Master's Cryptography: Encryption Techniques and Algorithms Analysis
VerifiedAdded on 2022/12/05
|13
|3022
|459
Homework Assignment
AI Summary
This assignment delves into various encryption techniques and algorithms, addressing key aspects of cryptography. The solution explores cryptographic solutions like Message Digest algorithm MD5 and Secure Hash Algorithm (SHA), detailing their advantages and disadvantages with supporting diagrams. It explains how message digests work in a file transfer scenario. The role of arbiters in digital signatures and the insufficiency of message authentication are also discussed. The assignment further examines security services provided by digital signatures and the order of signature and encryption functions. Furthermore, the assignment demonstrates transposition and substitution ciphers with examples and compares MD5, SHA, and RSA algorithms. Overall, the assignment provides a comprehensive overview of cryptographic principles, including practical applications and theoretical underpinnings.

Running head: ENCRYPTION TECHNIQUES AND ALGORITHMS
Encryption Techniques and Algorithms
Name of the Student
Name of the University
Author Note
Encryption Techniques and Algorithms
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
ENCRYPTION TECHNIQUES AND ALGORITHMS
Question 1
a) With the aid of diagram, describe the proposed solutions for the above
scenario. For each solution, provide ONE (1) advantage and ONE (1)
disadvantage.
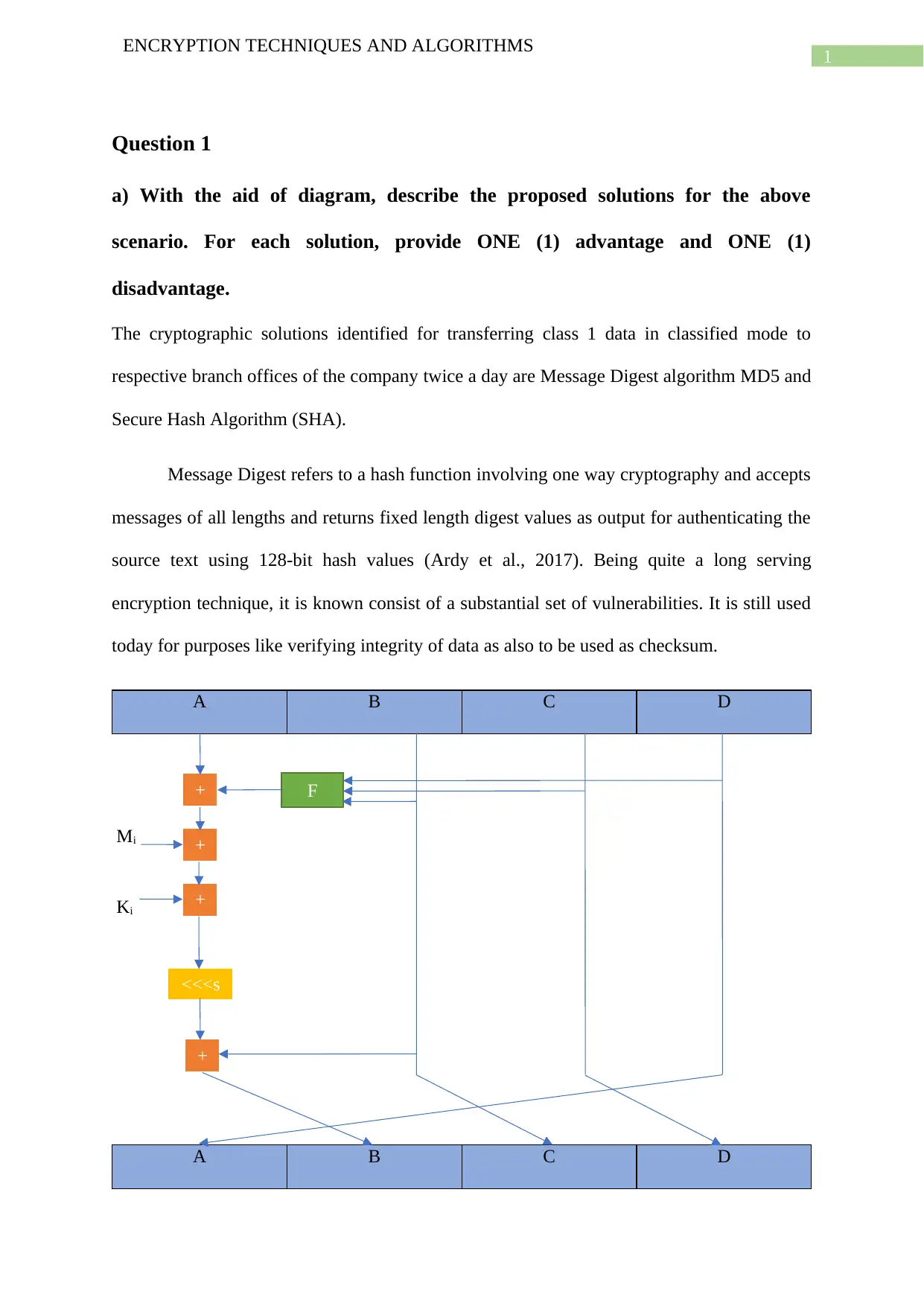
The cryptographic solutions identified for transferring class 1 data in classified mode to
respective branch offices of the company twice a day are Message Digest algorithm MD5 and
Secure Hash Algorithm (SHA).
Message Digest refers to a hash function involving one way cryptography and accepts
messages of all lengths and returns fixed length digest values as output for authenticating the
source text using 128-bit hash values (Ardy et al., 2017). Being quite a long serving
encryption technique, it is known consist of a substantial set of vulnerabilities. It is still used
today for purposes like verifying integrity of data as also to be used as checksum.
A B C D
Mi
Ki
A B C D
+
+
+
<<<s
+
F
ENCRYPTION TECHNIQUES AND ALGORITHMS
Question 1
a) With the aid of diagram, describe the proposed solutions for the above
scenario. For each solution, provide ONE (1) advantage and ONE (1)
disadvantage.
The cryptographic solutions identified for transferring class 1 data in classified mode to
respective branch offices of the company twice a day are Message Digest algorithm MD5 and
Secure Hash Algorithm (SHA).
Message Digest refers to a hash function involving one way cryptography and accepts
messages of all lengths and returns fixed length digest values as output for authenticating the
source text using 128-bit hash values (Ardy et al., 2017). Being quite a long serving
encryption technique, it is known consist of a substantial set of vulnerabilities. It is still used
today for purposes like verifying integrity of data as also to be used as checksum.
A B C D
Mi
Ki
A B C D
+
+
+
<<<s
+
F

2
ENCRYPTION TECHNIQUES AND ALGORITHMS
Figure 1: MD5 operation
The above diagram represents one of the 64 MD5 operations present in four different
rounds each which has 16 number of operations. Here, F denotes nonlinear functions and one
of these functions get used in every round. The variable Mi points to input messages of 32 bit
block sizes input messages while Ki is the constant and <<<s refers to the rotation towards
the left of bits by s places. Both Ki and <<<s differs with every operation.
Advantage: It is faster to compute 128 bit digests in md5 than 160 bit digests and above in
SHA. As MD5 already excels in purposes other than cryptography, the speed benefit that
MD5 provides makes it the preferred choice.
Disadvantage: The cryptographic algorithm MD5 is reportedly vulnerable to hash collision.
The weakness enables attackers in creating various different input sources which, when
the MD5 algorithm is in use, results in the output of the same fingerprint.
SHA or Secure Hash Algorithm refers to the group of cryptographic hashing
techniques that take inputs and produce 160 bit long (20 bytes) hash values called message
digest and typically gets rendered as hexadecimal numbers of length 40 digits.
A B C D E
Wt
Kt
+
+
+
+
F
<<<s
<<<30
ENCRYPTION TECHNIQUES AND ALGORITHMS
Figure 1: MD5 operation
The above diagram represents one of the 64 MD5 operations present in four different
rounds each which has 16 number of operations. Here, F denotes nonlinear functions and one
of these functions get used in every round. The variable Mi points to input messages of 32 bit
block sizes input messages while Ki is the constant and <<<s refers to the rotation towards
the left of bits by s places. Both Ki and <<<s differs with every operation.
Advantage: It is faster to compute 128 bit digests in md5 than 160 bit digests and above in
SHA. As MD5 already excels in purposes other than cryptography, the speed benefit that
MD5 provides makes it the preferred choice.
Disadvantage: The cryptographic algorithm MD5 is reportedly vulnerable to hash collision.
The weakness enables attackers in creating various different input sources which, when
the MD5 algorithm is in use, results in the output of the same fingerprint.
SHA or Secure Hash Algorithm refers to the group of cryptographic hashing
techniques that take inputs and produce 160 bit long (20 bytes) hash values called message
digest and typically gets rendered as hexadecimal numbers of length 40 digits.
A B C D E
Wt
Kt
+
+
+
+
F
<<<s
<<<30
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
ENCRYPTION TECHNIQUES AND ALGORITHMS
A B C D E
Figure 2: SHA operation
This presents one operation of the SHA hashing technique. Here A, B, C, D, E are 32
bit words of the state. <<<s is the left circular shift, Wt the message input and Kt is the
constant with <<<s and Kt varying for every iteration.
Advantage: The higher bit sized hashing provides tighter security as it becomes difficult to
crack these codes because the process requires greater number of combinations. It is
important to note that in cryptographic hashing algorithms every hash generated is a unique
one.
Disadvantage: Compared to MD5, SHA techniques are slower to process because of using
160bit or higher hash values (Canteaut, A. 2016). As a result SHA is generally not used in
non-cryptographic tasks.
ENCRYPTION TECHNIQUES AND ALGORITHMS
A B C D E
Figure 2: SHA operation
This presents one operation of the SHA hashing technique. Here A, B, C, D, E are 32
bit words of the state. <<<s is the left circular shift, Wt the message input and Kt is the
constant with <<<s and Kt varying for every iteration.
Advantage: The higher bit sized hashing provides tighter security as it becomes difficult to
crack these codes because the process requires greater number of combinations. It is
important to note that in cryptographic hashing algorithms every hash generated is a unique
one.
Disadvantage: Compared to MD5, SHA techniques are slower to process because of using
160bit or higher hash values (Canteaut, A. 2016). As a result SHA is generally not used in
non-cryptographic tasks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
ENCRYPTION TECHNIQUES AND ALGORITHMS
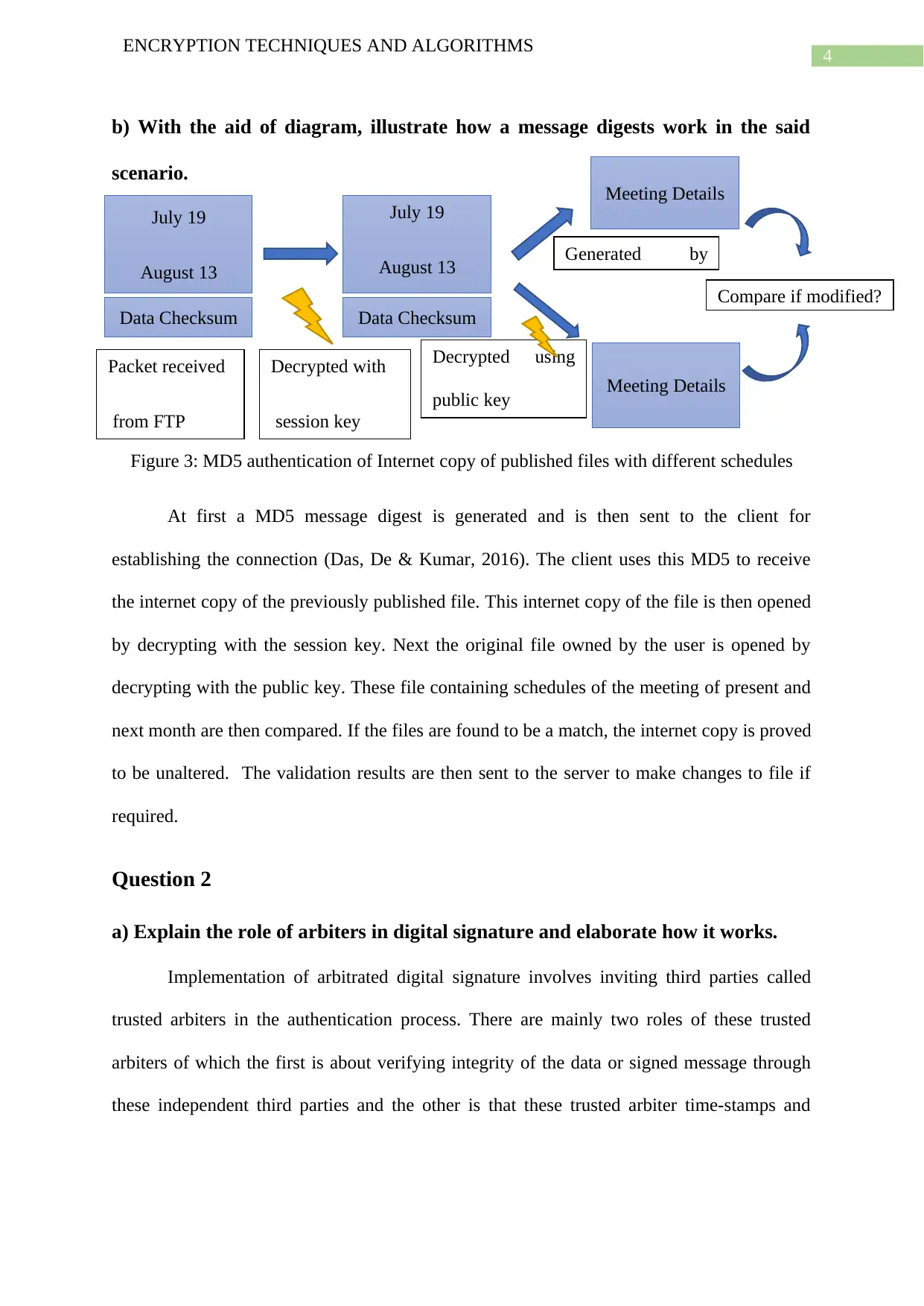
b) With the aid of diagram, illustrate how a message digests work in the said
scenario.
Figure 3: MD5 authentication of Internet copy of published files with different schedules
At first a MD5 message digest is generated and is then sent to the client for
establishing the connection (Das, De & Kumar, 2016). The client uses this MD5 to receive
the internet copy of the previously published file. This internet copy of the file is then opened
by decrypting with the session key. Next the original file owned by the user is opened by
decrypting with the public key. These file containing schedules of the meeting of present and
next month are then compared. If the files are found to be a match, the internet copy is proved
to be unaltered. The validation results are then sent to the server to make changes to file if
required.
Question 2
a) Explain the role of arbiters in digital signature and elaborate how it works.
Implementation of arbitrated digital signature involves inviting third parties called
trusted arbiters in the authentication process. There are mainly two roles of these trusted
arbiters of which the first is about verifying integrity of the data or signed message through
these independent third parties and the other is that these trusted arbiter time-stamps and
July 19
August 13
Data Checksum
July 19
August 13
Data Checksum
Decrypted with
session key
Packet received
from FTP
Meeting Details
Meeting Details
Generated by
MD5
Decrypted using
public key
Compare if modified?
ENCRYPTION TECHNIQUES AND ALGORITHMS
b) With the aid of diagram, illustrate how a message digests work in the said
scenario.
Figure 3: MD5 authentication of Internet copy of published files with different schedules
At first a MD5 message digest is generated and is then sent to the client for
establishing the connection (Das, De & Kumar, 2016). The client uses this MD5 to receive
the internet copy of the previously published file. This internet copy of the file is then opened
by decrypting with the session key. Next the original file owned by the user is opened by
decrypting with the public key. These file containing schedules of the meeting of present and
next month are then compared. If the files are found to be a match, the internet copy is proved
to be unaltered. The validation results are then sent to the server to make changes to file if
required.
Question 2
a) Explain the role of arbiters in digital signature and elaborate how it works.
Implementation of arbitrated digital signature involves inviting third parties called
trusted arbiters in the authentication process. There are mainly two roles of these trusted
arbiters of which the first is about verifying integrity of the data or signed message through
these independent third parties and the other is that these trusted arbiter time-stamps and
July 19
August 13
Data Checksum
July 19
August 13
Data Checksum
Decrypted with
session key
Packet received
from FTP
Meeting Details
Meeting Details
Generated by
MD5
Decrypted using
public key
Compare if modified?

5
ENCRYPTION TECHNIQUES AND ALGORITHMS
dates the documents and thus verifies receipts and passes on the signed documents to the
intended destination.
All signed messages between A and B come to the third party arbiter AB whom both
A and B trusts (Hwang et al., 2016). AB verifies the signature, the timestamp, origins,
contents and the like. Then it provides the dates to the message before sending to B while
also indicating that the message was verified and found to be legitimate. Here each user and
the arbiter shares a secret key.
· A sends the message to AB in encrypted forms along with P or plaintext containing
B’s id, the timestamp the random number RA.
AB then decrypts this message thereby ensuring that sender is A as also verifying the
timestamp to prevent replays.
· After that AB sends the message P to B along with the identity of A, the random
number RA and the timestamp. Additionally it sends the message which it encrypts with own
private key which is not known to anyone and contains identity of A, the plaintext P – a hash
and the timestamp.
Though B is unable to verify this signature, it trusts the signature as it comes from AB
– which it knows because KB is used to encrypt the total communication.
B does not encourage older messages and messages that have same RA in order to
prevent replays.
If any dispute occurs, B puts up the signature it received from AB and will get
decrypted by AB.
ENCRYPTION TECHNIQUES AND ALGORITHMS
dates the documents and thus verifies receipts and passes on the signed documents to the
intended destination.
All signed messages between A and B come to the third party arbiter AB whom both
A and B trusts (Hwang et al., 2016). AB verifies the signature, the timestamp, origins,
contents and the like. Then it provides the dates to the message before sending to B while
also indicating that the message was verified and found to be legitimate. Here each user and
the arbiter shares a secret key.
· A sends the message to AB in encrypted forms along with P or plaintext containing
B’s id, the timestamp the random number RA.
AB then decrypts this message thereby ensuring that sender is A as also verifying the
timestamp to prevent replays.
· After that AB sends the message P to B along with the identity of A, the random
number RA and the timestamp. Additionally it sends the message which it encrypts with own
private key which is not known to anyone and contains identity of A, the plaintext P – a hash
and the timestamp.
Though B is unable to verify this signature, it trusts the signature as it comes from AB
– which it knows because KB is used to encrypt the total communication.
B does not encourage older messages and messages that have same RA in order to
prevent replays.
If any dispute occurs, B puts up the signature it received from AB and will get
decrypted by AB.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
ENCRYPTION TECHNIQUES AND ALGORITHMS
b) With an appropriate example, explain why message authentication alone is
insufficient as proof of message origin in general, and to settle disputes about
whether messages have been sent.
It is a general mistake to solely focus on ensuring privacy of messages without any
concerns on the implications of modification to the message which can result by errors
in transmission or purposely by malicious attackers.
When this transmission is not authenticated and changes can be done to messages
over the communication lines, there can arise several kinds of problems. Some of these can
be like sending false credentials to merchants which the bank will always reject and since the
message is known to be a reject, the value of the message can simply be changed by flipping
the zero which the bank had sent into a one.
c) Identify security service that is provided by digital signatures and explain how
this service relates to message authentication.
Every entity availing the scheme of digital signatures, contain a pair of public private
key. These keys vary depending on processes like encryption or decryption and signing or
verifying. The signer sends data to the hash functions thus generating the hash values of this
data. Then this hash value along with the signature keys are provided to the encryption
algorithm, that then generates appropriate digital signature depending on this hash value. The
signature generated further gets added to this data provided to verifying entity. The verifying
entity again runs the received data on the same hash function for generating the hash values.
The hash value then gets verified by comparing with the verification algorithm and this
determines whether or not the digital signature is valid.
ENCRYPTION TECHNIQUES AND ALGORITHMS
b) With an appropriate example, explain why message authentication alone is
insufficient as proof of message origin in general, and to settle disputes about
whether messages have been sent.
It is a general mistake to solely focus on ensuring privacy of messages without any
concerns on the implications of modification to the message which can result by errors
in transmission or purposely by malicious attackers.
When this transmission is not authenticated and changes can be done to messages
over the communication lines, there can arise several kinds of problems. Some of these can
be like sending false credentials to merchants which the bank will always reject and since the
message is known to be a reject, the value of the message can simply be changed by flipping
the zero which the bank had sent into a one.
c) Identify security service that is provided by digital signatures and explain how
this service relates to message authentication.
Every entity availing the scheme of digital signatures, contain a pair of public private
key. These keys vary depending on processes like encryption or decryption and signing or
verifying. The signer sends data to the hash functions thus generating the hash values of this
data. Then this hash value along with the signature keys are provided to the encryption
algorithm, that then generates appropriate digital signature depending on this hash value. The
signature generated further gets added to this data provided to verifying entity. The verifying
entity again runs the received data on the same hash function for generating the hash values.
The hash value then gets verified by comparing with the verification algorithm and this
determines whether or not the digital signature is valid.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
ENCRYPTION TECHNIQUES AND ALGORITHMS
d) Determine in what order the signature function and the encryption function
should apply. Provide your justifications.
It is always better to first have the signature done, and proceed with encryption
thereafter (Vasco & Steinwandt, 2016). Since it largely depends on the use cases therefore
there may exist select situations in which one should opt for going the opposite way.
However the latter is quite rare.
The rough analogy is of encrypting in such a way that apart from keeping document
safe, the signature on the document is also safeguarded so that it cannot be forged by any
person or entity especially those who should not have access to the contents.
In other words, first signing and then encrypting is basically as good as signing some
document and then ensuring that the signed document is kept safe.
Thus this method only lets those people able to open the safe (here decrypting the
message) and thereby get the chance of verifying the signature.
Question 3
a) With appropriate examples, demonstrate the transposition cipher and the
substitution cipher.
Substitution and transposition are the two key ciphers that are typically used in
cryptography. The two ciphers mainly differ in the way message chunks get handled when
they are encrypted.
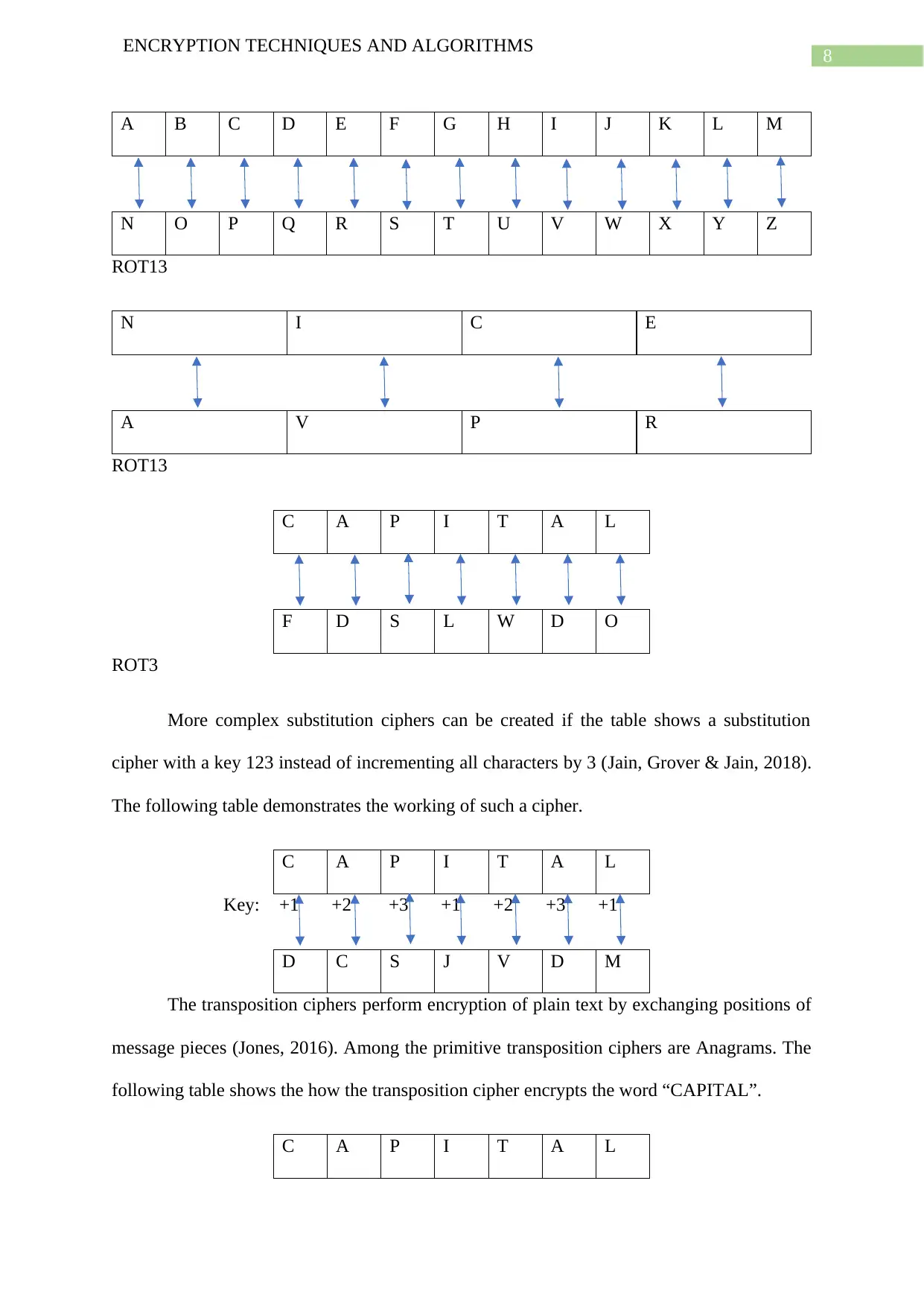
In substitution, the plaintext is encrypted by the ciphers, one at a time. The Caesar
cipher was an early substitution cipher where each character is rotated upwards (ROT) by a
fixed number like 13 or 3 (Khan & Qazi, 2018). The following tables show Caesar cipher
encrypting the plain texts NICE and CAPITAL by rotation 13 and 3 respectively.
ENCRYPTION TECHNIQUES AND ALGORITHMS
d) Determine in what order the signature function and the encryption function
should apply. Provide your justifications.
It is always better to first have the signature done, and proceed with encryption
thereafter (Vasco & Steinwandt, 2016). Since it largely depends on the use cases therefore
there may exist select situations in which one should opt for going the opposite way.
However the latter is quite rare.
The rough analogy is of encrypting in such a way that apart from keeping document
safe, the signature on the document is also safeguarded so that it cannot be forged by any
person or entity especially those who should not have access to the contents.
In other words, first signing and then encrypting is basically as good as signing some
document and then ensuring that the signed document is kept safe.
Thus this method only lets those people able to open the safe (here decrypting the
message) and thereby get the chance of verifying the signature.
Question 3
a) With appropriate examples, demonstrate the transposition cipher and the
substitution cipher.
Substitution and transposition are the two key ciphers that are typically used in
cryptography. The two ciphers mainly differ in the way message chunks get handled when
they are encrypted.
In substitution, the plaintext is encrypted by the ciphers, one at a time. The Caesar
cipher was an early substitution cipher where each character is rotated upwards (ROT) by a
fixed number like 13 or 3 (Khan & Qazi, 2018). The following tables show Caesar cipher
encrypting the plain texts NICE and CAPITAL by rotation 13 and 3 respectively.
8
ENCRYPTION TECHNIQUES AND ALGORITHMS
A B C D E F G H I J K L M
N O P Q R S T U V W X Y Z
ROT13
N I C E
A V P R
ROT13
C A P I T A L
F D S L W D O
ROT3
More complex substitution ciphers can be created if the table shows a substitution
cipher with a key 123 instead of incrementing all characters by 3 (Jain, Grover & Jain, 2018).
The following table demonstrates the working of such a cipher.
C A P I T A L
Key: +1 +2 +3 +1 +2 +3 +1
D C S J V D M
The transposition ciphers perform encryption of plain text by exchanging positions of
message pieces (Jones, 2016). Among the primitive transposition ciphers are Anagrams. The
following table shows the how the transposition cipher encrypts the word “CAPITAL”.
C A P I T A L
ENCRYPTION TECHNIQUES AND ALGORITHMS
A B C D E F G H I J K L M
N O P Q R S T U V W X Y Z
ROT13
N I C E
A V P R
ROT13
C A P I T A L
F D S L W D O
ROT3
More complex substitution ciphers can be created if the table shows a substitution
cipher with a key 123 instead of incrementing all characters by 3 (Jain, Grover & Jain, 2018).
The following table demonstrates the working of such a cipher.
C A P I T A L
Key: +1 +2 +3 +1 +2 +3 +1
D C S J V D M
The transposition ciphers perform encryption of plain text by exchanging positions of
message pieces (Jones, 2016). Among the primitive transposition ciphers are Anagrams. The
following table shows the how the transposition cipher encrypts the word “CAPITAL”.
C A P I T A L
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
ENCRYPTION TECHNIQUES AND ALGORITHMS
A C I P A T L
Here, the positions of every two adjacent letters of the word are exchanged thus
resulting in a different set of text (Lasry, Kopal & Wacker, 2016). Though today’s
cryptanalysis have largely rendered the substitution and transposition ciphers out of date, the
techniques still continue to lend significant insight on cryptography in general and even on
how current complex ciphers function.
b) Search articles for secure hash algorithms and write a summary on the
comparison of MD5, SHA and RSA.
Secure hash algorithms refer to the set of algorithms that have been developed by
National Institutes of Standards and Technology or NIST along with some private as well as
government parties (Novotny et al., 2017). They are secure cryptographic (file check)
functions which are formed for addressing the key cybersecurity risks that have been
plaguing the 21st century also termed the information age. The algorithm, SHA-0 came to
light in 1993. Similar to SHA-1 which follows it, SHA-0 also operates with 160 bit hash
values.
The secure hash algorithm that succeeds SHA-1 is SHA-2 and this encryption
algorithm can involve two functions, one of 256 bit size and the other of 512 bit size (Zhu,
Zhu & Wang, 2018). Another secure hash algorithm exists called SHA-3 or Keccak which
even succeeds SHA-2 and has been developed through a crowd sourced contest for
identifying the next generation of cryptographic algorithm for cybersecurity. SHA is
commonly applied in encrypting passwords for the server side just requires keeping track of
hash values of specific users instead of tracking the original passwords. This especially helps
in the event of databases getting hacked by attackers, the original passwords will not be
ENCRYPTION TECHNIQUES AND ALGORITHMS
A C I P A T L
Here, the positions of every two adjacent letters of the word are exchanged thus
resulting in a different set of text (Lasry, Kopal & Wacker, 2016). Though today’s
cryptanalysis have largely rendered the substitution and transposition ciphers out of date, the
techniques still continue to lend significant insight on cryptography in general and even on
how current complex ciphers function.
b) Search articles for secure hash algorithms and write a summary on the
comparison of MD5, SHA and RSA.
Secure hash algorithms refer to the set of algorithms that have been developed by
National Institutes of Standards and Technology or NIST along with some private as well as
government parties (Novotny et al., 2017). They are secure cryptographic (file check)
functions which are formed for addressing the key cybersecurity risks that have been
plaguing the 21st century also termed the information age. The algorithm, SHA-0 came to
light in 1993. Similar to SHA-1 which follows it, SHA-0 also operates with 160 bit hash
values.
The secure hash algorithm that succeeds SHA-1 is SHA-2 and this encryption
algorithm can involve two functions, one of 256 bit size and the other of 512 bit size (Zhu,
Zhu & Wang, 2018). Another secure hash algorithm exists called SHA-3 or Keccak which
even succeeds SHA-2 and has been developed through a crowd sourced contest for
identifying the next generation of cryptographic algorithm for cybersecurity. SHA is
commonly applied in encrypting passwords for the server side just requires keeping track of
hash values of specific users instead of tracking the original passwords. This especially helps
in the event of databases getting hacked by attackers, the original passwords will not be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
ENCRYPTION TECHNIQUES AND ALGORITHMS
known to the attacker easily, only the hashed values will appear. If these hashed values are
inserted by the attacker as passwords they will get converted to another string and access will
be denied. Moreover, SHAs can cause an avalanche effect, by which modifications to one or
few letters getting encrypted can result in a largely altered output, or otherwise dramatically
different strings can also end up producing similar hash values (Ye & Huang, 2016). Such
effects prevent hash values from providing information about the input string or the true
length.
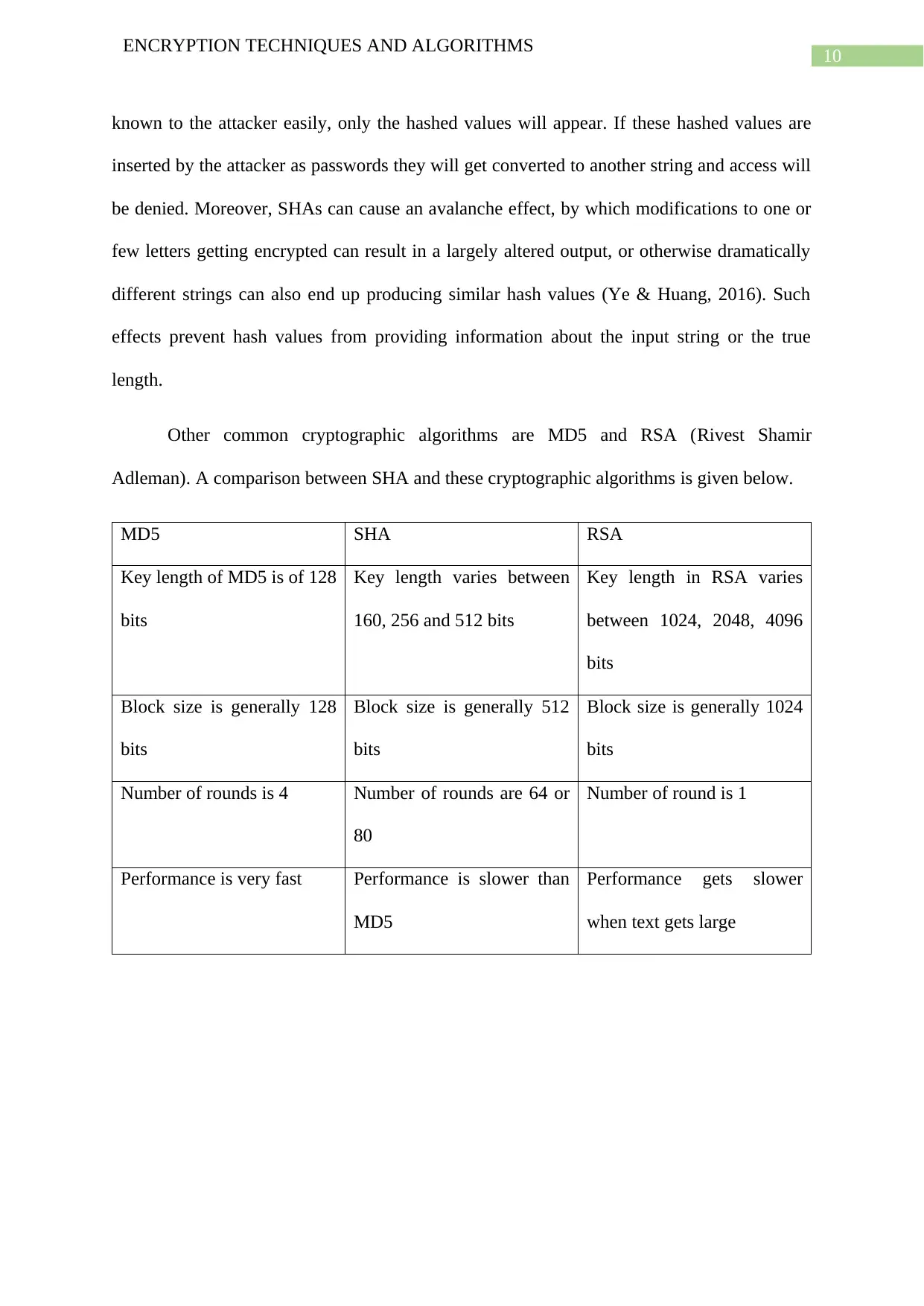
Other common cryptographic algorithms are MD5 and RSA (Rivest Shamir
Adleman). A comparison between SHA and these cryptographic algorithms is given below.
MD5 SHA RSA
Key length of MD5 is of 128
bits
Key length varies between
160, 256 and 512 bits
Key length in RSA varies
between 1024, 2048, 4096
bits
Block size is generally 128
bits
Block size is generally 512
bits
Block size is generally 1024
bits
Number of rounds is 4 Number of rounds are 64 or
80
Number of round is 1
Performance is very fast Performance is slower than
MD5
Performance gets slower
when text gets large
ENCRYPTION TECHNIQUES AND ALGORITHMS
known to the attacker easily, only the hashed values will appear. If these hashed values are
inserted by the attacker as passwords they will get converted to another string and access will
be denied. Moreover, SHAs can cause an avalanche effect, by which modifications to one or
few letters getting encrypted can result in a largely altered output, or otherwise dramatically
different strings can also end up producing similar hash values (Ye & Huang, 2016). Such
effects prevent hash values from providing information about the input string or the true
length.
Other common cryptographic algorithms are MD5 and RSA (Rivest Shamir
Adleman). A comparison between SHA and these cryptographic algorithms is given below.
MD5 SHA RSA
Key length of MD5 is of 128
bits
Key length varies between
160, 256 and 512 bits
Key length in RSA varies
between 1024, 2048, 4096
bits
Block size is generally 128
bits
Block size is generally 512
bits
Block size is generally 1024
bits
Number of rounds is 4 Number of rounds are 64 or
80
Number of round is 1
Performance is very fast Performance is slower than
MD5
Performance gets slower
when text gets large

11
ENCRYPTION TECHNIQUES AND ALGORITHMS
References
Ardy, R. D., Indriani, O. R., Sari, C. A., & Rachmawanto, E. H. (2017, November). Digital
image signature using triple protection cryptosystem (RSA, Vigenere, and MD5).
In 2017 International Conference on Smart Cities, Automation & Intelligent
Computing Systems (ICON-SONICS) (pp. 87-92). IEEE.
Canteaut, A. (2016, April). On the Origin of Trust: Struggle for Secure Cryptography. In Dot
Security 2016.
Das, S., De, S., & Kumar, R. (2016). Implementation and Comparative Analysis of RSA and
MD5 Algorithm. International Journal of Computer Applications, 141(9).
Hwang, T., Luo, Y. P., Gope, P., & Liu, Z. R. (2016, December). Forward/Backward
Unforgeable Digital Signature Scheme Using Symmetric-Key Crypto-System.
In 2016 International Computer Symposium (ICS) (pp. 244-247). IEEE.
Jain, A., Grover, J., & Jain, T. (2018). Cuckoo Search Strategies for Solving Combinatorial
Problems (Solving Substitution Cipher: An Investigation). In Proceedings of First
International Conference on Smart System, Innovations and Computing (pp. 585-
594). Springer, Singapore.
Jones, J. (2016). A Columnar Transposition cipher in a contemporary setting. IACR
Cryptology ePrint Archive, 2016, 5.
Khan, F. H., & Qazi, F. (2018). Advance Procedure Of Encryption And Decryption Using
Transposition And Substitution. Journal of Information Communication Technologies
and Robotic Applications, 43-56.
Lasry, G., Kopal, N., & Wacker, A. (2016). Cryptanalysis of columnar transposition cipher
with long keys. Cryptologia, 40(4), 374-398.
ENCRYPTION TECHNIQUES AND ALGORITHMS
References
Ardy, R. D., Indriani, O. R., Sari, C. A., & Rachmawanto, E. H. (2017, November). Digital
image signature using triple protection cryptosystem (RSA, Vigenere, and MD5).
In 2017 International Conference on Smart Cities, Automation & Intelligent
Computing Systems (ICON-SONICS) (pp. 87-92). IEEE.
Canteaut, A. (2016, April). On the Origin of Trust: Struggle for Secure Cryptography. In Dot
Security 2016.
Das, S., De, S., & Kumar, R. (2016). Implementation and Comparative Analysis of RSA and
MD5 Algorithm. International Journal of Computer Applications, 141(9).
Hwang, T., Luo, Y. P., Gope, P., & Liu, Z. R. (2016, December). Forward/Backward
Unforgeable Digital Signature Scheme Using Symmetric-Key Crypto-System.
In 2016 International Computer Symposium (ICS) (pp. 244-247). IEEE.
Jain, A., Grover, J., & Jain, T. (2018). Cuckoo Search Strategies for Solving Combinatorial
Problems (Solving Substitution Cipher: An Investigation). In Proceedings of First
International Conference on Smart System, Innovations and Computing (pp. 585-
594). Springer, Singapore.
Jones, J. (2016). A Columnar Transposition cipher in a contemporary setting. IACR
Cryptology ePrint Archive, 2016, 5.
Khan, F. H., & Qazi, F. (2018). Advance Procedure Of Encryption And Decryption Using
Transposition And Substitution. Journal of Information Communication Technologies
and Robotic Applications, 43-56.
Lasry, G., Kopal, N., & Wacker, A. (2016). Cryptanalysis of columnar transposition cipher
with long keys. Cryptologia, 40(4), 374-398.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




