Enterprise Information Architecture for eVoting in Australia
VerifiedAdded on 2023/05/28
|14
|3700
|371
AI Summary
This report discusses the benefits of Enterprise Information Architecture for eVoting in Australia and how it can improve the electoral process. It also talks about the challenges faced during implementation and the proposed strategy to meet the requirements.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Data System & Integration
Student Details
12/5/2018
Student Details
12/5/2018
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

eVoting
Executive Summary
Today, organisations have become greater information based totally whether or not it's far
non-public employer or a public sector. To assure their competitiveness, agencies are
making upgrades within the statistics sports on their pinnacle most priorities. Key technique
which will obtain these enhancements is developing Enterprise Information Architecture
(EIA). For any democratic system, voting is a vital element. In 2013, throughout the elections
in Australia, 1370 ballots got missed and taken into consideration as the largest failure of
Australian Electoral commission (AEC) in the history. To re-run the Senate election in
Australia, it cost around $21 million to the country and changed into considered as the
unparalleled harm to the popularity of AEC. The Joint standing Committee on Electoral
topics was given the investigation for missing poll slips. In its research, committee found
that poll slips have been missed due to the physical transportation of poll slips to the
counting centre in Perth. The committee handed over a document to the AEC that consist of
24 suggestions so as to enhance the present electoral process and to keep away from such
leave out happenings in future. One recommendation out of all is the usage of the digital
vote casting gadget in preference to poll slips system. Therefore, with using organisation
records structure, this document will speak at the reference architecture that may be
carried out in Australia for conducting election. EIA approach benefits of mobility, security
and reliability, cost effectiveness, and increased participation of citizens.
Student Details i
Executive Summary
Today, organisations have become greater information based totally whether or not it's far
non-public employer or a public sector. To assure their competitiveness, agencies are
making upgrades within the statistics sports on their pinnacle most priorities. Key technique
which will obtain these enhancements is developing Enterprise Information Architecture
(EIA). For any democratic system, voting is a vital element. In 2013, throughout the elections
in Australia, 1370 ballots got missed and taken into consideration as the largest failure of
Australian Electoral commission (AEC) in the history. To re-run the Senate election in
Australia, it cost around $21 million to the country and changed into considered as the
unparalleled harm to the popularity of AEC. The Joint standing Committee on Electoral
topics was given the investigation for missing poll slips. In its research, committee found
that poll slips have been missed due to the physical transportation of poll slips to the
counting centre in Perth. The committee handed over a document to the AEC that consist of
24 suggestions so as to enhance the present electoral process and to keep away from such
leave out happenings in future. One recommendation out of all is the usage of the digital
vote casting gadget in preference to poll slips system. Therefore, with using organisation
records structure, this document will speak at the reference architecture that may be
carried out in Australia for conducting election. EIA approach benefits of mobility, security
and reliability, cost effectiveness, and increased participation of citizens.
Student Details i

eVoting
Contents
Executive Summary....................................................................................................................1
Introduction...............................................................................................................................3
An Enterprise Information Architecture for eVoting.................................................................3
Information Management and Integration..............................................................................10
Conclusion................................................................................................................................12
References................................................................................................................................13
Student Details ii
Contents
Executive Summary....................................................................................................................1
Introduction...............................................................................................................................3
An Enterprise Information Architecture for eVoting.................................................................3
Information Management and Integration..............................................................................10
Conclusion................................................................................................................................12
References................................................................................................................................13
Student Details ii

eVoting
1.0 Introduction
Around 1400 ballots got missed in 2013, during the elections in Australia. This resulted in
the re-run of elections in the nation which cost around $21 million and was considered as
damage for the reputation of Australian Electoral Commission (AEC) (Poloni, 2015). The
entire investigation regarding the ballot missing was carried out by the Joint Standing
Committee on Electoral Matters and in its investigation it was founded that the reason
behind the missing of ballot slips is the physical transportation of ballot slips to the counting
centre in Perth. To rectify the problems that are faced during the election, the committee
suggested 24 recommendations to the AEC in its report (Connolly, 2004). This report
consists of several improvement procedures that can be implemented to improve the
existing election procedure and for avoiding such miss happenings in the future. One
recommendation by the committee was implementation of electronic voting system. Today,
almost every organization is becoming information based and hence, in order to achieve
these improvements organizations are developing Enterprise Information Architecture
2.0 An Enterprise Information Architecture for eVoting
Today, enterprises are becoming more information based whether it is private organization
or a public sector. To assure their competitiveness, organizations are making improvements
in the information activities on their top most priorities. Key approach in order to achieve
these improvements is developing an Enterprise Information Architecture (EIA) (Techopedia,
2018). For any democratic process, voting is a critical component. In 2013, during the
elections in Australia, 1370 ballots got missed and it was considered as the biggest failure of
Australian Electoral Commission (AEC) in the history. To re-run the Senate election in
Australia, it cost around $21 million to the country and was considered as the
unprecedented damage to the reputation of AEC (Ayo et al., 2011). The Joint Standing
Committee on Electoral Matters was given the investigation for missing ballot slips. In its
investigation committee found that ballot slips were missed due to the physical
transportation of ballot slips to the counting centre in Perth. The committee handed over a
report to the AEC that consist of 24 recommendations in order to improve the existing
electoral process and to avoid such miss happenings in future. One recommendation out of
all is using the electronic voting system instead of ballot slips system. Therefore, with the
use of enterprise information architecture, this report will discuss on the reference
architecture that can be implemented in Australia for conducting lection in the country
(Matters, 2014).
There is a long list of benefits that EIA RA approach can provide in developing a system for
electronic voting. An EIA provides framework for planning and implementing a standard
based, rich, digital information infrastructure with well integrated activities and services.
These benefits are as below:
Mobility: with the use of enterprise information architecture, such a system can be
developed for the electronic voting where people are allowed to cast their vote from
anywhere in the world. It allows location independent method for casting their vote
with the help of internet.
Student Details iii
1.0 Introduction
Around 1400 ballots got missed in 2013, during the elections in Australia. This resulted in
the re-run of elections in the nation which cost around $21 million and was considered as
damage for the reputation of Australian Electoral Commission (AEC) (Poloni, 2015). The
entire investigation regarding the ballot missing was carried out by the Joint Standing
Committee on Electoral Matters and in its investigation it was founded that the reason
behind the missing of ballot slips is the physical transportation of ballot slips to the counting
centre in Perth. To rectify the problems that are faced during the election, the committee
suggested 24 recommendations to the AEC in its report (Connolly, 2004). This report
consists of several improvement procedures that can be implemented to improve the
existing election procedure and for avoiding such miss happenings in the future. One
recommendation by the committee was implementation of electronic voting system. Today,
almost every organization is becoming information based and hence, in order to achieve
these improvements organizations are developing Enterprise Information Architecture
2.0 An Enterprise Information Architecture for eVoting
Today, enterprises are becoming more information based whether it is private organization
or a public sector. To assure their competitiveness, organizations are making improvements
in the information activities on their top most priorities. Key approach in order to achieve
these improvements is developing an Enterprise Information Architecture (EIA) (Techopedia,
2018). For any democratic process, voting is a critical component. In 2013, during the
elections in Australia, 1370 ballots got missed and it was considered as the biggest failure of
Australian Electoral Commission (AEC) in the history. To re-run the Senate election in
Australia, it cost around $21 million to the country and was considered as the
unprecedented damage to the reputation of AEC (Ayo et al., 2011). The Joint Standing
Committee on Electoral Matters was given the investigation for missing ballot slips. In its
investigation committee found that ballot slips were missed due to the physical
transportation of ballot slips to the counting centre in Perth. The committee handed over a
report to the AEC that consist of 24 recommendations in order to improve the existing
electoral process and to avoid such miss happenings in future. One recommendation out of
all is using the electronic voting system instead of ballot slips system. Therefore, with the
use of enterprise information architecture, this report will discuss on the reference
architecture that can be implemented in Australia for conducting lection in the country
(Matters, 2014).
There is a long list of benefits that EIA RA approach can provide in developing a system for
electronic voting. An EIA provides framework for planning and implementing a standard
based, rich, digital information infrastructure with well integrated activities and services.
These benefits are as below:
Mobility: with the use of enterprise information architecture, such a system can be
developed for the electronic voting where people are allowed to cast their vote from
anywhere in the world. It allows location independent method for casting their vote
with the help of internet.
Student Details iii
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

eVoting
Security and Reliability: Reference architecture for electronic voting can be
developed using the cloud computing technology. Cloud has the capability of
analysing a large amount of data. It can easily detect any kind of redundancy and
discrepancy. Enhanced security in cloud computing is mainly due to the universal
architecture and centralization of data. Cloud provides mechanism for the reliability
and the security of data by comparing the voters’ Unique Identification (UID) number
from the database with the voter, and also collects and counts the votes in the data
centre of Australian Electoral Commission (Achieng & Ruhode, 2013).
Economies of Scale and Cost Effectiveness: Regardless of the deployment model,
cloud implementation tends to be as large as possible to benefit from economies of
scale. In order to lower the cost, large cloud deployments are mainly located near
the cheap power stations.
Increased Citizen Participation: Citizen’s participation can be increased using the
electronic voting system. As voters will get the facility of casting their vote from
anywhere and at any time, this will provide them an easy of casting their vote (Aph,
2012).
To elaborate the benefits of enterprise information architecture reference architecture,
below a proposed model that can be developed using the cloud computing technology. This
model allows user to interact with the election commission with the help of clouds (Ayo et
al., 2011).
Source: (Okediran, 2015)
This model clearly provides the flexibility and mobility to the citizens’ as they can easily
register and cast their vote from anywhere and anytime. It is also providing the benefit of
restoring and backup for the user data and the casted votes. Below is the logical
architecture of the electronic voting (Frankland et al., 2011).
Student Details iv
Voter UID Database
Security and Reliability: Reference architecture for electronic voting can be
developed using the cloud computing technology. Cloud has the capability of
analysing a large amount of data. It can easily detect any kind of redundancy and
discrepancy. Enhanced security in cloud computing is mainly due to the universal
architecture and centralization of data. Cloud provides mechanism for the reliability
and the security of data by comparing the voters’ Unique Identification (UID) number
from the database with the voter, and also collects and counts the votes in the data
centre of Australian Electoral Commission (Achieng & Ruhode, 2013).
Economies of Scale and Cost Effectiveness: Regardless of the deployment model,
cloud implementation tends to be as large as possible to benefit from economies of
scale. In order to lower the cost, large cloud deployments are mainly located near
the cheap power stations.
Increased Citizen Participation: Citizen’s participation can be increased using the
electronic voting system. As voters will get the facility of casting their vote from
anywhere and at any time, this will provide them an easy of casting their vote (Aph,
2012).
To elaborate the benefits of enterprise information architecture reference architecture,
below a proposed model that can be developed using the cloud computing technology. This
model allows user to interact with the election commission with the help of clouds (Ayo et
al., 2011).
Source: (Okediran, 2015)
This model clearly provides the flexibility and mobility to the citizens’ as they can easily
register and cast their vote from anywhere and anytime. It is also providing the benefit of
restoring and backup for the user data and the casted votes. Below is the logical
architecture of the electronic voting (Frankland et al., 2011).
Student Details iv
Voter UID Database
eVoting
eVote Administration
Admin client
Key Management
KMS
eVote Counting
Cleanse Mix Count
DIFI
MinID
Internet
Voter
ER
ER import
AIRGAPPED
AIRGAPPED
Config EML
110
230
630
Counts
EML
510
Counts
LOG
EML
+
ER
LOG
SMS
Return Codes
Return Code
Generator Create Ret
Code
LOG
SMS Gateway
RCG DB
Phone Number
Return Codes
Electronic Voting
Vote Collector
Server
LOG
Applet - User Interface
eVote DB
Authentication Service
Receipts
import
Ballot Box
import
ER check
Voter Authentication
(SAML)
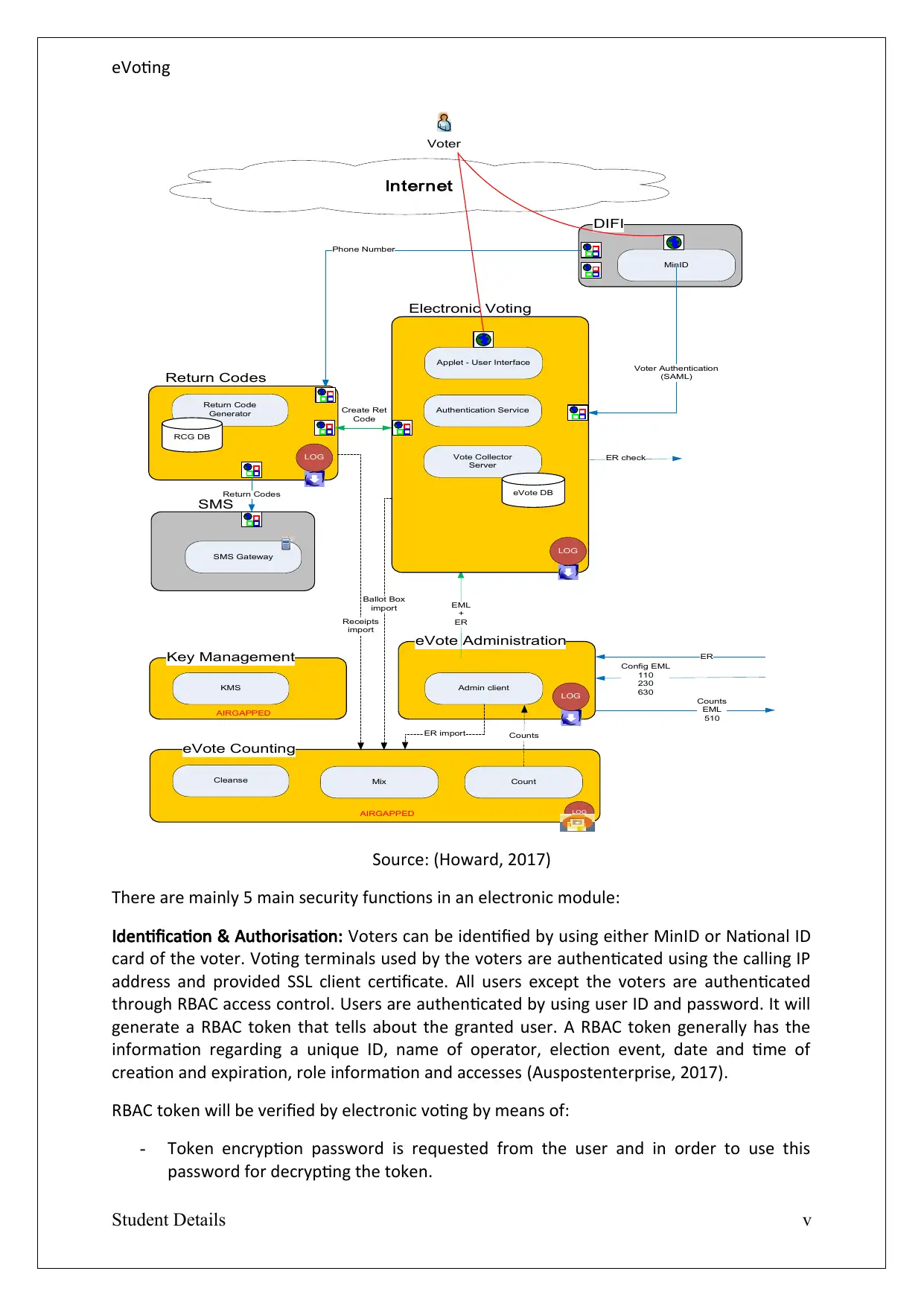
Source: (Howard, 2017)
There are mainly 5 main security functions in an electronic module:
Identification & Authorisation: Voters can be identified by using either MinID or National ID
card of the voter. Voting terminals used by the voters are authenticated using the calling IP
address and provided SSL client certificate. All users except the voters are authenticated
through RBAC access control. Users are authenticated by using user ID and password. It will
generate a RBAC token that tells about the granted user. A RBAC token generally has the
information regarding a unique ID, name of operator, election event, date and time of
creation and expiration, role information and accesses (Auspostenterprise, 2017).
RBAC token will be verified by electronic voting by means of:
- Token encryption password is requested from the user and in order to use this
password for decrypting the token.
Student Details v
eVote Administration
Admin client
Key Management
KMS
eVote Counting
Cleanse Mix Count
DIFI
MinID
Internet
Voter
ER
ER import
AIRGAPPED
AIRGAPPED
Config EML
110
230
630
Counts
EML
510
Counts
LOG
EML
+
ER
LOG
SMS
Return Codes
Return Code
Generator Create Ret
Code
LOG
SMS Gateway
RCG DB
Phone Number
Return Codes
Electronic Voting
Vote Collector
Server
LOG
Applet - User Interface
eVote DB
Authentication Service
Receipts
import
Ballot Box
import
ER check
Voter Authentication
(SAML)
Source: (Howard, 2017)
There are mainly 5 main security functions in an electronic module:
Identification & Authorisation: Voters can be identified by using either MinID or National ID
card of the voter. Voting terminals used by the voters are authenticated using the calling IP
address and provided SSL client certificate. All users except the voters are authenticated
through RBAC access control. Users are authenticated by using user ID and password. It will
generate a RBAC token that tells about the granted user. A RBAC token generally has the
information regarding a unique ID, name of operator, election event, date and time of
creation and expiration, role information and accesses (Auspostenterprise, 2017).
RBAC token will be verified by electronic voting by means of:
- Token encryption password is requested from the user and in order to use this
password for decrypting the token.
Student Details v

eVoting
- Verification of RBAC digital signature.
- Checking the validity of RBAC digital certificate that is used for verifying the
signature.
- Verification of election event.
- Verification of creation time that is not in future.
- Verification of expiration time that is not in the past.
Authorisations are of two types which include authorisation of voter for eVoting and
authorisation of election officials, auditors, and members of electoral board.
Authorisation of voters is checked through checking the eligibility of voter. Authentication
server checks the eligibility of voter by receiving an authentication token and verifying the
information in the authentication token like digital signature and certificate, unique ID, and
expiration time (Connolly, 2004). Authentication server then extracts the ID of voter from
the identification token and then sends the voter ID to the electoral roll service and request
to verify the voter. Once the voter’s eligibility is verified, then the server will perform the
authorisation verification for the voter. Voter’s authorisation is verified three times. First
verification is performed in the VCS when a vote is received from the voter. Second
verification is done in the RCG when a vote is received from the VCS, and third verification is
performed in the cleansing component when whole ballot is verified (Gibson et al., 2010).
Process Integrity and Accuracy: Vote casting, safe storing of votes, processing and counting
of votes is done by the Electronic Voting Software. Elections are critical task and voter and
polling confidentiality and polling integrity need to be protected. To manage and protect the
security of process, there are three information flows are defined: Election Management,
Voting Process, and the Tallying Process (Poloni, 2015).
Cryptographic Support: Every critical operation and the information asset are protected
using a cryptographic mechanism that ensures the confidentiality of information, integrity,
and the authenticity (Okediran, 2015).
Security Audit: All the components of eVoting system send a copy of the logs to the audit
system. It is done because if any component or the system is broken, a copy of the log is
always accessible (Sambo & Alexander, 2018).
Student Details vi
- Verification of RBAC digital signature.
- Checking the validity of RBAC digital certificate that is used for verifying the
signature.
- Verification of election event.
- Verification of creation time that is not in future.
- Verification of expiration time that is not in the past.
Authorisations are of two types which include authorisation of voter for eVoting and
authorisation of election officials, auditors, and members of electoral board.
Authorisation of voters is checked through checking the eligibility of voter. Authentication
server checks the eligibility of voter by receiving an authentication token and verifying the
information in the authentication token like digital signature and certificate, unique ID, and
expiration time (Connolly, 2004). Authentication server then extracts the ID of voter from
the identification token and then sends the voter ID to the electoral roll service and request
to verify the voter. Once the voter’s eligibility is verified, then the server will perform the
authorisation verification for the voter. Voter’s authorisation is verified three times. First
verification is performed in the VCS when a vote is received from the voter. Second
verification is done in the RCG when a vote is received from the VCS, and third verification is
performed in the cleansing component when whole ballot is verified (Gibson et al., 2010).
Process Integrity and Accuracy: Vote casting, safe storing of votes, processing and counting
of votes is done by the Electronic Voting Software. Elections are critical task and voter and
polling confidentiality and polling integrity need to be protected. To manage and protect the
security of process, there are three information flows are defined: Election Management,
Voting Process, and the Tallying Process (Poloni, 2015).
Cryptographic Support: Every critical operation and the information asset are protected
using a cryptographic mechanism that ensures the confidentiality of information, integrity,
and the authenticity (Okediran, 2015).
Security Audit: All the components of eVoting system send a copy of the logs to the audit
system. It is done because if any component or the system is broken, a copy of the log is
always accessible (Sambo & Alexander, 2018).
Student Details vi
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

eVoting
Source: (Darwish & El-Gendy, 2017)
This model consists of three phases that are first is pre-election phase, second is election
phase and the third is post-election phase.
Pre-election phase allows the citizens or the voters to get them registered with the electoral
commission. Here people with the help of electronic gadgets and internet, register them on
the electoral commission database. Information stored in the database is sent to the central
server and stored there forever for the future use (Howard, 2017).
Election phase consist of three steps which include login, authentication, and vote casting.
Voter is first requires to login on the website of the electoral commission. After login,
system authenticates the user by matching the voter information in the database and if the
user is authenticate then allows the voter to cast his/ her vote. His vote is again stored in
the database and further sent to the central server (Lauer, 2004).
Post-election phase consist of counting of votes. It requires login of the administration to
get access on the portal. After login, vote counting can be done and the result of counting is
displayed and sent to the central server (Frankland et al., 2011).
Student Details vii
Source: (Darwish & El-Gendy, 2017)
This model consists of three phases that are first is pre-election phase, second is election
phase and the third is post-election phase.
Pre-election phase allows the citizens or the voters to get them registered with the electoral
commission. Here people with the help of electronic gadgets and internet, register them on
the electoral commission database. Information stored in the database is sent to the central
server and stored there forever for the future use (Howard, 2017).
Election phase consist of three steps which include login, authentication, and vote casting.
Voter is first requires to login on the website of the electoral commission. After login,
system authenticates the user by matching the voter information in the database and if the
user is authenticate then allows the voter to cast his/ her vote. His vote is again stored in
the database and further sent to the central server (Lauer, 2004).
Post-election phase consist of counting of votes. It requires login of the administration to
get access on the portal. After login, vote counting can be done and the result of counting is
displayed and sent to the central server (Frankland et al., 2011).
Student Details vii

eVoting
Electronic Voting Process
3.0 Information Management and Integration
Now the implementation of the architecture that is designed above for the eVoting system
is the main challenge. This report is completed this challenge by giving a top-down structure
for requirements (Okediran, 2015). Following are the challenges that are faced during
maintaining requirements for the electronic voting machine are:
1. Information Sources: implementation of electronic machines for the voting requires
various documents containing high level recommendations and principles. Transition
from paper ballot to electronic elections needs compilation of various acts that
regulates elections. The integration and retention of the traceability of the actual
machine requirements from these principles becomes an important aspect in order
to guarantee effective management of the requirements (Galliers & Leidner, 2014).
2. Software Configuration: To conduct the various operations like voting, counting, and
many others, it requires management of complex configurations and logical sections
that will allow for the modularized program.
3. Hardware Configuration: Implementation of various hardware devices like PC, LCD
display, BIOS, and Printers is needed.
4. Integrations with Electoral Procedures: New voting machines are required to
compatible with the existing electoral laws. eVoting procedure should be familiar to
the voters and for that it should be as much similar to the manual as possible
(Dhillon, 2015).
5. Denial of Service Attack: In 2003, during the elections in Virginia, it was found that
many voting machines tried to send results at the same time. This created a huge
traffic jam and led to delay in the result declaration for one day. Hence, proper
management of traffic is needed for successfully implementing the electronic
system.
To address the challenges mentioned above, a careful planned strategy that will meet the
requirements is described below:
Student Details viii
Electronic Voting Process
3.0 Information Management and Integration
Now the implementation of the architecture that is designed above for the eVoting system
is the main challenge. This report is completed this challenge by giving a top-down structure
for requirements (Okediran, 2015). Following are the challenges that are faced during
maintaining requirements for the electronic voting machine are:
1. Information Sources: implementation of electronic machines for the voting requires
various documents containing high level recommendations and principles. Transition
from paper ballot to electronic elections needs compilation of various acts that
regulates elections. The integration and retention of the traceability of the actual
machine requirements from these principles becomes an important aspect in order
to guarantee effective management of the requirements (Galliers & Leidner, 2014).
2. Software Configuration: To conduct the various operations like voting, counting, and
many others, it requires management of complex configurations and logical sections
that will allow for the modularized program.
3. Hardware Configuration: Implementation of various hardware devices like PC, LCD
display, BIOS, and Printers is needed.
4. Integrations with Electoral Procedures: New voting machines are required to
compatible with the existing electoral laws. eVoting procedure should be familiar to
the voters and for that it should be as much similar to the manual as possible
(Dhillon, 2015).
5. Denial of Service Attack: In 2003, during the elections in Virginia, it was found that
many voting machines tried to send results at the same time. This created a huge
traffic jam and led to delay in the result declaration for one day. Hence, proper
management of traffic is needed for successfully implementing the electronic
system.
To address the challenges mentioned above, a careful planned strategy that will meet the
requirements is described below:
Student Details viii

eVoting
Information regarding users is mainly collected from the public and government documents.
The Australian laws have given specification for the electronic voting process. Voting
machines designed for the eVoting should be compatible with the laws (Sambo & Alexander,
2018). Principles are the high level requirements that define the boundaries for the
automation and system goals. This includes allowing the user for reviewing his/her choices
before casting the vote. Data associated with voters is collected from the various sources
and stored in the central server. Sources for the data collection include information from
hospitals, from organizations, and from universities. This data is unstructured data and
there would be chances of occurring redundancy which need to be rectified. Structured data
is collected from the governmental documents where each citizen is assigned a unique ID.
To conduct the electronic voting, it requires various software and mechanism for conducting
user login and authentication, exercising votes over the internet, counting of votes and
several others. Developing software and implementing it, will be done by the government
and this process is time consuming as well as expensive too. Main concerns in electronic
voting are system reliability and system security (Sambo & Alexander, 2018). Keeping the
confidentiality of the voting is mandatory in order to protect the democratic right and for
this public and private key cryptography is used for secure the communication between the
two parties. Authentication of the user is also important to identify the eligible voter and for
this unique ID of user is used to confirm the eligible voter. Using digital signatures eliminate
repudiation problem from the electronic voting.
Another concern associated with electronic voting is that government needs to provide
training to the public about the new technology of voting and also to inform about the new
system.
4.0 Conclusion
Therefore, it can be concluded that electronic voting system in Australia will provide several
benefits to the country and will help in eliminating the issues associated with the manual or
ballot paper voting system. After missing of around 1400 ballot slips in 2013 elections, the
Joint Standing Committee found main reason behind missing of ballot slips is physical
transportation of ballot slips to the counting location. Hence, committee suggested
Australian Electoral Commission to conduct the election process using technology that is
electronic voting. Enterprise Information Architecture plays vital role in every organization
for developing reference architectures for conducting the business activities and doing the
business with ease. In this paper, a proposed model is described which can be used for
conducting the electronic voting by using cloud technology with the help of internet.
Implementation of electronic voting system has several issues like collecting information
about the voters and preparing a database of the user, implementation of different software
and hardware configuration, and several others. In addition to that there are many other
issues related to the system reliability and system security. Three phases are important in
electronic voting that is pre-election phase, election phase, and the post-election phase.
Pre-election phase includes registering voters on the website of election commission and
creating a database of the voter. This provides user access to the portal to cast his vote.
Only eligible voters are registered. During election, users login at the portal and provide the
required details for verifying the eligible voter. System server verifies the user by matching
the details with the stored data and provides access only to the eligible voter. Post-election
Student Details ix
Information regarding users is mainly collected from the public and government documents.
The Australian laws have given specification for the electronic voting process. Voting
machines designed for the eVoting should be compatible with the laws (Sambo & Alexander,
2018). Principles are the high level requirements that define the boundaries for the
automation and system goals. This includes allowing the user for reviewing his/her choices
before casting the vote. Data associated with voters is collected from the various sources
and stored in the central server. Sources for the data collection include information from
hospitals, from organizations, and from universities. This data is unstructured data and
there would be chances of occurring redundancy which need to be rectified. Structured data
is collected from the governmental documents where each citizen is assigned a unique ID.
To conduct the electronic voting, it requires various software and mechanism for conducting
user login and authentication, exercising votes over the internet, counting of votes and
several others. Developing software and implementing it, will be done by the government
and this process is time consuming as well as expensive too. Main concerns in electronic
voting are system reliability and system security (Sambo & Alexander, 2018). Keeping the
confidentiality of the voting is mandatory in order to protect the democratic right and for
this public and private key cryptography is used for secure the communication between the
two parties. Authentication of the user is also important to identify the eligible voter and for
this unique ID of user is used to confirm the eligible voter. Using digital signatures eliminate
repudiation problem from the electronic voting.
Another concern associated with electronic voting is that government needs to provide
training to the public about the new technology of voting and also to inform about the new
system.
4.0 Conclusion
Therefore, it can be concluded that electronic voting system in Australia will provide several
benefits to the country and will help in eliminating the issues associated with the manual or
ballot paper voting system. After missing of around 1400 ballot slips in 2013 elections, the
Joint Standing Committee found main reason behind missing of ballot slips is physical
transportation of ballot slips to the counting location. Hence, committee suggested
Australian Electoral Commission to conduct the election process using technology that is
electronic voting. Enterprise Information Architecture plays vital role in every organization
for developing reference architectures for conducting the business activities and doing the
business with ease. In this paper, a proposed model is described which can be used for
conducting the electronic voting by using cloud technology with the help of internet.
Implementation of electronic voting system has several issues like collecting information
about the voters and preparing a database of the user, implementation of different software
and hardware configuration, and several others. In addition to that there are many other
issues related to the system reliability and system security. Three phases are important in
electronic voting that is pre-election phase, election phase, and the post-election phase.
Pre-election phase includes registering voters on the website of election commission and
creating a database of the voter. This provides user access to the portal to cast his vote.
Only eligible voters are registered. During election, users login at the portal and provide the
required details for verifying the eligible voter. System server verifies the user by matching
the details with the stored data and provides access only to the eligible voter. Post-election
Student Details ix
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

eVoting
includes vote counting, auditing and the result display. Electronic voting has the advantage
of mobility and gives flexibility to the voters.
5.0 Recommendations
There are few things that must be kept in mind while designing a architecture for the
electronic voting system. Architecture should be simple that can be understood by voters
easily and they can exercise their votes without any problems. Processors should be faster
so that voting errors can be reduced. They must ensure to have a well-structured and
secured cyber security services so that electronic voting data can be kept safe. There should
be some methods where voters can review their votes to make sure they have correctly
voted their votes.
Student Details x
includes vote counting, auditing and the result display. Electronic voting has the advantage
of mobility and gives flexibility to the voters.
5.0 Recommendations
There are few things that must be kept in mind while designing a architecture for the
electronic voting system. Architecture should be simple that can be understood by voters
easily and they can exercise their votes without any problems. Processors should be faster
so that voting errors can be reduced. They must ensure to have a well-structured and
secured cyber security services so that electronic voting data can be kept safe. There should
be some methods where voters can review their votes to make sure they have correctly
voted their votes.
Student Details x

eVoting
References
Achieng, M. & Ruhode, E., 2013. The adoption and challenges of electronic voting
technologies within the South African context.
arXiv preprint arXiv.
Aph, 2012.
e-voting: the promise and the practice. [Online] Available at:
https://www.aph.gov.au/About_Parliament/Parliamentary_Departments/
Parliamentary_Library/pubs/BN/2012-2013/EVoting.
Auspostenterprise, 2017.
eVoting – a new way to have our say. [Online] Available at:
https://auspostenterprise.com.au/content/dam/corp/ent-gov/documents/eVoting-insights-
paper.pdf.
Ayo, C.K., Daramola, J.O. & Azeta, A.A., 2011. Developing a Secure Integrated E-Voting
System.
In Handbook of research on e-services in the public sector: E-Government strategies
and advancements, pp.278-87.
Bouras, C., Katris, N. & Triantafillou, V., 2003. An Electronic Voting Service to Support
Decision-Making in Local Government.
Telematics and Informatics, 20(3), pp.255-74.
Connolly, N., 2004. Issues with Electronic Voting.
Darwish, A. & El-Gendy, M.M., 2017. A New Cryptographic Voting Verifiable Scheme for E-
Voting System Based on Bit Commitment and Blind Signature.
Dhillon, K., 2015.
Challenges for LargeScale Internet Voting Implementations.
Frankland, R., Demire, D., Budurushi, J. & Volkamer, M., 2011. Side-channels and eVoting
machine security.
International Workshop on Requirements Engineering for Electronic.
Student Details xi
References
Achieng, M. & Ruhode, E., 2013. The adoption and challenges of electronic voting
technologies within the South African context.
arXiv preprint arXiv.
Aph, 2012.
e-voting: the promise and the practice. [Online] Available at:
https://www.aph.gov.au/About_Parliament/Parliamentary_Departments/
Parliamentary_Library/pubs/BN/2012-2013/EVoting.
Auspostenterprise, 2017.
eVoting – a new way to have our say. [Online] Available at:
https://auspostenterprise.com.au/content/dam/corp/ent-gov/documents/eVoting-insights-
paper.pdf.
Ayo, C.K., Daramola, J.O. & Azeta, A.A., 2011. Developing a Secure Integrated E-Voting
System.
In Handbook of research on e-services in the public sector: E-Government strategies
and advancements, pp.278-87.
Bouras, C., Katris, N. & Triantafillou, V., 2003. An Electronic Voting Service to Support
Decision-Making in Local Government.
Telematics and Informatics, 20(3), pp.255-74.
Connolly, N., 2004. Issues with Electronic Voting.
Darwish, A. & El-Gendy, M.M., 2017. A New Cryptographic Voting Verifiable Scheme for E-
Voting System Based on Bit Commitment and Blind Signature.
Dhillon, K., 2015.
Challenges for LargeScale Internet Voting Implementations.
Frankland, R., Demire, D., Budurushi, J. & Volkamer, M., 2011. Side-channels and eVoting
machine security.
International Workshop on Requirements Engineering for Electronic.
Student Details xi

eVoting
Galliers, R.D. & Leidner, D.E., 2014.
Strategic information management: challenges and
strategies in managing information systems. Routledge.
Gibson, J.P., Lallet, E. & Raffy, J., 2010. Enginerring Distributed e-Voting System Architecture:
Meeting Critical Requirements. 6150, pp.89-108.
Howard, S., 2017.
How new technology can help solve the eVoting challenge. [Online]
Available at: https://auspostenterprise.com.au/insights/digitising-services/evoting-
technology.
Lauer, T.W., 2004. The Risk of e-Voting.
Electronic Journal of E-government, 2(3), pp.177-86.
Matters, J.S.C.o.E., 2014.
Second Interim Report on the Inquiry into the Conduct of the 2013
Federal Election: An assessment of Electronic Voting Options, Canberra.
Okediran, O., 2015.
Architectural Framework of the Proposed E-voting System. [Online]
Available at: https://www.researchgate.net/figure/Architectural-Framework-of-the-
Proposed-E-voting-System_fig1_284146629.
Okediran, O., 2015.
Sequence Diagram of the Proposed E-voting System. [Online] Available
at: https://www.researchgate.net/figure/Sequence-Diagram-of-the-Proposed-E-voting-
System-scans-the-PVC-and-the-voters_fig2_284146629.
Poloni, G.D., 2015.
Missing Senate ballot boxes may have fallen off a truck, committee finds.
[Online] Available at: https://www.abc.net.au/news/2015-04-15/senate-ballot-boxes-may-
have-fallen-off-truck-committee-finds/6395716.
Sambo, P. & Alexander, P., 2018. A scheme of analysis for e V oting as a technological
innovation system.
The Electronic Journal of Information Systems in Developing Countries,
Student Details xii
Galliers, R.D. & Leidner, D.E., 2014.
Strategic information management: challenges and
strategies in managing information systems. Routledge.
Gibson, J.P., Lallet, E. & Raffy, J., 2010. Enginerring Distributed e-Voting System Architecture:
Meeting Critical Requirements. 6150, pp.89-108.
Howard, S., 2017.
How new technology can help solve the eVoting challenge. [Online]
Available at: https://auspostenterprise.com.au/insights/digitising-services/evoting-
technology.
Lauer, T.W., 2004. The Risk of e-Voting.
Electronic Journal of E-government, 2(3), pp.177-86.
Matters, J.S.C.o.E., 2014.
Second Interim Report on the Inquiry into the Conduct of the 2013
Federal Election: An assessment of Electronic Voting Options, Canberra.
Okediran, O., 2015.
Architectural Framework of the Proposed E-voting System. [Online]
Available at: https://www.researchgate.net/figure/Architectural-Framework-of-the-
Proposed-E-voting-System_fig1_284146629.
Okediran, O., 2015.
Sequence Diagram of the Proposed E-voting System. [Online] Available
at: https://www.researchgate.net/figure/Sequence-Diagram-of-the-Proposed-E-voting-
System-scans-the-PVC-and-the-voters_fig2_284146629.
Poloni, G.D., 2015.
Missing Senate ballot boxes may have fallen off a truck, committee finds.
[Online] Available at: https://www.abc.net.au/news/2015-04-15/senate-ballot-boxes-may-
have-fallen-off-truck-committee-finds/6395716.
Sambo, P. & Alexander, P., 2018. A scheme of analysis for e V oting as a technological
innovation system.
The Electronic Journal of Information Systems in Developing Countries,
Student Details xii
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

eVoting
84(2).
Techopedia, 2018.
Enterprise Information Architecture (EIA). [Online] Available at:
https://www.techopedia.com/definition/30587/enterprise-information-architecture-eia.
Student Details xiii
84(2).
Techopedia, 2018.
Enterprise Information Architecture (EIA). [Online] Available at:
https://www.techopedia.com/definition/30587/enterprise-information-architecture-eia.
Student Details xiii
1 out of 14
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.