Error Detection & Correction in Intermediate Computer Networking
VerifiedAdded on 2023/06/11
|11
|2025
|396
Report
AI Summary
This report provides an overview of error detection and correction mechanisms in computer networking, focusing on techniques like parity checking, Cyclic Redundancy Check (CRC), and checksum. It details the types of errors encountered during data transmission, including single-bit, multiple-bit, and burst errors. The report compares the pros and cons of different error detection techniques, highlighting their effectiveness and limitations. Additionally, it introduces Forward Error Correction (FEC) mechanisms, discussing block code FEC and convolution code FEC, and compares their advantages and disadvantages. The document emphasizes the importance of these mechanisms in ensuring reliable data delivery across networks and includes relevant examples and diagrams to illustrate key concepts.

Running head: INTERMEDIATE COMPUTER NETWORKING
Intermediate Computer Networking: Part A
Name of the Student
Name of the University
Author Note
Intermediate Computer Networking: Part A
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTERMEDIATE COMPUTER NETWORKING
Table of Contents
1. Introduction to Error Detection and Correction mechanisms..........................................2
2. Types of Errors................................................................................................................2
3. Error Detection Mechanisms...........................................................................................5
4. Comparison between Error Detection Techniques..........................................................6
5. Introduction to Forward Error Correction mechanisms...................................................8
6. Comparison between Forward Error Detection Techniques...........................................9
INTERMEDIATE COMPUTER NETWORKING
Table of Contents
1. Introduction to Error Detection and Correction mechanisms..........................................2
2. Types of Errors................................................................................................................2
3. Error Detection Mechanisms...........................................................................................5
4. Comparison between Error Detection Techniques..........................................................6
5. Introduction to Forward Error Correction mechanisms...................................................8
6. Comparison between Forward Error Detection Techniques...........................................9

2
INTERMEDIATE COMPUTER NETWORKING
1. Introduction to Error Detection and Correction mechanisms
Error can be described as a condition when the output of information of the system does
not match with the input information. The noise in the channel of disrupts the smooth
transmission of the digital signal often resulting in addition of the errors to the binary bits. When
a message is transmitted, the noise can scramble the digital message thus corrupting the data.
Therefore, certain error detecting codes are needed to be added with the message during
transmission so that the incorrect messages can be detection and corrected (Clark Jr & Cain,
2013). One of the simple error detection codes includes parity check. The error detection codes
are designed in such a way that the original message can be figured out even after distortion. If
an error code, say parity check receives a signal different from what it was suppose to receive,
the presence of the error is confirmed. On detection of the error, the signal is retransmitted as an
error correction mechanism.
2. Types of Errors
An error in the code is detected if in a data sequence, 1 is changed to zero and zero is
changed to 1. There are mainly three types of errors, that can be faced while transmission of a
particular data from transmitter to receiver. The types of errors faced in data transmission are
listed below-
1. Single bit errors- In single bit errors, only one bit of a particular data is changed from
0 to 1 or from 1 to 0. The occurrence of this type of error in signal transmission is however low.
INTERMEDIATE COMPUTER NETWORKING
1. Introduction to Error Detection and Correction mechanisms
Error can be described as a condition when the output of information of the system does
not match with the input information. The noise in the channel of disrupts the smooth
transmission of the digital signal often resulting in addition of the errors to the binary bits. When
a message is transmitted, the noise can scramble the digital message thus corrupting the data.
Therefore, certain error detecting codes are needed to be added with the message during
transmission so that the incorrect messages can be detection and corrected (Clark Jr & Cain,
2013). One of the simple error detection codes includes parity check. The error detection codes
are designed in such a way that the original message can be figured out even after distortion. If
an error code, say parity check receives a signal different from what it was suppose to receive,
the presence of the error is confirmed. On detection of the error, the signal is retransmitted as an
error correction mechanism.
2. Types of Errors
An error in the code is detected if in a data sequence, 1 is changed to zero and zero is
changed to 1. There are mainly three types of errors, that can be faced while transmission of a
particular data from transmitter to receiver. The types of errors faced in data transmission are
listed below-
1. Single bit errors- In single bit errors, only one bit of a particular data is changed from
0 to 1 or from 1 to 0. The occurrence of this type of error in signal transmission is however low.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
INTERMEDIATE COMPUTER NETWORKING
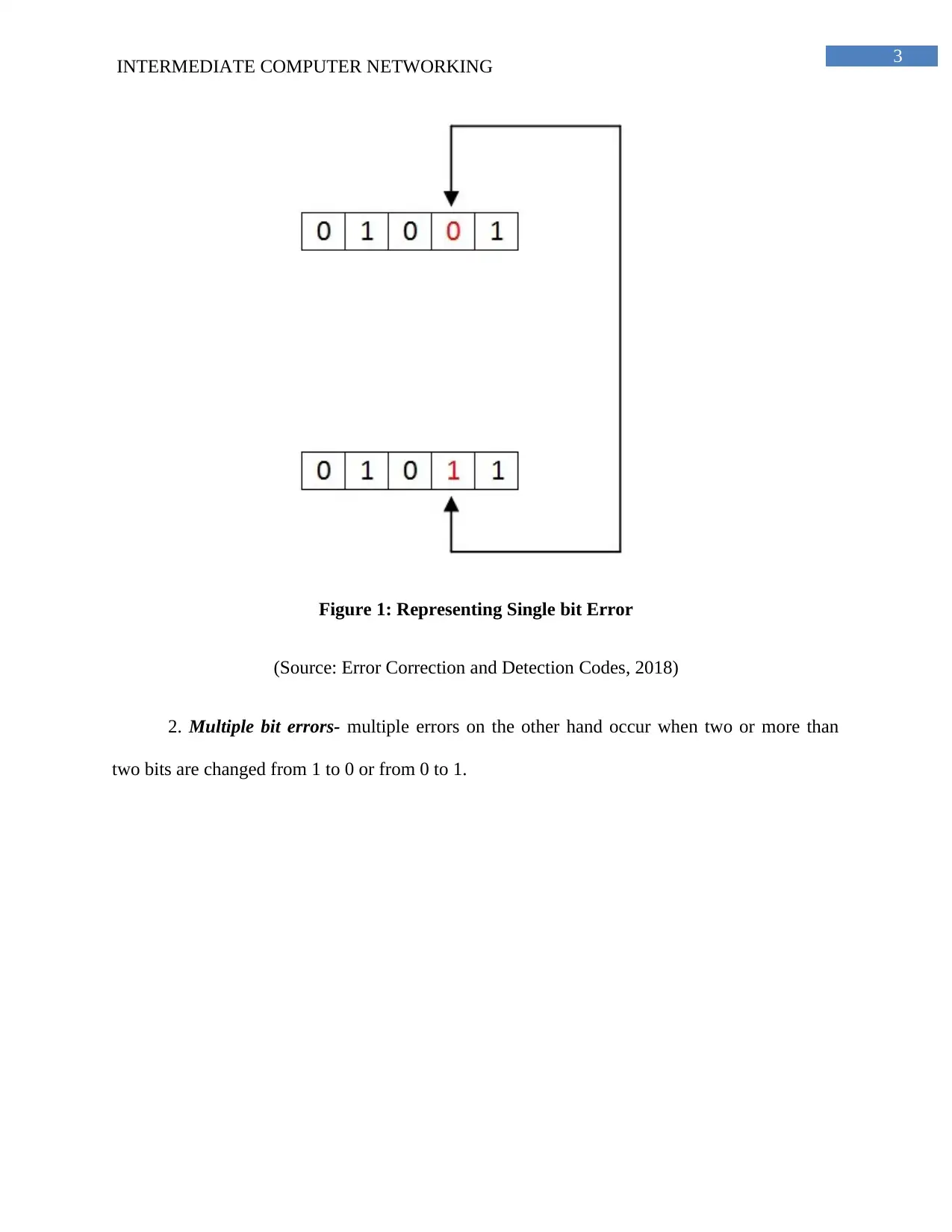
Figure 1: Representing Single bit Error
(Source: Error Correction and Detection Codes, 2018)
2. Multiple bit errors- multiple errors on the other hand occur when two or more than
two bits are changed from 1 to 0 or from 0 to 1.
INTERMEDIATE COMPUTER NETWORKING
Figure 1: Representing Single bit Error
(Source: Error Correction and Detection Codes, 2018)
2. Multiple bit errors- multiple errors on the other hand occur when two or more than
two bits are changed from 1 to 0 or from 0 to 1.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
INTERMEDIATE COMPUTER NETWORKING
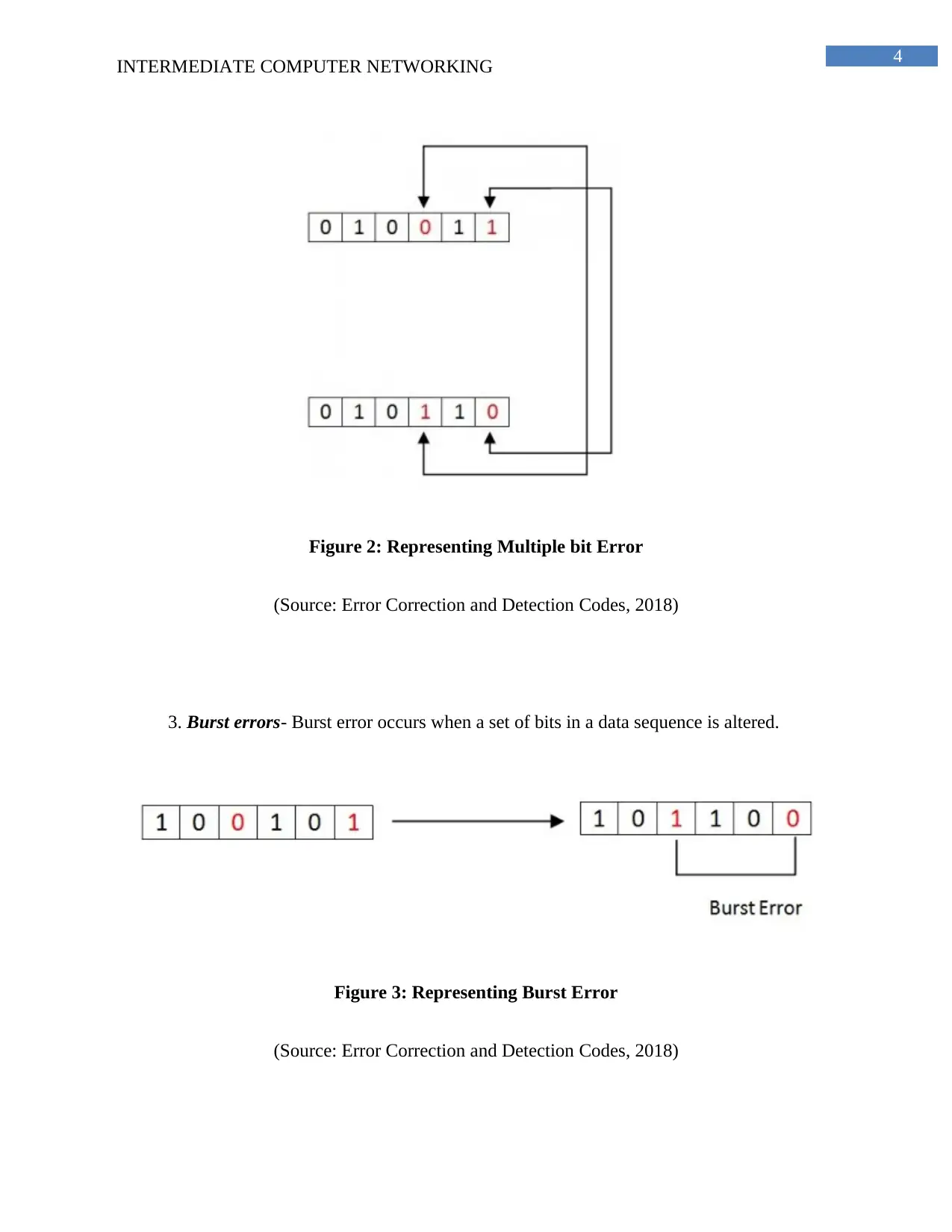
Figure 2: Representing Multiple bit Error
(Source: Error Correction and Detection Codes, 2018)
3. Burst errors- Burst error occurs when a set of bits in a data sequence is altered.
Figure 3: Representing Burst Error
(Source: Error Correction and Detection Codes, 2018)
INTERMEDIATE COMPUTER NETWORKING
Figure 2: Representing Multiple bit Error
(Source: Error Correction and Detection Codes, 2018)
3. Burst errors- Burst error occurs when a set of bits in a data sequence is altered.
Figure 3: Representing Burst Error
(Source: Error Correction and Detection Codes, 2018)

5
INTERMEDIATE COMPUTER NETWORKING
3. Error Detection Mechanisms
The receiver of a signal is able to detect the presence of an error. Error detection is
generally referred to the technique of detecting certain impairments that can be introduced in a
data while its transmission. The error detection mechanism mainly ensures reliable data delivery
even across certain vulnerable network. If the error is not detected or corrected, the data can be
permanently lost (Imai, 2014). The error detection mechanisms ensure that a particular data is
transferred with high accuracy. As an error detection mechanism, some redundancy codes are
used for detecting the errors. The different types of error detection mechanism or techniques are
listed below-
1. Parity checking- In parity checking, an additional bit is added to the data that is to be
transmitted before data transmission. The parity bit is added in a data after calculating the
number of one and zeros present in the data. The addition of the parity bit is mainly based on this
calculation and the addition of the same results in the change of the data string or data size
(Pontarelli & Ottavi, 2013). The parity check technique is also called vertical redundancy check
and there are mainly two types of error detection techniques, which are even parity and odd
parity.
2. Cyclic Redundancy Check- The error detection technique, cyclic redundancy check is
mainly used in digital network and is used to detect the accidental changes in the original data.
cyclic redundancy check (CRC) is mainly a hash function and is used to detect accidental
changes to the original data of the network (Sheng-Ju, 2015). The codes that are used for cyclic
redundancy check are often known as CRC codes. These codes provide an effective and high
level protection for the transmitted signal. A particular process is maintained for generation of
INTERMEDIATE COMPUTER NETWORKING
3. Error Detection Mechanisms
The receiver of a signal is able to detect the presence of an error. Error detection is
generally referred to the technique of detecting certain impairments that can be introduced in a
data while its transmission. The error detection mechanism mainly ensures reliable data delivery
even across certain vulnerable network. If the error is not detected or corrected, the data can be
permanently lost (Imai, 2014). The error detection mechanisms ensure that a particular data is
transferred with high accuracy. As an error detection mechanism, some redundancy codes are
used for detecting the errors. The different types of error detection mechanism or techniques are
listed below-
1. Parity checking- In parity checking, an additional bit is added to the data that is to be
transmitted before data transmission. The parity bit is added in a data after calculating the
number of one and zeros present in the data. The addition of the parity bit is mainly based on this
calculation and the addition of the same results in the change of the data string or data size
(Pontarelli & Ottavi, 2013). The parity check technique is also called vertical redundancy check
and there are mainly two types of error detection techniques, which are even parity and odd
parity.
2. Cyclic Redundancy Check- The error detection technique, cyclic redundancy check is
mainly used in digital network and is used to detect the accidental changes in the original data.
cyclic redundancy check (CRC) is mainly a hash function and is used to detect accidental
changes to the original data of the network (Sheng-Ju, 2015). The codes that are used for cyclic
redundancy check are often known as CRC codes. These codes provide an effective and high
level protection for the transmitted signal. A particular process is maintained for generation of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INTERMEDIATE COMPUTER NETWORKING
CRC code. In this process, some redundant zeros are added to the actual data and then the new
data thus formed divided by a new word of n+ 1 bit length (here n is the number of bits added).
The remainder obtained from this module-2 division is then added to the bit sequence of the
cyclic code (Ye & Hongyu, 2013). In this way, the new code generated is divisible completely
by the divisor used in ode generation. The code is then checked in the receiver side and the
received code is divided with the same divisor to get the actual data.
3. Longitudinal Redundancy Check- In this error checking mechanism, a block of data
bits are arranged in a table format and from that table, the parity of each column is calculated
separately (Clark Jr & Cain, 2013). In this technique, bit by bit parity computation is followed
which provides an advanced error detection process.
4. Check Sum- The checksum methodology includes the combination of parity bits,
check digits and the longitudinal redundancy check. It is quite similar to parity bits but the
number of bits in the check sum is larger than that in the parity (Imai, 2014). In this method, the
number of bits that is transmitted is tallied with the number of bits in the receiver to check
whether any erroneous bit is added during transmission.
4. Comparison between Error Detection Techniques
The three most commonly used error detection techniques include, parity checking,
cyclic redundancy check and check sum. The differences among these three redundancy check
methods are discussed below-
INTERMEDIATE COMPUTER NETWORKING
CRC code. In this process, some redundant zeros are added to the actual data and then the new
data thus formed divided by a new word of n+ 1 bit length (here n is the number of bits added).
The remainder obtained from this module-2 division is then added to the bit sequence of the
cyclic code (Ye & Hongyu, 2013). In this way, the new code generated is divisible completely
by the divisor used in ode generation. The code is then checked in the receiver side and the
received code is divided with the same divisor to get the actual data.
3. Longitudinal Redundancy Check- In this error checking mechanism, a block of data
bits are arranged in a table format and from that table, the parity of each column is calculated
separately (Clark Jr & Cain, 2013). In this technique, bit by bit parity computation is followed
which provides an advanced error detection process.
4. Check Sum- The checksum methodology includes the combination of parity bits,
check digits and the longitudinal redundancy check. It is quite similar to parity bits but the
number of bits in the check sum is larger than that in the parity (Imai, 2014). In this method, the
number of bits that is transmitted is tallied with the number of bits in the receiver to check
whether any erroneous bit is added during transmission.
4. Comparison between Error Detection Techniques
The three most commonly used error detection techniques include, parity checking,
cyclic redundancy check and check sum. The differences among these three redundancy check
methods are discussed below-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INTERMEDIATE COMPUTER NETWORKING
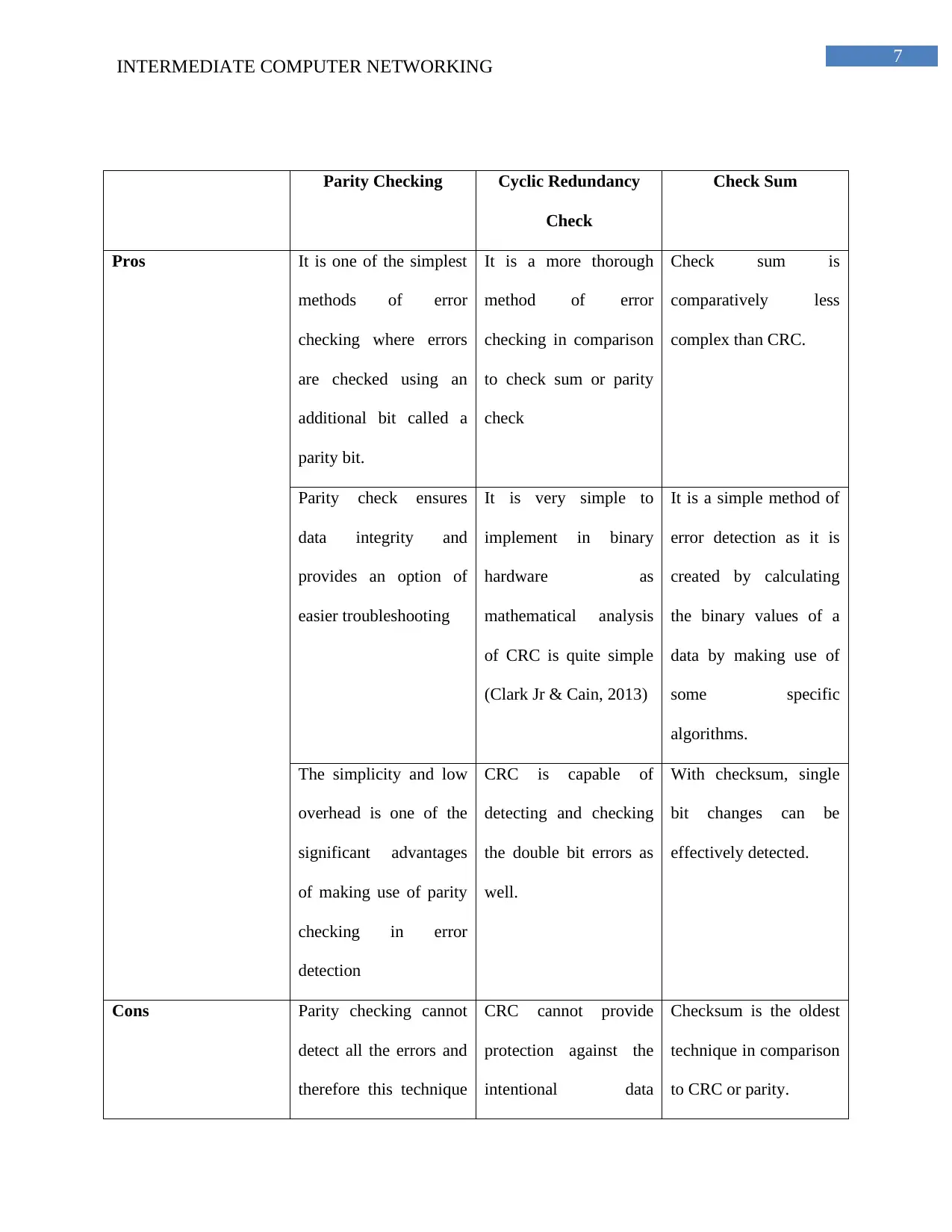
Parity Checking Cyclic Redundancy
Check
Check Sum
Pros It is one of the simplest
methods of error
checking where errors
are checked using an
additional bit called a
parity bit.
It is a more thorough
method of error
checking in comparison
to check sum or parity
check
Check sum is
comparatively less
complex than CRC.
Parity check ensures
data integrity and
provides an option of
easier troubleshooting
It is very simple to
implement in binary
hardware as
mathematical analysis
of CRC is quite simple
(Clark Jr & Cain, 2013)
It is a simple method of
error detection as it is
created by calculating
the binary values of a
data by making use of
some specific
algorithms.
The simplicity and low
overhead is one of the
significant advantages
of making use of parity
checking in error
detection
CRC is capable of
detecting and checking
the double bit errors as
well.
With checksum, single
bit changes can be
effectively detected.
Cons Parity checking cannot
detect all the errors and
therefore this technique
CRC cannot provide
protection against the
intentional data
Checksum is the oldest
technique in comparison
to CRC or parity.
INTERMEDIATE COMPUTER NETWORKING
Parity Checking Cyclic Redundancy
Check
Check Sum
Pros It is one of the simplest
methods of error
checking where errors
are checked using an
additional bit called a
parity bit.
It is a more thorough
method of error
checking in comparison
to check sum or parity
check
Check sum is
comparatively less
complex than CRC.
Parity check ensures
data integrity and
provides an option of
easier troubleshooting
It is very simple to
implement in binary
hardware as
mathematical analysis
of CRC is quite simple
(Clark Jr & Cain, 2013)
It is a simple method of
error detection as it is
created by calculating
the binary values of a
data by making use of
some specific
algorithms.
The simplicity and low
overhead is one of the
significant advantages
of making use of parity
checking in error
detection
CRC is capable of
detecting and checking
the double bit errors as
well.
With checksum, single
bit changes can be
effectively detected.
Cons Parity checking cannot
detect all the errors and
therefore this technique
CRC cannot provide
protection against the
intentional data
Checksum is the oldest
technique in comparison
to CRC or parity.
8
INTERMEDIATE COMPUTER NETWORKING
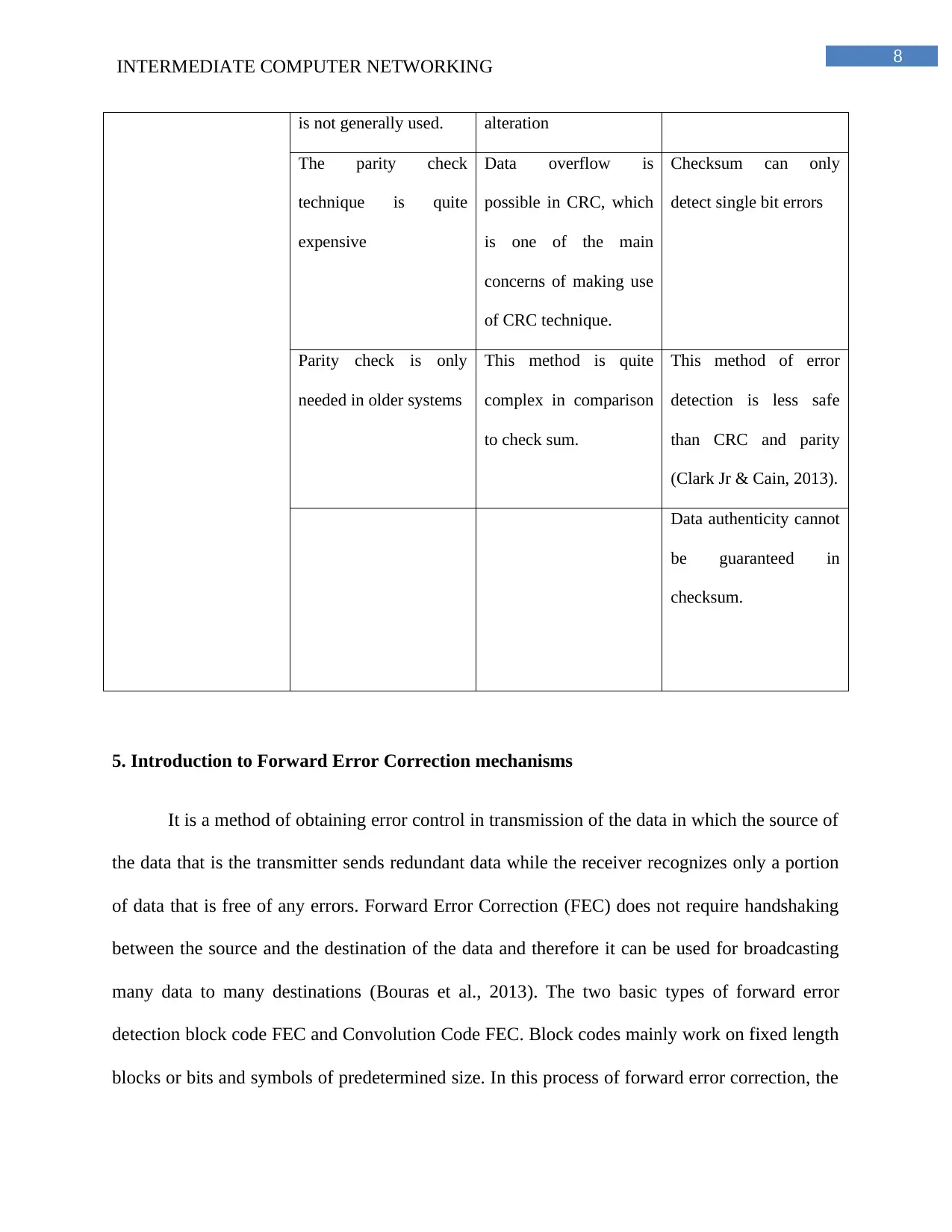
is not generally used. alteration
The parity check
technique is quite
expensive
Data overflow is
possible in CRC, which
is one of the main
concerns of making use
of CRC technique.
Checksum can only
detect single bit errors
Parity check is only
needed in older systems
This method is quite
complex in comparison
to check sum.
This method of error
detection is less safe
than CRC and parity
(Clark Jr & Cain, 2013).
Data authenticity cannot
be guaranteed in
checksum.
5. Introduction to Forward Error Correction mechanisms
It is a method of obtaining error control in transmission of the data in which the source of
the data that is the transmitter sends redundant data while the receiver recognizes only a portion
of data that is free of any errors. Forward Error Correction (FEC) does not require handshaking
between the source and the destination of the data and therefore it can be used for broadcasting
many data to many destinations (Bouras et al., 2013). The two basic types of forward error
detection block code FEC and Convolution Code FEC. Block codes mainly work on fixed length
blocks or bits and symbols of predetermined size. In this process of forward error correction, the
INTERMEDIATE COMPUTER NETWORKING
is not generally used. alteration
The parity check
technique is quite
expensive
Data overflow is
possible in CRC, which
is one of the main
concerns of making use
of CRC technique.
Checksum can only
detect single bit errors
Parity check is only
needed in older systems
This method is quite
complex in comparison
to check sum.
This method of error
detection is less safe
than CRC and parity
(Clark Jr & Cain, 2013).
Data authenticity cannot
be guaranteed in
checksum.
5. Introduction to Forward Error Correction mechanisms
It is a method of obtaining error control in transmission of the data in which the source of
the data that is the transmitter sends redundant data while the receiver recognizes only a portion
of data that is free of any errors. Forward Error Correction (FEC) does not require handshaking
between the source and the destination of the data and therefore it can be used for broadcasting
many data to many destinations (Bouras et al., 2013). The two basic types of forward error
detection block code FEC and Convolution Code FEC. Block codes mainly work on fixed length
blocks or bits and symbols of predetermined size. In this process of forward error correction, the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
INTERMEDIATE COMPUTER NETWORKING
data is encoded by a complex matrix while in receiver the decoder reconstructs the data and
corrects the errors. Convolution code on the other hand work on a bit of arbitrary length. It
considers streams of arbitrary length and is decoded using a Viterbi algorithm (Clark Jr & Cain,
2013). In Convolution code, the encoding of one bit is influenced by its preceding bits. The
convolution code encodes k bits of information into n bits of symbol.
6. Comparison between Forward Error Detection Techniques
Advantages and the disadvantages of the above identified forward error correction
methods are discussed in the following table-
Block FEC Convolution FEC
Pros Used for error detection for the
data that is transmitted in blocks
This type of FEC is very easy to
implement.
It converts k bit of message
signal to n bit codeword
The type of error control coding
is generally different and easier
in comparison to the block FEC
Cons A block code has no memory It involves longer units
It works on fixed size of blocks The bit sequence depends on
both current bits and previous
bits of data.
It encodes one block at a time
References
INTERMEDIATE COMPUTER NETWORKING
data is encoded by a complex matrix while in receiver the decoder reconstructs the data and
corrects the errors. Convolution code on the other hand work on a bit of arbitrary length. It
considers streams of arbitrary length and is decoded using a Viterbi algorithm (Clark Jr & Cain,
2013). In Convolution code, the encoding of one bit is influenced by its preceding bits. The
convolution code encodes k bits of information into n bits of symbol.
6. Comparison between Forward Error Detection Techniques
Advantages and the disadvantages of the above identified forward error correction
methods are discussed in the following table-
Block FEC Convolution FEC
Pros Used for error detection for the
data that is transmitted in blocks
This type of FEC is very easy to
implement.
It converts k bit of message
signal to n bit codeword
The type of error control coding
is generally different and easier
in comparison to the block FEC
Cons A block code has no memory It involves longer units
It works on fixed size of blocks The bit sequence depends on
both current bits and previous
bits of data.
It encodes one block at a time
References
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INTERMEDIATE COMPUTER NETWORKING
Bouras, C., Kanakis, N., Kokkinos, V., & Papazois, A. (2013). Application layer forward error
correction for multicast streaming over LTE networks. International journal of
communication systems, 26(11), 1459-1474.
Clark Jr, G. C., & Cain, J. B. (2013). Error-correction coding for digital communications.
Springer Science & Business Media.
Error Correction and Detection Codes. (2018). Retrieved from
https://www.electronicshub.org/error-correction-and-detection-codes/#Types_Of_Errors
Imai, H. (Ed.). (2014). Essentials of error-control coding techniques. Academic Press.
Imai, H. (Ed.). (2014). Essentials of error-control coding techniques. Academic Press.
Pontarelli, S., & Ottavi, M. (2013). Error detection and correction in content addressable
memories by using bloom filters. IEEE Transactions on Computers, 62(6), 1111-1126.
Sheng-Ju, S. (2015, December). Implementation of cyclic redundancy check in data
communication. In Computational Intelligence and Communication Networks (CICN),
2015 International Conference on (pp. 529-531). IEEE.
Ye, T., & Hongyu, Z. (2013). A New Cyclic Redundancy Check Algorithm for UHF RFID
System [J]. Microcontrollers & Embedded Systems, 9, 000.
INTERMEDIATE COMPUTER NETWORKING
Bouras, C., Kanakis, N., Kokkinos, V., & Papazois, A. (2013). Application layer forward error
correction for multicast streaming over LTE networks. International journal of
communication systems, 26(11), 1459-1474.
Clark Jr, G. C., & Cain, J. B. (2013). Error-correction coding for digital communications.
Springer Science & Business Media.
Error Correction and Detection Codes. (2018). Retrieved from
https://www.electronicshub.org/error-correction-and-detection-codes/#Types_Of_Errors
Imai, H. (Ed.). (2014). Essentials of error-control coding techniques. Academic Press.
Imai, H. (Ed.). (2014). Essentials of error-control coding techniques. Academic Press.
Pontarelli, S., & Ottavi, M. (2013). Error detection and correction in content addressable
memories by using bloom filters. IEEE Transactions on Computers, 62(6), 1111-1126.
Sheng-Ju, S. (2015, December). Implementation of cyclic redundancy check in data
communication. In Computational Intelligence and Communication Networks (CICN),
2015 International Conference on (pp. 529-531). IEEE.
Ye, T., & Hongyu, Z. (2013). A New Cyclic Redundancy Check Algorithm for UHF RFID
System [J]. Microcontrollers & Embedded Systems, 9, 000.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




