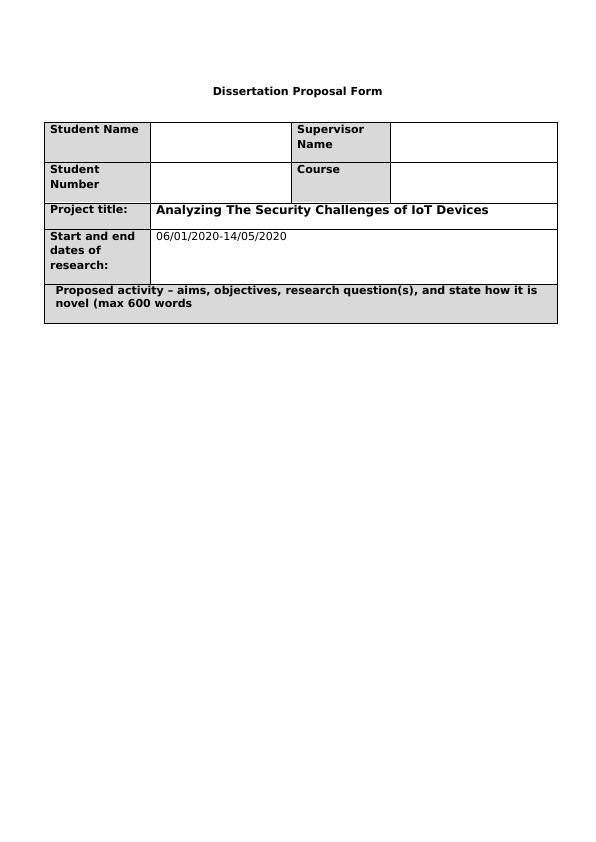
Analyzing The Security Challenges of IoT Devices
Proposed activity, aims, objectives, research question(s), and novelty of analyzing the security challenges of IoT devices.
12 Pages4267 Words74 Views
Added on 2022-11-26
About This Document
This research proposal focuses on analyzing the security challenges of IoT devices and aims to understand the customers' privacy and security issues when using IoT gadgets. It also explores the general security views of IoT devices and the countermeasures needed to deliver safe and secure IoT devices to customers.
Analyzing The Security Challenges of IoT Devices
Proposed activity, aims, objectives, research question(s), and novelty of analyzing the security challenges of IoT devices.
Added on 2022-11-26
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Internet of Things (IOT) - PDF
|14
|3561
|82
The Main Concept of loT is Wireless Sensor Networks
|8
|1673
|42
Internet of Things Security and Privacy
|12
|2833
|99
Security and Privacy Issues in IoT
|5
|3262
|310
Vulnerabilities with Internet of Things 0 Name STUDENT ID IT SECURITY Introduction IoT
|7
|1808
|461
Network Security Issues
|9
|2037
|42