E-Commerce Security: Risks and Mitigation Measures
VerifiedAdded on 2023/04/21
|81
|18103
|393
AI Summary
This research paper discusses the risks associated with e-commerce transactions and explores different security measures to ensure secure e-commerce. It covers topics such as phishing attacks, denial of service attacks, and risk mitigation approaches. The study aims to provide recommendations for secure usage of e-commerce.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: E-COMMERCE SECURITY
Research Topic: E-Commerce Security
Name of Student
Name of University
Author Note
Research Topic: E-Commerce Security
Name of Student
Name of University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

E-COMMERCE SECURITY
Acknowledgement
This research has helped me improve my knowledge in the field of research along with my
analytical ability. This particular research has helped be to face challenges and has helped me in
conquering the challenges. Without the help of my supervisor, this research would not have been
possible. I would also like to thank my professors and fellow companions who have helped me in
performing this research study. I would thank all the research participants who have helped me to
conduct this research successfully. Lastly, I want to thank my family for encouraging me to
undertake this work.
Page | 1
Acknowledgement
This research has helped me improve my knowledge in the field of research along with my
analytical ability. This particular research has helped be to face challenges and has helped me in
conquering the challenges. Without the help of my supervisor, this research would not have been
possible. I would also like to thank my professors and fellow companions who have helped me in
performing this research study. I would thank all the research participants who have helped me to
conduct this research successfully. Lastly, I want to thank my family for encouraging me to
undertake this work.
Page | 1

E-COMMERCE SECURITY
Abstract
The research paper is related to ecommerce security and the risks in ecommerce transactions.
The research paper talks about different risks in the field of ecommerce. This particular study
aims in finding different approaches that can help in mitigation of the various risks and issues in
ecommerce. The basic risk management framework that is considered for this research study is
identification of the risk, assessment of risks and identification of various risk mitigation
approaches. The researcher has chosen a planned approach for this. The entire research has been
divided into certain manageable sections in form on different chapter. The research involves an
extensive literature review that identifies the risk and issues associated with ecommerce. The
major risk associated with the security in ecommerce involves denial of service attack, brute
force attack, Teardrop attack, phishing attack, social engineering and others. The risk mitigation
approaches for the identified risks are discussed in the research report. In order to identify the
different approaches to risk mitigation, data is collected from the literature review and from the
primary sources as well. The collected data from these sources has helped in understanding the
different approached to risk mitigation. Researcher paper identifies the research methods suitable
for this research. The aim of the research along with the research objective is identified in the
Introduction chapter of this paper. The research aims in identification of the major risks in
ecommerce transaction and to recommend the mitigation approaches for the risk. Collection of
primary data and quantitative data analysis have helped the researcher in finding solution to the
research problem. The research report further discusses the major research limitations and
discusses about the future work in this field of research. This is a small scale research in the field
of ecommerce.
Page | 2
Abstract
The research paper is related to ecommerce security and the risks in ecommerce transactions.
The research paper talks about different risks in the field of ecommerce. This particular study
aims in finding different approaches that can help in mitigation of the various risks and issues in
ecommerce. The basic risk management framework that is considered for this research study is
identification of the risk, assessment of risks and identification of various risk mitigation
approaches. The researcher has chosen a planned approach for this. The entire research has been
divided into certain manageable sections in form on different chapter. The research involves an
extensive literature review that identifies the risk and issues associated with ecommerce. The
major risk associated with the security in ecommerce involves denial of service attack, brute
force attack, Teardrop attack, phishing attack, social engineering and others. The risk mitigation
approaches for the identified risks are discussed in the research report. In order to identify the
different approaches to risk mitigation, data is collected from the literature review and from the
primary sources as well. The collected data from these sources has helped in understanding the
different approached to risk mitigation. Researcher paper identifies the research methods suitable
for this research. The aim of the research along with the research objective is identified in the
Introduction chapter of this paper. The research aims in identification of the major risks in
ecommerce transaction and to recommend the mitigation approaches for the risk. Collection of
primary data and quantitative data analysis have helped the researcher in finding solution to the
research problem. The research report further discusses the major research limitations and
discusses about the future work in this field of research. This is a small scale research in the field
of ecommerce.
Page | 2

E-COMMERCE SECURITY
Table of Contents
Table of Tables....................................................................................................................6
Table of Figures...................................................................................................................7
Chapter 1: Introduction........................................................................................................9
1.1. Background of the study...........................................................................................9
1.2. Research Aims and Objectives...............................................................................10
1.2.1. Aims of the study.............................................................................................10
1.2.2. Objectives of the study....................................................................................10
1.3. Research Questions.................................................................................................10
1.4. Problem Statement..................................................................................................11
1.5. Rationale of the study.............................................................................................11
1.6. Structure of the Study.............................................................................................12
Chapter 2: Literature Review.............................................................................................15
2.1. Introduction.............................................................................................................15
2.2. Concept of Ecommerce...........................................................................................16
2.2.1. Advantages of Ecommerce to Organization....................................................16
2.2.2. Advantages of Ecommerce to the Customers..................................................17
2.2.3. Advantages of Ecommerce to the Society.......................................................17
2.2.4. Disadvantages of ecommerce..........................................................................18
2.2.5. Ecommerce Models.........................................................................................19
Page | 3
Table of Contents
Table of Tables....................................................................................................................6
Table of Figures...................................................................................................................7
Chapter 1: Introduction........................................................................................................9
1.1. Background of the study...........................................................................................9
1.2. Research Aims and Objectives...............................................................................10
1.2.1. Aims of the study.............................................................................................10
1.2.2. Objectives of the study....................................................................................10
1.3. Research Questions.................................................................................................10
1.4. Problem Statement..................................................................................................11
1.5. Rationale of the study.............................................................................................11
1.6. Structure of the Study.............................................................................................12
Chapter 2: Literature Review.............................................................................................15
2.1. Introduction.............................................................................................................15
2.2. Concept of Ecommerce...........................................................................................16
2.2.1. Advantages of Ecommerce to Organization....................................................16
2.2.2. Advantages of Ecommerce to the Customers..................................................17
2.2.3. Advantages of Ecommerce to the Society.......................................................17
2.2.4. Disadvantages of ecommerce..........................................................................18
2.2.5. Ecommerce Models.........................................................................................19
Page | 3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

E-COMMERCE SECURITY
2.3. Risks associated with Ecommerce Transactions................................................20
2.4. Privacy and Security Risks in Ecommerce.............................................................21
2.4.1. Risks and Security in the Way of E-commerce Transactions..........................23
2.5. Ecommerce Risks and Mitigation...........................................................................25
2.6. Risk Management in reducing the risks in Ecommerce.........................................26
2.7. Proposed Risk Mitigation Approaches...................................................................27
2.8. Conceptual Framework...........................................................................................28
2.9. Chapter Summary...................................................................................................29
Chapter 3: Methodology and Research Activity...............................................................31
3.1. Introduction.............................................................................................................31
3.2. Research Activity........................................................................................................31
3.3. Research Philosophy...................................................................................................32
3.3.1. Justification of Research Philosophy: Positivism............................................33
3.4. Research Approach.....................................................................................................34
3.4.1. Justification for Research Approach: Inductive..............................................35
3.5. Research Design.........................................................................................................35
3.5.1. Justification for the chosen Research Design: Descriptive..............................36
3.6. Data Collection Process..............................................................................................36
3.7. Sampling Method........................................................................................................37
3.7.1. Sample Size.....................................................................................................37
Page | 4
2.3. Risks associated with Ecommerce Transactions................................................20
2.4. Privacy and Security Risks in Ecommerce.............................................................21
2.4.1. Risks and Security in the Way of E-commerce Transactions..........................23
2.5. Ecommerce Risks and Mitigation...........................................................................25
2.6. Risk Management in reducing the risks in Ecommerce.........................................26
2.7. Proposed Risk Mitigation Approaches...................................................................27
2.8. Conceptual Framework...........................................................................................28
2.9. Chapter Summary...................................................................................................29
Chapter 3: Methodology and Research Activity...............................................................31
3.1. Introduction.............................................................................................................31
3.2. Research Activity........................................................................................................31
3.3. Research Philosophy...................................................................................................32
3.3.1. Justification of Research Philosophy: Positivism............................................33
3.4. Research Approach.....................................................................................................34
3.4.1. Justification for Research Approach: Inductive..............................................35
3.5. Research Design.........................................................................................................35
3.5.1. Justification for the chosen Research Design: Descriptive..............................36
3.6. Data Collection Process..............................................................................................36
3.7. Sampling Method........................................................................................................37
3.7.1. Sample Size.....................................................................................................37
Page | 4

E-COMMERCE SECURITY
3.8. Data Analysis Method............................................................................................37
3.9. Ethical Consideration..................................................................................................38
Chapter 4: Results and Analysis........................................................................................39
4.1. Introduction.............................................................................................................39
4.2. Data Analysis..........................................................................................................39
4.2.1. Demographic Data Analysis............................................................................39
4.2.2. Quantitative Data Analysis..............................................................................43
4.3. Chapter Summary...............................................................................................58
Chapter 5: Discussion and Recommendations..................................................................60
5.1. Introduction.............................................................................................................60
5.2. Discussion...............................................................................................................60
5.3. Recommendations...................................................................................................68
5.4. Chapter Summary...................................................................................................69
Chapter 6: Conclusion, Key Findings and Future Work...................................................71
6.1. Conclusion..................................................................................................................71
6.2. Linking with Objectives.............................................................................................72
6.3. Recommendations.......................................................................................................74
6.4. Limitations of research...............................................................................................75
6.5 Future scope of the study.............................................................................................75
References..........................................................................................................................77
Page | 5
3.8. Data Analysis Method............................................................................................37
3.9. Ethical Consideration..................................................................................................38
Chapter 4: Results and Analysis........................................................................................39
4.1. Introduction.............................................................................................................39
4.2. Data Analysis..........................................................................................................39
4.2.1. Demographic Data Analysis............................................................................39
4.2.2. Quantitative Data Analysis..............................................................................43
4.3. Chapter Summary...............................................................................................58
Chapter 5: Discussion and Recommendations..................................................................60
5.1. Introduction.............................................................................................................60
5.2. Discussion...............................................................................................................60
5.3. Recommendations...................................................................................................68
5.4. Chapter Summary...................................................................................................69
Chapter 6: Conclusion, Key Findings and Future Work...................................................71
6.1. Conclusion..................................................................................................................71
6.2. Linking with Objectives.............................................................................................72
6.3. Recommendations.......................................................................................................74
6.4. Limitations of research...............................................................................................75
6.5 Future scope of the study.............................................................................................75
References..........................................................................................................................77
Page | 5

E-COMMERCE SECURITY
Table of Tables
Table 1: Representing the age demography of the respondents........................................39
Table 2: Representing responses of the respondents.........................................................40
Table 3: Reponses regarding the Type of Ecommerce......................................................42
Table 4: Responses about Ecommerce benefits.................................................................43
Table 5: Responses regarding ecommerce in increasing global reach..............................45
Table 6: Responses regarding ecommerce in increasing transactional Risks....................46
Table 7: Responses regarding the risks in ecommerce......................................................48
Table 8: Responses regarding the preventive measures in ecommerce.............................50
Table 9: Responses on Encryption as a Risk Management Approach..............................51
Table 10: Responses on digital signature as a Risk Management Approach....................53
Table 11: Responses on firewall as a Risk Management Approach..................................54
Table 12: Responses on regular security update as a Risk Management Approach..........56
Table 13: Responses on use of cryptographic technologies as Risk Management
Approach........................................................................................................................................57
Page | 6
Table of Tables
Table 1: Representing the age demography of the respondents........................................39
Table 2: Representing responses of the respondents.........................................................40
Table 3: Reponses regarding the Type of Ecommerce......................................................42
Table 4: Responses about Ecommerce benefits.................................................................43
Table 5: Responses regarding ecommerce in increasing global reach..............................45
Table 6: Responses regarding ecommerce in increasing transactional Risks....................46
Table 7: Responses regarding the risks in ecommerce......................................................48
Table 8: Responses regarding the preventive measures in ecommerce.............................50
Table 9: Responses on Encryption as a Risk Management Approach..............................51
Table 10: Responses on digital signature as a Risk Management Approach....................53
Table 11: Responses on firewall as a Risk Management Approach..................................54
Table 12: Responses on regular security update as a Risk Management Approach..........56
Table 13: Responses on use of cryptographic technologies as Risk Management
Approach........................................................................................................................................57
Page | 6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-COMMERCE SECURITY
Table of Figures
Figure 1: Representing the ecommerce Transaction.........................................................22
Figure 2: Representing the Conceptual Framework of the Research................................27
Figure 3: Representing the age of the respondents............................................................38
Figure 4: Representing the responses................................................................................40
Figure 5: The reposes regarding the type of ecommerce transaction................................41
Figure 6: Representing the responses about ecommerce benefit.......................................43
Figure 7: Representing the responses about ecommerce in global reach..........................44
Figure 8: Representing the responses about role of ecommerce in increasing transactional
Risks..............................................................................................................................................46
Figure 9: Representing the responses about the Risks in Ecommerce..............................48
Figure 10: Representing the preventive measures in Ecommerce.....................................50
Figure 11: Representing the responses regarding use of encryption as risk mitigation
approach.........................................................................................................................................51
Figure 12: Representing the responses regarding use of Digital Signature as risk
mitigation approach.......................................................................................................................53
Figure 13: Representing the responses regarding use of firewall as risk mitigation
approach.........................................................................................................................................54
Figure 14: Responses on regular security update as a Risk Management Approach........55
Figure 15: Responses on making use of cryptographic transaction as a Risk Management
Approach........................................................................................................................................56
Figure 16: Responses on the most significant Risk...........................................................59
Figure 17: Responses on Increase of Transactional Risks.................................................60
Page | 7
Table of Figures
Figure 1: Representing the ecommerce Transaction.........................................................22
Figure 2: Representing the Conceptual Framework of the Research................................27
Figure 3: Representing the age of the respondents............................................................38
Figure 4: Representing the responses................................................................................40
Figure 5: The reposes regarding the type of ecommerce transaction................................41
Figure 6: Representing the responses about ecommerce benefit.......................................43
Figure 7: Representing the responses about ecommerce in global reach..........................44
Figure 8: Representing the responses about role of ecommerce in increasing transactional
Risks..............................................................................................................................................46
Figure 9: Representing the responses about the Risks in Ecommerce..............................48
Figure 10: Representing the preventive measures in Ecommerce.....................................50
Figure 11: Representing the responses regarding use of encryption as risk mitigation
approach.........................................................................................................................................51
Figure 12: Representing the responses regarding use of Digital Signature as risk
mitigation approach.......................................................................................................................53
Figure 13: Representing the responses regarding use of firewall as risk mitigation
approach.........................................................................................................................................54
Figure 14: Responses on regular security update as a Risk Management Approach........55
Figure 15: Responses on making use of cryptographic transaction as a Risk Management
Approach........................................................................................................................................56
Figure 16: Responses on the most significant Risk...........................................................59
Figure 17: Responses on Increase of Transactional Risks.................................................60
Page | 7

E-COMMERCE SECURITY
Figure 18: Responses on use of encryption as risk mitigation approach...........................61
Figure 19: Responses on use of digital signature as risk mitigation approach..................62
Figure 20: Responses on use of firewall as risk mitigation approach...............................63
Figure 21: Responses on importance of regular security updates.....................................64
Figure 22: Responses on use of cryptographic technique as risk mitigation approach.....65
Page | 8
Figure 18: Responses on use of encryption as risk mitigation approach...........................61
Figure 19: Responses on use of digital signature as risk mitigation approach..................62
Figure 20: Responses on use of firewall as risk mitigation approach...............................63
Figure 21: Responses on importance of regular security updates.....................................64
Figure 22: Responses on use of cryptographic technique as risk mitigation approach.....65
Page | 8

E-COMMERCE SECURITY
Research Topic: E-Commerce Security
Chapter 1: Introduction
1.1. Background of the study
In this era of technology, e commerce has become a significant need of every individual.
E-commerce has become an important consideration as it offers the business a whole new range
of opportunities that includes increase of marketing opportunities along with the generation of
more sales. The reason behind generation of more sales can be benefits that are offered by e-
commerce. With e commerce, it becomes easier to buy and sell goods from the convenience of
home. Thus, it becomes mandatory to ensure security in e-commerce. E-commerce security can
be described as a set of protocols that can be used for safely guiding transaction in e commerce.
The e-commerce security although provides a number of benefits and convenience to the
consumers, any online transaction related to e commerce security can be risky as it is associated
with cyber risk and cybercrime. The threats associated with ecommerce include threats from
credit card fraud, hacking and loss of personal derails. Advanced e-commerce security is
implemented by major business organizations in order to ensure that any unauthorised e-
commerce transaction is prevented. E-commerce is a platform that offers the business with a
whole new range of opportunities and therefore, security risk management becomes vital for e
commerce. However, the ease, that an ecommerce system provides ensures that a large number
of customer will continue to use the e-commerce system. The e-commerce transactions are
important as it enhances the normal operations and normal business flow. Researchers prove that
a majority of the purchases in recent years are done online and this number is expected to
increase. Therefore, it becomes essential to ensure appropriate security in e-commerce. The
research will be evaluating the risks and the ecommerce security options.
Page | 9
Research Topic: E-Commerce Security
Chapter 1: Introduction
1.1. Background of the study
In this era of technology, e commerce has become a significant need of every individual.
E-commerce has become an important consideration as it offers the business a whole new range
of opportunities that includes increase of marketing opportunities along with the generation of
more sales. The reason behind generation of more sales can be benefits that are offered by e-
commerce. With e commerce, it becomes easier to buy and sell goods from the convenience of
home. Thus, it becomes mandatory to ensure security in e-commerce. E-commerce security can
be described as a set of protocols that can be used for safely guiding transaction in e commerce.
The e-commerce security although provides a number of benefits and convenience to the
consumers, any online transaction related to e commerce security can be risky as it is associated
with cyber risk and cybercrime. The threats associated with ecommerce include threats from
credit card fraud, hacking and loss of personal derails. Advanced e-commerce security is
implemented by major business organizations in order to ensure that any unauthorised e-
commerce transaction is prevented. E-commerce is a platform that offers the business with a
whole new range of opportunities and therefore, security risk management becomes vital for e
commerce. However, the ease, that an ecommerce system provides ensures that a large number
of customer will continue to use the e-commerce system. The e-commerce transactions are
important as it enhances the normal operations and normal business flow. Researchers prove that
a majority of the purchases in recent years are done online and this number is expected to
increase. Therefore, it becomes essential to ensure appropriate security in e-commerce. The
research will be evaluating the risks and the ecommerce security options.
Page | 9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

E-COMMERCE SECURITY
1.2. Research Aims and Objectives
In order to carry out the research in a specific manner, it becomes essential to identify the
aims and the objectives of the research. The thesis will be elaborating the process by which the
ecommerce security can be enforced in a transaction. The e commerce transaction is associated
with the generation of sensitive information and therefore appropriate security measures are
needed to be ensured. The research scope is to evaluate the existing literatures and collect data
about E commerce security to recommend appropriate solution to the e commerce security
problem.
1.2.1. Aims of the study
The aim of the study is to identify the risks associated with e commerce transaction and
to evaluate the different security measures that can help in ensuring secure e commerce
transaction.
1.2.2. Objectives of the study
The objectives identified for the thesis are as follows-
To identify the risks associated with the ecommerce transactions
To understand the source of risk related to ecommerce
To evaluate the risk mitigation options in E-commerce
To recommend secure usage of E-commerce
1.3. Research Questions
The primary research question identified for the thesis is identified below-
Page | 10
1.2. Research Aims and Objectives
In order to carry out the research in a specific manner, it becomes essential to identify the
aims and the objectives of the research. The thesis will be elaborating the process by which the
ecommerce security can be enforced in a transaction. The e commerce transaction is associated
with the generation of sensitive information and therefore appropriate security measures are
needed to be ensured. The research scope is to evaluate the existing literatures and collect data
about E commerce security to recommend appropriate solution to the e commerce security
problem.
1.2.1. Aims of the study
The aim of the study is to identify the risks associated with e commerce transaction and
to evaluate the different security measures that can help in ensuring secure e commerce
transaction.
1.2.2. Objectives of the study
The objectives identified for the thesis are as follows-
To identify the risks associated with the ecommerce transactions
To understand the source of risk related to ecommerce
To evaluate the risk mitigation options in E-commerce
To recommend secure usage of E-commerce
1.3. Research Questions
The primary research question identified for the thesis is identified below-
Page | 10

E-COMMERCE SECURITY
Why is E commerce Security Important?
In support to the primary research question, certain secondary research questions are
identified. The secondary research questions identified for the research are as follows-
What are the risks associated with e commerce?
Why is mitigation of the risk in ecommerce important?
1.4. Problem Statement
It is quite vital to identify the issues associated with e-commerce since the use of e
commerce is set to increase in future. Considering the rapid development and increase in use of e
commerce, the security risks associated with the ecommerce is needed to be evaluated as well. E
commerce is an advantage mainly because of the ease of access it provides along with the
advantage of performing a transaction online as per the convenience. Thus, it is clear that the use
of e-commerce is likely to increase over the years. It therefore becomes mandatory for business
organizations to ensure effective security measures so as to protect the e commerce transactions
from any sort of cyber threat. The risks management process in E commerce will incorporate
identification of the risks and issues and therefore it becomes essential to identify the process by
which the risks can be identified and mitigated. Since, mitigation of the risks related to e
commerce security is important, it becomes essential to identify appropriate process of achieving
the same.
1.5. Rationale of the study
The research aims in evaluating the security risks related to e-commerce. The risks in
ecommerce is a major issue since it is vulnerable to the phishing attacks, distributed denial of
Page | 11
Why is E commerce Security Important?
In support to the primary research question, certain secondary research questions are
identified. The secondary research questions identified for the research are as follows-
What are the risks associated with e commerce?
Why is mitigation of the risk in ecommerce important?
1.4. Problem Statement
It is quite vital to identify the issues associated with e-commerce since the use of e
commerce is set to increase in future. Considering the rapid development and increase in use of e
commerce, the security risks associated with the ecommerce is needed to be evaluated as well. E
commerce is an advantage mainly because of the ease of access it provides along with the
advantage of performing a transaction online as per the convenience. Thus, it is clear that the use
of e-commerce is likely to increase over the years. It therefore becomes mandatory for business
organizations to ensure effective security measures so as to protect the e commerce transactions
from any sort of cyber threat. The risks management process in E commerce will incorporate
identification of the risks and issues and therefore it becomes essential to identify the process by
which the risks can be identified and mitigated. Since, mitigation of the risks related to e
commerce security is important, it becomes essential to identify appropriate process of achieving
the same.
1.5. Rationale of the study
The research aims in evaluating the security risks related to e-commerce. The risks in
ecommerce is a major issue since it is vulnerable to the phishing attacks, distributed denial of
Page | 11

E-COMMERCE SECURITY
service attacks, man in the middle attack, malware attacks and others. Since the use of e-
commerce is likely to increase over the years, the possible risks in ecommerce is expected to
increase as well. There are certain challenges associated with the modern ecommerce system that
the researcher will be identifying. On identification of the risks, it becomes essential for the
researcher to identify the mitigation approach that can help in prevention of loss of any personal
information such as credit and debit card details. It has been observed that with the increase of
use of ecommerce, the security implications associated with ecommerce is needed to be
identified as well. Thus, this research is justified and the research results will help the different
business organizations in easier mitigation of the risks associated with the use of e-commerce in
different business organization.
1.6. Structure of the Study
The thesis paper will consists of six chapters that will guide the researcher is successful
completion of research project. Each chapter of the research project holds significance in
successful project completion. Therefore, the project researcher has subdivided the entire
research in smaller section so that every perspective of the research can be highlighted in an
efficient manner. The details of the chapter and its contents are highlighted in the following
paragraphs-
Chapter 1: Introduction: This chapter the very first chapter of the research that highlights the
basic concept of the topic chosen and the background of the topic so that a reader is able to
understand the theme of the research project. This project will be evaluating the major risks
associated with the e-commerce transactions and the chapter discusses the process by which the
researcher will be evaluating the risks and issues related to ecommerce transactions.
Page | 12
service attacks, man in the middle attack, malware attacks and others. Since the use of e-
commerce is likely to increase over the years, the possible risks in ecommerce is expected to
increase as well. There are certain challenges associated with the modern ecommerce system that
the researcher will be identifying. On identification of the risks, it becomes essential for the
researcher to identify the mitigation approach that can help in prevention of loss of any personal
information such as credit and debit card details. It has been observed that with the increase of
use of ecommerce, the security implications associated with ecommerce is needed to be
identified as well. Thus, this research is justified and the research results will help the different
business organizations in easier mitigation of the risks associated with the use of e-commerce in
different business organization.
1.6. Structure of the Study
The thesis paper will consists of six chapters that will guide the researcher is successful
completion of research project. Each chapter of the research project holds significance in
successful project completion. Therefore, the project researcher has subdivided the entire
research in smaller section so that every perspective of the research can be highlighted in an
efficient manner. The details of the chapter and its contents are highlighted in the following
paragraphs-
Chapter 1: Introduction: This chapter the very first chapter of the research that highlights the
basic concept of the topic chosen and the background of the topic so that a reader is able to
understand the theme of the research project. This project will be evaluating the major risks
associated with the e-commerce transactions and the chapter discusses the process by which the
researcher will be evaluating the risks and issues related to ecommerce transactions.
Page | 12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-COMMERCE SECURITY
Chapter 2: Literature Review: The literature review chapter is a vital part of the thesis as it will
be evaluating the major findings from the previous research papers in this field. The literature
review chapter builds an understanding of the chosen topic and helps the reader in understanding
the core concepts of the research. With the data collected from the previous research papers, the
literature review chapter forms the base of the research project and therefore, it is one of the vital
chapters.
Chapter 3: Research Methodology: The chapter of research methodology identifies the major
tools and techniques with which a research can be conducted. Research Methodology chapter
therefore act as a guiding path for conducting the research. The choice of appropriate research
methodology indicates that the research will be conducted in an appropriate manner. A choice of
appropriate research technique and research methods is necessary for appropriate data analysis
which in the next chapter of the research.
Chapter 4: Results and Analysis: The results and analysis chapter analyses the major findings
of the research by collecting data from various sources. The collected data undergoes the chosen
process of data analysis in this chapter. This chapter is vital for completion of the research as the
researcher collects data related to the research from various sources and analyses the collected
data. With appropriate analysis of the data, proper results are generated in concern to the
research topic.
Chapter 5: Discussion and Recommendations: With the identified data in the previous chapter
the results obtained are discussed in this chapter. The data analysed in the results and analysis
part is discussed in this section. On basis of the results obtained, the researcher will propose
Page | 13
Chapter 2: Literature Review: The literature review chapter is a vital part of the thesis as it will
be evaluating the major findings from the previous research papers in this field. The literature
review chapter builds an understanding of the chosen topic and helps the reader in understanding
the core concepts of the research. With the data collected from the previous research papers, the
literature review chapter forms the base of the research project and therefore, it is one of the vital
chapters.
Chapter 3: Research Methodology: The chapter of research methodology identifies the major
tools and techniques with which a research can be conducted. Research Methodology chapter
therefore act as a guiding path for conducting the research. The choice of appropriate research
methodology indicates that the research will be conducted in an appropriate manner. A choice of
appropriate research technique and research methods is necessary for appropriate data analysis
which in the next chapter of the research.
Chapter 4: Results and Analysis: The results and analysis chapter analyses the major findings
of the research by collecting data from various sources. The collected data undergoes the chosen
process of data analysis in this chapter. This chapter is vital for completion of the research as the
researcher collects data related to the research from various sources and analyses the collected
data. With appropriate analysis of the data, proper results are generated in concern to the
research topic.
Chapter 5: Discussion and Recommendations: With the identified data in the previous chapter
the results obtained are discussed in this chapter. The data analysed in the results and analysis
part is discussed in this section. On basis of the results obtained, the researcher will propose
Page | 13

E-COMMERCE SECURITY
certain recommendations that will help in mitigation of the risks associated with the e-commerce
transactions.
Chapter 6: Conclusion, Key Findings and Future Work: The last chapter of this research will
discuss the overall research topic and will conclude with the major findings of the research. In
this section, the researcher will be linking the research objectives to the findings of the research
for determining the success of the project and for determining the extent in which the researcher
is able to find solutions to the identified problems.
Page | 14
certain recommendations that will help in mitigation of the risks associated with the e-commerce
transactions.
Chapter 6: Conclusion, Key Findings and Future Work: The last chapter of this research will
discuss the overall research topic and will conclude with the major findings of the research. In
this section, the researcher will be linking the research objectives to the findings of the research
for determining the success of the project and for determining the extent in which the researcher
is able to find solutions to the identified problems.
Page | 14

E-COMMERCE SECURITY
Chapter 2: Literature Review
2.1. Introduction
The purpose of the literature review chapter is investigating the previous journals and
literatures in the field of ecommerce security. According to Fang et al. [1] the e commerce
security can be described as a set of protocols that helps in safely guiding different e commerce
transactions. It is essential to ensure that every e commerce transaction is secure in order to
protect the companies from different threats that include credit and debit card fraud. Appropriate
payment successful measures are needed to be ensured so that online payments are processed in
a successful manner. Any suspicious purchasing activity is needed to be identified in an
appropriate manner and the risk mitigation approach for the same is needed to be identified.
Similar researchers in the field of e commerce security have been conducted earlier as well. The
details of the research findings from previously published literatures will be evaluated in order to
collect data regarding the ecommerce risks, issues and security. According to Hossain et al [2].
analysis of the security issues related to the use of modern technologies are needed to be
identified. The main problem associated with different ecommerce transactions is that the
transactions are prone to security risks and security issues. Security is needed for e commerce
transaction. With the increase in use of ecommerce and online transactions, it is essential for the
customers to ensure safe e commerce transactions. The stored data of the customers should
ensure data confidentiality, integrity, data availability, authenticity, non repundiability and
encryption [9]. Data encryption is one of the most widely used aspects for ensuring same e
commerce transactions. The research will be evaluating the most commonly used security
protocols in internet transactions.
Page | 15
Chapter 2: Literature Review
2.1. Introduction
The purpose of the literature review chapter is investigating the previous journals and
literatures in the field of ecommerce security. According to Fang et al. [1] the e commerce
security can be described as a set of protocols that helps in safely guiding different e commerce
transactions. It is essential to ensure that every e commerce transaction is secure in order to
protect the companies from different threats that include credit and debit card fraud. Appropriate
payment successful measures are needed to be ensured so that online payments are processed in
a successful manner. Any suspicious purchasing activity is needed to be identified in an
appropriate manner and the risk mitigation approach for the same is needed to be identified.
Similar researchers in the field of e commerce security have been conducted earlier as well. The
details of the research findings from previously published literatures will be evaluated in order to
collect data regarding the ecommerce risks, issues and security. According to Hossain et al [2].
analysis of the security issues related to the use of modern technologies are needed to be
identified. The main problem associated with different ecommerce transactions is that the
transactions are prone to security risks and security issues. Security is needed for e commerce
transaction. With the increase in use of ecommerce and online transactions, it is essential for the
customers to ensure safe e commerce transactions. The stored data of the customers should
ensure data confidentiality, integrity, data availability, authenticity, non repundiability and
encryption [9]. Data encryption is one of the most widely used aspects for ensuring same e
commerce transactions. The research will be evaluating the most commonly used security
protocols in internet transactions.
Page | 15
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

E-COMMERCE SECURITY
2.2. Concept of Ecommerce
The process of buying and selling of the goods in an electronic platform that includes
mobile applications and internet is termed as ecommerce. An ecommerce transaction therefore
refers to online retail and to electronic transactions as well. There is a striking dissimilarity
between ecommerce and e-business. Ecommerce only deals with the services and transactions
between a seller and a consumer [3]. The e-business on the contrary relates to the entire process
of managing an online business. This research is related to exploration of various security issues
related to an ecommerce transaction. As indicated by Hossain et al. [2] the main reason behind
the security risk can be phishing attacks, unprotected online services and hacking.
The use of ecommerce has significantly increased over the years mainly because of the
advantages it offers. E commerce has an advantage over traditional commerce, as it offers
advantages to the organizations, who are in e commerce business, it provides benefits to the
consumers and is advantageous to the society as well [1]. With the use of ecommerce,
organizations can easily expand their business to the national and the international markets that
too in a very limited capital expanses. E commerce provides a huge customer base and global
reach which in beneficial for a business.
2.2.1. Advantages of Ecommerce to Organization
There are a number of advantages that are offered by ecommerce. These advantages are
as follows-
1. E-commerce helps the organization to reduce the cost of creating, distributing and
retrieving any paper based information and all the information associated with an ecommerce is
digitized. Thus, the use of ecommerce mainly reduces the paperwork.
Page | 16
2.2. Concept of Ecommerce
The process of buying and selling of the goods in an electronic platform that includes
mobile applications and internet is termed as ecommerce. An ecommerce transaction therefore
refers to online retail and to electronic transactions as well. There is a striking dissimilarity
between ecommerce and e-business. Ecommerce only deals with the services and transactions
between a seller and a consumer [3]. The e-business on the contrary relates to the entire process
of managing an online business. This research is related to exploration of various security issues
related to an ecommerce transaction. As indicated by Hossain et al. [2] the main reason behind
the security risk can be phishing attacks, unprotected online services and hacking.
The use of ecommerce has significantly increased over the years mainly because of the
advantages it offers. E commerce has an advantage over traditional commerce, as it offers
advantages to the organizations, who are in e commerce business, it provides benefits to the
consumers and is advantageous to the society as well [1]. With the use of ecommerce,
organizations can easily expand their business to the national and the international markets that
too in a very limited capital expanses. E commerce provides a huge customer base and global
reach which in beneficial for a business.
2.2.1. Advantages of Ecommerce to Organization
There are a number of advantages that are offered by ecommerce. These advantages are
as follows-
1. E-commerce helps the organization to reduce the cost of creating, distributing and
retrieving any paper based information and all the information associated with an ecommerce is
digitized. Thus, the use of ecommerce mainly reduces the paperwork.
Page | 16

E-COMMERCE SECURITY
2. The use of ecommerce helps in improving the brand image of the company
3. Ecommerce helps a particular to provide a better customer service
4. The use of e commerce helps in simplifying the different business processes thereby
making the business faster and efficient.
5. The use of ecommerce increases the productivity of the organization and reaching to
the customers becomes easy with ecommerce.
2.2.2. Advantages of Ecommerce to the Customers
The advantages of making use of ecommerce to the customers are as follows-
1. With the use of ecommerce, the business organizations are able to provide 24x7
support to the customers [2]. This acts as a great advantage to the customers as they can easily
enquire about any product or services anytime anywhere.
2. The option for Ecommerce provides the users with the option to compare and select
better and cheaper options.
3. Ecommerce provides an easier option for virtual auction.
4. Ecommerce increases the competitiveness between the different organizations, which
in turn forces the organizations to offer huge discounts to the customers.
2.2.3. Advantages of Ecommerce to the Society
Apart from the consumers and the organizations, the use of ecommerce in business
provides advantages to the society. These advantages are as follows-
Page | 17
2. The use of ecommerce helps in improving the brand image of the company
3. Ecommerce helps a particular to provide a better customer service
4. The use of e commerce helps in simplifying the different business processes thereby
making the business faster and efficient.
5. The use of ecommerce increases the productivity of the organization and reaching to
the customers becomes easy with ecommerce.
2.2.2. Advantages of Ecommerce to the Customers
The advantages of making use of ecommerce to the customers are as follows-
1. With the use of ecommerce, the business organizations are able to provide 24x7
support to the customers [2]. This acts as a great advantage to the customers as they can easily
enquire about any product or services anytime anywhere.
2. The option for Ecommerce provides the users with the option to compare and select
better and cheaper options.
3. Ecommerce provides an easier option for virtual auction.
4. Ecommerce increases the competitiveness between the different organizations, which
in turn forces the organizations to offer huge discounts to the customers.
2.2.3. Advantages of Ecommerce to the Society
Apart from the consumers and the organizations, the use of ecommerce in business
provides advantages to the society. These advantages are as follows-
Page | 17

E-COMMERCE SECURITY
1. With the help of ecommerce, a customer does not need to travel to a shop to buy any
product.
2. Ecommerce is now enabled in the rural areas as well [1]. This increases the access of
the different services and products to the rural areas which is otherwise not accessible there.
3. Ecommerce furthermore enables the government to deliver different public services
that includes healthcare, educational services and social services at a much lower or reduced
cost.
Thus, the use of ecommerce is expected to increase further in future. The use of
ecommerce increases the security risks as well [6]. Therefore, it becomes mandatory to ensure
that the risks in ecommerce are identified and eliminated.
2.2.4. Disadvantages of ecommerce
Apart from the various advantages, there are certain disadvantages of making use of
ecommerce as well. These disadvantages are as follows-
1. There is a lack of security of a system and reliability in implementation of ecommerce
[8]. The security and reliability can result in increase of the security issues.
2. It is observed that the software industry is evolving and it keeps on changing rapidly.
The ecommerce might experience a drastic change as well, which is a major disadvantage of e-
commerce.
3. The network bandwidth might cause an issue if a large number of requests are initiated
simultaneously, which is a major disadvantage of the ecommerce.
Page | 18
1. With the help of ecommerce, a customer does not need to travel to a shop to buy any
product.
2. Ecommerce is now enabled in the rural areas as well [1]. This increases the access of
the different services and products to the rural areas which is otherwise not accessible there.
3. Ecommerce furthermore enables the government to deliver different public services
that includes healthcare, educational services and social services at a much lower or reduced
cost.
Thus, the use of ecommerce is expected to increase further in future. The use of
ecommerce increases the security risks as well [6]. Therefore, it becomes mandatory to ensure
that the risks in ecommerce are identified and eliminated.
2.2.4. Disadvantages of ecommerce
Apart from the various advantages, there are certain disadvantages of making use of
ecommerce as well. These disadvantages are as follows-
1. There is a lack of security of a system and reliability in implementation of ecommerce
[8]. The security and reliability can result in increase of the security issues.
2. It is observed that the software industry is evolving and it keeps on changing rapidly.
The ecommerce might experience a drastic change as well, which is a major disadvantage of e-
commerce.
3. The network bandwidth might cause an issue if a large number of requests are initiated
simultaneously, which is a major disadvantage of the ecommerce.
Page | 18
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-COMMERCE SECURITY
4. For carrying on with the ecommerce business, the vendor needs different process of
web servers and other software.
5. Often it might be difficult to integrate ecommerce software to the existing database and
applications. This is another major disadvantage related to ecommerce [7].
6. There can be certain hardware and software compatibility issues related to ecommerce
as it might be incompatible to the different operating system.
7. The main issue related to ecommerce implementation is its cost of implementation and
building an application [5]. Launch of an ecommerce transaction can be considerably delayed as
a result of the mistake and lack of experience.
8. It is very vital to address privacy and security in online transactions which can be
counted as one major disadvantage related to online transactions.
9. Ecommerce applications need continuous internet access, which may not be affordable
to many potential customers and customers from rural areas.
2.2.5. Ecommerce Models
There are a number of ecommerce business models that can be segregated into following
subparts, which are as follows-
1. Business to Business (B2B)
2. Business to Consumer (B2C)
3. Consumer to Consumer (C2C)
Page | 19
4. For carrying on with the ecommerce business, the vendor needs different process of
web servers and other software.
5. Often it might be difficult to integrate ecommerce software to the existing database and
applications. This is another major disadvantage related to ecommerce [7].
6. There can be certain hardware and software compatibility issues related to ecommerce
as it might be incompatible to the different operating system.
7. The main issue related to ecommerce implementation is its cost of implementation and
building an application [5]. Launch of an ecommerce transaction can be considerably delayed as
a result of the mistake and lack of experience.
8. It is very vital to address privacy and security in online transactions which can be
counted as one major disadvantage related to online transactions.
9. Ecommerce applications need continuous internet access, which may not be affordable
to many potential customers and customers from rural areas.
2.2.5. Ecommerce Models
There are a number of ecommerce business models that can be segregated into following
subparts, which are as follows-
1. Business to Business (B2B)
2. Business to Consumer (B2C)
3. Consumer to Consumer (C2C)
Page | 19

E-COMMERCE SECURITY
4. Consumer to Business (C2B)
5. Business to Government (B2G)
6. Government to Business (G2B)
7. Government to Citizen (G2C)
Thus, ecommerce is widespread in different sections of a society. It is therefore, essential
to investigate different security measures that can ensure mitigation of the security risks and
issues related with the transactions in ecommerce.
2.3. Risks associated with Ecommerce Transactions
The research aims in identification of the security risks and issues related to ecommerce
transactions. The risks in a basic ecommerce transaction are evaluated in this section by
collecting data from the previously published research papers. As identified earlier, it is needed
to identify the major security risks related to ecommerce transactions.
Online transaction is associated with online security. There are a range of security threats
that are needed to be identified and addressed [4]. This includes malware and phishing attack and
spam mail. The major security risks are highlighted in the paragraphs below-
System Reliability: System reliability is a major issue related to online payment
system. Improper system reliability can show errors and bugs in ecommerce plugin [6]. In order
to address the issues related to system reliability, all the operating systems and APIs are needed
to be kept updated.
Page | 20
4. Consumer to Business (C2B)
5. Business to Government (B2G)
6. Government to Business (G2B)
7. Government to Citizen (G2C)
Thus, ecommerce is widespread in different sections of a society. It is therefore, essential
to investigate different security measures that can ensure mitigation of the security risks and
issues related with the transactions in ecommerce.
2.3. Risks associated with Ecommerce Transactions
The research aims in identification of the security risks and issues related to ecommerce
transactions. The risks in a basic ecommerce transaction are evaluated in this section by
collecting data from the previously published research papers. As identified earlier, it is needed
to identify the major security risks related to ecommerce transactions.
Online transaction is associated with online security. There are a range of security threats
that are needed to be identified and addressed [4]. This includes malware and phishing attack and
spam mail. The major security risks are highlighted in the paragraphs below-
System Reliability: System reliability is a major issue related to online payment
system. Improper system reliability can show errors and bugs in ecommerce plugin [6]. In order
to address the issues related to system reliability, all the operating systems and APIs are needed
to be kept updated.
Page | 20

E-COMMERCE SECURITY
Privacy Issues: One of the main areas of research includes privacy issue. The personal
data of the customers can be compromised and can be used for spamming, identity theft and
unsolicited marketing [7]. Therefore, certain security measures are needed to identified, which
includes making use of strong passwords and encryption.
Customer Dispute: Online transactions are prone to customer disputes. The customer
disputes include issues with an order or product that is not received. The dispute might also arise
in case any product does not fit to the online description.
Credit card Fraud: The credit card details that are stored for online transaction might be
stolen by the hackers [3]. The hacker might make use of the stolen card to make an online
purchase.
Intellectual Property Issues: The website images, product descriptions and the videos
related to a product might be copied by someone resulting in violation of someone else
intellectual property.
These are the major issues related to the use of ecommerce. As per the requirements of
the research, the security and the privacy issues related to ecommerce are evaluated.
2.4. Privacy and Security Risks in Ecommerce
With the invention of World Wide Web, the internet based electronic commerce has
evolved as well. As outlined by Savrul et al. the ecommerce has led to a new generation of the
associated security threats. There are several threats related to the ecommerce business that can
badly affect the ecommerce business [12]. The increasing threats in ecommerce often give rise to
access and connectivity issues. The technical attacks can be considered as the most challenging
Page | 21
Privacy Issues: One of the main areas of research includes privacy issue. The personal
data of the customers can be compromised and can be used for spamming, identity theft and
unsolicited marketing [7]. Therefore, certain security measures are needed to identified, which
includes making use of strong passwords and encryption.
Customer Dispute: Online transactions are prone to customer disputes. The customer
disputes include issues with an order or product that is not received. The dispute might also arise
in case any product does not fit to the online description.
Credit card Fraud: The credit card details that are stored for online transaction might be
stolen by the hackers [3]. The hacker might make use of the stolen card to make an online
purchase.
Intellectual Property Issues: The website images, product descriptions and the videos
related to a product might be copied by someone resulting in violation of someone else
intellectual property.
These are the major issues related to the use of ecommerce. As per the requirements of
the research, the security and the privacy issues related to ecommerce are evaluated.
2.4. Privacy and Security Risks in Ecommerce
With the invention of World Wide Web, the internet based electronic commerce has
evolved as well. As outlined by Savrul et al. the ecommerce has led to a new generation of the
associated security threats. There are several threats related to the ecommerce business that can
badly affect the ecommerce business [12]. The increasing threats in ecommerce often give rise to
access and connectivity issues. The technical attacks can be considered as the most challenging
Page | 21
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

E-COMMERCE SECURITY
type of the security compromise in e commerce. The perpetrators of the different technical
attacks include denial of service attacks that typically targets the sites and services related to high
profile web servers
Denial of service attack is a major reason behind the privacy and security issue in
ecommerce as the DOS attack mainly involves an overwhelming server and a network of website
that intends to paralyze a normal activity [11]. Therefore, defending against the DoS attack is
therefore considered to be one of the most challenging security issue related to ecommerce. The
prevention of such attack includes tracing of the source of attack. This is a difficult step since the
use of incorrect or spoofed IP address can hide the true origin of the attack.
The symptoms of the denial of service attacks are as follows-
1. Denial of service attack is related to slow network performance
2. This attack is related to unavailability of particular web site
3. Inability of accessing a website
4. A considerable increase in the number of email spams
A DoS attack can be conducted in number of ways which includes-
1. ICMP Flooding
2. Teardrop Attack
3. Phlashing
Page | 22
type of the security compromise in e commerce. The perpetrators of the different technical
attacks include denial of service attacks that typically targets the sites and services related to high
profile web servers
Denial of service attack is a major reason behind the privacy and security issue in
ecommerce as the DOS attack mainly involves an overwhelming server and a network of website
that intends to paralyze a normal activity [11]. Therefore, defending against the DoS attack is
therefore considered to be one of the most challenging security issue related to ecommerce. The
prevention of such attack includes tracing of the source of attack. This is a difficult step since the
use of incorrect or spoofed IP address can hide the true origin of the attack.
The symptoms of the denial of service attacks are as follows-
1. Denial of service attack is related to slow network performance
2. This attack is related to unavailability of particular web site
3. Inability of accessing a website
4. A considerable increase in the number of email spams
A DoS attack can be conducted in number of ways which includes-
1. ICMP Flooding
2. Teardrop Attack
3. Phlashing
Page | 22

E-COMMERCE SECURITY
Thus, the denial of service attack can be considered as one of the greatest security fear for
the IT managers associated with ecommerce transactions.
The security issues related to ecommerce include Brute Force Attack, which include a
method of defeating a specific cryptographic scheme. This is mainly done by trying a large
number of possible keys [14]. Although the Brute Force attack is often perceived as low tech in
nature, it is still one of the significant reasons behind the security issues in ecommerce.
Apart from that, there are certain non-technical attacks that are needed to be considered
in evaluation of the risks and issues in ecommerce. One of such attack is phishing attack.
Phishing is considered to be a criminally fraudulent process related to the attempting and
acquiring of sensitive information. The scams related to phishing are set to be carried out by
dropping emails to the victims. These fraudulent email seeks to collect sensitive information
from the victims.
The list of non-technical attacks related to ecommerce security includes social
engineering as well. Social engineering is considered to be an art of manipulating people into
performing certain actions that is capable of divulging the confidential information [17]. Social
engineering technique include making use of interactive voice regarding and phone phishing to
get the victim divulge about the sensitive information.
2.4.1. Risks and Security in the Way of E-commerce Transactions
The success and failure of an ecommerce business mainly relates on the security and
privacy. With the increasing popularization of the electronic payment the security issues in
ecommerce have increased as well. Thefts to the personal and private data along with
unauthorised access can result in major security issues related to transactions in ecommerce.
Page | 23
Thus, the denial of service attack can be considered as one of the greatest security fear for
the IT managers associated with ecommerce transactions.
The security issues related to ecommerce include Brute Force Attack, which include a
method of defeating a specific cryptographic scheme. This is mainly done by trying a large
number of possible keys [14]. Although the Brute Force attack is often perceived as low tech in
nature, it is still one of the significant reasons behind the security issues in ecommerce.
Apart from that, there are certain non-technical attacks that are needed to be considered
in evaluation of the risks and issues in ecommerce. One of such attack is phishing attack.
Phishing is considered to be a criminally fraudulent process related to the attempting and
acquiring of sensitive information. The scams related to phishing are set to be carried out by
dropping emails to the victims. These fraudulent email seeks to collect sensitive information
from the victims.
The list of non-technical attacks related to ecommerce security includes social
engineering as well. Social engineering is considered to be an art of manipulating people into
performing certain actions that is capable of divulging the confidential information [17]. Social
engineering technique include making use of interactive voice regarding and phone phishing to
get the victim divulge about the sensitive information.
2.4.1. Risks and Security in the Way of E-commerce Transactions
The success and failure of an ecommerce business mainly relates on the security and
privacy. With the increasing popularization of the electronic payment the security issues in
ecommerce have increased as well. Thefts to the personal and private data along with
unauthorised access can result in major security issues related to transactions in ecommerce.
Page | 23
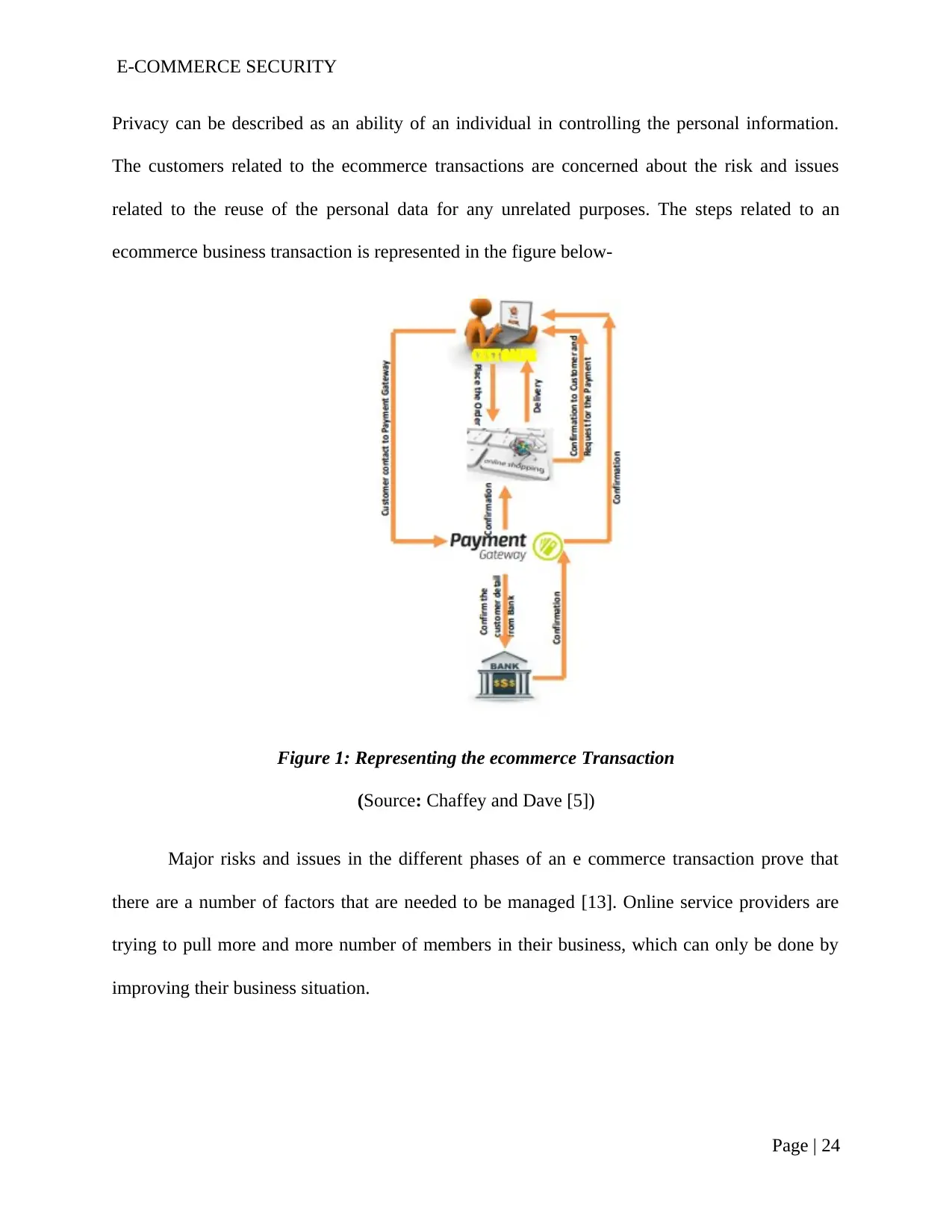
E-COMMERCE SECURITY
Privacy can be described as an ability of an individual in controlling the personal information.
The customers related to the ecommerce transactions are concerned about the risk and issues
related to the reuse of the personal data for any unrelated purposes. The steps related to an
ecommerce business transaction is represented in the figure below-
Figure 1: Representing the ecommerce Transaction
(Source: Chaffey and Dave [5])
Major risks and issues in the different phases of an e commerce transaction prove that
there are a number of factors that are needed to be managed [13]. Online service providers are
trying to pull more and more number of members in their business, which can only be done by
improving their business situation.
Page | 24
Privacy can be described as an ability of an individual in controlling the personal information.
The customers related to the ecommerce transactions are concerned about the risk and issues
related to the reuse of the personal data for any unrelated purposes. The steps related to an
ecommerce business transaction is represented in the figure below-
Figure 1: Representing the ecommerce Transaction
(Source: Chaffey and Dave [5])
Major risks and issues in the different phases of an e commerce transaction prove that
there are a number of factors that are needed to be managed [13]. Online service providers are
trying to pull more and more number of members in their business, which can only be done by
improving their business situation.
Page | 24
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-COMMERCE SECURITY
Apart from that, software management is considered to be a substantially larger problem
related to ecommerce. Hackers discover newer vulnerabilities in the attack and therefore, it is
necessary to identify appropriate security measures for the same.
However, understanding the security will be incomplete without the actual analysis of
underlying the economic issues related to ecommerce transaction. Therefore, certain security
mechanisms are needed to be identified that can be used to govern the compatibility of the
ecommerce system.
2.5. Ecommerce Risks and Mitigation
There are several risks involved with the ecommerce and therefore the need for
identification of the risk mitigation approaches are needed to be identified. With the increasing
in the different processes of attacks in ecommerce, privacy has gradually become a major
concern for the consumers [16]. Ecommerce involves transactions between the strangers.
Therefore, identification of the risk mitigation approaches is essential. Ecommerce can be a
tremendous boon for any small business. A business needs to ensure certain risk mitigation
processes for reducing the chances of business loss. The risk mitigation approaches that can be
implemented in mitigation of the risks related to ecommerce transactions is discussed in the
following paragraphs-
It is essential to achieve and maintain the PCI compliance in order to ensure that the
security risks and issues related to ecommerce are controlled. Furthermore, it is essential to keep
the shopping cart software updated [8]. An updated software can help in mitigation of the risks
and issues in ecommerce security. The steps that a consumer and a business can undertake in
mitigation of the risks associated with ecommerce are as follows-
Page | 25
Apart from that, software management is considered to be a substantially larger problem
related to ecommerce. Hackers discover newer vulnerabilities in the attack and therefore, it is
necessary to identify appropriate security measures for the same.
However, understanding the security will be incomplete without the actual analysis of
underlying the economic issues related to ecommerce transaction. Therefore, certain security
mechanisms are needed to be identified that can be used to govern the compatibility of the
ecommerce system.
2.5. Ecommerce Risks and Mitigation
There are several risks involved with the ecommerce and therefore the need for
identification of the risk mitigation approaches are needed to be identified. With the increasing
in the different processes of attacks in ecommerce, privacy has gradually become a major
concern for the consumers [16]. Ecommerce involves transactions between the strangers.
Therefore, identification of the risk mitigation approaches is essential. Ecommerce can be a
tremendous boon for any small business. A business needs to ensure certain risk mitigation
processes for reducing the chances of business loss. The risk mitigation approaches that can be
implemented in mitigation of the risks related to ecommerce transactions is discussed in the
following paragraphs-
It is essential to achieve and maintain the PCI compliance in order to ensure that the
security risks and issues related to ecommerce are controlled. Furthermore, it is essential to keep
the shopping cart software updated [8]. An updated software can help in mitigation of the risks
and issues in ecommerce security. The steps that a consumer and a business can undertake in
mitigation of the risks associated with ecommerce are as follows-
Page | 25

E-COMMERCE SECURITY
Ensure Information Security: It is needed to ensure appropriate information security so
that the risks related to ecommerce are addressed. The information related to an ecommerce
transaction includes the buying requests, the payment processes and other personal details. A
hacker can easily hack a customer database to gain certain information that can increase the data
security risks. In an ecommerce business, it is needed to set up a secure and efficient process of
carrying on with an ecommerce transaction and to avoid the risks associated with the same.
Understanding the Risk and Training the Staffs: The staffs of the organization should
have correct information of the risks related to ecommerce business so that they can easily deal
with the same [7]. This is one major risk mitigation approach that can be undertaken by a
business in order to reduce the risks related to ecommerce and to ensure the information security.
Training the staffs of the organization should be prioritized as it one of the most effective
techniques of risk mitigation.
2.6. Risk Management in reducing the risks in Ecommerce
Electronic payment can be considered as an easy and quick payment methods that are
associated with either buying or selling of any goods online or after availing any services. In the
early days of internet, the popularity of e commerce is hinged on whether the data is transferred
in a secure manner or not.
The risk management in ecommerce is related to finding solutions associated with the
risks and issues in ecommerce. Providing appropriate training to the e commerce team can be
considered as an appropriate approach to risk management [15]. The team is needed to be trained
in appropriate risk management policies and procedures so that the security issues and frauds in
Page | 26
Ensure Information Security: It is needed to ensure appropriate information security so
that the risks related to ecommerce are addressed. The information related to an ecommerce
transaction includes the buying requests, the payment processes and other personal details. A
hacker can easily hack a customer database to gain certain information that can increase the data
security risks. In an ecommerce business, it is needed to set up a secure and efficient process of
carrying on with an ecommerce transaction and to avoid the risks associated with the same.
Understanding the Risk and Training the Staffs: The staffs of the organization should
have correct information of the risks related to ecommerce business so that they can easily deal
with the same [7]. This is one major risk mitigation approach that can be undertaken by a
business in order to reduce the risks related to ecommerce and to ensure the information security.
Training the staffs of the organization should be prioritized as it one of the most effective
techniques of risk mitigation.
2.6. Risk Management in reducing the risks in Ecommerce
Electronic payment can be considered as an easy and quick payment methods that are
associated with either buying or selling of any goods online or after availing any services. In the
early days of internet, the popularity of e commerce is hinged on whether the data is transferred
in a secure manner or not.
The risk management in ecommerce is related to finding solutions associated with the
risks and issues in ecommerce. Providing appropriate training to the e commerce team can be
considered as an appropriate approach to risk management [15]. The team is needed to be trained
in appropriate risk management policies and procedures so that the security issues and frauds in
Page | 26

E-COMMERCE SECURITY
online transaction can directly be dealt with. Apart from that, the customer needs to ensure
secure ecommerce options that include a secure internet connection.
It is needed to ensure that a e commerce business is protected from intrusion. The system
that is associated with an ecommerce transaction should be checked regularly for viruses and
malware. This can help in reducing the chances of intrusion and hacking into the system. The
ecommerce business companies should ensure checking of sensitive data on a regular basis.
As an approach for risk management, it is needed to know the details of the service
provider prior to payment in order to prevent any unauthorised activities. Making strict laws on
the other hand can help in reduction of the issues related to ecommerce.
According to Savrul et al. certain privacy enhancing techniques can be used for
surveillance. Appropriate surveillance of the ecommerce transaction can subsequently help in
reduction of the risk and issues in ecommerce.
2.7. Proposed Risk Mitigation Approaches
The proposed risk mitigation approaches for elimination of the risks identified in
ecommerce are as follows-
Encryption Technology: Data encryption technique can help in reduction of the risks
and issues related to ecommerce transaction. Public key systems, which is also termed as
symmetric cryptosystem can help in reduction of the risks in ecommerce [9]. The sender and the
receiver should have an access to the information related to public key and private key in order
to encrypt and decrypt a message. Cryptographic technologies can help in mitigation of the risk
at various points in the payment system.
Page | 27
online transaction can directly be dealt with. Apart from that, the customer needs to ensure
secure ecommerce options that include a secure internet connection.
It is needed to ensure that a e commerce business is protected from intrusion. The system
that is associated with an ecommerce transaction should be checked regularly for viruses and
malware. This can help in reducing the chances of intrusion and hacking into the system. The
ecommerce business companies should ensure checking of sensitive data on a regular basis.
As an approach for risk management, it is needed to know the details of the service
provider prior to payment in order to prevent any unauthorised activities. Making strict laws on
the other hand can help in reduction of the issues related to ecommerce.
According to Savrul et al. certain privacy enhancing techniques can be used for
surveillance. Appropriate surveillance of the ecommerce transaction can subsequently help in
reduction of the risk and issues in ecommerce.
2.7. Proposed Risk Mitigation Approaches
The proposed risk mitigation approaches for elimination of the risks identified in
ecommerce are as follows-
Encryption Technology: Data encryption technique can help in reduction of the risks
and issues related to ecommerce transaction. Public key systems, which is also termed as
symmetric cryptosystem can help in reduction of the risks in ecommerce [9]. The sender and the
receiver should have an access to the information related to public key and private key in order
to encrypt and decrypt a message. Cryptographic technologies can help in mitigation of the risk
at various points in the payment system.
Page | 27
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

E-COMMERCE SECURITY
Digital Signature: The use of digital signature can be considered as another
cryptographic tag that can help in mitigation of the risks related to ecommerce [10]. A digital
signature can therefore be described as the salient application of the concept of public key
cryptography.
Digital Envelopes: Secure electronic transactions can be ensured by making use of
digital envelopes. In digital envelop, the system make use of a randomly chosen set of generated
symmetric keys for encryption of data.
Apart from that the change of password on a regular basis can help in mitigation of the
risks related to ecommerce.
2.8. Conceptual Framework
The conceptual Framework that is designed for the research is indicated in the following
figure-
Page | 28
Digital Signature: The use of digital signature can be considered as another
cryptographic tag that can help in mitigation of the risks related to ecommerce [10]. A digital
signature can therefore be described as the salient application of the concept of public key
cryptography.
Digital Envelopes: Secure electronic transactions can be ensured by making use of
digital envelopes. In digital envelop, the system make use of a randomly chosen set of generated
symmetric keys for encryption of data.
Apart from that the change of password on a regular basis can help in mitigation of the
risks related to ecommerce.
2.8. Conceptual Framework
The conceptual Framework that is designed for the research is indicated in the following
figure-
Page | 28
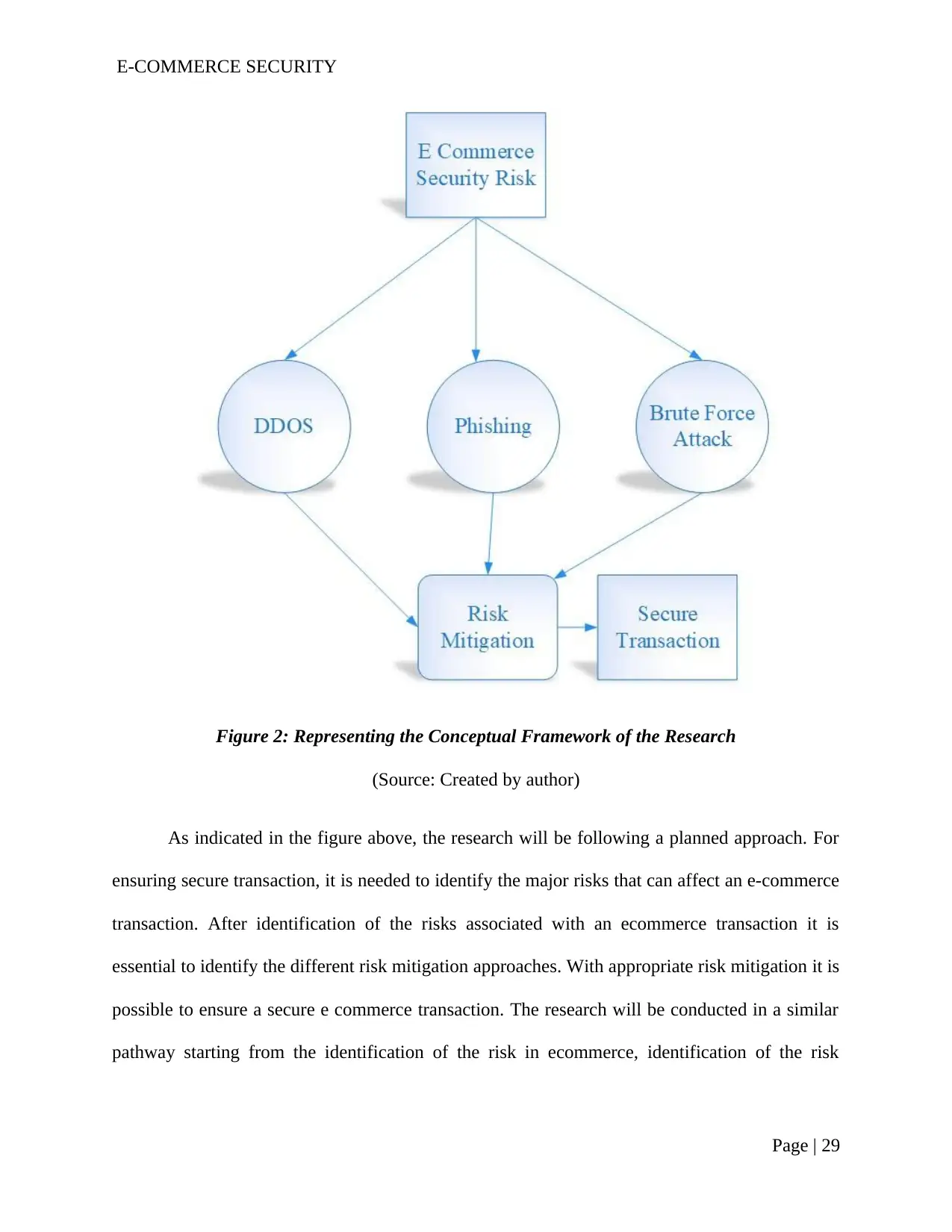
E-COMMERCE SECURITY
Figure 2: Representing the Conceptual Framework of the Research
(Source: Created by author)
As indicated in the figure above, the research will be following a planned approach. For
ensuring secure transaction, it is needed to identify the major risks that can affect an e-commerce
transaction. After identification of the risks associated with an ecommerce transaction it is
essential to identify the different risk mitigation approaches. With appropriate risk mitigation it is
possible to ensure a secure e commerce transaction. The research will be conducted in a similar
pathway starting from the identification of the risk in ecommerce, identification of the risk
Page | 29
Figure 2: Representing the Conceptual Framework of the Research
(Source: Created by author)
As indicated in the figure above, the research will be following a planned approach. For
ensuring secure transaction, it is needed to identify the major risks that can affect an e-commerce
transaction. After identification of the risks associated with an ecommerce transaction it is
essential to identify the different risk mitigation approaches. With appropriate risk mitigation it is
possible to ensure a secure e commerce transaction. The research will be conducted in a similar
pathway starting from the identification of the risk in ecommerce, identification of the risk
Page | 29

E-COMMERCE SECURITY
mitigation approaches and recommending the approaches that can ensure secure ecommerce
transactions.
2.9. Chapter Summary
The literature review chapter discusses the concept of ecommerce transactions and the
issues related to ecommerce. It has been observed that there are certain risks and issues related to
ecommerce security. The mitigation approaches for the risks and issues associated with the e
commerce transaction are discussed. The ecommerce transactions are prone to security risks
mainly because it involves major transactions over internet. Certain risk mitigation approaches
are proposed that can help in risk mitigation or controlling of the risks related to e commerce and
online transactions. A conceptual framework is designed that proposes the framework of the
research. The researcher has developed a viable framework that is capable of fulfilling the major
objectives of the research. Since the research purpose is to reflect on the ecommerce security risk
and the risk mitigation approaches, the developed framework is appropriate for conducting the
research. The literature review section formed the base of the research project by identifying the
significant risks related to the project. It has been observed that with the increase in use of
ecommerce transaction, the risks related to ecommerce increases as well. Researchers based on
the purchasing intention of the online customers prove that it will further increase in future.
Therefore, this research is essential to understand the most prominent risk in the area of e
commerce and mitigation approaches of the same.
Page | 30
mitigation approaches and recommending the approaches that can ensure secure ecommerce
transactions.
2.9. Chapter Summary
The literature review chapter discusses the concept of ecommerce transactions and the
issues related to ecommerce. It has been observed that there are certain risks and issues related to
ecommerce security. The mitigation approaches for the risks and issues associated with the e
commerce transaction are discussed. The ecommerce transactions are prone to security risks
mainly because it involves major transactions over internet. Certain risk mitigation approaches
are proposed that can help in risk mitigation or controlling of the risks related to e commerce and
online transactions. A conceptual framework is designed that proposes the framework of the
research. The researcher has developed a viable framework that is capable of fulfilling the major
objectives of the research. Since the research purpose is to reflect on the ecommerce security risk
and the risk mitigation approaches, the developed framework is appropriate for conducting the
research. The literature review section formed the base of the research project by identifying the
significant risks related to the project. It has been observed that with the increase in use of
ecommerce transaction, the risks related to ecommerce increases as well. Researchers based on
the purchasing intention of the online customers prove that it will further increase in future.
Therefore, this research is essential to understand the most prominent risk in the area of e
commerce and mitigation approaches of the same.
Page | 30
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-COMMERCE SECURITY
Chapter 3: Methodology and Research Activity
3.1. Introduction
Research methodology is a vital consideration of a research project as it details the tools
and techniques needed for conducting a research. Choosing appropriate research methods and
highlighting the major aspects of the research is the aim of the research methodology chapter.
In this chapter the researcher has aimed in providing an analysis of different research methods
that can be utilized for undertaking and completing a research [33]. Apart from that, the chapter
analyses the main research activities that is followed while conducting the research. The chapter
gives an idea of the various processes that has been used by the researcher in undertaking this
research.
3.2. Research Activity
This research aims in identification of the security issues related to E-Commerce, mainly
in terms of communication. As an initial research activity, the already published literatures and
research journals in this field are evaluated. Through an extensive literature review, the
researcher has identified the major risks associated with a basic e commerce transaction. On
basis of the findings, the researcher has developed a conceptual framework that analyses the
research pathway [31]. The research is mainly based on primary research. The data from the
primary research will be collected on basis of a survey that will be conducted to collect
information from the individuals who have an experience in the field of e commerce
transactions. A quantitative data analysis method will evaluate the responses of each of the
research participants in order to identify the issues related to e commerce transaction. A set of
questionnaires have been developed for the online survey. The questionnaires are mainly based
Page | 31
Chapter 3: Methodology and Research Activity
3.1. Introduction
Research methodology is a vital consideration of a research project as it details the tools
and techniques needed for conducting a research. Choosing appropriate research methods and
highlighting the major aspects of the research is the aim of the research methodology chapter.
In this chapter the researcher has aimed in providing an analysis of different research methods
that can be utilized for undertaking and completing a research [33]. Apart from that, the chapter
analyses the main research activities that is followed while conducting the research. The chapter
gives an idea of the various processes that has been used by the researcher in undertaking this
research.
3.2. Research Activity
This research aims in identification of the security issues related to E-Commerce, mainly
in terms of communication. As an initial research activity, the already published literatures and
research journals in this field are evaluated. Through an extensive literature review, the
researcher has identified the major risks associated with a basic e commerce transaction. On
basis of the findings, the researcher has developed a conceptual framework that analyses the
research pathway [31]. The research is mainly based on primary research. The data from the
primary research will be collected on basis of a survey that will be conducted to collect
information from the individuals who have an experience in the field of e commerce
transactions. A quantitative data analysis method will evaluate the responses of each of the
research participants in order to identify the issues related to e commerce transaction. A set of
questionnaires have been developed for the online survey. The questionnaires are mainly based
Page | 31

E-COMMERCE SECURITY
on the risks that are identified from the review of literature in this field. The responses obtained
from the survey will help in cross checking the correctness of the data that is identified [24]. The
secondary sources are however considered to be valid sources while that of the data collected
from primary sources can be vague as well. Therefore, it is mandatory to confirm to what extend
the collected data matches the findings from the previous research papers.
As a part of research activity, the consent of each research participant is taken. The
ethical considerations are followed while conducting the research and the research participants
are allowed to opt out of the entire process as per their wish [32]. The data collected from the
survey are securely stored in order to avoid data manipulation. The survey questions are prepared
making use of Google forms.
Therefore, the results obtained from the literature review formed the base of the research.
The following section identifies research approach undertaken, the research philosophy used
along with the sampling technique for data collection [26]. The ethical considerations related to
the research are discussed as well. The methods used for conducting this research are highlighted
in the sections below.
3.3. Research Philosophy
The research philosophy identifies the process by which the draining details of the
research is collected in order for ensuring that the research results thus obtained are true and
legitimate. The process of evaluation of a particular topic depends on the philosophy of the
research [30]. This is particularly because the research philosophy is associated with finding the
source of knowledge and development of the knowledge based on that. Research philosophy,
therefore, deals with the idea of knowledge creation. The basic research philosophies associated
Page | 32
on the risks that are identified from the review of literature in this field. The responses obtained
from the survey will help in cross checking the correctness of the data that is identified [24]. The
secondary sources are however considered to be valid sources while that of the data collected
from primary sources can be vague as well. Therefore, it is mandatory to confirm to what extend
the collected data matches the findings from the previous research papers.
As a part of research activity, the consent of each research participant is taken. The
ethical considerations are followed while conducting the research and the research participants
are allowed to opt out of the entire process as per their wish [32]. The data collected from the
survey are securely stored in order to avoid data manipulation. The survey questions are prepared
making use of Google forms.
Therefore, the results obtained from the literature review formed the base of the research.
The following section identifies research approach undertaken, the research philosophy used
along with the sampling technique for data collection [26]. The ethical considerations related to
the research are discussed as well. The methods used for conducting this research are highlighted
in the sections below.
3.3. Research Philosophy
The research philosophy identifies the process by which the draining details of the
research is collected in order for ensuring that the research results thus obtained are true and
legitimate. The process of evaluation of a particular topic depends on the philosophy of the
research [30]. This is particularly because the research philosophy is associated with finding the
source of knowledge and development of the knowledge based on that. Research philosophy,
therefore, deals with the idea of knowledge creation. The basic research philosophies associated
Page | 32

E-COMMERCE SECURITY
with an academic research include positivism, interpretivism and realism. These are the common
forms of epistemology [18].
The philosophy of positivism deals with the application and analysis of the hidden facts
and information in a specific manner. It mainly initiates exploration of logic in the data that is
being used to conduct a research [20]. The positivism research philosophy therefore considers
the use of only factual knowledge in the research, which is one significant advantage of making
use of positivism philosophy of research [22]. However, in positivism research philosophy, the
researcher is mainly assigned with the role of data collection and correct interpretation of the
data.
The interpretivism research philosophy on a contrary deals with the interpretation of the
various elements of a particular research. Development of the interpretive researches therefore
enables the researcher to assume certain elements of the research [23]. The interpretivism
research philosophy is often explained as a critique of the positivism research philosophy [19]. It
is a form of epistemology that supports the mix of complex structures related to the social world
of business and management activities.
The realism research philosophy on the other hand is described as a mixed approach that
involves the characteristics of both the positivism and the interpretivism research philosophy
[27]. Realism research philosophy has two major subdivisions which includes direct subdivision
and critical subdivision.
In order to find and analyse data related to e commerce security, the researcher has
chosen the use of positivism research philosophy.
3.3.1. Justification of Research Philosophy: Positivism
Page | 33
with an academic research include positivism, interpretivism and realism. These are the common
forms of epistemology [18].
The philosophy of positivism deals with the application and analysis of the hidden facts
and information in a specific manner. It mainly initiates exploration of logic in the data that is
being used to conduct a research [20]. The positivism research philosophy therefore considers
the use of only factual knowledge in the research, which is one significant advantage of making
use of positivism philosophy of research [22]. However, in positivism research philosophy, the
researcher is mainly assigned with the role of data collection and correct interpretation of the
data.
The interpretivism research philosophy on a contrary deals with the interpretation of the
various elements of a particular research. Development of the interpretive researches therefore
enables the researcher to assume certain elements of the research [23]. The interpretivism
research philosophy is often explained as a critique of the positivism research philosophy [19]. It
is a form of epistemology that supports the mix of complex structures related to the social world
of business and management activities.
The realism research philosophy on the other hand is described as a mixed approach that
involves the characteristics of both the positivism and the interpretivism research philosophy
[27]. Realism research philosophy has two major subdivisions which includes direct subdivision
and critical subdivision.
In order to find and analyse data related to e commerce security, the researcher has
chosen the use of positivism research philosophy.
3.3.1. Justification of Research Philosophy: Positivism
Page | 33
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

E-COMMERCE SECURITY
In line with the increase in the use of e commerce, the sophistication of the e commerce
risks increases as well. Therefore, it is important for the research to consider only the factual
knowledge related to the research topic [21]. The use of positivism research philosophy therefore
indicates the better analysis of the all the hidden facts related to ecommerce security and
transactions in ecommerce [30]. Since in positivism research, only factual knowledge is
considered, the chances of data manipulation are reduced leading to minimization of data errors.
Therefore, the positivism research philosophy is apt for finding data related to the security in
ecommerce.
3.4. Research Approach
It is vital to identify the appropriate research approach as the conduction of the research
is largely based on the research approach chosen. The research approach provides a clear idea of
the format used in the research [25]. The research approach can be broadly classified into two
approaches, which are inductive research approach and deductive research approach.
The inductive approach or inductive reasoning is mainly based on the observations to
develop theories related to the topic of the research. With inductive approach, a particular pattern
is searched from the collected data for finding answers to the identified research questions. Thus,
it can be said that inductive research approach is not related to the disregarding theories
associated with the research while formulating the research questions and objectives of this
research [27]. The inductive research approach therefore deals with the formulation of
appropriate research questions objectives of the research. Inductive approach does not involve
any hypotheses that are needed to be tested.
Page | 34
In line with the increase in the use of e commerce, the sophistication of the e commerce
risks increases as well. Therefore, it is important for the research to consider only the factual
knowledge related to the research topic [21]. The use of positivism research philosophy therefore
indicates the better analysis of the all the hidden facts related to ecommerce security and
transactions in ecommerce [30]. Since in positivism research, only factual knowledge is
considered, the chances of data manipulation are reduced leading to minimization of data errors.
Therefore, the positivism research philosophy is apt for finding data related to the security in
ecommerce.
3.4. Research Approach
It is vital to identify the appropriate research approach as the conduction of the research
is largely based on the research approach chosen. The research approach provides a clear idea of
the format used in the research [25]. The research approach can be broadly classified into two
approaches, which are inductive research approach and deductive research approach.
The inductive approach or inductive reasoning is mainly based on the observations to
develop theories related to the topic of the research. With inductive approach, a particular pattern
is searched from the collected data for finding answers to the identified research questions. Thus,
it can be said that inductive research approach is not related to the disregarding theories
associated with the research while formulating the research questions and objectives of this
research [27]. The inductive research approach therefore deals with the formulation of
appropriate research questions objectives of the research. Inductive approach does not involve
any hypotheses that are needed to be tested.
Page | 34

E-COMMERCE SECURITY
Deductive approach on the other hand mainly implies the practical application of the
different theories related to the research [23]. Deductive approach aims in developing theories
specific to the content and the specification of the research [22]. It is mainly concerned with the
development of a research hypothesis related to an existing theory. A deductive research
approach always tests the link between the data and the variables associated with a research.
The research related to ecommerce security in ecommerce transactions has made use of
inductive research approach.
3.4.1. Justification for Research Approach: Inductive
The inductive approach is found to be apt for this research as no hypothesis is considered
in this research. This research approach deals with a detailed observation of the different aspects
of the research. In inductive approach, the researcher develops a planned empirical
generalization of the research topic in order to identify the preliminary relationship between
them [27]. Therefore, no hypotheses are generally found in the initial stages of the research that
is associated with the inductive research approach. Similarly, in the research related to the
identification of the e commerce security issues and their mitigation approaches, no research
hypotheses are set at the beginning of the research. Thus the choice of making use of inductive
research approach in conducting this research study is found to be apt.
3.5. Research Design
The use of a specific research design helps in better understanding of the framework
chosen for the research. The use of a particular research design indicates that the data collection
process chosen for the research is appropriate for successful completion of the research. The
Page | 35
Deductive approach on the other hand mainly implies the practical application of the
different theories related to the research [23]. Deductive approach aims in developing theories
specific to the content and the specification of the research [22]. It is mainly concerned with the
development of a research hypothesis related to an existing theory. A deductive research
approach always tests the link between the data and the variables associated with a research.
The research related to ecommerce security in ecommerce transactions has made use of
inductive research approach.
3.4.1. Justification for Research Approach: Inductive
The inductive approach is found to be apt for this research as no hypothesis is considered
in this research. This research approach deals with a detailed observation of the different aspects
of the research. In inductive approach, the researcher develops a planned empirical
generalization of the research topic in order to identify the preliminary relationship between
them [27]. Therefore, no hypotheses are generally found in the initial stages of the research that
is associated with the inductive research approach. Similarly, in the research related to the
identification of the e commerce security issues and their mitigation approaches, no research
hypotheses are set at the beginning of the research. Thus the choice of making use of inductive
research approach in conducting this research study is found to be apt.
3.5. Research Design
The use of a specific research design helps in better understanding of the framework
chosen for the research. The use of a particular research design indicates that the data collection
process chosen for the research is appropriate for successful completion of the research. The
Page | 35

E-COMMERCE SECURITY
research design related to academic research includes exploratory research design, explanatory
research design and descriptive research design.
The use of exploratory research design enables a researcher in acknowledging the
different aspects of a research [29]. The explanatory research design on the other hand describes
the reason behind the occurrence of the different events and the incidents related to a particular
research. The descriptive research design however is related to identification of the details relate
to the occurrence of the events with appropriate description of the same. The examiner in this
research has chosen to use descriptive design for evaluation of the research results.
3.5.1. Justification for the chosen Research Design: Descriptive
The use of descriptive design is considered to be apt for this research as it identifies the
occurrence of different events. This is essential in order to identify the issues related to
ecommerce transactions. Thus use of descriptive research design is justified.
3.6. Data Collection Process
The different sources of collection of data include primary source and secondary data
source. The primary source indicates collection of data directly from the individuals who might
have a knowledge about the research problem [28]. The methods or channel for collection of
primary data include the interview, observation and surveys. For this research, the method of
online survey is chosen to collect the data from primary sources.
The secondary data source refer to already published data sources such as books, research
journals and annual reports of the company [23]. One of the basic advantages of using secondary
Page | 36
research design related to academic research includes exploratory research design, explanatory
research design and descriptive research design.
The use of exploratory research design enables a researcher in acknowledging the
different aspects of a research [29]. The explanatory research design on the other hand describes
the reason behind the occurrence of the different events and the incidents related to a particular
research. The descriptive research design however is related to identification of the details relate
to the occurrence of the events with appropriate description of the same. The examiner in this
research has chosen to use descriptive design for evaluation of the research results.
3.5.1. Justification for the chosen Research Design: Descriptive
The use of descriptive design is considered to be apt for this research as it identifies the
occurrence of different events. This is essential in order to identify the issues related to
ecommerce transactions. Thus use of descriptive research design is justified.
3.6. Data Collection Process
The different sources of collection of data include primary source and secondary data
source. The primary source indicates collection of data directly from the individuals who might
have a knowledge about the research problem [28]. The methods or channel for collection of
primary data include the interview, observation and surveys. For this research, the method of
online survey is chosen to collect the data from primary sources.
The secondary data source refer to already published data sources such as books, research
journals and annual reports of the company [23]. One of the basic advantages of using secondary
Page | 36
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-COMMERCE SECURITY
source is that a large quantity of valid data can be gathered. A literature review has been
conducted in this research my evaluating the secondary data sources.
3.7. Sampling Method
There are majorly two different methods of sampling, which are probability sampling and
non-probability sampling. The probability sampling method enables each member of a
population to participate in the survey that is being conducted [30]. The non-probability
sampling on the other hand allows only a certain member of population to participate in the
survey. The sampling method chosen for this survey is simple random probability sampling.
3.7.1. Sample Size
The sample size chosen for this research is 50 individuals who have an experience of e
commerce transaction and/or have faced transactional issue in ecommerce. This data will be
validated based on the data collected from evaluation of the secondary sources in the literature
review section.
3.8. Data Analysis Method
The different data analysis methods in a research include qualitative data analysis and
quantitative data analysis.
The qualitative research is associated with the collection and analysis of the non-numeric
information that includes interviews, transcripts, notes and videos [27]. No statistical analysis of
the data is involved with qualitative research.
The quantitative data analysis on the other hand deals with statistical data analysis and is
mainly related to the numeric data associated with a research [26]. Since the research related to
Page | 37
source is that a large quantity of valid data can be gathered. A literature review has been
conducted in this research my evaluating the secondary data sources.
3.7. Sampling Method
There are majorly two different methods of sampling, which are probability sampling and
non-probability sampling. The probability sampling method enables each member of a
population to participate in the survey that is being conducted [30]. The non-probability
sampling on the other hand allows only a certain member of population to participate in the
survey. The sampling method chosen for this survey is simple random probability sampling.
3.7.1. Sample Size
The sample size chosen for this research is 50 individuals who have an experience of e
commerce transaction and/or have faced transactional issue in ecommerce. This data will be
validated based on the data collected from evaluation of the secondary sources in the literature
review section.
3.8. Data Analysis Method
The different data analysis methods in a research include qualitative data analysis and
quantitative data analysis.
The qualitative research is associated with the collection and analysis of the non-numeric
information that includes interviews, transcripts, notes and videos [27]. No statistical analysis of
the data is involved with qualitative research.
The quantitative data analysis on the other hand deals with statistical data analysis and is
mainly related to the numeric data associated with a research [26]. Since the research related to
Page | 37

E-COMMERCE SECURITY
the evaluation of the e commerce security is related to the collection and analysis of primary
data, the quantitative data analysis method is chosen for analysis of the collected data.
3.9. Ethical Consideration
Any academic research is related to certain ethical considerations that are needed to be
followed. The ethical considerations in the research are as follows-
1. It is the responsibility of the researcher to make sure that the participants of the
research are not subjected to any harm. For ensuring that, the consent of each of the research
participants is collected.
2. The research should ensure adequate level of confidentiality till publish of the research
paper.
3. Manipulation of the collected data in order to obtain the desired results is strictly
prohibited in this research.
4. Anonymity of the participants of the research is maintained while conducting this
research.
Page | 38
the evaluation of the e commerce security is related to the collection and analysis of primary
data, the quantitative data analysis method is chosen for analysis of the collected data.
3.9. Ethical Consideration
Any academic research is related to certain ethical considerations that are needed to be
followed. The ethical considerations in the research are as follows-
1. It is the responsibility of the researcher to make sure that the participants of the
research are not subjected to any harm. For ensuring that, the consent of each of the research
participants is collected.
2. The research should ensure adequate level of confidentiality till publish of the research
paper.
3. Manipulation of the collected data in order to obtain the desired results is strictly
prohibited in this research.
4. Anonymity of the participants of the research is maintained while conducting this
research.
Page | 38

E-COMMERCE SECURITY
Chapter 4: Results and Analysis
4.1. Introduction
This particular chapter aims in discussing the results of the responses of the survey that is
being conducted online. The data analysis chapter is one of the most vital chapters of a research
as it enables a researcher in finding answers to the identified research questions. The results and
analysis chapter identifies and discusses the major findings of the research, which includes the
issues associated with an ecommerce transaction and the risks. In order to identify the risks and
issues associated with any ecommerce transaction, the respondents were asked to provide their
opinions regarding certain major risks related to ecommerce. The collected data is analysed in
order to understand the major risk related to ecommerce and its risk mitigation approach. The
data collection was based on a pre-determined questionnaire where the respondents were asked
to provide their opinions regarding certain major issues in e commerce that they might have
faced or experienced. Based on their responses, the most prominent risks in e commerce are
categorised.
4.2. Data Analysis
The data analysis is categorised into two parts, one is demographic data analysis and
analysis of the data based on the responses of the respondents. The demographic data analysis of
the research respondents of the survey is discussed in the section below.
4.2.1. Demographic Data Analysis
As a part of collection of demographic data, the details of the age of each respondent of
the survey is taken into consideration. The responses prove that majority of the respondents of
Page | 39
Chapter 4: Results and Analysis
4.1. Introduction
This particular chapter aims in discussing the results of the responses of the survey that is
being conducted online. The data analysis chapter is one of the most vital chapters of a research
as it enables a researcher in finding answers to the identified research questions. The results and
analysis chapter identifies and discusses the major findings of the research, which includes the
issues associated with an ecommerce transaction and the risks. In order to identify the risks and
issues associated with any ecommerce transaction, the respondents were asked to provide their
opinions regarding certain major risks related to ecommerce. The collected data is analysed in
order to understand the major risk related to ecommerce and its risk mitigation approach. The
data collection was based on a pre-determined questionnaire where the respondents were asked
to provide their opinions regarding certain major issues in e commerce that they might have
faced or experienced. Based on their responses, the most prominent risks in e commerce are
categorised.
4.2. Data Analysis
The data analysis is categorised into two parts, one is demographic data analysis and
analysis of the data based on the responses of the respondents. The demographic data analysis of
the research respondents of the survey is discussed in the section below.
4.2.1. Demographic Data Analysis
As a part of collection of demographic data, the details of the age of each respondent of
the survey is taken into consideration. The responses prove that majority of the respondents of
Page | 39
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
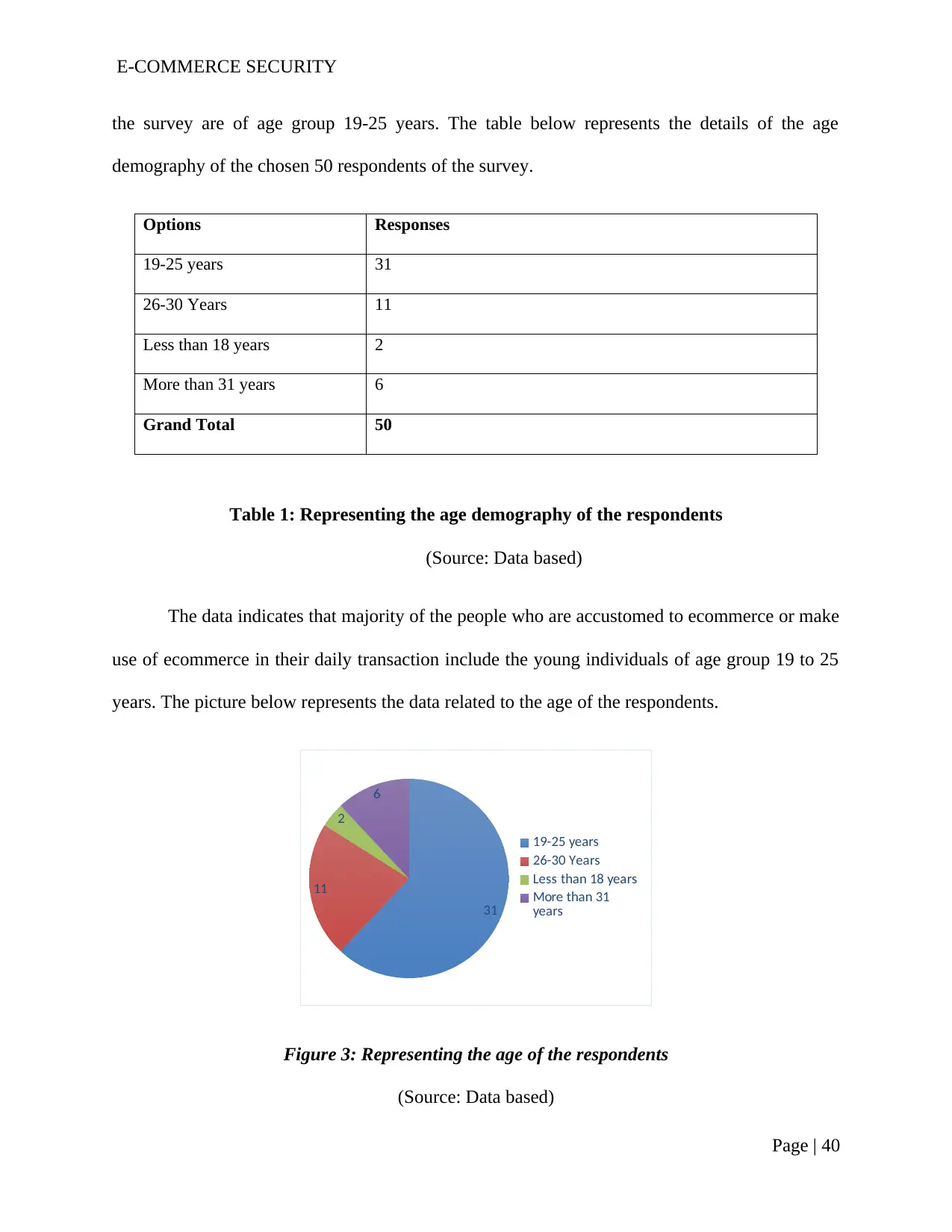
E-COMMERCE SECURITY
the survey are of age group 19-25 years. The table below represents the details of the age
demography of the chosen 50 respondents of the survey.
Options Responses
19-25 years 31
26-30 Years 11
Less than 18 years 2
More than 31 years 6
Grand Total 50
Table 1: Representing the age demography of the respondents
(Source: Data based)
The data indicates that majority of the people who are accustomed to ecommerce or make
use of ecommerce in their daily transaction include the young individuals of age group 19 to 25
years. The picture below represents the data related to the age of the respondents.
31
11
2
6
19-25 years
26-30 Years
Less than 18 years
More than 31
years
Figure 3: Representing the age of the respondents
(Source: Data based)
Page | 40
the survey are of age group 19-25 years. The table below represents the details of the age
demography of the chosen 50 respondents of the survey.
Options Responses
19-25 years 31
26-30 Years 11
Less than 18 years 2
More than 31 years 6
Grand Total 50
Table 1: Representing the age demography of the respondents
(Source: Data based)
The data indicates that majority of the people who are accustomed to ecommerce or make
use of ecommerce in their daily transaction include the young individuals of age group 19 to 25
years. The picture below represents the data related to the age of the respondents.
31
11
2
6
19-25 years
26-30 Years
Less than 18 years
More than 31
years
Figure 3: Representing the age of the respondents
(Source: Data based)
Page | 40

E-COMMERCE SECURITY
In relation to data collection process, and to understand the extent to which the research
respondents are addicted to e commerce or make use of ecommerce, the research respondents
were allowed to provide the opinion regarding the number of times in a month, they make use of
ecommerce transaction. The data suggest that majority of the individuals make only a minimal
use of ecommerce transaction in a month. 28 respondents said that they make use of ecommerce
for 2-10 times in a month while only 4 individuals make use of the same for more than 21 times.
From this data, the conclusion which can be drawn is that the research respondents might not
consider ecommerce a safe option for transaction. There can be a number of reasons behind the
same. The table below represents the responses of the respondents regarding the number of times
they make use of ecommerce in a month.
Options Responses
11- 20 times 14
2-10 times 28
More than 21 times 4
Once 4
Grand Total 50
Table 2: Representing responses of the respondents
(Source: Data Based)
The figure below indicates the responses obtained in a chart form-
Page | 41
In relation to data collection process, and to understand the extent to which the research
respondents are addicted to e commerce or make use of ecommerce, the research respondents
were allowed to provide the opinion regarding the number of times in a month, they make use of
ecommerce transaction. The data suggest that majority of the individuals make only a minimal
use of ecommerce transaction in a month. 28 respondents said that they make use of ecommerce
for 2-10 times in a month while only 4 individuals make use of the same for more than 21 times.
From this data, the conclusion which can be drawn is that the research respondents might not
consider ecommerce a safe option for transaction. There can be a number of reasons behind the
same. The table below represents the responses of the respondents regarding the number of times
they make use of ecommerce in a month.
Options Responses
11- 20 times 14
2-10 times 28
More than 21 times 4
Once 4
Grand Total 50
Table 2: Representing responses of the respondents
(Source: Data Based)
The figure below indicates the responses obtained in a chart form-
Page | 41
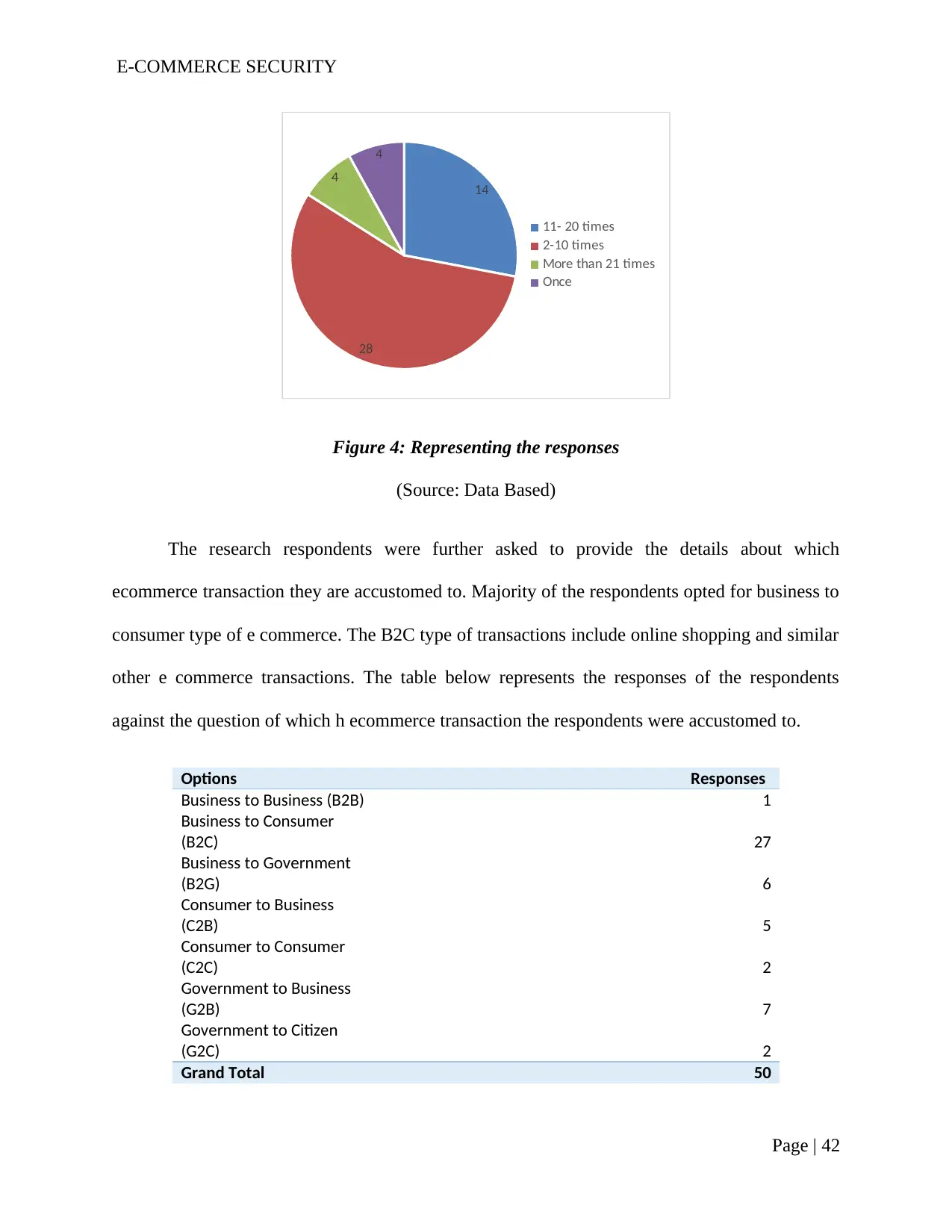
E-COMMERCE SECURITY
14
28
4
4
11- 20 times
2-10 times
More than 21 times
Once
Figure 4: Representing the responses
(Source: Data Based)
The research respondents were further asked to provide the details about which
ecommerce transaction they are accustomed to. Majority of the respondents opted for business to
consumer type of e commerce. The B2C type of transactions include online shopping and similar
other e commerce transactions. The table below represents the responses of the respondents
against the question of which h ecommerce transaction the respondents were accustomed to.
Options Responses
Business to Business (B2B) 1
Business to Consumer
(B2C) 27
Business to Government
(B2G) 6
Consumer to Business
(C2B) 5
Consumer to Consumer
(C2C) 2
Government to Business
(G2B) 7
Government to Citizen
(G2C) 2
Grand Total 50
Page | 42
14
28
4
4
11- 20 times
2-10 times
More than 21 times
Once
Figure 4: Representing the responses
(Source: Data Based)
The research respondents were further asked to provide the details about which
ecommerce transaction they are accustomed to. Majority of the respondents opted for business to
consumer type of e commerce. The B2C type of transactions include online shopping and similar
other e commerce transactions. The table below represents the responses of the respondents
against the question of which h ecommerce transaction the respondents were accustomed to.
Options Responses
Business to Business (B2B) 1
Business to Consumer
(B2C) 27
Business to Government
(B2G) 6
Consumer to Business
(C2B) 5
Consumer to Consumer
(C2C) 2
Government to Business
(G2B) 7
Government to Citizen
(G2C) 2
Grand Total 50
Page | 42
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
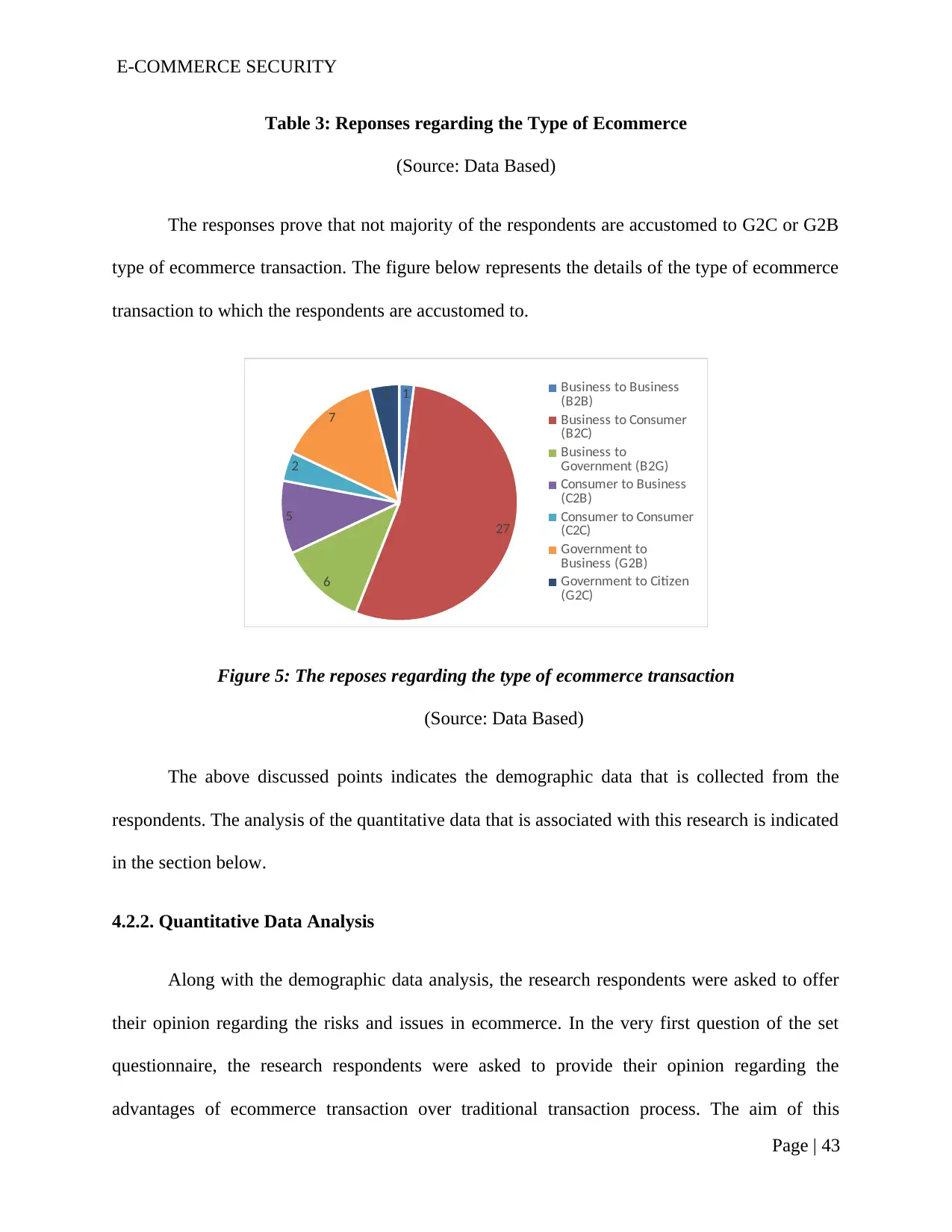
E-COMMERCE SECURITY
Table 3: Reponses regarding the Type of Ecommerce
(Source: Data Based)
The responses prove that not majority of the respondents are accustomed to G2C or G2B
type of ecommerce transaction. The figure below represents the details of the type of ecommerce
transaction to which the respondents are accustomed to.
1
27
6
5
2
7
2 Business to Business
(B2B)
Business to Consumer
(B2C)
Business to
Government (B2G)
Consumer to Business
(C2B)
Consumer to Consumer
(C2C)
Government to
Business (G2B)
Government to Citizen
(G2C)
Figure 5: The reposes regarding the type of ecommerce transaction
(Source: Data Based)
The above discussed points indicates the demographic data that is collected from the
respondents. The analysis of the quantitative data that is associated with this research is indicated
in the section below.
4.2.2. Quantitative Data Analysis
Along with the demographic data analysis, the research respondents were asked to offer
their opinion regarding the risks and issues in ecommerce. In the very first question of the set
questionnaire, the research respondents were asked to provide their opinion regarding the
advantages of ecommerce transaction over traditional transaction process. The aim of this
Page | 43
Table 3: Reponses regarding the Type of Ecommerce
(Source: Data Based)
The responses prove that not majority of the respondents are accustomed to G2C or G2B
type of ecommerce transaction. The figure below represents the details of the type of ecommerce
transaction to which the respondents are accustomed to.
1
27
6
5
2
7
2 Business to Business
(B2B)
Business to Consumer
(B2C)
Business to
Government (B2G)
Consumer to Business
(C2B)
Consumer to Consumer
(C2C)
Government to
Business (G2B)
Government to Citizen
(G2C)
Figure 5: The reposes regarding the type of ecommerce transaction
(Source: Data Based)
The above discussed points indicates the demographic data that is collected from the
respondents. The analysis of the quantitative data that is associated with this research is indicated
in the section below.
4.2.2. Quantitative Data Analysis
Along with the demographic data analysis, the research respondents were asked to offer
their opinion regarding the risks and issues in ecommerce. In the very first question of the set
questionnaire, the research respondents were asked to provide their opinion regarding the
advantages of ecommerce transaction over traditional transaction process. The aim of this
Page | 43
E-COMMERCE SECURITY
question was to ensure whether the respondents finds an ecommerce transaction has benefits
over the traditional transactional process. According to the majority of the research respondents,
the use of ecommerce certainly has benefits over the traditional process.
Options Respon
ses
Agree 23
Disagree 6
Neutral 14
Strongly Agree 5
Strongly Disagree 2
Grand Total 50
Table 4: Responses about Ecommerce benefits
(Source: Data Based)
From the data obtained, it can be said that the respondents of the research consider
ecommerce to be beneficial. However, few of the respondents have disagreed to the same and 14
respondents have chosen not to comment on the topic. The disagreement of the 8 respondents
can possibly be because of the transactional risks that are associated with an ecommerce
transaction. The figure below indicates the responses related to ecommerce benefits.
Page | 44
question was to ensure whether the respondents finds an ecommerce transaction has benefits
over the traditional transactional process. According to the majority of the research respondents,
the use of ecommerce certainly has benefits over the traditional process.
Options Respon
ses
Agree 23
Disagree 6
Neutral 14
Strongly Agree 5
Strongly Disagree 2
Grand Total 50
Table 4: Responses about Ecommerce benefits
(Source: Data Based)
From the data obtained, it can be said that the respondents of the research consider
ecommerce to be beneficial. However, few of the respondents have disagreed to the same and 14
respondents have chosen not to comment on the topic. The disagreement of the 8 respondents
can possibly be because of the transactional risks that are associated with an ecommerce
transaction. The figure below indicates the responses related to ecommerce benefits.
Page | 44

E-COMMERCE SECURITY
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
Total
Figure 6: Representing the responses about ecommerce benefit
(Source: Data Based)
Figure 6 clearly indicates that a large number research respondents agrees to the fact that
ecommerce has certain advantage over traditional commerce. Therefore, it can be concluded that
ecommerce is indeed beneficial over the traditional commerce.
The aim of this research is identification and evaluation of the risks related to ecommerce
transactions. In short, the ecommerce security is evaluated in the research.
On analysing the already existing literatures in the field of ecommerce, it has been
observed that the use of ecommerce has increased significantly mainly because it provides the
existing business an opportunity to research a global business model. Therefore, the respondents
were asked to offer their opinion regarding whether the use of ecommerce helps in increasing the
global reach. The responses of the respondents are indicated in the table below-
Options Respon
ses
Agree 22
Page | 45
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
Total
Figure 6: Representing the responses about ecommerce benefit
(Source: Data Based)
Figure 6 clearly indicates that a large number research respondents agrees to the fact that
ecommerce has certain advantage over traditional commerce. Therefore, it can be concluded that
ecommerce is indeed beneficial over the traditional commerce.
The aim of this research is identification and evaluation of the risks related to ecommerce
transactions. In short, the ecommerce security is evaluated in the research.
On analysing the already existing literatures in the field of ecommerce, it has been
observed that the use of ecommerce has increased significantly mainly because it provides the
existing business an opportunity to research a global business model. Therefore, the respondents
were asked to offer their opinion regarding whether the use of ecommerce helps in increasing the
global reach. The responses of the respondents are indicated in the table below-
Options Respon
ses
Agree 22
Page | 45
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
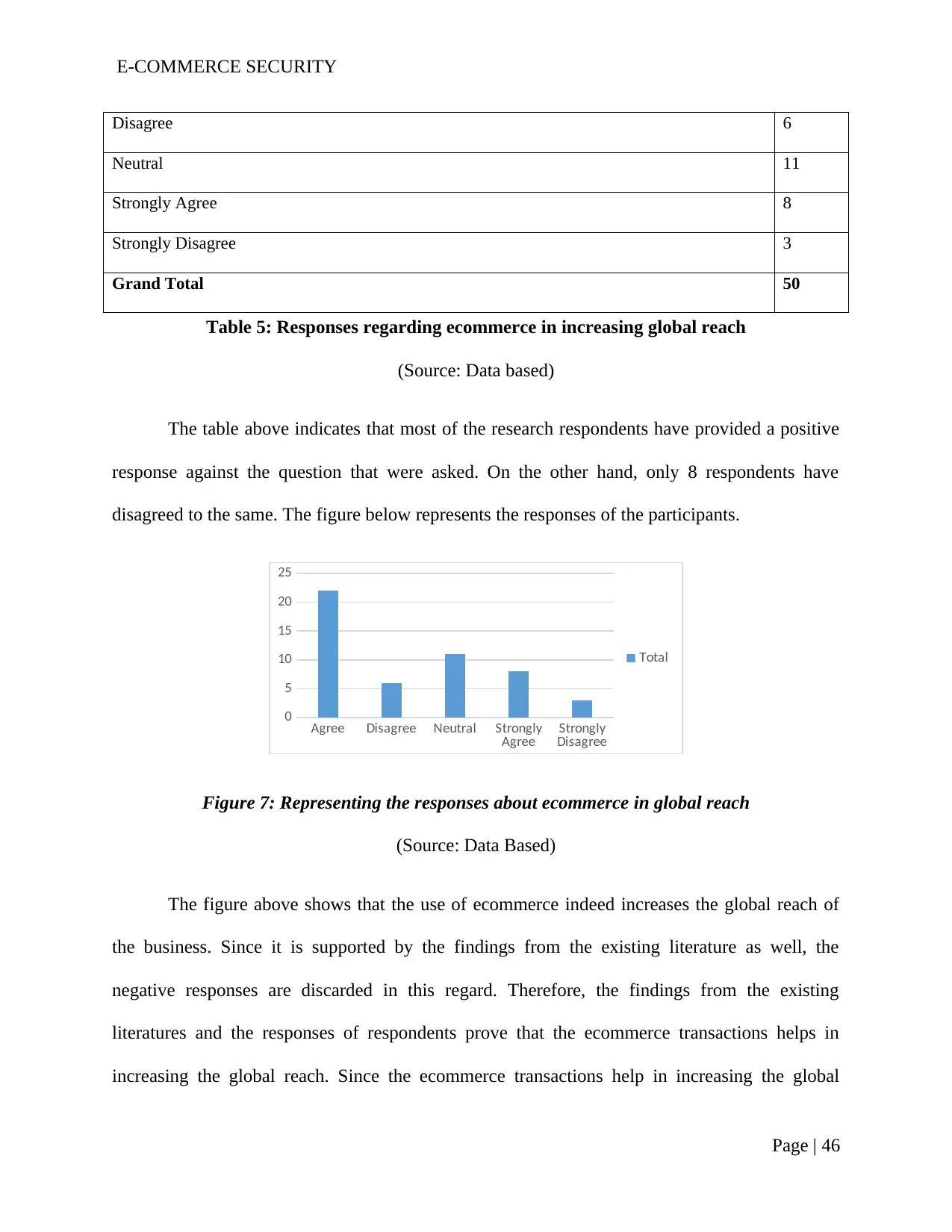
E-COMMERCE SECURITY
Disagree 6
Neutral 11
Strongly Agree 8
Strongly Disagree 3
Grand Total 50
Table 5: Responses regarding ecommerce in increasing global reach
(Source: Data based)
The table above indicates that most of the research respondents have provided a positive
response against the question that were asked. On the other hand, only 8 respondents have
disagreed to the same. The figure below represents the responses of the participants.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
Total
Figure 7: Representing the responses about ecommerce in global reach
(Source: Data Based)
The figure above shows that the use of ecommerce indeed increases the global reach of
the business. Since it is supported by the findings from the existing literature as well, the
negative responses are discarded in this regard. Therefore, the findings from the existing
literatures and the responses of respondents prove that the ecommerce transactions helps in
increasing the global reach. Since the ecommerce transactions help in increasing the global
Page | 46
Disagree 6
Neutral 11
Strongly Agree 8
Strongly Disagree 3
Grand Total 50
Table 5: Responses regarding ecommerce in increasing global reach
(Source: Data based)
The table above indicates that most of the research respondents have provided a positive
response against the question that were asked. On the other hand, only 8 respondents have
disagreed to the same. The figure below represents the responses of the participants.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
Total
Figure 7: Representing the responses about ecommerce in global reach
(Source: Data Based)
The figure above shows that the use of ecommerce indeed increases the global reach of
the business. Since it is supported by the findings from the existing literature as well, the
negative responses are discarded in this regard. Therefore, the findings from the existing
literatures and the responses of respondents prove that the ecommerce transactions helps in
increasing the global reach. Since the ecommerce transactions help in increasing the global
Page | 46

E-COMMERCE SECURITY
reach, the transactional risks related to ecommerce transactions are needed to be identified as
well. In the online survey that was conducted with an aim of data collection related to this
research, the respondents were asked questions regarding the various risks and issues in
ecommerce.
The researcher were asked to provide their opinion on the question that whether they
agree that with the increase in use of ecommerce, the transactional risks increases as well. The
responses of the 50 respondents of the survey is indicated in the table below-
Options
Response
s
Agree 22
Disagree 6
Neutral 11
Strongly Agree 8
Strongly Disagree 3
Grand Total 50
Table 6: Responses regarding ecommerce in increasing transactional Risks
(Source: Data based)
The data from the table above shows that most of the respondents agree to the fact that
the transactional risks are more in ecommerce than in traditional commerce. This risks increases
as ecommerce is mainly based on the transactions over internet. The figure below represents the
views of the respondents regarding role of ecommerce in increasing the transactional risks
associated with an ecommerce transaction.
Page | 47
reach, the transactional risks related to ecommerce transactions are needed to be identified as
well. In the online survey that was conducted with an aim of data collection related to this
research, the respondents were asked questions regarding the various risks and issues in
ecommerce.
The researcher were asked to provide their opinion on the question that whether they
agree that with the increase in use of ecommerce, the transactional risks increases as well. The
responses of the 50 respondents of the survey is indicated in the table below-
Options
Response
s
Agree 22
Disagree 6
Neutral 11
Strongly Agree 8
Strongly Disagree 3
Grand Total 50
Table 6: Responses regarding ecommerce in increasing transactional Risks
(Source: Data based)
The data from the table above shows that most of the respondents agree to the fact that
the transactional risks are more in ecommerce than in traditional commerce. This risks increases
as ecommerce is mainly based on the transactions over internet. The figure below represents the
views of the respondents regarding role of ecommerce in increasing the transactional risks
associated with an ecommerce transaction.
Page | 47
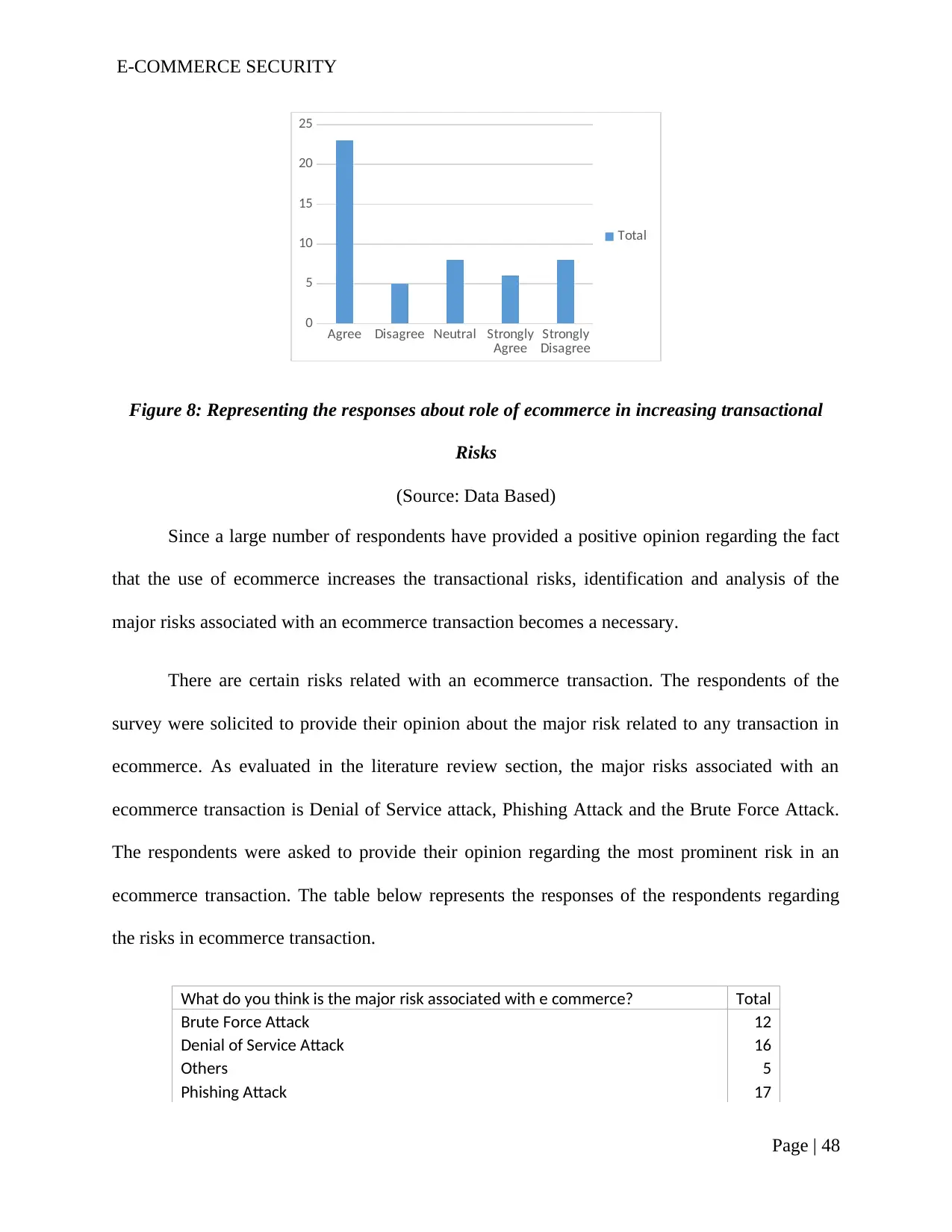
E-COMMERCE SECURITY
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
Total
Figure 8: Representing the responses about role of ecommerce in increasing transactional
Risks
(Source: Data Based)
Since a large number of respondents have provided a positive opinion regarding the fact
that the use of ecommerce increases the transactional risks, identification and analysis of the
major risks associated with an ecommerce transaction becomes a necessary.
There are certain risks related with an ecommerce transaction. The respondents of the
survey were solicited to provide their opinion about the major risk related to any transaction in
ecommerce. As evaluated in the literature review section, the major risks associated with an
ecommerce transaction is Denial of Service attack, Phishing Attack and the Brute Force Attack.
The respondents were asked to provide their opinion regarding the most prominent risk in an
ecommerce transaction. The table below represents the responses of the respondents regarding
the risks in ecommerce transaction.
What do you think is the major risk associated with e commerce? Total
Brute Force Attack 12
Denial of Service Attack 16
Others 5
Phishing Attack 17
Page | 48
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
Total
Figure 8: Representing the responses about role of ecommerce in increasing transactional
Risks
(Source: Data Based)
Since a large number of respondents have provided a positive opinion regarding the fact
that the use of ecommerce increases the transactional risks, identification and analysis of the
major risks associated with an ecommerce transaction becomes a necessary.
There are certain risks related with an ecommerce transaction. The respondents of the
survey were solicited to provide their opinion about the major risk related to any transaction in
ecommerce. As evaluated in the literature review section, the major risks associated with an
ecommerce transaction is Denial of Service attack, Phishing Attack and the Brute Force Attack.
The respondents were asked to provide their opinion regarding the most prominent risk in an
ecommerce transaction. The table below represents the responses of the respondents regarding
the risks in ecommerce transaction.
What do you think is the major risk associated with e commerce? Total
Brute Force Attack 12
Denial of Service Attack 16
Others 5
Phishing Attack 17
Page | 48
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-COMMERCE SECURITY
Grand Total 50
Table 7: Responses regarding the risks in ecommerce
(Source: Data based)
The responses that are obtained from the survey that is conducted indicates that all the
three types of attacks that were analysed and documented in the literature review section of the
research report are considered to be certain most prominent risks related to ecommerce. Highest
number of respondents (17) have marked the phishing attack to be one of the most prominent
risks associated with an ecommerce transaction. 16 respondents have marked Denial of Service
attack as the prominent risk in ecommerce, while that 12 respondents consider Brute Force
Attack to be one of the major risks related to ecommerce transaction.
The Phishing attack is considered to be a type of social engineering attack that is used by
the hackers to steal user’s data that includes login credentials, credit and debit card numbers and
others. This type of attack occurs only if an attacker masquerade as a trusted entity and dupe a
victim in opening an email. This is indeed one of the major risks related an ecommerce
transaction. Therefore, this risk is needed to be mitigated.
The denial of service attack is another major risks related to ecommerce. The denial of
service attack is laid with an aim of shutting down an entire machine or network so that it
becomes inaccessible to the legitimate customers. This is a major risk from the business
perspective and may not be that severe from the perspective of the consumers. When the
resource becomes unavailable for the intended users a normal ecommerce transaction is
interrupted.
Page | 49
Grand Total 50
Table 7: Responses regarding the risks in ecommerce
(Source: Data based)
The responses that are obtained from the survey that is conducted indicates that all the
three types of attacks that were analysed and documented in the literature review section of the
research report are considered to be certain most prominent risks related to ecommerce. Highest
number of respondents (17) have marked the phishing attack to be one of the most prominent
risks associated with an ecommerce transaction. 16 respondents have marked Denial of Service
attack as the prominent risk in ecommerce, while that 12 respondents consider Brute Force
Attack to be one of the major risks related to ecommerce transaction.
The Phishing attack is considered to be a type of social engineering attack that is used by
the hackers to steal user’s data that includes login credentials, credit and debit card numbers and
others. This type of attack occurs only if an attacker masquerade as a trusted entity and dupe a
victim in opening an email. This is indeed one of the major risks related an ecommerce
transaction. Therefore, this risk is needed to be mitigated.
The denial of service attack is another major risks related to ecommerce. The denial of
service attack is laid with an aim of shutting down an entire machine or network so that it
becomes inaccessible to the legitimate customers. This is a major risk from the business
perspective and may not be that severe from the perspective of the consumers. When the
resource becomes unavailable for the intended users a normal ecommerce transaction is
interrupted.
Page | 49
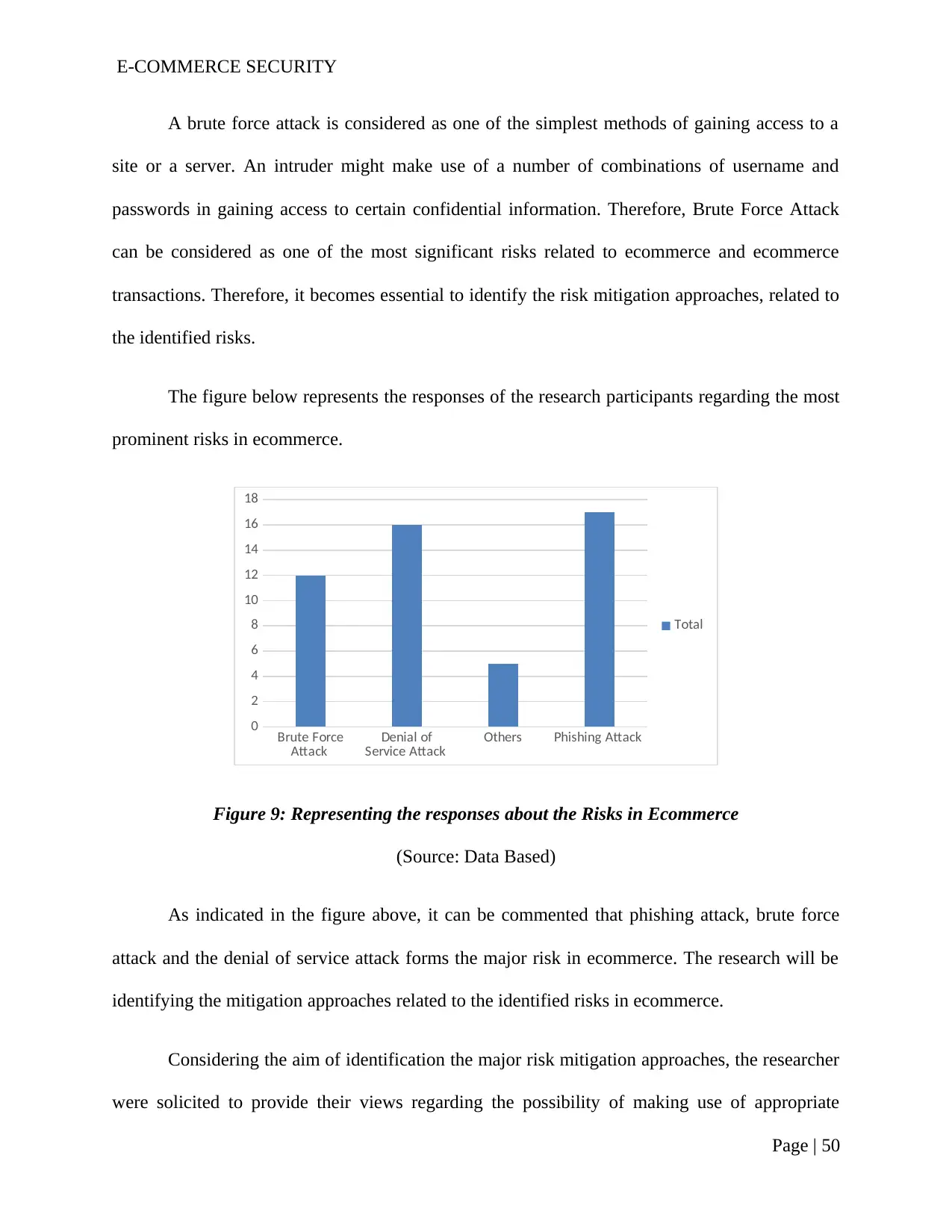
E-COMMERCE SECURITY
A brute force attack is considered as one of the simplest methods of gaining access to a
site or a server. An intruder might make use of a number of combinations of username and
passwords in gaining access to certain confidential information. Therefore, Brute Force Attack
can be considered as one of the most significant risks related to ecommerce and ecommerce
transactions. Therefore, it becomes essential to identify the risk mitigation approaches, related to
the identified risks.
The figure below represents the responses of the research participants regarding the most
prominent risks in ecommerce.
Brute Force
Attack Denial of
Service Attack Others Phishing Attack
0
2
4
6
8
10
12
14
16
18
Total
Figure 9: Representing the responses about the Risks in Ecommerce
(Source: Data Based)
As indicated in the figure above, it can be commented that phishing attack, brute force
attack and the denial of service attack forms the major risk in ecommerce. The research will be
identifying the mitigation approaches related to the identified risks in ecommerce.
Considering the aim of identification the major risk mitigation approaches, the researcher
were solicited to provide their views regarding the possibility of making use of appropriate
Page | 50
A brute force attack is considered as one of the simplest methods of gaining access to a
site or a server. An intruder might make use of a number of combinations of username and
passwords in gaining access to certain confidential information. Therefore, Brute Force Attack
can be considered as one of the most significant risks related to ecommerce and ecommerce
transactions. Therefore, it becomes essential to identify the risk mitigation approaches, related to
the identified risks.
The figure below represents the responses of the research participants regarding the most
prominent risks in ecommerce.
Brute Force
Attack Denial of
Service Attack Others Phishing Attack
0
2
4
6
8
10
12
14
16
18
Total
Figure 9: Representing the responses about the Risks in Ecommerce
(Source: Data Based)
As indicated in the figure above, it can be commented that phishing attack, brute force
attack and the denial of service attack forms the major risk in ecommerce. The research will be
identifying the mitigation approaches related to the identified risks in ecommerce.
Considering the aim of identification the major risk mitigation approaches, the researcher
were solicited to provide their views regarding the possibility of making use of appropriate
Page | 50
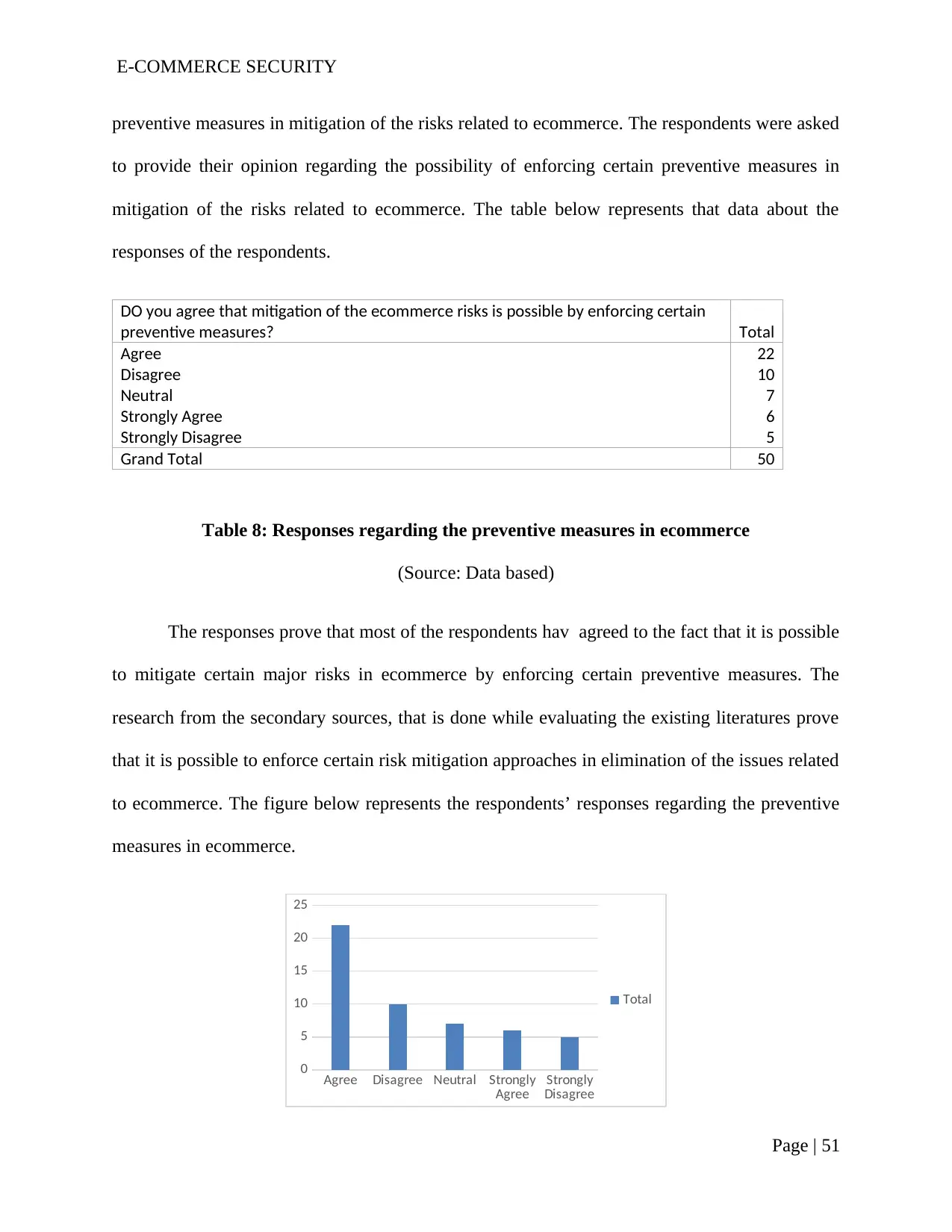
E-COMMERCE SECURITY
preventive measures in mitigation of the risks related to ecommerce. The respondents were asked
to provide their opinion regarding the possibility of enforcing certain preventive measures in
mitigation of the risks related to ecommerce. The table below represents that data about the
responses of the respondents.
DO you agree that mitigation of the ecommerce risks is possible by enforcing certain
preventive measures? Total
Agree 22
Disagree 10
Neutral 7
Strongly Agree 6
Strongly Disagree 5
Grand Total 50
Table 8: Responses regarding the preventive measures in ecommerce
(Source: Data based)
The responses prove that most of the respondents hav agreed to the fact that it is possible
to mitigate certain major risks in ecommerce by enforcing certain preventive measures. The
research from the secondary sources, that is done while evaluating the existing literatures prove
that it is possible to enforce certain risk mitigation approaches in elimination of the issues related
to ecommerce. The figure below represents the respondents’ responses regarding the preventive
measures in ecommerce.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
Total
Page | 51
preventive measures in mitigation of the risks related to ecommerce. The respondents were asked
to provide their opinion regarding the possibility of enforcing certain preventive measures in
mitigation of the risks related to ecommerce. The table below represents that data about the
responses of the respondents.
DO you agree that mitigation of the ecommerce risks is possible by enforcing certain
preventive measures? Total
Agree 22
Disagree 10
Neutral 7
Strongly Agree 6
Strongly Disagree 5
Grand Total 50
Table 8: Responses regarding the preventive measures in ecommerce
(Source: Data based)
The responses prove that most of the respondents hav agreed to the fact that it is possible
to mitigate certain major risks in ecommerce by enforcing certain preventive measures. The
research from the secondary sources, that is done while evaluating the existing literatures prove
that it is possible to enforce certain risk mitigation approaches in elimination of the issues related
to ecommerce. The figure below represents the respondents’ responses regarding the preventive
measures in ecommerce.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
Total
Page | 51
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

E-COMMERCE SECURITY
Figure 10: Representing the preventive measures in Ecommerce
(Source: Data Based)
The responses received indicates that it is possible to mitigate or reduce the risks
associated with ecommerce by making use of certain risk mitigation approaches or processes.
On identification of the major risks related to ecommerce, the researcher has indicated
that need of identifying the preventive measures. As indicated in the literature review section of
the research report, encryption is considered to be a major risk mitigation approach related to
ecommerce transaction. Thus, the respondents were solicited to offer their opinion regarding on
whether encryption can be considered as an approach for risk mitigation in ecommerce
transactions. The responses of the respondents is indicated in the table below-
DO you agree that that encryption is one of the most efficient risk mitigation approaches
related to ecommerce?
Tota
l
Agree 23
Disagree 6
Neutral 10
Strongly Agree 6
Strongly Disagree 5
Grand Total 50
Table 9: Responses on Encryption as a Risk Management Approach
(Source: Data based)
The above table indicates that encryption is one of the most efficient approach of risk
management in ecommerce. This can be an effective measure against the phishing attack.
However, 11 respondents out of the chosen 50 respondents considers that encryption is not a
significant risk mitigation approach. The reason behind this can be the fact that not all risks
Page | 52
Figure 10: Representing the preventive measures in Ecommerce
(Source: Data Based)
The responses received indicates that it is possible to mitigate or reduce the risks
associated with ecommerce by making use of certain risk mitigation approaches or processes.
On identification of the major risks related to ecommerce, the researcher has indicated
that need of identifying the preventive measures. As indicated in the literature review section of
the research report, encryption is considered to be a major risk mitigation approach related to
ecommerce transaction. Thus, the respondents were solicited to offer their opinion regarding on
whether encryption can be considered as an approach for risk mitigation in ecommerce
transactions. The responses of the respondents is indicated in the table below-
DO you agree that that encryption is one of the most efficient risk mitigation approaches
related to ecommerce?
Tota
l
Agree 23
Disagree 6
Neutral 10
Strongly Agree 6
Strongly Disagree 5
Grand Total 50
Table 9: Responses on Encryption as a Risk Management Approach
(Source: Data based)
The above table indicates that encryption is one of the most efficient approach of risk
management in ecommerce. This can be an effective measure against the phishing attack.
However, 11 respondents out of the chosen 50 respondents considers that encryption is not a
significant risk mitigation approach. The reason behind this can be the fact that not all risks
Page | 52
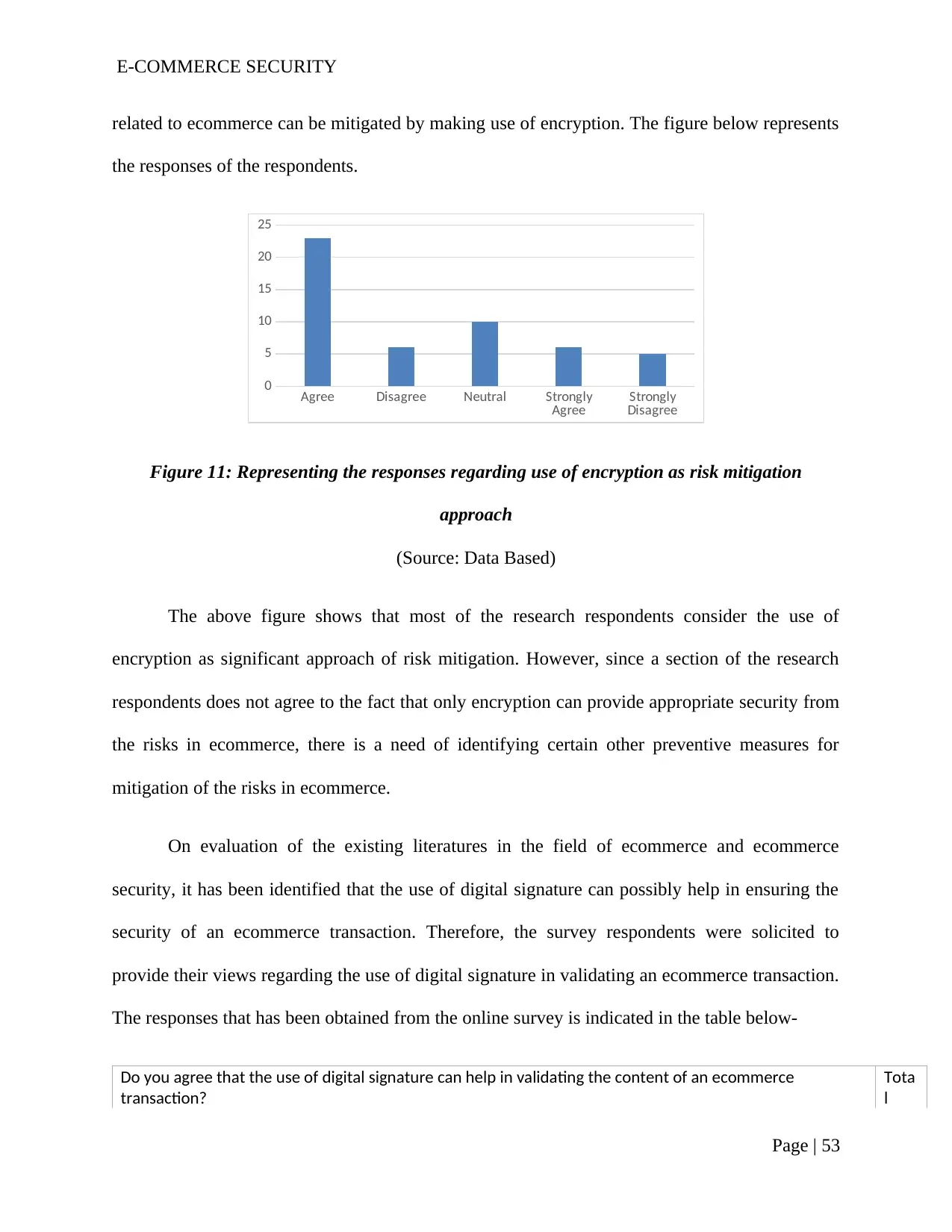
E-COMMERCE SECURITY
related to ecommerce can be mitigated by making use of encryption. The figure below represents
the responses of the respondents.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
Figure 11: Representing the responses regarding use of encryption as risk mitigation
approach
(Source: Data Based)
The above figure shows that most of the research respondents consider the use of
encryption as significant approach of risk mitigation. However, since a section of the research
respondents does not agree to the fact that only encryption can provide appropriate security from
the risks in ecommerce, there is a need of identifying certain other preventive measures for
mitigation of the risks in ecommerce.
On evaluation of the existing literatures in the field of ecommerce and ecommerce
security, it has been identified that the use of digital signature can possibly help in ensuring the
security of an ecommerce transaction. Therefore, the survey respondents were solicited to
provide their views regarding the use of digital signature in validating an ecommerce transaction.
The responses that has been obtained from the online survey is indicated in the table below-
Do you agree that the use of digital signature can help in validating the content of an ecommerce
transaction?
Tota
l
Page | 53
related to ecommerce can be mitigated by making use of encryption. The figure below represents
the responses of the respondents.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
Figure 11: Representing the responses regarding use of encryption as risk mitigation
approach
(Source: Data Based)
The above figure shows that most of the research respondents consider the use of
encryption as significant approach of risk mitigation. However, since a section of the research
respondents does not agree to the fact that only encryption can provide appropriate security from
the risks in ecommerce, there is a need of identifying certain other preventive measures for
mitigation of the risks in ecommerce.
On evaluation of the existing literatures in the field of ecommerce and ecommerce
security, it has been identified that the use of digital signature can possibly help in ensuring the
security of an ecommerce transaction. Therefore, the survey respondents were solicited to
provide their views regarding the use of digital signature in validating an ecommerce transaction.
The responses that has been obtained from the online survey is indicated in the table below-
Do you agree that the use of digital signature can help in validating the content of an ecommerce
transaction?
Tota
l
Page | 53
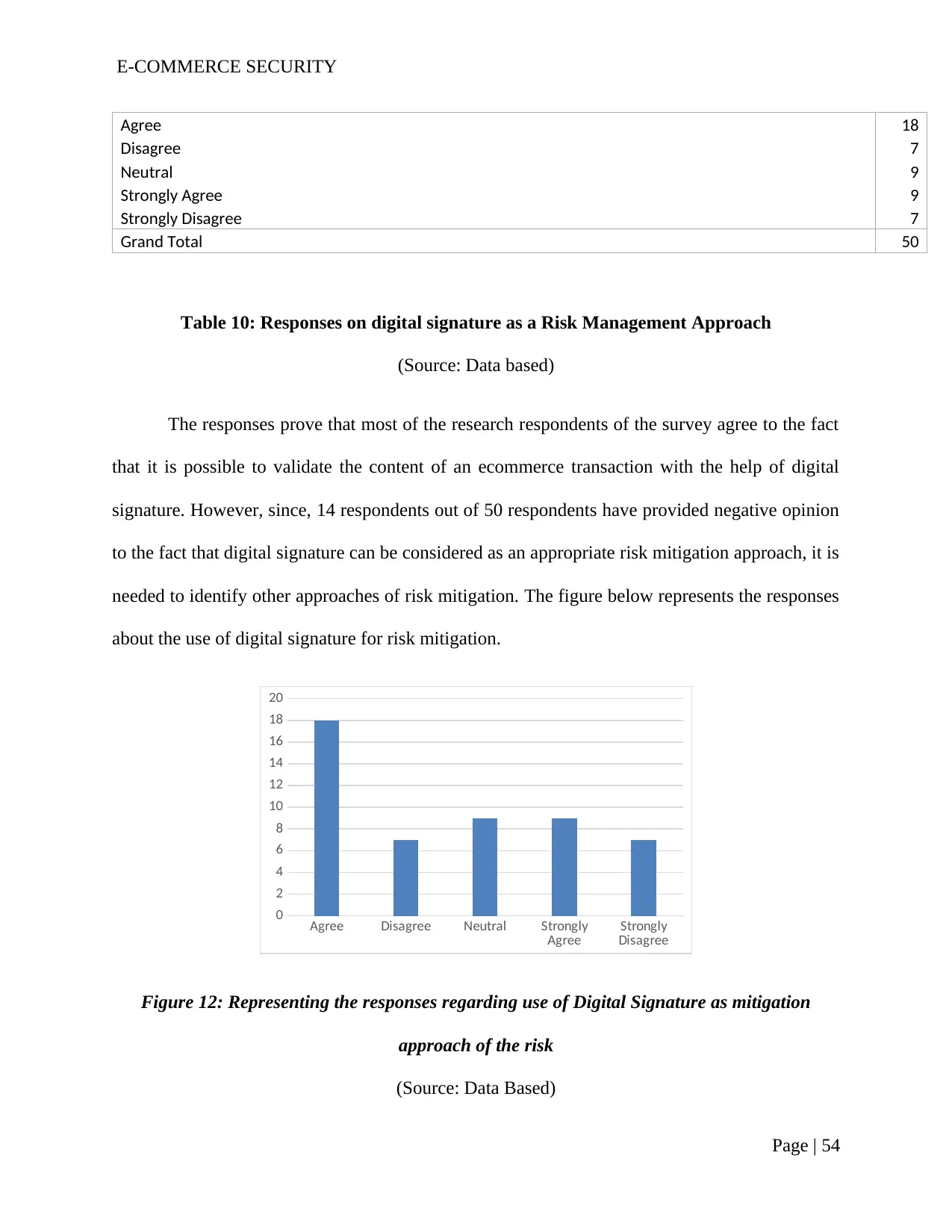
E-COMMERCE SECURITY
Agree 18
Disagree 7
Neutral 9
Strongly Agree 9
Strongly Disagree 7
Grand Total 50
Table 10: Responses on digital signature as a Risk Management Approach
(Source: Data based)
The responses prove that most of the research respondents of the survey agree to the fact
that it is possible to validate the content of an ecommerce transaction with the help of digital
signature. However, since, 14 respondents out of 50 respondents have provided negative opinion
to the fact that digital signature can be considered as an appropriate risk mitigation approach, it is
needed to identify other approaches of risk mitigation. The figure below represents the responses
about the use of digital signature for risk mitigation.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
2
4
6
8
10
12
14
16
18
20
Figure 12: Representing the responses regarding use of Digital Signature as mitigation
approach of the risk
(Source: Data Based)
Page | 54
Agree 18
Disagree 7
Neutral 9
Strongly Agree 9
Strongly Disagree 7
Grand Total 50
Table 10: Responses on digital signature as a Risk Management Approach
(Source: Data based)
The responses prove that most of the research respondents of the survey agree to the fact
that it is possible to validate the content of an ecommerce transaction with the help of digital
signature. However, since, 14 respondents out of 50 respondents have provided negative opinion
to the fact that digital signature can be considered as an appropriate risk mitigation approach, it is
needed to identify other approaches of risk mitigation. The figure below represents the responses
about the use of digital signature for risk mitigation.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
2
4
6
8
10
12
14
16
18
20
Figure 12: Representing the responses regarding use of Digital Signature as mitigation
approach of the risk
(Source: Data Based)
Page | 54
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-COMMERCE SECURITY
The use of digital signature is considered to be a viable risk mitigation approach in case
of mitigation of the risks related to ecommerce transaction. It is mandatory to validate the
transactions related to ecommerce.
As indicated in the literature review part of the research report, the use of firewalls can
considerably reduce the risks associated with an ecommerce transaction. The respondents were
solicited to provide their views regarding the use of firewalls in risk mitigation in ecommerce.
The table below gives an idea of the responses received in this regard.
DO you agree that business organization should make use of firewalls in order to prevent unauthorized
intrusion?
Tota
l
Agree 23
Disagree 7
Neutral 7
Strongly Agree 6
Strongly Disagree 7
Grand Total 50
Table 11: Responses on firewall as a Risk Management Approach
(Source: Data based)
From the table above, it is seen that the firewalls are considered to be an efficient risk
mitigation process related to ecommerce transaction. The responses of the respondents are
indicated in the figure below-
Page | 55
The use of digital signature is considered to be a viable risk mitigation approach in case
of mitigation of the risks related to ecommerce transaction. It is mandatory to validate the
transactions related to ecommerce.
As indicated in the literature review part of the research report, the use of firewalls can
considerably reduce the risks associated with an ecommerce transaction. The respondents were
solicited to provide their views regarding the use of firewalls in risk mitigation in ecommerce.
The table below gives an idea of the responses received in this regard.
DO you agree that business organization should make use of firewalls in order to prevent unauthorized
intrusion?
Tota
l
Agree 23
Disagree 7
Neutral 7
Strongly Agree 6
Strongly Disagree 7
Grand Total 50
Table 11: Responses on firewall as a Risk Management Approach
(Source: Data based)
From the table above, it is seen that the firewalls are considered to be an efficient risk
mitigation process related to ecommerce transaction. The responses of the respondents are
indicated in the figure below-
Page | 55
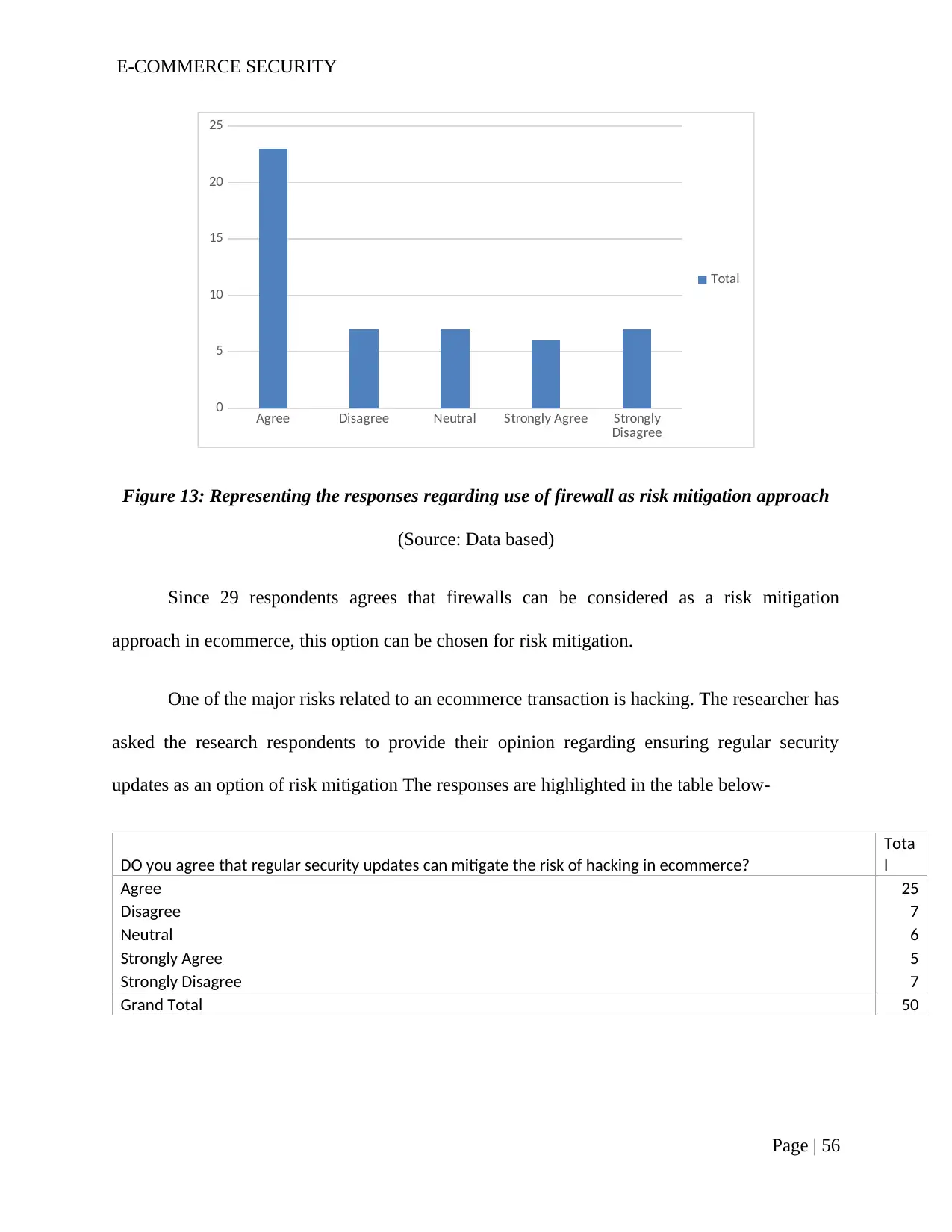
E-COMMERCE SECURITY
Agree Disagree Neutral Strongly Agree Strongly
Disagree
0
5
10
15
20
25
Total
Figure 13: Representing the responses regarding use of firewall as risk mitigation approach
(Source: Data based)
Since 29 respondents agrees that firewalls can be considered as a risk mitigation
approach in ecommerce, this option can be chosen for risk mitigation.
One of the major risks related to an ecommerce transaction is hacking. The researcher has
asked the research respondents to provide their opinion regarding ensuring regular security
updates as an option of risk mitigation The responses are highlighted in the table below-
DO you agree that regular security updates can mitigate the risk of hacking in ecommerce?
Tota
l
Agree 25
Disagree 7
Neutral 6
Strongly Agree 5
Strongly Disagree 7
Grand Total 50
Page | 56
Agree Disagree Neutral Strongly Agree Strongly
Disagree
0
5
10
15
20
25
Total
Figure 13: Representing the responses regarding use of firewall as risk mitigation approach
(Source: Data based)
Since 29 respondents agrees that firewalls can be considered as a risk mitigation
approach in ecommerce, this option can be chosen for risk mitigation.
One of the major risks related to an ecommerce transaction is hacking. The researcher has
asked the research respondents to provide their opinion regarding ensuring regular security
updates as an option of risk mitigation The responses are highlighted in the table below-
DO you agree that regular security updates can mitigate the risk of hacking in ecommerce?
Tota
l
Agree 25
Disagree 7
Neutral 6
Strongly Agree 5
Strongly Disagree 7
Grand Total 50
Page | 56
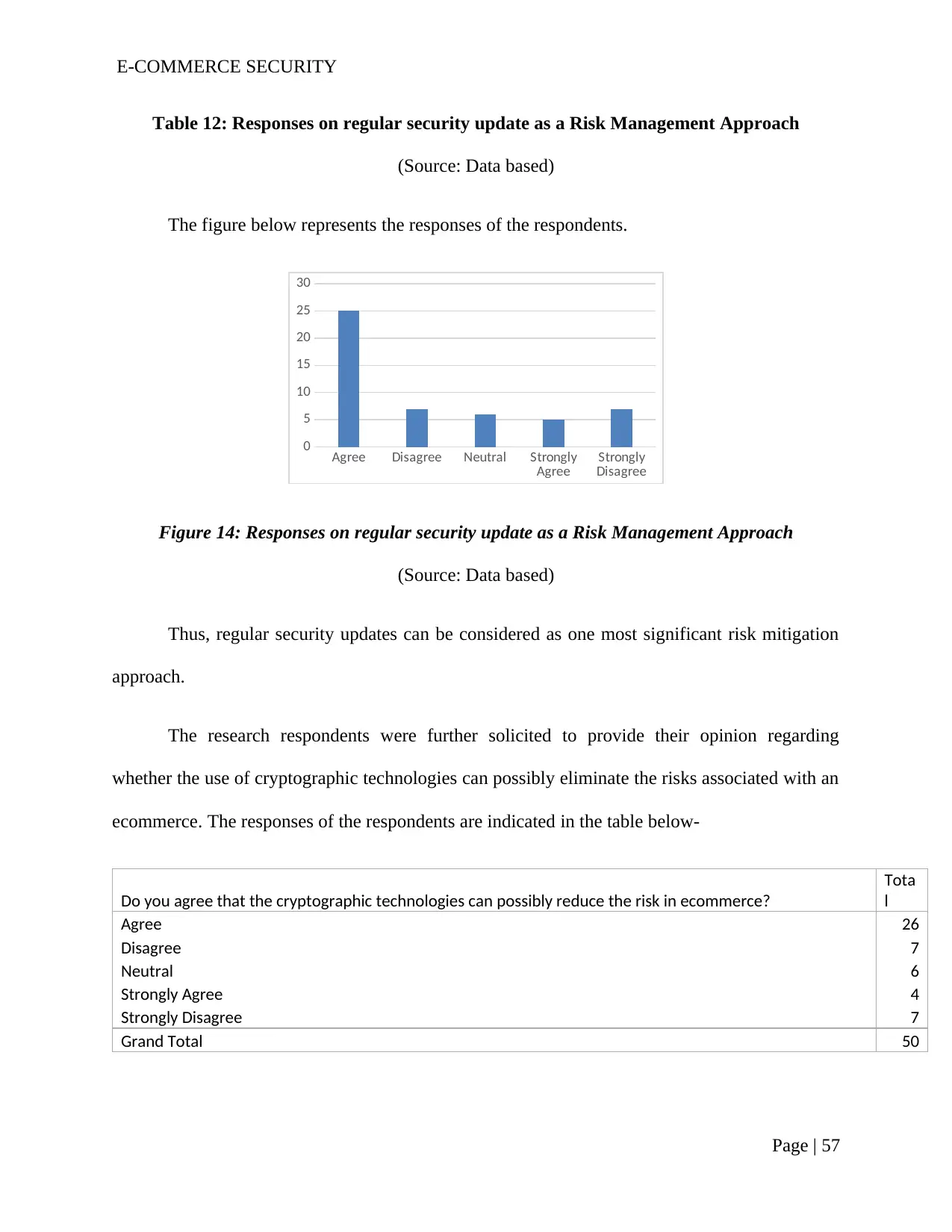
E-COMMERCE SECURITY
Table 12: Responses on regular security update as a Risk Management Approach
(Source: Data based)
The figure below represents the responses of the respondents.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
30
Figure 14: Responses on regular security update as a Risk Management Approach
(Source: Data based)
Thus, regular security updates can be considered as one most significant risk mitigation
approach.
The research respondents were further solicited to provide their opinion regarding
whether the use of cryptographic technologies can possibly eliminate the risks associated with an
ecommerce. The responses of the respondents are indicated in the table below-
Do you agree that the cryptographic technologies can possibly reduce the risk in ecommerce?
Tota
l
Agree 26
Disagree 7
Neutral 6
Strongly Agree 4
Strongly Disagree 7
Grand Total 50
Page | 57
Table 12: Responses on regular security update as a Risk Management Approach
(Source: Data based)
The figure below represents the responses of the respondents.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
30
Figure 14: Responses on regular security update as a Risk Management Approach
(Source: Data based)
Thus, regular security updates can be considered as one most significant risk mitigation
approach.
The research respondents were further solicited to provide their opinion regarding
whether the use of cryptographic technologies can possibly eliminate the risks associated with an
ecommerce. The responses of the respondents are indicated in the table below-
Do you agree that the cryptographic technologies can possibly reduce the risk in ecommerce?
Tota
l
Agree 26
Disagree 7
Neutral 6
Strongly Agree 4
Strongly Disagree 7
Grand Total 50
Page | 57
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
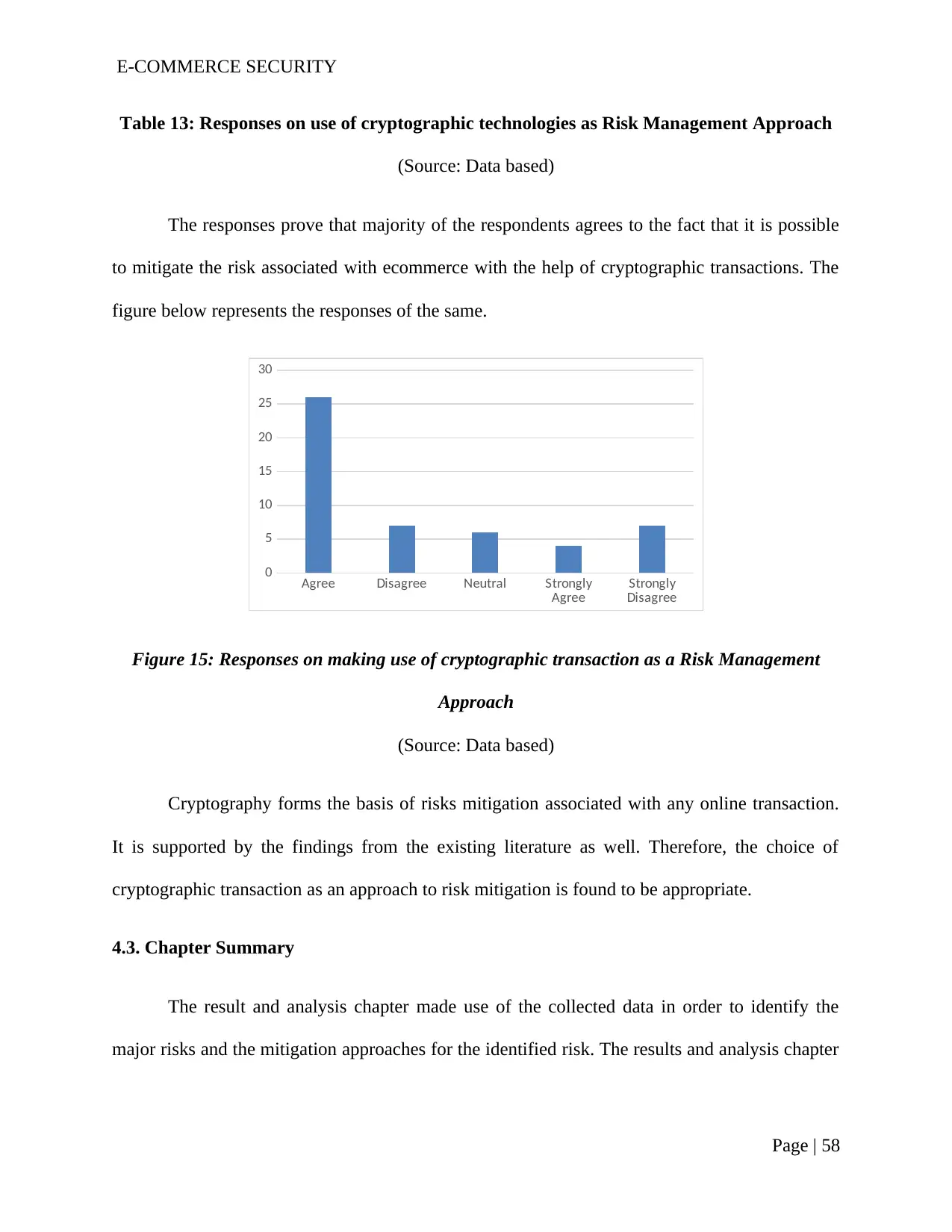
E-COMMERCE SECURITY
Table 13: Responses on use of cryptographic technologies as Risk Management Approach
(Source: Data based)
The responses prove that majority of the respondents agrees to the fact that it is possible
to mitigate the risk associated with ecommerce with the help of cryptographic transactions. The
figure below represents the responses of the same.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
30
Figure 15: Responses on making use of cryptographic transaction as a Risk Management
Approach
(Source: Data based)
Cryptography forms the basis of risks mitigation associated with any online transaction.
It is supported by the findings from the existing literature as well. Therefore, the choice of
cryptographic transaction as an approach to risk mitigation is found to be appropriate.
4.3. Chapter Summary
The result and analysis chapter made use of the collected data in order to identify the
major risks and the mitigation approaches for the identified risk. The results and analysis chapter
Page | 58
Table 13: Responses on use of cryptographic technologies as Risk Management Approach
(Source: Data based)
The responses prove that majority of the respondents agrees to the fact that it is possible
to mitigate the risk associated with ecommerce with the help of cryptographic transactions. The
figure below represents the responses of the same.
Agree Disagree Neutral Strongly
Agree Strongly
Disagree
0
5
10
15
20
25
30
Figure 15: Responses on making use of cryptographic transaction as a Risk Management
Approach
(Source: Data based)
Cryptography forms the basis of risks mitigation associated with any online transaction.
It is supported by the findings from the existing literature as well. Therefore, the choice of
cryptographic transaction as an approach to risk mitigation is found to be appropriate.
4.3. Chapter Summary
The result and analysis chapter made use of the collected data in order to identify the
major risks and the mitigation approaches for the identified risk. The results and analysis chapter
Page | 58

E-COMMERCE SECURITY
is mainly based on the data collected from the survey. The data analysis chapter successfully
identifies the major risks and discusses the risk mitigation approaches.
Page | 59
is mainly based on the data collected from the survey. The data analysis chapter successfully
identifies the major risks and discusses the risk mitigation approaches.
Page | 59

E-COMMERCE SECURITY
Chapter 5: Discussion and Recommendations
5.1. Introduction
The aim of the discussion and the recommendation chapter is to analyse the findings of
the data analysis chapter and to relate those findings with the data that has been collected from
the extensive literature review. The dissertation aims in analysis of e commerce security,
identification of the major risks in ecommerce and the analysis of the risk mitigation approaches
that has been found while reviewing the literature associated with ecommerce and transactions in
ecommerce. The discussion chapter will form the base of the recommendations related to the
enforcement of e-commerce security. The recommendations will be provided mainly on basis of
the results received from the quantitative analysis of collected data, from the primary sources.
The validity of the data obtained from the primary sources will be examined on basis of the data
collected from the secondary sources in the literature review part of the research.
5.2. Discussion
The literature review section of this report identifies the major risks related to the security
of ecommerce. The data obtained from the literature review section of the research indicates that
the major related to an e-commerce transaction includes Brute Force Attack and phishing attack.
Apart from that, the denial of service attack is considered to be another most significant risk
associated with an e-commerce security. The collected from the primary sources, also indicates
the presence of such risk in ecommerce transaction. The figure below indicates the responses of
the primary sources regarding the most significant risk in an ecommerce transaction.
Page | 60
Chapter 5: Discussion and Recommendations
5.1. Introduction
The aim of the discussion and the recommendation chapter is to analyse the findings of
the data analysis chapter and to relate those findings with the data that has been collected from
the extensive literature review. The dissertation aims in analysis of e commerce security,
identification of the major risks in ecommerce and the analysis of the risk mitigation approaches
that has been found while reviewing the literature associated with ecommerce and transactions in
ecommerce. The discussion chapter will form the base of the recommendations related to the
enforcement of e-commerce security. The recommendations will be provided mainly on basis of
the results received from the quantitative analysis of collected data, from the primary sources.
The validity of the data obtained from the primary sources will be examined on basis of the data
collected from the secondary sources in the literature review part of the research.
5.2. Discussion
The literature review section of this report identifies the major risks related to the security
of ecommerce. The data obtained from the literature review section of the research indicates that
the major related to an e-commerce transaction includes Brute Force Attack and phishing attack.
Apart from that, the denial of service attack is considered to be another most significant risk
associated with an e-commerce security. The collected from the primary sources, also indicates
the presence of such risk in ecommerce transaction. The figure below indicates the responses of
the primary sources regarding the most significant risk in an ecommerce transaction.
Page | 60
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
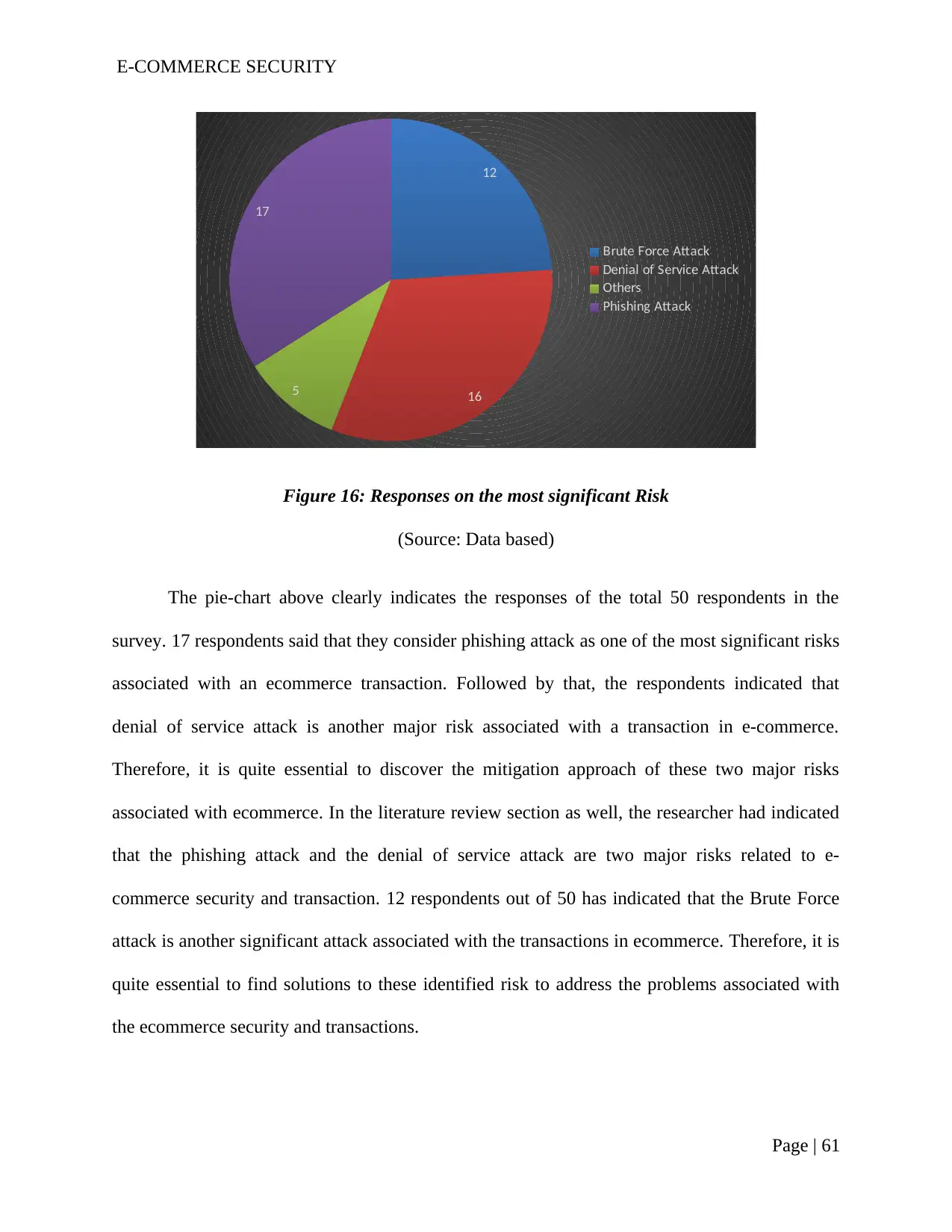
E-COMMERCE SECURITY
12
165
17
Brute Force Attack
Denial of Service Attack
Others
Phishing Attack
Figure 16: Responses on the most significant Risk
(Source: Data based)
The pie-chart above clearly indicates the responses of the total 50 respondents in the
survey. 17 respondents said that they consider phishing attack as one of the most significant risks
associated with an ecommerce transaction. Followed by that, the respondents indicated that
denial of service attack is another major risk associated with a transaction in e-commerce.
Therefore, it is quite essential to discover the mitigation approach of these two major risks
associated with ecommerce. In the literature review section as well, the researcher had indicated
that the phishing attack and the denial of service attack are two major risks related to e-
commerce security and transaction. 12 respondents out of 50 has indicated that the Brute Force
attack is another significant attack associated with the transactions in ecommerce. Therefore, it is
quite essential to find solutions to these identified risk to address the problems associated with
the ecommerce security and transactions.
Page | 61
12
165
17
Brute Force Attack
Denial of Service Attack
Others
Phishing Attack
Figure 16: Responses on the most significant Risk
(Source: Data based)
The pie-chart above clearly indicates the responses of the total 50 respondents in the
survey. 17 respondents said that they consider phishing attack as one of the most significant risks
associated with an ecommerce transaction. Followed by that, the respondents indicated that
denial of service attack is another major risk associated with a transaction in e-commerce.
Therefore, it is quite essential to discover the mitigation approach of these two major risks
associated with ecommerce. In the literature review section as well, the researcher had indicated
that the phishing attack and the denial of service attack are two major risks related to e-
commerce security and transaction. 12 respondents out of 50 has indicated that the Brute Force
attack is another significant attack associated with the transactions in ecommerce. Therefore, it is
quite essential to find solutions to these identified risk to address the problems associated with
the ecommerce security and transactions.
Page | 61
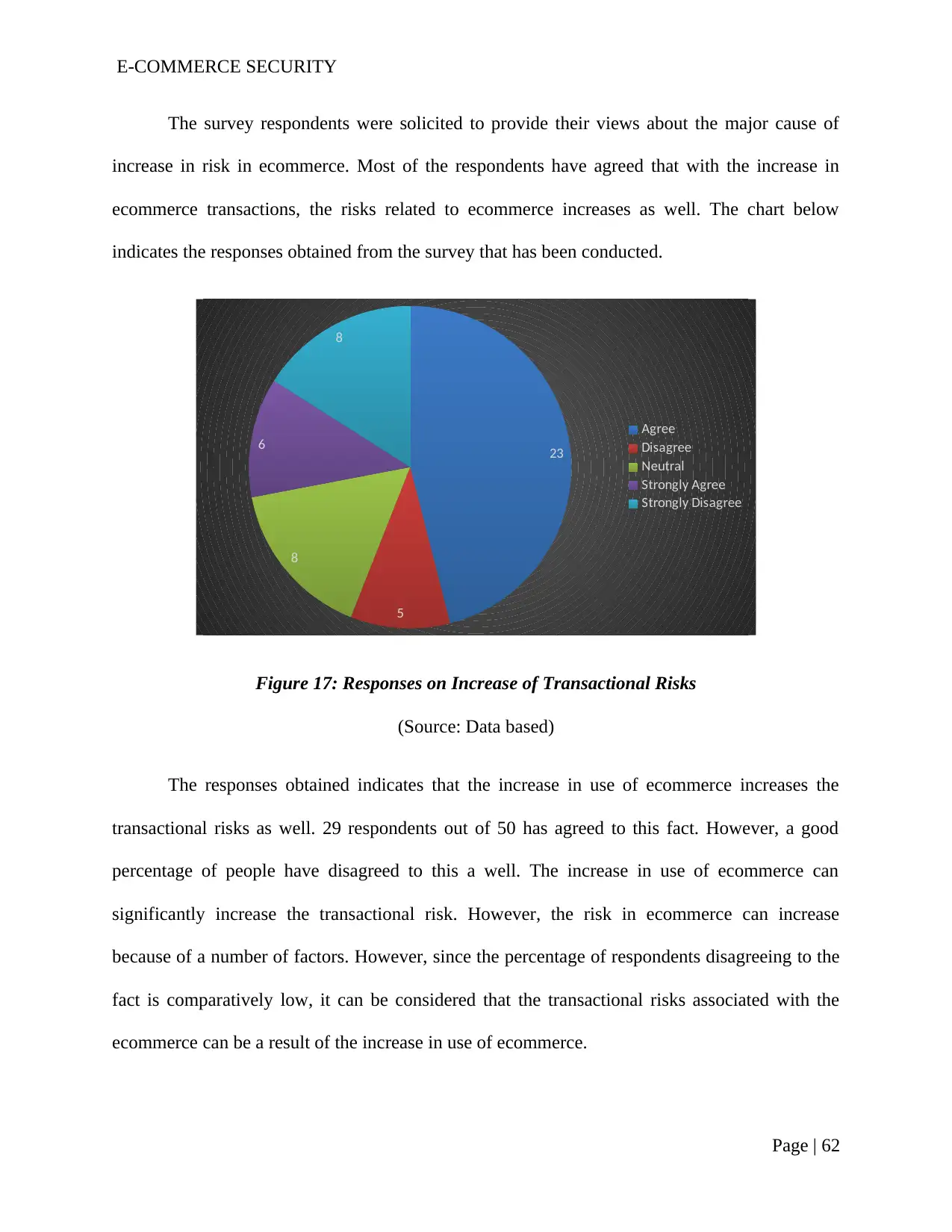
E-COMMERCE SECURITY
The survey respondents were solicited to provide their views about the major cause of
increase in risk in ecommerce. Most of the respondents have agreed that with the increase in
ecommerce transactions, the risks related to ecommerce increases as well. The chart below
indicates the responses obtained from the survey that has been conducted.
23
5
8
6
8
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 17: Responses on Increase of Transactional Risks
(Source: Data based)
The responses obtained indicates that the increase in use of ecommerce increases the
transactional risks as well. 29 respondents out of 50 has agreed to this fact. However, a good
percentage of people have disagreed to this a well. The increase in use of ecommerce can
significantly increase the transactional risk. However, the risk in ecommerce can increase
because of a number of factors. However, since the percentage of respondents disagreeing to the
fact is comparatively low, it can be considered that the transactional risks associated with the
ecommerce can be a result of the increase in use of ecommerce.
Page | 62
The survey respondents were solicited to provide their views about the major cause of
increase in risk in ecommerce. Most of the respondents have agreed that with the increase in
ecommerce transactions, the risks related to ecommerce increases as well. The chart below
indicates the responses obtained from the survey that has been conducted.
23
5
8
6
8
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 17: Responses on Increase of Transactional Risks
(Source: Data based)
The responses obtained indicates that the increase in use of ecommerce increases the
transactional risks as well. 29 respondents out of 50 has agreed to this fact. However, a good
percentage of people have disagreed to this a well. The increase in use of ecommerce can
significantly increase the transactional risk. However, the risk in ecommerce can increase
because of a number of factors. However, since the percentage of respondents disagreeing to the
fact is comparatively low, it can be considered that the transactional risks associated with the
ecommerce can be a result of the increase in use of ecommerce.
Page | 62

E-COMMERCE SECURITY
The risks and issues associated with the ecommerce is needed to be mitigated. The data
related to the risk mitigation approaches are collected from the primary sources. The literature
review section of this research report has analysed various mitigation approaches of the risk. The
identified mitigation approaches of the risks include making use of encryption technology,
making use of digital signature and making use of digital envelope. Risk management is a
planned approach. The steps in risk management process involves the risk analysis and
identification of mitigation approaches of the risk. Encryption is identified as one most effective
risk mitigation approaches related to the transactional risks in ecommerce. The chart below
indicates the responses regarding the use of encryption as a risk mitigation approach.
23
6
10
6
5
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 18: Responses on use of encryption as risk mitigation approach
(Source: Data based)
The responses indicates that most of the research respondents have agreed that encryption
is one of the most effective risk mitigation techniques related to e-commerce. Encryption is one
of the most effective techniques of risk mitigation. Encryption is a cryptographic technique that
Page | 63
The risks and issues associated with the ecommerce is needed to be mitigated. The data
related to the risk mitigation approaches are collected from the primary sources. The literature
review section of this research report has analysed various mitigation approaches of the risk. The
identified mitigation approaches of the risks include making use of encryption technology,
making use of digital signature and making use of digital envelope. Risk management is a
planned approach. The steps in risk management process involves the risk analysis and
identification of mitigation approaches of the risk. Encryption is identified as one most effective
risk mitigation approaches related to the transactional risks in ecommerce. The chart below
indicates the responses regarding the use of encryption as a risk mitigation approach.
23
6
10
6
5
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 18: Responses on use of encryption as risk mitigation approach
(Source: Data based)
The responses indicates that most of the research respondents have agreed that encryption
is one of the most effective risk mitigation techniques related to e-commerce. Encryption is one
of the most effective techniques of risk mitigation. Encryption is a cryptographic technique that
Page | 63
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
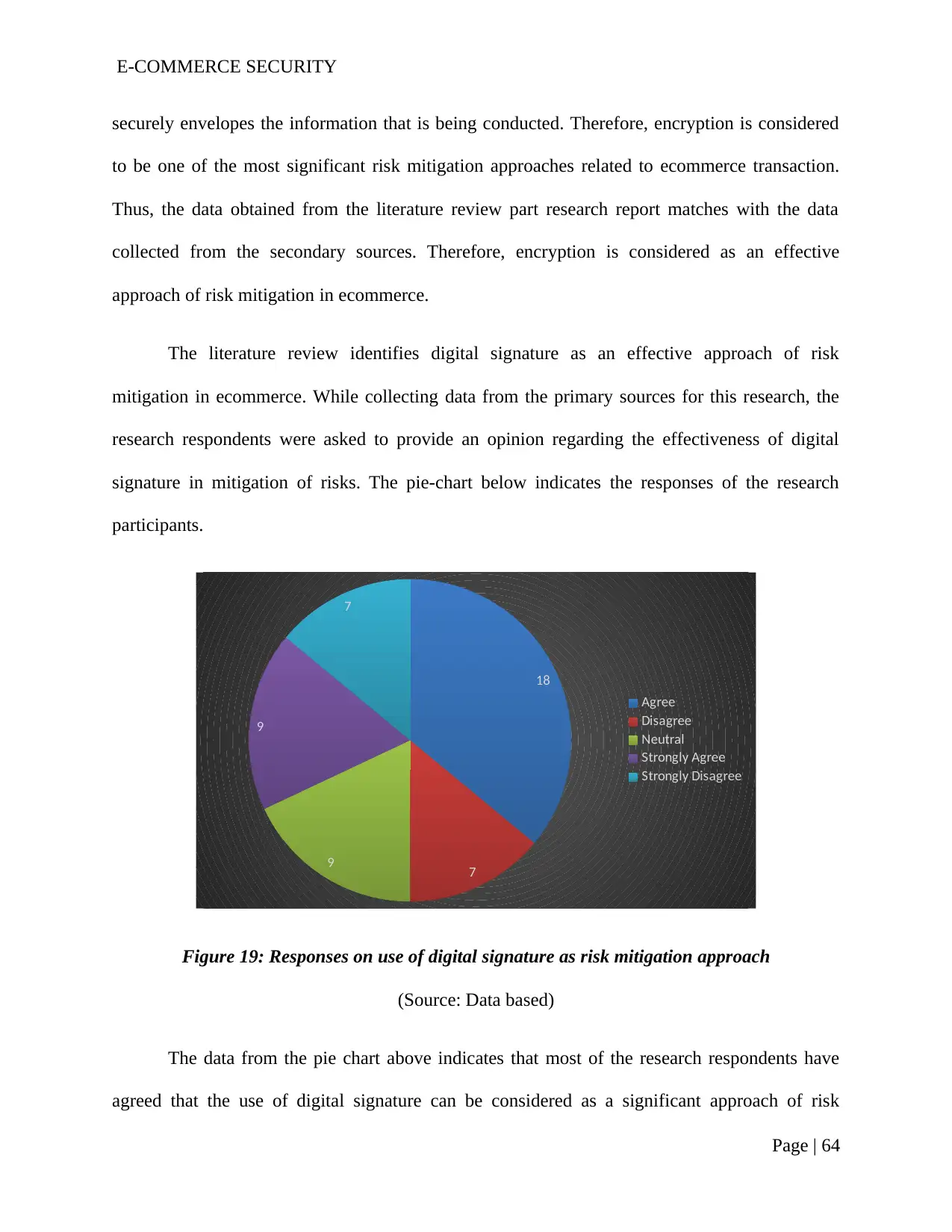
E-COMMERCE SECURITY
securely envelopes the information that is being conducted. Therefore, encryption is considered
to be one of the most significant risk mitigation approaches related to ecommerce transaction.
Thus, the data obtained from the literature review part research report matches with the data
collected from the secondary sources. Therefore, encryption is considered as an effective
approach of risk mitigation in ecommerce.
The literature review identifies digital signature as an effective approach of risk
mitigation in ecommerce. While collecting data from the primary sources for this research, the
research respondents were asked to provide an opinion regarding the effectiveness of digital
signature in mitigation of risks. The pie-chart below indicates the responses of the research
participants.
18
7
9
9
7
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 19: Responses on use of digital signature as risk mitigation approach
(Source: Data based)
The data from the pie chart above indicates that most of the research respondents have
agreed that the use of digital signature can be considered as a significant approach of risk
Page | 64
securely envelopes the information that is being conducted. Therefore, encryption is considered
to be one of the most significant risk mitigation approaches related to ecommerce transaction.
Thus, the data obtained from the literature review part research report matches with the data
collected from the secondary sources. Therefore, encryption is considered as an effective
approach of risk mitigation in ecommerce.
The literature review identifies digital signature as an effective approach of risk
mitigation in ecommerce. While collecting data from the primary sources for this research, the
research respondents were asked to provide an opinion regarding the effectiveness of digital
signature in mitigation of risks. The pie-chart below indicates the responses of the research
participants.
18
7
9
9
7
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 19: Responses on use of digital signature as risk mitigation approach
(Source: Data based)
The data from the pie chart above indicates that most of the research respondents have
agreed that the use of digital signature can be considered as a significant approach of risk
Page | 64
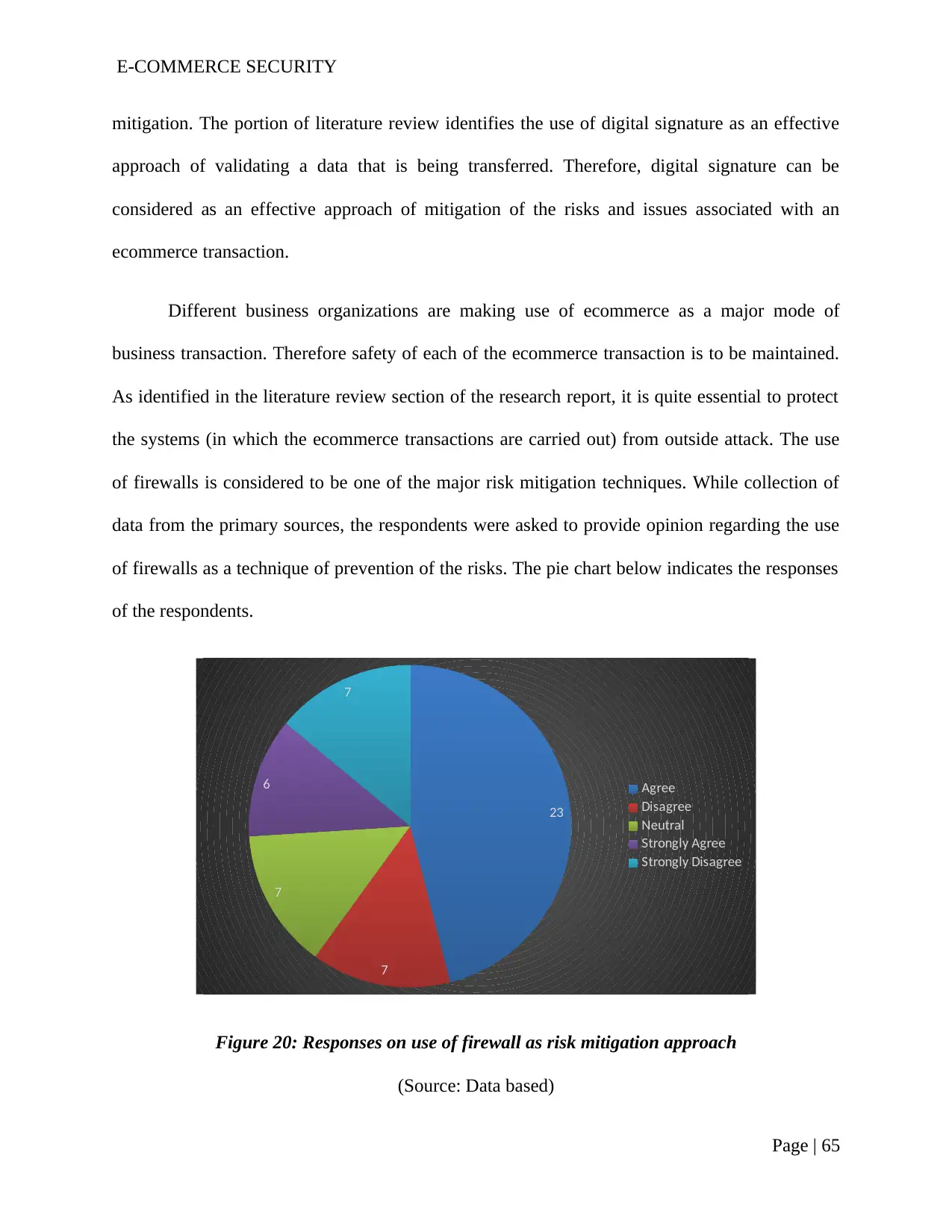
E-COMMERCE SECURITY
mitigation. The portion of literature review identifies the use of digital signature as an effective
approach of validating a data that is being transferred. Therefore, digital signature can be
considered as an effective approach of mitigation of the risks and issues associated with an
ecommerce transaction.
Different business organizations are making use of ecommerce as a major mode of
business transaction. Therefore safety of each of the ecommerce transaction is to be maintained.
As identified in the literature review section of the research report, it is quite essential to protect
the systems (in which the ecommerce transactions are carried out) from outside attack. The use
of firewalls is considered to be one of the major risk mitigation techniques. While collection of
data from the primary sources, the respondents were asked to provide opinion regarding the use
of firewalls as a technique of prevention of the risks. The pie chart below indicates the responses
of the respondents.
23
7
7
6
7
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 20: Responses on use of firewall as risk mitigation approach
(Source: Data based)
Page | 65
mitigation. The portion of literature review identifies the use of digital signature as an effective
approach of validating a data that is being transferred. Therefore, digital signature can be
considered as an effective approach of mitigation of the risks and issues associated with an
ecommerce transaction.
Different business organizations are making use of ecommerce as a major mode of
business transaction. Therefore safety of each of the ecommerce transaction is to be maintained.
As identified in the literature review section of the research report, it is quite essential to protect
the systems (in which the ecommerce transactions are carried out) from outside attack. The use
of firewalls is considered to be one of the major risk mitigation techniques. While collection of
data from the primary sources, the respondents were asked to provide opinion regarding the use
of firewalls as a technique of prevention of the risks. The pie chart below indicates the responses
of the respondents.
23
7
7
6
7
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 20: Responses on use of firewall as risk mitigation approach
(Source: Data based)
Page | 65
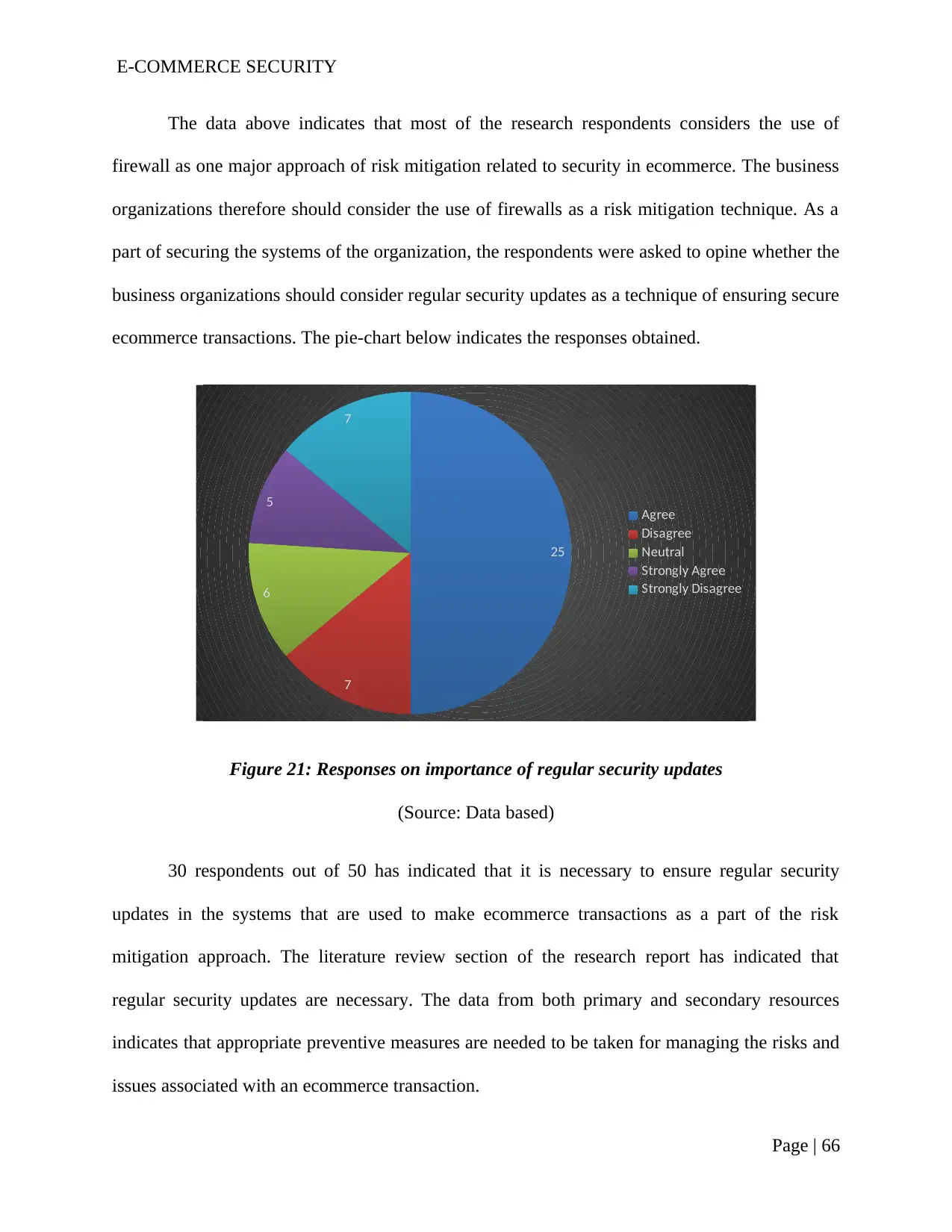
E-COMMERCE SECURITY
The data above indicates that most of the research respondents considers the use of
firewall as one major approach of risk mitigation related to security in ecommerce. The business
organizations therefore should consider the use of firewalls as a risk mitigation technique. As a
part of securing the systems of the organization, the respondents were asked to opine whether the
business organizations should consider regular security updates as a technique of ensuring secure
ecommerce transactions. The pie-chart below indicates the responses obtained.
25
7
6
5
7
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 21: Responses on importance of regular security updates
(Source: Data based)
30 respondents out of 50 has indicated that it is necessary to ensure regular security
updates in the systems that are used to make ecommerce transactions as a part of the risk
mitigation approach. The literature review section of the research report has indicated that
regular security updates are necessary. The data from both primary and secondary resources
indicates that appropriate preventive measures are needed to be taken for managing the risks and
issues associated with an ecommerce transaction.
Page | 66
The data above indicates that most of the research respondents considers the use of
firewall as one major approach of risk mitigation related to security in ecommerce. The business
organizations therefore should consider the use of firewalls as a risk mitigation technique. As a
part of securing the systems of the organization, the respondents were asked to opine whether the
business organizations should consider regular security updates as a technique of ensuring secure
ecommerce transactions. The pie-chart below indicates the responses obtained.
25
7
6
5
7
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 21: Responses on importance of regular security updates
(Source: Data based)
30 respondents out of 50 has indicated that it is necessary to ensure regular security
updates in the systems that are used to make ecommerce transactions as a part of the risk
mitigation approach. The literature review section of the research report has indicated that
regular security updates are necessary. The data from both primary and secondary resources
indicates that appropriate preventive measures are needed to be taken for managing the risks and
issues associated with an ecommerce transaction.
Page | 66
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
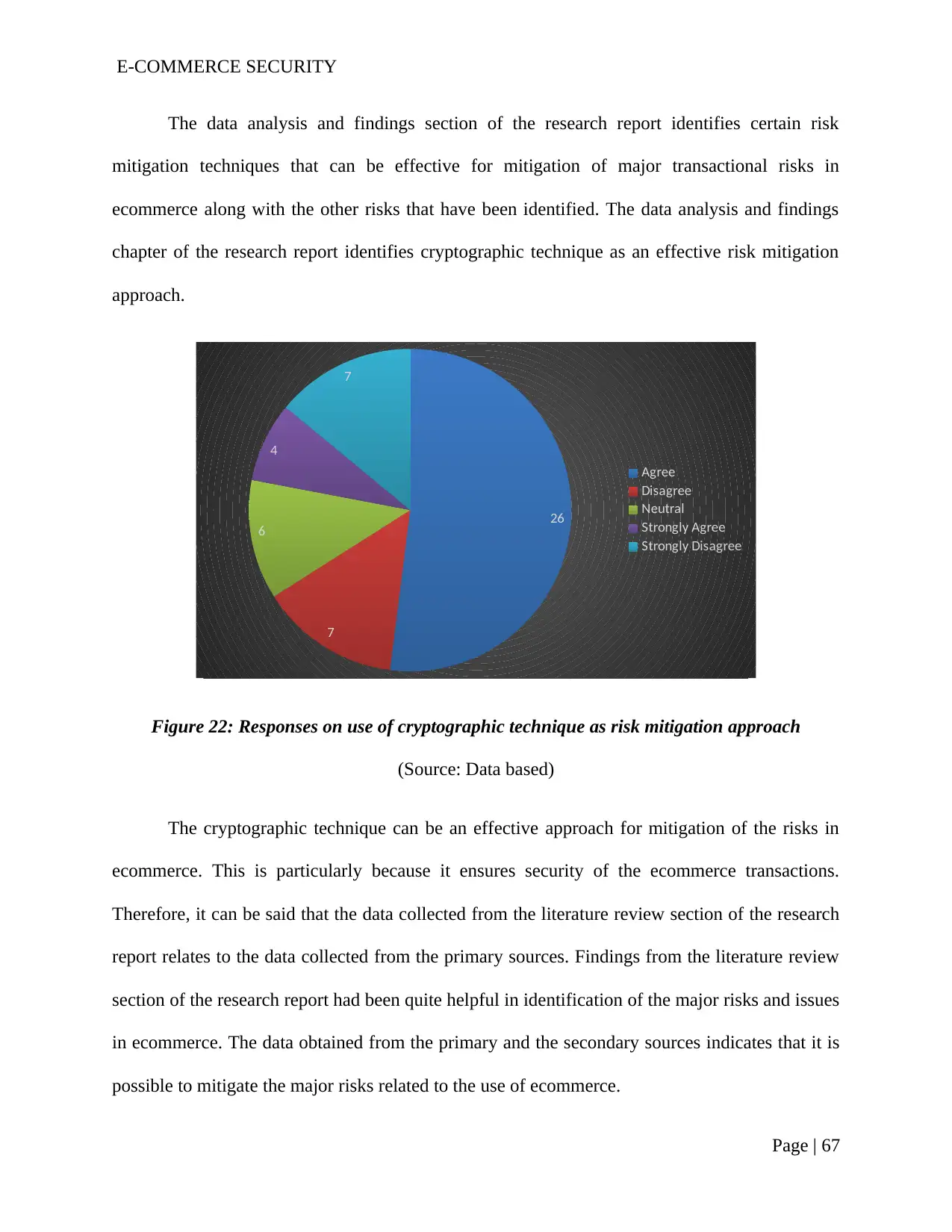
E-COMMERCE SECURITY
The data analysis and findings section of the research report identifies certain risk
mitigation techniques that can be effective for mitigation of major transactional risks in
ecommerce along with the other risks that have been identified. The data analysis and findings
chapter of the research report identifies cryptographic technique as an effective risk mitigation
approach.
26
7
6
4
7
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 22: Responses on use of cryptographic technique as risk mitigation approach
(Source: Data based)
The cryptographic technique can be an effective approach for mitigation of the risks in
ecommerce. This is particularly because it ensures security of the ecommerce transactions.
Therefore, it can be said that the data collected from the literature review section of the research
report relates to the data collected from the primary sources. Findings from the literature review
section of the research report had been quite helpful in identification of the major risks and issues
in ecommerce. The data obtained from the primary and the secondary sources indicates that it is
possible to mitigate the major risks related to the use of ecommerce.
Page | 67
The data analysis and findings section of the research report identifies certain risk
mitigation techniques that can be effective for mitigation of major transactional risks in
ecommerce along with the other risks that have been identified. The data analysis and findings
chapter of the research report identifies cryptographic technique as an effective risk mitigation
approach.
26
7
6
4
7
Agree
Disagree
Neutral
Strongly Agree
Strongly Disagree
Figure 22: Responses on use of cryptographic technique as risk mitigation approach
(Source: Data based)
The cryptographic technique can be an effective approach for mitigation of the risks in
ecommerce. This is particularly because it ensures security of the ecommerce transactions.
Therefore, it can be said that the data collected from the literature review section of the research
report relates to the data collected from the primary sources. Findings from the literature review
section of the research report had been quite helpful in identification of the major risks and issues
in ecommerce. The data obtained from the primary and the secondary sources indicates that it is
possible to mitigate the major risks related to the use of ecommerce.
Page | 67

E-COMMERCE SECURITY
Based on the data obtained from the primary sources and the data collected from the
literature review section of the research report, certain recommendations to ensure appropriate
mitigation of the risks and issues in ecommerce can be made. The following section of the
research report indicates the major recommendations related to ecommerce security and
transaction.
5.3. Recommendations
The recommendations are made on basis of the data obtained from the literature review
and the data analysis and findings chapter of this research report. The recommendations are as
follows.
Use of Secure Connection: One of the most significant risk management approach that
can help in prevention of the major risks associated with an ecommerce transaction is making
use of a secure connection. An unsecure connection often proves to be a major factor behind the
increasing risks and issues in ecommerce. Use of secure connection will ensue no information is
leaked during its transmission. Use of a secure connection can further help in elimination of the
risks associated to stealing of personal and sensitive information by the hackers, loss of personal
credentials such as credit cards numbers and other confidential information. Therefore, use of a
secure connection is recommended.
Training the Employees: In order to reduce the risk of data breach, it is quite essential
for a business organization to train its employees regarding the security aspects of an
organization. The employees are needed to be trained about the different security policies and the
process of ensuring appropriate security in a transaction. The employees should be aware of the
different risks related to the use of ecommerce in an organization and the security needs. The
Page | 68
Based on the data obtained from the primary sources and the data collected from the
literature review section of the research report, certain recommendations to ensure appropriate
mitigation of the risks and issues in ecommerce can be made. The following section of the
research report indicates the major recommendations related to ecommerce security and
transaction.
5.3. Recommendations
The recommendations are made on basis of the data obtained from the literature review
and the data analysis and findings chapter of this research report. The recommendations are as
follows.
Use of Secure Connection: One of the most significant risk management approach that
can help in prevention of the major risks associated with an ecommerce transaction is making
use of a secure connection. An unsecure connection often proves to be a major factor behind the
increasing risks and issues in ecommerce. Use of secure connection will ensue no information is
leaked during its transmission. Use of a secure connection can further help in elimination of the
risks associated to stealing of personal and sensitive information by the hackers, loss of personal
credentials such as credit cards numbers and other confidential information. Therefore, use of a
secure connection is recommended.
Training the Employees: In order to reduce the risk of data breach, it is quite essential
for a business organization to train its employees regarding the security aspects of an
organization. The employees are needed to be trained about the different security policies and the
process of ensuring appropriate security in a transaction. The employees should be aware of the
different risks related to the use of ecommerce in an organization and the security needs. The
Page | 68

E-COMMERCE SECURITY
employees should be aware of the various security needs that should be incorporated in a system
in order to ensure that secure transaction is maintained. The employees should be trained about
the network level firewall and need of ensuring user authentication while engaging in any online
or ecommerce transaction.
Traffic Monitoring: From the review of the literature and the data analysis chapter of this
research paper, it has been identified that DDoS attack is one of the most critical attacks
associated with security in ecommerce. Therefore, appropriate traffic monitoring is
recommended that will help in identification of similar threats in the ecommerce security.
Regular Vulnerability Scan: It is recommended that a business organization should
perform regular vulnerability scan to identify the vulnerabilities associated with an ecommerce
transaction. Regular updates and vulnerability scan can further help in elimination of certain
major risks in the field of ecommerce.
The above discussed points indicates the major recommendations in the field of
ecommerce. The risks in ecommerce transactions can be mitigated by taking certain preventive
measures which are recommended.
5.4. Chapter Summary
The chapter discusses the major findings of the results and analysis of the data collected
for this particular research. The data obtained from the primary sources are analysed by
following a quantitative data analysis method. The findings from the primary data are related to
the data obtained from the review of the literature. After identifying the major risks associated
with the security of the ecommerce, the researcher has provided certain recommendations to
reduce the transactional issues associated with the use of ecommerce. The chapter provides an
Page | 69
employees should be aware of the various security needs that should be incorporated in a system
in order to ensure that secure transaction is maintained. The employees should be trained about
the network level firewall and need of ensuring user authentication while engaging in any online
or ecommerce transaction.
Traffic Monitoring: From the review of the literature and the data analysis chapter of this
research paper, it has been identified that DDoS attack is one of the most critical attacks
associated with security in ecommerce. Therefore, appropriate traffic monitoring is
recommended that will help in identification of similar threats in the ecommerce security.
Regular Vulnerability Scan: It is recommended that a business organization should
perform regular vulnerability scan to identify the vulnerabilities associated with an ecommerce
transaction. Regular updates and vulnerability scan can further help in elimination of certain
major risks in the field of ecommerce.
The above discussed points indicates the major recommendations in the field of
ecommerce. The risks in ecommerce transactions can be mitigated by taking certain preventive
measures which are recommended.
5.4. Chapter Summary
The chapter discusses the major findings of the results and analysis of the data collected
for this particular research. The data obtained from the primary sources are analysed by
following a quantitative data analysis method. The findings from the primary data are related to
the data obtained from the review of the literature. After identifying the major risks associated
with the security of the ecommerce, the researcher has provided certain recommendations to
reduce the transactional issues associated with the use of ecommerce. The chapter provides an
Page | 69
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

E-COMMERCE SECURITY
insight of the various risk mitigation approaches that are effective in management of the
identified ecommerce security risks. The following chapter will conclude the research work with
the key findings of this chapter and the possible future work in this field.
Page | 70
insight of the various risk mitigation approaches that are effective in management of the
identified ecommerce security risks. The following chapter will conclude the research work with
the key findings of this chapter and the possible future work in this field.
Page | 70

E-COMMERCE SECURITY
Chapter 6: Conclusion, Key Findings and Future Work
6.1. Conclusion
The last chapter of the research project concludes the findings of the researcher in the
field of security in ecommerce. A primary research has been conducted for collection of data,
analysis of which has led to the identification of major risks and issues in the field of
ecommerce. It is vital to identify the major risks in the field of ecommerce as ecommerce is
being increasingly adopted by a number of business organizations and individuals as well. The
researcher has chosen to make use of effective research tools and technologies in the research to
ensure that a research is being completed in a planned manner. The research has been conducted
by making use of positivism research philosophy and descriptive research approach. The choice
of these appropriate research techniques has helped the researcher to find answers to the
identified research questions and fulfil the research objectives. Since the research aimed in
findings the major issues related to the use of ecommerce, the researcher has evaluated the
findings of the previously published literature in the field of ecommerce. The literature review
section of the research report has identified the most significant issues persisting in the field of
ecommerce. Identification of the issues in ecommerce is one of the first stages of risk
management. The next step of risk management is a assessing the risks and identification of the
mitigation approaches of the identified risk. In literature review part of the research report, the
researcher identifies the major approaches of risk mitigation.
On basis of the data collected from the literature review section of the research report, the
researcher has conducted a survey with a pre-developed questionnaire in order to collect data
about the risks and issues in ecommerce. The data collected from the primary research indicates
Page | 71
Chapter 6: Conclusion, Key Findings and Future Work
6.1. Conclusion
The last chapter of the research project concludes the findings of the researcher in the
field of security in ecommerce. A primary research has been conducted for collection of data,
analysis of which has led to the identification of major risks and issues in the field of
ecommerce. It is vital to identify the major risks in the field of ecommerce as ecommerce is
being increasingly adopted by a number of business organizations and individuals as well. The
researcher has chosen to make use of effective research tools and technologies in the research to
ensure that a research is being completed in a planned manner. The research has been conducted
by making use of positivism research philosophy and descriptive research approach. The choice
of these appropriate research techniques has helped the researcher to find answers to the
identified research questions and fulfil the research objectives. Since the research aimed in
findings the major issues related to the use of ecommerce, the researcher has evaluated the
findings of the previously published literature in the field of ecommerce. The literature review
section of the research report has identified the most significant issues persisting in the field of
ecommerce. Identification of the issues in ecommerce is one of the first stages of risk
management. The next step of risk management is a assessing the risks and identification of the
mitigation approaches of the identified risk. In literature review part of the research report, the
researcher identifies the major approaches of risk mitigation.
On basis of the data collected from the literature review section of the research report, the
researcher has conducted a survey with a pre-developed questionnaire in order to collect data
about the risks and issues in ecommerce. The data collected from the primary research indicates
Page | 71

E-COMMERCE SECURITY
the risks in ecommerce that had been identified while reviewing the literature are, indeed some
major risks in the field of ecommerce. By making use of the data collected from the primary
sources, the researcher identified certain risk mitigation approaches that can enforce ecommerce
security. It is necessary for a business or an individual to ensure appropriate ecommerce security.
The risk mitigation approaches that has been identified is expected to provide a valid solution to
the persisting risks and issues related to ecommerce security and transactions.
The risk in ecommerce transactions mainly arises because the transactions are carried
over internet. Security of ecommerce is needed to be maintained mainly because it is associated
with the transfer of personal information. Any risk in ecommerce security can result in hacking
of the personal data of an individual or a business organization. Therefore, it is quite essential to
ensure appropriate mitigation of the risks in ecommerce. The risk mitigation process involves
finding the most appropriate risk mitigation approach that can help in eliminating the risks and
issues in ecommerce.
Ecommerce security is associated with a particular set of protocols that can help in safely
guiding a transaction in ecommerce. Appropriate security requirements are needed to be in place
to protect the companies from various threats that include credit card fraud and loss of personal
information. The researcher, with the help of various research tool has analysed the collected
data to identify the mitigation approaches of the ecommerce security risks. The researcher has
been able to fulfil the major research objectives. The link of the research with the objectives
identified for the research are discussed in the section below.
6.2. Linking with Objectives
Page | 72
the risks in ecommerce that had been identified while reviewing the literature are, indeed some
major risks in the field of ecommerce. By making use of the data collected from the primary
sources, the researcher identified certain risk mitigation approaches that can enforce ecommerce
security. It is necessary for a business or an individual to ensure appropriate ecommerce security.
The risk mitigation approaches that has been identified is expected to provide a valid solution to
the persisting risks and issues related to ecommerce security and transactions.
The risk in ecommerce transactions mainly arises because the transactions are carried
over internet. Security of ecommerce is needed to be maintained mainly because it is associated
with the transfer of personal information. Any risk in ecommerce security can result in hacking
of the personal data of an individual or a business organization. Therefore, it is quite essential to
ensure appropriate mitigation of the risks in ecommerce. The risk mitigation process involves
finding the most appropriate risk mitigation approach that can help in eliminating the risks and
issues in ecommerce.
Ecommerce security is associated with a particular set of protocols that can help in safely
guiding a transaction in ecommerce. Appropriate security requirements are needed to be in place
to protect the companies from various threats that include credit card fraud and loss of personal
information. The researcher, with the help of various research tool has analysed the collected
data to identify the mitigation approaches of the ecommerce security risks. The researcher has
been able to fulfil the major research objectives. The link of the research with the objectives
identified for the research are discussed in the section below.
6.2. Linking with Objectives
Page | 72
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-COMMERCE SECURITY
Objective 1: To identify the risks associated with the ecommerce transactions: The
first objective that was set for this research project was identification of major risks and issues in
ecommerce transaction. The researcher has been successful in fulfilling this objective of the
research by identifying the major ecommerce security risks in the literature review part of the
research report. In order to find the risks in ecommerce, a survey was planned to collect data
about the risks and issues in ecommerce. Therefore, it can be said that the researcher has been
able to identify the major risks and issues in ecommerce transaction. Therefore, the primary
objective of the research is fulfilled.
Objective 2: To understand the source of risk related to ecommerce: The second
research objective is to understand the source of risks in ecommerce. In order to fulfil this
research objective, the researcher has performed an extensive literature review to understand the
source of risk. The researcher has been able to collect data about the source of risk in
ecommerce. Thus, it can be said that the second major objective of the research has been fulfilled
as well.
Objective 3: To evaluate the risk mitigation options in E-commerce: The main aim of
this research is evaluating ecommerce security. The risk mitigation approach in ecommerce is
identified with the help of the data collected in the literature review part and from the data that
has been obtained from the primary sources. The research identifies a set of protocols associated
with the security of ecommerce. The data collected from the primary sources has helped the
researcher to gain an idea of the major risk mitigation approaches and has further helped in
recommending the same. Thus, it can be said that the third objective of the research has been
fulfilled as well.
Page | 73
Objective 1: To identify the risks associated with the ecommerce transactions: The
first objective that was set for this research project was identification of major risks and issues in
ecommerce transaction. The researcher has been successful in fulfilling this objective of the
research by identifying the major ecommerce security risks in the literature review part of the
research report. In order to find the risks in ecommerce, a survey was planned to collect data
about the risks and issues in ecommerce. Therefore, it can be said that the researcher has been
able to identify the major risks and issues in ecommerce transaction. Therefore, the primary
objective of the research is fulfilled.
Objective 2: To understand the source of risk related to ecommerce: The second
research objective is to understand the source of risks in ecommerce. In order to fulfil this
research objective, the researcher has performed an extensive literature review to understand the
source of risk. The researcher has been able to collect data about the source of risk in
ecommerce. Thus, it can be said that the second major objective of the research has been fulfilled
as well.
Objective 3: To evaluate the risk mitigation options in E-commerce: The main aim of
this research is evaluating ecommerce security. The risk mitigation approach in ecommerce is
identified with the help of the data collected in the literature review part and from the data that
has been obtained from the primary sources. The research identifies a set of protocols associated
with the security of ecommerce. The data collected from the primary sources has helped the
researcher to gain an idea of the major risk mitigation approaches and has further helped in
recommending the same. Thus, it can be said that the third objective of the research has been
fulfilled as well.
Page | 73

E-COMMERCE SECURITY
Objective 4: To recommend secure usage of E-commerce: The fourth and the last
objective that has been identified for this research project is recommendation of secure use of
ecommerce. The chapter five of this research report has provided recommendations based on the
findings and analysis of data. The recommendations that have been provided are based on
ensuring secure use of ecommerce and to ensure that the ecommerce security is incorporated in
an organization. Therefore, it is clear that the researcher has been successful in fulfilling the final
objective of the research as well.
All the identified research objectives were fulfilled in research project. The researcher
has been successful in finding answer to the identified questions of the research. The research
aim has been fulfilled as the mitigation approach of the identified ecommerce security risks and
issues are identified and recommended. With this, it can be concluded that the research has been
completed in a successful manner. The recommendations for this research study are indicated in
the section below.
6.3. Recommendations
The research that has been undertaken has been able to find answers to the risks and
issues associated with transactions in ecommerce. However, the research could have been
improved in a number of ways. The recommendations associated with this research study are as
follows-
Planned Approach: The research followed a planned approach. However, this particular
research mainly focused on certain limited aspect of ecommerce security. For future work in this
topic, a similar planned approach is recommended.
Page | 74
Objective 4: To recommend secure usage of E-commerce: The fourth and the last
objective that has been identified for this research project is recommendation of secure use of
ecommerce. The chapter five of this research report has provided recommendations based on the
findings and analysis of data. The recommendations that have been provided are based on
ensuring secure use of ecommerce and to ensure that the ecommerce security is incorporated in
an organization. Therefore, it is clear that the researcher has been successful in fulfilling the final
objective of the research as well.
All the identified research objectives were fulfilled in research project. The researcher
has been successful in finding answer to the identified questions of the research. The research
aim has been fulfilled as the mitigation approach of the identified ecommerce security risks and
issues are identified and recommended. With this, it can be concluded that the research has been
completed in a successful manner. The recommendations for this research study are indicated in
the section below.
6.3. Recommendations
The research that has been undertaken has been able to find answers to the risks and
issues associated with transactions in ecommerce. However, the research could have been
improved in a number of ways. The recommendations associated with this research study are as
follows-
Planned Approach: The research followed a planned approach. However, this particular
research mainly focused on certain limited aspect of ecommerce security. For future work in this
topic, a similar planned approach is recommended.
Page | 74

E-COMMERCE SECURITY
Data Collection: The sample size chosen for the research was quite constricted. It is
recommended that future works in this research should consider the use of a large sample, which
will ensure analysis of the data in an effective manner.
These two are major recommendations in the field of ecommerce security. There is a
future scope for this research and the recommendations provided will contribute to the further
research in this filed.
6.4. Limitations of research
The research although is conducted in a successful manner, the research involves certain
limitations. The limitations in this field of research are as follows-
The time constraint is a major limitation associated with this research. This
research study has been conducted in an extremely less time, which is one of the
major limitations in this field.
The sample size chosen for the research is quite low, which is another major
limitation in this field of research.
Another major limitations associated with this research is that the research has
considered only the common security risks and issues in the field of ecommerce.
However, there can be other risks in the field of ecommerce as well, which should
be identified.
6.5 Future scope of the study
The research that has been conducted can be further modified by implementing the same
on a larger scale. There is a scope of detailing the research findings. The current research in the
Page | 75
Data Collection: The sample size chosen for the research was quite constricted. It is
recommended that future works in this research should consider the use of a large sample, which
will ensure analysis of the data in an effective manner.
These two are major recommendations in the field of ecommerce security. There is a
future scope for this research and the recommendations provided will contribute to the further
research in this filed.
6.4. Limitations of research
The research although is conducted in a successful manner, the research involves certain
limitations. The limitations in this field of research are as follows-
The time constraint is a major limitation associated with this research. This
research study has been conducted in an extremely less time, which is one of the
major limitations in this field.
The sample size chosen for the research is quite low, which is another major
limitation in this field of research.
Another major limitations associated with this research is that the research has
considered only the common security risks and issues in the field of ecommerce.
However, there can be other risks in the field of ecommerce as well, which should
be identified.
6.5 Future scope of the study
The research that has been conducted can be further modified by implementing the same
on a larger scale. There is a scope of detailing the research findings. The current research in the
Page | 75
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

E-COMMERCE SECURITY
field of ecommerce security can be considered as a small scale research and therefore, this
particular research has scope of improvement. A large scale research can be performed on
ecommerce security and this research study can act as a base for further research in this field.
Page | 76
field of ecommerce security can be considered as a small scale research and therefore, this
particular research has scope of improvement. A large scale research can be performed on
ecommerce security and this research study can act as a base for further research in this field.
Page | 76

E-COMMERCE SECURITY
References
[1]. Y. Fang, Q. Israr, S. Heshan, M. Patrick, R. Elaine, and L. Kai H.. "Trust, satisfaction, and
online repurchase intention: The moderating role of perceived effectiveness of e-commerce
institutional mechanisms." Mis Quarterly 38, no. 2 (2014).
[2]. M. Hossain, F. Maziar, and H. Ragib. "Towards an analysis of security issues, challenges,
and open problems in the internet of things." In Services (SERVICES), 2015 IEEE World
Congress on, pp. 21-28. IEEE, 2015.
[3]. M. Savrul, I. Ahmet, and S. Sefer. "The potential of e-commerce for SMEs in a globalizing
business environment." Procedia-Social and Behavioral Sciences 150 (2014): 35-45.
[4]. E. Turban, K. David, L. Jae Kyu, TP. Liang, and C. Deborrah. Turban. "E-Commerce
Security and Fraud Issues and Protections." In Electronic Commerce, pp. 457-518. Springer,
Cham, 2015.
[5]. D. Chaffey. Digital business and e-commerce management. Pearson Education Limited,
2015.
[6]. J. Choi, and DL. Nazareth. "Repairing trust in an e-commerce and security context: an agent-
based modeling approach." Information Management & Computer Security 22, no. 5 (2014):
490-512.
[7]. T. Mayayise, and I. Olusegun Osunmakinde. "E-commerce assurance models and
trustworthiness issues: an empirical study." Information Management & Computer Security 22,
no. 1 (2014): 76-96.
Page | 77
References
[1]. Y. Fang, Q. Israr, S. Heshan, M. Patrick, R. Elaine, and L. Kai H.. "Trust, satisfaction, and
online repurchase intention: The moderating role of perceived effectiveness of e-commerce
institutional mechanisms." Mis Quarterly 38, no. 2 (2014).
[2]. M. Hossain, F. Maziar, and H. Ragib. "Towards an analysis of security issues, challenges,
and open problems in the internet of things." In Services (SERVICES), 2015 IEEE World
Congress on, pp. 21-28. IEEE, 2015.
[3]. M. Savrul, I. Ahmet, and S. Sefer. "The potential of e-commerce for SMEs in a globalizing
business environment." Procedia-Social and Behavioral Sciences 150 (2014): 35-45.
[4]. E. Turban, K. David, L. Jae Kyu, TP. Liang, and C. Deborrah. Turban. "E-Commerce
Security and Fraud Issues and Protections." In Electronic Commerce, pp. 457-518. Springer,
Cham, 2015.
[5]. D. Chaffey. Digital business and e-commerce management. Pearson Education Limited,
2015.
[6]. J. Choi, and DL. Nazareth. "Repairing trust in an e-commerce and security context: an agent-
based modeling approach." Information Management & Computer Security 22, no. 5 (2014):
490-512.
[7]. T. Mayayise, and I. Olusegun Osunmakinde. "E-commerce assurance models and
trustworthiness issues: an empirical study." Information Management & Computer Security 22,
no. 1 (2014): 76-96.
Page | 77

E-COMMERCE SECURITY
[8]. A. Chaudhary, A. Khaleel, and M. A. Rizvi. "E-commerce security through asymmetric key
algorithm." In Communication Systems and Network Technologies (CSNT), 2014 Fourth
International Conference on, pp. 776-781. IEEE, 2014.
[9]. I. Arpaci, K. Kerem, and Salih Bardakci. "Effects of security and privacy concerns on
educational use of cloud services." Computers in Human Behavior 45 (2015): 93-98.
[10]. G. Sharma, and L. Wang. "Ethical perspectives on e-commerce: an empirical
investigation." Internet Research24, no. 4 (2014): 414-435.
[11]. AJ. Flanagin, MJ. Metzger, P. Rebekah, M. Alex, and H. Ethan. "Mitigating risk in
ecommerce transactions: perceptions of information credibility and the role of user-generated
ratings in product quality and purchase intention." Electronic Commerce Research 14, no. 1
(2014): 1-23.
[12]. E. Turban, K. David, L. Jae Kyu, L. Ting-Peng, and C. Deborrah. Turban. Electronic
commerce: A managerial and social networks perspective. Springer, 2015.
[13]. J. Fernie, and S. Leigh. Logistics and retail management: emerging issues and new
challenges in the retail supply chain. Kogan page publishers, 2014.
[14]. G. Sharma, and L. Wang. "Ethical perspectives on e-commerce: an empirical
investigation." Internet Research24, no. 4 (2014): 414-435.
[15]. CM. Chiu, W. Eric TG, F. Yu‐Hui, and H. Hsin‐Yi. "Understanding customers' repeat
purchase intentions in B2C e‐commerce: the roles of utilitarian value, hedonic value and
perceived risk." Information Systems Journal 24, no. 1 (2014): 85-114.
Page | 78
[8]. A. Chaudhary, A. Khaleel, and M. A. Rizvi. "E-commerce security through asymmetric key
algorithm." In Communication Systems and Network Technologies (CSNT), 2014 Fourth
International Conference on, pp. 776-781. IEEE, 2014.
[9]. I. Arpaci, K. Kerem, and Salih Bardakci. "Effects of security and privacy concerns on
educational use of cloud services." Computers in Human Behavior 45 (2015): 93-98.
[10]. G. Sharma, and L. Wang. "Ethical perspectives on e-commerce: an empirical
investigation." Internet Research24, no. 4 (2014): 414-435.
[11]. AJ. Flanagin, MJ. Metzger, P. Rebekah, M. Alex, and H. Ethan. "Mitigating risk in
ecommerce transactions: perceptions of information credibility and the role of user-generated
ratings in product quality and purchase intention." Electronic Commerce Research 14, no. 1
(2014): 1-23.
[12]. E. Turban, K. David, L. Jae Kyu, L. Ting-Peng, and C. Deborrah. Turban. Electronic
commerce: A managerial and social networks perspective. Springer, 2015.
[13]. J. Fernie, and S. Leigh. Logistics and retail management: emerging issues and new
challenges in the retail supply chain. Kogan page publishers, 2014.
[14]. G. Sharma, and L. Wang. "Ethical perspectives on e-commerce: an empirical
investigation." Internet Research24, no. 4 (2014): 414-435.
[15]. CM. Chiu, W. Eric TG, F. Yu‐Hui, and H. Hsin‐Yi. "Understanding customers' repeat
purchase intentions in B2C e‐commerce: the roles of utilitarian value, hedonic value and
perceived risk." Information Systems Journal 24, no. 1 (2014): 85-114.
Page | 78
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-COMMERCE SECURITY
[16]. LJ. Trautman, "E-Commerce, cyber, and electronic payment system risks: lessons from
PayPal." UC Davis Bus. LJ 16 (2015): 261.
[17]. J. Choi, and D L. Nazareth. "Repairing trust in an e-commerce and security context: an
agent-based modeling approach." Information Management & Computer Security 22, no. 5
(2014): 490-512.
[18]. SJ. Taylor, B. Robert, and D. Marjorie. Introduction to qualitative research methods: A
guidebook and resource. John Wiley & Sons, 2015.
[19]. D. Silverman, ed. Qualitative research. Sage, 2016.
[20]. N. Walliman, Research methods: The basics. Routledge, 2017.
[21]. R. Panneerselvam, Research methodology. PHI Learning Pvt. Ltd., 2014.
[22]. A. Wiek, and LJ. Daniel "Transformational sustainability research methodology."
In Sustainability Science, pp. 31-41. Springer, Dordrecht, 2016.
[23]. D. Crowther, and G. Lancaster. Research methods. Routledge, 2012.
[24]. MB. Davies, and H. Nathan Doing a successful research project: Using qualitative or
quantitative methods. Macmillan International Higher Education, 2014.
[25]. J. Brannen, "Combining qualitative and quantitative approaches: an overview." In Mixing
methods: Qualitative and quantitative research, pp. 3-37. Routledge, 2017.
[26]. S. Lewis, "Qualitative inquiry and research design: Choosing among five
approaches." Health promotion practice16, no. 4 (2015): 473-475.
Page | 79
[16]. LJ. Trautman, "E-Commerce, cyber, and electronic payment system risks: lessons from
PayPal." UC Davis Bus. LJ 16 (2015): 261.
[17]. J. Choi, and D L. Nazareth. "Repairing trust in an e-commerce and security context: an
agent-based modeling approach." Information Management & Computer Security 22, no. 5
(2014): 490-512.
[18]. SJ. Taylor, B. Robert, and D. Marjorie. Introduction to qualitative research methods: A
guidebook and resource. John Wiley & Sons, 2015.
[19]. D. Silverman, ed. Qualitative research. Sage, 2016.
[20]. N. Walliman, Research methods: The basics. Routledge, 2017.
[21]. R. Panneerselvam, Research methodology. PHI Learning Pvt. Ltd., 2014.
[22]. A. Wiek, and LJ. Daniel "Transformational sustainability research methodology."
In Sustainability Science, pp. 31-41. Springer, Dordrecht, 2016.
[23]. D. Crowther, and G. Lancaster. Research methods. Routledge, 2012.
[24]. MB. Davies, and H. Nathan Doing a successful research project: Using qualitative or
quantitative methods. Macmillan International Higher Education, 2014.
[25]. J. Brannen, "Combining qualitative and quantitative approaches: an overview." In Mixing
methods: Qualitative and quantitative research, pp. 3-37. Routledge, 2017.
[26]. S. Lewis, "Qualitative inquiry and research design: Choosing among five
approaches." Health promotion practice16, no. 4 (2015): 473-475.
Page | 79

E-COMMERCE SECURITY
[27]. U. Flick, An introduction to qualitative research. Sage Publications Limited, 2018.
[28]. E. Bell, B. Alan, and H. Bill. Business research methods. Oxford university press, 2018.
[29]. S. Ketefian, "Ethical considerations in research. Focus on vulnerable groups." Investigación
y Educación en Enfermería33, no. 1 (2015): 164-172.
[30]. MN. Saunders, L. Philip, T. Adrian, and B. Alexandra. "Understanding research philosophy
and approaches to theory development." (2015): 122-161.
[31]. G. Marczyk, D. David, and F. David. Essentials of research design and methodology. John
Wiley, 2017.
[32]. JM. Morse. Mixed method design: Principles and procedures. Routledge, 2016.
[33]. U. Sekaran, and B. Roger. Research methods for business: A skill building approach. John
Wiley & Sons, 2016.
Page | 80
[27]. U. Flick, An introduction to qualitative research. Sage Publications Limited, 2018.
[28]. E. Bell, B. Alan, and H. Bill. Business research methods. Oxford university press, 2018.
[29]. S. Ketefian, "Ethical considerations in research. Focus on vulnerable groups." Investigación
y Educación en Enfermería33, no. 1 (2015): 164-172.
[30]. MN. Saunders, L. Philip, T. Adrian, and B. Alexandra. "Understanding research philosophy
and approaches to theory development." (2015): 122-161.
[31]. G. Marczyk, D. David, and F. David. Essentials of research design and methodology. John
Wiley, 2017.
[32]. JM. Morse. Mixed method design: Principles and procedures. Routledge, 2016.
[33]. U. Sekaran, and B. Roger. Research methods for business: A skill building approach. John
Wiley & Sons, 2016.
Page | 80
1 out of 81
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





