Research Proposal: Analyzing Security Challenges of IoT Devices
VerifiedAdded on 2022/11/26
|12
|4267
|74
Project
AI Summary
This dissertation proposal investigates the security challenges of Internet of Things (IoT) devices from both customer and vendor perspectives. The research aims to analyze the security and privacy threats associated with IoT, including vulnerabilities, viruses, and hacking. The study seeks to address key research questions such as the security of IoT devices, vendor responsibilities, and potential countermeasures. The proposal outlines the research methodology, including qualitative data collection through semi-structured interviews and online surveys. The research will involve interviews with IoT device vendors and users. The study will employ a qualitative approach using semi-structured interviews and surveys to gather data. The project aims to provide insights into the security challenges and offer solutions to enhance the safety and privacy of IoT devices, contributing to the understanding of security issues in the field of information technology. The study also discusses the importance of the research, its scope, and the novelty of the study in the context of the growing IoT market. The research will also analyze the security challenges of IoT devices and the countermeasures that are available to deal with the security challenges. The research will be conducted in-depth with the use of structured interview questions targeting interviewees of 18 years and above of age that uses (customers) IoT devices and the vendors of the IoT of devices.
Dissertation Proposal Form
Student Name Supervisor
Name
Student
Number
Course
Project title: Analyzing The Security Challenges of IoT Devices
Start and end
dates of
research:
06/01/2020-14/05/2020
Proposed activity – aims, objectives, research question(s), and state how it
is novel (max 600 words
Introduction.
The term Internet of Things was first used by Kevin Ashton in 1998 at the MIT
Auto-ID Centre (Ashton, 2009). The Internet of Things has the potential to
transform the world. IoT was initially used majorly in the supply change
management sector. The basic knowledge of IoT technology is attaching
embedded gadgets to ordinary objects, making them ‘smart’ devices. There is an
advancement of technology and connecting IoT devices through the internet.
There is also a prediction of connecting IoT devices will furthermore grow (Bonetto
et al. 2012). The notion of connecting physical things to digital platforms is not a
new idea in the technology sector. The development and acceptance of wireless
sensor networks (WSN) and technologies and radio frequency identification (RFID)
have made the IoT more practical. It has grown to become the world’s biggest
growing technology. The number of wireless devices has gone up by 25 billion in
this current year of 2020.
Millions of IoT gadgets need big distributed network systems and also the
procedure of converting raw information into meaningful data. IoT changes the
way people live their life. IoT technology will create an “always connected
paradigm” (Bahekmat et al. 2012). The development in connected devices will
inevitably result in vulnerabilities and security issues “IoT technology has negative
on economic, legal and social aspects. Precisely IoT technologies development has
led to privacy and safety concerns (Thierer, 2015). The IoT technology still at its
Student Name Supervisor
Name
Student
Number
Course
Project title: Analyzing The Security Challenges of IoT Devices
Start and end
dates of
research:
06/01/2020-14/05/2020
Proposed activity – aims, objectives, research question(s), and state how it
is novel (max 600 words
Introduction.
The term Internet of Things was first used by Kevin Ashton in 1998 at the MIT
Auto-ID Centre (Ashton, 2009). The Internet of Things has the potential to
transform the world. IoT was initially used majorly in the supply change
management sector. The basic knowledge of IoT technology is attaching
embedded gadgets to ordinary objects, making them ‘smart’ devices. There is an
advancement of technology and connecting IoT devices through the internet.
There is also a prediction of connecting IoT devices will furthermore grow (Bonetto
et al. 2012). The notion of connecting physical things to digital platforms is not a
new idea in the technology sector. The development and acceptance of wireless
sensor networks (WSN) and technologies and radio frequency identification (RFID)
have made the IoT more practical. It has grown to become the world’s biggest
growing technology. The number of wireless devices has gone up by 25 billion in
this current year of 2020.
Millions of IoT gadgets need big distributed network systems and also the
procedure of converting raw information into meaningful data. IoT changes the
way people live their life. IoT technology will create an “always connected
paradigm” (Bahekmat et al. 2012). The development in connected devices will
inevitably result in vulnerabilities and security issues “IoT technology has negative
on economic, legal and social aspects. Precisely IoT technologies development has
led to privacy and safety concerns (Thierer, 2015). The IoT technology still at its
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
initial early stages, and the security and privacy threats have yet to be fully
investigated and mitigated. Companies such as Apple and Microsoft have also
faced security challenges, during the use of IoT devices. Therefore, the papers will
try to analyze the security and privacy threats from the vendors’ perspective (Ingla
& Sachdeva,2013).
The advancement of IoT technology and the interconnection of IoT devices is
leading to the raising of vulnerabilities and compromising the systems such as
viruses, hackers and other forms of attacks. These IoT technologies have got a lot
of challenges arising from them such as security, safety, and privacy (Thierer,
2015). There is a need to analyze the security issue over the challenges the IoT
devices are at present facing.
Aims of this Research
This research aim is to look at the customers’ privacy and security issues when
using IoT gadgets. It is an important matter in both the business and academic
sectors presently. The other study components presented emphasizes on these
main questions:
Which are some of the most popular IoT devices customers that use most
and what are the major security concern of their services?
Are customers aware of private data they share at the moment they are
using Internet of Things devices?
What are the general security views of the IoT devices?
Do customers have any security views on the threats in using Internet of
Things devices?
The Objective of the current
The objective of the current research is to give an overview of the security and
privacy apprehensions of the Internet of Things and what security needs to be
considered from the vendor’s perspective to deliver a safe and secure Internet of
Things devices to customers.
Research Questions
investigated and mitigated. Companies such as Apple and Microsoft have also
faced security challenges, during the use of IoT devices. Therefore, the papers will
try to analyze the security and privacy threats from the vendors’ perspective (Ingla
& Sachdeva,2013).
The advancement of IoT technology and the interconnection of IoT devices is
leading to the raising of vulnerabilities and compromising the systems such as
viruses, hackers and other forms of attacks. These IoT technologies have got a lot
of challenges arising from them such as security, safety, and privacy (Thierer,
2015). There is a need to analyze the security issue over the challenges the IoT
devices are at present facing.
Aims of this Research
This research aim is to look at the customers’ privacy and security issues when
using IoT gadgets. It is an important matter in both the business and academic
sectors presently. The other study components presented emphasizes on these
main questions:
Which are some of the most popular IoT devices customers that use most
and what are the major security concern of their services?
Are customers aware of private data they share at the moment they are
using Internet of Things devices?
What are the general security views of the IoT devices?
Do customers have any security views on the threats in using Internet of
Things devices?
The Objective of the current
The objective of the current research is to give an overview of the security and
privacy apprehensions of the Internet of Things and what security needs to be
considered from the vendor’s perspective to deliver a safe and secure Internet of
Things devices to customers.
Research Questions

The following primary research question will be surveyed in this study:
1. Are IoT devices secure to be used by the customer of the internet of things
technology?
2. What can the vendor provide safe and secure IoT devices for customers?
3. What are the presently known countermeasures to secure Internet of Things
devices?
4. Will safety and Privacy challenges stop on the use of IoT devices by
customers?
Importance of the Study
The internet of things is one of the new and emerging concepts of research in the
arena of information technology. The Internet of Things enables the
interconnection of devices or nodes to each other and sharing of information
globally (Dijkman 2015). This topic is interesting, and it shall require a researcher
to explore the new and emerging terms of the internet of things.
This research proposal is focusing on the security challenges of the Internet of
Things device, and this research believes security issues have huge concerns in
the field of information technology (Woods 2016). Carrying out this research shall
enable customers and vendors of the internet of things to understand more of the
security challenges of the internet of things and countermeasures available of
dealing with the security challenges.
This report shall address the security challenges of the Internet of Things devices
when the security of IoT has been compromised the cost of security in the annual
budget of security increases by 20%. Security of the IoT is one of the top priorities
of the companies that intend to adopt the IoT technologies in their operations.
This proposal is on how the analysis of security challenges is vital in the education
1. Are IoT devices secure to be used by the customer of the internet of things
technology?
2. What can the vendor provide safe and secure IoT devices for customers?
3. What are the presently known countermeasures to secure Internet of Things
devices?
4. Will safety and Privacy challenges stop on the use of IoT devices by
customers?
Importance of the Study
The internet of things is one of the new and emerging concepts of research in the
arena of information technology. The Internet of Things enables the
interconnection of devices or nodes to each other and sharing of information
globally (Dijkman 2015). This topic is interesting, and it shall require a researcher
to explore the new and emerging terms of the internet of things.
This research proposal is focusing on the security challenges of the Internet of
Things device, and this research believes security issues have huge concerns in
the field of information technology (Woods 2016). Carrying out this research shall
enable customers and vendors of the internet of things to understand more of the
security challenges of the internet of things and countermeasures available of
dealing with the security challenges.
This report shall address the security challenges of the Internet of Things devices
when the security of IoT has been compromised the cost of security in the annual
budget of security increases by 20%. Security of the IoT is one of the top priorities
of the companies that intend to adopt the IoT technologies in their operations.
This proposal is on how the analysis of security challenges is vital in the education
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
and industrial sectors. Also, it is one of the limited qualitative studies to be done
and security challenges on devices.
According to the prediction of the International Data Corporation (IDC), All of the major
vendors in the technology sector, for example, Apple, Microsoft, IBM, and Google
are venturing in this developing marketplace and are predicted to grow up to $235
billion in the coming years (MacGillivray & Vernon, 2015).
The Scope of the study
The research is to be conducted in-depth with the use of structured interview
questions targeting interviewees of 18 years and above of age that uses
(customers) IoT devices and the vendors of the IoT of devices. The survey is also
going to be conducted on social media targeting users of IoT of devices. This
research proposal particularly focuses on the security challenges facing while
using or interacting with IoT technology. The inductive method shall be used to
analyze the interview data.
The Novelty of the study.
The Internet of Things is one of new, growing, and emerging concepts in the
information technology field and little research has been done on it (Tang et al.
2014). This topic is an interesting topic that needs detailed research to be done in
it, and the research can be beneficial to organizations such as Microsoft, Google,
and Apple that embrace the advancement of the internet of things technology.
This report shall discuss advancement achieved through the use of IoT and its
impact on the participants.
This research shall be equipped with facts obtained after surveying on security
challenges and provide a solution on how to solve these security issues arising
through the use of the internet of things technology.
Methodology – rationale, data selection and collection, recruitment, participant
demographics, analytical process (max 600 words)
This section shall review the research design deeply, Area of study, targeted
population, the sample size, sampling methods, data gathering and data analysis
and security challenges on devices.
According to the prediction of the International Data Corporation (IDC), All of the major
vendors in the technology sector, for example, Apple, Microsoft, IBM, and Google
are venturing in this developing marketplace and are predicted to grow up to $235
billion in the coming years (MacGillivray & Vernon, 2015).
The Scope of the study
The research is to be conducted in-depth with the use of structured interview
questions targeting interviewees of 18 years and above of age that uses
(customers) IoT devices and the vendors of the IoT of devices. The survey is also
going to be conducted on social media targeting users of IoT of devices. This
research proposal particularly focuses on the security challenges facing while
using or interacting with IoT technology. The inductive method shall be used to
analyze the interview data.
The Novelty of the study.
The Internet of Things is one of new, growing, and emerging concepts in the
information technology field and little research has been done on it (Tang et al.
2014). This topic is an interesting topic that needs detailed research to be done in
it, and the research can be beneficial to organizations such as Microsoft, Google,
and Apple that embrace the advancement of the internet of things technology.
This report shall discuss advancement achieved through the use of IoT and its
impact on the participants.
This research shall be equipped with facts obtained after surveying on security
challenges and provide a solution on how to solve these security issues arising
through the use of the internet of things technology.
Methodology – rationale, data selection and collection, recruitment, participant
demographics, analytical process (max 600 words)
This section shall review the research design deeply, Area of study, targeted
population, the sample size, sampling methods, data gathering and data analysis
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
methods to be used in this study. This section demonstrates all the steps that are
being taken by the researcher during the extraction of the information from the
interviewees.
This section shall answer the research question through demonstration of the
research techniques to be used and justification of those techniques.
This section explains the way research is to be conducted and in what manner
data is to be collected.
This section shall also explain in detailed the research approaches that are going
to be used.
Rationale.
The literary review shall highlight IoT technology as a new and growing concept in
the field of information technology. The challenges of IoT technologies are facing
are security issues. There is a need to carry out research and collect information
about the thoughts, opinions, and experiences of vendors who develop the IoT
devices and consumers who use IoT devices.
This proposal is to be designed to identify the users’ opinions about security
challenges while operating or interacting with IoT devices.
A lot of research approaches have been proposed in this research such as
qualitative and quantitative. Still, there is a clear indication there are few
qualitative kinds of research carried out on security challenges on IoT devices.
Therefore, there are very few qualitative data, and there is a need to explore more
research about this qualitative approach.
This research suggests that an individual’s view on the security challenges is
completely different from other people’s views (Weber, 2004). So, every person
has to provide their individual opinions about security issues.
There is no way we can prove people’s feelings, opinions and views towards
security challenges of the IoT technologies, and the best way is to carry research
using the qualitative approach.
being taken by the researcher during the extraction of the information from the
interviewees.
This section shall answer the research question through demonstration of the
research techniques to be used and justification of those techniques.
This section explains the way research is to be conducted and in what manner
data is to be collected.
This section shall also explain in detailed the research approaches that are going
to be used.
Rationale.
The literary review shall highlight IoT technology as a new and growing concept in
the field of information technology. The challenges of IoT technologies are facing
are security issues. There is a need to carry out research and collect information
about the thoughts, opinions, and experiences of vendors who develop the IoT
devices and consumers who use IoT devices.
This proposal is to be designed to identify the users’ opinions about security
challenges while operating or interacting with IoT devices.
A lot of research approaches have been proposed in this research such as
qualitative and quantitative. Still, there is a clear indication there are few
qualitative kinds of research carried out on security challenges on IoT devices.
Therefore, there are very few qualitative data, and there is a need to explore more
research about this qualitative approach.
This research suggests that an individual’s view on the security challenges is
completely different from other people’s views (Weber, 2004). So, every person
has to provide their individual opinions about security issues.
There is no way we can prove people’s feelings, opinions and views towards
security challenges of the IoT technologies, and the best way is to carry research
using the qualitative approach.

Data collection.
This research shall adopt the qualitative approach through the use of semi-
structured interviews to collect data. The interview questions shall focus mainly on
security assessments of the Internet of Things technologies from users. The pilot
study shall be conducted through the usage of the Survey Monkey platform
targeting users who own and uses IoT devices.
The data is to be collected from May 10th, 2020 to May15th, 2020. Start the
research on the collection of data.
Recruitment and participant.
The participants for this research are the vendors of IoT devices companies such
as Microsoft, Google, Apple and customer of the IoT devices. The vendor
participants are the developers of IoT devices. The vendor participants shall be
recruited from the Microsoft, Google and Apple companies’ official websites. The
customer participants are recruited from social media platforms such as Facebook,
Instagram, and Twitter. The customer participants are to be aware of IoT
technology and the owner or user of IoT devices. The customer participants from
social media are recruited basing on the understanding of IoT technologies and the
use of IoT devices. The researcher shall select the participant randomly with the
use of the summary letter explaining the purpose and objective of carrying out the
research. The researcher will inform participants that contribution is optional and
has no monetary value. The participant will accept the offer by writing an
acceptance letter acknowledging participation in research. Then interviews can be
agreed on a specific date for an interview to be conducted. All participants have to
consent before carrying out any research.
Analytics process.
The twitter analytics tool is going to be used to analyses people’s views, opinions
and experience about the security challenge users of IoT devices are facing
(Farooq et al. 2015). The data from the interviews shall also be analyzed to obtain
This research shall adopt the qualitative approach through the use of semi-
structured interviews to collect data. The interview questions shall focus mainly on
security assessments of the Internet of Things technologies from users. The pilot
study shall be conducted through the usage of the Survey Monkey platform
targeting users who own and uses IoT devices.
The data is to be collected from May 10th, 2020 to May15th, 2020. Start the
research on the collection of data.
Recruitment and participant.
The participants for this research are the vendors of IoT devices companies such
as Microsoft, Google, Apple and customer of the IoT devices. The vendor
participants are the developers of IoT devices. The vendor participants shall be
recruited from the Microsoft, Google and Apple companies’ official websites. The
customer participants are recruited from social media platforms such as Facebook,
Instagram, and Twitter. The customer participants are to be aware of IoT
technology and the owner or user of IoT devices. The customer participants from
social media are recruited basing on the understanding of IoT technologies and the
use of IoT devices. The researcher shall select the participant randomly with the
use of the summary letter explaining the purpose and objective of carrying out the
research. The researcher will inform participants that contribution is optional and
has no monetary value. The participant will accept the offer by writing an
acceptance letter acknowledging participation in research. Then interviews can be
agreed on a specific date for an interview to be conducted. All participants have to
consent before carrying out any research.
Analytics process.
The twitter analytics tool is going to be used to analyses people’s views, opinions
and experience about the security challenge users of IoT devices are facing
(Farooq et al. 2015). The data from the interviews shall also be analyzed to obtain
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
useful information.
Research Strategy
The semi-structured interviews and surveys are the appropriate strategies for this
research.
This research shall adopt a qualitative method of using semi-structured interviews
to gather data and use online surveys to get opinions and views from the
participants.
The guiding questions are set before conducting the interview and used to carry
out in-depth findings while discussing with the participant.
The survey applies in the present case, and it is generally linking with deductive
study, which is a suitable plan for responding to the research inquiries. The Survey
study involves collecting data from the sample of individuals through replying to
survey questions.
Sample Population
This study shall involve interviewing twenty participants; ten of the participants
shall be from vendors of IoT devices company such as Microsoft, Google, and
Apple. These vendors participants are developers that develop the IoT devices and
the remaining ten shall be users (customers) of IoT devices.
The sample audience for this research shall be identified using a qualitative
approach.
The target subjects for this research shall be users (customers) of IoT devices and
vendors of IoT devices companies such as Microsoft, Google, and Apple (vendors
of IoT devices).
Plan of Survey.
The research shall have an overall of 42 questions. The questions shall be
categorized in the units that are fixed on the specific area of interest.
Pilot Survey
The pilot study is defined as a small study where the planning of the survey and
Research Strategy
The semi-structured interviews and surveys are the appropriate strategies for this
research.
This research shall adopt a qualitative method of using semi-structured interviews
to gather data and use online surveys to get opinions and views from the
participants.
The guiding questions are set before conducting the interview and used to carry
out in-depth findings while discussing with the participant.
The survey applies in the present case, and it is generally linking with deductive
study, which is a suitable plan for responding to the research inquiries. The Survey
study involves collecting data from the sample of individuals through replying to
survey questions.
Sample Population
This study shall involve interviewing twenty participants; ten of the participants
shall be from vendors of IoT devices company such as Microsoft, Google, and
Apple. These vendors participants are developers that develop the IoT devices and
the remaining ten shall be users (customers) of IoT devices.
The sample audience for this research shall be identified using a qualitative
approach.
The target subjects for this research shall be users (customers) of IoT devices and
vendors of IoT devices companies such as Microsoft, Google, and Apple (vendors
of IoT devices).
Plan of Survey.
The research shall have an overall of 42 questions. The questions shall be
categorized in the units that are fixed on the specific area of interest.
Pilot Survey
The pilot study is defined as a small study where the planning of the survey and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

applying each measure is verified basing on the people of the study. The goal is to
identify potential challenges of the research, for example, wrong word queries and
issues associated with executions. Priority of issuing the research questions, a
pilot study shall be formed through the usage of the Survey Monkey platform and
offered to 100 contributors to get their feedback.
DATA Analysis.
The data analysis section is the representation of the research result and clarifying
how the planning, examining and understanding of data shall be done. The
research shall be conducted using an online survey on the survey monkey
platform, social media-specific on twitter and interviews as it was initially stated in
the methodology section. The IBM SPSS, twitter analytic tool and Epi Data (version
3.1) shall be used to collect and analyze data during this study.
Data Preparation
The analysis of interview data shall start by the principal researcher inserting the
data into Epi Data (version 3.1) and the use of SPSS to analyse the data. The
preliminary frequency shall be run using the eyeballing technique to choose if any
omitted variables exist. The evaluations of security challenges from interview data
are to be made based on the interviewee’s information. The chi-square test shall
be used to test meaning. The analyzed data will be presented using tables,
graphs, and charts.
The analysis of an online survey from Twitter data shall be done by creating
tweets in the form of questions relating to the security challenges of IoT devices.
Those questions shall be tweeted on twitter, and users or owners of IoT devices on
twitter shall comment, give their views or opinions then twitter analytic tools shall
be used to analyze the data from the survey.
References.
Bahekmat, M., Yaghmaee, M. H., Yazdi, A. S., &Sadeghi, S. (2012). A Novel
Algorithm
For Detecting Sinkhole Attacks in WSNs. IJCTE, 4(3), 418-421
Tang, D, Li, T., J. Ren, and Wu, J.(2014). “Cost-aware Secure routing (CASER)
identify potential challenges of the research, for example, wrong word queries and
issues associated with executions. Priority of issuing the research questions, a
pilot study shall be formed through the usage of the Survey Monkey platform and
offered to 100 contributors to get their feedback.
DATA Analysis.
The data analysis section is the representation of the research result and clarifying
how the planning, examining and understanding of data shall be done. The
research shall be conducted using an online survey on the survey monkey
platform, social media-specific on twitter and interviews as it was initially stated in
the methodology section. The IBM SPSS, twitter analytic tool and Epi Data (version
3.1) shall be used to collect and analyze data during this study.
Data Preparation
The analysis of interview data shall start by the principal researcher inserting the
data into Epi Data (version 3.1) and the use of SPSS to analyse the data. The
preliminary frequency shall be run using the eyeballing technique to choose if any
omitted variables exist. The evaluations of security challenges from interview data
are to be made based on the interviewee’s information. The chi-square test shall
be used to test meaning. The analyzed data will be presented using tables,
graphs, and charts.
The analysis of an online survey from Twitter data shall be done by creating
tweets in the form of questions relating to the security challenges of IoT devices.
Those questions shall be tweeted on twitter, and users or owners of IoT devices on
twitter shall comment, give their views or opinions then twitter analytic tools shall
be used to analyze the data from the survey.
References.
Bahekmat, M., Yaghmaee, M. H., Yazdi, A. S., &Sadeghi, S. (2012). A Novel
Algorithm
For Detecting Sinkhole Attacks in WSNs. IJCTE, 4(3), 418-421
Tang, D, Li, T., J. Ren, and Wu, J.(2014). “Cost-aware Secure routing (CASER)

protocol
design for wireless sensor networks,” IEEE Transactions on Parallel and
Distributed Systems, vol. 26, no. 4, pp. 960–973.
Bonetto, R., Bui, R. Lakkundi, V. Olivereau, A. Serbanati, A. and Rossi, M(2012)
“Secure
communication for smart IoT objects: protocol stacks, use cases and
practical
examples,” in World of Wireless, Mobile and Multimedia Networks
(WoWMoM),
pp. 1–7.
Ingla, A., &Sachdeva, R. (2013). Review on Security Issues and Attacks in Wireless
Sensor
Networks. International Journal of Advanced Research in Computer
Science and
Software Engineering, 3(4), 529-534.
Farooq, M., Waseem, M.., Khairi, A., & Mazhar, S. (2015). A Critical Analysis of the
Security
Concerns of the Internet of Things (IoT). International Journal of Computer
Applications, 1-6
Kajaree, D. and Behera, R. (2017) “A Survey on IoT Security Threats and
Solutions,” International
Journal of Innovative Research in Computer and Communication
Engineering,
vol. 5, no. 2, pp. 1302–1309.
Andersen, R. (2016) Security Engineering: A guide to building dependable
distributed systems.
2nd Ed, Wiley,
Schneier, B. (2016). Security Engineering. (5th Ed) Pearson.
design for wireless sensor networks,” IEEE Transactions on Parallel and
Distributed Systems, vol. 26, no. 4, pp. 960–973.
Bonetto, R., Bui, R. Lakkundi, V. Olivereau, A. Serbanati, A. and Rossi, M(2012)
“Secure
communication for smart IoT objects: protocol stacks, use cases and
practical
examples,” in World of Wireless, Mobile and Multimedia Networks
(WoWMoM),
pp. 1–7.
Ingla, A., &Sachdeva, R. (2013). Review on Security Issues and Attacks in Wireless
Sensor
Networks. International Journal of Advanced Research in Computer
Science and
Software Engineering, 3(4), 529-534.
Farooq, M., Waseem, M.., Khairi, A., & Mazhar, S. (2015). A Critical Analysis of the
Security
Concerns of the Internet of Things (IoT). International Journal of Computer
Applications, 1-6
Kajaree, D. and Behera, R. (2017) “A Survey on IoT Security Threats and
Solutions,” International
Journal of Innovative Research in Computer and Communication
Engineering,
vol. 5, no. 2, pp. 1302–1309.
Andersen, R. (2016) Security Engineering: A guide to building dependable
distributed systems.
2nd Ed, Wiley,
Schneier, B. (2016). Security Engineering. (5th Ed) Pearson.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Ashton, K. (2009). "That ‘Internet of Things’ thing." RFID Journal: 97-114.
Thierer, A. D. (2015). "The Internet of Things and wearable technology:
Addressing privacy
and security concerns without derailing innovation." Adam Thierer, The
Internet of
Things and Wearable Technology: Addressing Privacy and Security
Concerns without
Derailing innovation.
Dijkman, R. (2015). "Business models for the Internet of Things." International
Journal of
Information Management 35(6): 672-678.
MacGillivray, C. and Vernon, T. (2015). "Worldwide Internet of Things Forecast
2015–2020."
From http://www.idc.com/getdoc.jsp?containerId=256397.
Woods, V. (2016). "Gartner Press Release."
From http://www.gartner.com/newsroom/id/3185623
Weber, R. (2004). "Editor's comments: the rhetoric of positivism versus
interpretivism:
A personal view." MIS Quarterly: iii-xii.
MacGillivray, C. &Vernon, T. (2015). "Worldwide Internet of Things Forecast 2015–
2020." from
http://www.idc.com/getdoc.jsp?containerId=256397.
Project management (max 350 words)
Table: Project timeline and key outputs
Thierer, A. D. (2015). "The Internet of Things and wearable technology:
Addressing privacy
and security concerns without derailing innovation." Adam Thierer, The
Internet of
Things and Wearable Technology: Addressing Privacy and Security
Concerns without
Derailing innovation.
Dijkman, R. (2015). "Business models for the Internet of Things." International
Journal of
Information Management 35(6): 672-678.
MacGillivray, C. and Vernon, T. (2015). "Worldwide Internet of Things Forecast
2015–2020."
From http://www.idc.com/getdoc.jsp?containerId=256397.
Woods, V. (2016). "Gartner Press Release."
From http://www.gartner.com/newsroom/id/3185623
Weber, R. (2004). "Editor's comments: the rhetoric of positivism versus
interpretivism:
A personal view." MIS Quarterly: iii-xii.
MacGillivray, C. &Vernon, T. (2015). "Worldwide Internet of Things Forecast 2015–
2020." from
http://www.idc.com/getdoc.jsp?containerId=256397.
Project management (max 350 words)
Table: Project timeline and key outputs
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
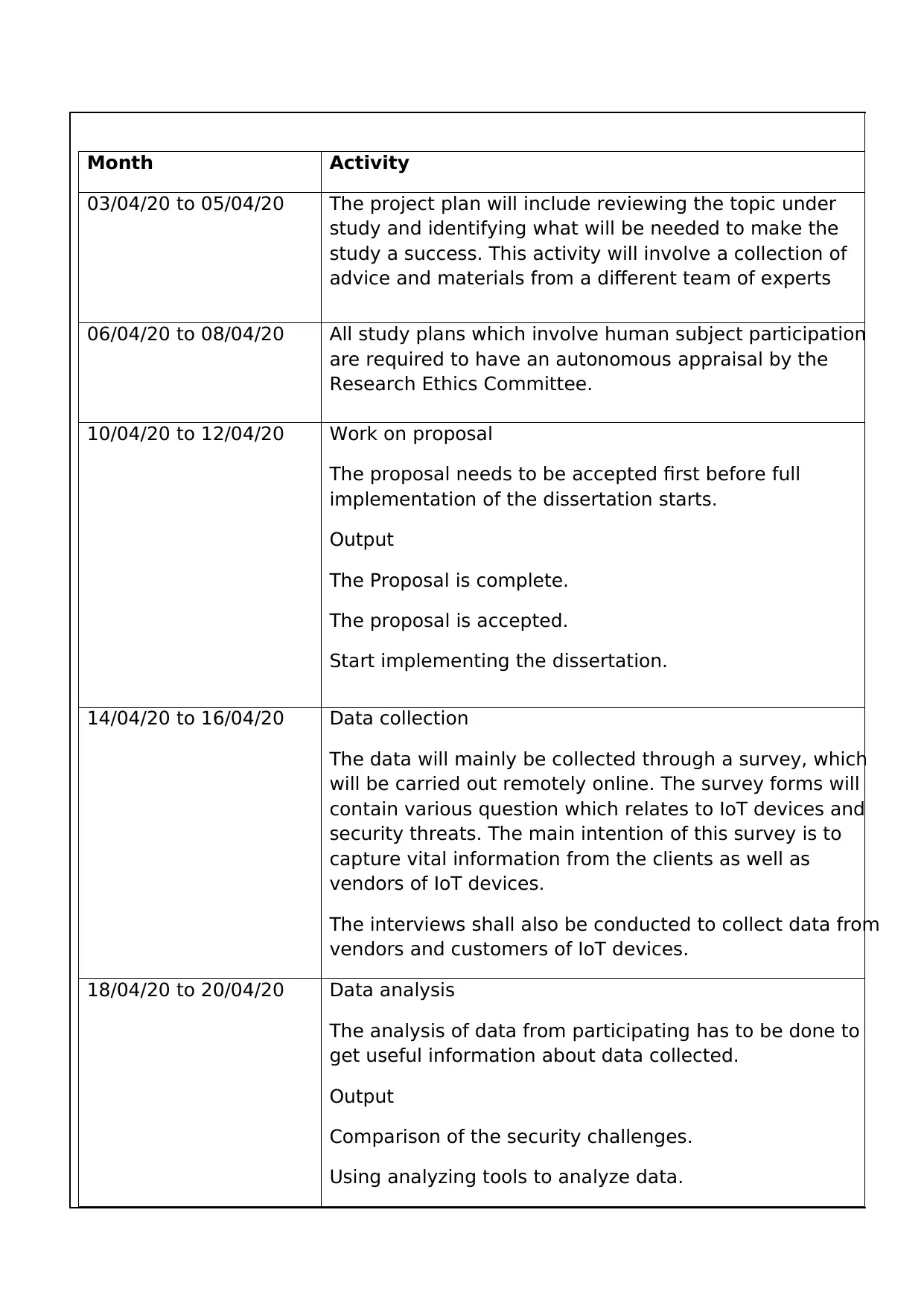
Month Activity
03/04/20 to 05/04/20 The project plan will include reviewing the topic under
study and identifying what will be needed to make the
study a success. This activity will involve a collection of
advice and materials from a different team of experts
06/04/20 to 08/04/20 All study plans which involve human subject participation
are required to have an autonomous appraisal by the
Research Ethics Committee.
10/04/20 to 12/04/20 Work on proposal
The proposal needs to be accepted first before full
implementation of the dissertation starts.
Output
The Proposal is complete.
The proposal is accepted.
Start implementing the dissertation.
14/04/20 to 16/04/20 Data collection
The data will mainly be collected through a survey, which
will be carried out remotely online. The survey forms will
contain various question which relates to IoT devices and
security threats. The main intention of this survey is to
capture vital information from the clients as well as
vendors of IoT devices.
The interviews shall also be conducted to collect data from
vendors and customers of IoT devices.
18/04/20 to 20/04/20 Data analysis
The analysis of data from participating has to be done to
get useful information about data collected.
Output
Comparison of the security challenges.
Using analyzing tools to analyze data.
03/04/20 to 05/04/20 The project plan will include reviewing the topic under
study and identifying what will be needed to make the
study a success. This activity will involve a collection of
advice and materials from a different team of experts
06/04/20 to 08/04/20 All study plans which involve human subject participation
are required to have an autonomous appraisal by the
Research Ethics Committee.
10/04/20 to 12/04/20 Work on proposal
The proposal needs to be accepted first before full
implementation of the dissertation starts.
Output
The Proposal is complete.
The proposal is accepted.
Start implementing the dissertation.
14/04/20 to 16/04/20 Data collection
The data will mainly be collected through a survey, which
will be carried out remotely online. The survey forms will
contain various question which relates to IoT devices and
security threats. The main intention of this survey is to
capture vital information from the clients as well as
vendors of IoT devices.
The interviews shall also be conducted to collect data from
vendors and customers of IoT devices.
18/04/20 to 20/04/20 Data analysis
The analysis of data from participating has to be done to
get useful information about data collected.
Output
Comparison of the security challenges.
Using analyzing tools to analyze data.
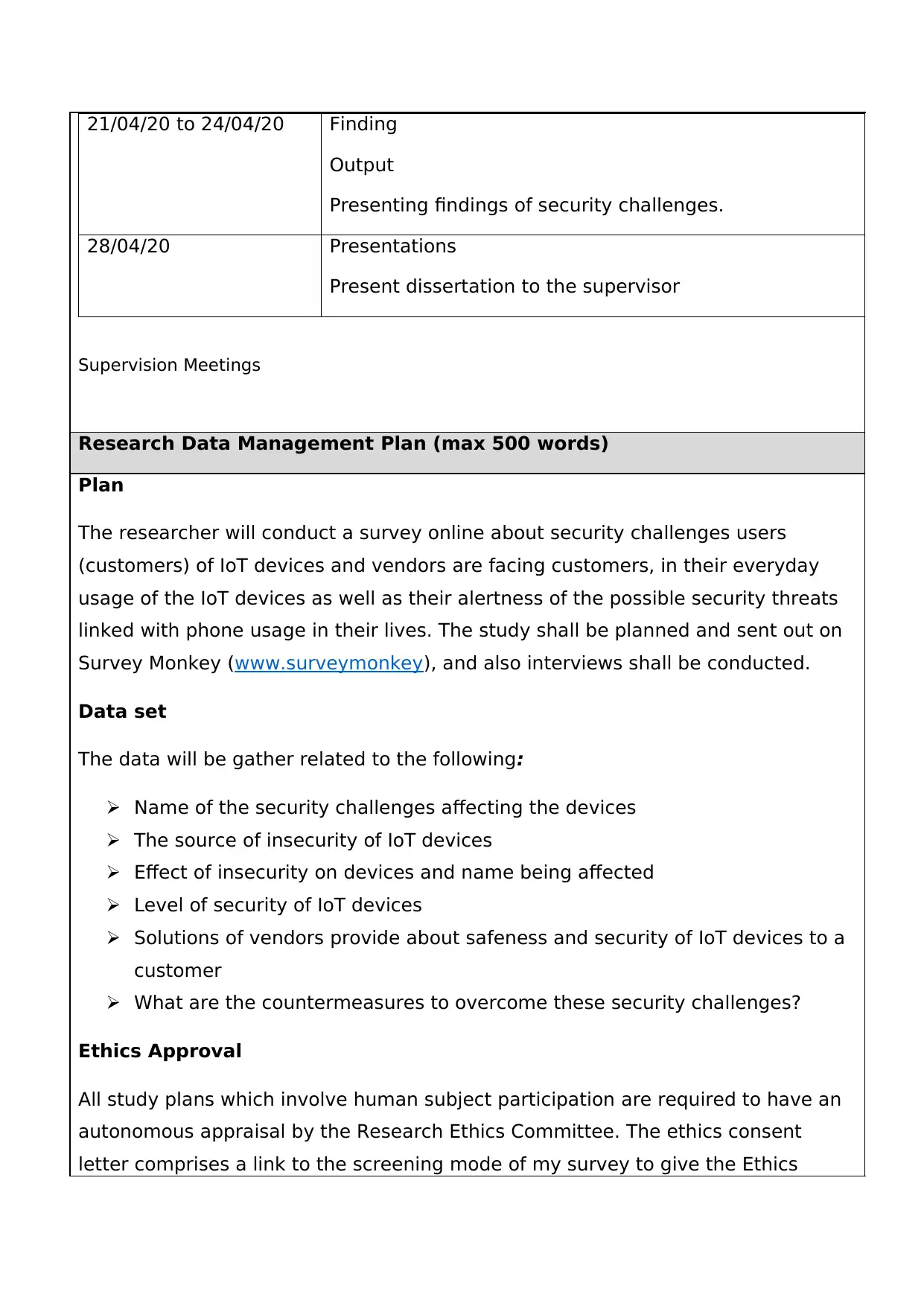
21/04/20 to 24/04/20 Finding
Output
Presenting findings of security challenges.
28/04/20 Presentations
Present dissertation to the supervisor
Supervision Meetings
Research Data Management Plan (max 500 words)
Plan
The researcher will conduct a survey online about security challenges users
(customers) of IoT devices and vendors are facing customers, in their everyday
usage of the IoT devices as well as their alertness of the possible security threats
linked with phone usage in their lives. The study shall be planned and sent out on
Survey Monkey (www.surveymonkey), and also interviews shall be conducted.
Data set
The data will be gather related to the following:
Name of the security challenges affecting the devices
The source of insecurity of IoT devices
Effect of insecurity on devices and name being affected
Level of security of IoT devices
Solutions of vendors provide about safeness and security of IoT devices to a
customer
What are the countermeasures to overcome these security challenges?
Ethics Approval
All study plans which involve human subject participation are required to have an
autonomous appraisal by the Research Ethics Committee. The ethics consent
letter comprises a link to the screening mode of my survey to give the Ethics
Output
Presenting findings of security challenges.
28/04/20 Presentations
Present dissertation to the supervisor
Supervision Meetings
Research Data Management Plan (max 500 words)
Plan
The researcher will conduct a survey online about security challenges users
(customers) of IoT devices and vendors are facing customers, in their everyday
usage of the IoT devices as well as their alertness of the possible security threats
linked with phone usage in their lives. The study shall be planned and sent out on
Survey Monkey (www.surveymonkey), and also interviews shall be conducted.
Data set
The data will be gather related to the following:
Name of the security challenges affecting the devices
The source of insecurity of IoT devices
Effect of insecurity on devices and name being affected
Level of security of IoT devices
Solutions of vendors provide about safeness and security of IoT devices to a
customer
What are the countermeasures to overcome these security challenges?
Ethics Approval
All study plans which involve human subject participation are required to have an
autonomous appraisal by the Research Ethics Committee. The ethics consent
letter comprises a link to the screening mode of my survey to give the Ethics
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




