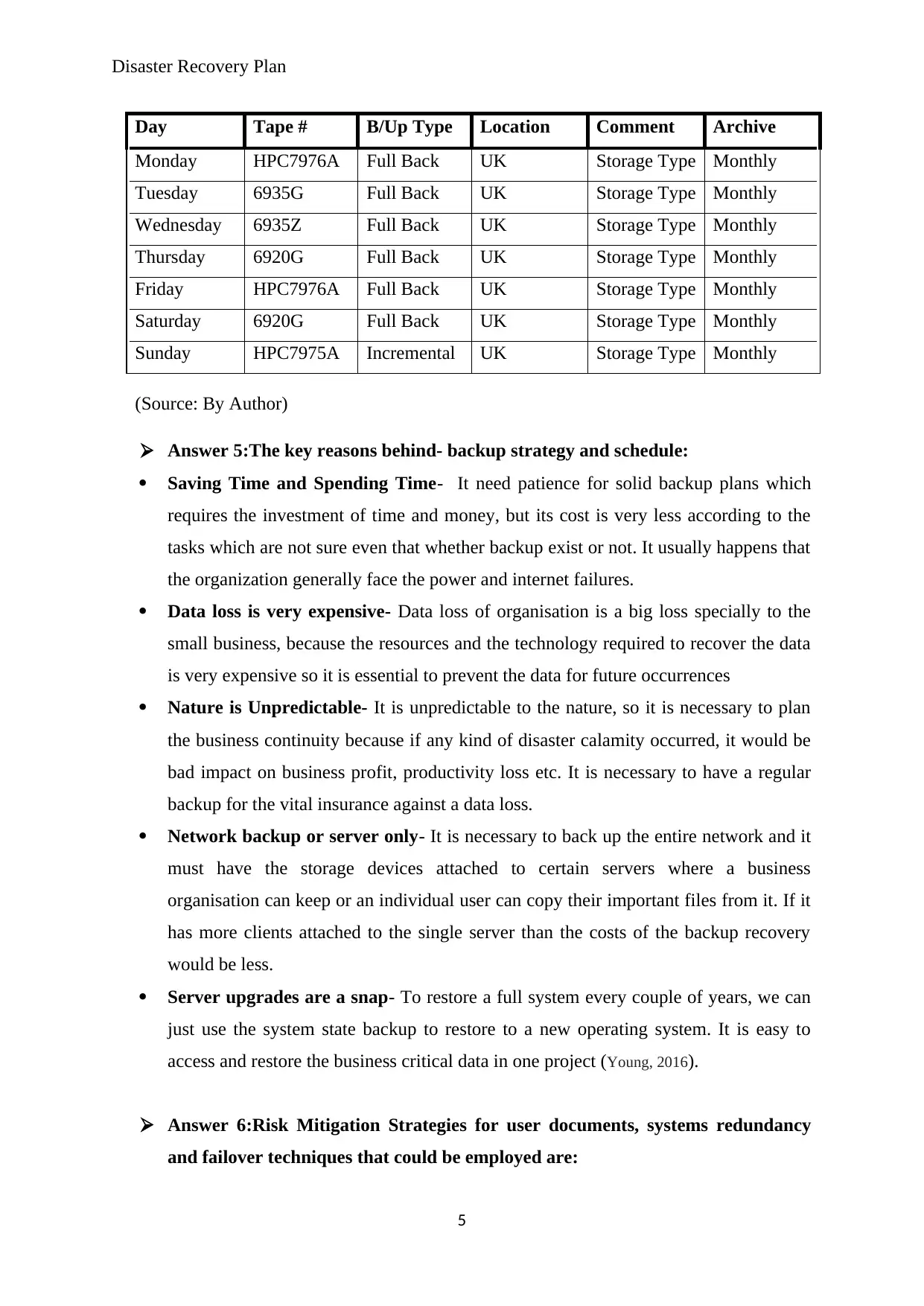
Day Tape # B/Up Type Location Comment Archive
Monday HPC7976A Full Back UK Storage Type Monthly
Tuesday 6935G Full Back UK Storage Type Monthly
Wednesday 6935Z Full Back UK Storage Type Monthly
Thursday 6920G Full Back UK Storage Type Monthly
Friday HPC7976A Full Back UK Storage Type Monthly
Saturday 6920G Full Back UK Storage Type Monthly
Sunday HPC7975A Incremental UK Storage Type Monthly
(Source: By Author)
Answer 5:The key reasons behind- backup strategy and schedule:
Saving Time and Spending Time- It need patience for solid backup plans which
requires the investment of time and money, but its cost is very less according to the
tasks which are not sure even that whether backup exist or not. It usually happens that
the organization generally face the power and internet failures.
Data loss is very expensive- Data loss of organisation is a big loss specially to the
small business, because the resources and the technology required to recover the data
is very expensive so it is essential to prevent the data for future occurrences
Nature is Unpredictable- It is unpredictable to the nature, so it is necessary to plan
the business continuity because if any kind of disaster calamity occurred, it would be
bad impact on business profit, productivity loss etc. It is necessary to have a regular
backup for the vital insurance against a data loss.
Network backup or server only- It is necessary to back up the entire network and it
must have the storage devices attached to certain servers where a business
organisation can keep or an individual user can copy their important files from it. If it
has more clients attached to the single server than the costs of the backup recovery
would be less.
Server upgrades are a snap- To restore a full system every couple of years, we can
just use the system state backup to restore to a new operating system. It is easy to
access and restore the business critical data in one project (Young, 2016).
Answer 6:Risk Mitigation Strategies for user documents, systems redundancy
and failover techniques that could be employed are:
5
Day Tape # B/Up Type Location Comment Archive
Monday HPC7976A Full Back UK Storage Type Monthly
Tuesday 6935G Full Back UK Storage Type Monthly
Wednesday 6935Z Full Back UK Storage Type Monthly
Thursday 6920G Full Back UK Storage Type Monthly
Friday HPC7976A Full Back UK Storage Type Monthly
Saturday 6920G Full Back UK Storage Type Monthly
Sunday HPC7975A Incremental UK Storage Type Monthly
(Source: By Author)
Answer 5:The key reasons behind- backup strategy and schedule:
Saving Time and Spending Time- It need patience for solid backup plans which
requires the investment of time and money, but its cost is very less according to the
tasks which are not sure even that whether backup exist or not. It usually happens that
the organization generally face the power and internet failures.
Data loss is very expensive- Data loss of organisation is a big loss specially to the
small business, because the resources and the technology required to recover the data
is very expensive so it is essential to prevent the data for future occurrences
Nature is Unpredictable- It is unpredictable to the nature, so it is necessary to plan
the business continuity because if any kind of disaster calamity occurred, it would be
bad impact on business profit, productivity loss etc. It is necessary to have a regular
backup for the vital insurance against a data loss.
Network backup or server only- It is necessary to back up the entire network and it
must have the storage devices attached to certain servers where a business
organisation can keep or an individual user can copy their important files from it. If it
has more clients attached to the single server than the costs of the backup recovery
would be less.
Server upgrades are a snap- To restore a full system every couple of years, we can
just use the system state backup to restore to a new operating system. It is easy to
access and restore the business critical data in one project (Young, 2016).
Answer 6:Risk Mitigation Strategies for user documents, systems redundancy
and failover techniques that could be employed are:
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Disaster Recovery Plan
1. Reasonableness- A Company need not to manage every possible risk just because not
all the risk is reasonable to manage. It is basically the test that can be applied to
determine whether the risk can be controlled. It is derived from the reasonable person
standard in law.
2. Balancing Risk and Cost-The cost charge to manage or control the risk must be
balanced against the impact value. The cost is basically balanced according to its
actual monetary values if they are available. While there is another form to balance
the costs using relative values such as low, medium and high (Strong and, 2011).
3. Role-based Perceptions of Risk-In personnel not all the ideal people will understand
the threat to a company’s if risk is not managed. One of the most challenging tasks
with the effective risk management is to achieve a proper balance between the
security and usability.
4. Balanced security and Usability- One of the challenging task with effective risk
management is to achieve a proper balancing of system usability and security.
5. Risk Identification Techniques- It is basically to learn and identify the risks
occurred. Losses are occurred generally when the threat exposes vulnerability. There
are 3 steps:
Identify Threats
Identification of vulnerabilities
Calculate the Livelihood of a threat
References
Cook, J., 2015. A six-stage business continuity and disaster recovery planning cycle. SAM
Advanced Management Journal, 80(3), p.23.
6
1. Reasonableness- A Company need not to manage every possible risk just because not
all the risk is reasonable to manage. It is basically the test that can be applied to
determine whether the risk can be controlled. It is derived from the reasonable person
standard in law.
2. Balancing Risk and Cost-The cost charge to manage or control the risk must be
balanced against the impact value. The cost is basically balanced according to its
actual monetary values if they are available. While there is another form to balance
the costs using relative values such as low, medium and high (Strong and, 2011).
3. Role-based Perceptions of Risk-In personnel not all the ideal people will understand
the threat to a company’s if risk is not managed. One of the most challenging tasks
with the effective risk management is to achieve a proper balance between the
security and usability.
4. Balanced security and Usability- One of the challenging task with effective risk
management is to achieve a proper balancing of system usability and security.
5. Risk Identification Techniques- It is basically to learn and identify the risks
occurred. Losses are occurred generally when the threat exposes vulnerability. There
are 3 steps:
Identify Threats
Identification of vulnerabilities
Calculate the Livelihood of a threat
References
Cook, J., 2015. A six-stage business continuity and disaster recovery planning cycle. SAM
Advanced Management Journal, 80(3), p.23.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Disaster Recovery Plan
Haddow, G., Bullock, J. and Coppola, D.P., 2017. Introduction to emergency management.
Butterworth-Heinemann.
Johnson, L.A. and Mamula-Seadon, L., 2014. Transforming governance: how national
policies and organizations for managing disaster recovery evolved following the 4 September
2010 and 22 February 2011 Canterbury earthquakes. Earthquake Spectra, 30(1), pp.577-605.
Phillips, B.D., 2015. Disaster recovery. CRC press.
Sahebjamnia, N., Torabi, S.A. and Mansouri, S.A., 2015. Integrated business continuity and
disaster recovery planning: Towards organizational resilience. European Journal of
Operational Research, 242(1), pp.261-273.
Snedaker, S., 2013. Business continuity and disaster recovery planning for IT professionals.
Newnes.
Strong C. K and Shane S. J, 2011. RISK MITIGATION STRATEGIES FOR OPERATIONS
AND MAINTENANCE ACTIVITIES. Available at: http://www.intrans.iastate.edu/reports/tr-
627_risk_mit_w_cvr2.pdf Accessed on:30th August 2017
Young, S., 2016. Disaster Recovery 5 and Business Continuity of SCADA. Handbook of
SCADA/Control Systems Security, p.115
7
Haddow, G., Bullock, J. and Coppola, D.P., 2017. Introduction to emergency management.
Butterworth-Heinemann.
Johnson, L.A. and Mamula-Seadon, L., 2014. Transforming governance: how national
policies and organizations for managing disaster recovery evolved following the 4 September
2010 and 22 February 2011 Canterbury earthquakes. Earthquake Spectra, 30(1), pp.577-605.
Phillips, B.D., 2015. Disaster recovery. CRC press.
Sahebjamnia, N., Torabi, S.A. and Mansouri, S.A., 2015. Integrated business continuity and
disaster recovery planning: Towards organizational resilience. European Journal of
Operational Research, 242(1), pp.261-273.
Snedaker, S., 2013. Business continuity and disaster recovery planning for IT professionals.
Newnes.
Strong C. K and Shane S. J, 2011. RISK MITIGATION STRATEGIES FOR OPERATIONS
AND MAINTENANCE ACTIVITIES. Available at: http://www.intrans.iastate.edu/reports/tr-
627_risk_mit_w_cvr2.pdf Accessed on:30th August 2017
Young, S., 2016. Disaster Recovery 5 and Business Continuity of SCADA. Handbook of
SCADA/Control Systems Security, p.115
7
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





