ITC506 Assignment 1: IT Ethical Dilemma / Early Launch Case Study
VerifiedAdded on 2021/04/17
|10
|2090
|33
Case Study
AI Summary
This case study analyzes an ethical dilemma faced during the early launch of software. The scenario involves a project manager recommending the delivery of software without proper encryption to meet a deadline and secure a bonus, while the project director must decide whether to prioritize security or the early launch. The analysis, using the 'Doing Ethics Technique', covers the facts, issues, stakeholders, ethical implications, and available options, concluding that delaying the launch to incorporate necessary security measures is the best course of action. The assignment highlights the importance of data security, ethical decision-making, and the potential consequences of compromising security for short-term gains. The student has provided a comprehensive analysis, including the identification of ethical issues, evaluation of options, and justification of the chosen solution, supported by relevant literature. The case study also touches upon the impact on the organization, the potential for data breaches, and the importance of aligning project decisions with ethical principles.

SCHOOL OF COMPUTING AND MATHS, Charles Sturt University
IT Ethical Dilemma / Early Launch
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count: 1000
IT Ethical Dilemma / Early Launch
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count: 1000
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Title of you case study/scenario
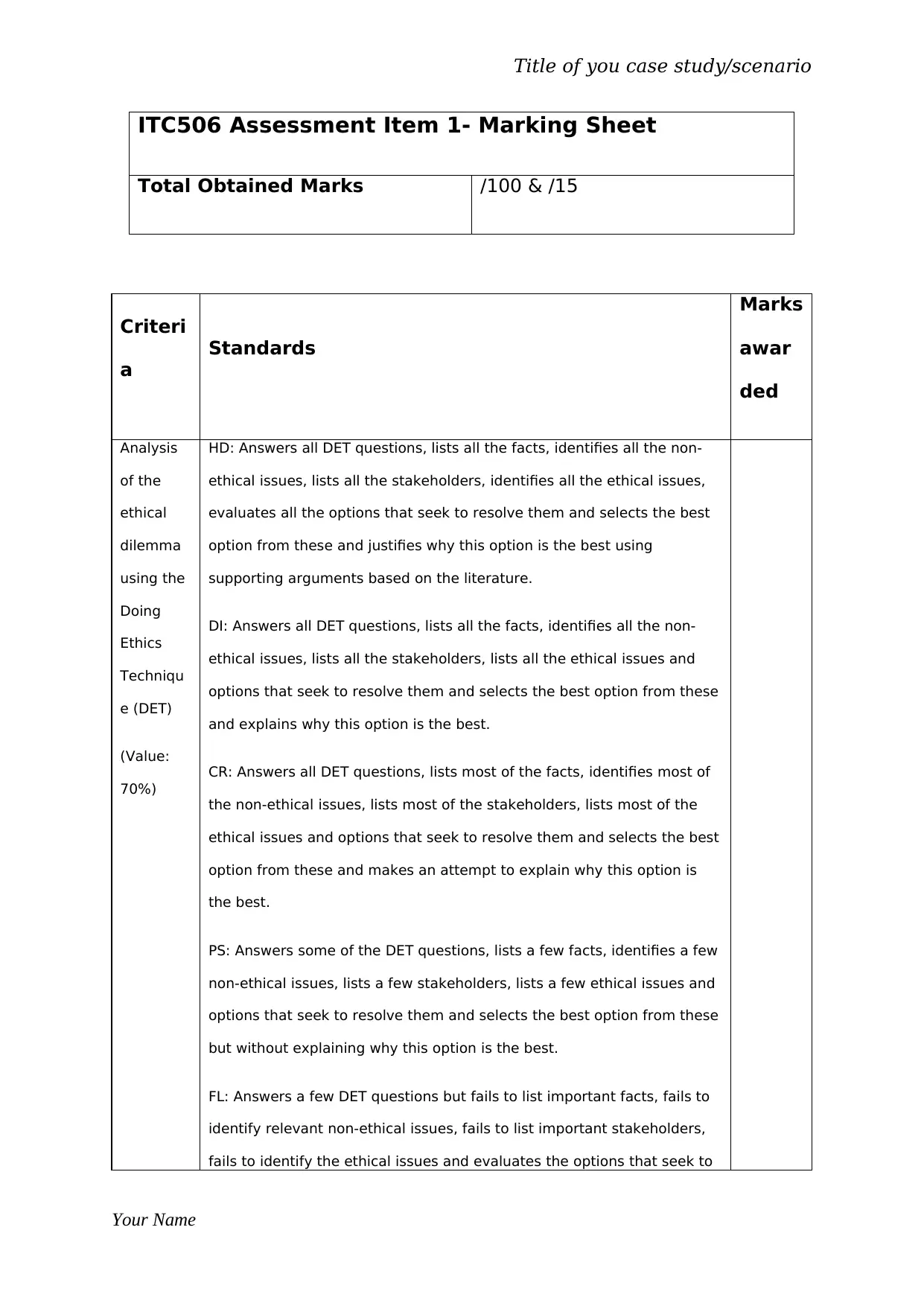
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteri
a
Standards
Marks
awar
ded
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Techniqu
e (DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is
the best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
Your Name
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteri
a
Standards
Marks
awar
ded
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Techniqu
e (DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is
the best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
Your Name
Title of you case study/scenario
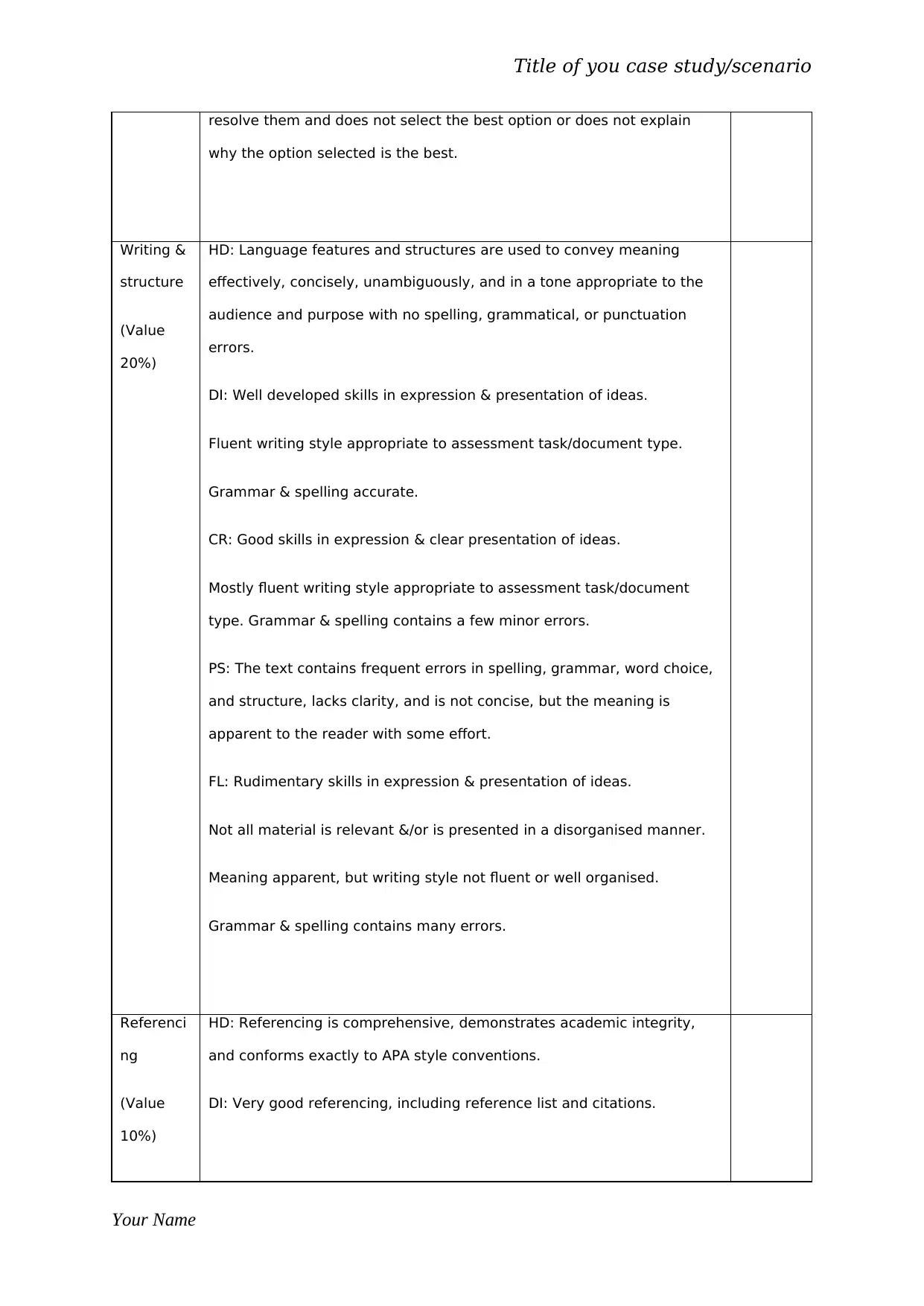
resolve them and does not select the best option or does not explain
why the option selected is the best.
Writing &
structure
(Value
20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity,
and conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
Your Name
resolve them and does not select the best option or does not explain
why the option selected is the best.
Writing &
structure
(Value
20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity,
and conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Title of you case study/scenario
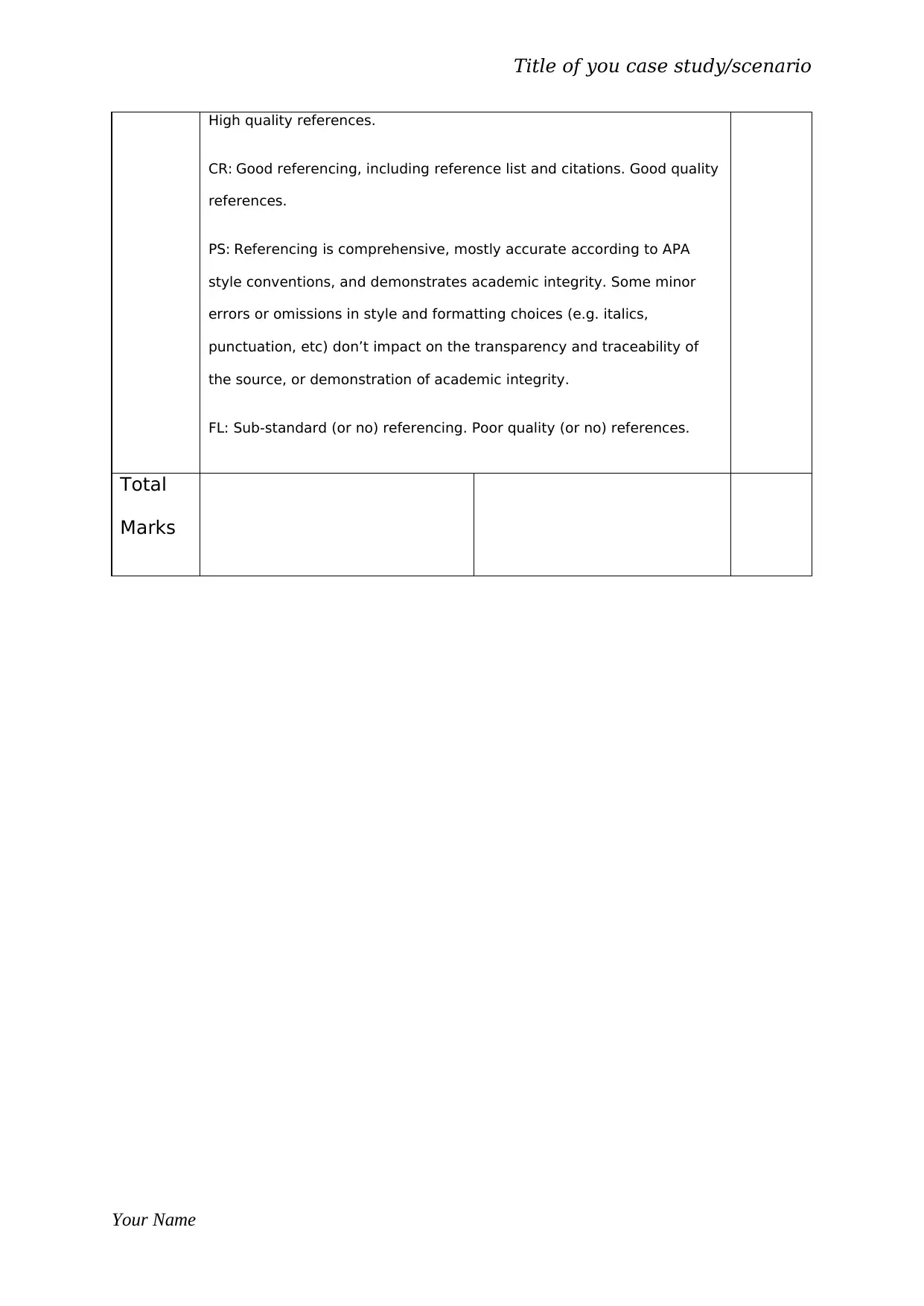
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
PS: Referencing is comprehensive, mostly accurate according to APA
style conventions, and demonstrates academic integrity. Some minor
errors or omissions in style and formatting choices (e.g. italics,
punctuation, etc) don’t impact on the transparency and traceability of
the source, or demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Your Name
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
PS: Referencing is comprehensive, mostly accurate according to APA
style conventions, and demonstrates academic integrity. Some minor
errors or omissions in style and formatting choices (e.g. italics,
punctuation, etc) don’t impact on the transparency and traceability of
the source, or demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Title of you case study/scenario
Q1. What's going on?
In the scenario which is selected i.e. Early launch the main issue, which is seen in the
case study, is that a software without proper encryption process is being delivered to the
client. This suggestion is mainly provided from the end of the project manager. The project
director who has the overall control over the working of the project would take the main
decision in this context. The main fear that the project directors has if the software is
delivered without any proper encryption is that if the hackers indulge themselves into illegal
activity. This could lead to a big problem form the point of view of the organization and it
would directly leak out the important data of the organization. On the other hand the
reputation of the organization would also be at stack as a software without any proper
encryption can be very easy to indulge into and get the information leaked out.
Q2. What are the facts?
The main facts, which are seen in the scenario, is that the project manager to deliver
the software before provides a recommendation and proper encryption process be involved
into the software. The main aspect, which is focused by doing this, is that the early delivery
of the software would result in a bonus, which would be provided due to the early launch of
the project. On the other hand, it was stated that a patch would be initiated few days after the
launch of the software, which would consist of all the necessary security aspects.
Q3. What are the issues?
The main issue, which is seen in the case study, is that a project without proper
encryption process can affect the working of the system. It can be stated that it is some sort of
security aspect ignored if the project is delivered to the client without any proper encryption
process involved into it. The project director would be directly responsible if the delivery of
Your Name
Q1. What's going on?
In the scenario which is selected i.e. Early launch the main issue, which is seen in the
case study, is that a software without proper encryption process is being delivered to the
client. This suggestion is mainly provided from the end of the project manager. The project
director who has the overall control over the working of the project would take the main
decision in this context. The main fear that the project directors has if the software is
delivered without any proper encryption is that if the hackers indulge themselves into illegal
activity. This could lead to a big problem form the point of view of the organization and it
would directly leak out the important data of the organization. On the other hand the
reputation of the organization would also be at stack as a software without any proper
encryption can be very easy to indulge into and get the information leaked out.
Q2. What are the facts?
The main facts, which are seen in the scenario, is that the project manager to deliver
the software before provides a recommendation and proper encryption process be involved
into the software. The main aspect, which is focused by doing this, is that the early delivery
of the software would result in a bonus, which would be provided due to the early launch of
the project. On the other hand, it was stated that a patch would be initiated few days after the
launch of the software, which would consist of all the necessary security aspects.
Q3. What are the issues?
The main issue, which is seen in the case study, is that a project without proper
encryption process can affect the working of the system. It can be stated that it is some sort of
security aspect ignored if the project is delivered to the client without any proper encryption
process involved into it. The project director would be directly responsible if the delivery of
Your Name

Title of you case study/scenario
the project is done without proper encryption involved into the aspect. This is due to the
factor that the overall working of the project is dependent on the project director and if the
software faces any sort of problem, relating to the security it would be project director who
would be responsible for the issue.
Q4. Who is affected?
The sector, which is affected in this scenario if the project is delivered without any
proper encryption, is the organization or the business body who implement and will use the
software. It can be seen that the hacker in this context can achieve most of the important data
of the organization. It can lead to a huge business loss. On the other hand, the reputation of
the organization would also be at stack as from the end of the organization the delivery of the
software should have incorporated the aspect of encryption as this is one of the most vital
aspect of security which can be involved in a software.
Q5. What are the ethical issues and their implications?
The main ethical issue that is seen is that a delivery of a software without proper
encryption involved into it. This issue can be considered as ethical issue for the reason that
the software can be easily be hacked by the hackers and this main result in possession of the
important data of the organization or the company. On the other hand the software is also
about to be launched without proper encryption as a matter of gaining a bonus due to early
delivery of the software.
Q6. What could have been done about it?
In this context, it can be stated that the launch of the software should have been
delayed up to the mark where the necessary security implementations could be made. In this
scenario the process of encryption. On the other hand the fact of providing a patch at a later
Your Name
the project is done without proper encryption involved into the aspect. This is due to the
factor that the overall working of the project is dependent on the project director and if the
software faces any sort of problem, relating to the security it would be project director who
would be responsible for the issue.
Q4. Who is affected?
The sector, which is affected in this scenario if the project is delivered without any
proper encryption, is the organization or the business body who implement and will use the
software. It can be seen that the hacker in this context can achieve most of the important data
of the organization. It can lead to a huge business loss. On the other hand, the reputation of
the organization would also be at stack as from the end of the organization the delivery of the
software should have incorporated the aspect of encryption as this is one of the most vital
aspect of security which can be involved in a software.
Q5. What are the ethical issues and their implications?
The main ethical issue that is seen is that a delivery of a software without proper
encryption involved into it. This issue can be considered as ethical issue for the reason that
the software can be easily be hacked by the hackers and this main result in possession of the
important data of the organization or the company. On the other hand the software is also
about to be launched without proper encryption as a matter of gaining a bonus due to early
delivery of the software.
Q6. What could have been done about it?
In this context, it can be stated that the launch of the software should have been
delayed up to the mark where the necessary security implementations could be made. In this
scenario the process of encryption. On the other hand the fact of providing a patch at a later
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Title of you case study/scenario
phase which would incorporate all the necessary security process can be problematic. The
main issue, which can arise in this case, is the compatibility with the software. The patch
would be incorporated into the system as a third party application or patch, which sometimes
would not involve as much security it should have involved. Most of the organisation tend to
delivery software to the client before the actual delivery time and making compromise with
the sector of security. The main effect of the activity would not be founded out in few days’
time but few days after it could lead to security aspects, which would affect the overall
working of the software. The aspect of resolving the issue later with a patch or an update
could create another set of problem. One of the most important problem, which can be faced
in this issue, is the aspect of compatibility.
Q7. What are the options?
The options, which are available in this context, have different implications. Firstly,
the option of program director surrenders to the pressure, this would result in the delivery of
the project without security aspects involved into it. Secondly the option of project director
ignoring the recommendation of the project manager would result in the software being
delivered late but would consist the necessary security aspects which would safeguard the
software from being hacked. Thirdly, the option of project director listens to the team and
delivers the project it would result in the software being delivered without the security
implementations.
Q8. Which option is the best and why?
Taking into consideration the above stated options one of the best option would be to
the project director ignoring the recommendation of the project manager. This is the best
option due to the factor that the software delivery in this case would be taking up some time
but the software would consist of the necessary security aspects, which would keep the
Your Name
phase which would incorporate all the necessary security process can be problematic. The
main issue, which can arise in this case, is the compatibility with the software. The patch
would be incorporated into the system as a third party application or patch, which sometimes
would not involve as much security it should have involved. Most of the organisation tend to
delivery software to the client before the actual delivery time and making compromise with
the sector of security. The main effect of the activity would not be founded out in few days’
time but few days after it could lead to security aspects, which would affect the overall
working of the software. The aspect of resolving the issue later with a patch or an update
could create another set of problem. One of the most important problem, which can be faced
in this issue, is the aspect of compatibility.
Q7. What are the options?
The options, which are available in this context, have different implications. Firstly,
the option of program director surrenders to the pressure, this would result in the delivery of
the project without security aspects involved into it. Secondly the option of project director
ignoring the recommendation of the project manager would result in the software being
delivered late but would consist the necessary security aspects which would safeguard the
software from being hacked. Thirdly, the option of project director listens to the team and
delivers the project it would result in the software being delivered without the security
implementations.
Q8. Which option is the best and why?
Taking into consideration the above stated options one of the best option would be to
the project director ignoring the recommendation of the project manager. This is the best
option due to the factor that the software delivery in this case would be taking up some time
but the software would consist of the necessary security aspects, which would keep the
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Title of you case study/scenario
system safe. This option would be benefiting the organization and the ethical aspect relating
to the early launch would not be faced.
Your Name
system safe. This option would be benefiting the organization and the ethical aspect relating
to the early launch would not be faced.
Your Name

Title of you case study/scenario
Bibliography
Bautista, S., Mazaj, J., & Cárdenas, M. (2018). Developing RRI Practices: The Role of the
ICT in Stakeholders’ Knowledge Exchange and Co-creation Processes. In Responsible
Research and Innovation Actions in Science Education, Gender and Ethics (pp. 21-26).
Springer, Cham.
Hilty, L. M., & Aebischer, B. (2015). Ict for sustainability: An emerging research field. In
ICT Innovations for Sustainability (pp. 3-36). Springer, Cham.
Jafarkarimi, H., Saadatdoost, R., Sim, A. T. H., & Hee, J. M. (2016). Behavioral intention in
social networking sites ethical dilemmas: An extended model based on Theory of Planned
Behavior. Computers in human behavior, 62, 545-561.
Ludwig, T., Reuter, C., & Pipek, V. (2016). From Publics to Communities: Researching the
Path of Shared Issues Through ICT. Computer Supported Cooperative Work (CSCW), 25(2-
3), 193-225.
Marcial, D. E. (2017). ICT social and ethical competency among teacher educators in the
philippines. Інформаційні технології і засоби навчання, (57, вип. 1), 96-103.
Mlitwa, N. B., & Alexander, B. M. (2015). Exploratory Articulation of a Post-Graduate
Diploma (PGDip) in Information & Communication Technology (ICT) at the Cape Peninsula
University of Technology. In the 8th International Conference of Education, Research and
Innovation (iCERi).
Shin, S.K., 2015. Teaching critical, ethical, and safe use of ICT to teachers.
Vanderlinde, R., Aesaert, K., & Braak, J. (2015). Measuring ICT use and contributing
conditions in primary schools. British Journal of Educational Technology, 46(5), 1056-1063.
Your Name
Bibliography
Bautista, S., Mazaj, J., & Cárdenas, M. (2018). Developing RRI Practices: The Role of the
ICT in Stakeholders’ Knowledge Exchange and Co-creation Processes. In Responsible
Research and Innovation Actions in Science Education, Gender and Ethics (pp. 21-26).
Springer, Cham.
Hilty, L. M., & Aebischer, B. (2015). Ict for sustainability: An emerging research field. In
ICT Innovations for Sustainability (pp. 3-36). Springer, Cham.
Jafarkarimi, H., Saadatdoost, R., Sim, A. T. H., & Hee, J. M. (2016). Behavioral intention in
social networking sites ethical dilemmas: An extended model based on Theory of Planned
Behavior. Computers in human behavior, 62, 545-561.
Ludwig, T., Reuter, C., & Pipek, V. (2016). From Publics to Communities: Researching the
Path of Shared Issues Through ICT. Computer Supported Cooperative Work (CSCW), 25(2-
3), 193-225.
Marcial, D. E. (2017). ICT social and ethical competency among teacher educators in the
philippines. Інформаційні технології і засоби навчання, (57, вип. 1), 96-103.
Mlitwa, N. B., & Alexander, B. M. (2015). Exploratory Articulation of a Post-Graduate
Diploma (PGDip) in Information & Communication Technology (ICT) at the Cape Peninsula
University of Technology. In the 8th International Conference of Education, Research and
Innovation (iCERi).
Shin, S.K., 2015. Teaching critical, ethical, and safe use of ICT to teachers.
Vanderlinde, R., Aesaert, K., & Braak, J. (2015). Measuring ICT use and contributing
conditions in primary schools. British Journal of Educational Technology, 46(5), 1056-1063.
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Title of you case study/scenario
Your Name
Your Name
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





