Encryption and Security in Cloud Computing
Added on 2023-05-31
6 Pages2894 Words168 Views
Cloud Computing
First Author#1, Second Author*2, Third Author#3
#First-Third Department, First-Third University
Address Including Country Name
1first.author@first-third.edu
3third.author@first-third.edu
*Second Company
Address Including Country Name
2second.author@second.com
First Author#1, Second Author*2, Third Author#3
#First-Third Department, First-Third University
Address Including Country Name
1first.author@first-third.edu
3third.author@first-third.edu
*Second Company
Address Including Country Name
2second.author@second.com

Abstract— Cloud computing has found great importance in the
market. This is the most convenient way to share or store data.
This contains several computer systems that are connected
together to share resources. The well-known cloud software’s are
Google cloud platform, Microsoft Azure, iCloud and many more.
This is necessary to maintain a security for the stored data within
the cloud. Thus with time the need of security also increases and
this requires a huge amount of cash. This paper will identify and
analyse the need of encryption and security in the cloud
computing. Encryption helps in protecting the data from
unauthorized access and also provides highest security, as the
data can be accessed by only those members who are having the
key to decrypt thee message. There are several encryption
methods available and thus it is very necessary to understand the
perfect encryption method for the company.
Keywords- Encryption, Cloud computing, Data privacy,
Storage, Business, Cryptomator
I. INTRODUCTION
The aim of the report is to analyse the need of encryption
in providing security for the cloud computing in an
organization. The main advantage of shifting to cloud system
is that it provides easy recovery of data and backups are been
done frequently. This helps the organization to recover data
easily. Cloud computing is also known as the cloud. This
provides on demand resources and the user needs to pay for
the resources they are using. Cloud computing enables the
users with free storage and provides high elasticity. The
resources pool offered by the cloud to their customer is in a
huge amount. This ensures that a huge amount of resource is
being dynamically allocated to the customers [10]. There is no
upfront cost associated with the cloud and maintains a
transparent structure. There are different architectures
provided by the cloud and the user can choose among this
infrastructure. There are mainly three infrastructure offered by
cloud, this are as follows: IaaS ( infrastructure as a Servicee),
PaaS(Platform as a Service) and SaaS(Software as a Service).
This paper aims at discussing the advantages and
disadvantages of using cloud computing and the features
offered by this service in detailed. The paper will also discuss
about the types of security ad encryption methods offered with
the cloud.
II. IDENTIFICATION OF THE PROBLEM
The aim of the report is to identify the challenges that
are likely to cone with the use of cloud computing. There
are several challenges faced and also there are lot of
issues that arises with the security provided by the cloud.
The organization always needs to understand the need of
customer and analyse accordingly [17]. This is the
responsibility of each organization to meet the
requirement of the customer and satisfy them with their
services. The objective is to transfer and store all data
with highest security. The main problem that are faced
with the security issues are as follows:
A. Authentication
This is the responsibility of each data stored
within the organization to maintain confidentiality
and privacy. The customer’s data needs to be stored
with highest security. The user’s needs the
satisfaction that the data stored maintains the
integrity and also it is accessed by authorized person
only. This ensures that the data stored will never get
breached [13]. Moreover, it is the responsibility of
the mouser to maintain password and not to share
those credentials with other members. This will
ensure the authentication and also a necessary aspect.
B. Access control
The ability of the system to give access to only
authorized persons. This controls the number of users
and ensures that only registered person is allowed to
have the access [11].
C. Privacy
Another important factor is the privacy factor. It
is the responsibility of each site to maintain privacy
that is the data shared needs to be kept private. In
case the customer demands for deleting the
information related to the customer, it is the
responsibility of the organization to delete all records
[12].
III. LITERATURE REVIEW
A. Importance of cryptography
Cryptography is the science of providing security for
information and resources by using appropriate technologies.
Cryptography is mainly used for non-technological reasons.
This includes hiding of physical messages, or creating ciphers
so that only authorized person can have the access and can
understand the contents. This is basically the main reason for
Data Encryption [9]. The logic used in Cryptography is based
on maths and uses this logic to create algorithms for computer
systems. This is used mainly for securing the data or before
transferring the data or just before securing data storage.
Cryptography is the science of providing security for
information and resources by using appropriate technologies.
The transmission made with the Cryptography ensures that the
transferred it is done with highest security. In order to
maintain the security within the data transferred between the
computers it is necessary to encrypt the data [6].
Cryptography aim is to ensure their users that the transaction
done is secured. Key management is an important aspect in
encryption that allows you to apply common encryption
policies across all data on all managed devices. The number of
areas in which the cryptography is being used are as follows:
• One way cryptographic are used for storing the
password in a way that cannot be achieved.
• Cryptography allows securing delivery of
authenticating data only in one direction.
• Cryptography ensures that the information is sent too
desired customer only.
market. This is the most convenient way to share or store data.
This contains several computer systems that are connected
together to share resources. The well-known cloud software’s are
Google cloud platform, Microsoft Azure, iCloud and many more.
This is necessary to maintain a security for the stored data within
the cloud. Thus with time the need of security also increases and
this requires a huge amount of cash. This paper will identify and
analyse the need of encryption and security in the cloud
computing. Encryption helps in protecting the data from
unauthorized access and also provides highest security, as the
data can be accessed by only those members who are having the
key to decrypt thee message. There are several encryption
methods available and thus it is very necessary to understand the
perfect encryption method for the company.
Keywords- Encryption, Cloud computing, Data privacy,
Storage, Business, Cryptomator
I. INTRODUCTION
The aim of the report is to analyse the need of encryption
in providing security for the cloud computing in an
organization. The main advantage of shifting to cloud system
is that it provides easy recovery of data and backups are been
done frequently. This helps the organization to recover data
easily. Cloud computing is also known as the cloud. This
provides on demand resources and the user needs to pay for
the resources they are using. Cloud computing enables the
users with free storage and provides high elasticity. The
resources pool offered by the cloud to their customer is in a
huge amount. This ensures that a huge amount of resource is
being dynamically allocated to the customers [10]. There is no
upfront cost associated with the cloud and maintains a
transparent structure. There are different architectures
provided by the cloud and the user can choose among this
infrastructure. There are mainly three infrastructure offered by
cloud, this are as follows: IaaS ( infrastructure as a Servicee),
PaaS(Platform as a Service) and SaaS(Software as a Service).
This paper aims at discussing the advantages and
disadvantages of using cloud computing and the features
offered by this service in detailed. The paper will also discuss
about the types of security ad encryption methods offered with
the cloud.
II. IDENTIFICATION OF THE PROBLEM
The aim of the report is to identify the challenges that
are likely to cone with the use of cloud computing. There
are several challenges faced and also there are lot of
issues that arises with the security provided by the cloud.
The organization always needs to understand the need of
customer and analyse accordingly [17]. This is the
responsibility of each organization to meet the
requirement of the customer and satisfy them with their
services. The objective is to transfer and store all data
with highest security. The main problem that are faced
with the security issues are as follows:
A. Authentication
This is the responsibility of each data stored
within the organization to maintain confidentiality
and privacy. The customer’s data needs to be stored
with highest security. The user’s needs the
satisfaction that the data stored maintains the
integrity and also it is accessed by authorized person
only. This ensures that the data stored will never get
breached [13]. Moreover, it is the responsibility of
the mouser to maintain password and not to share
those credentials with other members. This will
ensure the authentication and also a necessary aspect.
B. Access control
The ability of the system to give access to only
authorized persons. This controls the number of users
and ensures that only registered person is allowed to
have the access [11].
C. Privacy
Another important factor is the privacy factor. It
is the responsibility of each site to maintain privacy
that is the data shared needs to be kept private. In
case the customer demands for deleting the
information related to the customer, it is the
responsibility of the organization to delete all records
[12].
III. LITERATURE REVIEW
A. Importance of cryptography
Cryptography is the science of providing security for
information and resources by using appropriate technologies.
Cryptography is mainly used for non-technological reasons.
This includes hiding of physical messages, or creating ciphers
so that only authorized person can have the access and can
understand the contents. This is basically the main reason for
Data Encryption [9]. The logic used in Cryptography is based
on maths and uses this logic to create algorithms for computer
systems. This is used mainly for securing the data or before
transferring the data or just before securing data storage.
Cryptography is the science of providing security for
information and resources by using appropriate technologies.
The transmission made with the Cryptography ensures that the
transferred it is done with highest security. In order to
maintain the security within the data transferred between the
computers it is necessary to encrypt the data [6].
Cryptography aim is to ensure their users that the transaction
done is secured. Key management is an important aspect in
encryption that allows you to apply common encryption
policies across all data on all managed devices. The number of
areas in which the cryptography is being used are as follows:
• One way cryptographic are used for storing the
password in a way that cannot be achieved.
• Cryptography allows securing delivery of
authenticating data only in one direction.
• Cryptography ensures that the information is sent too
desired customer only.

• Digital signature helps in providing an effective way
to sign off an instruction within a computer.
B. Encryption
This is necessary to maintain a proper secured way of
encryption that will help in protecting the data. There are
several types of encryption available that helps in protecting
the data sets properly. This is a process of encoding a message
received by the user. In an encryption a plain text is encrypted
using encryption algorithm. After this with the help of a
cipher, cipher text is generated and that is being decoded with
the use of decryption key. With the help of Encryption it
becomes difficult for viruses, Trojans and logic bomb to get
hooked up[4]. This is the responsibility of the user to keep in
mind that in time of the encryption any coding can be placed
in the same bracket. The motive is to make the coding more
relatable and easy to interpret. This signifies that in the time of
encryption the technique used is cryptographic and every time
you compress a file or transmit it with error correction codes.
This all factors are important from the security point of view.
There are several types of encryption available, this are as
follows:
1. Symmetric and asymmetric key
cryptography
In the case of symmetric key cryptography a key is
being generated and whose copy is being kept with the
one encrypting the data and given to the user to whom
this information belongs. Thus, this ensures that only
authorized person will be able to read the message. In the
case of asymmetric key cryptography, two keys are
created one the public key and another one the private
key [7]. The public key is used to encrypt plain text
whereas the working of the private key involves
decrypting the cipher text to plain text.
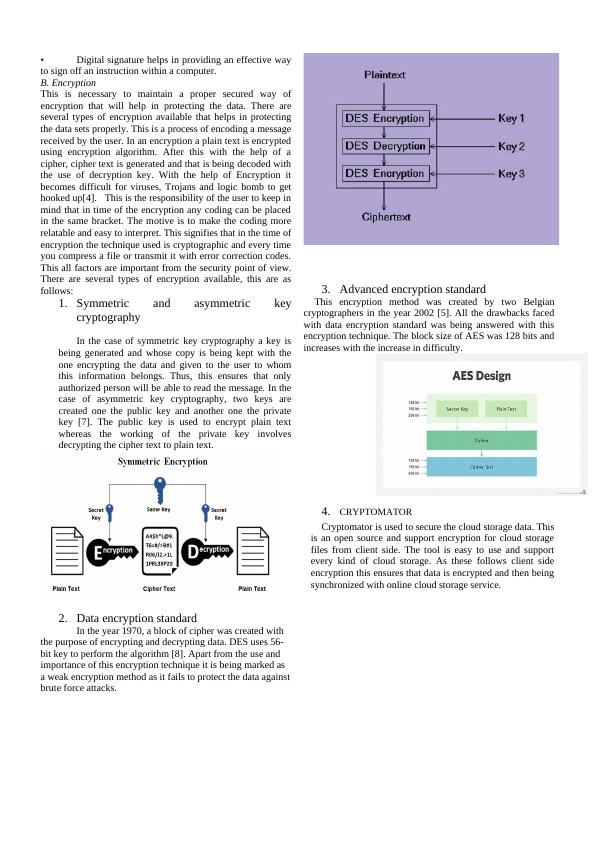
2. Data encryption standard
In the year 1970, a block of cipher was created with
the purpose of encrypting and decrypting data. DES uses 56-
bit key to perform the algorithm [8]. Apart from the use and
importance of this encryption technique it is being marked as
a weak encryption method as it fails to protect the data against
brute force attacks.
3. Advanced encryption standard
This encryption method was created by two Belgian
cryptographers in the year 2002 [5]. All the drawbacks faced
with data encryption standard was being answered with this
encryption technique. The block size of AES was 128 bits and
increases with the increase in difficulty.
4. CRYPTOMATOR
Cryptomator is used to secure the cloud storage data. This
is an open source and support encryption for cloud storage
files from client side. The tool is easy to use and support
every kind of cloud storage. As these follows client side
encryption this ensures that data is encrypted and then being
synchronized with online cloud storage service.
to sign off an instruction within a computer.
B. Encryption
This is necessary to maintain a proper secured way of
encryption that will help in protecting the data. There are
several types of encryption available that helps in protecting
the data sets properly. This is a process of encoding a message
received by the user. In an encryption a plain text is encrypted
using encryption algorithm. After this with the help of a
cipher, cipher text is generated and that is being decoded with
the use of decryption key. With the help of Encryption it
becomes difficult for viruses, Trojans and logic bomb to get
hooked up[4]. This is the responsibility of the user to keep in
mind that in time of the encryption any coding can be placed
in the same bracket. The motive is to make the coding more
relatable and easy to interpret. This signifies that in the time of
encryption the technique used is cryptographic and every time
you compress a file or transmit it with error correction codes.
This all factors are important from the security point of view.
There are several types of encryption available, this are as
follows:
1. Symmetric and asymmetric key
cryptography
In the case of symmetric key cryptography a key is
being generated and whose copy is being kept with the
one encrypting the data and given to the user to whom
this information belongs. Thus, this ensures that only
authorized person will be able to read the message. In the
case of asymmetric key cryptography, two keys are
created one the public key and another one the private
key [7]. The public key is used to encrypt plain text
whereas the working of the private key involves
decrypting the cipher text to plain text.
2. Data encryption standard
In the year 1970, a block of cipher was created with
the purpose of encrypting and decrypting data. DES uses 56-
bit key to perform the algorithm [8]. Apart from the use and
importance of this encryption technique it is being marked as
a weak encryption method as it fails to protect the data against
brute force attacks.
3. Advanced encryption standard
This encryption method was created by two Belgian
cryptographers in the year 2002 [5]. All the drawbacks faced
with data encryption standard was being answered with this
encryption technique. The block size of AES was 128 bits and
increases with the increase in difficulty.
4. CRYPTOMATOR
Cryptomator is used to secure the cloud storage data. This
is an open source and support encryption for cloud storage
files from client side. The tool is easy to use and support
every kind of cloud storage. As these follows client side
encryption this ensures that data is encrypted and then being
synchronized with online cloud storage service.
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Secure User Data in Cloud Computing Using Encryption Algorithmslg...
|6
|1418
|140
Cloud Computing and its Securitylg...
|6
|1303
|492
Securing User Data In Computing Of Cloud Using Encryption Algorithmlg...
|13
|780
|167
Security Issue in Cloud Computinglg...
|14
|624
|70
Security and Privacy Issues and Prevention Methods in Cloud Computinglg...
|4
|4001
|93
Cloud Computing Security PDFlg...
|13
|3038
|39
