Computer Networks Assignment: Weeks 1-7 - Summaries of Key Topics
VerifiedAdded on 2020/03/23
|8
|3858
|29
Homework Assignment
AI Summary
This assignment comprises summaries of seven weeks of computer network topics. Week 1 discusses modern computing architecture and highlights the contributions of David Patterson, focusing on his work on RAID and RISC. Week 2 explores operating systems, with a summary of Bill Gates' role in the development of Windows OS. Week 3 examines the evolution of the Internet, focusing on ARPANET. Week 4 delves into L2 protocols, specifically ARP. Week 5 discusses a famous hacker, Kevin Mitnick. Week 6 explores future networking technologies, with a focus on wireless data links for drones. Finally, Week 7 summarizes the history of Facebook. Each summary includes a title, reference, and concise overview of the resource.

Week 1
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title and Reference:
Contribution sand Work done by David Patterson
Computerhistory (2017). David Patterson | Computer History Museum. [online]
Computerhistory.org. Available at:
http://www.computerhistory.org/fellowawards/hall/david-patterson/ [Accessed 22
Sep. 2017].
Summary:
The resource that is selected is an online article that lists out the contributions,
qualifications, skills and achievements of a computer architect named David
Patterson. Many of the concepts that are used and applied in the modern computing
architecture were provided by David that makes him an extremely significant entity in
the same field. He completed his graduation from UCLA in the year 1976 and is
currently working as a Professor in the California University in the department of
Computer Science and Technology. David carried out a lot many research and
development processes and came up with two extremely important discoveries with
the concepts of Redundant Array of Inexpensive Disks which is normally abbreviated
as RAID and Reduced Instruction Set Computers which is commonly known as
RISC. RISC and RAID are used in the modern computing architecture which
describes the use of instruction sets and the application of the virtualization
technology. These concepts have made it possible to easily arrange the data sets in
the present day architecture and have also strengthened the integration and flow of
information and instructions. David has been rewarded with 35 awards and
recognition for all the work that he has done in the fields of research and teaching.
He has also been a part of around 7 books in which he has co-authored and
provided his ideas. His research works have provided the other researches with a
viewpoint and clarity on the concepts of modern architecture and the article
beautifully captures his contribution in a brief manner.
Week 2
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONE such individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title and Reference:
Contribution sand Work done by Bill Gates
Economictimes (2008). The long and successful journey of Bill Gates. [online] The
Economic Times. Available at: http://economictimes.indiatimes.com/microsoft-says-
yahoo/the-long-and-successful-journey-of-bill-gates/articleshow/3170834.cms
[Accessed 22 Sep. 2017].
Summary:
Operating systems are the software packages that act as an interface between the
users and the computer hardware. Many of the desktop and mobile operating
systems have been created for this purpose. One such widely used and one of the
most popular one in this list is Windows Operating System (OS). It was in the year
1985 that a software company called Microsoft released the initial version of
Windows OS. It was a disruptive innovation and the face behind the release of this
1
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title and Reference:
Contribution sand Work done by David Patterson
Computerhistory (2017). David Patterson | Computer History Museum. [online]
Computerhistory.org. Available at:
http://www.computerhistory.org/fellowawards/hall/david-patterson/ [Accessed 22
Sep. 2017].
Summary:
The resource that is selected is an online article that lists out the contributions,
qualifications, skills and achievements of a computer architect named David
Patterson. Many of the concepts that are used and applied in the modern computing
architecture were provided by David that makes him an extremely significant entity in
the same field. He completed his graduation from UCLA in the year 1976 and is
currently working as a Professor in the California University in the department of
Computer Science and Technology. David carried out a lot many research and
development processes and came up with two extremely important discoveries with
the concepts of Redundant Array of Inexpensive Disks which is normally abbreviated
as RAID and Reduced Instruction Set Computers which is commonly known as
RISC. RISC and RAID are used in the modern computing architecture which
describes the use of instruction sets and the application of the virtualization
technology. These concepts have made it possible to easily arrange the data sets in
the present day architecture and have also strengthened the integration and flow of
information and instructions. David has been rewarded with 35 awards and
recognition for all the work that he has done in the fields of research and teaching.
He has also been a part of around 7 books in which he has co-authored and
provided his ideas. His research works have provided the other researches with a
viewpoint and clarity on the concepts of modern architecture and the article
beautifully captures his contribution in a brief manner.
Week 2
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONE such individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title and Reference:
Contribution sand Work done by Bill Gates
Economictimes (2008). The long and successful journey of Bill Gates. [online] The
Economic Times. Available at: http://economictimes.indiatimes.com/microsoft-says-
yahoo/the-long-and-successful-journey-of-bill-gates/articleshow/3170834.cms
[Accessed 22 Sep. 2017].
Summary:
Operating systems are the software packages that act as an interface between the
users and the computer hardware. Many of the desktop and mobile operating
systems have been created for this purpose. One such widely used and one of the
most popular one in this list is Windows Operating System (OS). It was in the year
1985 that a software company called Microsoft released the initial version of
Windows OS. It was a disruptive innovation and the face behind the release of this
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OS was Bill Gates. Windows OS continues to be on the top charts till date and has
provided the users with enhanced capabilities with all of its nine versions. Bill co-
founded Microsoft and remained associated with the organization till the year 2000.
During his journey with Microsoft, he worked in different roles with chief solution
architect and CEO being the most prominent ones. He gave a new vision and
perspective to the company and contributed a lot in the field of technology and
software. The first project that he worked on in the organization was the BASIC
interpreter which was being done for the creation of a floppy disk system. He then
worked along with another company called IBM to work on the Windows OS which
was released in 1985. He continued to inspire the staff members with the dedication
towards creating something better each day. The article that is referred sums up all
his work in a concise manner along with the achievements and the success that he
achieved.
Week 3
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONE of the networks that led to the development of the
modern Internet.
Title and Reference:
Network before Internet - ARPANET
Theconversation (2016). How the Internet was born: from the ARPANET to the
Internet. [online] The Conversation. Available at: http://theconversation.com/how-the-
internet-was-born-from-the-arpanet-to-the-internet-68072 [Accessed 22 Sep. 2017].
Summary:
Internet is being used in every business sector and the users for personal as well as
professional activities. The launch of Internet was contributed with many other
networks that were set up prior to the same. Advanced Research Project Agency
Network (ARPANET) is one of the most prominent ones in the list that involved the
concept of packet switching and had an immense contribution in the launch of
Internet. There were two main bodies that were involved in the release and setup of
ARPANET Information Processing Techniques Office (IPTO) and Defense /
Advanced Research Project Agency (DARPA). The routers that were used in this
network were developed by a company called BBN technologies. All of these units
came together to create ARPANET which was released on August 30, 1969. It made
use of Interface Message Processor (IMP) and was basically used for information
sharing and communication with the aid of digital components. Many of the protocols
that are currently used in the functioning of the Internet were also developed during
the ARPANET project. Some of the extremely useful ones include File Transfer
Protocol (FTP) and Telnet. These are used for sharing and transfer of files from one
machine to the other. ARPANET is a network that is considered as a base for the
Internet and therefore has a lot of significance in the field of communication and
networks. The article also describes the complete timeline of the project and the set
of activities that were covered in a brief and clear manner.
Week 4
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
2
provided the users with enhanced capabilities with all of its nine versions. Bill co-
founded Microsoft and remained associated with the organization till the year 2000.
During his journey with Microsoft, he worked in different roles with chief solution
architect and CEO being the most prominent ones. He gave a new vision and
perspective to the company and contributed a lot in the field of technology and
software. The first project that he worked on in the organization was the BASIC
interpreter which was being done for the creation of a floppy disk system. He then
worked along with another company called IBM to work on the Windows OS which
was released in 1985. He continued to inspire the staff members with the dedication
towards creating something better each day. The article that is referred sums up all
his work in a concise manner along with the achievements and the success that he
achieved.
Week 3
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONE of the networks that led to the development of the
modern Internet.
Title and Reference:
Network before Internet - ARPANET
Theconversation (2016). How the Internet was born: from the ARPANET to the
Internet. [online] The Conversation. Available at: http://theconversation.com/how-the-
internet-was-born-from-the-arpanet-to-the-internet-68072 [Accessed 22 Sep. 2017].
Summary:
Internet is being used in every business sector and the users for personal as well as
professional activities. The launch of Internet was contributed with many other
networks that were set up prior to the same. Advanced Research Project Agency
Network (ARPANET) is one of the most prominent ones in the list that involved the
concept of packet switching and had an immense contribution in the launch of
Internet. There were two main bodies that were involved in the release and setup of
ARPANET Information Processing Techniques Office (IPTO) and Defense /
Advanced Research Project Agency (DARPA). The routers that were used in this
network were developed by a company called BBN technologies. All of these units
came together to create ARPANET which was released on August 30, 1969. It made
use of Interface Message Processor (IMP) and was basically used for information
sharing and communication with the aid of digital components. Many of the protocols
that are currently used in the functioning of the Internet were also developed during
the ARPANET project. Some of the extremely useful ones include File Transfer
Protocol (FTP) and Telnet. These are used for sharing and transfer of files from one
machine to the other. ARPANET is a network that is considered as a base for the
Internet and therefore has a lot of significance in the field of communication and
networks. The article also describes the complete timeline of the project and the set
of activities that were covered in a brief and clear manner.
Week 4
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
2

Title and Reference:
L-2 Protocol: Address Resolution Protocol (ARP)
Erg (2017). Address Resolution Protocol (arp). [online] Erg.abdn.ac.uk. Available at:
http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/arp.html [Accessed 22 Sep.
2017].
Summary:
Layer two makes use of many different protocols to make sure that communication
and networking processes are done correctly. Address Resolution Protocol (ARP) is
an example of one such protocol that works one L-2 and acts as a base for the
working of Wi-Fi connections and modern Ethernet. In order for a system or a mobile
device to be connected with a network, there is a unique address that is used by
every machine which is known as Media Access Control or the MAC address. The
message sharing and their delivery are possible only with the aid of the MAC
address. The process of networking and connections is done through MAC address.
Also, the mapping between the IP address and MAC address is established using
APR cache. In the scenario if this match is not found or is found invalid, then a
request is sent in the form of an ARP request to which ARP reply is obtained. This
reply provides the required permission for updating the cache and to continue with
the message delivery. There are also options which can be used for the
enhancement of network efficiency. There are also variations that have been
developed in association with this protocol with the setting up of inverse and reverse
ARP. In the article that has been used as a reference, there is a complete detail
about the ARP protocol and its functioning covered. Also, the information around the
variations and other instances has also been highlighted in the article.
Week 5
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title and Reference:
Famous Hacker: Kevin Mitnick
Mitnicksecurity (2017). Kevin Mitnick - The World's Most Famous Hacker. [online]
Mitnicksecurity.com. Available at: https://www.mitnicksecurity.com/about/kevin-
mitnick-worlds-most-famous-hacker-biography [Accessed 22 Sep. 2017].
Summary:
Hacking refers to the process in which the system or application security is breached
and the viable properties and the contents of the same are played with. The
properties of the information may get affected negatively through hacking services
and jobs. There are many hackers that have executed high-profile hack jobs and one
such name is of Kevin Mitnick. The United States Department of Justice has put him
in the category of the most-wanted computer criminals and these credits are because
of the list of hacking services that he has executed so far. Some of the cyber crimes
and hacking activities performed by Kevin have had sever implications on the
victims. Many of the popular and reputed organizations have also become the victims
of the crimes done by Kevin which include big names like Nokia and Motorola along
with many years. FBI arrested Kevin in 1995 and he had to serve five years in jail as
a punishment. He did not consider his attempts as crime because he believed them
to be the social engineering activities. He currently owns and works in a consulting
agency in the area of computer related services. He was released for the prison on
3
L-2 Protocol: Address Resolution Protocol (ARP)
Erg (2017). Address Resolution Protocol (arp). [online] Erg.abdn.ac.uk. Available at:
http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/arp.html [Accessed 22 Sep.
2017].
Summary:
Layer two makes use of many different protocols to make sure that communication
and networking processes are done correctly. Address Resolution Protocol (ARP) is
an example of one such protocol that works one L-2 and acts as a base for the
working of Wi-Fi connections and modern Ethernet. In order for a system or a mobile
device to be connected with a network, there is a unique address that is used by
every machine which is known as Media Access Control or the MAC address. The
message sharing and their delivery are possible only with the aid of the MAC
address. The process of networking and connections is done through MAC address.
Also, the mapping between the IP address and MAC address is established using
APR cache. In the scenario if this match is not found or is found invalid, then a
request is sent in the form of an ARP request to which ARP reply is obtained. This
reply provides the required permission for updating the cache and to continue with
the message delivery. There are also options which can be used for the
enhancement of network efficiency. There are also variations that have been
developed in association with this protocol with the setting up of inverse and reverse
ARP. In the article that has been used as a reference, there is a complete detail
about the ARP protocol and its functioning covered. Also, the information around the
variations and other instances has also been highlighted in the article.
Week 5
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title and Reference:
Famous Hacker: Kevin Mitnick
Mitnicksecurity (2017). Kevin Mitnick - The World's Most Famous Hacker. [online]
Mitnicksecurity.com. Available at: https://www.mitnicksecurity.com/about/kevin-
mitnick-worlds-most-famous-hacker-biography [Accessed 22 Sep. 2017].
Summary:
Hacking refers to the process in which the system or application security is breached
and the viable properties and the contents of the same are played with. The
properties of the information may get affected negatively through hacking services
and jobs. There are many hackers that have executed high-profile hack jobs and one
such name is of Kevin Mitnick. The United States Department of Justice has put him
in the category of the most-wanted computer criminals and these credits are because
of the list of hacking services that he has executed so far. Some of the cyber crimes
and hacking activities performed by Kevin have had sever implications on the
victims. Many of the popular and reputed organizations have also become the victims
of the crimes done by Kevin which include big names like Nokia and Motorola along
with many years. FBI arrested Kevin in 1995 and he had to serve five years in jail as
a punishment. He did not consider his attempts as crime because he believed them
to be the social engineering activities. He currently owns and works in a consulting
agency in the area of computer related services. He was released for the prison on
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
the terms of his good behaviour and cordial attitude with the rest of the prisoners. In
the article, the details and the set of hacking services executed by ten different
hacking professionals has been covered. The article has covered the information for
each of the hacker in a concise and to-the-point manner which adds to the readability
and connectivity for the readers.
Week 6
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title and Reference:
Wireless Data links and connections for Drones
Knutson, R. (2016). Verizon to Start Selling Wireless Data Plans for Drones. [online]
WSJ. Available at: https://www.wsj.com/articles/verizon-to-start-selling-wireless-data-
plans-for-drones-1475774573 [Accessed 22 Sep. 2017].
Summary:
Technology is changing rapidly and one area that has witnessed many
improvements and enhancement is the networking and communication. There are
many research projects that are going around in this field with wireless data setups
for drones as one of the prime topics. Drones are defined as the unmanned aerial
units that have a lot of applicability in many of the industrial sectors. Drones have
made it possible to allow the passengers to stay in the networking zones while they
take a flight for travelling for one place to the other place. In the present scenario, it is
seen that the network connections are not available mid-air and there is no way
through which the passengers may stay in touch with their contacts. Drones are
being applied in this area to make sure that long-distance connectivity can be easily
maintained without the issues of network lags and drops. It will also be extremely
useful and applicable for the purpose of defence and security. There will be a
revolution that will come up in the aviation industry with the release of such
technology as the tracking processes will also be more reliable. The technology will
benefit the travellers, aviation industry resources along with the countries as well as
their defence processes with strengthen. The article provides the details of the
research work that is being done by various researchers in this field and the benefits
that will be caused as a result have also been highlighted.
Week 7
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title and Reference:
Facebook & its History
Carlson, N. (2010). At Last -- The Full Story Of How Facebook Was Founded.
[online] Business Insider. Available at: http://www.businessinsider.com/how-
facebook-was-founded-2010-3?IR=T [Accessed 22 Sep. 2017].
Summary:
The present generation is making use of social media networking in most of their
personal and professional tasks and communication activities. Life without social
networking mediums is now hard to imagine and there are various such platforms
that are being widely used such as Instagram, Facebook, Twitter, Pinterest and
many more. One of the initial and most popular social media platforms is Facebook.
4
the article, the details and the set of hacking services executed by ten different
hacking professionals has been covered. The article has covered the information for
each of the hacker in a concise and to-the-point manner which adds to the readability
and connectivity for the readers.
Week 6
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title and Reference:
Wireless Data links and connections for Drones
Knutson, R. (2016). Verizon to Start Selling Wireless Data Plans for Drones. [online]
WSJ. Available at: https://www.wsj.com/articles/verizon-to-start-selling-wireless-data-
plans-for-drones-1475774573 [Accessed 22 Sep. 2017].
Summary:
Technology is changing rapidly and one area that has witnessed many
improvements and enhancement is the networking and communication. There are
many research projects that are going around in this field with wireless data setups
for drones as one of the prime topics. Drones are defined as the unmanned aerial
units that have a lot of applicability in many of the industrial sectors. Drones have
made it possible to allow the passengers to stay in the networking zones while they
take a flight for travelling for one place to the other place. In the present scenario, it is
seen that the network connections are not available mid-air and there is no way
through which the passengers may stay in touch with their contacts. Drones are
being applied in this area to make sure that long-distance connectivity can be easily
maintained without the issues of network lags and drops. It will also be extremely
useful and applicable for the purpose of defence and security. There will be a
revolution that will come up in the aviation industry with the release of such
technology as the tracking processes will also be more reliable. The technology will
benefit the travellers, aviation industry resources along with the countries as well as
their defence processes with strengthen. The article provides the details of the
research work that is being done by various researchers in this field and the benefits
that will be caused as a result have also been highlighted.
Week 7
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title and Reference:
Facebook & its History
Carlson, N. (2010). At Last -- The Full Story Of How Facebook Was Founded.
[online] Business Insider. Available at: http://www.businessinsider.com/how-
facebook-was-founded-2010-3?IR=T [Accessed 22 Sep. 2017].
Summary:
The present generation is making use of social media networking in most of their
personal and professional tasks and communication activities. Life without social
networking mediums is now hard to imagine and there are various such platforms
that are being widely used such as Instagram, Facebook, Twitter, Pinterest and
many more. One of the initial and most popular social media platforms is Facebook.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

It is being used by the users from every part of the globe and there are millions of
accounts that have been created on the same. It was developed in the year 2004 by
Mark Zuckerberg during his college days in the Harvard University. Initially it was a
website that was created to inter-connect the students of Harvard and the attempt
was successful as it earned over 1,200 users in one day. It later was being used by
more than half of the undergraduate student population in the university in 30 days.
Till the year 2005, Facebook was restricted for usage by only the entities from
Educational institutions and the address was made public thereafter. It was sold for
$200,000 and it allowed any user having a valid email id to create and setup an
account on Facebook. The social media platform is the largest of its kind in the world
and has more than 2.2 billion users all across the world. Users can perform several
tasks and activities on the platform, such as, connecting with other users, uploading
pictures and videos, tagging their friends in the pictures and videos, creating pages
and groups, instant messaging etc. The article was selected as a resource as it
covered the history and the relevance in a brief and clear manner.
Week 8
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title and Reference:
Application of Data Mining in Healthcare Organization
Silver M (2011). Case study: how to apply data mining techniques in a healthcare
data warehouse. - PubMed - NCBI. [online] Ncbi.nlm.nih.gov. Available at:
https://www.ncbi.nlm.nih.gov/pubmed/11452577 [Accessed 16 Sep. 2017].
Summary:
Technology is being improved and developed at a fast speed and one of the latest
additions to the technology is Business Intelligence concepts. There are various
technologies that come under Business Intelligence, such as data analysis, Online
Analytical Process, Data Mining etc. Data mining provides the organizations with
many benefits and is being used in many business sectors from all across the globe.
One such sector is the healthcare sector. Hitachi America Ltd along with St. Luke's
Medical Centre collaborated with each other to make use of data mining techniques
and applications in the data warehouses. Patient care and assistance and its
development was one of the prime focus of the project which further aimed at cutting
down the costs and increasing the revenues and efficiency levels. In case of the
health organizations like these, there are many different information types and
categories that are involved. It is also essential to carefully deal with all of these
information types so that the diagnostic and treatment process is accurate. These
capabilities were provided with the application of data mining techniques and it
further assisted in the decision making tasks as well. There are events wherein it
becomes difficult to understand the patient condition due to the involvement of so
many different symptoms. The task was made easy with the use of business
intelligence technique as data mining and the information has been captured with all
the details of the project in the case study that has been referred as a resource.
Week 9
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title and Reference:
5
accounts that have been created on the same. It was developed in the year 2004 by
Mark Zuckerberg during his college days in the Harvard University. Initially it was a
website that was created to inter-connect the students of Harvard and the attempt
was successful as it earned over 1,200 users in one day. It later was being used by
more than half of the undergraduate student population in the university in 30 days.
Till the year 2005, Facebook was restricted for usage by only the entities from
Educational institutions and the address was made public thereafter. It was sold for
$200,000 and it allowed any user having a valid email id to create and setup an
account on Facebook. The social media platform is the largest of its kind in the world
and has more than 2.2 billion users all across the world. Users can perform several
tasks and activities on the platform, such as, connecting with other users, uploading
pictures and videos, tagging their friends in the pictures and videos, creating pages
and groups, instant messaging etc. The article was selected as a resource as it
covered the history and the relevance in a brief and clear manner.
Week 8
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title and Reference:
Application of Data Mining in Healthcare Organization
Silver M (2011). Case study: how to apply data mining techniques in a healthcare
data warehouse. - PubMed - NCBI. [online] Ncbi.nlm.nih.gov. Available at:
https://www.ncbi.nlm.nih.gov/pubmed/11452577 [Accessed 16 Sep. 2017].
Summary:
Technology is being improved and developed at a fast speed and one of the latest
additions to the technology is Business Intelligence concepts. There are various
technologies that come under Business Intelligence, such as data analysis, Online
Analytical Process, Data Mining etc. Data mining provides the organizations with
many benefits and is being used in many business sectors from all across the globe.
One such sector is the healthcare sector. Hitachi America Ltd along with St. Luke's
Medical Centre collaborated with each other to make use of data mining techniques
and applications in the data warehouses. Patient care and assistance and its
development was one of the prime focus of the project which further aimed at cutting
down the costs and increasing the revenues and efficiency levels. In case of the
health organizations like these, there are many different information types and
categories that are involved. It is also essential to carefully deal with all of these
information types so that the diagnostic and treatment process is accurate. These
capabilities were provided with the application of data mining techniques and it
further assisted in the decision making tasks as well. There are events wherein it
becomes difficult to understand the patient condition due to the involvement of so
many different symptoms. The task was made easy with the use of business
intelligence technique as data mining and the information has been captured with all
the details of the project in the case study that has been referred as a resource.
Week 9
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title and Reference:
5

Jan Koum
Thefamouspeople (2017). Who is Jan Koum? Everything You Need to Know. [online]
Thefamouspeople.com. Available at: https://www.thefamouspeople.com/profiles/jan-
koum-7407.php [Accessed 22 Sep. 2017].
Summary:
WhatsApp has become more of a mandatory application for the present day mobile
users. It is a mobile messaging app that is being used by the users worldwide to stay
in touch with their personal and professional contacts. Sharing of messages and
other graphic content is done through WhatsApp that allows personal as well as
group chats. The man behind the development of this application is Jan Koum who
co-founded and developed the application. He is the CEO of the WhatsApp and
belongs to Ukraine. He started his career as a web developer at Yahoo and acquired
programming skills over there. He later quit his job and travelled all across the world
so that he could gain some inspiration and motivation. Apple’s marketplace was
launched in the year 2009 which was named as App Store and with its launch; Jan
received a goal in his life. He began working on the development of WhatsApp and
came up with the release of first version in January, 2010. The source code of
WhatsApp is written in Erlang language and there is also implementation of
Extensible Messaging and Presence Protocol (XMPP). It is an open standard that
has been used and implemented by Jan in its customized form in the application.
The users have gained the capability to stay connected with their contacts at all
times irrespective of their location. WhatsApp was sold out to Facebook in 2014 and
the deal was closed at the amount of USD 19 billion. The skills and contribution of
Jan has been covered in the article.
Week 10
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title and Reference:
Decline of language command in humans
Ukessays (2016). The Negative Impacts Of Information Technology On Society.
[online] UKEssays. Available at: https://www.ukessays.com/essays/information-
technology/the-negative-impacts-of-information-technology.php [Accessed 22 Sep.
2017].
Summary:
There are several benefits and advantages that have been given to the users with
the increased application of Information Systems in their personal and professional
tasks. This has also brought many of the negative outcomes for the business units.
There is a great use of information system and application in the field of networking
and communication. Users make use of applications like WhatsApp or Facebook to
talk to their contacts. All of these applications come with the capability to implement
auto-correction features which automatically corrects the incorrect words or spellings.
This has led to the issue of language command and proficiency in most of the
humans. The users do not focus upon the errors that they make in terms of the
incorrect use of grammar or the error in terms of spelling during their chats with other
users. Also, the web is filled up with a lot of information that comes from a variety of
sources. Some of these sources are reliable while most of these are unreliable that
6
Thefamouspeople (2017). Who is Jan Koum? Everything You Need to Know. [online]
Thefamouspeople.com. Available at: https://www.thefamouspeople.com/profiles/jan-
koum-7407.php [Accessed 22 Sep. 2017].
Summary:
WhatsApp has become more of a mandatory application for the present day mobile
users. It is a mobile messaging app that is being used by the users worldwide to stay
in touch with their personal and professional contacts. Sharing of messages and
other graphic content is done through WhatsApp that allows personal as well as
group chats. The man behind the development of this application is Jan Koum who
co-founded and developed the application. He is the CEO of the WhatsApp and
belongs to Ukraine. He started his career as a web developer at Yahoo and acquired
programming skills over there. He later quit his job and travelled all across the world
so that he could gain some inspiration and motivation. Apple’s marketplace was
launched in the year 2009 which was named as App Store and with its launch; Jan
received a goal in his life. He began working on the development of WhatsApp and
came up with the release of first version in January, 2010. The source code of
WhatsApp is written in Erlang language and there is also implementation of
Extensible Messaging and Presence Protocol (XMPP). It is an open standard that
has been used and implemented by Jan in its customized form in the application.
The users have gained the capability to stay connected with their contacts at all
times irrespective of their location. WhatsApp was sold out to Facebook in 2014 and
the deal was closed at the amount of USD 19 billion. The skills and contribution of
Jan has been covered in the article.
Week 10
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title and Reference:
Decline of language command in humans
Ukessays (2016). The Negative Impacts Of Information Technology On Society.
[online] UKEssays. Available at: https://www.ukessays.com/essays/information-
technology/the-negative-impacts-of-information-technology.php [Accessed 22 Sep.
2017].
Summary:
There are several benefits and advantages that have been given to the users with
the increased application of Information Systems in their personal and professional
tasks. This has also brought many of the negative outcomes for the business units.
There is a great use of information system and application in the field of networking
and communication. Users make use of applications like WhatsApp or Facebook to
talk to their contacts. All of these applications come with the capability to implement
auto-correction features which automatically corrects the incorrect words or spellings.
This has led to the issue of language command and proficiency in most of the
humans. The users do not focus upon the errors that they make in terms of the
incorrect use of grammar or the error in terms of spelling during their chats with other
users. Also, the web is filled up with a lot of information that comes from a variety of
sources. Some of these sources are reliable while most of these are unreliable that
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

add up to the ambiguity of the information. The in-person discussions and
communication mediums are slowly beginning to decline and the humans are also
found to be engaged with their phones. Even a low complexity task is now being
performed by taking aid of the mobile devices and the information systems and
applications that are installed in these devices. The article covers these problems in
an elaborated manner and their long-term damages on the human race.
7
communication mediums are slowly beginning to decline and the humans are also
found to be engaged with their phones. Even a low complexity task is now being
performed by taking aid of the mobile devices and the information systems and
applications that are installed in these devices. The article covers these problems in
an elaborated manner and their long-term damages on the human race.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
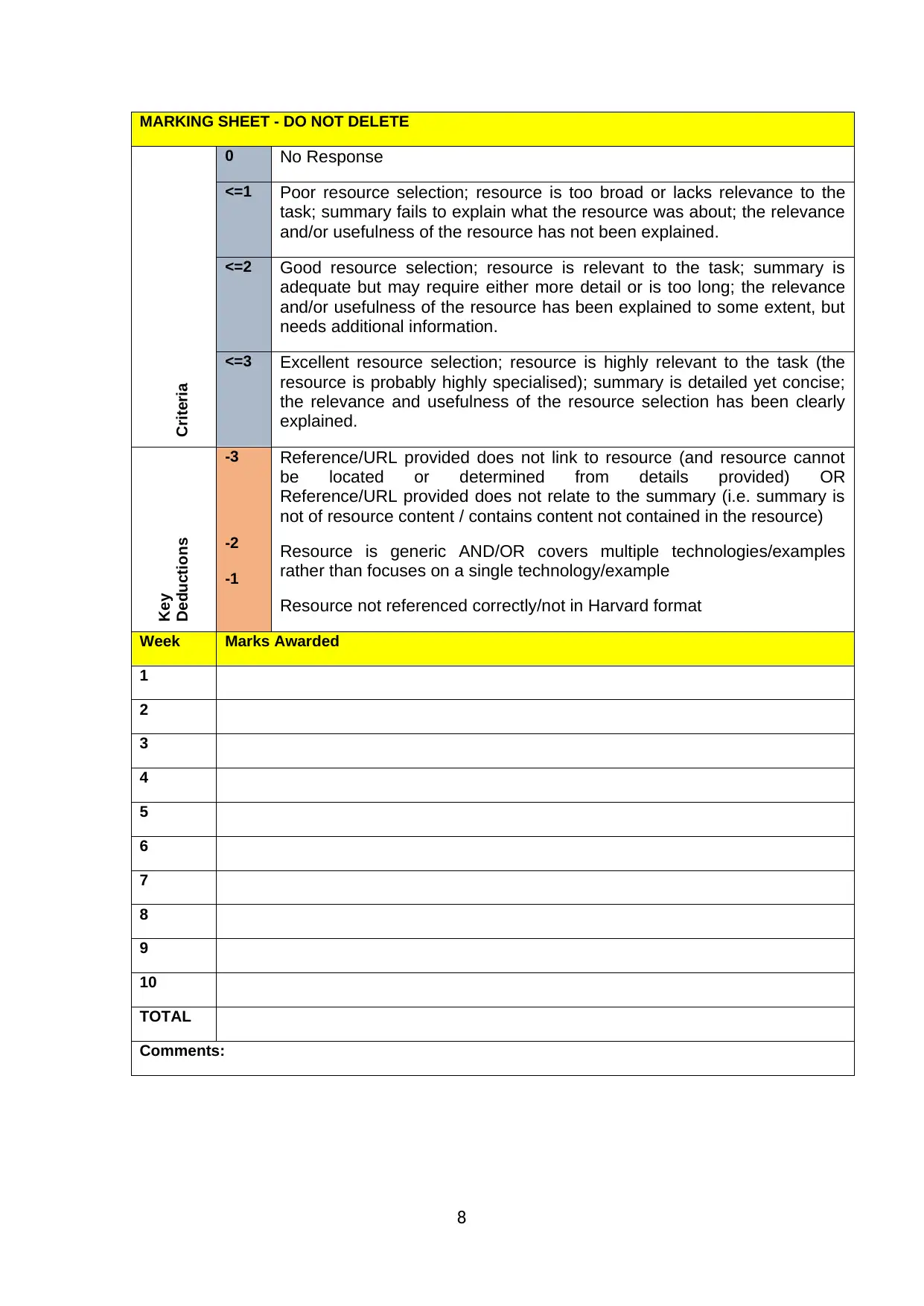
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
8
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
8
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





