Information Systems Manager's Report: STP Network Upgrade Analysis
VerifiedAdded on 2020/04/07
|14
|3581
|32
Report
AI Summary
This report, prepared by a new information systems manager, analyzes the recently upgraded network of STP Limited, encompassing its head office and expanded premises. The report addresses limitations related to staff technical skills and outlines the scope, assumptions, and project background, including the purpose of the upgrade driven by business growth and the need for enhanced stock control, customer management, and accounting systems across multiple locations. The report details the project's goals, strategic alignment via a SWOT analysis, and network security considerations, including data protection, people, products, policies, procedures, and ISP security. It also covers other data threats, mobile device security, and a plan for hardware purchases, including acquisition strategies and the importance of an asset register. Furthermore, the report discusses business continuity through data backup, physical security, and staff succession planning, along with risk management strategies, security policies, and training. Recommendations are provided to ensure the upgraded information system is compliant with regulations and safeguards STP's data. The report emphasizes the importance of security measures to protect against various threats and ensure the smooth operation of the upgraded network.
[Document title]
[Document subtitle]
[DATE]
Student Name
Student Number
[Document subtitle]
[DATE]
Student Name
Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction...........................................................................................................................................2
Limitations.........................................................................................................................................2
Scope of the report............................................................................................................................2
Assumptions......................................................................................................................................2
Project Background...............................................................................................................................3
Purpose of STP Limited Network Upgrade.........................................................................................3
Scope of the project..........................................................................................................................3
Goal of the Project.............................................................................................................................3
Strategic Alignment of the Project.....................................................................................................4
Network Security...................................................................................................................................5
Securing Data.....................................................................................................................................5
People, products, policies and procedures........................................................................................5
ISP security and privacy considerations.............................................................................................5
Other threats to data.........................................................................................................................5
Mobile device security.......................................................................................................................6
Plan for Hardware Purchases.................................................................................................................7
Hardware Acquisition........................................................................................................................7
Staff feedback and reviews................................................................................................................7
Strategies of Hardware Purchase......................................................................................................7
Asset register.....................................................................................................................................7
Business Continuity...............................................................................................................................9
Data Backup.......................................................................................................................................9
Assets Physical Security.....................................................................................................................9
Staffs Succession Planning.................................................................................................................9
Risk Management................................................................................................................................10
Security policy.................................................................................................................................10
Training and awareness...................................................................................................................10
Conclusion...........................................................................................................................................11
Recommendations...............................................................................................................................12
References...........................................................................................................................................13
Introduction...........................................................................................................................................2
Limitations.........................................................................................................................................2
Scope of the report............................................................................................................................2
Assumptions......................................................................................................................................2
Project Background...............................................................................................................................3
Purpose of STP Limited Network Upgrade.........................................................................................3
Scope of the project..........................................................................................................................3
Goal of the Project.............................................................................................................................3
Strategic Alignment of the Project.....................................................................................................4
Network Security...................................................................................................................................5
Securing Data.....................................................................................................................................5
People, products, policies and procedures........................................................................................5
ISP security and privacy considerations.............................................................................................5
Other threats to data.........................................................................................................................5
Mobile device security.......................................................................................................................6
Plan for Hardware Purchases.................................................................................................................7
Hardware Acquisition........................................................................................................................7
Staff feedback and reviews................................................................................................................7
Strategies of Hardware Purchase......................................................................................................7
Asset register.....................................................................................................................................7
Business Continuity...............................................................................................................................9
Data Backup.......................................................................................................................................9
Assets Physical Security.....................................................................................................................9
Staffs Succession Planning.................................................................................................................9
Risk Management................................................................................................................................10
Security policy.................................................................................................................................10
Training and awareness...................................................................................................................10
Conclusion...........................................................................................................................................11
Recommendations...............................................................................................................................12
References...........................................................................................................................................13

Introduction
Being a new information systems manager hired by STP owner, this report entails analysis
and evaluation of the new or updated STP information system with the aim of ensuring that it
is compliant with all regulations and observes information privacy for the security of the STP
information or data at large.
Limitations
Considering the fact that staffs at STP have limited technical skills, the details of this report
provide may be limited at some point.
Scope of the report
The scope of this report revolve around the analysis of the STP upgraded network which will
serve the head office at Wollongong, recently bought premises at Brthurst and Lithgow and
another store in sydeney where the company has built a state of the art computerised
manufacturing facility.
Assumptions.
In this report, it is assumed that there is a Internet Service Provider that supplies the STP
Limited Company with ADSL internet connectivity via modem and switches.
Being a new information systems manager hired by STP owner, this report entails analysis
and evaluation of the new or updated STP information system with the aim of ensuring that it
is compliant with all regulations and observes information privacy for the security of the STP
information or data at large.
Limitations
Considering the fact that staffs at STP have limited technical skills, the details of this report
provide may be limited at some point.
Scope of the report
The scope of this report revolve around the analysis of the STP upgraded network which will
serve the head office at Wollongong, recently bought premises at Brthurst and Lithgow and
another store in sydeney where the company has built a state of the art computerised
manufacturing facility.
Assumptions.
In this report, it is assumed that there is a Internet Service Provider that supplies the STP
Limited Company with ADSL internet connectivity via modem and switches.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project Background
This part of the report identifies some of the challenges that STP Limited may face in the
process of ensuring that the upgraded information system complies with the privacy
regulations set. This entails evaluation of the purpose of this project, the scope of the project,
project goals and strategic alignment of this STP Limited project.
Purpose of STP Limited Network Upgrade
STP Limited has upgraded its information system in order to meet some of its goal of
managing their business that has since grown as a result of buying competitors operation and
premises at Bathurst and Lithgow as well as in sydney where they have a computerised
manufacturing state of art. This inturn has led to grwoth of customers number that seek
services from the company and therfore a customer management system was needed to avoid
ringing at their locations. A quality stock control system, in this case a distributed system was
essential due to the expansion of the company and the fact that it is operating from different
four locations. The upgrade of the STP information system enhances accessibility of the stock
management system by all employees thus making service delivery more effective and
efficient.
Scope of the project
This project aimed at facilitating a distributed information system that consists of a Stock
Control system, a customer management system and an accounting system. All these systems
were to be accessed in all the four locations, that is, Wollongong, Bathurst, Lithgow and
Sydney. Each location has its own distributed database and staff can access these systems
through ADSL internet connection using modem and network switch located in each office.
Wireless Access Points are also made part of this project in order to facilitate staff
connectivity using Bring Your Own Device (BYOB) mechanism. This network was
implemented in order to enhance scalability to all the four STP Limited offices in the four
locations as well as expand the operations of the staffs currently and in future.
Goal of the Project
The main goal of this project was to put into place an information system infrastructure that
helps in the management of the rapidly growing number of customers and business
operations now that the company’s operations have expanded as well. The STP company one
objective was to a have a stock control system that could be shared or distributed across all of
its location. The system was to be accessed by the employees and it provide accurate and
reliable stock details. Another goal was to put in place a customer management system that
could help the staff to serve and manage the large number of customer’s accounts. An
accounting system was also essential in order to manage the sales of products by the
company. Lastly, STP Limited implemented a website that helped in advertising and
marketing their available products for sale. The upgrade of the system was generally aimed at
improving service delivery across the company and improving customer - staff relation.
This part of the report identifies some of the challenges that STP Limited may face in the
process of ensuring that the upgraded information system complies with the privacy
regulations set. This entails evaluation of the purpose of this project, the scope of the project,
project goals and strategic alignment of this STP Limited project.
Purpose of STP Limited Network Upgrade
STP Limited has upgraded its information system in order to meet some of its goal of
managing their business that has since grown as a result of buying competitors operation and
premises at Bathurst and Lithgow as well as in sydney where they have a computerised
manufacturing state of art. This inturn has led to grwoth of customers number that seek
services from the company and therfore a customer management system was needed to avoid
ringing at their locations. A quality stock control system, in this case a distributed system was
essential due to the expansion of the company and the fact that it is operating from different
four locations. The upgrade of the STP information system enhances accessibility of the stock
management system by all employees thus making service delivery more effective and
efficient.
Scope of the project
This project aimed at facilitating a distributed information system that consists of a Stock
Control system, a customer management system and an accounting system. All these systems
were to be accessed in all the four locations, that is, Wollongong, Bathurst, Lithgow and
Sydney. Each location has its own distributed database and staff can access these systems
through ADSL internet connection using modem and network switch located in each office.
Wireless Access Points are also made part of this project in order to facilitate staff
connectivity using Bring Your Own Device (BYOB) mechanism. This network was
implemented in order to enhance scalability to all the four STP Limited offices in the four
locations as well as expand the operations of the staffs currently and in future.
Goal of the Project
The main goal of this project was to put into place an information system infrastructure that
helps in the management of the rapidly growing number of customers and business
operations now that the company’s operations have expanded as well. The STP company one
objective was to a have a stock control system that could be shared or distributed across all of
its location. The system was to be accessed by the employees and it provide accurate and
reliable stock details. Another goal was to put in place a customer management system that
could help the staff to serve and manage the large number of customer’s accounts. An
accounting system was also essential in order to manage the sales of products by the
company. Lastly, STP Limited implemented a website that helped in advertising and
marketing their available products for sale. The upgrade of the system was generally aimed at
improving service delivery across the company and improving customer - staff relation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
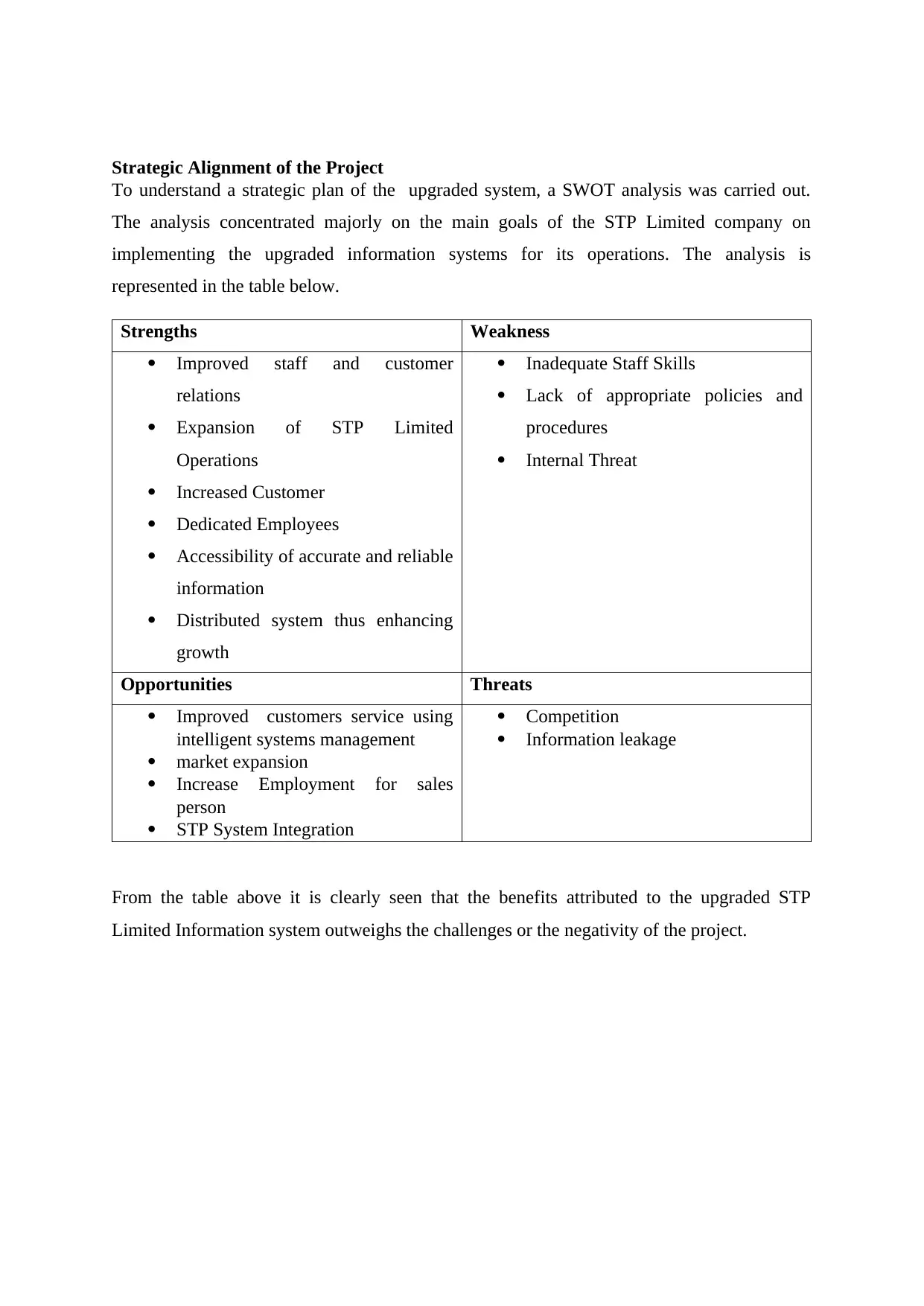
Strategic Alignment of the Project
To understand a strategic plan of the upgraded system, a SWOT analysis was carried out.
The analysis concentrated majorly on the main goals of the STP Limited company on
implementing the upgraded information systems for its operations. The analysis is
represented in the table below.
Strengths Weakness
Improved staff and customer
relations
Expansion of STP Limited
Operations
Increased Customer
Dedicated Employees
Accessibility of accurate and reliable
information
Distributed system thus enhancing
growth
Inadequate Staff Skills
Lack of appropriate policies and
procedures
Internal Threat
Opportunities Threats
Improved customers service using
intelligent systems management
market expansion
Increase Employment for sales
person
STP System Integration
Competition
Information leakage
From the table above it is clearly seen that the benefits attributed to the upgraded STP
Limited Information system outweighs the challenges or the negativity of the project.
To understand a strategic plan of the upgraded system, a SWOT analysis was carried out.
The analysis concentrated majorly on the main goals of the STP Limited company on
implementing the upgraded information systems for its operations. The analysis is
represented in the table below.
Strengths Weakness
Improved staff and customer
relations
Expansion of STP Limited
Operations
Increased Customer
Dedicated Employees
Accessibility of accurate and reliable
information
Distributed system thus enhancing
growth
Inadequate Staff Skills
Lack of appropriate policies and
procedures
Internal Threat
Opportunities Threats
Improved customers service using
intelligent systems management
market expansion
Increase Employment for sales
person
STP System Integration
Competition
Information leakage
From the table above it is clearly seen that the benefits attributed to the upgraded STP
Limited Information system outweighs the challenges or the negativity of the project.

Network Security
This consist the evaluation of al network components, which include technologies, used,
devices connected to it and how the STP network is designed. Considering that the whole
STP Limited information system was upgraded, there are some of the security issues that may
arise as of these implementations. One of the greatest security threat for this upgraded system
is the users of the system, which are the staff. Therefore, security of the information shared
and accessed in this system is paramount and can be protected via different technologies. The
system can be affected by malwares especially with the fact that BYOB mechanism was
implemented to accommodate more mobile devices to be connected (Keller, 2010). This
section therefore, explains some of the network security measures that STP Limited should
enhance in safeguarding their information.
Securing Data
Considering the rapid growth of STP Limited business operations, protection mechanism
ought to be put into place in ensuring the security of the large information being handled by
the company because of increased customers and business locations. To secure data, the
company should put in place internal mechanisms to manage employees, company’s products
as well as implement proper policies and procedures that defines how employees should
conduct themselves while using the network.
People, products, policies and procedures
The above three factors relate with each other. Policies and procedures provide a clear way in
which employees at STP Limited will follow while executing their services in selling of STP
product. These rules are very important considering that the company relies on internet to
conduct its service and therefore employees might engage in other activities that do not
benefit the organization but rather put it at risk. Policies and procedures ensures defines what
information is to be accessed, used and by who. It also outlines some of the rules that staff
ought to observe while using the companies network. The policies also dictate the network
design and configuration mechanism thus ensuring that the information shared across this
network is secured.
ISP security and privacy considerations
The upgraded version of the information system relies mostly on the internet for operations.
This therefore, means that the internet Service Provider for STP Limited Company should
ensure that their network is well secured and does not allow infiltration by malicious attacks
such as virus. The company therefore, should ensure that the ISP provides a more secured
network free from vulnerabilities that could be used by attackers to risk the privacy of the
STP Information System.
Other threats to data
The fact that the staffs at STP Limited do not have proper technical skills to operate the
information system in place makes them a big threat to the security of the STP data. The staff
could interfere with the information system knowingly or unknowingly thus calling for other
measures in ensuring security of the information system. These measures include; installation
and configuration of firewalls to filter unwanted actions, physical protection of information
system components, implementation of intrusion detection mechanism, authentication and
authorisation, use of anti-virus software and use of up to date software.
This consist the evaluation of al network components, which include technologies, used,
devices connected to it and how the STP network is designed. Considering that the whole
STP Limited information system was upgraded, there are some of the security issues that may
arise as of these implementations. One of the greatest security threat for this upgraded system
is the users of the system, which are the staff. Therefore, security of the information shared
and accessed in this system is paramount and can be protected via different technologies. The
system can be affected by malwares especially with the fact that BYOB mechanism was
implemented to accommodate more mobile devices to be connected (Keller, 2010). This
section therefore, explains some of the network security measures that STP Limited should
enhance in safeguarding their information.
Securing Data
Considering the rapid growth of STP Limited business operations, protection mechanism
ought to be put into place in ensuring the security of the large information being handled by
the company because of increased customers and business locations. To secure data, the
company should put in place internal mechanisms to manage employees, company’s products
as well as implement proper policies and procedures that defines how employees should
conduct themselves while using the network.
People, products, policies and procedures
The above three factors relate with each other. Policies and procedures provide a clear way in
which employees at STP Limited will follow while executing their services in selling of STP
product. These rules are very important considering that the company relies on internet to
conduct its service and therefore employees might engage in other activities that do not
benefit the organization but rather put it at risk. Policies and procedures ensures defines what
information is to be accessed, used and by who. It also outlines some of the rules that staff
ought to observe while using the companies network. The policies also dictate the network
design and configuration mechanism thus ensuring that the information shared across this
network is secured.
ISP security and privacy considerations
The upgraded version of the information system relies mostly on the internet for operations.
This therefore, means that the internet Service Provider for STP Limited Company should
ensure that their network is well secured and does not allow infiltration by malicious attacks
such as virus. The company therefore, should ensure that the ISP provides a more secured
network free from vulnerabilities that could be used by attackers to risk the privacy of the
STP Information System.
Other threats to data
The fact that the staffs at STP Limited do not have proper technical skills to operate the
information system in place makes them a big threat to the security of the STP data. The staff
could interfere with the information system knowingly or unknowingly thus calling for other
measures in ensuring security of the information system. These measures include; installation
and configuration of firewalls to filter unwanted actions, physical protection of information
system components, implementation of intrusion detection mechanism, authentication and
authorisation, use of anti-virus software and use of up to date software.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Mobile device security
The use of mobile devices such as laptops, tablets and smartphones has rapidly increased in
organizations such as STP Limited. These devices are easy to move around with across the
network. However, contrary to their flexibility and mobility, they come with security threats,
which include; downloading of malicious applications, physical security issues and access of
unsecured sites that might affect the integrity of the STP Network (Collett, 2017). Therefore,
STP should come up with protection mechanisms to ensure that mobile devices do not
compromise the company’s network.
With the BYOD mechanism in place at STP, which allows the staff to come with their own
devices and connect to the network wirelessly via the Wireless Access Points, puts the STP
Limited company to risks that may arise as a result of exposing important or private
information due to sharing of personal devices by the staff or non-staffs (Phifer, 2013) . In
addition, the use of personal devices by the staff to download software from unsecured sites
may lead to intrusion of malicious software into the entire STP network thus affecting or
paralyzing the network. Proper guidelines should be put into place to ensure that staffs who
come with their own devices do not use the in a manner that might compromise the security
of the STP network. They should also be trained on ensuring that they keep their information
in a more protected manner to avoid exposing the company’s information to unauthorised
persons.
The use of mobile devices such as laptops, tablets and smartphones has rapidly increased in
organizations such as STP Limited. These devices are easy to move around with across the
network. However, contrary to their flexibility and mobility, they come with security threats,
which include; downloading of malicious applications, physical security issues and access of
unsecured sites that might affect the integrity of the STP Network (Collett, 2017). Therefore,
STP should come up with protection mechanisms to ensure that mobile devices do not
compromise the company’s network.
With the BYOD mechanism in place at STP, which allows the staff to come with their own
devices and connect to the network wirelessly via the Wireless Access Points, puts the STP
Limited company to risks that may arise as a result of exposing important or private
information due to sharing of personal devices by the staff or non-staffs (Phifer, 2013) . In
addition, the use of personal devices by the staff to download software from unsecured sites
may lead to intrusion of malicious software into the entire STP network thus affecting or
paralyzing the network. Proper guidelines should be put into place to ensure that staffs who
come with their own devices do not use the in a manner that might compromise the security
of the STP network. They should also be trained on ensuring that they keep their information
in a more protected manner to avoid exposing the company’s information to unauthorised
persons.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Plan for Hardware Purchases
The hardware to be used at STP Limited Company in facilitating the operations of the
upgraded information system is of great importance. The purchase of hardware should factor
in the goals, performance and operations of the STP Limited Network. The hardware to be
used should ensure that the company has more advantage over their competitors (P,
2015).The hardware purchase plan is very important in ensuring the continuity of the STP
Operations smoothly without delays or interference.
Hardware Acquisition
The company should have a clear plan to acquire hardware that may fail or may be damaged
in the process of operations considering that the staff do not have technical skills to operate
such hardware. In order to enhance continuity, STP Limited should create emergency plans
on how to acquire new hardware in case unfortunate situations happens. This will reduce
delays and ensure that there is no loss in production.
Staff feedback and reviews
The STP Company should make the staff part of the hardware purchase plan. This may be
through regular review on the compatibility of the software in use with the hardware
versions. Also, the company should seek feedback from the staff on the performance of the
hardware systems in place. This will allow the management to realize what hardware
components are wanting and so forth.
Strategies of Hardware Purchase
STP Limited management should try to understand their business requirements by using their
asset register to determine chances of buying low cost hardware form their preferred supplies.
This will enable the company to come up with proper procurement strategies that will be
compatible with the business plan and that the purchases do not affect the progress of the
business operations due to financial constraints.
Asset register
This is a record of all the tools that are available in STP Limited Company (Intelligence,
2017). The company should have a clear record of each hardware device and where it is
located. The asset register help the management to monitor and manage all the assets of the
information system put in place at STP Limited Company. Asset Register is of much
importance as it helps the management to determine which hardware requires replacement in
order to improve performance or reduce security risks.
The table below represent an asset register for STP Limited located at the four locations of
this company.
The hardware to be used at STP Limited Company in facilitating the operations of the
upgraded information system is of great importance. The purchase of hardware should factor
in the goals, performance and operations of the STP Limited Network. The hardware to be
used should ensure that the company has more advantage over their competitors (P,
2015).The hardware purchase plan is very important in ensuring the continuity of the STP
Operations smoothly without delays or interference.
Hardware Acquisition
The company should have a clear plan to acquire hardware that may fail or may be damaged
in the process of operations considering that the staff do not have technical skills to operate
such hardware. In order to enhance continuity, STP Limited should create emergency plans
on how to acquire new hardware in case unfortunate situations happens. This will reduce
delays and ensure that there is no loss in production.
Staff feedback and reviews
The STP Company should make the staff part of the hardware purchase plan. This may be
through regular review on the compatibility of the software in use with the hardware
versions. Also, the company should seek feedback from the staff on the performance of the
hardware systems in place. This will allow the management to realize what hardware
components are wanting and so forth.
Strategies of Hardware Purchase
STP Limited management should try to understand their business requirements by using their
asset register to determine chances of buying low cost hardware form their preferred supplies.
This will enable the company to come up with proper procurement strategies that will be
compatible with the business plan and that the purchases do not affect the progress of the
business operations due to financial constraints.
Asset register
This is a record of all the tools that are available in STP Limited Company (Intelligence,
2017). The company should have a clear record of each hardware device and where it is
located. The asset register help the management to monitor and manage all the assets of the
information system put in place at STP Limited Company. Asset Register is of much
importance as it helps the management to determine which hardware requires replacement in
order to improve performance or reduce security risks.
The table below represent an asset register for STP Limited located at the four locations of
this company.
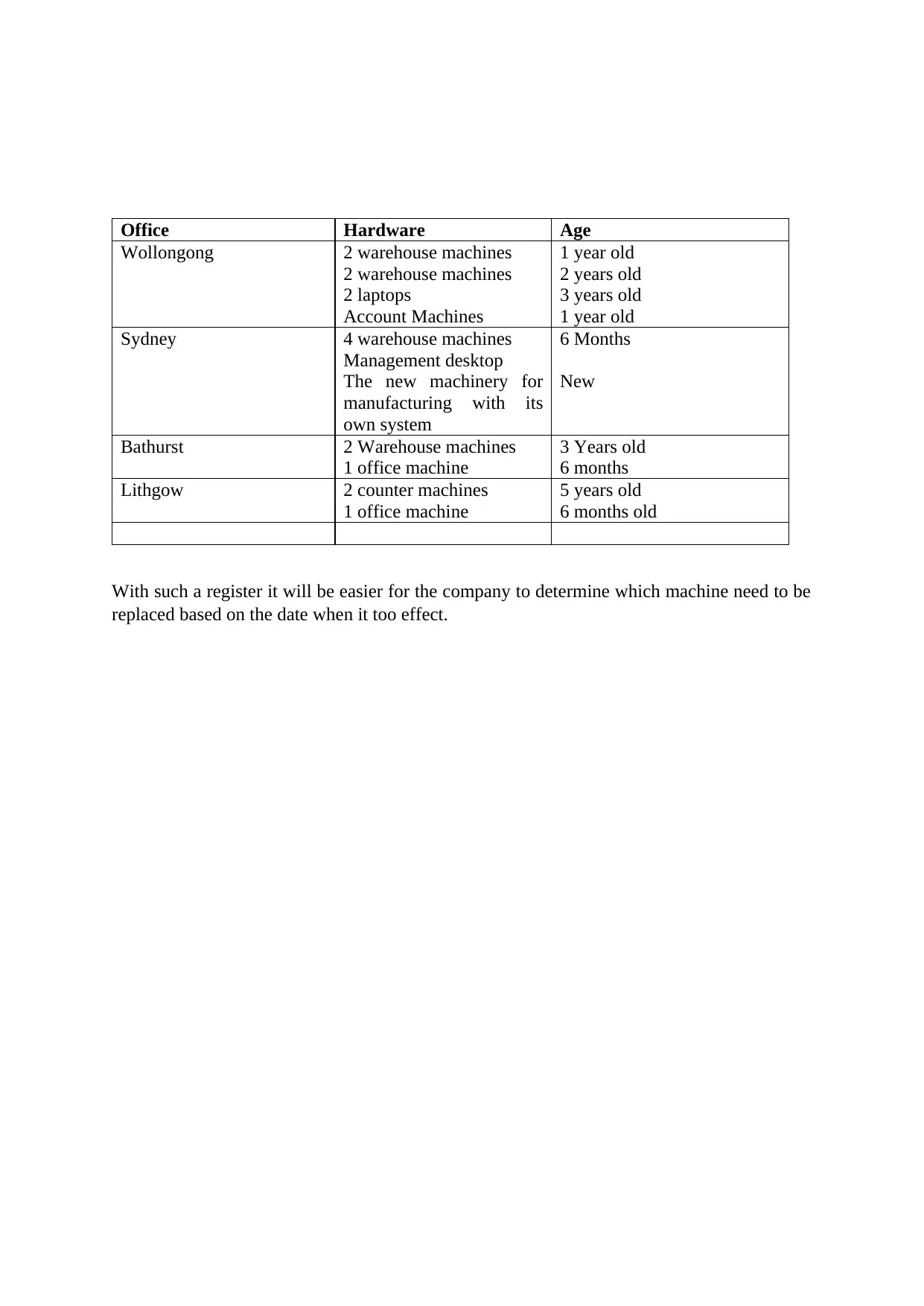
Office Hardware Age
Wollongong 2 warehouse machines
2 warehouse machines
2 laptops
Account Machines
1 year old
2 years old
3 years old
1 year old
Sydney 4 warehouse machines
Management desktop
The new machinery for
manufacturing with its
own system
6 Months
New
Bathurst 2 Warehouse machines
1 office machine
3 Years old
6 months
Lithgow 2 counter machines
1 office machine
5 years old
6 months old
With such a register it will be easier for the company to determine which machine need to be
replaced based on the date when it too effect.
Wollongong 2 warehouse machines
2 warehouse machines
2 laptops
Account Machines
1 year old
2 years old
3 years old
1 year old
Sydney 4 warehouse machines
Management desktop
The new machinery for
manufacturing with its
own system
6 Months
New
Bathurst 2 Warehouse machines
1 office machine
3 Years old
6 months
Lithgow 2 counter machines
1 office machine
5 years old
6 months old
With such a register it will be easier for the company to determine which machine need to be
replaced based on the date when it too effect.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Business Continuity
The implementation of distributed systems such as stock control system, which is hosted at
TradeGecko, Customer management system hosted at SalesForce and finally Accounting
System at MYOB, enhance business growth and continuity at STP Limited. The upgraded
system is hosted on cloud and can be accessed by staffs from any of the four locations.
Therefore, business continuity here refers to the fact that the operations of the STP Limited
will still proceed and there will be no loss of tools or information in case of any failure or
disruption that might affect the STP information system infrastructure in place (Institute,
2017). To ensure business continuity measures such as information backups, physical
equipment security and succession plans should be put into place. These three business
continuity measures are discussed below.
Data Backup
There are 2 to 4 desktops systems installed with standalone applications to handle point of
sale transactions at STP Limited. These transactions are carried out offline contrary to the
other applications that are hosted on cloud and do not need any backups mechanisms (IT,
2017). Therefore, the company should ensure that the POS transactions data is backed up and
stored separately in a more secured place. This will ensure that in case the POS desktops are
damaged or lost, STP Limited will be able to recover their data and carry on with their
operations. The backups can be stored on the cloud which ensures quality security and less
cost as there will be no physical monitoring or maintenance of the backups.
Assets Physical Security
The STP Limited should come up with security plans that protect the physical or business
assets from being interfered with, stolen by staffs or external persons (Hutter, 2016). Also in
case of incidents such as power outages, floods, fire outbreak among other calamities, the
company should have laid down quality disaster recovery plan that will enable STP to
overcome and enhance continuity of its operations.
Staffs Succession Planning
At some point the staffs may not be available at work due to sickness or even death. This
means that if that particular staff was the only one capable of doing the job, the operations of
the STP Limited will be highly affected. Therefore, the company should have clear
succession plans by training their staff who are technically illiterate. So that in the case of
such an event there will be no vacuum and the company management will be able to appoint
another person to oversee the operations of the STP Limited without having to affect the
entire or part of the company’s operation
The implementation of distributed systems such as stock control system, which is hosted at
TradeGecko, Customer management system hosted at SalesForce and finally Accounting
System at MYOB, enhance business growth and continuity at STP Limited. The upgraded
system is hosted on cloud and can be accessed by staffs from any of the four locations.
Therefore, business continuity here refers to the fact that the operations of the STP Limited
will still proceed and there will be no loss of tools or information in case of any failure or
disruption that might affect the STP information system infrastructure in place (Institute,
2017). To ensure business continuity measures such as information backups, physical
equipment security and succession plans should be put into place. These three business
continuity measures are discussed below.
Data Backup
There are 2 to 4 desktops systems installed with standalone applications to handle point of
sale transactions at STP Limited. These transactions are carried out offline contrary to the
other applications that are hosted on cloud and do not need any backups mechanisms (IT,
2017). Therefore, the company should ensure that the POS transactions data is backed up and
stored separately in a more secured place. This will ensure that in case the POS desktops are
damaged or lost, STP Limited will be able to recover their data and carry on with their
operations. The backups can be stored on the cloud which ensures quality security and less
cost as there will be no physical monitoring or maintenance of the backups.
Assets Physical Security
The STP Limited should come up with security plans that protect the physical or business
assets from being interfered with, stolen by staffs or external persons (Hutter, 2016). Also in
case of incidents such as power outages, floods, fire outbreak among other calamities, the
company should have laid down quality disaster recovery plan that will enable STP to
overcome and enhance continuity of its operations.
Staffs Succession Planning
At some point the staffs may not be available at work due to sickness or even death. This
means that if that particular staff was the only one capable of doing the job, the operations of
the STP Limited will be highly affected. Therefore, the company should have clear
succession plans by training their staff who are technically illiterate. So that in the case of
such an event there will be no vacuum and the company management will be able to appoint
another person to oversee the operations of the STP Limited without having to affect the
entire or part of the company’s operation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk Management
There are a number of risk issues that are involved now that the business at STP Limited has
grown and the fact that there is an upgraded information system in place (isaca, 2017). The
risk issues revolve on the privacy, optimisation and security of the new information system.
Some of the risks that STP Limited is likely to face are: Strategic, operational, technical,
managerial, financial and compliance risks respectively. These risks may arise due to
completion, theft, increased costs, calamities such as fire, information system attacks,
unavailability of the staff, among others. All these call for risk management measures by the
STP Limited in order to avoid any negative effect that might interfere with the smooth
operation of the company.
Security policy
In order to protect its assets and guidelines or procedures in which its staff ought to conduct
themselves while rendering services, STP Limited should have proper security policy. This
policy will communicate expectations of the company from the employees in the process of
safeguarding the company’s information and assets. Some of the security policy that should
be implemented include:
Use of antivirus – This will protect the company from malicious attacks by viruses directed to
its information system via the network (Paulsen, 2016).
Data Policy - This will provide staffs of STP Limited with proper definition on how the data
should be stored and used thus preventing data loss via theft.
Ethics policy – Ensures that staff conduct themselves in an ethical manner that observes
integrity and openness.
Access Management – This will determine the amount of information access each staff is
entitled to.
Wireless Communication policy – this will govern the connection and use of mobile devices
across the network.
Training and awareness
The Company should train its employees in order to equip them with proper skills that they
highly lack. This will ensure that the staffs are able to comply with the set standards bt STP
while conducting their duties. Also the staff should be made aware of the security threats that
are associated with information systems. This will help them avoid actions that could lead to
such threats.
There are a number of risk issues that are involved now that the business at STP Limited has
grown and the fact that there is an upgraded information system in place (isaca, 2017). The
risk issues revolve on the privacy, optimisation and security of the new information system.
Some of the risks that STP Limited is likely to face are: Strategic, operational, technical,
managerial, financial and compliance risks respectively. These risks may arise due to
completion, theft, increased costs, calamities such as fire, information system attacks,
unavailability of the staff, among others. All these call for risk management measures by the
STP Limited in order to avoid any negative effect that might interfere with the smooth
operation of the company.
Security policy
In order to protect its assets and guidelines or procedures in which its staff ought to conduct
themselves while rendering services, STP Limited should have proper security policy. This
policy will communicate expectations of the company from the employees in the process of
safeguarding the company’s information and assets. Some of the security policy that should
be implemented include:
Use of antivirus – This will protect the company from malicious attacks by viruses directed to
its information system via the network (Paulsen, 2016).
Data Policy - This will provide staffs of STP Limited with proper definition on how the data
should be stored and used thus preventing data loss via theft.
Ethics policy – Ensures that staff conduct themselves in an ethical manner that observes
integrity and openness.
Access Management – This will determine the amount of information access each staff is
entitled to.
Wireless Communication policy – this will govern the connection and use of mobile devices
across the network.
Training and awareness
The Company should train its employees in order to equip them with proper skills that they
highly lack. This will ensure that the staffs are able to comply with the set standards bt STP
while conducting their duties. Also the staff should be made aware of the security threats that
are associated with information systems. This will help them avoid actions that could lead to
such threats.

Conclusion
From this report, a clear evaluation of the upgraded information system is carried out and
some of the network security analysis. This report has outlined several security threats that
the STP limited should address to ensure business continuity and proper management of
processes. A thorough training of the staff should also be carried out in order to ensure that
the staffs are more conversant with the upgraded system. STP Limited should also formulate
policies to manage wireless network and BYOD devices in order to ensure that their network
is not compromised by the use of mobile devices.
From this report, a clear evaluation of the upgraded information system is carried out and
some of the network security analysis. This report has outlined several security threats that
the STP limited should address to ensure business continuity and proper management of
processes. A thorough training of the staff should also be carried out in order to ensure that
the staffs are more conversant with the upgraded system. STP Limited should also formulate
policies to manage wireless network and BYOD devices in order to ensure that their network
is not compromised by the use of mobile devices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





