Deakin University: Kebin's Music EIM & Security Report
VerifiedAdded on 2023/06/07
|16
|3719
|406
Report
AI Summary
This report provides a comprehensive analysis of Enterprise Information Management and Security for Kebin's Music, a business with two models: music shows and teaching classes. The report includes an Executive Summary outlining the data modeling and cybersecurity management, focusing on the EERD model and SQL codes for accessing operational data. The EERD model accurately represents the generalization and relationships within the business, and the SQL codes demonstrate how to retrieve relevant data. The report addresses internal and external threats, including malware, phishing, SQL injection, cross-site scripting, and denial-of-service attacks. It also covers internal threats like malicious insiders. A probability-impact matrix assesses the risks, and the report proposes risk control measures for each threat. The report concludes with a summary of the findings and references to the sources used.

Running head: ENTERPRISE INFORMATION MANAGEMENT & SECURITY
Enterprise Information Management & Security
Name of the Student
Name of the University
Author’s note
Enterprise Information Management & Security
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ENTERPRISE INFORMATION MANAGEMENT & SECURITY
Executive Summary
The report reflects the data modeling and cyber security management for Kebin’s music system.
Kevin’s music has two business models. The organization books music shows and also schedule
music teaching classes for students. The organization has a rule that minor musicians and
musicians with expired “Working With Children Check” cannot work as a teacher. The EERD
model shows generalization accurately. The model also shows relation between a teacher
teaching in class and students who attend the class. The SQL codes for accessing the operation
related data is provided. The inner join has been used to connect various tables in one query. The
internal, external, deliberate and unintentional threats are properly described in the report.
Executive Summary
The report reflects the data modeling and cyber security management for Kebin’s music system.
Kevin’s music has two business models. The organization books music shows and also schedule
music teaching classes for students. The organization has a rule that minor musicians and
musicians with expired “Working With Children Check” cannot work as a teacher. The EERD
model shows generalization accurately. The model also shows relation between a teacher
teaching in class and students who attend the class. The SQL codes for accessing the operation
related data is provided. The inner join has been used to connect various tables in one query. The
internal, external, deliberate and unintentional threats are properly described in the report.

2ENTERPRISE INFORMATION MANAGEMENT & SECURITY
Table of Contents
Introduction:....................................................................................................................................3
Enhanced Entity Relationship Diagram:.........................................................................................4
SQL Statements:..............................................................................................................................5
System Security and Solutions:.......................................................................................................6
External Threats:..........................................................................................................................6
Internal Threats:...........................................................................................................................8
Probability-Impact Matrix:..........................................................................................................8
Risk Control:..............................................................................................................................10
Conclusion:....................................................................................................................................12
References:....................................................................................................................................13
Table of Contents
Introduction:....................................................................................................................................3
Enhanced Entity Relationship Diagram:.........................................................................................4
SQL Statements:..............................................................................................................................5
System Security and Solutions:.......................................................................................................6
External Threats:..........................................................................................................................6
Internal Threats:...........................................................................................................................8
Probability-Impact Matrix:..........................................................................................................8
Risk Control:..............................................................................................................................10
Conclusion:....................................................................................................................................12
References:....................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ENTERPRISE INFORMATION MANAGEMENT & SECURITY
Introduction:
The ICT system is configured and installed using the software, hardware, information and
human resource. The human resource are the users of the system. As the main focus of an ICT
system is collection, processing and distribution of data, a database is considered to be one of the
most significant parts of ICT. The database is created based on the modeling done in the design
phase. The EERD is the logical model of database, to be implemented. The ORACLE is the
platform where the database can be developed and queries can be run.
The report is generated based on the case study of Kevin’s Music Business. The
organization runs two kinds of businesses. One is arranging live music in various venues and
running a music teaching school. The reports consist of the EERD, SQL queries to show
business process related outputs and six threats and solutions to those threats.
Introduction:
The ICT system is configured and installed using the software, hardware, information and
human resource. The human resource are the users of the system. As the main focus of an ICT
system is collection, processing and distribution of data, a database is considered to be one of the
most significant parts of ICT. The database is created based on the modeling done in the design
phase. The EERD is the logical model of database, to be implemented. The ORACLE is the
platform where the database can be developed and queries can be run.
The report is generated based on the case study of Kevin’s Music Business. The
organization runs two kinds of businesses. One is arranging live music in various venues and
running a music teaching school. The reports consist of the EERD, SQL queries to show
business process related outputs and six threats and solutions to those threats.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ENTERPRISE INFORMATION MANAGEMENT & SECURITY
Enhanced Entity Relationship Diagram:
Figure 1: Enhanced Entity Relationship Diagram
(Source: Created by Author)
The proposed ERD in the figure 1 illustrates the data model of Kevin’s Music. The
organization has registered musicians who performs in venues. A musician can be part of a band
or work alone. The band has a manager. It is assumed that a manager can leave current band and
join another. In case a registered band employs new manager, the database will not delete the
manager data as he/she may join another band, registered in the system. The musicians can have
Enhanced Entity Relationship Diagram:
Figure 1: Enhanced Entity Relationship Diagram
(Source: Created by Author)
The proposed ERD in the figure 1 illustrates the data model of Kevin’s Music. The
organization has registered musicians who performs in venues. A musician can be part of a band
or work alone. The band has a manager. It is assumed that a manager can leave current band and
join another. In case a registered band employs new manager, the database will not delete the
manager data as he/she may join another band, registered in the system. The musicians can have

5ENTERPRISE INFORMATION MANAGEMENT & SECURITY
“Working with Children Check” card. The database will record the expiry date of the card. If the
musician does not have a card or it has expired then the musician cannot work as a teacher. The
musician and band will perform at a program which will be held at a particular venue. It is
assumed that a venue can handle various programs. The teacher will teach at class that will have
different lessons. Each lessons are of a particular style of music. The students can apply for
different lessons. The database will store only those application names who has applied for a
lesson. A lesson can exist in the database even if no one has applied for it. An applicant can
submit many applications. A student can attend lesson after he/she is registered.
SQL Statements:
Condition 1: Count of all new students who have joined Kevin's music after the 1st of
July 2018.
Statement 1 Count(studentID) From Student Where joiningDate =
TO_DATE('01/07/2018', 'DD/MM/YYYY')
Condition 2: List of all underage male musicians and their age sorted by the first name.
Statement 2 select firstName, lastName, age from Musician Where age <18 Order By
firstName DESC
Condition 3: List of all teachers who have an expired Working With Children Check
(WWCC), with names, expiry date and their age, sorted by date.
Statement3 select firstName, lastName, age, expiryDate from Musician inner join Card
on Musician.musicianID = Card.musicianID Where expiryDate < TO_CHAR (SYSDATE, 'DD-
MON-YYYY')
“Working with Children Check” card. The database will record the expiry date of the card. If the
musician does not have a card or it has expired then the musician cannot work as a teacher. The
musician and band will perform at a program which will be held at a particular venue. It is
assumed that a venue can handle various programs. The teacher will teach at class that will have
different lessons. Each lessons are of a particular style of music. The students can apply for
different lessons. The database will store only those application names who has applied for a
lesson. A lesson can exist in the database even if no one has applied for it. An applicant can
submit many applications. A student can attend lesson after he/she is registered.
SQL Statements:
Condition 1: Count of all new students who have joined Kevin's music after the 1st of
July 2018.
Statement 1 Count(studentID) From Student Where joiningDate =
TO_DATE('01/07/2018', 'DD/MM/YYYY')
Condition 2: List of all underage male musicians and their age sorted by the first name.
Statement 2 select firstName, lastName, age from Musician Where age <18 Order By
firstName DESC
Condition 3: List of all teachers who have an expired Working With Children Check
(WWCC), with names, expiry date and their age, sorted by date.
Statement3 select firstName, lastName, age, expiryDate from Musician inner join Card
on Musician.musicianID = Card.musicianID Where expiryDate < TO_CHAR (SYSDATE, 'DD-
MON-YYYY')
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ENTERPRISE INFORMATION MANAGEMENT & SECURITY
Condition 4: List of all current lesson bookings sorted by the style of music and the
booking date
Statement 4 select AP.name, applicationDate, StyleOfMusic.name From Applicant AP
inner join Application on Applicant.applicantID = Application.applicantID inner join Lesson on
Application.lessionID = Lesson.lessonID inner join StyleOfMusic on Lesson.styleID =
StyleOfMusic.styleID Where status = ‘pending’ Order By applicationDate DESC
Condition 5: A report on the students enrolled, the style of music and the teacher for the
current calendar month
Statement 5 select Student.name, StyleOfMusic.name From Student inner join Lesson
on Student.lessonID = Lesson.lessonID inner join Class on Lesson.lessionID = Class.lessonID
inner join Teacher on Class.teacherID = Teacher.teacherID inner join StyleOfMusic on
Lesson.styleID = StyleOfMusic.styleID Where Class.Month= TO_CHAR (SYSDATE, 'MON')
System Security and Solutions:
External Threats:
Malware: The malware is released into the system of the user when he clicks on an
antivirus alter pop-up screen in browser or clicked on mail attachment that is malisons. The
malware is very intriguing tool for attackers to gain access to the victims personal or office
computer. The ransomware and viruses can be put in the categories of malware. It is originally a
harmful application. Once the malware enters victim’s commuter it can manipulate the
computer’s processes to sending confidential data to hackers and monitoring the activities of the
victim.
Condition 4: List of all current lesson bookings sorted by the style of music and the
booking date
Statement 4 select AP.name, applicationDate, StyleOfMusic.name From Applicant AP
inner join Application on Applicant.applicantID = Application.applicantID inner join Lesson on
Application.lessionID = Lesson.lessonID inner join StyleOfMusic on Lesson.styleID =
StyleOfMusic.styleID Where status = ‘pending’ Order By applicationDate DESC
Condition 5: A report on the students enrolled, the style of music and the teacher for the
current calendar month
Statement 5 select Student.name, StyleOfMusic.name From Student inner join Lesson
on Student.lessonID = Lesson.lessonID inner join Class on Lesson.lessionID = Class.lessonID
inner join Teacher on Class.teacherID = Teacher.teacherID inner join StyleOfMusic on
Lesson.styleID = StyleOfMusic.styleID Where Class.Month= TO_CHAR (SYSDATE, 'MON')
System Security and Solutions:
External Threats:
Malware: The malware is released into the system of the user when he clicks on an
antivirus alter pop-up screen in browser or clicked on mail attachment that is malisons. The
malware is very intriguing tool for attackers to gain access to the victims personal or office
computer. The ransomware and viruses can be put in the categories of malware. It is originally a
harmful application. Once the malware enters victim’s commuter it can manipulate the
computer’s processes to sending confidential data to hackers and monitoring the activities of the
victim.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ENTERPRISE INFORMATION MANAGEMENT & SECURITY
Phishing: The phishing technique is used to trick the user. It is pretty obvious that a
person would not open a random mail. For that reason, the cyber attackers use mail contents that
user is familiar with. Using the similar mail names or websites, the attackers disguise as someone
else, the phasing attack is completed. The user thinks that he/she is accessing an authentic mail
or website and allow system privilege to the attacker.
SQL Injection Attack: The SQL is the abbreviation of Structured Query Language. This
language establishes connection between client-side script and database. Various servers use the
SQL language to store and retrieve critical data coming to-and-fro web application. These kind
of application and servers are the victim of the SQL injection attack. The attack initiates by
identifying the SQL code vulnerabilities and inject malicious code in the server.
Cross-Site Scripting: The cross-site scripting is used to attack the users of the website
instead of attacking the vulnerable SQL codes. In this attack also, the malicious codes are
injected into the website. The cross-site scripting only affects client side. Other users of the
website who are not a victim of cross-site scripting will experience unaffected website. In cross-
site scripting, the malicious code is injected into the script or comment that runs automatically.
The cross-site scripting is able to put the user information at risk without even letting the user or
the server know.
Denial-of-Service: The Denial-of-Service or DoS attack is the most severe attack of all.
This attack is capable of brining a whole server down and stop communication between user side
and server side. The DDoS or Distributive Denial-of-Service attack is more severe than DoS.
The DoS or DDoS attack sends more request to the server than it can handle thus original user
requests are not processed by the server and server goes down. The Denial of Service is so bad
Phishing: The phishing technique is used to trick the user. It is pretty obvious that a
person would not open a random mail. For that reason, the cyber attackers use mail contents that
user is familiar with. Using the similar mail names or websites, the attackers disguise as someone
else, the phasing attack is completed. The user thinks that he/she is accessing an authentic mail
or website and allow system privilege to the attacker.
SQL Injection Attack: The SQL is the abbreviation of Structured Query Language. This
language establishes connection between client-side script and database. Various servers use the
SQL language to store and retrieve critical data coming to-and-fro web application. These kind
of application and servers are the victim of the SQL injection attack. The attack initiates by
identifying the SQL code vulnerabilities and inject malicious code in the server.
Cross-Site Scripting: The cross-site scripting is used to attack the users of the website
instead of attacking the vulnerable SQL codes. In this attack also, the malicious codes are
injected into the website. The cross-site scripting only affects client side. Other users of the
website who are not a victim of cross-site scripting will experience unaffected website. In cross-
site scripting, the malicious code is injected into the script or comment that runs automatically.
The cross-site scripting is able to put the user information at risk without even letting the user or
the server know.
Denial-of-Service: The Denial-of-Service or DoS attack is the most severe attack of all.
This attack is capable of brining a whole server down and stop communication between user side
and server side. The DDoS or Distributive Denial-of-Service attack is more severe than DoS.
The DoS or DDoS attack sends more request to the server than it can handle thus original user
requests are not processed by the server and server goes down. The Denial of Service is so bad
8ENTERPRISE INFORMATION MANAGEMENT & SECURITY
that it cannot be stopped once it reaches the server. The only thing that can be done is shutting
down all the server machines.
Internal Threats:
Malicious Insider: This kind of insider threat is the most difficult threat to handle. This
threat cannot be easily mitigated using strict protocols or advanced ICT security training. A
malicious insider can be a criminal who disguises as a worker in an organization or any staff who
is willing to harm the employer. An outsider who has the login credentials can easily breach a
network and access crucial business data.
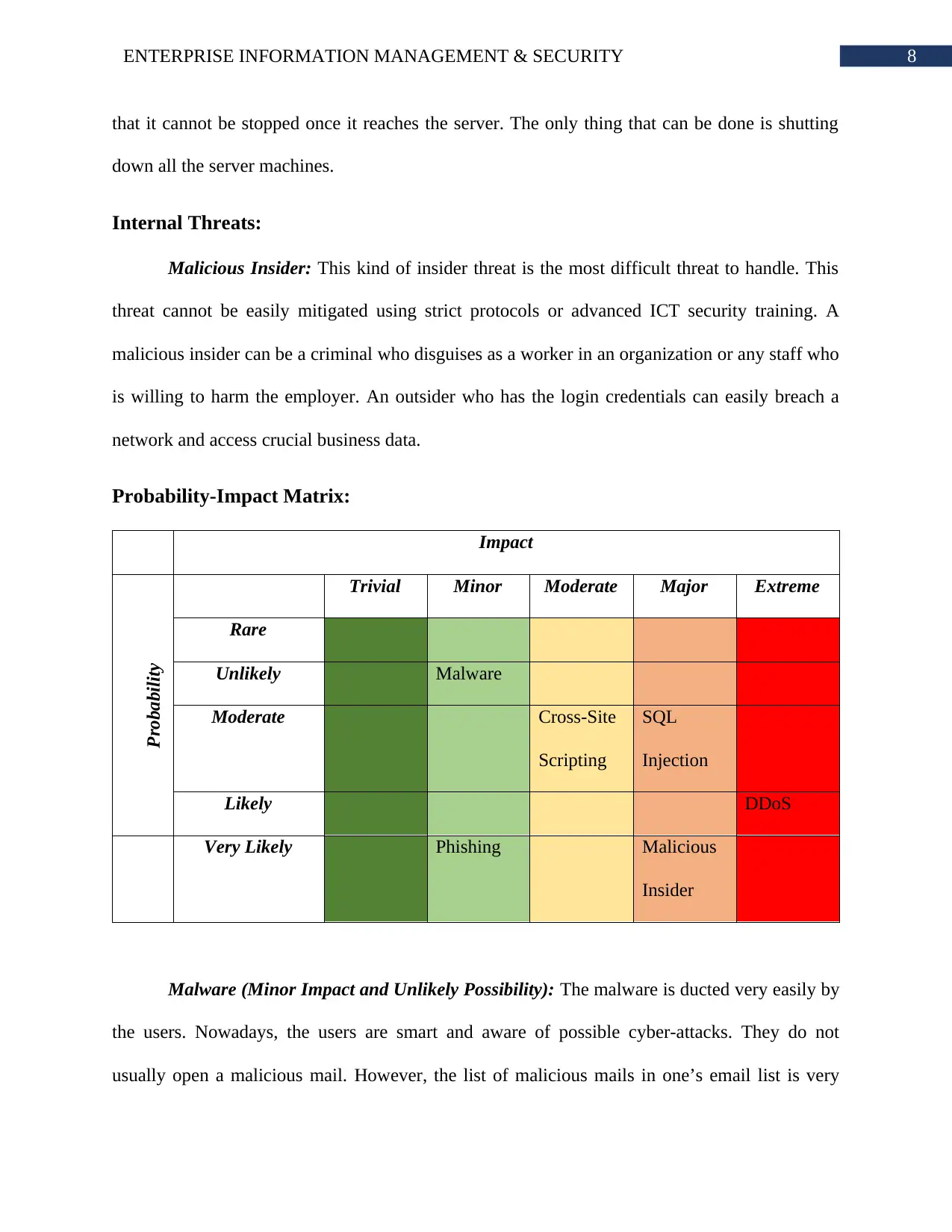
Probability-Impact Matrix:
Impact
Probability
Trivial Minor Moderate Major Extreme
Rare
Unlikely Malware
Moderate Cross-Site
Scripting
SQL
Injection
Likely DDoS
Very Likely Phishing Malicious
Insider
Malware (Minor Impact and Unlikely Possibility): The malware is ducted very easily by
the users. Nowadays, the users are smart and aware of possible cyber-attacks. They do not
usually open a malicious mail. However, the list of malicious mails in one’s email list is very
that it cannot be stopped once it reaches the server. The only thing that can be done is shutting
down all the server machines.
Internal Threats:
Malicious Insider: This kind of insider threat is the most difficult threat to handle. This
threat cannot be easily mitigated using strict protocols or advanced ICT security training. A
malicious insider can be a criminal who disguises as a worker in an organization or any staff who
is willing to harm the employer. An outsider who has the login credentials can easily breach a
network and access crucial business data.
Probability-Impact Matrix:
Impact
Probability
Trivial Minor Moderate Major Extreme
Rare
Unlikely Malware
Moderate Cross-Site
Scripting
SQL
Injection
Likely DDoS
Very Likely Phishing Malicious
Insider
Malware (Minor Impact and Unlikely Possibility): The malware is ducted very easily by
the users. Nowadays, the users are smart and aware of possible cyber-attacks. They do not
usually open a malicious mail. However, the list of malicious mails in one’s email list is very
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ENTERPRISE INFORMATION MANAGEMENT & SECURITY
high. Numerous attackers and vague business persons send malicious mail to thousands of
people. That is why the possibility of getting attacked by a malware is very low.
Phishing (Minor Impact and Very Likely Possibility): The phishing is used to trick a
user. The user may not even notice that he/she is tricked. The phishing has same impact as
malware. The only difference is the access granting process. The possibility is very high as users
often tricked by the attacker. Many users provide the attacker access to their system assuming
that they are using legitimate website or web application.
Cross-Site Scripting (Moderate Possibility and Moderate Impact): The cross-site
scripting is done to within the system of the user. Only the victim user is affected by this attack.
The whole website does not get affected while this attack is in progress. The cross-site scripting
requires good knowledge of website it is attacking. New antiviruses are smart enough to detect
most of the cross-site scripting attacks. Therefore, both the possibility and impact of this attack is
moderate.
SQL Injection Attack (Moderate Possibility and Major Impact): The SQL injection is
used for attacking the web servers that runs SQL codes to collect and share data. Nowadays,
SQL based software production houses are generating new methods to counter this attack. The
use of the SQL is diminishing slowly due to presence of bug data solutions. Thus, the probability
of this attack is moderate. However, if the attack is successfully done on a website server then
the consequences can be very severe. The whole server may lose its valuable data to the attacker.
The attack can be stopped if identified at right time. The impact of this attack is major and can
lead to blundering organization’s reputation.
high. Numerous attackers and vague business persons send malicious mail to thousands of
people. That is why the possibility of getting attacked by a malware is very low.
Phishing (Minor Impact and Very Likely Possibility): The phishing is used to trick a
user. The user may not even notice that he/she is tricked. The phishing has same impact as
malware. The only difference is the access granting process. The possibility is very high as users
often tricked by the attacker. Many users provide the attacker access to their system assuming
that they are using legitimate website or web application.
Cross-Site Scripting (Moderate Possibility and Moderate Impact): The cross-site
scripting is done to within the system of the user. Only the victim user is affected by this attack.
The whole website does not get affected while this attack is in progress. The cross-site scripting
requires good knowledge of website it is attacking. New antiviruses are smart enough to detect
most of the cross-site scripting attacks. Therefore, both the possibility and impact of this attack is
moderate.
SQL Injection Attack (Moderate Possibility and Major Impact): The SQL injection is
used for attacking the web servers that runs SQL codes to collect and share data. Nowadays,
SQL based software production houses are generating new methods to counter this attack. The
use of the SQL is diminishing slowly due to presence of bug data solutions. Thus, the probability
of this attack is moderate. However, if the attack is successfully done on a website server then
the consequences can be very severe. The whole server may lose its valuable data to the attacker.
The attack can be stopped if identified at right time. The impact of this attack is major and can
lead to blundering organization’s reputation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10ENTERPRISE INFORMATION MANAGEMENT & SECURITY
Malicious Insider (Likely Possibility and Extreme Impact): Any employee can be
unhappy due to the organizations behavior to them. Any criminal can get a job in the
organization and use the given access privilege to the system to exploit the system. Malicious
insiders are hard to identify until something harmful happens. There can be numerous reasons for
an employee to become an insider threat. On the other hand, an outsider can get access to the
system using a staff’s login credentials. Thus, the possibility of the attack is extremely high. The
insider threat can reveal organizational data to the competitors without even alerting anyone.
They can inject other threats into the system. The whole system will be exploited from the inside
and stopping it is very hard. Thus, the malicious insider is a major cyber threat to system.
DoS/DDoS (Very Likely Possibility and Major Impact): The DDoS or DoS attacks are
the most dangerous cyber threats. The DDoS or DoS attacks are very hard to convey but the
impact it has on the system is making it more popular. The recent studies states that DDoS is
third highest conveyed attacks. However, the attack is conveyed for big organizations only.
Small organizations may not have sufficient information or resource to fulfill the needs of the
attackers so cost and effort of attack cannot be recovered. For this reason, the DDoS and DoS
attack is of like probability. The attack cannot be stopped if it initiates. The whole organization
would lose connection with the customers. All the sensitive data can be erased from the server.
The huge impact it can have on the system makes it extremely severe. Therefore, the impact of
this threat is extreme.
Risk Control:
Malware: The user must not reply to e-mails that does not seem authentic. The user must
not share any financial or personal information through the mail. The user must not share
password of any web app or desktop app. File attachments of malicious mails often carry
Malicious Insider (Likely Possibility and Extreme Impact): Any employee can be
unhappy due to the organizations behavior to them. Any criminal can get a job in the
organization and use the given access privilege to the system to exploit the system. Malicious
insiders are hard to identify until something harmful happens. There can be numerous reasons for
an employee to become an insider threat. On the other hand, an outsider can get access to the
system using a staff’s login credentials. Thus, the possibility of the attack is extremely high. The
insider threat can reveal organizational data to the competitors without even alerting anyone.
They can inject other threats into the system. The whole system will be exploited from the inside
and stopping it is very hard. Thus, the malicious insider is a major cyber threat to system.
DoS/DDoS (Very Likely Possibility and Major Impact): The DDoS or DoS attacks are
the most dangerous cyber threats. The DDoS or DoS attacks are very hard to convey but the
impact it has on the system is making it more popular. The recent studies states that DDoS is
third highest conveyed attacks. However, the attack is conveyed for big organizations only.
Small organizations may not have sufficient information or resource to fulfill the needs of the
attackers so cost and effort of attack cannot be recovered. For this reason, the DDoS and DoS
attack is of like probability. The attack cannot be stopped if it initiates. The whole organization
would lose connection with the customers. All the sensitive data can be erased from the server.
The huge impact it can have on the system makes it extremely severe. Therefore, the impact of
this threat is extreme.
Risk Control:
Malware: The user must not reply to e-mails that does not seem authentic. The user must
not share any financial or personal information through the mail. The user must not share
password of any web app or desktop app. File attachments of malicious mails often carry

11ENTERPRISE INFORMATION MANAGEMENT & SECURITY
malware. The user must not open any such attachment. Not replying to any suspicious mail will
reduce the chance of malware attack. Installing unauthorized applications can lead to allowing
malware to enter the system. The user must have an enabled firewall so that malicious mail can
be prevented.
Phishing: The organizations must educate the employees about phishing attacks. They
must conduct training for employees. The user can install a SPAM filter that can detect viruses
and disguised mails. The security application installed in the system must be updated so that new
types of phishing attacks can be encountered. Installing antiviruses can lead to reduction in
phishing attack possibility. The organization must implement policies like password expiration,
session expiring and many more. Web filters are highly effective in filtering malicious websites.
Cross-Site Scripting: The system of any organization must be developed by following
security development lifecycle. Validating the input type is a well-known counter measure for
cross-site scripting. The website must not relied on client side scripting, all the data validation
must be carried out in server side.
SQL Injection Attack: For the SQL injection attack also, input validation is a crucial
procedure. The web application firewall must be installed in the server to prevent such attacks.
Insider Threat: The insider threat is deliberate or unintentional threat. The organization
must create policies to prevent the user to access malicious website and install unauthorized
applications. In order to deal with deliberate threat, the server must have a list of website and
other entities that can cause initiate an attack. The authorization level must be planned properly.
DDoS: Scanning the web services frequently has been a great way to prevent low scaled
DDoS attacks. Network assets must be scanned periodically or event better if regularly. An
malware. The user must not open any such attachment. Not replying to any suspicious mail will
reduce the chance of malware attack. Installing unauthorized applications can lead to allowing
malware to enter the system. The user must have an enabled firewall so that malicious mail can
be prevented.
Phishing: The organizations must educate the employees about phishing attacks. They
must conduct training for employees. The user can install a SPAM filter that can detect viruses
and disguised mails. The security application installed in the system must be updated so that new
types of phishing attacks can be encountered. Installing antiviruses can lead to reduction in
phishing attack possibility. The organization must implement policies like password expiration,
session expiring and many more. Web filters are highly effective in filtering malicious websites.
Cross-Site Scripting: The system of any organization must be developed by following
security development lifecycle. Validating the input type is a well-known counter measure for
cross-site scripting. The website must not relied on client side scripting, all the data validation
must be carried out in server side.
SQL Injection Attack: For the SQL injection attack also, input validation is a crucial
procedure. The web application firewall must be installed in the server to prevent such attacks.
Insider Threat: The insider threat is deliberate or unintentional threat. The organization
must create policies to prevent the user to access malicious website and install unauthorized
applications. In order to deal with deliberate threat, the server must have a list of website and
other entities that can cause initiate an attack. The authorization level must be planned properly.
DDoS: Scanning the web services frequently has been a great way to prevent low scaled
DDoS attacks. Network assets must be scanned periodically or event better if regularly. An
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


