Group Project: IT Security Mock Hack for Pennsylvania HIE Network
VerifiedAdded on 2022/09/22
|10
|850
|20
Project
AI Summary
This project notebook outlines a comprehensive IT security project plan developed for a mock hack into the Pennsylvania HIE network. It includes an introductory letter to the CEO, cost overviews, use cases (SQL injection, risk assessment, and penetration testing), an evaluation matrix, work breakdown structure, Gantt chart, resource sheet, and personal assignments. The project aims to assess and improve the IT security of the Pennsylvania HIE network through vulnerability assessments, server and firewall security assessments, and implementation of security measures. The team's goal is to identify vulnerabilities and threats, test the server's response to SQL injection, and ultimately enhance the network's security infrastructure. The project encompasses planning, research, implementation, and reporting phases, detailing tasks, durations, and responsible individuals.

Running head: PROJECT MANAGEMENT
PROJECT MANAGEMENT
(Student’s Name)
(Professor’s Name)
(Course Title)
(Date of Submission)
PROJECT MANAGEMENT
(Student’s Name)
(Professor’s Name)
(Course Title)
(Date of Submission)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

PROJECT MANAGEMENT 2
Introductory letter
To: CEO State of Pennsylvania HIE network
Thanks for offering us an opportunity to serve you. Our esteemed team of four offers a
comprehensive, efficient, and cost-effective IT security services. As our norm, we will address
any of your company IT security services in an innovative and dynamic approach. The need for
the mock-up test is due to rarely enough time to test to showcase our abilities. The mock
activities will involve;
Establishing Pennsylvania HIE network security policy
Establishing Pennsylvania HIE network data communication policies
Pinging the organizational server
Provide firewall activities report
This project book will notebook will detail all the activities to be carried chronologically. Also,
this document will detail our expected compensation package, risk management matrix, a
communication plan for our group. The overall goal is to improve the Pennsylvania HIE IT
security structure.
The cost of services overview
Dollars
1 Project management
Project Manager 960
Project team members 1920
2 Hardware
Handheld devices 100
Servers 7000
3 Software
Licensed software 100
Testing process 2340
2440
Resource cost overview
Introductory letter
To: CEO State of Pennsylvania HIE network
Thanks for offering us an opportunity to serve you. Our esteemed team of four offers a
comprehensive, efficient, and cost-effective IT security services. As our norm, we will address
any of your company IT security services in an innovative and dynamic approach. The need for
the mock-up test is due to rarely enough time to test to showcase our abilities. The mock
activities will involve;
Establishing Pennsylvania HIE network security policy
Establishing Pennsylvania HIE network data communication policies
Pinging the organizational server
Provide firewall activities report
This project book will notebook will detail all the activities to be carried chronologically. Also,
this document will detail our expected compensation package, risk management matrix, a
communication plan for our group. The overall goal is to improve the Pennsylvania HIE IT
security structure.
The cost of services overview
Dollars
1 Project management
Project Manager 960
Project team members 1920
2 Hardware
Handheld devices 100
Servers 7000
3 Software
Licensed software 100
Testing process 2340
2440
Resource cost overview
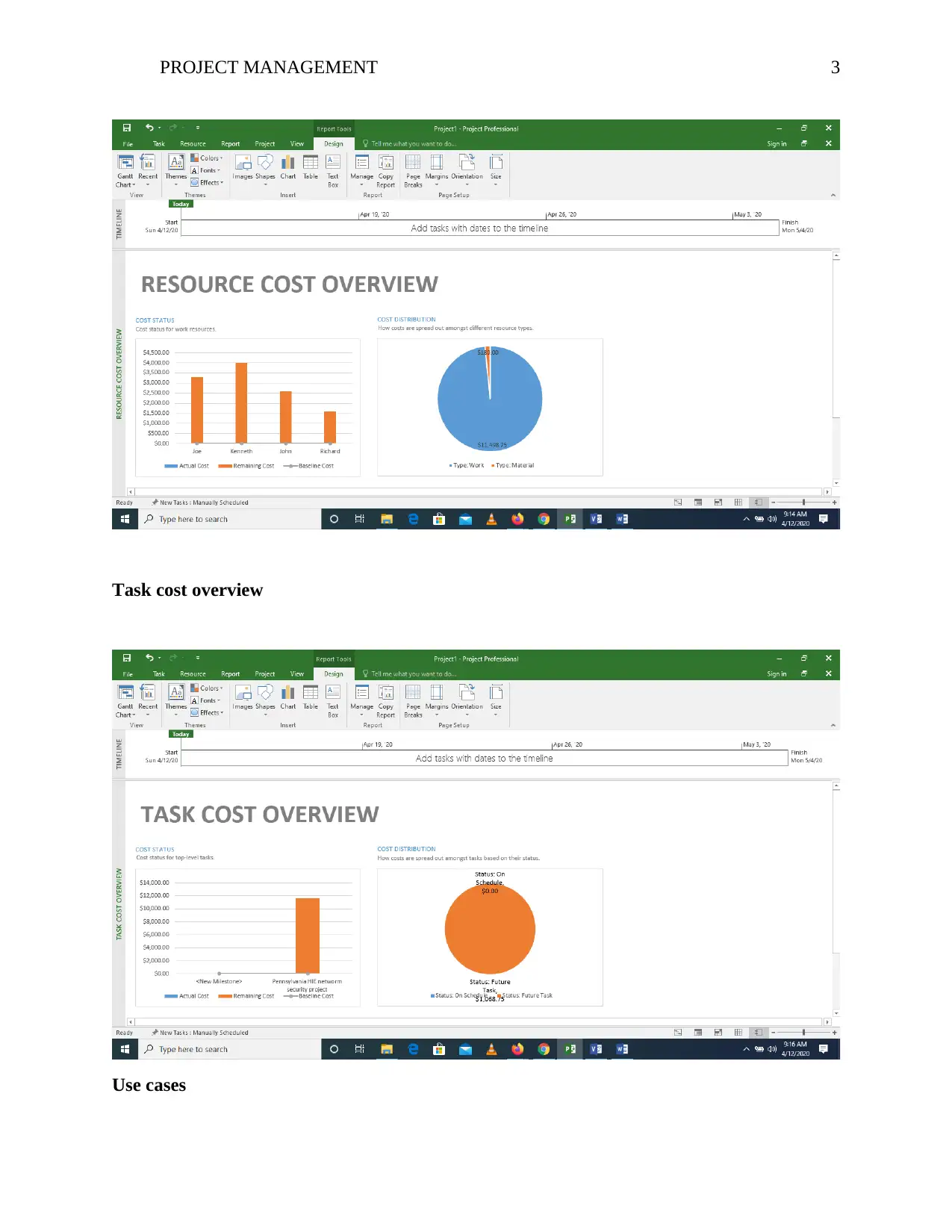
PROJECT MANAGEMENT 3
Task cost overview
Use cases
Task cost overview
Use cases
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
PROJECT MANAGEMENT 4
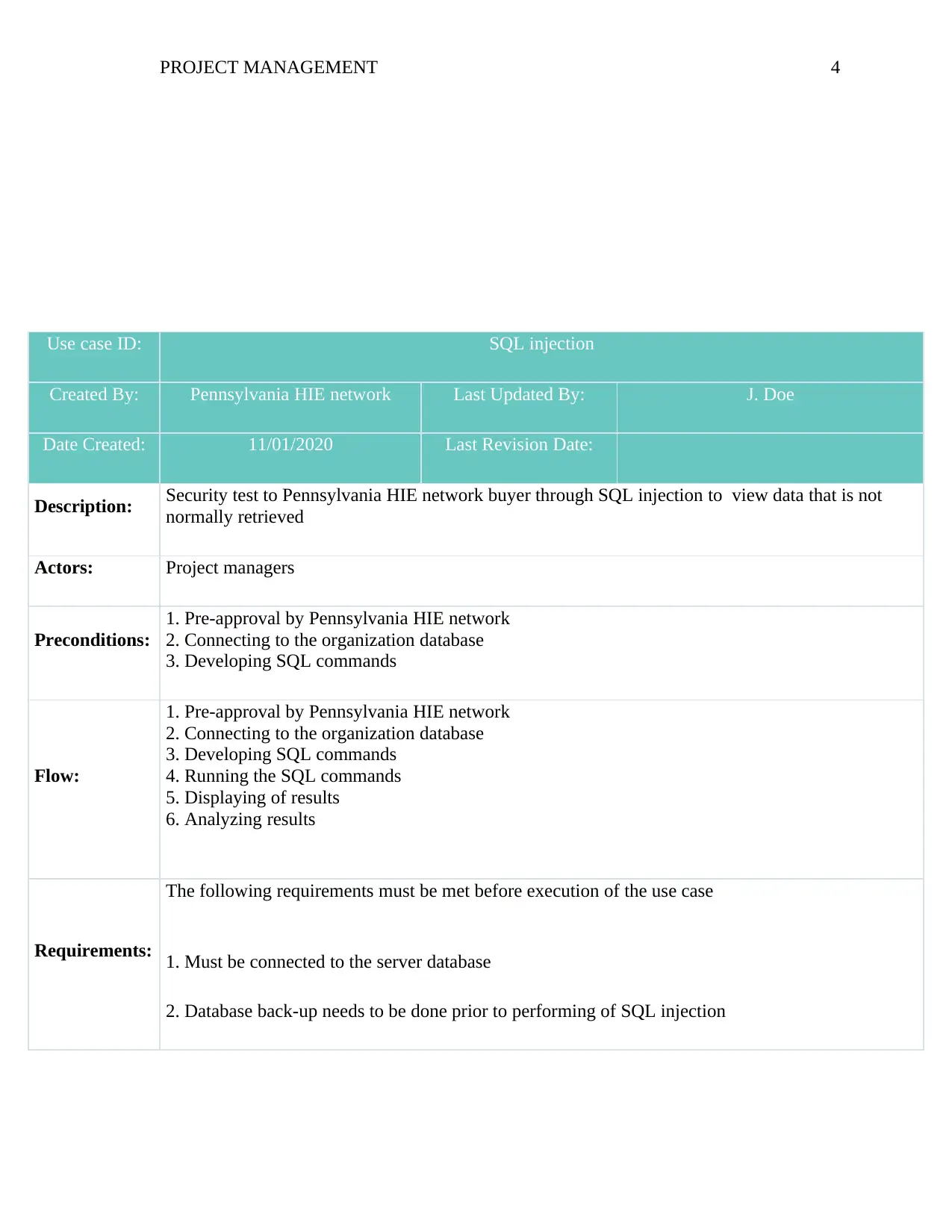
Use case ID: SQL injection
Created By: Pennsylvania HIE network Last Updated By: J. Doe
Date Created: 11/01/2020 Last Revision Date:
Description: Security test to Pennsylvania HIE network buyer through SQL injection to view data that is not
normally retrieved
Actors: Project managers
Preconditions:
1. Pre-approval by Pennsylvania HIE network
2. Connecting to the organization database
3. Developing SQL commands
Flow:
1. Pre-approval by Pennsylvania HIE network
2. Connecting to the organization database
3. Developing SQL commands
4. Running the SQL commands
5. Displaying of results
6. Analyzing results
Requirements:
The following requirements must be met before execution of the use case
1. Must be connected to the server database
2. Database back-up needs to be done prior to performing of SQL injection
Use case ID: SQL injection
Created By: Pennsylvania HIE network Last Updated By: J. Doe
Date Created: 11/01/2020 Last Revision Date:
Description: Security test to Pennsylvania HIE network buyer through SQL injection to view data that is not
normally retrieved
Actors: Project managers
Preconditions:
1. Pre-approval by Pennsylvania HIE network
2. Connecting to the organization database
3. Developing SQL commands
Flow:
1. Pre-approval by Pennsylvania HIE network
2. Connecting to the organization database
3. Developing SQL commands
4. Running the SQL commands
5. Displaying of results
6. Analyzing results
Requirements:
The following requirements must be met before execution of the use case
1. Must be connected to the server database
2. Database back-up needs to be done prior to performing of SQL injection
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
PROJECT MANAGEMENT 5
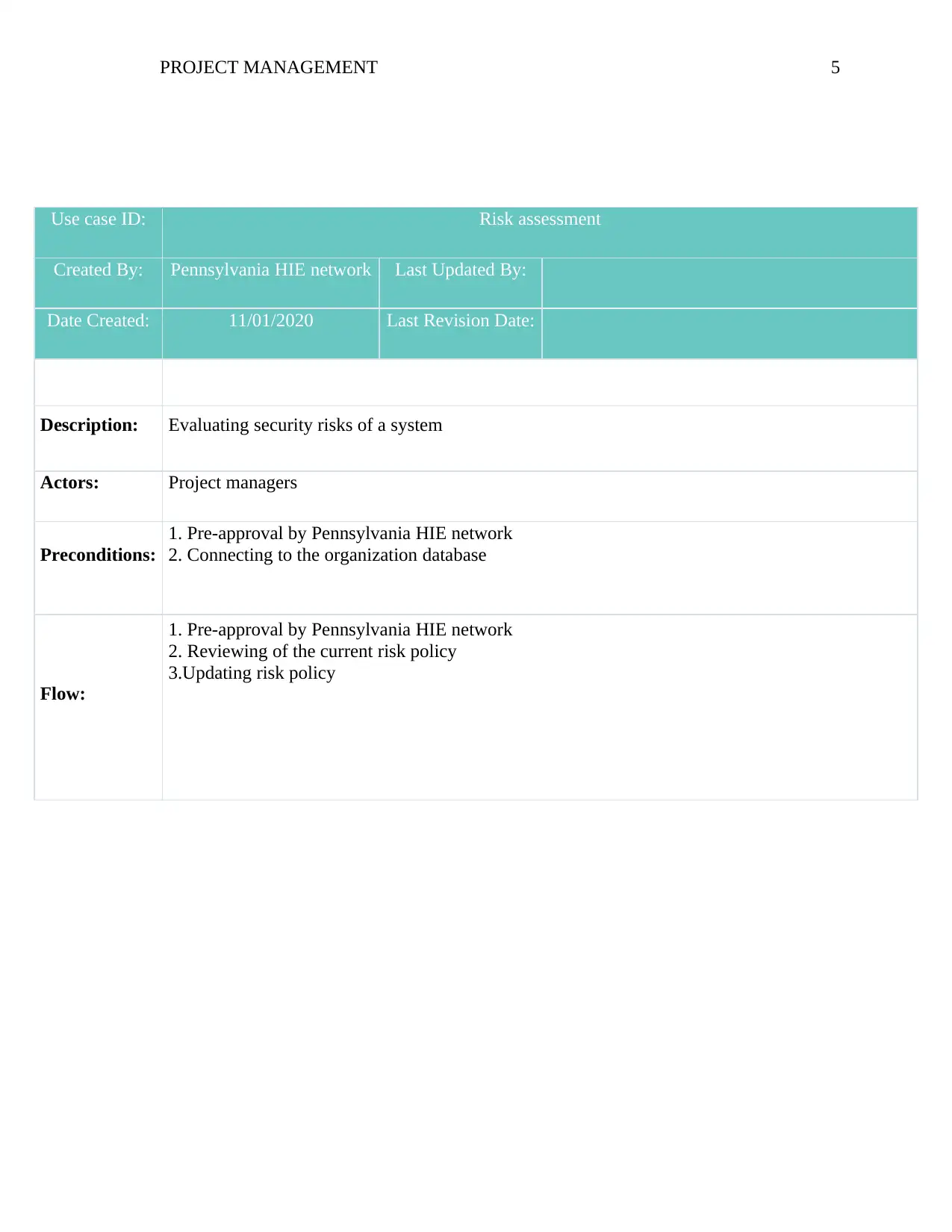
Use case ID: Risk assessment
Created By: Pennsylvania HIE network Last Updated By:
Date Created: 11/01/2020 Last Revision Date:
Description: Evaluating security risks of a system
Actors: Project managers
Preconditions:
1. Pre-approval by Pennsylvania HIE network
2. Connecting to the organization database
Flow:
1. Pre-approval by Pennsylvania HIE network
2. Reviewing of the current risk policy
3.Updating risk policy
Use case ID: Risk assessment
Created By: Pennsylvania HIE network Last Updated By:
Date Created: 11/01/2020 Last Revision Date:
Description: Evaluating security risks of a system
Actors: Project managers
Preconditions:
1. Pre-approval by Pennsylvania HIE network
2. Connecting to the organization database
Flow:
1. Pre-approval by Pennsylvania HIE network
2. Reviewing of the current risk policy
3.Updating risk policy
PROJECT MANAGEMENT 6
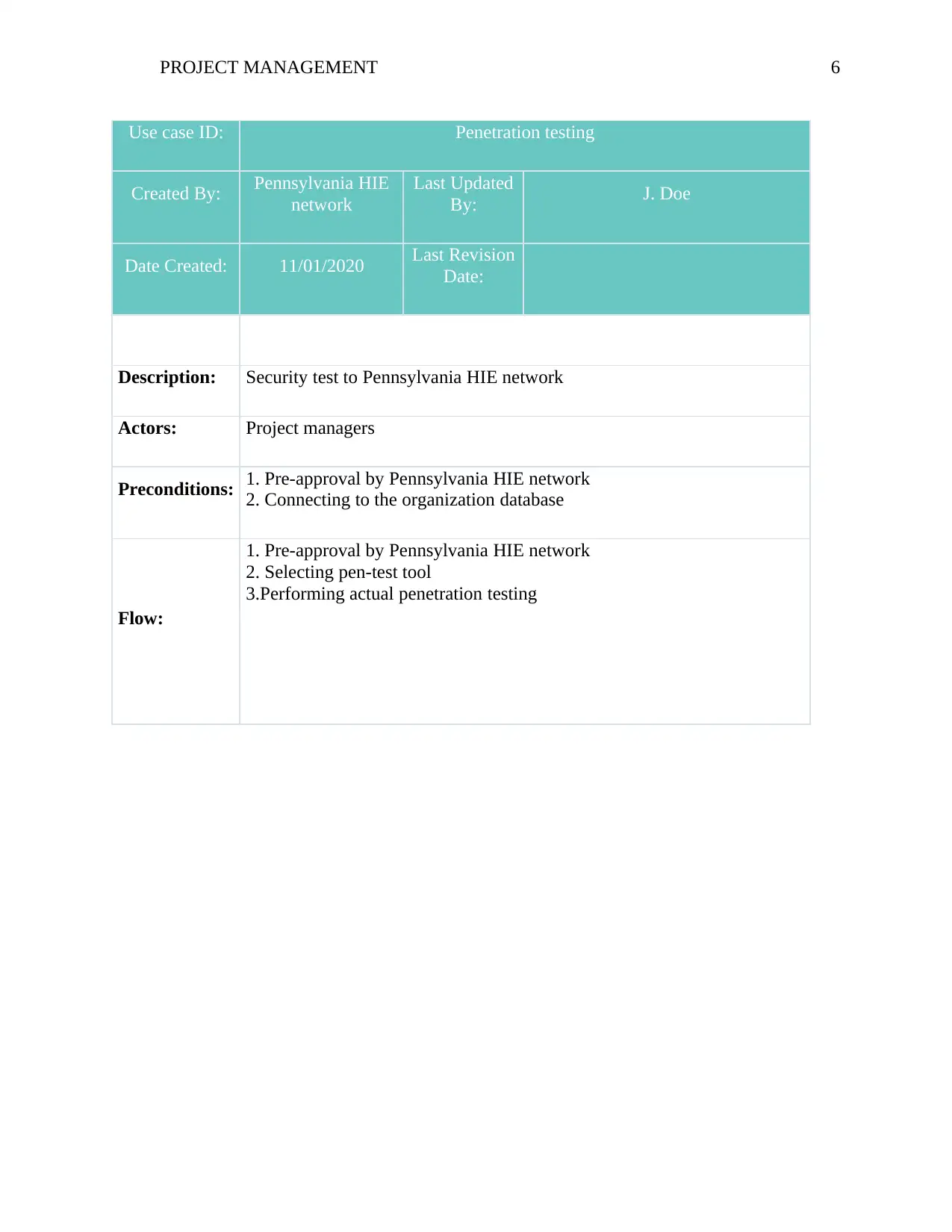
Use case ID: Penetration testing
Created By: Pennsylvania HIE
network
Last Updated
By: J. Doe
Date Created: 11/01/2020 Last Revision
Date:
Description: Security test to Pennsylvania HIE network
Actors: Project managers
Preconditions: 1. Pre-approval by Pennsylvania HIE network
2. Connecting to the organization database
Flow:
1. Pre-approval by Pennsylvania HIE network
2. Selecting pen-test tool
3.Performing actual penetration testing
Use case ID: Penetration testing
Created By: Pennsylvania HIE
network
Last Updated
By: J. Doe
Date Created: 11/01/2020 Last Revision
Date:
Description: Security test to Pennsylvania HIE network
Actors: Project managers
Preconditions: 1. Pre-approval by Pennsylvania HIE network
2. Connecting to the organization database
Flow:
1. Pre-approval by Pennsylvania HIE network
2. Selecting pen-test tool
3.Performing actual penetration testing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
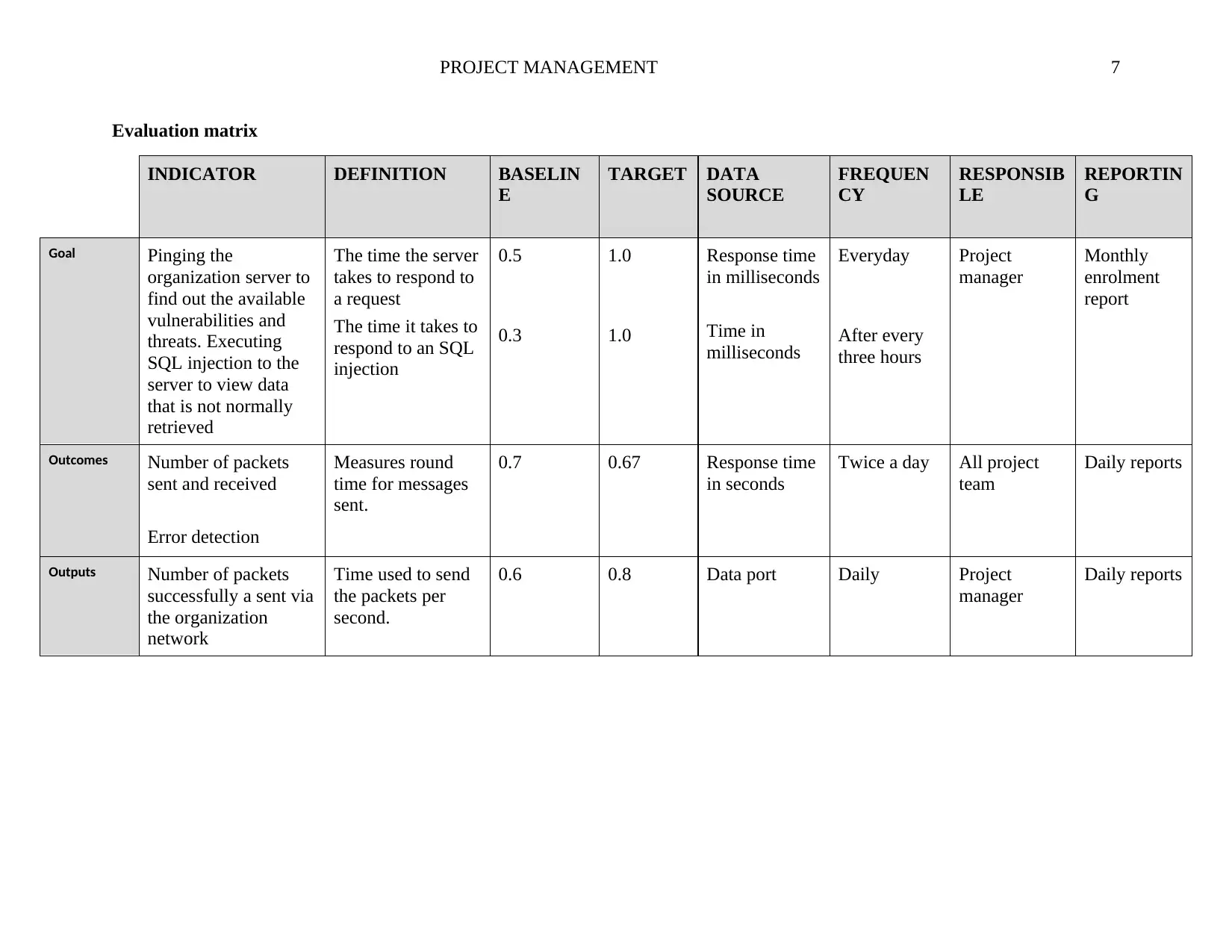
PROJECT MANAGEMENT 7
Evaluation matrix
INDICATOR DEFINITION BASELIN
E
TARGET DATA
SOURCE
FREQUEN
CY
RESPONSIB
LE
REPORTIN
G
Goal Pinging the
organization server to
find out the available
vulnerabilities and
threats. Executing
SQL injection to the
server to view data
that is not normally
retrieved
The time the server
takes to respond to
a request
The time it takes to
respond to an SQL
injection
0.5
0.3
1.0
1.0
Response time
in milliseconds
Time in
milliseconds
Everyday
After every
three hours
Project
manager
Monthly
enrolment
report
Outcomes Number of packets
sent and received
Error detection
Measures round
time for messages
sent.
0.7 0.67 Response time
in seconds
Twice a day All project
team
Daily reports
Outputs Number of packets
successfully a sent via
the organization
network
Time used to send
the packets per
second.
0.6 0.8 Data port Daily Project
manager
Daily reports
Evaluation matrix
INDICATOR DEFINITION BASELIN
E
TARGET DATA
SOURCE
FREQUEN
CY
RESPONSIB
LE
REPORTIN
G
Goal Pinging the
organization server to
find out the available
vulnerabilities and
threats. Executing
SQL injection to the
server to view data
that is not normally
retrieved
The time the server
takes to respond to
a request
The time it takes to
respond to an SQL
injection
0.5
0.3
1.0
1.0
Response time
in milliseconds
Time in
milliseconds
Everyday
After every
three hours
Project
manager
Monthly
enrolment
report
Outcomes Number of packets
sent and received
Error detection
Measures round
time for messages
sent.
0.7 0.67 Response time
in seconds
Twice a day All project
team
Daily reports
Outputs Number of packets
successfully a sent via
the organization
network
Time used to send
the packets per
second.
0.6 0.8 Data port Daily Project
manager
Daily reports
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
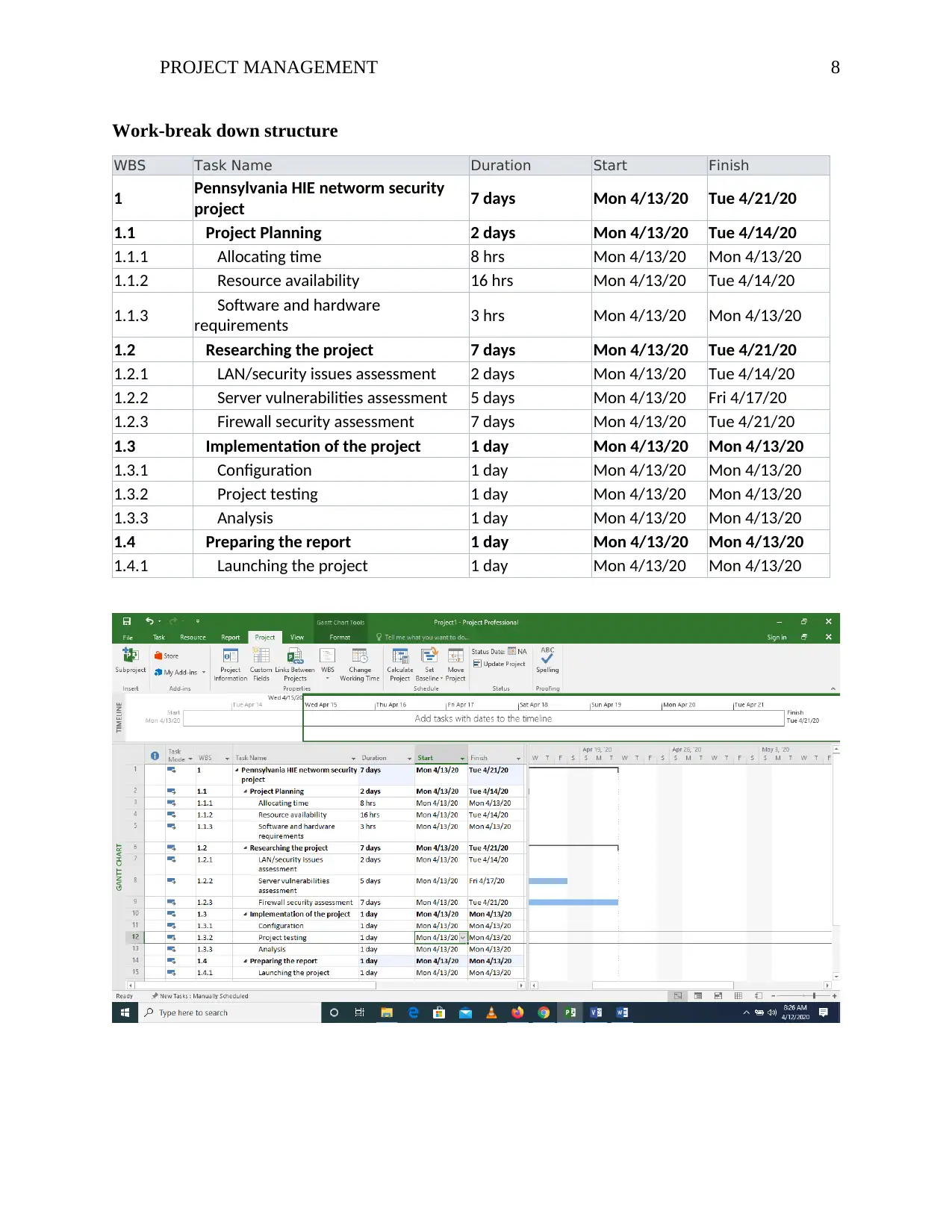
PROJECT MANAGEMENT 8
Work-break down structure
WBS Task Name Duration Start Finish
1 Pennsylvania HIE networm security
project 7 days Mon 4/13/20 Tue 4/21/20
1.1 Project Planning 2 days Mon 4/13/20 Tue 4/14/20
1.1.1 Allocating time 8 hrs Mon 4/13/20 Mon 4/13/20
1.1.2 Resource availability 16 hrs Mon 4/13/20 Tue 4/14/20
1.1.3 Software and hardware
requirements 3 hrs Mon 4/13/20 Mon 4/13/20
1.2 Researching the project 7 days Mon 4/13/20 Tue 4/21/20
1.2.1 LAN/security issues assessment 2 days Mon 4/13/20 Tue 4/14/20
1.2.2 Server vulnerabilities assessment 5 days Mon 4/13/20 Fri 4/17/20
1.2.3 Firewall security assessment 7 days Mon 4/13/20 Tue 4/21/20
1.3 Implementation of the project 1 day Mon 4/13/20 Mon 4/13/20
1.3.1 Configuration 1 day Mon 4/13/20 Mon 4/13/20
1.3.2 Project testing 1 day Mon 4/13/20 Mon 4/13/20
1.3.3 Analysis 1 day Mon 4/13/20 Mon 4/13/20
1.4 Preparing the report 1 day Mon 4/13/20 Mon 4/13/20
1.4.1 Launching the project 1 day Mon 4/13/20 Mon 4/13/20
Work-break down structure
WBS Task Name Duration Start Finish
1 Pennsylvania HIE networm security
project 7 days Mon 4/13/20 Tue 4/21/20
1.1 Project Planning 2 days Mon 4/13/20 Tue 4/14/20
1.1.1 Allocating time 8 hrs Mon 4/13/20 Mon 4/13/20
1.1.2 Resource availability 16 hrs Mon 4/13/20 Tue 4/14/20
1.1.3 Software and hardware
requirements 3 hrs Mon 4/13/20 Mon 4/13/20
1.2 Researching the project 7 days Mon 4/13/20 Tue 4/21/20
1.2.1 LAN/security issues assessment 2 days Mon 4/13/20 Tue 4/14/20
1.2.2 Server vulnerabilities assessment 5 days Mon 4/13/20 Fri 4/17/20
1.2.3 Firewall security assessment 7 days Mon 4/13/20 Tue 4/21/20
1.3 Implementation of the project 1 day Mon 4/13/20 Mon 4/13/20
1.3.1 Configuration 1 day Mon 4/13/20 Mon 4/13/20
1.3.2 Project testing 1 day Mon 4/13/20 Mon 4/13/20
1.3.3 Analysis 1 day Mon 4/13/20 Mon 4/13/20
1.4 Preparing the report 1 day Mon 4/13/20 Mon 4/13/20
1.4.1 Launching the project 1 day Mon 4/13/20 Mon 4/13/20
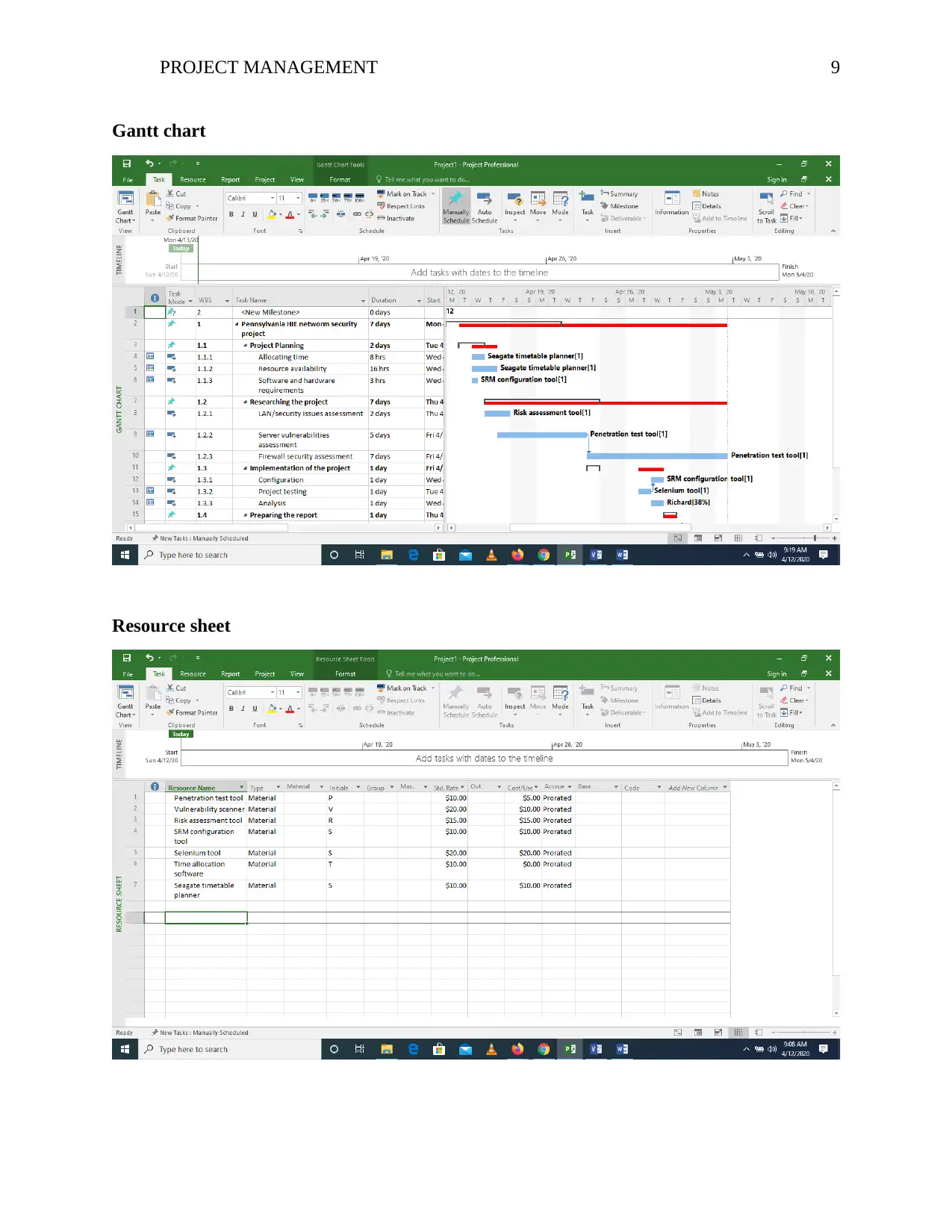
PROJECT MANAGEMENT 9
Gantt chart
Resource sheet
Gantt chart
Resource sheet
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
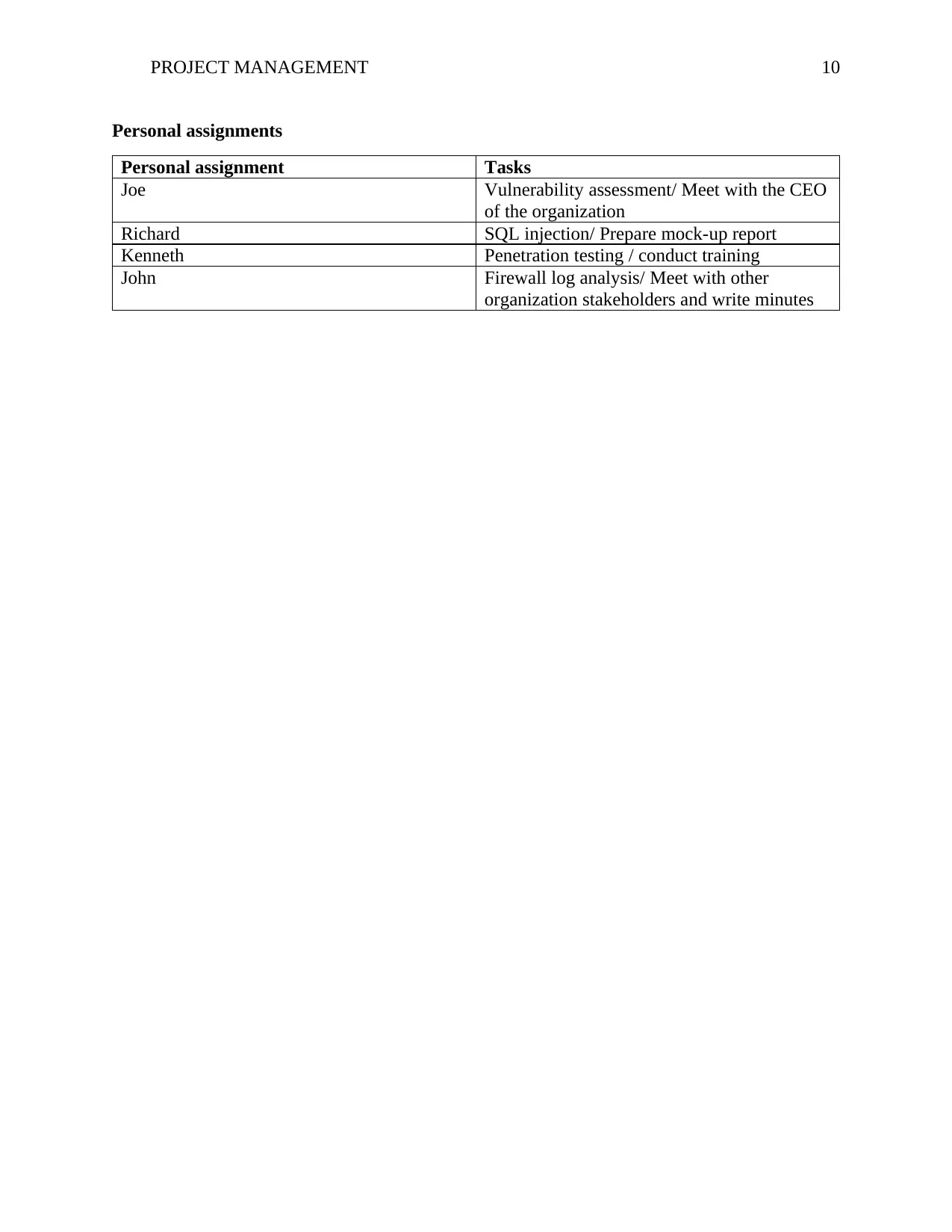
PROJECT MANAGEMENT 10
Personal assignments
Personal assignment Tasks
Joe Vulnerability assessment/ Meet with the CEO
of the organization
Richard SQL injection/ Prepare mock-up report
Kenneth Penetration testing / conduct training
John Firewall log analysis/ Meet with other
organization stakeholders and write minutes
Personal assignments
Personal assignment Tasks
Joe Vulnerability assessment/ Meet with the CEO
of the organization
Richard SQL injection/ Prepare mock-up report
Kenneth Penetration testing / conduct training
John Firewall log analysis/ Meet with other
organization stakeholders and write minutes
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.