System Security Analysis: WebGoat and Backtrack Implementation
VerifiedAdded on 2020/04/01
|28
|4265
|173
Report
AI Summary
This report provides a detailed analysis of system security, focusing on the WebGoat J2EE web application package and the Backtrack GNU/Linux distribution. The report begins with an introduction to system security, followed by a discussion of WebGoat, including procedures for download and installation, and an overview of exploits such as SQL injection and session hijacking. It then explores various attack scenarios in three stages, providing screenshots and methods for testing attacks. Part B delves into Backtrack, describing DoS attacks and the steps involved in their implementation, along with an evaluation of the data after implementation and defense mechanisms. The report covers topics like breaking authentication, credit card theft, and website defacement, along with testing methods like login credentials checks, SQL injection execution, URL manipulation, and cache usage. The report concludes with a summary of the findings and references.

System
security
security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction....................................................................................................................................3
Part A......................................................................................................................................................3
2. Web goat J2EE web application package....................................................................................3
3. Procedures followed to download web goat................................................................................3
4. Exploits used to attack a webpage................................................................................................8
5. Description of the scenarios in 3 stages of the challenge............................................................8
6. Screenshots...................................................................................................................................13
7. Method used to test the attack and result..................................................................................16
Part B....................................................................................................................................................17
8. Backtrack GNU/Linux distributions..........................................................................................17
9. Description of the attack-DoS attack.........................................................................................20
10. Steps followed to implement (DoS) Attack............................................................................21
11. Evaluation of data after implementation...............................................................................25
12. Defence mechanisms used to defend the attack....................................................................26
13. Conclusion................................................................................................................................27
References..............................................................................................................................................28
1. Introduction....................................................................................................................................3
Part A......................................................................................................................................................3
2. Web goat J2EE web application package....................................................................................3
3. Procedures followed to download web goat................................................................................3
4. Exploits used to attack a webpage................................................................................................8
5. Description of the scenarios in 3 stages of the challenge............................................................8
6. Screenshots...................................................................................................................................13
7. Method used to test the attack and result..................................................................................16
Part B....................................................................................................................................................17
8. Backtrack GNU/Linux distributions..........................................................................................17
9. Description of the attack-DoS attack.........................................................................................20
10. Steps followed to implement (DoS) Attack............................................................................21
11. Evaluation of data after implementation...............................................................................25
12. Defence mechanisms used to defend the attack....................................................................26
13. Conclusion................................................................................................................................27
References..............................................................................................................................................28

1. Introduction
System security could be known as IT security or cyber security. It protect computer
from the damage to their hardware, theft and software. The system security will be performed
by WebGoatJ2EE web application package and Backtrack GNU/Linux distribution. The web
Goat challenging questions will be completed using the web application package. The perfect
Java source code is used for complete the Web Goat challenge. The theoretical description of
the attack will be attached. The short evaluation and considerations of the attack will be
provided. The defence mechanism will be included that is used for defend from such an
attack. Defence mechanisms are having knowledge of how people have awareness of
behaviours, feelings and unpleasant thoughts. The procedures will be included to download
web goat. The method for testing the attack and result will be added. The steps will be added
to implement the task. After the implementation step the evaluation of data will be written.
Different techniques will be used to defend such attack. Backtrack GNU/Linux distributions
description will be added.
Part A
2. Web goat J2EE web application package
Web Goat is the J2EE application maintained by OWASP. It is created with security
flaws for learning. OWASP stands for Open Web Application Security Project. It makes
freely-available articles, tools, documentation, methodologies and technologies in the web
application security field. In this application SQL injection is used for stealing the credit card
numbers. To learn and implement is difficult in web application security. The initial aim of
the web Goat is to create the de-facto interactive for web application security. It is Java based
web application. IT is very insecure one. The Web Goat attack is made by using Tamber.
Web Scarab and Burp Suite also used for this attack. Three challenges are done by the Web
Goat that is Break the authentication, steal all the credit cards from the database and deface
the website.
3. Procedures followed to download web goat
To download the web Goat some software files are needed. The required software
files
1. Operating system could be (Windows, Mac Osx, Ubuntu).
2. Download the JDK file and install.
System security could be known as IT security or cyber security. It protect computer
from the damage to their hardware, theft and software. The system security will be performed
by WebGoatJ2EE web application package and Backtrack GNU/Linux distribution. The web
Goat challenging questions will be completed using the web application package. The perfect
Java source code is used for complete the Web Goat challenge. The theoretical description of
the attack will be attached. The short evaluation and considerations of the attack will be
provided. The defence mechanism will be included that is used for defend from such an
attack. Defence mechanisms are having knowledge of how people have awareness of
behaviours, feelings and unpleasant thoughts. The procedures will be included to download
web goat. The method for testing the attack and result will be added. The steps will be added
to implement the task. After the implementation step the evaluation of data will be written.
Different techniques will be used to defend such attack. Backtrack GNU/Linux distributions
description will be added.
Part A
2. Web goat J2EE web application package
Web Goat is the J2EE application maintained by OWASP. It is created with security
flaws for learning. OWASP stands for Open Web Application Security Project. It makes
freely-available articles, tools, documentation, methodologies and technologies in the web
application security field. In this application SQL injection is used for stealing the credit card
numbers. To learn and implement is difficult in web application security. The initial aim of
the web Goat is to create the de-facto interactive for web application security. It is Java based
web application. IT is very insecure one. The Web Goat attack is made by using Tamber.
Web Scarab and Burp Suite also used for this attack. Three challenges are done by the Web
Goat that is Break the authentication, steal all the credit cards from the database and deface
the website.
3. Procedures followed to download web goat
To download the web Goat some software files are needed. The required software
files
1. Operating system could be (Windows, Mac Osx, Ubuntu).
2. Download the JDK file and install.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3. Apache Tomcat Server
4. Download and install the Web Goat War file.
Create variable Java
1. Windows
2. Ubuntu
How to download and install the Apache Tomcat Server on Windows, Ubuntu, Mac OS
1. Mac OS X
Goto http://tomcat.apache.org --> Download --> Tomcat 8.0 --> "8.0.{xx}" (where {xx}
denotes the latest upgrade number) --> Binary distribution --> Core --> "tar.gz" package (e.g.,
"apache-tomcat-8.0.{xx}.tar.gz", about 8 MB)
Steps for installing Tomcat
a. Goto "~/Downloads", double-click the downloaded tarball (e.g., "apache-tomcat-8.0.
{xx}.tar.gz") to expand it into a folder (e.g., "apache-tomcat-8.0.{xx}")
b. Move the extracted folder (e.g., "apache-tomcat-8.0.{xx}") to "/Applications".
c. For ease of use, we shall shorten and rename this folder to "tomcat".
2. Windows
a. Goto http://tomcat.apache.org --> Downloads --> Tomcat 8.0 --> "8.0.{xx}" (where
{xx} is the latest upgrade number) --> Binary Distributions --> Core --> "ZIP"
package (e.g., "apache-tomcat-8.0.{xx}.zip", about 8 MB).
b. Create your project directory, say "d:\myProject" or "c:\myProject". UNZIP the
downloaded file into your project directory. Tomcat will be unzipped into directory
"d:\myProject\apache-tomcat-8.0.{xx}".
c. For ease of use, we shall shorten and rename this directory to "d:\myProject\tomcat".
Configuration for Tomcat Server
1. open the Tomcat-users.xml file under "Tomcat_Home\conf\"
2. the Tomcat manager is enabled by adding the highlighted lines, inside the <Tomcat-
users>elements
4. Download and install the Web Goat War file.
Create variable Java
1. Windows
2. Ubuntu
How to download and install the Apache Tomcat Server on Windows, Ubuntu, Mac OS
1. Mac OS X
Goto http://tomcat.apache.org --> Download --> Tomcat 8.0 --> "8.0.{xx}" (where {xx}
denotes the latest upgrade number) --> Binary distribution --> Core --> "tar.gz" package (e.g.,
"apache-tomcat-8.0.{xx}.tar.gz", about 8 MB)
Steps for installing Tomcat
a. Goto "~/Downloads", double-click the downloaded tarball (e.g., "apache-tomcat-8.0.
{xx}.tar.gz") to expand it into a folder (e.g., "apache-tomcat-8.0.{xx}")
b. Move the extracted folder (e.g., "apache-tomcat-8.0.{xx}") to "/Applications".
c. For ease of use, we shall shorten and rename this folder to "tomcat".
2. Windows
a. Goto http://tomcat.apache.org --> Downloads --> Tomcat 8.0 --> "8.0.{xx}" (where
{xx} is the latest upgrade number) --> Binary Distributions --> Core --> "ZIP"
package (e.g., "apache-tomcat-8.0.{xx}.zip", about 8 MB).
b. Create your project directory, say "d:\myProject" or "c:\myProject". UNZIP the
downloaded file into your project directory. Tomcat will be unzipped into directory
"d:\myProject\apache-tomcat-8.0.{xx}".
c. For ease of use, we shall shorten and rename this directory to "d:\myProject\tomcat".
Configuration for Tomcat Server
1. open the Tomcat-users.xml file under "Tomcat_Home\conf\"
2. the Tomcat manager is enabled by adding the highlighted lines, inside the <Tomcat-
users>elements
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

<tomcat-users>
<role rolename="manager-gui"/>
<user username="manager" password="xxxx" roles="manager-gui"/>
</tomcat-users>
The Webgoat.war is copied to the Tomcat directory
1. Mac OS X sudocp webgoat-container-5.4war /Applications/tomcat/webapps/
2. Ubuntu sudocp webgoat-container-5.4.war /var/lib/tomcat/webapps/
3. Windows copy webgoat-container-5.4.war and paste to D:\myProject\tomcat\
Procedure for start and shutdown Tomcat server
1. Ubuntu and Mac OS X
By using terminal select bin folder under the tomcat directory.
Type this command to run the tomcat server "sudo ./startup.sh"
Write this command to stop the tomcat server "sudo ./shutdown.sh"
2. Windows
By using window command prompt select the bin folder present in the tomcat directory.
Type this command to run the tomcat server "startup"
Write this command to stop the tomcat server "shutdown"
After the installation of tomcat server open the server and enter the URL
http://localhost:8080/webgoat_war_filename/ on browser address bar
<role rolename="manager-gui"/>
<user username="manager" password="xxxx" roles="manager-gui"/>
</tomcat-users>
The Webgoat.war is copied to the Tomcat directory
1. Mac OS X sudocp webgoat-container-5.4war /Applications/tomcat/webapps/
2. Ubuntu sudocp webgoat-container-5.4.war /var/lib/tomcat/webapps/
3. Windows copy webgoat-container-5.4.war and paste to D:\myProject\tomcat\
Procedure for start and shutdown Tomcat server
1. Ubuntu and Mac OS X
By using terminal select bin folder under the tomcat directory.
Type this command to run the tomcat server "sudo ./startup.sh"
Write this command to stop the tomcat server "sudo ./shutdown.sh"
2. Windows
By using window command prompt select the bin folder present in the tomcat directory.
Type this command to run the tomcat server "startup"
Write this command to stop the tomcat server "shutdown"
After the installation of tomcat server open the server and enter the URL
http://localhost:8080/webgoat_war_filename/ on browser address bar
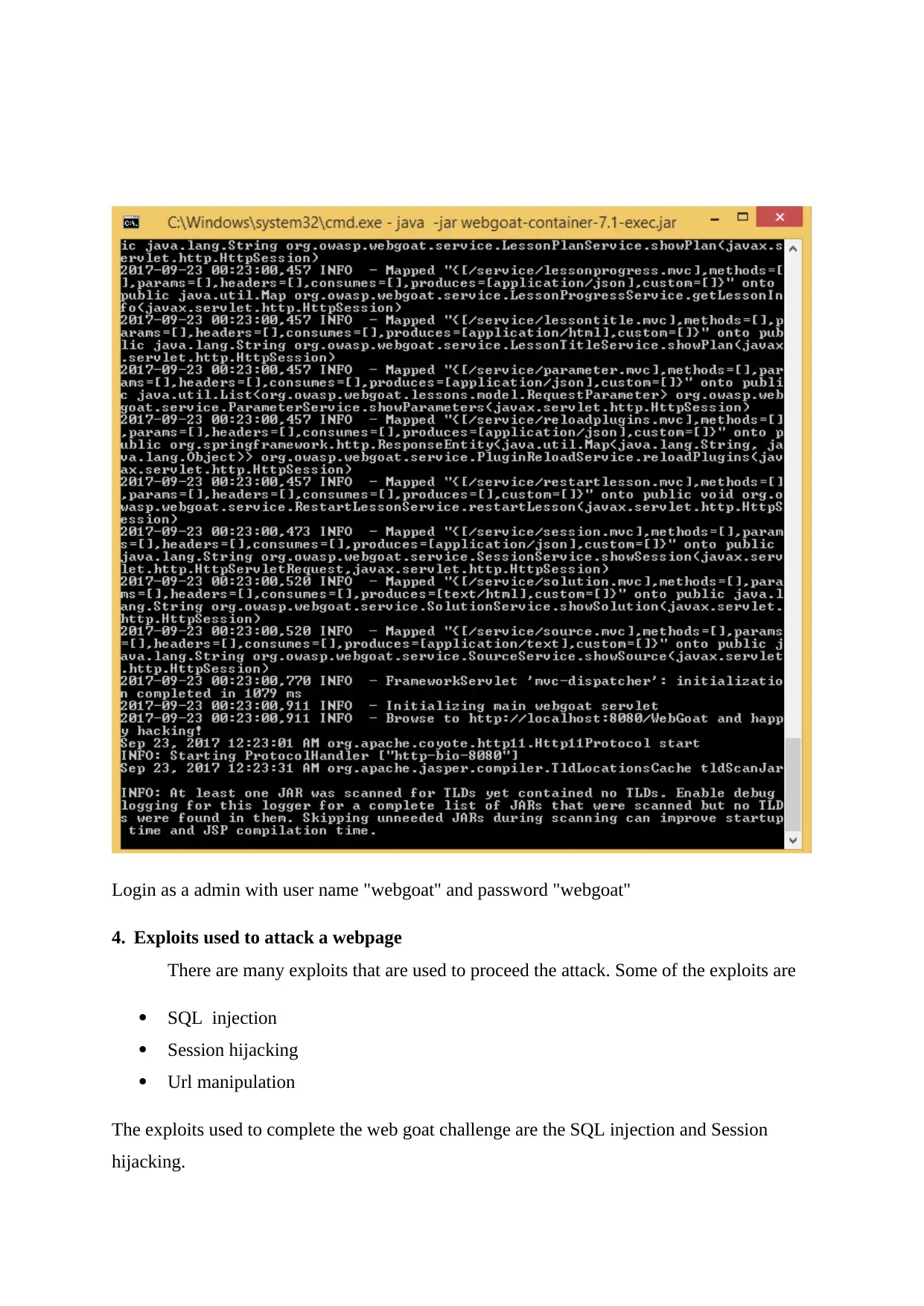
Login as a admin with user name "webgoat" and password "webgoat"
4. Exploits used to attack a webpage
There are many exploits that are used to proceed the attack. Some of the exploits are
SQL injection
Session hijacking
Url manipulation
The exploits used to complete the web goat challenge are the SQL injection and Session
hijacking.
4. Exploits used to attack a webpage
There are many exploits that are used to proceed the attack. Some of the exploits are
SQL injection
Session hijacking
Url manipulation
The exploits used to complete the web goat challenge are the SQL injection and Session
hijacking.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SQL injection represent to an injection attack in which attacker can also execute malicious
SQL statement that controls a web application database server. It commonly represents
relational database management system. SQL injection obligation could possibly affect any
website or web application that uses SQL based database. One of the oldest is vulnerability. It
is one of the most dangerous web application vulnerabilities. Session hijacking or cookie
hijacking is one in which unauthorised information can be tracked.
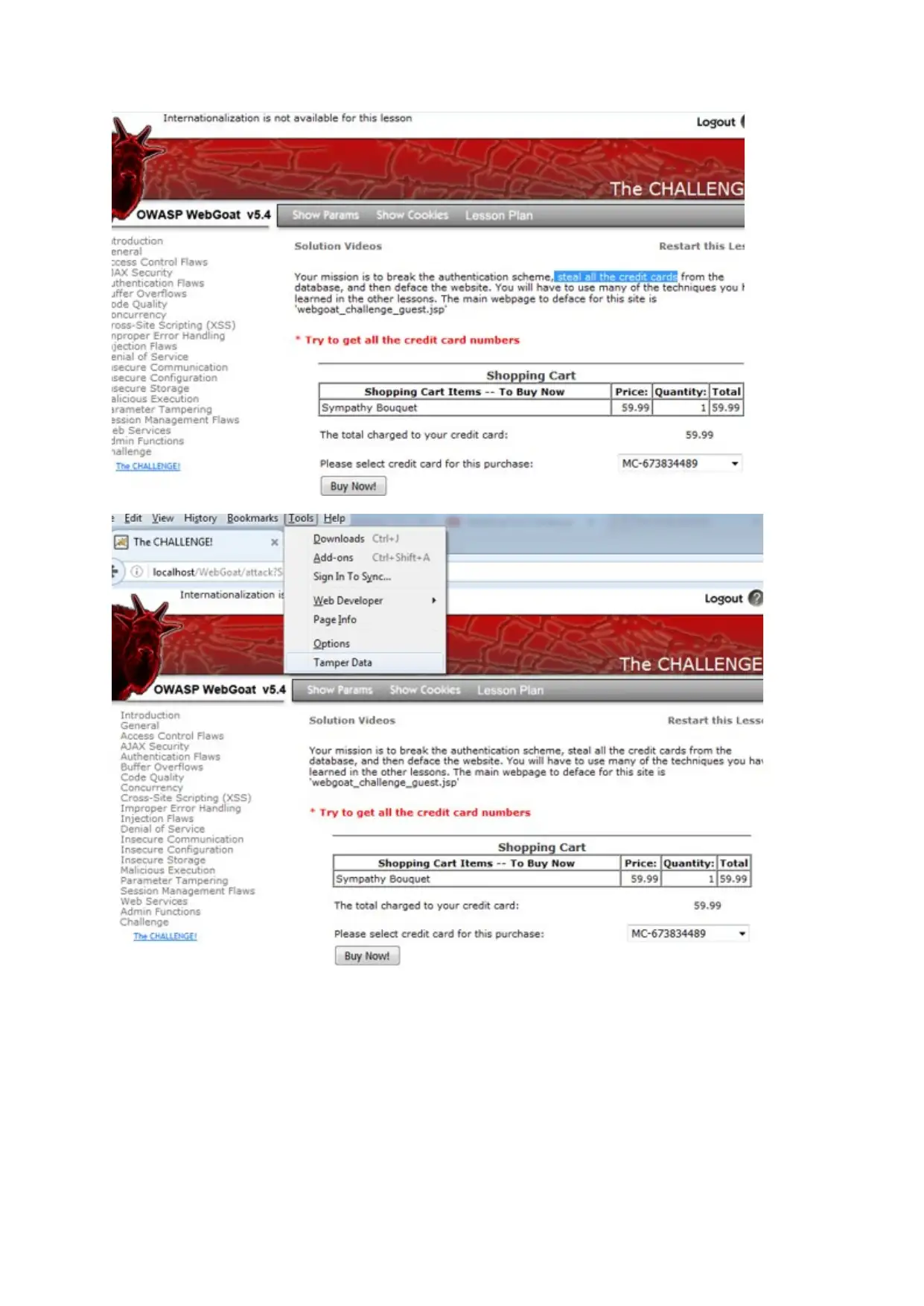
5. Description of the scenarios in 3 stages of the challenge
Challenge 1
Breaking the authentication
The authenticated users would be done the highly secured activities. So that
authentication is introduced. Many methods are introduced to provide authentication. But
these methods are not safe and the process perfectly. Authentication page and authentication
scheme could be built using old technology. For that reason authentication page could be
broken easily. Many techniques are used for breaking authentication. Some of these
techniques are stealing session's keys, changing the form activities.
Way for attack
The User name and password could be taken by using some methods such as use the
fake URLs, session stealing, SQL injection and modifying the fixed parameters. The hacker
hacks the user name and password without the authentication through the higher level of
pages. Because the key developer code the authentication for the end user to provide the
access to the web page. The hacker produce the code like auth=0 or auth=1 for break the
authentication page without any authentication. The authentication page is bypassed with the
help of SQL injection. The user will provide the user names and password easily by sending
fake and look alike URLs. Because they think the request is come from usual websites.
Prevention ways
1. Protecting the data firmware patching
2. The metasploit is one of the authentication frameworks.
3. Check the two errors (SQL injection and Buffer overflow) in the time of development
process.
SQL statement that controls a web application database server. It commonly represents
relational database management system. SQL injection obligation could possibly affect any
website or web application that uses SQL based database. One of the oldest is vulnerability. It
is one of the most dangerous web application vulnerabilities. Session hijacking or cookie
hijacking is one in which unauthorised information can be tracked.
5. Description of the scenarios in 3 stages of the challenge
Challenge 1
Breaking the authentication
The authenticated users would be done the highly secured activities. So that
authentication is introduced. Many methods are introduced to provide authentication. But
these methods are not safe and the process perfectly. Authentication page and authentication
scheme could be built using old technology. For that reason authentication page could be
broken easily. Many techniques are used for breaking authentication. Some of these
techniques are stealing session's keys, changing the form activities.
Way for attack
The User name and password could be taken by using some methods such as use the
fake URLs, session stealing, SQL injection and modifying the fixed parameters. The hacker
hacks the user name and password without the authentication through the higher level of
pages. Because the key developer code the authentication for the end user to provide the
access to the web page. The hacker produce the code like auth=0 or auth=1 for break the
authentication page without any authentication. The authentication page is bypassed with the
help of SQL injection. The user will provide the user names and password easily by sending
fake and look alike URLs. Because they think the request is come from usual websites.
Prevention ways
1. Protecting the data firmware patching
2. The metasploit is one of the authentication frameworks.
3. Check the two errors (SQL injection and Buffer overflow) in the time of development
process.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Challenge2
Credit card theft
The main usage of the credit card is taking money through e-banking. The credit theft is
made due to customers sharing their card information to their family members, unknown
person and friends. When credit card are is missed or stolen by someone.at that time the
criminals take the card details by diverting the email. Some techniques are used for stealing
credit card information, that are balance transfer check, Malware, Skimming and Phishing
(Hacking,2011).
Preventing credit card steal
1. Use the spyware remover or spam filter software for security.
2. If you received any mail or message from the financial company. Check the website
and mobile number, you receiving it from the correct person. Corresponding website
and mobile number is present at the back side of your credit card.
Challenge3
Defacing the website
For defacing the website the most common method is SQL injection. To process the injection
attack SQL commands provide the injection of query. With the help of SQL DB or web page,
the user data input theft lead the injection of SQL.DB coding is small, so it is implemented
very easily by the user. By referring Relational database management system, the web
applications data server could be controlled. Either injection or insertion are consist by SQL.
It performs many operations, that is issuing commands to the Update or insert or delete the
database, content recovery of a given file placed on the data base management system and OS
(Halde, 2014).
.
SQL injection Testing
The SQL injection is used for software manipulation such as developing and testing.
It is used for fetch the data by accessing the database. Three testing methods are there in the
SQL injection.
1. Classical SQL Injection
Credit card theft
The main usage of the credit card is taking money through e-banking. The credit theft is
made due to customers sharing their card information to their family members, unknown
person and friends. When credit card are is missed or stolen by someone.at that time the
criminals take the card details by diverting the email. Some techniques are used for stealing
credit card information, that are balance transfer check, Malware, Skimming and Phishing
(Hacking,2011).
Preventing credit card steal
1. Use the spyware remover or spam filter software for security.
2. If you received any mail or message from the financial company. Check the website
and mobile number, you receiving it from the correct person. Corresponding website
and mobile number is present at the back side of your credit card.
Challenge3
Defacing the website
For defacing the website the most common method is SQL injection. To process the injection
attack SQL commands provide the injection of query. With the help of SQL DB or web page,
the user data input theft lead the injection of SQL.DB coding is small, so it is implemented
very easily by the user. By referring Relational database management system, the web
applications data server could be controlled. Either injection or insertion are consist by SQL.
It performs many operations, that is issuing commands to the Update or insert or delete the
database, content recovery of a given file placed on the data base management system and OS
(Halde, 2014).
.
SQL injection Testing
The SQL injection is used for software manipulation such as developing and testing.
It is used for fetch the data by accessing the database. Three testing methods are there in the
SQL injection.
1. Classical SQL Injection

2. SELECT statement
3. Stack Queries
Classical SQL Injection
Consider the SQL query
To validate a login to the user the query mentioned below is been used.If the login value is
assumed to be same with the database, then the login will be valuated or the value does not
make a login to the user. The input should be given through the web pages like as given
below(Center, 2016).
The query is:
The user values inserted by GET functions,then the website shows like
3. Stack Queries
Classical SQL Injection
Consider the SQL query
To validate a login to the user the query mentioned below is been used.If the login value is
assumed to be same with the database, then the login will be valuated or the value does not
make a login to the user. The input should be given through the web pages like as given
below(Center, 2016).
The query is:
The user values inserted by GET functions,then the website shows like
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SELECT statement
Consider the SQL query
this displays the current user login
The credentials results are checked via testing process.
String insert = "INSERT INTO customer(name,address,email) VALUES(?, ?, ?);";
PreparedStatementps = connection.prepareStatement(insert);
ps.setString(1, name);
ps.setString(2, addre);
ps.setString(3, email);
ResultSetrs = ps.executeQuery();
Consider the SQL query
this displays the current user login
The credentials results are checked via testing process.
String insert = "INSERT INTO customer(name,address,email) VALUES(?, ?, ?);";
PreparedStatementps = connection.prepareStatement(insert);
ps.setString(1, name);
ps.setString(2, addre);
ps.setString(3, email);
ResultSetrs = ps.executeQuery();
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
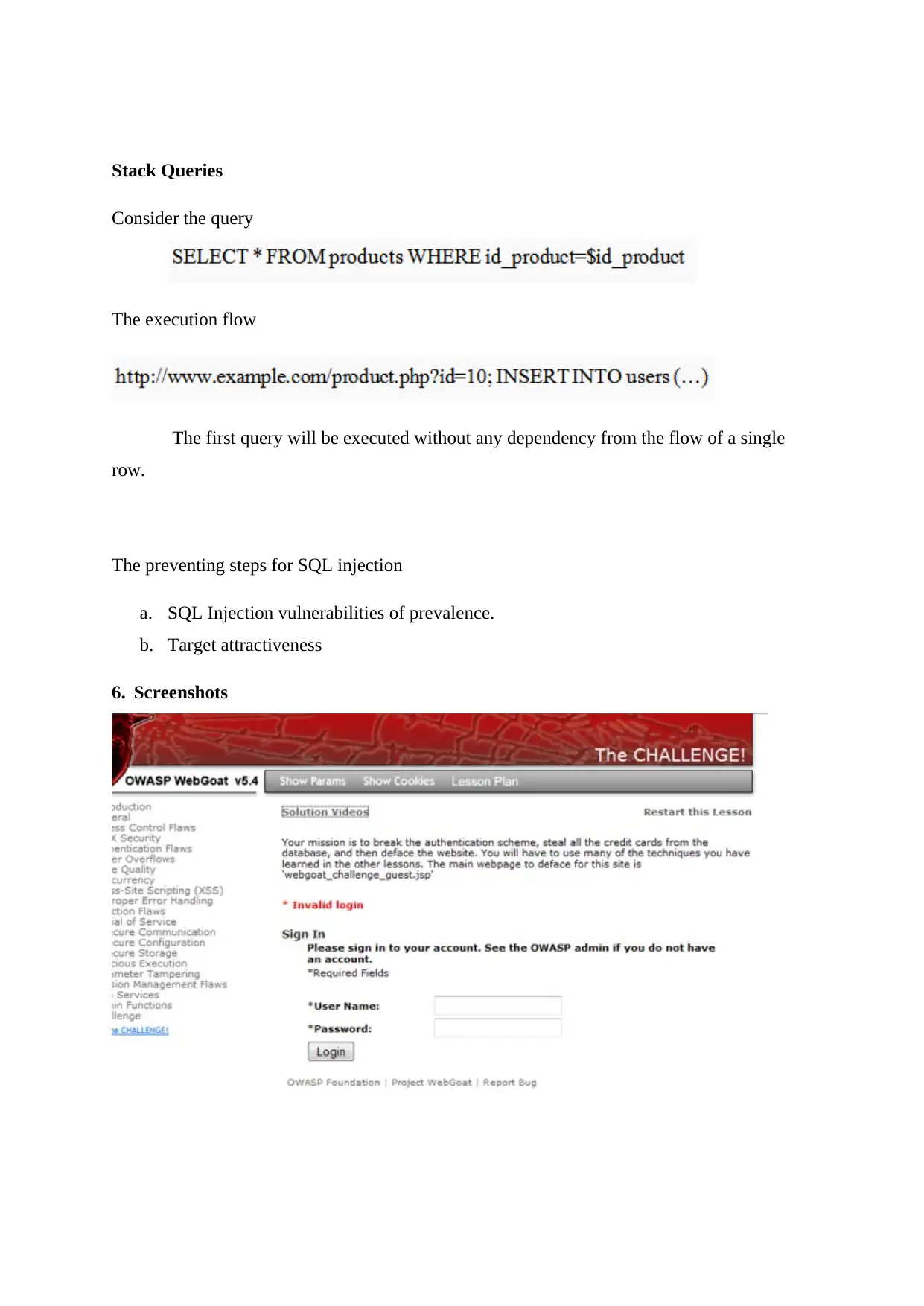
Stack Queries
Consider the query
The execution flow
The first query will be executed without any dependency from the flow of a single
row.
The preventing steps for SQL injection
a. SQL Injection vulnerabilities of prevalence.
b. Target attractiveness
6. Screenshots
Consider the query
The execution flow
The first query will be executed without any dependency from the flow of a single
row.
The preventing steps for SQL injection
a. SQL Injection vulnerabilities of prevalence.
b. Target attractiveness
6. Screenshots
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 28
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





