Electronic Security: Guidelines for Secure Data in Transit Report
VerifiedAdded on 2022/12/15
|2
|1473
|73
Report
AI Summary
This report delves into the critical domain of electronic security, with a specific emphasis on the secure transit of data. It begins by defining electronic security as the protection of data and information from cyber threats, and it explores various guidelines and techniques for achieving this. The report covers key areas such as securing wireless local area networks (WLANs) with strong encryption, implementing national policies for securing voice communication, utilizing protected distribution systems, and ensuring the safety of cryptographic modules. It also examines data access management, including identity authentication for information systems and general access control guidelines for cloud systems. Furthermore, the report addresses securing web transactions and server certificate management, alongside personal identity verification methods. The conclusion underscores the importance of electronic security for organizational functionality and highlights the significance of managing access to ensure data integrity. The report provides a comprehensive overview of electronic security, offering practical insights and recommendations for safeguarding data in transit.
\
Electronic security can be defined as the security of data, information and any
other thing which is stored and captured by the internet from ant cybercrimes
or unusual attacks (Rappert, 2019). There are many threats which are
associated with the internet security and solutions are also introduced for the
same. This requires technology which is based on the cyber security and its
guidelines to be achieved in a legal manner in order to safeguard the data.
The following discussion is made on the secure data in transit which includes
the guidelines for securing wireless local area networks, national policy on
securing voice communication, protected distribution systems and safety
requirements for cryptographic modules and manage access which includes
persona; identity verification, general access control guidelines for cloud
systems, securing web transactions and server certificate management and
identity authentication for information systems with proper findings and
conclusion.
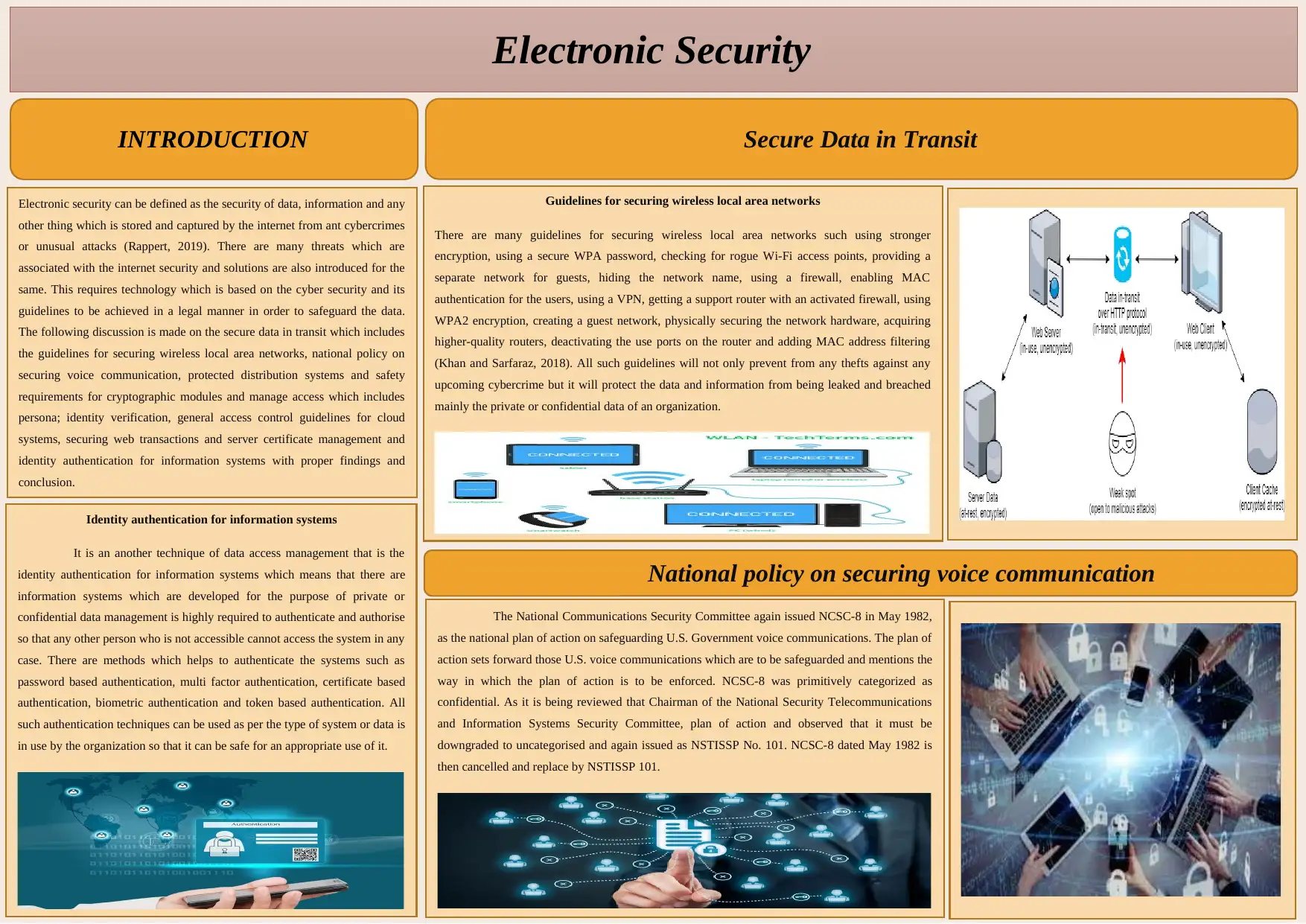
Guidelines for securing wireless local area networks
There are many guidelines for securing wireless local area networks such using stronger
encryption, using a secure WPA password, checking for rogue Wi-Fi access points, providing a
separate network for guests, hiding the network name, using a firewall, enabling MAC
authentication for the users, using a VPN, getting a support router with an activated firewall, using
WPA2 encryption, creating a guest network, physically securing the network hardware, acquiring
higher-quality routers, deactivating the use ports on the router and adding MAC address filtering
(Khan and Sarfaraz, 2018). All such guidelines will not only prevent from any thefts against any
upcoming cybercrime but it will protect the data and information from being leaked and breached
mainly the private or confidential data of an organization.
Electronic Security
INTRODUCTION Secure Data in Transit
National policy on securing voice communication
The National Communications Security Committee again issued NCSC-8 in May 1982,
as the national plan of action on safeguarding U.S. Government voice communications. The plan of
action sets forward those U.S. voice communications which are to be safeguarded and mentions the
way in which the plan of action is to be enforced. NCSC-8 was primitively categorized as
confidential. As it is being reviewed that Chairman of the National Security Telecommunications
and Information Systems Security Committee, plan of action and observed that it must be
downgraded to uncategorised and again issued as NSTISSP No. 101. NCSC-8 dated May 1982 is
then cancelled and replace by NSTISSP 101.
Identity authentication for information systems
It is an another technique of data access management that is the
identity authentication for information systems which means that there are
information systems which are developed for the purpose of private or
confidential data management is highly required to authenticate and authorise
so that any other person who is not accessible cannot access the system in any
case. There are methods which helps to authenticate the systems such as
password based authentication, multi factor authentication, certificate based
authentication, biometric authentication and token based authentication. All
such authentication techniques can be used as per the type of system or data is
in use by the organization so that it can be safe for an appropriate use of it.
Electronic security can be defined as the security of data, information and any
other thing which is stored and captured by the internet from ant cybercrimes
or unusual attacks (Rappert, 2019). There are many threats which are
associated with the internet security and solutions are also introduced for the
same. This requires technology which is based on the cyber security and its
guidelines to be achieved in a legal manner in order to safeguard the data.
The following discussion is made on the secure data in transit which includes
the guidelines for securing wireless local area networks, national policy on
securing voice communication, protected distribution systems and safety
requirements for cryptographic modules and manage access which includes
persona; identity verification, general access control guidelines for cloud
systems, securing web transactions and server certificate management and
identity authentication for information systems with proper findings and
conclusion.
Guidelines for securing wireless local area networks
There are many guidelines for securing wireless local area networks such using stronger
encryption, using a secure WPA password, checking for rogue Wi-Fi access points, providing a
separate network for guests, hiding the network name, using a firewall, enabling MAC
authentication for the users, using a VPN, getting a support router with an activated firewall, using
WPA2 encryption, creating a guest network, physically securing the network hardware, acquiring
higher-quality routers, deactivating the use ports on the router and adding MAC address filtering
(Khan and Sarfaraz, 2018). All such guidelines will not only prevent from any thefts against any
upcoming cybercrime but it will protect the data and information from being leaked and breached
mainly the private or confidential data of an organization.
Electronic Security
INTRODUCTION Secure Data in Transit
National policy on securing voice communication
The National Communications Security Committee again issued NCSC-8 in May 1982,
as the national plan of action on safeguarding U.S. Government voice communications. The plan of
action sets forward those U.S. voice communications which are to be safeguarded and mentions the
way in which the plan of action is to be enforced. NCSC-8 was primitively categorized as
confidential. As it is being reviewed that Chairman of the National Security Telecommunications
and Information Systems Security Committee, plan of action and observed that it must be
downgraded to uncategorised and again issued as NSTISSP No. 101. NCSC-8 dated May 1982 is
then cancelled and replace by NSTISSP 101.
Identity authentication for information systems
It is an another technique of data access management that is the
identity authentication for information systems which means that there are
information systems which are developed for the purpose of private or
confidential data management is highly required to authenticate and authorise
so that any other person who is not accessible cannot access the system in any
case. There are methods which helps to authenticate the systems such as
password based authentication, multi factor authentication, certificate based
authentication, biometric authentication and token based authentication. All
such authentication techniques can be used as per the type of system or data is
in use by the organization so that it can be safe for an appropriate use of it.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Electronic Security
Protected distribution systems
A Protected distribution system is used to defend unencrypted national security information (NSI) that is transmissible on optical
fibre or wire line, this is because the NSI is not protected, the Protected distribution systems must render protection to deter utilisation. The
importance is on invasion sensing instead of prevention of attack (Sallam and Malik, 2018). It helps in data from not breaching from the
systems so that organization can work in an appropriate manner by maintaining safety and security to the work which is private and
confidential. Such systems are required to install which needs initial and maintaining cost more than the operating cost, that is why it is not no
expensive and not too cheap, thereby easy to afford and use in order to safeguard the organizational systems.
Securing web transactions and server certificate management
Transport Layer Security (TLS) server certificates are captious to the safety of both private web services and internet facing. Con-
tempting the captious value of these certificates, numerous firms is deficient in a formal TLS certificate administration system and do not have
the power to peripherally supervise and carry off their certificates. The NIST Cybersecurity Guide displays big and average firms that how to
utilize a formal TLS certificate administration system to address certificate dependent hazards and situations. It defines the TLS certificate
administration situation faced by firms which renders suggestions of best practices for big scale TLS server certificate administration which
defines an automatic proof of concept execution that shows how to forbid, discover and retrieve from certificate related incidents and gives a
procedure of the demonstrated culpableness to the suggested best practices and to NIST safety guidance and structure (Souppaya, Haag,
Turner and Barker, 2018).
Conclusion
It is concluded that electronic security is an important concept to learn in order to apply technology in
real time organizations because without the security of data and systems, it can be difficult for the
system to work on a proper way and it cannot be able to give smooth functioning to the company.
Therefore, it is important to analyse the security of data in transit and it is essential to examine the
management of access. Hence, this poster covers all such areas in order to better understand the concept
of electronic security.
Safety requirements for cryptographic modules
A cryptographic needed to either consider particular security characteristics planned to
discover displacements and cancel CSPs or to experience strict situational non achievement
experimentation to render a sensible certainty that the module will not be affected by displacements outs
of the natural function. Safety requirements can be that it should be encrypted with a code or
programming in order to safeguard the data or information consisting high security issues that is needed
to be resolved in any way and therefore, cryptography is mandatory to use so that people with wrong
intentions or even the systems could not damage the data if it is protected with the cryptography method
which highly includes encoding and decoding technique to protect the system's information while
transmitting over the network.
General access control guidelines for cloud systems
It is defined as the first measure toward knowing the safety situation in cloud systems by
examining the access control (AC) thought process in all the three cloud service conveyance models
such as Infrastructure as a Service that is IaaS, Platform as a Service that is PaaS and Software as a
Service that is SaaS. Necessary features that can impact the Cloud's AC designing are also sum-up such
as broad network access, rapid elasticity, resource pooling, data sharing and measured service. Different
counselling for AC designing of IaaS, PaaS and SaaS are planned as per their various features.
Recommendations for AC designing in various cloud systems are also enclosed to ease forthcoming
execution. In addition, possible plan of action regulation is sum-up for all cloud system.
Personal identity verification
It is one of the technique to safeguard the information that is the personal identity verification which means that in an organization, to access
the private data of the company, it is important to get access because usually the private information is encrypted to over protected from an
unnecessary access to it. Therefore, such data are protected with the help of the personal identity verification which states that each and every
person who is authorised and authenticated to access the organization's data is only allowed to access and they can only crack its passwords or
by biometric systems and no one else can destroy the passwords (Inoue, Suzuki, Kurita and Imai, 2020).
Manage Access
References
Inoue, K., Suzuki, D., Kurita, T. and Imai, S., 2020, September. Cooperative Task Scheduling for Personal Identity Verification in Networked Systems. In 2020 32nd International
Teletraffic Congress (ITC 32) (pp. 97-105). IEEE.
Khan, A. and Sarfaraz, A., 2018. Practical guidelines for securing wireless local area networks (WLANs). International Journal of Security and Its Applications. 12(3). pp.19-28.
Protected distribution systems
A Protected distribution system is used to defend unencrypted national security information (NSI) that is transmissible on optical
fibre or wire line, this is because the NSI is not protected, the Protected distribution systems must render protection to deter utilisation. The
importance is on invasion sensing instead of prevention of attack (Sallam and Malik, 2018). It helps in data from not breaching from the
systems so that organization can work in an appropriate manner by maintaining safety and security to the work which is private and
confidential. Such systems are required to install which needs initial and maintaining cost more than the operating cost, that is why it is not no
expensive and not too cheap, thereby easy to afford and use in order to safeguard the organizational systems.
Securing web transactions and server certificate management
Transport Layer Security (TLS) server certificates are captious to the safety of both private web services and internet facing. Con-
tempting the captious value of these certificates, numerous firms is deficient in a formal TLS certificate administration system and do not have
the power to peripherally supervise and carry off their certificates. The NIST Cybersecurity Guide displays big and average firms that how to
utilize a formal TLS certificate administration system to address certificate dependent hazards and situations. It defines the TLS certificate
administration situation faced by firms which renders suggestions of best practices for big scale TLS server certificate administration which
defines an automatic proof of concept execution that shows how to forbid, discover and retrieve from certificate related incidents and gives a
procedure of the demonstrated culpableness to the suggested best practices and to NIST safety guidance and structure (Souppaya, Haag,
Turner and Barker, 2018).
Conclusion
It is concluded that electronic security is an important concept to learn in order to apply technology in
real time organizations because without the security of data and systems, it can be difficult for the
system to work on a proper way and it cannot be able to give smooth functioning to the company.
Therefore, it is important to analyse the security of data in transit and it is essential to examine the
management of access. Hence, this poster covers all such areas in order to better understand the concept
of electronic security.
Safety requirements for cryptographic modules
A cryptographic needed to either consider particular security characteristics planned to
discover displacements and cancel CSPs or to experience strict situational non achievement
experimentation to render a sensible certainty that the module will not be affected by displacements outs
of the natural function. Safety requirements can be that it should be encrypted with a code or
programming in order to safeguard the data or information consisting high security issues that is needed
to be resolved in any way and therefore, cryptography is mandatory to use so that people with wrong
intentions or even the systems could not damage the data if it is protected with the cryptography method
which highly includes encoding and decoding technique to protect the system's information while
transmitting over the network.
General access control guidelines for cloud systems
It is defined as the first measure toward knowing the safety situation in cloud systems by
examining the access control (AC) thought process in all the three cloud service conveyance models
such as Infrastructure as a Service that is IaaS, Platform as a Service that is PaaS and Software as a
Service that is SaaS. Necessary features that can impact the Cloud's AC designing are also sum-up such
as broad network access, rapid elasticity, resource pooling, data sharing and measured service. Different
counselling for AC designing of IaaS, PaaS and SaaS are planned as per their various features.
Recommendations for AC designing in various cloud systems are also enclosed to ease forthcoming
execution. In addition, possible plan of action regulation is sum-up for all cloud system.
Personal identity verification
It is one of the technique to safeguard the information that is the personal identity verification which means that in an organization, to access
the private data of the company, it is important to get access because usually the private information is encrypted to over protected from an
unnecessary access to it. Therefore, such data are protected with the help of the personal identity verification which states that each and every
person who is authorised and authenticated to access the organization's data is only allowed to access and they can only crack its passwords or
by biometric systems and no one else can destroy the passwords (Inoue, Suzuki, Kurita and Imai, 2020).
Manage Access
References
Inoue, K., Suzuki, D., Kurita, T. and Imai, S., 2020, September. Cooperative Task Scheduling for Personal Identity Verification in Networked Systems. In 2020 32nd International
Teletraffic Congress (ITC 32) (pp. 97-105). IEEE.
Khan, A. and Sarfaraz, A., 2018. Practical guidelines for securing wireless local area networks (WLANs). International Journal of Security and Its Applications. 12(3). pp.19-28.
1 out of 2
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





