Ethical Hacking and Penetration Testing : Presentation
VerifiedAdded on 2022/08/12
|10
|689
|39
Presentation
AI Summary
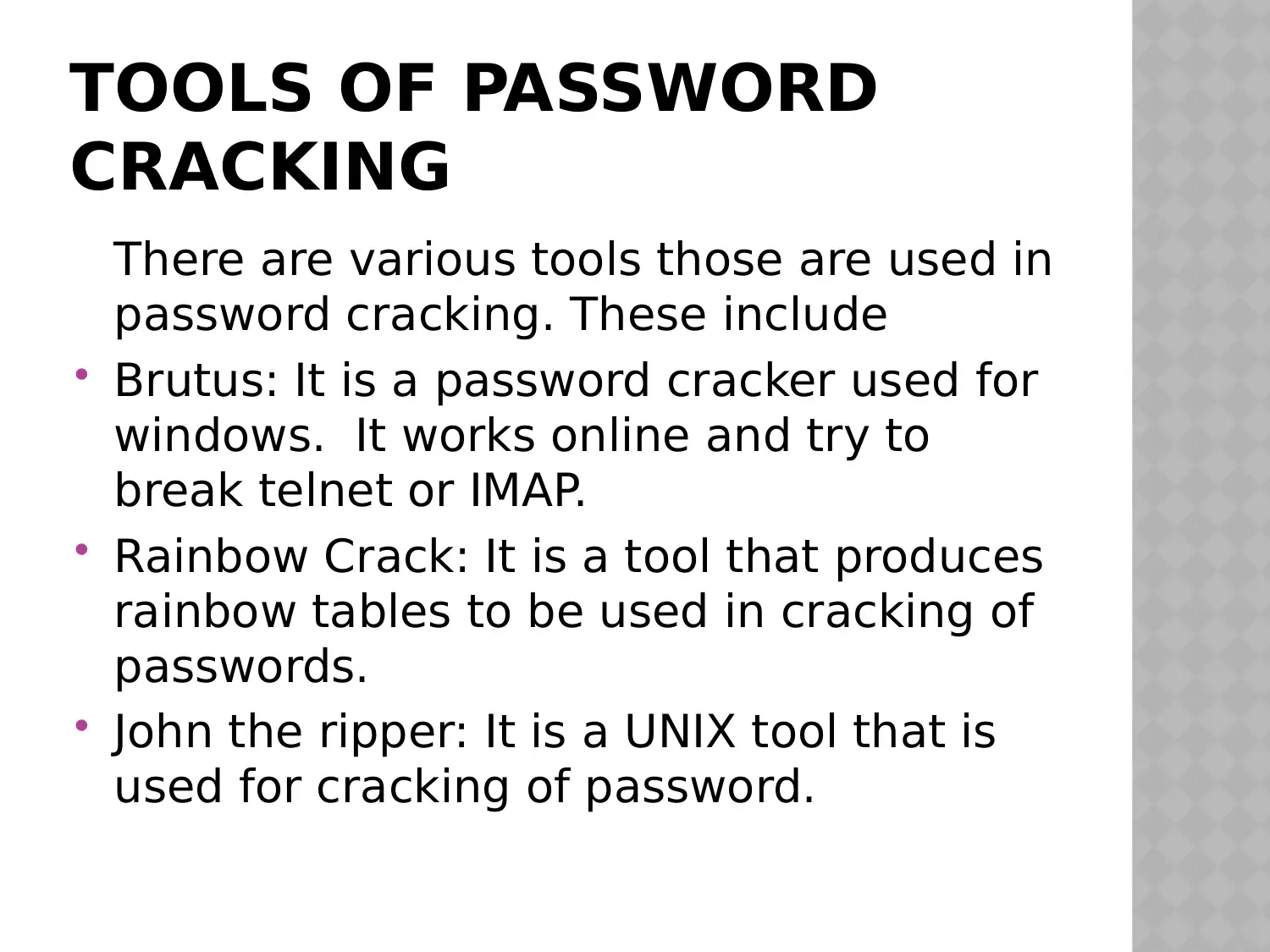
As the Lead Security Analyst in your organization, you have been asked by the Chief Security Officer to prepare a presentation to introduce concepts, skills, and tools used by hackers to compromise systems. You should include information about the following: What is a hash, and how does it play a role with passwords? What are the locations of passwords in each of the following: UNIX/Linux Windows Mac OSX What are the methods or permissions needed to view the passwords for all three operating systems? Describe the process of password cracking, and include a discussion about the following attacks: Dictionary Brute force Rainbow tables Describe at least 3 tools used for password cracking; include at least 1 for Windows and 1 for UNIX/Linux. note- PowerPoint presentation: 8–10 slides
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
1 out of 10













![[object Object]](/_next/static/media/star-bottom.7253800d.svg)