BN203 Network Security: Analyzing Threats, Attacks & Mitigation Plans
VerifiedAdded on 2024/07/29
|9
|2241
|361
Report
AI Summary
This report provides a comprehensive overview of network device security, focusing on emerging threats, attacks, and mitigation strategies. It begins with an introduction to network device security, emphasizing the importance of device authentication and encryption. The report categorizes security attacks into passive and active types, detailing device, data, privacy, and network availability attacks. It further examines threats and attacks on TCP layers and routing protocols, including AODV, DSR, ARAN, ARIADNE, and SEAD. The report concludes by outlining various measure strategies, such as digital signatures, worm defense mechanisms, and geographic and temporal leashes, to enhance network security. This document is available on Desklib, where students can find additional resources and solved assignments.

BN203
Network Security 1
Identify emerging threats and mitigation strategies in
Information Systems
Student Name:
Student ID:
Network Security 1
Identify emerging threats and mitigation strategies in
Information Systems
Student Name:
Student ID:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Executive summary..................................................................................................................................... 3
Introduction.................................................................................................................................................3
Threats and attacks in network devices security.....................................................................................4
Threats and attacks on TCP layers........................................................................................................... 4
Attacks on the routing protocol............................................................................................................... 5
Measure strategies...................................................................................................................................... 5
Conclusion................................................................................................................................................... 6
References................................................................................................................................................... 7
Executive summary..................................................................................................................................... 3
Introduction.................................................................................................................................................3
Threats and attacks in network devices security.....................................................................................4
Threats and attacks on TCP layers........................................................................................................... 4
Attacks on the routing protocol............................................................................................................... 5
Measure strategies...................................................................................................................................... 5
Conclusion................................................................................................................................................... 6
References................................................................................................................................................... 7

Executive summary
This report discussed the challenges, threats, and issues in network devices security and strategies also
to control the cyber-attacks. This report starts with the introduction of network devices security. Device
authentication is the major concern in any communication session in which several approaches and
protocols are used for encryption, authentication of data packets and data integrity. The newly
developed strategies and its features were also discussed in this paper. Review of 10 papers was done to
make this report in which attacks on TCP layers and on routing protocols were discussed.
Introduction
Network devices are connected in a network in which routers and switches play an important role to
establish a connection and need to be in the secure environment either in a locked cabinet, a lock data
closet or both. Routers are used to send the packets from one network to another network in which
messages are encrypted and only authorized user can decrypt the message. There are many algorithms
and techniques which are used to secure the data packets from attackers. There are basic requirements
to secure the network devices such as setting passwords which user mode and privileged mode
passwords then encrypted the passwords [2]. Security attacks are categorized in two types: passive
attack and active attacks. Traffic analysis and eavesdropping are included in passive attacks and replay
attacks are included in active attacks active attacks include replay attack, denial of services, a man in the
middle attack [1]. There are different techniques which attackers used to alter, delete and insert data
while communication [9]. There are four types of attacks as:
1. Device attack: Once the attacker attack on the device, it leads to three more attacks because all data
is saved in a device which results in data attack, network availability attack, and privacy attack
because the attacker can control the device and the data which is stored in the device.it is the initial
step. To control device attack strict access control is required.
2. Data attack: Data attackers resulted in the wrong decision because irrelevant data can be inserted,
deleted in the original data and can modify the original data such as fabrication of data, back-hole
attack etc.
3. Privacy attack: By analyzing electricity data attacker can collect the personal information of the user
which leads to privacy attack.
4. Network availability attack: Attacking while transferring protocols via a network can cause network
availability attack in which delay or failure of data communication can result in a big loss to any
organization.
This report discussed the challenges, threats, and issues in network devices security and strategies also
to control the cyber-attacks. This report starts with the introduction of network devices security. Device
authentication is the major concern in any communication session in which several approaches and
protocols are used for encryption, authentication of data packets and data integrity. The newly
developed strategies and its features were also discussed in this paper. Review of 10 papers was done to
make this report in which attacks on TCP layers and on routing protocols were discussed.
Introduction
Network devices are connected in a network in which routers and switches play an important role to
establish a connection and need to be in the secure environment either in a locked cabinet, a lock data
closet or both. Routers are used to send the packets from one network to another network in which
messages are encrypted and only authorized user can decrypt the message. There are many algorithms
and techniques which are used to secure the data packets from attackers. There are basic requirements
to secure the network devices such as setting passwords which user mode and privileged mode
passwords then encrypted the passwords [2]. Security attacks are categorized in two types: passive
attack and active attacks. Traffic analysis and eavesdropping are included in passive attacks and replay
attacks are included in active attacks active attacks include replay attack, denial of services, a man in the
middle attack [1]. There are different techniques which attackers used to alter, delete and insert data
while communication [9]. There are four types of attacks as:
1. Device attack: Once the attacker attack on the device, it leads to three more attacks because all data
is saved in a device which results in data attack, network availability attack, and privacy attack
because the attacker can control the device and the data which is stored in the device.it is the initial
step. To control device attack strict access control is required.
2. Data attack: Data attackers resulted in the wrong decision because irrelevant data can be inserted,
deleted in the original data and can modify the original data such as fabrication of data, back-hole
attack etc.
3. Privacy attack: By analyzing electricity data attacker can collect the personal information of the user
which leads to privacy attack.
4. Network availability attack: Attacking while transferring protocols via a network can cause network
availability attack in which delay or failure of data communication can result in a big loss to any
organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

There are two mechanisms to handle the attacks: cryptographic approaches using new networking
protocols and physical layer security protocols. New cryptography uses public key cryptography and
symmetric key cryptography. Security approaches are based on availability, data confidentiality, data
integrity, authentication. HetNet, D2D, massive MIMO, IoT, and SDN are the new technologies which are
used to secure 5G wireless network. [1]
Network security services
1. Availability: After various security attacks availability ensures to provide resources and attacks can
cause a loss in availability.
2. Confidentiality: It ensures that the data can only access by the authorized user so that no third party
can take advantage or benefits.
3. Integrity: It ensures that the data cannot be modified or attack by an unauthorized user or any third
party.
4. Authentication: It ensures that the connection is authenticated and only authorized user can access
the data.
5. Scalability: It ensures to handle large networks such as ad hoc network is a large network in which
network should be scalable.[2]
Threats and attacks in network devices security
There are many attacks that occur in ad hoc environment and an infected node can create many attacks
which leads to generating more other attacks such as spoofing which change the identity, MAC AND IP
address in packets because there is authentication of the data packets in the ad hoc environment [2].
1. The modification is an attack in which the original data are modified by an unauthorized party. It
changes the meaning or objective of the data [2].
2. Fabrication allows an attacker to access the data and inject false information into the system. This
attack is not easy to handle or verify because they fabricated the original data and no one can find
the original data [2].
3. In back hole attack, the attacker modified or change packets from the originating node and the data
from the other node remain unaffected.
4. When a single node or multiple nodes work in cooperation to attack then it is called Byzantine
attack. It may form routing loops which can degrade the performance of routing services. In this
attack, packets follow a long route rather than the short one and may drop packets while routing.
protocols and physical layer security protocols. New cryptography uses public key cryptography and
symmetric key cryptography. Security approaches are based on availability, data confidentiality, data
integrity, authentication. HetNet, D2D, massive MIMO, IoT, and SDN are the new technologies which are
used to secure 5G wireless network. [1]
Network security services
1. Availability: After various security attacks availability ensures to provide resources and attacks can
cause a loss in availability.
2. Confidentiality: It ensures that the data can only access by the authorized user so that no third party
can take advantage or benefits.
3. Integrity: It ensures that the data cannot be modified or attack by an unauthorized user or any third
party.
4. Authentication: It ensures that the connection is authenticated and only authorized user can access
the data.
5. Scalability: It ensures to handle large networks such as ad hoc network is a large network in which
network should be scalable.[2]
Threats and attacks in network devices security
There are many attacks that occur in ad hoc environment and an infected node can create many attacks
which leads to generating more other attacks such as spoofing which change the identity, MAC AND IP
address in packets because there is authentication of the data packets in the ad hoc environment [2].
1. The modification is an attack in which the original data are modified by an unauthorized party. It
changes the meaning or objective of the data [2].
2. Fabrication allows an attacker to access the data and inject false information into the system. This
attack is not easy to handle or verify because they fabricated the original data and no one can find
the original data [2].
3. In back hole attack, the attacker modified or change packets from the originating node and the data
from the other node remain unaffected.
4. When a single node or multiple nodes work in cooperation to attack then it is called Byzantine
attack. It may form routing loops which can degrade the performance of routing services. In this
attack, packets follow a long route rather than the short one and may drop packets while routing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5. Denial of service attack is a kind of wormhole attack which changes the track of the original route by
form a tunnel such as ARN and Ariadne. It is also known as tunnelling attack in which two nodes get
overlap and exchange the messages in the original route [5].
6. Information in the location disclosure attack gets leak related to the location such as route map and
create traffic analysis attack against MANETs.
7. In session hijacking, the data were authenticated only at the starting of the session set up and allow
an attacker to hijack the system.
Threats and attacks on TCP layers
This segment discussed the attacks on each layer of the TCP protocol and its countermeasures [2]. Many
attacks occur on TCP protocol layers are:
form a tunnel such as ARN and Ariadne. It is also known as tunnelling attack in which two nodes get
overlap and exchange the messages in the original route [5].
6. Information in the location disclosure attack gets leak related to the location such as route map and
create traffic analysis attack against MANETs.
7. In session hijacking, the data were authenticated only at the starting of the session set up and allow
an attacker to hijack the system.
Threats and attacks on TCP layers
This segment discussed the attacks on each layer of the TCP protocol and its countermeasures [2]. Many
attacks occur on TCP protocol layers are:
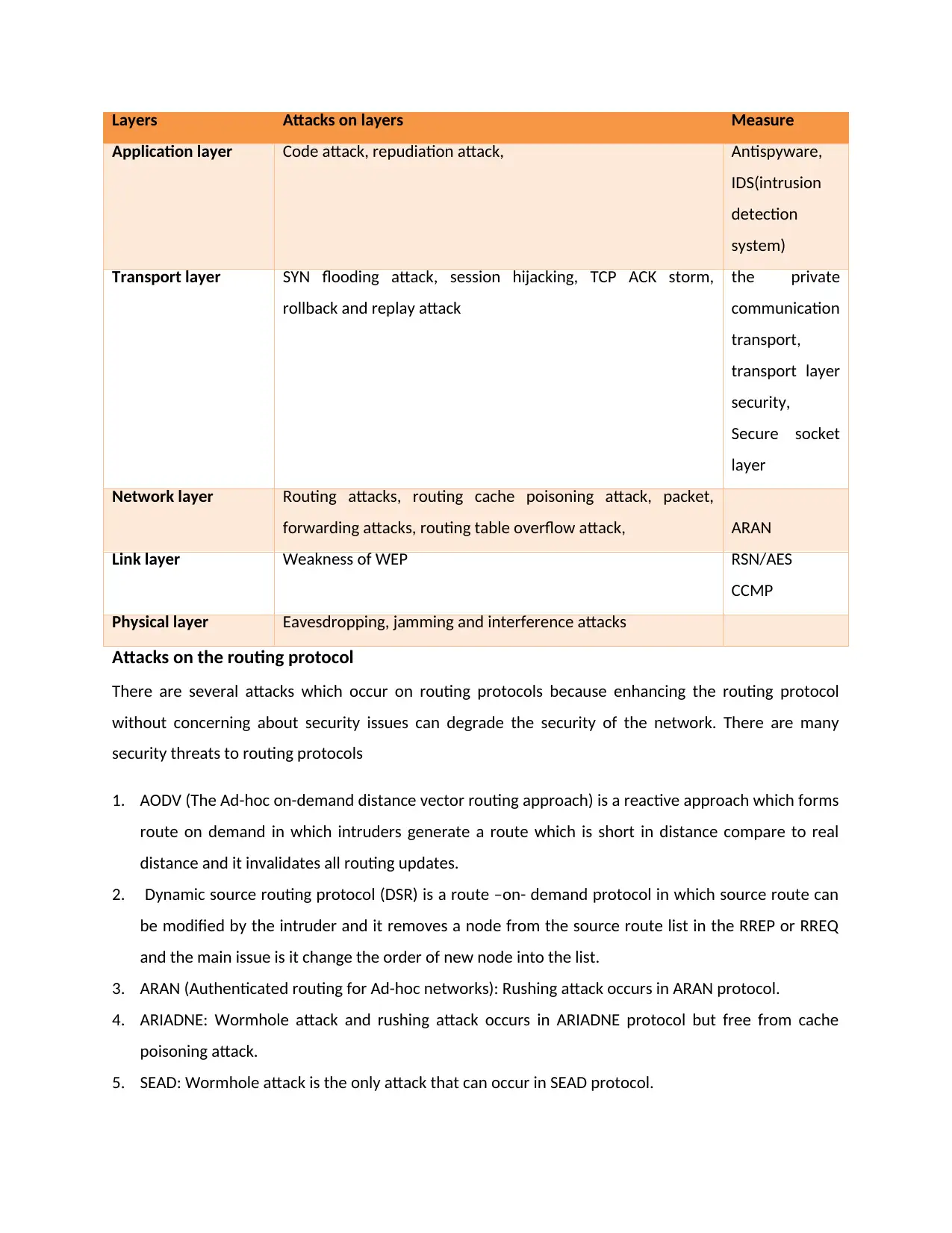
Layers Attacks on layers Measure
Application layer Code attack, repudiation attack, Antispyware,
IDS(intrusion
detection
system)
Transport layer SYN flooding attack, session hijacking, TCP ACK storm,
rollback and replay attack
the private
communication
transport,
transport layer
security,
Secure socket
layer
Network layer Routing attacks, routing cache poisoning attack, packet,
forwarding attacks, routing table overflow attack, ARAN
Link layer Weakness of WEP RSN/AES
CCMP
Physical layer Eavesdropping, jamming and interference attacks
Attacks on the routing protocol
There are several attacks which occur on routing protocols because enhancing the routing protocol
without concerning about security issues can degrade the security of the network. There are many
security threats to routing protocols
1. AODV (The Ad-hoc on-demand distance vector routing approach) is a reactive approach which forms
route on demand in which intruders generate a route which is short in distance compare to real
distance and it invalidates all routing updates.
2. Dynamic source routing protocol (DSR) is a route –on- demand protocol in which source route can
be modified by the intruder and it removes a node from the source route list in the RREP or RREQ
and the main issue is it change the order of new node into the list.
3. ARAN (Authenticated routing for Ad-hoc networks): Rushing attack occurs in ARAN protocol.
4. ARIADNE: Wormhole attack and rushing attack occurs in ARIADNE protocol but free from cache
poisoning attack.
5. SEAD: Wormhole attack is the only attack that can occur in SEAD protocol.
Application layer Code attack, repudiation attack, Antispyware,
IDS(intrusion
detection
system)
Transport layer SYN flooding attack, session hijacking, TCP ACK storm,
rollback and replay attack
the private
communication
transport,
transport layer
security,
Secure socket
layer
Network layer Routing attacks, routing cache poisoning attack, packet,
forwarding attacks, routing table overflow attack, ARAN
Link layer Weakness of WEP RSN/AES
CCMP
Physical layer Eavesdropping, jamming and interference attacks
Attacks on the routing protocol
There are several attacks which occur on routing protocols because enhancing the routing protocol
without concerning about security issues can degrade the security of the network. There are many
security threats to routing protocols
1. AODV (The Ad-hoc on-demand distance vector routing approach) is a reactive approach which forms
route on demand in which intruders generate a route which is short in distance compare to real
distance and it invalidates all routing updates.
2. Dynamic source routing protocol (DSR) is a route –on- demand protocol in which source route can
be modified by the intruder and it removes a node from the source route list in the RREP or RREQ
and the main issue is it change the order of new node into the list.
3. ARAN (Authenticated routing for Ad-hoc networks): Rushing attack occurs in ARAN protocol.
4. ARIADNE: Wormhole attack and rushing attack occurs in ARIADNE protocol but free from cache
poisoning attack.
5. SEAD: Wormhole attack is the only attack that can occur in SEAD protocol.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Measure strategies
1. Digital signature: It involves encryption and decryption or signing process and based on asymmetric
key cryptography such as RSA.
2. Two mechanisms are used to protect MANET: preventive and reactive in cooperation enforcement
mechanism, intrusion detection system, encryption, digital signature.
3. There are six classes of worm defence: worm containment which is based on filter, threshold
random walk scan detection, worm scan filtering based on a signature, rate limiting, payload
classification based containment, and rate halting.
4. Indra is a mechanism which shares sensitive information of two authorized users in a network to
protect or secure the network against intruders. It is a detection tool which follows a P2P approach
to secure the network [5].
5. To restrict the transmission of maximum distance of a packet in wormhole attack, geographic and
temporal leashes is used [6].
6. AODV routing algorithm does not create traffic while communication across wireless mesh network
and requires less memory.
7. DSR routing algorithm doesn’t depend on the routing table, it uses source routing.
8. ARAN protects and detects suspicious actions against the unauthorized party in the Ad-hoc
environment. It provides message integrity, authentication and no –repudiation to minimize the
security attacks.
9. ARIADNE: It offers point to point authentication by MAC (message authentication code) which share
the key between two authorized users. It is based on DSR which implements symmetric
cryptography.
10. SEAD: It is based on DSDV protocol (Destination sequenced distance vector). It uses one-way hash
chains instead of using expensive symmetric cryptography. It deals against many attacks such as
replay attacks and modification of routing information.
Conclusion
In this report, we discussed the attacks and various approaches to defend against these attacks and the
approaches to overcome these attacks. This report describes the challenges and issues in the network
security. There are several countermeasures which were affected by attacks because enhancement of
protocols without concerning about security can increase the security threats which degrade the
performance of the protocols or approaches which are made to secure the network devices. New
1. Digital signature: It involves encryption and decryption or signing process and based on asymmetric
key cryptography such as RSA.
2. Two mechanisms are used to protect MANET: preventive and reactive in cooperation enforcement
mechanism, intrusion detection system, encryption, digital signature.
3. There are six classes of worm defence: worm containment which is based on filter, threshold
random walk scan detection, worm scan filtering based on a signature, rate limiting, payload
classification based containment, and rate halting.
4. Indra is a mechanism which shares sensitive information of two authorized users in a network to
protect or secure the network against intruders. It is a detection tool which follows a P2P approach
to secure the network [5].
5. To restrict the transmission of maximum distance of a packet in wormhole attack, geographic and
temporal leashes is used [6].
6. AODV routing algorithm does not create traffic while communication across wireless mesh network
and requires less memory.
7. DSR routing algorithm doesn’t depend on the routing table, it uses source routing.
8. ARAN protects and detects suspicious actions against the unauthorized party in the Ad-hoc
environment. It provides message integrity, authentication and no –repudiation to minimize the
security attacks.
9. ARIADNE: It offers point to point authentication by MAC (message authentication code) which share
the key between two authorized users. It is based on DSR which implements symmetric
cryptography.
10. SEAD: It is based on DSDV protocol (Destination sequenced distance vector). It uses one-way hash
chains instead of using expensive symmetric cryptography. It deals against many attacks such as
replay attacks and modification of routing information.
Conclusion
In this report, we discussed the attacks and various approaches to defend against these attacks and the
approaches to overcome these attacks. This report describes the challenges and issues in the network
security. There are several countermeasures which were affected by attacks because enhancement of
protocols without concerning about security can increase the security threats which degrade the
performance of the protocols or approaches which are made to secure the network devices. New
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
technologies are discussed in this paper to secure a 5G wireless network. This report review 10 papers in
which security threats, approaches to secure the network against attacks, attacks on routing protocols
was discussed which helps to find the best approach for a particular attack.
which security threats, approaches to secure the network against attacks, attacks on routing protocols
was discussed which helps to find the best approach for a particular attack.

References
[1] D. Fang, Y. Qian and R. Q. Hu, "Security for 5G Mobile Wireless Networks," in IEEE Access, vol. 6, pp.
4850-4874, 2018.
[2] Biswas, Kamanashis, and Md Ali. "Security threats in mobile ad hoc network." (2007).
[3] Yang, Hao, et al. "Security in mobile ad hoc networks: challenges and solutions." (2004): 38-47.
[4] Stallings, William. Network Security Essentials: Applications and Standards, 4/e. Pearson Education
India, 2000.
[5] Janakiraman, Ramaprabhu, Marcel Waldvogel, and Qi Zhang. "Indra: A peer-to-peer approach to
network intrusion detection and prevention." Enabling Technologies: Infrastructure for Collaborative
Enterprises, 2003. WET ICE 2003. Proceedings. Twelfth IEEE International Workshops on. IEEE, 2003.
[6] Hu, Y-C., Adrian Perrig, and David B. Johnson. "Packet leashes: a defense against wormhole attacks in
wireless networks." INFOCOM 2003. Twenty-Second Annual Joint Conference of the IEEE Computer and
Communications. IEEE Societies. Vol. 3. IEEE, 2003.
[7] Karlof, Chris, and David Wagner. "Secure routing in wireless sensor networks: Attacks and
countermeasures." Sensor Network Protocols and Applications, 2003. Proceedings of the First IEEE. 2003
IEEE International Workshop on. IEEE, 2003.
[8] Zhu, Sencun, Sanjeev Setia, and SushilJajodia. "LEAP+: Efficient security mechanisms for large-scale
distributed sensor networks." ACM Transactions on Sensor Networks (TOSN) 2.4 (2006): 500-528.
[9] Li, Xu, et al. "Securing smart grid: cyber-attacks, countermeasures, and challenges." IEEE
Communications Magazine 50.8 (2012).
[10] Teixeira, André, Henrik Sandberg, and Karl H. Johansson. "Networked control systems under cyber-
attacks with applications to power networks." American Control Conference (ACC), 2010. IEEE, 2010.
[11] Cardenas, Alvaro A., Saurabh Amin, and Shankar Sastry. "Secure control: Towards survivable cyber-
physical systems." Distributed Computing Systems Workshops, 2008. ICDCS'08. 28th International
Conference on. IEEE, 2008.
[1] D. Fang, Y. Qian and R. Q. Hu, "Security for 5G Mobile Wireless Networks," in IEEE Access, vol. 6, pp.
4850-4874, 2018.
[2] Biswas, Kamanashis, and Md Ali. "Security threats in mobile ad hoc network." (2007).
[3] Yang, Hao, et al. "Security in mobile ad hoc networks: challenges and solutions." (2004): 38-47.
[4] Stallings, William. Network Security Essentials: Applications and Standards, 4/e. Pearson Education
India, 2000.
[5] Janakiraman, Ramaprabhu, Marcel Waldvogel, and Qi Zhang. "Indra: A peer-to-peer approach to
network intrusion detection and prevention." Enabling Technologies: Infrastructure for Collaborative
Enterprises, 2003. WET ICE 2003. Proceedings. Twelfth IEEE International Workshops on. IEEE, 2003.
[6] Hu, Y-C., Adrian Perrig, and David B. Johnson. "Packet leashes: a defense against wormhole attacks in
wireless networks." INFOCOM 2003. Twenty-Second Annual Joint Conference of the IEEE Computer and
Communications. IEEE Societies. Vol. 3. IEEE, 2003.
[7] Karlof, Chris, and David Wagner. "Secure routing in wireless sensor networks: Attacks and
countermeasures." Sensor Network Protocols and Applications, 2003. Proceedings of the First IEEE. 2003
IEEE International Workshop on. IEEE, 2003.
[8] Zhu, Sencun, Sanjeev Setia, and SushilJajodia. "LEAP+: Efficient security mechanisms for large-scale
distributed sensor networks." ACM Transactions on Sensor Networks (TOSN) 2.4 (2006): 500-528.
[9] Li, Xu, et al. "Securing smart grid: cyber-attacks, countermeasures, and challenges." IEEE
Communications Magazine 50.8 (2012).
[10] Teixeira, André, Henrik Sandberg, and Karl H. Johansson. "Networked control systems under cyber-
attacks with applications to power networks." American Control Conference (ACC), 2010. IEEE, 2010.
[11] Cardenas, Alvaro A., Saurabh Amin, and Shankar Sastry. "Secure control: Towards survivable cyber-
physical systems." Distributed Computing Systems Workshops, 2008. ICDCS'08. 28th International
Conference on. IEEE, 2008.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





