Enterprise Security Assignment Report - Stuxnet, Risk Analysis, TOGAF
VerifiedAdded on 2021/09/12
|11
|2209
|18
Report
AI Summary
This report provides a comprehensive analysis of enterprise security, beginning with an explanation of the Stuxnet malware, its impact, and operational mechanisms. It delves into qualitative risk analysis, assessing potential threats and vulnerabilities within a nuclear program context, including the evaluation of safeguards like the S300 and HQ18 missile systems. The report then examines the TOGAF (The Open Group Architecture Framework) standard, its application, and relevant requirements. It concludes with a discussion on the selection of safeguards for nuclear attack protection, considering cost-effectiveness and risk mitigation strategies. The assignment draws upon multiple sources, including academic research papers to support the analysis and findings. The report aims to provide insights into securing enterprise systems, and the application of security frameworks.

Running head: ENTERPRISE SECURITY ASSIGNMENT
Enterprise Security Assignment
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Enterprise Security Assignment
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ENTERPRISE SECURITY ASSIGNMENT
Table of Contents
Introduction......................................................................................................................................2
Explanation of Stuxnet....................................................................................................................2
Qualitative Risk analysis.................................................................................................................3
TOGAF............................................................................................................................................5
Movie Contact.................................................................................................................................6
Conclusion.......................................................................................................................................7
Bibliography....................................................................................................................................8
Table of Contents
Introduction......................................................................................................................................2
Explanation of Stuxnet....................................................................................................................2
Qualitative Risk analysis.................................................................................................................3
TOGAF............................................................................................................................................5
Movie Contact.................................................................................................................................6
Conclusion.......................................................................................................................................7
Bibliography....................................................................................................................................8

2ENTERPRISE SECURITY ASSIGNMENT
Introduction
The architecture for the security consideration would be developed for defining the
management of the successful and effective management of factors. The implication of the
information management had been implied with the successful management process. The
development of the report had been implied for the identifying the implication and listing the
development of the effective management processing. The Stuxnet has been considered for
evaluating the role of the malicious worms and the formation of the effective influence of the
development model.
Explanation of Stuxnet
Stuxnet is one of the most primitive term for the development of the successive
formation management. The malware would form the impact on the exploitation of the factors
for the development of the effective and smart management processing. The multiple windows
would be exhausted and crucified for the management of the successful information
development. The malware was introduced by the Americana and Israeli for targeting the
information of the factors. The analysis would be cohesively factored with the consideration of
the smart factorial development and the significant management processing. The PLC or
program logic controller controlled devices would be affected by the malware Stuxnet. The
automation in PLC is hindered by the malware attacks on the electrochemical process for
forming the major operative setback for the operations. The designing of the software has been
supported by the influence of the programmable logical circuits. The attack on the initial vector
was predominantly influenced by the consideration of the effective management processing.
Introduction
The architecture for the security consideration would be developed for defining the
management of the successful and effective management of factors. The implication of the
information management had been implied with the successful management process. The
development of the report had been implied for the identifying the implication and listing the
development of the effective management processing. The Stuxnet has been considered for
evaluating the role of the malicious worms and the formation of the effective influence of the
development model.
Explanation of Stuxnet
Stuxnet is one of the most primitive term for the development of the successive
formation management. The malware would form the impact on the exploitation of the factors
for the development of the effective and smart management processing. The multiple windows
would be exhausted and crucified for the management of the successful information
development. The malware was introduced by the Americana and Israeli for targeting the
information of the factors. The analysis would be cohesively factored with the consideration of
the smart factorial development and the significant management processing. The PLC or
program logic controller controlled devices would be affected by the malware Stuxnet. The
automation in PLC is hindered by the malware attacks on the electrochemical process for
forming the major operative setback for the operations. The designing of the software has been
supported by the influence of the programmable logical circuits. The attack on the initial vector
was predominantly influenced by the consideration of the effective management processing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ENTERPRISE SECURITY ASSIGNMENT
The OS of the windows has been designed for taking care of the effective alignment
management and it would be formed for inducing the listing of the factor and formation of the
successful development model. The USB environmental management has been implied with the
consideration of the factors and the significant listing of the improved management process. The
USB port environmental management has been implied for taking care of the factors and
implying the significance influence of the developing management. The Stuxnet has been
harmed for specific attack and harm to the system of developing the management activities. The
Stuxnet has been resulting in the exploitation and exhausting of the factors for listing the
management of the activities. The Stuxnet has been resulting in the probable hardware
component management and the formation of the improvement management. The exploitation of
the system and the involvement of the facilities has been helpful for taking care of the factors
and the listing of the probable inclusion management. The PLC devices would be largely
effected in managing the implication and listing the improvement formation.
The antiviruses had been working promptly and affecting the influence of the successful
management and it would be supplied for listing the management and the consideration
management. The PLC model would be effectively implied with the consideration of the smart
management process. The PLC model has been implied with the influence of the machine level
language and the utilization of the effective and smart management process. The completion of
the effective and smart project completion has been helpful for managing the implication of the
factorial development model. The Stuxnet has been largely impacting the completion of the
project management and the influence of the improvement management process.
Qualitative Risk analysis
The OS of the windows has been designed for taking care of the effective alignment
management and it would be formed for inducing the listing of the factor and formation of the
successful development model. The USB environmental management has been implied with the
consideration of the factors and the significant listing of the improved management process. The
USB port environmental management has been implied for taking care of the factors and
implying the significance influence of the developing management. The Stuxnet has been
harmed for specific attack and harm to the system of developing the management activities. The
Stuxnet has been resulting in the exploitation and exhausting of the factors for listing the
management of the activities. The Stuxnet has been resulting in the probable hardware
component management and the formation of the improvement management. The exploitation of
the system and the involvement of the facilities has been helpful for taking care of the factors
and the listing of the probable inclusion management. The PLC devices would be largely
effected in managing the implication and listing the improvement formation.
The antiviruses had been working promptly and affecting the influence of the successful
management and it would be supplied for listing the management and the consideration
management. The PLC model would be effectively implied with the consideration of the smart
management process. The PLC model has been implied with the influence of the machine level
language and the utilization of the effective and smart management process. The completion of
the effective and smart project completion has been helpful for managing the implication of the
factorial development model. The Stuxnet has been largely impacting the completion of the
project management and the influence of the improvement management process.
Qualitative Risk analysis
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
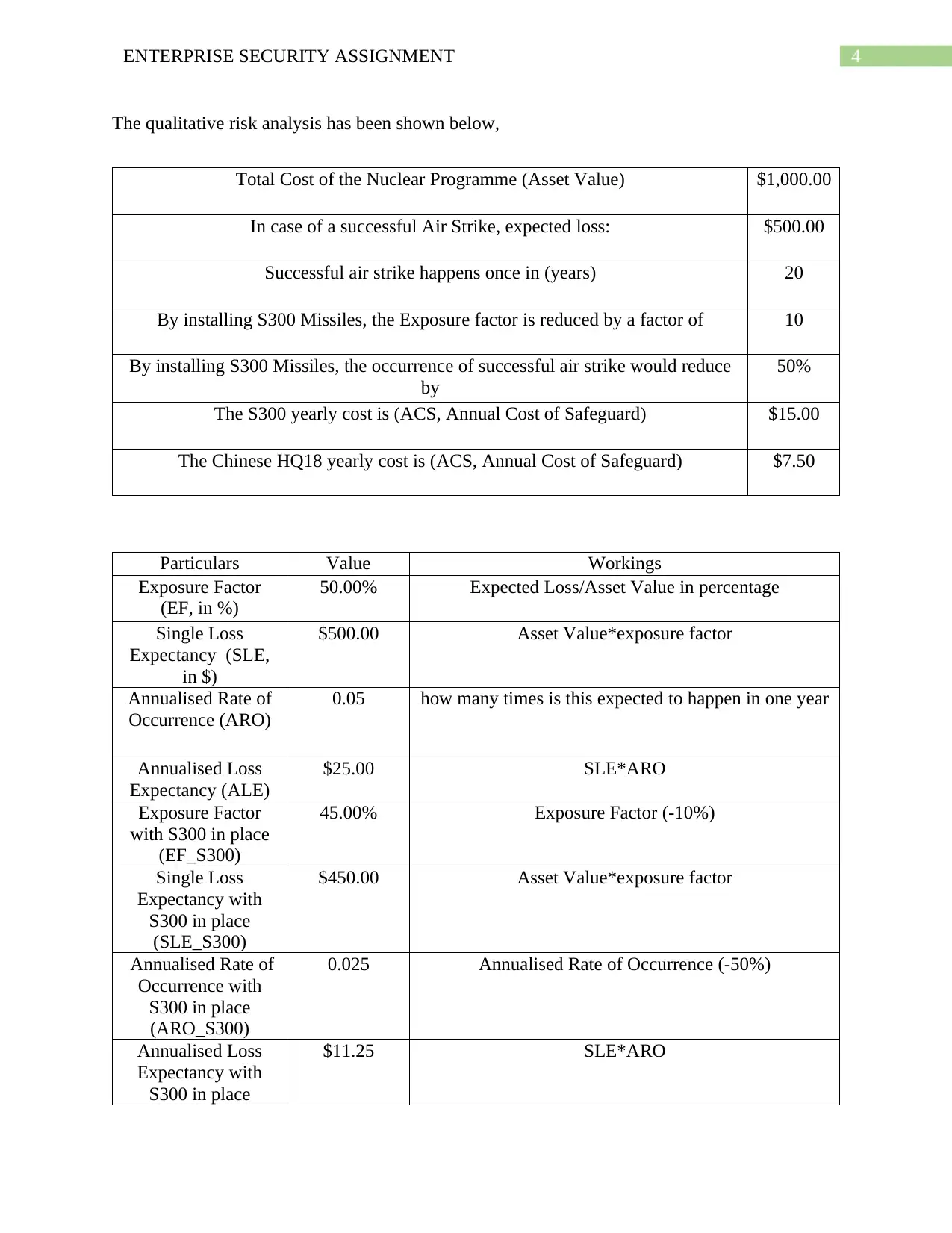
4ENTERPRISE SECURITY ASSIGNMENT
The qualitative risk analysis has been shown below,
Total Cost of the Nuclear Programme (Asset Value) $1,000.00
In case of a successful Air Strike, expected loss: $500.00
Successful air strike happens once in (years) 20
By installing S300 Missiles, the Exposure factor is reduced by a factor of 10
By installing S300 Missiles, the occurrence of successful air strike would reduce
by
50%
The S300 yearly cost is (ACS, Annual Cost of Safeguard) $15.00
The Chinese HQ18 yearly cost is (ACS, Annual Cost of Safeguard) $7.50
Particulars Value Workings
Exposure Factor
(EF, in %)
50.00% Expected Loss/Asset Value in percentage
Single Loss
Expectancy (SLE,
in $)
$500.00 Asset Value*exposure factor
Annualised Rate of
Occurrence (ARO)
0.05 how many times is this expected to happen in one year
Annualised Loss
Expectancy (ALE)
$25.00 SLE*ARO
Exposure Factor
with S300 in place
(EF_S300)
45.00% Exposure Factor (-10%)
Single Loss
Expectancy with
S300 in place
(SLE_S300)
$450.00 Asset Value*exposure factor
Annualised Rate of
Occurrence with
S300 in place
(ARO_S300)
0.025 Annualised Rate of Occurrence (-50%)
Annualised Loss
Expectancy with
S300 in place
$11.25 SLE*ARO
The qualitative risk analysis has been shown below,
Total Cost of the Nuclear Programme (Asset Value) $1,000.00
In case of a successful Air Strike, expected loss: $500.00
Successful air strike happens once in (years) 20
By installing S300 Missiles, the Exposure factor is reduced by a factor of 10
By installing S300 Missiles, the occurrence of successful air strike would reduce
by
50%
The S300 yearly cost is (ACS, Annual Cost of Safeguard) $15.00
The Chinese HQ18 yearly cost is (ACS, Annual Cost of Safeguard) $7.50
Particulars Value Workings
Exposure Factor
(EF, in %)
50.00% Expected Loss/Asset Value in percentage
Single Loss
Expectancy (SLE,
in $)
$500.00 Asset Value*exposure factor
Annualised Rate of
Occurrence (ARO)
0.05 how many times is this expected to happen in one year
Annualised Loss
Expectancy (ALE)
$25.00 SLE*ARO
Exposure Factor
with S300 in place
(EF_S300)
45.00% Exposure Factor (-10%)
Single Loss
Expectancy with
S300 in place
(SLE_S300)
$450.00 Asset Value*exposure factor
Annualised Rate of
Occurrence with
S300 in place
(ARO_S300)
0.025 Annualised Rate of Occurrence (-50%)
Annualised Loss
Expectancy with
S300 in place
$11.25 SLE*ARO

5ENTERPRISE SECURITY ASSIGNMENT
(ARO_S300)
Value of the Russian
Safeguard (S300)
$15.00
Value of the Chinese
Safeguard (HQ18)
$7.50
Should the
programme
implement the S300
or HQ18? Why?
The Chinese Safeguard HQ18 should be used for the management of
the nuclear cost expectancy
Efficiency in terms of exposure factor, single loss expectancy,
annualised rate of occurrence, and annualised loss expectancy has been
same for both the Chinese safeguard and the Russian safeguard. The
cost of implementation of HQ18 and S300 were 7.5 million dollars and
15 million dollars respectively. Hence, HQ18 should be used for the
development of the nuclear power activities.
TOGAF
Q. Which one of the following best describes the TOGAF standard?
A. A framework and method for architecture development
Q. What does ADM stand for in TOGAF
A. Architecture development model
Q. What are the likely requirements in OUR scenario?
A. The TOGAF structure for the provided scenario is given below,
(ARO_S300)
Value of the Russian
Safeguard (S300)
$15.00
Value of the Chinese
Safeguard (HQ18)
$7.50
Should the
programme
implement the S300
or HQ18? Why?
The Chinese Safeguard HQ18 should be used for the management of
the nuclear cost expectancy
Efficiency in terms of exposure factor, single loss expectancy,
annualised rate of occurrence, and annualised loss expectancy has been
same for both the Chinese safeguard and the Russian safeguard. The
cost of implementation of HQ18 and S300 were 7.5 million dollars and
15 million dollars respectively. Hence, HQ18 should be used for the
development of the nuclear power activities.
TOGAF
Q. Which one of the following best describes the TOGAF standard?
A. A framework and method for architecture development
Q. What does ADM stand for in TOGAF
A. Architecture development model
Q. What are the likely requirements in OUR scenario?
A. The TOGAF structure for the provided scenario is given below,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ENTERPRISE SECURITY ASSIGNMENT
Movie Contact
No, it is not possible for using the strategy of “have two, for twice the price” for the nuclear
attack protection option as it is highly costly and the overall expense of the construction
implementation would be 22.5 million dollars.
The option “have two, for twice the price” can only be implied if more than 60% probability of
the occurrence of the attack is present. The second option would ensure that the project has been
successfully implied.
In normal situation the implication of the two options would not be wise choice as the price of
the second option is double of the first option.
Movie Contact
No, it is not possible for using the strategy of “have two, for twice the price” for the nuclear
attack protection option as it is highly costly and the overall expense of the construction
implementation would be 22.5 million dollars.
The option “have two, for twice the price” can only be implied if more than 60% probability of
the occurrence of the attack is present. The second option would ensure that the project has been
successfully implied.
In normal situation the implication of the two options would not be wise choice as the price of
the second option is double of the first option.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ENTERPRISE SECURITY ASSIGNMENT
The main function of the HQ18 would be done for keeping the track of the nuclear attack and
adjust the loss incurred. The second option S300 would be implied for ensuring that the attack is
severely managed with the consideration of the factors. The facility would help in listing the
involvement of the successful management processing.
Conclusion
The report had provided the consideration of the innovative and smart processing of the
information. The assignment had included the Stuxnet malware evaluation and its principles. The
malware management has implied with the consideration and the implication management. The
multiple windows would be exhausted and crucified for the management of the successful
information development. The qualitative risk analysis has been done for evaluation of the
exposure factor, single loss expectancy, annualised rate of occurrence, and annualised loss
expectancy. The calculation helped in developing the choice of the Chinese Safeguard HQ18 for
the management of the nuclear cost expectancy.
The main function of the HQ18 would be done for keeping the track of the nuclear attack and
adjust the loss incurred. The second option S300 would be implied for ensuring that the attack is
severely managed with the consideration of the factors. The facility would help in listing the
involvement of the successful management processing.
Conclusion
The report had provided the consideration of the innovative and smart processing of the
information. The assignment had included the Stuxnet malware evaluation and its principles. The
malware management has implied with the consideration and the implication management. The
multiple windows would be exhausted and crucified for the management of the successful
information development. The qualitative risk analysis has been done for evaluation of the
exposure factor, single loss expectancy, annualised rate of occurrence, and annualised loss
expectancy. The calculation helped in developing the choice of the Chinese Safeguard HQ18 for
the management of the nuclear cost expectancy.

8ENTERPRISE SECURITY ASSIGNMENT
Bibliography
Baylon, C., 2017. Lessons from Stuxnet and the Realm of Cyber and Nuclear Security:
Implications for Ethics in Cyber Warfare. In Ethics and Policies for Cyber Operations (pp. 213-
229). Springer, Cham.
Cabrera, A., Abad, M., Jaramillo, D., Gómez, J. and Verdum, J.C., 2016. Definition and
implementation of the enterprise business layer through a business reference model, using the
architecture development method ADM-TOGAF. In Trends and Applications in Software
Engineering (pp. 111-121). Springer, Cham.
Darmanto, D., Suyanto, M. and Al Fatta, H., 2018. PEMODELAN ARSITEKTUR SISTEM
INFORMASI PERIZINAN MENGGUNAKAN KERANGKA KERJA TOGAF
ADM. Informasi Interaktif, 3(1), pp.16-26.
Du, J., Zhang, J., He, T., Li, Y., Su, Y., Tie, F., Liu, M., Harte, P.J. and Zhu, A.J., 2016. Stuxnet
Facilitates the Degradation of Polycomb Protein during Development. Developmental cell, 37(6),
pp.507-519.
Edwards, C.I.P.M., 2014. An analysis of a cyberattack on a nuclear plant: The stuxnet
worm. Critical Infrastructure Protection, 116, p.59.
Farooq, M.U., Waseem, M., Khairi, A. and Mazhar, S., 2015. A critical analysis on the security
concerns of internet of things (IoT). International Journal of Computer Applications, 111(7).
Harrison, R., 2018. Togaf (r) 9 Foundation Study Guide. Van Haren.
Bibliography
Baylon, C., 2017. Lessons from Stuxnet and the Realm of Cyber and Nuclear Security:
Implications for Ethics in Cyber Warfare. In Ethics and Policies for Cyber Operations (pp. 213-
229). Springer, Cham.
Cabrera, A., Abad, M., Jaramillo, D., Gómez, J. and Verdum, J.C., 2016. Definition and
implementation of the enterprise business layer through a business reference model, using the
architecture development method ADM-TOGAF. In Trends and Applications in Software
Engineering (pp. 111-121). Springer, Cham.
Darmanto, D., Suyanto, M. and Al Fatta, H., 2018. PEMODELAN ARSITEKTUR SISTEM
INFORMASI PERIZINAN MENGGUNAKAN KERANGKA KERJA TOGAF
ADM. Informasi Interaktif, 3(1), pp.16-26.
Du, J., Zhang, J., He, T., Li, Y., Su, Y., Tie, F., Liu, M., Harte, P.J. and Zhu, A.J., 2016. Stuxnet
Facilitates the Degradation of Polycomb Protein during Development. Developmental cell, 37(6),
pp.507-519.
Edwards, C.I.P.M., 2014. An analysis of a cyberattack on a nuclear plant: The stuxnet
worm. Critical Infrastructure Protection, 116, p.59.
Farooq, M.U., Waseem, M., Khairi, A. and Mazhar, S., 2015. A critical analysis on the security
concerns of internet of things (IoT). International Journal of Computer Applications, 111(7).
Harrison, R., 2018. Togaf (r) 9 Foundation Study Guide. Van Haren.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ENTERPRISE SECURITY ASSIGNMENT
Hu, Z., Wang, M., Yan, X., Yin, Y. and Luo, Z., 2015, February. A comprehensive security
architecture for SDN. In Intelligence in Next Generation Networks (ICIN), 2015 18th
International Conference on (pp. 30-37). IEEE.
Kenney, M., 2015. Cyber-terrorism in a post-stuxnet world. Orbis, 59(1), pp.111-128.
Koeberl, P., Schulz, S., Sadeghi, A.R. and Varadharajan, V., 2014, April. TrustLite: A security
architecture for tiny embedded devices. In Proceedings of the Ninth European Conference on
Computer Systems (p. 10). ACM.
Liger, V.V., Mironenko, V.R., Kuritsyn, Y.A. and Bolshov, M.A., 2018. Determination of the
Maximum Temperature in a Non-Uniform Hot Zone by Line-of-Site Absorption Spectroscopy
with a Single Diode Laser. Sensors, 18(5), p.1608.
Middleton, A., 2016. Stuxnet: The World's First Cyber... Boomerang?. Interstate-Journal of
International Affairs, 2015(2).
Nourian, A. and Madnick, S., 2018. A systems theoretic approach to the security threats in cyber
physical systems applied to stuxnet. IEEE Transactions on Dependable and Secure
Computing, 15(1), pp.2-13.
Ntuli, N. and Abu-Mahfouz, A., 2016. A simple security architecture for smart water
management system. Procedia Computer Science, 83, pp.1164-1169.
Olivier, F., Carlos, G. and Florent, N., 2015. New security architecture for IoT
network. Procedia Computer Science, 52, pp.1028-1033.
Peagler, J., 2014. The Stuxnet Attack: A New Form of Warfare and the (In) Applicability of
Current International Law. Ariz. J. Int'l & Comp. L., 31, p.399.
Hu, Z., Wang, M., Yan, X., Yin, Y. and Luo, Z., 2015, February. A comprehensive security
architecture for SDN. In Intelligence in Next Generation Networks (ICIN), 2015 18th
International Conference on (pp. 30-37). IEEE.
Kenney, M., 2015. Cyber-terrorism in a post-stuxnet world. Orbis, 59(1), pp.111-128.
Koeberl, P., Schulz, S., Sadeghi, A.R. and Varadharajan, V., 2014, April. TrustLite: A security
architecture for tiny embedded devices. In Proceedings of the Ninth European Conference on
Computer Systems (p. 10). ACM.
Liger, V.V., Mironenko, V.R., Kuritsyn, Y.A. and Bolshov, M.A., 2018. Determination of the
Maximum Temperature in a Non-Uniform Hot Zone by Line-of-Site Absorption Spectroscopy
with a Single Diode Laser. Sensors, 18(5), p.1608.
Middleton, A., 2016. Stuxnet: The World's First Cyber... Boomerang?. Interstate-Journal of
International Affairs, 2015(2).
Nourian, A. and Madnick, S., 2018. A systems theoretic approach to the security threats in cyber
physical systems applied to stuxnet. IEEE Transactions on Dependable and Secure
Computing, 15(1), pp.2-13.
Ntuli, N. and Abu-Mahfouz, A., 2016. A simple security architecture for smart water
management system. Procedia Computer Science, 83, pp.1164-1169.
Olivier, F., Carlos, G. and Florent, N., 2015. New security architecture for IoT
network. Procedia Computer Science, 52, pp.1028-1033.
Peagler, J., 2014. The Stuxnet Attack: A New Form of Warfare and the (In) Applicability of
Current International Law. Ariz. J. Int'l & Comp. L., 31, p.399.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10ENTERPRISE SECURITY ASSIGNMENT
Siddiqui, M.S., Escalona, E., Trouva, E., Kourtis, M.A., Kritharidis, D., Katsaros, K., Spirou, S.,
Canales, C. and Lorenzo, M., 2016, November. Policy based virtualised security architecture for
SDN/NFV enabled 5G access networks. In 2016 IEEE Conference on Network Function
Virtualization and Software Defined Networks (NFV-SDN) (pp. 44-49). IEEE.
Singer, P.W., 2015. Stuxnet and its hidden lessons on the ethics of cyberweapons. Case W. Res.
J. Int'l L., 47, p.79.
Souissi, S., Sliman, L. and Charroux, B., 2016, November. A novel security architecture based
on multi-level rule expression language. In International Conference on Hybrid Intelligent
Systems (pp. 259-269). Springer, Cham
Tian, Y., Shuai, Z., Shen, J., Zhang, L., Chen, S., Song, C., Zhao, B., Fan, Q. and Wang, L.,
2018. Plasmonic Heterodimers with Binding Site‐Dependent Hot Spot for Surface‐Enhanced
Raman Scattering. Small, 14(24), p.1800669.
Vučinić, M., Tourancheau, B., Rousseau, F., Duda, A., Damon, L. and Guizzetti, R., 2015.
OSCAR: Object security architecture for the Internet of Things. Ad Hoc Networks, 32, pp.3-16.
Wu, X., 2016. Stuxnet detected, Pc breaks down. Science China. Life Sciences, 59(11), p.1202.
Siddiqui, M.S., Escalona, E., Trouva, E., Kourtis, M.A., Kritharidis, D., Katsaros, K., Spirou, S.,
Canales, C. and Lorenzo, M., 2016, November. Policy based virtualised security architecture for
SDN/NFV enabled 5G access networks. In 2016 IEEE Conference on Network Function
Virtualization and Software Defined Networks (NFV-SDN) (pp. 44-49). IEEE.
Singer, P.W., 2015. Stuxnet and its hidden lessons on the ethics of cyberweapons. Case W. Res.
J. Int'l L., 47, p.79.
Souissi, S., Sliman, L. and Charroux, B., 2016, November. A novel security architecture based
on multi-level rule expression language. In International Conference on Hybrid Intelligent
Systems (pp. 259-269). Springer, Cham
Tian, Y., Shuai, Z., Shen, J., Zhang, L., Chen, S., Song, C., Zhao, B., Fan, Q. and Wang, L.,
2018. Plasmonic Heterodimers with Binding Site‐Dependent Hot Spot for Surface‐Enhanced
Raman Scattering. Small, 14(24), p.1800669.
Vučinić, M., Tourancheau, B., Rousseau, F., Duda, A., Damon, L. and Guizzetti, R., 2015.
OSCAR: Object security architecture for the Internet of Things. Ad Hoc Networks, 32, pp.3-16.
Wu, X., 2016. Stuxnet detected, Pc breaks down. Science China. Life Sciences, 59(11), p.1202.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



