Detailed Report on DDoS Attack on GitHub - Cyber Security - ECU
VerifiedAdded on 2023/04/07
|12
|2202
|350
Report
AI Summary
This report provides a detailed analysis of Distributed Denial of Service (DDoS) attacks, using the large-scale attack on GitHub as a case study. It explains how DDoS attacks operate, including techniques like NTP amplification and reflected attacks. The report then delves into the specifics of the GitHub attack, detailing its impact, the security breaches that occurred, and the actions taken by GitHub and Akamai to mitigate the attack. It further outlines essential steps organizations can take to prevent future DDoS attacks, such as developing incident response plans, installing firewalls, and maintaining secure network architectures. The report concludes by emphasizing the evolving nature of DDoS attacks and the need for continuous improvement in network security measures to protect against these threats.

Running head: DISTRIBUTED DENIAL OF SERVICE ATTACK
Distributed Denial of Service Attack
Name of the student:
Name of the university:
Author note:
Distributed Denial of Service Attack
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DISTRIBUTED DENIAL OF SERVICE ATTACK
Abstract
The following report is prepared to discuss the effect of Distributed Denial of Service Attack
on different platforms. To analyse it, the most massive DDoS attack that took place on
GitHub is chosen. The main reason for the attack is thus reflected and based on it the impact,
and accordingly, the steps taken to prevent a data breach is pointed out. The last part of the
report focusses on some techniques by which the future DDoS attacks can be prevented.
Abstract
The following report is prepared to discuss the effect of Distributed Denial of Service Attack
on different platforms. To analyse it, the most massive DDoS attack that took place on
GitHub is chosen. The main reason for the attack is thus reflected and based on it the impact,
and accordingly, the steps taken to prevent a data breach is pointed out. The last part of the
report focusses on some techniques by which the future DDoS attacks can be prevented.

2DISTRIBUTED DENIAL OF SERVICE ATTACK
Table of Contents
Introduction:...............................................................................................................................3
Operation of the attack in the real world:...................................................................................3
Real world example of NTP Amplification attack:....................................................................6
Impact of the attack:...................................................................................................................7
Actions taken against the attack:............................................................................................7
Conclusion:................................................................................................................................9
References:...............................................................................................................................10
Table of Contents
Introduction:...............................................................................................................................3
Operation of the attack in the real world:...................................................................................3
Real world example of NTP Amplification attack:....................................................................6
Impact of the attack:...................................................................................................................7
Actions taken against the attack:............................................................................................7
Conclusion:................................................................................................................................9
References:...............................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DISTRIBUTED DENIAL OF SERVICE ATTACK
Introduction:
DDoS or Distributed denial of service is a cyber-attack that is performed on an
explicit server or system with the envisioned purpose of unsettling the network’s regular
operation (Sonar, K., & Upadhyay, 2014). The Distributed denial of service attack occurs by
overflowing the beset network or server with a persistent flood of circulation such as
fraudulent requests which overpowers the system instigating a disturbance or denial of
service to relevant traffic (Kolias et al., 2017). Thus it prevents the users from accessing the
websites creating a bad user experience. Hackers generate these delays over resource fatigue
where they yield up or exhaust all available bandwidth, diskette space or memory volume. A
successful Distributed denial of service attack is very dangerous, and it can even harm the
organisation’s reputation causing damage to the relationship between clients and breaching
important information of the company and the client as well. Smaller business can face
enormous damage leading to the financial loss which may even result up to the closing of the
business organisation. This report focuses on the detailed operation of the Distributed denial
of service attack and the possible measures that can be taken against it to prevent the attack in
future.
Operation of the attack in the real world:
A denial of service could be in the form of hijacking webservers, overloading ports
with request rendering them unusable, denying wireless authentication and denying any
services provided on the internet (De Donno et al.,2017). Attacks of such intent can be
performed with the help of a single machine as they are much easier to execute and monitor.
They are also easy to detect and mitigate issues. As these attacks can take place over multiple
devices spreading across multiple areas, it becomes difficult to stop this attack pointing out
the main culprit behind the attack.
Introduction:
DDoS or Distributed denial of service is a cyber-attack that is performed on an
explicit server or system with the envisioned purpose of unsettling the network’s regular
operation (Sonar, K., & Upadhyay, 2014). The Distributed denial of service attack occurs by
overflowing the beset network or server with a persistent flood of circulation such as
fraudulent requests which overpowers the system instigating a disturbance or denial of
service to relevant traffic (Kolias et al., 2017). Thus it prevents the users from accessing the
websites creating a bad user experience. Hackers generate these delays over resource fatigue
where they yield up or exhaust all available bandwidth, diskette space or memory volume. A
successful Distributed denial of service attack is very dangerous, and it can even harm the
organisation’s reputation causing damage to the relationship between clients and breaching
important information of the company and the client as well. Smaller business can face
enormous damage leading to the financial loss which may even result up to the closing of the
business organisation. This report focuses on the detailed operation of the Distributed denial
of service attack and the possible measures that can be taken against it to prevent the attack in
future.
Operation of the attack in the real world:
A denial of service could be in the form of hijacking webservers, overloading ports
with request rendering them unusable, denying wireless authentication and denying any
services provided on the internet (De Donno et al.,2017). Attacks of such intent can be
performed with the help of a single machine as they are much easier to execute and monitor.
They are also easy to detect and mitigate issues. As these attacks can take place over multiple
devices spreading across multiple areas, it becomes difficult to stop this attack pointing out
the main culprit behind the attack.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4DISTRIBUTED DENIAL OF SERVICE ATTACK
The primary method of operation of a Distributed denial of service attack is by
making web services unavailable. Since everything that is attacked is available in reality, the
service can be made unavailable if the performance of the machine is brought down. This is
the main principle behind every Distributed denial of service attack. Flooding servers can
execute some of the Distributed Denial of Service Attacks by executing requests causing
overloading of the server. Another mode by which the Distributed denial of service attack can
take place is by sending un-fragmented packets to a server which are unable to handle. These
methods when executed by Botnets, exponentially increase the rate of damage that is
intended and becomes challenging to mitigate the damage.
Figure1: Distributed Denial of Service Attack (Source: Created by Author)
Some of the commonly known Distributed Denial of Service attack based on their
methodology are listed below:
1. Ping of Death:
According to the TCP/IP protocol, the amount of packet size can range up to
65535 bytes. The sound of death exploits this particular fact. In this type of attack,
The primary method of operation of a Distributed denial of service attack is by
making web services unavailable. Since everything that is attacked is available in reality, the
service can be made unavailable if the performance of the machine is brought down. This is
the main principle behind every Distributed denial of service attack. Flooding servers can
execute some of the Distributed Denial of Service Attacks by executing requests causing
overloading of the server. Another mode by which the Distributed denial of service attack can
take place is by sending un-fragmented packets to a server which are unable to handle. These
methods when executed by Botnets, exponentially increase the rate of damage that is
intended and becomes challenging to mitigate the damage.
Figure1: Distributed Denial of Service Attack (Source: Created by Author)
Some of the commonly known Distributed Denial of Service attack based on their
methodology are listed below:
1. Ping of Death:
According to the TCP/IP protocol, the amount of packet size can range up to
65535 bytes. The sound of death exploits this particular fact. In this type of attack,

5DISTRIBUTED DENIAL OF SERVICE ATTACK
the attackers send packets that are more than the maximum packet size and then
packet fragments are added up (Acharya, Arpitha & Santhosh Kumar, 2016).
Computers generally do not know what to do with such packets and end up
freezing and sometimes crashing the system entirely.
2. Reflected Attack:
This particular attack is more often and is used with the help of a botnet. The
attacker sends a host of reliable computer system a request using the botnet which
is also known as reflectors (Santanna et al., 2015). The connection that comes
from the botnet looks like the connection coming from the victim. This is done by
spoofing the source part in the packet header, and as a result, the computer sends
an acknowledgement to the victim computer. Multiple such requests to the same
network from a different machine overload the computer and crash it. This is also
known as a spoof attack.
3. Mail bomb Attack:
The mail bomb attack is generally caused to email servers. In this type of
attack instead of packets, oversized emails are filled with random garbage values
are sent to the targets email server, and it crashes the email server due to suddenly
stricken load and renders abuses until fixed (Al-Jarrah & Arafat, 2015).
4. Teardrop Attack:
In this type of attack, the fragmentation offset fills when the packets are
abused. A single field in IP header is the part counterbalance fill representing the
preliminary situation or the equipoise of the information controlled in the
disjointed container comparative to the content of the record in the single bottle.
When the magnitude of the equaliser and the scrappy pouch varies from the
conforming uneven pack the sachets correspondence. This makes the server
the attackers send packets that are more than the maximum packet size and then
packet fragments are added up (Acharya, Arpitha & Santhosh Kumar, 2016).
Computers generally do not know what to do with such packets and end up
freezing and sometimes crashing the system entirely.
2. Reflected Attack:
This particular attack is more often and is used with the help of a botnet. The
attacker sends a host of reliable computer system a request using the botnet which
is also known as reflectors (Santanna et al., 2015). The connection that comes
from the botnet looks like the connection coming from the victim. This is done by
spoofing the source part in the packet header, and as a result, the computer sends
an acknowledgement to the victim computer. Multiple such requests to the same
network from a different machine overload the computer and crash it. This is also
known as a spoof attack.
3. Mail bomb Attack:
The mail bomb attack is generally caused to email servers. In this type of
attack instead of packets, oversized emails are filled with random garbage values
are sent to the targets email server, and it crashes the email server due to suddenly
stricken load and renders abuses until fixed (Al-Jarrah & Arafat, 2015).
4. Teardrop Attack:
In this type of attack, the fragmentation offset fills when the packets are
abused. A single field in IP header is the part counterbalance fill representing the
preliminary situation or the equipoise of the information controlled in the
disjointed container comparative to the content of the record in the single bottle.
When the magnitude of the equaliser and the scrappy pouch varies from the
conforming uneven pack the sachets correspondence. This makes the server
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6DISTRIBUTED DENIAL OF SERVICE ATTACK
susceptible to teardrop attack causing difficulty to reconvene the packets
consequential in the denial of service condition (Patel & Katkar, 2016).
5. NTP Amplification: In this type of DDoS attack the network time protocol servers
gets exploited. It is also known as amplified reflection attack where the response that
is received from the server is spoofed to an IP address (Kührer et al., 2014).
Real world example of NTP Amplification attack:
The most significant offence of Distributed Denial of Services was reported to take
place at GitHub. GitHub is an essential resource of code for some major organisations all
around the world. The attack took place with the help of mem-crashing about 1.35 terabits of
traffic per second which hit the GitHub all at once. GitHub is the podium that aids people
resolve snags by structuring software together. On 28 February 2018 GitHub experienced the
major Distributed Denial of Service attack ever documented in human history. The attackers
took advantage of the caching system known as mem-cash D by spoofing the IP address of
the intended victim and sending queries to multiple Memcached servers.. Mem-cash D is a
distributed open source caching system that is used by a lot of websites for extensive use of
database calls and other information as it allows data to be cached there and presents it to the
user in a much faster way. A distributed network of servers containing memory, responds to
the request made by users to the web server. The mechanism by which the mem-cache D
works is that the most recent data is held in these Mem-cache D servers and gradually fills up
with tons of web server data (Bawany, Shamsi & Salah, 2017). No authentication system is
designed in the mem-cache D system as they are not intended to be exposed to the public
internet. As there is no authentication present with the system, data can be loaded by anyone.
GitHub revealed that the attack had taken over the memory system called the mem-cache to
amplify the volume of data sent to GitHub ranging to about 51000. This means each of the
susceptible to teardrop attack causing difficulty to reconvene the packets
consequential in the denial of service condition (Patel & Katkar, 2016).
5. NTP Amplification: In this type of DDoS attack the network time protocol servers
gets exploited. It is also known as amplified reflection attack where the response that
is received from the server is spoofed to an IP address (Kührer et al., 2014).
Real world example of NTP Amplification attack:
The most significant offence of Distributed Denial of Services was reported to take
place at GitHub. GitHub is an essential resource of code for some major organisations all
around the world. The attack took place with the help of mem-crashing about 1.35 terabits of
traffic per second which hit the GitHub all at once. GitHub is the podium that aids people
resolve snags by structuring software together. On 28 February 2018 GitHub experienced the
major Distributed Denial of Service attack ever documented in human history. The attackers
took advantage of the caching system known as mem-cash D by spoofing the IP address of
the intended victim and sending queries to multiple Memcached servers.. Mem-cash D is a
distributed open source caching system that is used by a lot of websites for extensive use of
database calls and other information as it allows data to be cached there and presents it to the
user in a much faster way. A distributed network of servers containing memory, responds to
the request made by users to the web server. The mechanism by which the mem-cache D
works is that the most recent data is held in these Mem-cache D servers and gradually fills up
with tons of web server data (Bawany, Shamsi & Salah, 2017). No authentication system is
designed in the mem-cache D system as they are not intended to be exposed to the public
internet. As there is no authentication present with the system, data can be loaded by anyone.
GitHub revealed that the attack had taken over the memory system called the mem-cache to
amplify the volume of data sent to GitHub ranging to about 51000. This means each of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7DISTRIBUTED DENIAL OF SERVICE ATTACK
bytes sent by the attacker up to 51 kb was sent towards the target. This is known as the
amplification factor. The UDP reflection initiates the attack by taking advantage of the UDP
traffic between the sender and the recipients.
Impact of the attack:
As a result of the attack, a massive influx of traffic was generated. It was reported that
the amount of traffic that stroked the developers’ platform was 1.3 terabytes per second at its
peak (Rajan & Vijayprasath, 2015). The attacker originated from different autonomous
systems across tens and thousands of different endpoints. The entire attack lasted for about 8
minutes and was offline for 5 minutes (Shamsolmoali, Alam & Biswas, 2014). The objective
of the Distributed denial of service attack was to block access to the services of GitHub
temporarily.
Effect of the attack:
1. As a result of this attack, the DNS provider of US was stroked by traffic of 1.2 Tbps.
2. GitHub faced enormous traffic of 1.35 terabits per second.
3. In spite of this massive traffic, no such information breach had taken place due to the
attack.
Actions were taken against the attack:
After noticing the attack, GitHub demanded help from prolific service of Akamai that
helps in mitigating such events by steering traffic over its superior system and also by
blocking spiteful requests (Malhotra et al., 2016). The company has not faced such traffic
before but as it had premeditated its set-up to knob five times the circulation from the prior
attack that was recorded no such data breach was reported in this instance. Akamai
accomplished to bring GitHub connected in just a few actions.
bytes sent by the attacker up to 51 kb was sent towards the target. This is known as the
amplification factor. The UDP reflection initiates the attack by taking advantage of the UDP
traffic between the sender and the recipients.
Impact of the attack:
As a result of the attack, a massive influx of traffic was generated. It was reported that
the amount of traffic that stroked the developers’ platform was 1.3 terabytes per second at its
peak (Rajan & Vijayprasath, 2015). The attacker originated from different autonomous
systems across tens and thousands of different endpoints. The entire attack lasted for about 8
minutes and was offline for 5 minutes (Shamsolmoali, Alam & Biswas, 2014). The objective
of the Distributed denial of service attack was to block access to the services of GitHub
temporarily.
Effect of the attack:
1. As a result of this attack, the DNS provider of US was stroked by traffic of 1.2 Tbps.
2. GitHub faced enormous traffic of 1.35 terabits per second.
3. In spite of this massive traffic, no such information breach had taken place due to the
attack.
Actions were taken against the attack:
After noticing the attack, GitHub demanded help from prolific service of Akamai that
helps in mitigating such events by steering traffic over its superior system and also by
blocking spiteful requests (Malhotra et al., 2016). The company has not faced such traffic
before but as it had premeditated its set-up to knob five times the circulation from the prior
attack that was recorded no such data breach was reported in this instance. Akamai
accomplished to bring GitHub connected in just a few actions.
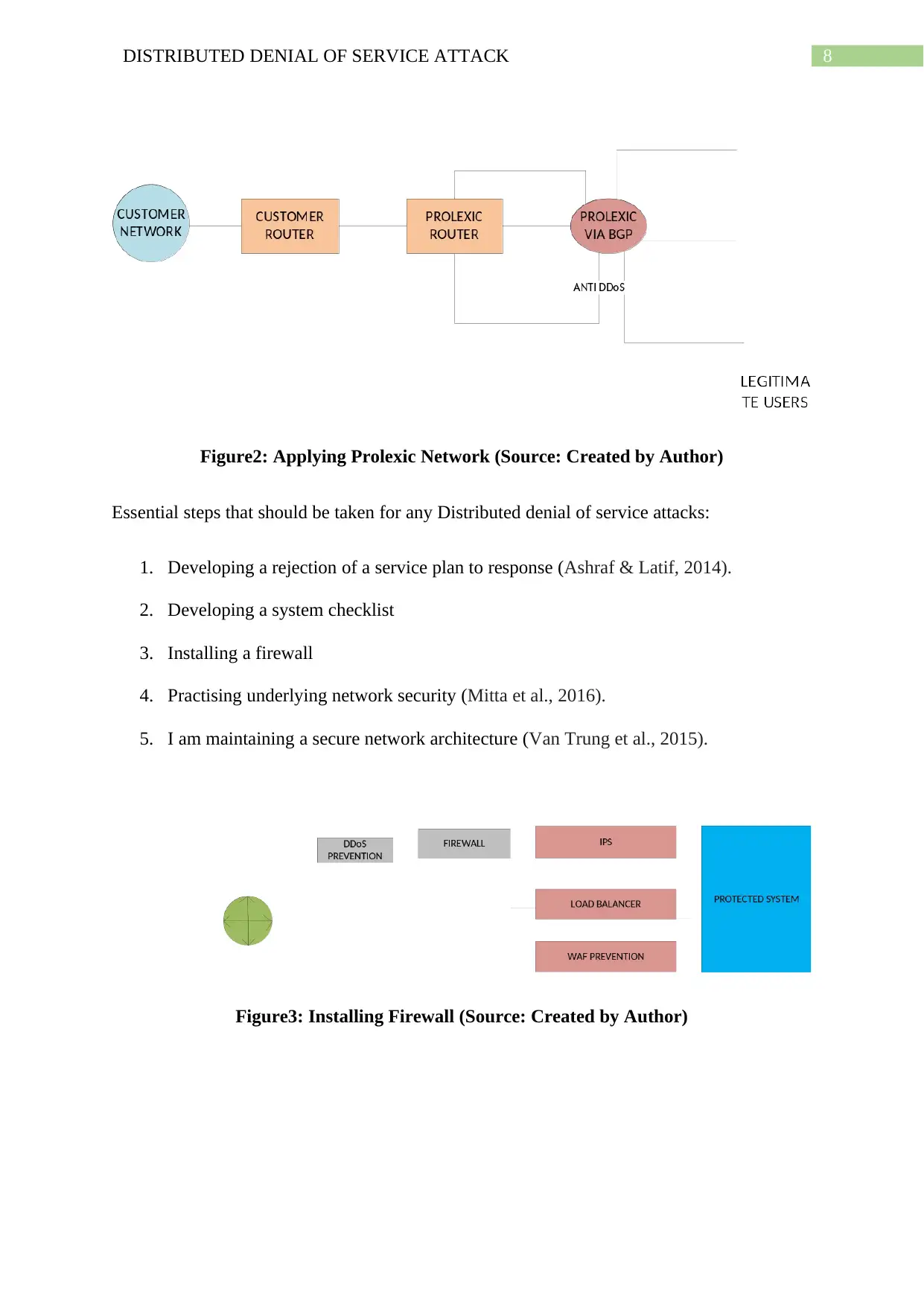
8DISTRIBUTED DENIAL OF SERVICE ATTACK
Figure2: Applying Prolexic Network (Source: Created by Author)
Essential steps that should be taken for any Distributed denial of service attacks:
1. Developing a rejection of a service plan to response (Ashraf & Latif, 2014).
2. Developing a system checklist
3. Installing a firewall
4. Practising underlying network security (Mitta et al., 2016).
5. I am maintaining a secure network architecture (Van Trung et al., 2015).
Figure3: Installing Firewall (Source: Created by Author)
Figure2: Applying Prolexic Network (Source: Created by Author)
Essential steps that should be taken for any Distributed denial of service attacks:
1. Developing a rejection of a service plan to response (Ashraf & Latif, 2014).
2. Developing a system checklist
3. Installing a firewall
4. Practising underlying network security (Mitta et al., 2016).
5. I am maintaining a secure network architecture (Van Trung et al., 2015).
Figure3: Installing Firewall (Source: Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9DISTRIBUTED DENIAL OF SERVICE ATTACK
Conclusion:
With the continuous evolution of sophisticated and dangerous attacks, Distributed
Denial of Service Attack is likely to take place in future. Modern-day software-defined
applications will open up to certain elements that will initiate the future Distributed Denial of
Service attacks from the user environment. In future trend will grow up on locking down
users’ environment by the government. Denial of service attacks no longer confined to the
massive corporation as it can attack small enterprises too where the risk of a data breach will
be much more dangerous. Distributed denial of service attack can last for hours or even days.
It entirely depends on the intent of the attacker. In future, this attack can be for many reasons
which involve financial reasons where the attacker will be DDoSing, a competitor in the
market place. It could also be for political reasons where attackers do not like the targeted
organisation’s beliefs. Network frame breadwinners are getting better at treating these
attacks, but they must enhance their infrastructure services to prevent and mitigate the future
possible Distributed Denial of Service attacks.
Conclusion:
With the continuous evolution of sophisticated and dangerous attacks, Distributed
Denial of Service Attack is likely to take place in future. Modern-day software-defined
applications will open up to certain elements that will initiate the future Distributed Denial of
Service attacks from the user environment. In future trend will grow up on locking down
users’ environment by the government. Denial of service attacks no longer confined to the
massive corporation as it can attack small enterprises too where the risk of a data breach will
be much more dangerous. Distributed denial of service attack can last for hours or even days.
It entirely depends on the intent of the attacker. In future, this attack can be for many reasons
which involve financial reasons where the attacker will be DDoSing, a competitor in the
market place. It could also be for political reasons where attackers do not like the targeted
organisation’s beliefs. Network frame breadwinners are getting better at treating these
attacks, but they must enhance their infrastructure services to prevent and mitigate the future
possible Distributed Denial of Service attacks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10DISTRIBUTED DENIAL OF SERVICE ATTACK
References:
Al-Jarrah, O., & Arafat, A. (2015). Network intrusion detection system using neural network
classification of attack behavior. Journal of Advances in Information Technology
Vol, 6(1)
Ashraf, J., & Latif, S. (2014, November). Handling intrusion and DDoS attacks in Software
Defined Networks using machine learning techniques. In 2014 National Software
Engineering Conference (pp. 55-60). IEEE.
Bawany, N. Z., Shamsi, J. A., & Salah, K. (2017). DDoS attack detection and mitigation
using SDN: methods, practices, and solutions. Arabian Journal for Science and
Engineering, 42(2), 425-441.
De Donno, M., Dragoni, N., Giaretta, A., & Mazzara, M. (2016, May). AntibIoTic: protecting
IoT devices against DDoS attacks. In International Conference on Software
Engineering for Defence Applications (pp. 59-72). Springer, Cham.
Kolias, C., Kambourakis, G., Stavrou, A., & Voas, J. (2017). DDoS in the IoT: Mirai and
other botnets. Computer, 50(7), 80-84.
Kührer, M., Hupperich, T., Rossow, C., & Holz, T. (2014). Exit from Hell? Reducing the
Impact of Amplification DDoS Attacks. In 23rd {USENIX} Security Symposium
({USENIX} Security 14) (pp. 111-125
Malhotra, A., Cohen, I. E., Brakke, E., & Goldberg, S. (2016, February). Attacking the
Network Time Protocol. In NDSS.
Mittal, S., Das, P. K., Mulwad, V., Joshi, A., & Finin, T. (2016, August). Cybertwitter: Using
Twitter to generate alerts for cybersecurity threats and vulnerabilities. In Proceedings
References:
Al-Jarrah, O., & Arafat, A. (2015). Network intrusion detection system using neural network
classification of attack behavior. Journal of Advances in Information Technology
Vol, 6(1)
Ashraf, J., & Latif, S. (2014, November). Handling intrusion and DDoS attacks in Software
Defined Networks using machine learning techniques. In 2014 National Software
Engineering Conference (pp. 55-60). IEEE.
Bawany, N. Z., Shamsi, J. A., & Salah, K. (2017). DDoS attack detection and mitigation
using SDN: methods, practices, and solutions. Arabian Journal for Science and
Engineering, 42(2), 425-441.
De Donno, M., Dragoni, N., Giaretta, A., & Mazzara, M. (2016, May). AntibIoTic: protecting
IoT devices against DDoS attacks. In International Conference on Software
Engineering for Defence Applications (pp. 59-72). Springer, Cham.
Kolias, C., Kambourakis, G., Stavrou, A., & Voas, J. (2017). DDoS in the IoT: Mirai and
other botnets. Computer, 50(7), 80-84.
Kührer, M., Hupperich, T., Rossow, C., & Holz, T. (2014). Exit from Hell? Reducing the
Impact of Amplification DDoS Attacks. In 23rd {USENIX} Security Symposium
({USENIX} Security 14) (pp. 111-125
Malhotra, A., Cohen, I. E., Brakke, E., & Goldberg, S. (2016, February). Attacking the
Network Time Protocol. In NDSS.
Mittal, S., Das, P. K., Mulwad, V., Joshi, A., & Finin, T. (2016, August). Cybertwitter: Using
Twitter to generate alerts for cybersecurity threats and vulnerabilities. In Proceedings

11DISTRIBUTED DENIAL OF SERVICE ATTACK
of the 2016 IEEE/ACM International Conference on Advances in Social Networks
Analysis and Mining (pp. 860-867). IEEE Press.
Patel, J., & Katkar, V. (2016). A multi-classifiers based novel DoS/DDoS attack detection
using fuzzy logic. In Proceedings of International Conference on ICT for Sustainable
Development (pp. 809-815). Springer, Singapore
Shamsolmoali, P., Alam, M. A., & Biswas, R. (2014). C DF: High Rate DDOS filtering₂
method in Cloud Computing. Computer Network and Information Security no.
August, 43-50.
Sonar, K., & Upadhyay, H. (2014). A survey: DDOS attack on the Internet of
Things. International Journal of Engineering Research and Development, 10(11), 58-63.
Van Trung, P., Huong, T. T., Van Tuyen, D., Duc, D. M., Thanh, N. H., & Marshall, A.
(2015, October). A multi-criteria-based DDoS-attack prevention solution using
software-defined networking. In 2015 International Conference on Advanced
Technologies for Communications (ATC) (pp. 308-313). IEEE.
of the 2016 IEEE/ACM International Conference on Advances in Social Networks
Analysis and Mining (pp. 860-867). IEEE Press.
Patel, J., & Katkar, V. (2016). A multi-classifiers based novel DoS/DDoS attack detection
using fuzzy logic. In Proceedings of International Conference on ICT for Sustainable
Development (pp. 809-815). Springer, Singapore
Shamsolmoali, P., Alam, M. A., & Biswas, R. (2014). C DF: High Rate DDOS filtering₂
method in Cloud Computing. Computer Network and Information Security no.
August, 43-50.
Sonar, K., & Upadhyay, H. (2014). A survey: DDOS attack on the Internet of
Things. International Journal of Engineering Research and Development, 10(11), 58-63.
Van Trung, P., Huong, T. T., Van Tuyen, D., Duc, D. M., Thanh, N. H., & Marshall, A.
(2015, October). A multi-criteria-based DDoS-attack prevention solution using
software-defined networking. In 2015 International Conference on Advanced
Technologies for Communications (ATC) (pp. 308-313). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12