Ethical Hacking: Teaching and Implications
VerifiedAdded on 2020/05/04
|19
|5428
|271
AI Summary
This assignment delves into the complex world of ethical hacking education. It analyzes the legal and ethical ramifications of teaching hacking techniques to students, emphasizing the importance of responsible practices and adherence to ethical guidelines. The assignment considers various perspectives on this topic, including the benefits and risks associated with teaching hacking skills in an academic setting.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Research proposal on ethical hacking 1
RESEARCH PROPOSAL ON ETHICAL HACKING
By (Name)
Course
Instructor’s Name
Institutional Affiliation
The City and State
The Date
RESEARCH PROPOSAL ON ETHICAL HACKING
By (Name)
Course
Instructor’s Name
Institutional Affiliation
The City and State
The Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Research proposal on ethical hacking 2
Abstract;
For decades, there has been a substantial and dynamic change in the level of technology.
However, the dynamic change of technology has come along with high levels of insecurity, there
has been recurring cases of information insecurity in form of hacking and cybercrime which has
caused serious breaching of rights, linking of confidential information, loss of money through
credit cards and identity theft among others. One of the solutions created to cub some of these
risks include Ethical Hacking which tends to increase security protection by identifying security
vulnerabilities in a system.
Therefore, this research is to critically investigate, analyze and establish the extent to
which ethical hacking has contributed to the prevention of system hacking/ internet hacking, both
positive and negative. In other words, the research will aim at answering the question, “is
hacking really ethical?”
Introduction:
An increase in growth of internet and technology has brought great things such as Net
banking, Cloud Computing, Email, Social Media among others, but there is a Dark side known
as Hacking, Back doors, breaching our right to privacy. It is the biggest problem faced by many
organizations, people, government and private companies all over the world (Wilhelm 2009).
Hacking can be in any form from abducting credit card numbers to reading emails and recording
videos by the camera of your own devices (Veruggio et al 2016, p.2160). But there is also a good
side of hacking known as ethical hacking where white-collar hackers come in that is to say they
help people from hacking or people who are suffered by hacking. Security for our systems is
vital in protecting data (Yang 2009, p.20). The paper is meant to describe the meaning of
Abstract;
For decades, there has been a substantial and dynamic change in the level of technology.
However, the dynamic change of technology has come along with high levels of insecurity, there
has been recurring cases of information insecurity in form of hacking and cybercrime which has
caused serious breaching of rights, linking of confidential information, loss of money through
credit cards and identity theft among others. One of the solutions created to cub some of these
risks include Ethical Hacking which tends to increase security protection by identifying security
vulnerabilities in a system.
Therefore, this research is to critically investigate, analyze and establish the extent to
which ethical hacking has contributed to the prevention of system hacking/ internet hacking, both
positive and negative. In other words, the research will aim at answering the question, “is
hacking really ethical?”
Introduction:
An increase in growth of internet and technology has brought great things such as Net
banking, Cloud Computing, Email, Social Media among others, but there is a Dark side known
as Hacking, Back doors, breaching our right to privacy. It is the biggest problem faced by many
organizations, people, government and private companies all over the world (Wilhelm 2009).
Hacking can be in any form from abducting credit card numbers to reading emails and recording
videos by the camera of your own devices (Veruggio et al 2016, p.2160). But there is also a good
side of hacking known as ethical hacking where white-collar hackers come in that is to say they
help people from hacking or people who are suffered by hacking. Security for our systems is
vital in protecting data (Yang 2009, p.20). The paper is meant to describe the meaning of

Research proposal on ethical hacking 3
hacking, the aims of ethical hacking, how it is trained and how it affects the world IT
department, in relation to already written articles (Venter and Eloff 2000, p.15).
The growth of internet has brought many good things such as electronic commerce, e-
mail, easy access to vast stores of reference material among others. However, to maintain the
relevance of dynamism in the internet, there is need to maintain high levels of security and one
of the more effective ways of testing system security is by ethical hacking. Using an ethical
hacking technique, activities focus on to identify, and exploit security vulnerabilities and
subsequent implementation of corrective measures (Logan and Clarkson 2005). Through the
ethical hacking process, organizations are able to evaluate the extent of success or failure of their
current security measures and also to prevent criminal hackers who can secretly link the
organization’s information to unauthorized parties, putting the company at a danger (Graves
2010). These types of hackers are called black hat hackers, and in order to overcome such major/
alarming issue, another type of hackers came in place and these are the ethical hackers (Hafele
2004).
Various research has been carried out on ethical hackers, their skills and how they go
about helping their customers. It is noted that ethical hackers perform the hack as security tests
for their systems and this type of hacking is legal and trustworthy. In other terms, ethical hacking
is the process of testing for the security level and availing the needs for the improvement of
technology (Reddy et al. 2010, p.189). It focuses on securing and protecting the IP systems.
According to a research made, understanding an ethical hacker is more complicated than
understanding the public itself (Farsole et al 2010, p.15). Technology is ever growing and we are
facing tools and gadgets that are beneficial to people depending on their usage, and on the other
side, they are more vulnerable to hacking. This is where ethical hacking comes in as a preventive
hacking, the aims of ethical hacking, how it is trained and how it affects the world IT
department, in relation to already written articles (Venter and Eloff 2000, p.15).
The growth of internet has brought many good things such as electronic commerce, e-
mail, easy access to vast stores of reference material among others. However, to maintain the
relevance of dynamism in the internet, there is need to maintain high levels of security and one
of the more effective ways of testing system security is by ethical hacking. Using an ethical
hacking technique, activities focus on to identify, and exploit security vulnerabilities and
subsequent implementation of corrective measures (Logan and Clarkson 2005). Through the
ethical hacking process, organizations are able to evaluate the extent of success or failure of their
current security measures and also to prevent criminal hackers who can secretly link the
organization’s information to unauthorized parties, putting the company at a danger (Graves
2010). These types of hackers are called black hat hackers, and in order to overcome such major/
alarming issue, another type of hackers came in place and these are the ethical hackers (Hafele
2004).
Various research has been carried out on ethical hackers, their skills and how they go
about helping their customers. It is noted that ethical hackers perform the hack as security tests
for their systems and this type of hacking is legal and trustworthy. In other terms, ethical hacking
is the process of testing for the security level and availing the needs for the improvement of
technology (Reddy et al. 2010, p.189). It focuses on securing and protecting the IP systems.
According to a research made, understanding an ethical hacker is more complicated than
understanding the public itself (Farsole et al 2010, p.15). Technology is ever growing and we are
facing tools and gadgets that are beneficial to people depending on their usage, and on the other
side, they are more vulnerable to hacking. This is where ethical hacking comes in as a preventive

Research proposal on ethical hacking 4
step in ensuring the information safety (Krutz and Vines 2007). It constitutes tools that can find
and exploit a security weakness. Ethical hackers use the same tools and techniques of hackers to
test and evaluate system security. It is an effective tool that can assist companies, people and
government to protect data against hackers if used ethically well.
This therefore brings as to the point that, information security holds an important place
in information technology and information system as a whole. Computers and systems use as
many updates as new technologies come up day after day some of which include; cloud
computing, virtualization among others to be able to deal with security issues (Johnson 2017).
Ethical hackers must think and work carefully, that is the reason why all the academic
curriculum has the "attacker" and "defender” perspective for students to know how a hacker
thinks and performs attacks and how to defend them by adjusting their systems, policies, and
architecture accordingly (Engebretson 2013). With keeping all of the above in mind, ethical
hacking has become talk of the town. Students are being taught hacking at schools, organizations
have been setup providing hacking courses and certifications for individuals which has led to
increase in the number of hackers in down side towns and they are mostly trained to aid in the
prevention of cybercrimes and hacking (Graves 2007). Questions are being raised such as is
ethical hacking solving our problems or creating new ones? Ethics form a core part of any
activity as breaking the ethics or not having any may cause damage instead of benefit. Logan and
Chatzidakis and Mitussis (2007) found that a course in information and security should
emphasize the ethical responsibility of the security professional who are entrusted to protect data
assets. So, ethical hacking is an assessment to check and test an information technological
environment for possible links and vulnerabilities. It describes the process of hacking a network
in an ethical way.
step in ensuring the information safety (Krutz and Vines 2007). It constitutes tools that can find
and exploit a security weakness. Ethical hackers use the same tools and techniques of hackers to
test and evaluate system security. It is an effective tool that can assist companies, people and
government to protect data against hackers if used ethically well.
This therefore brings as to the point that, information security holds an important place
in information technology and information system as a whole. Computers and systems use as
many updates as new technologies come up day after day some of which include; cloud
computing, virtualization among others to be able to deal with security issues (Johnson 2017).
Ethical hackers must think and work carefully, that is the reason why all the academic
curriculum has the "attacker" and "defender” perspective for students to know how a hacker
thinks and performs attacks and how to defend them by adjusting their systems, policies, and
architecture accordingly (Engebretson 2013). With keeping all of the above in mind, ethical
hacking has become talk of the town. Students are being taught hacking at schools, organizations
have been setup providing hacking courses and certifications for individuals which has led to
increase in the number of hackers in down side towns and they are mostly trained to aid in the
prevention of cybercrimes and hacking (Graves 2007). Questions are being raised such as is
ethical hacking solving our problems or creating new ones? Ethics form a core part of any
activity as breaking the ethics or not having any may cause damage instead of benefit. Logan and
Chatzidakis and Mitussis (2007) found that a course in information and security should
emphasize the ethical responsibility of the security professional who are entrusted to protect data
assets. So, ethical hacking is an assessment to check and test an information technological
environment for possible links and vulnerabilities. It describes the process of hacking a network
in an ethical way.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Research proposal on ethical hacking 5
Then another question may arise of what generally is ethical hacking? It can be defined
as breaking into a computer system with an aim of securing an information environment. Ethical
comes in to put a positive touch and explain something normal and legal because it is assumed
that hacking is illegal so ethical comes in to legalize it (Harper et al 2011). Hacking describes the
process of attacking computer systems and get access to certain information. Ethical hacking can
be categorized as an assessment of security, a kind of evaluating, or a test of security of an
information technology environment. An ethical hack shows the risk an IT environment is facing
and actions that can be taken to reduce this risk. Ethical hacking therefore perfectly fit in the
security life cycle which includes planning, policy enforcement or implications, monitoring and
managing, intrusion detection, security assessment, threat analysis, and security policy creation.
As the name ethical hacking tells, the idea has something to do with hacking which refers to the
profession of working with computers by breaking into it (Tavani 2011).
Aim of the research.
Ethical hacking has been a vital topic given the contribution of information technology in
the society. There has been a lot of arguments as on if it is actually ethical or not due to the
incidents in the past, of misusing the same tools used for a good purpose for accomplishing
illegal intentions (Harvey 2004.). As intentions of people cannot be determined to understand the
motives of each ethical hacker, and it’s quite difficult Issue pertaining to it (Harvey 2004). It has
been highlighted in the media and there have been reports that over 90% of the attacks happen on
the inside. There is a question that has ethical hacking reduced problems or has it created new
ones? Research has been done in this report to find out if hacking should be taught to students,
and should it be legalized or not. Logan and Clarkson said intention of the person may depend if
he wants to use it for good or bad (Veruggio and Bekey 2016, p.2160). Questions like should
Then another question may arise of what generally is ethical hacking? It can be defined
as breaking into a computer system with an aim of securing an information environment. Ethical
comes in to put a positive touch and explain something normal and legal because it is assumed
that hacking is illegal so ethical comes in to legalize it (Harper et al 2011). Hacking describes the
process of attacking computer systems and get access to certain information. Ethical hacking can
be categorized as an assessment of security, a kind of evaluating, or a test of security of an
information technology environment. An ethical hack shows the risk an IT environment is facing
and actions that can be taken to reduce this risk. Ethical hacking therefore perfectly fit in the
security life cycle which includes planning, policy enforcement or implications, monitoring and
managing, intrusion detection, security assessment, threat analysis, and security policy creation.
As the name ethical hacking tells, the idea has something to do with hacking which refers to the
profession of working with computers by breaking into it (Tavani 2011).
Aim of the research.
Ethical hacking has been a vital topic given the contribution of information technology in
the society. There has been a lot of arguments as on if it is actually ethical or not due to the
incidents in the past, of misusing the same tools used for a good purpose for accomplishing
illegal intentions (Harvey 2004.). As intentions of people cannot be determined to understand the
motives of each ethical hacker, and it’s quite difficult Issue pertaining to it (Harvey 2004). It has
been highlighted in the media and there have been reports that over 90% of the attacks happen on
the inside. There is a question that has ethical hacking reduced problems or has it created new
ones? Research has been done in this report to find out if hacking should be taught to students,
and should it be legalized or not. Logan and Clarkson said intention of the person may depend if
he wants to use it for good or bad (Veruggio and Bekey 2016, p.2160). Questions like should

Research proposal on ethical hacking 6
faculties teach ethical hacking to students? Should the students be screened before them sign-up
for a course in hacking? And many others have been posed already, The response received
showed a clear picture but was limited to few aspects such as should it be made mandatory for all
computer science students to learn at least one aspect of hacking which might help in giving
them a little grasp of the subject and should they be authorized to take actions? And other
questions plus arguments were raised (Foulger et al. 2009, p.10). The aim of this research proposal
is to address the above questions and other main questions like;
Does really ethical hacking follow the ethics?
Should ethical hacking be legalized?
Should it be taught to young students?
Is there an impact brought by ethical hacking to the modern society?
How has ethical hacking contributed to the development of the information
technology environment?
How is the ethical hacking process developed?
Getting the response to these questions will help in understanding and focusing on the
real underlying issue of ethical hacking being used as a defensive tool for securing our systems.
As earlier referred to, Logan and Clarkson added that a deep insight in the background of the
student might help in identifying if he is eligible for studying ethical hacking (Graves 2010).
Background and literature review
To obtain answers for the critical questions above, an assessment was made for our
research proposal in the form of an online survey technique and consultations of different articles
based on qualitative research analysis.
faculties teach ethical hacking to students? Should the students be screened before them sign-up
for a course in hacking? And many others have been posed already, The response received
showed a clear picture but was limited to few aspects such as should it be made mandatory for all
computer science students to learn at least one aspect of hacking which might help in giving
them a little grasp of the subject and should they be authorized to take actions? And other
questions plus arguments were raised (Foulger et al. 2009, p.10). The aim of this research proposal
is to address the above questions and other main questions like;
Does really ethical hacking follow the ethics?
Should ethical hacking be legalized?
Should it be taught to young students?
Is there an impact brought by ethical hacking to the modern society?
How has ethical hacking contributed to the development of the information
technology environment?
How is the ethical hacking process developed?
Getting the response to these questions will help in understanding and focusing on the
real underlying issue of ethical hacking being used as a defensive tool for securing our systems.
As earlier referred to, Logan and Clarkson added that a deep insight in the background of the
student might help in identifying if he is eligible for studying ethical hacking (Graves 2010).
Background and literature review
To obtain answers for the critical questions above, an assessment was made for our
research proposal in the form of an online survey technique and consultations of different articles
based on qualitative research analysis.

Research proposal on ethical hacking 7
In our results/ analysis, we found out that Ethical hacking has been in existence and it has
been a very curtail tool used by almost the entire major organizations for advancing their security
tactics. The first ever ethical hacking team formed was back in 1950 called Tiger team which
helped in securing the system. Another famous incident in 2011 where about 77 million Sony
PlayStation accounts were compromised by a hacking group known as Lulzsec which made all
the PlayStation services to go down and led to heavy loss of data and made people think that
there was always a possibility of attack (Nelson 2014, p.520).
Jami and Khan (2011) describes the case of Morris, a student at MIT who developed the
Morris worm which caused severe crashing of about 2000 PCs in only a duration of few hours,
experts were able to stop the worm immediately by putting a great effort. The case of Morris
worm shows that ethical hacking was supposed to be a defensive mechanism but its wrongful use
made its teaching doubtful. Morris was a high distinctive student, who had knowledge of security
but the questions comes what made him do such an activity, these kind of incidents lead us to
doubt if hacking is actually ethical or not and the say that every ethical hacker has his or her
intentions
In our review of Ethical Hacking and penetration Guide, Rafay (2013) justifies that
Ethical hacking follows ethics because it is recommended since it does not generate any log of
presence on the target system. The best example of this is to use Linked in, Facebook, among
other social networks to get information from the employees and to know their interests. This is
vital when performing phishing, key logging, browser exploitation, and other client side attacks
on the employees.
In our results/ analysis, we found out that Ethical hacking has been in existence and it has
been a very curtail tool used by almost the entire major organizations for advancing their security
tactics. The first ever ethical hacking team formed was back in 1950 called Tiger team which
helped in securing the system. Another famous incident in 2011 where about 77 million Sony
PlayStation accounts were compromised by a hacking group known as Lulzsec which made all
the PlayStation services to go down and led to heavy loss of data and made people think that
there was always a possibility of attack (Nelson 2014, p.520).
Jami and Khan (2011) describes the case of Morris, a student at MIT who developed the
Morris worm which caused severe crashing of about 2000 PCs in only a duration of few hours,
experts were able to stop the worm immediately by putting a great effort. The case of Morris
worm shows that ethical hacking was supposed to be a defensive mechanism but its wrongful use
made its teaching doubtful. Morris was a high distinctive student, who had knowledge of security
but the questions comes what made him do such an activity, these kind of incidents lead us to
doubt if hacking is actually ethical or not and the say that every ethical hacker has his or her
intentions
In our review of Ethical Hacking and penetration Guide, Rafay (2013) justifies that
Ethical hacking follows ethics because it is recommended since it does not generate any log of
presence on the target system. The best example of this is to use Linked in, Facebook, among
other social networks to get information from the employees and to know their interests. This is
vital when performing phishing, key logging, browser exploitation, and other client side attacks
on the employees.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Research proposal on ethical hacking 8
According to Reddy (2010), the hacking process is planned in advance; all the technical
management and strategically issues must be considered. Planning is crucial for any amount of
testing from a simple password test to all penetration test on a web application. Backup data
must be ensured, if not the testing may be called off unexpectedly if someone claims they never
authorized for the tests and the process involves specific systems to be tested, risks that involves,
test preparation schedule, gather and explore knowledge among others
On the other side, Harper et al (2011) gives a brief statement of a young hacker from the
UK Hutchins who stopped the world’s biggest hacking attack in the history, by finding a kill
switch in the attack script. This type of incident shows the bright side of ethical hacking.
Through keeping these things in mind, it is said that, regulated use of hacking will be under
ethics and leads us to further investigation about the topic.
Training students to be ethical professionals should begin with an instructor as quoted by
Logan & Clarkson (2005) by finding an ethical solution to the problem which may help in
regulating its use and demonstrating legal practice which will certainly aid in the betterment of
ethical behavior of students guidelines and punishment for inappropriate computer morals,
among other items. Pastel (2006) quoted that it is still necessary for the documentation of
guidelines and punishment for inappropriate computer behavior, among other items.
Kaupins and Park (2011) found out that protecting current system and networks requires a
wide understanding of the strategies which may attack and affect the system and should have
depth knowledge of the hacker’s tactics, tools and motivations. He went on and clarifies that
effective ethical hacking is based on the knowledge of the system network, equipment, user
According to Reddy (2010), the hacking process is planned in advance; all the technical
management and strategically issues must be considered. Planning is crucial for any amount of
testing from a simple password test to all penetration test on a web application. Backup data
must be ensured, if not the testing may be called off unexpectedly if someone claims they never
authorized for the tests and the process involves specific systems to be tested, risks that involves,
test preparation schedule, gather and explore knowledge among others
On the other side, Harper et al (2011) gives a brief statement of a young hacker from the
UK Hutchins who stopped the world’s biggest hacking attack in the history, by finding a kill
switch in the attack script. This type of incident shows the bright side of ethical hacking.
Through keeping these things in mind, it is said that, regulated use of hacking will be under
ethics and leads us to further investigation about the topic.
Training students to be ethical professionals should begin with an instructor as quoted by
Logan & Clarkson (2005) by finding an ethical solution to the problem which may help in
regulating its use and demonstrating legal practice which will certainly aid in the betterment of
ethical behavior of students guidelines and punishment for inappropriate computer morals,
among other items. Pastel (2006) quoted that it is still necessary for the documentation of
guidelines and punishment for inappropriate computer behavior, among other items.
Kaupins and Park (2011) found out that protecting current system and networks requires a
wide understanding of the strategies which may attack and affect the system and should have
depth knowledge of the hacker’s tactics, tools and motivations. He went on and clarifies that
effective ethical hacking is based on the knowledge of the system network, equipment, user

Research proposal on ethical hacking 9
intention, interaction policies, procedures, physical security and business culture. Furthermore,
the increasing use of social engineering attack methodologies calls for each tester as aware of the
organization and habits of its information technology users (Kaupins and Park 2011, p.92).
According to Regalado et al (2010), the important of ethical hacking is to test the
resources for a good cause and for the betterment of the technology. Technically it is penetration
testing which is focused on securing and protecting IT systems. It scans the computer’s networks
or the application and looks for potential weakness that could be used by the attackers to
accomplish their aims. It also magnifies the system by sending specific data to target the network
and based on its analysis of response received from the aim or target, it may be able to determine
many things such as open ports, services, operating system vulnerabilities among others.
Tiller (2004) starts with an overview of ethical hacking and the role of the ethical hacker.
She reviews the kinds of threats networks face, and introduces the five phases of ethical hacking,
from reconnaissance to covering your tracks. She also covers penetration-testing techniques and
tools. The materials map directly to the "Introduction to Ethical Hacking" competency from the
CEH Body of Knowledge, and provide an excellent jumping off point for the next courses in this
series. She also says that Ethical hacking is a key in strengthening network security, and it's one
of the most desired skills for any IT security professional when you're interested in becoming an
ethical hacker, or getting started to securing your own network. Therefore it has played a big role
in developing the information technology modern environment users
Research scope;
intention, interaction policies, procedures, physical security and business culture. Furthermore,
the increasing use of social engineering attack methodologies calls for each tester as aware of the
organization and habits of its information technology users (Kaupins and Park 2011, p.92).
According to Regalado et al (2010), the important of ethical hacking is to test the
resources for a good cause and for the betterment of the technology. Technically it is penetration
testing which is focused on securing and protecting IT systems. It scans the computer’s networks
or the application and looks for potential weakness that could be used by the attackers to
accomplish their aims. It also magnifies the system by sending specific data to target the network
and based on its analysis of response received from the aim or target, it may be able to determine
many things such as open ports, services, operating system vulnerabilities among others.
Tiller (2004) starts with an overview of ethical hacking and the role of the ethical hacker.
She reviews the kinds of threats networks face, and introduces the five phases of ethical hacking,
from reconnaissance to covering your tracks. She also covers penetration-testing techniques and
tools. The materials map directly to the "Introduction to Ethical Hacking" competency from the
CEH Body of Knowledge, and provide an excellent jumping off point for the next courses in this
series. She also says that Ethical hacking is a key in strengthening network security, and it's one
of the most desired skills for any IT security professional when you're interested in becoming an
ethical hacker, or getting started to securing your own network. Therefore it has played a big role
in developing the information technology modern environment users
Research scope;

Research proposal on ethical hacking 10
This is a secondary research which will cover a world wide scope by consulting already
written research in different articles and online survey to get the response to the proposed
research questions and carrying out different activities in the specific time period. The paper will
evaluate the concept of ethical hacking as to why it is developed, its roles to the IT environment
and the consequences (Palmer 2001). The documentation will vary depending on the area where
the scope covers and the amount of resources dedicated to data collection. The research will also
update the coverage of some documents, by establishing the existing gaps and identifying/
adding new information to the topic area (Kaupins and Park 2011, p.92).
Question
The main question being answered in this research proposal is generally “is ethical
hacking really ethical?” In other words, how does ethical hacking operates? And does it follow
ethics?
Hypothesis
This is a single guess that tentatively express good hunches, expected relationship
between independent and dependent variables. In our research proposal, we are expecting to get
firsthand information from our proposed resources which is expected to be an easy and quick
process and mainly our topic of ethical hacking will be fully analyzed. Individuals in our group
who don’t know this method of data collection shall be trained by technical experts and they are
expected to have the ability to gather relevant information (Nelson 2014, p.515).
For this research, our hypothesis will be “ethical hacking is ethical”
This is a secondary research which will cover a world wide scope by consulting already
written research in different articles and online survey to get the response to the proposed
research questions and carrying out different activities in the specific time period. The paper will
evaluate the concept of ethical hacking as to why it is developed, its roles to the IT environment
and the consequences (Palmer 2001). The documentation will vary depending on the area where
the scope covers and the amount of resources dedicated to data collection. The research will also
update the coverage of some documents, by establishing the existing gaps and identifying/
adding new information to the topic area (Kaupins and Park 2011, p.92).
Question
The main question being answered in this research proposal is generally “is ethical
hacking really ethical?” In other words, how does ethical hacking operates? And does it follow
ethics?
Hypothesis
This is a single guess that tentatively express good hunches, expected relationship
between independent and dependent variables. In our research proposal, we are expecting to get
firsthand information from our proposed resources which is expected to be an easy and quick
process and mainly our topic of ethical hacking will be fully analyzed. Individuals in our group
who don’t know this method of data collection shall be trained by technical experts and they are
expected to have the ability to gather relevant information (Nelson 2014, p.515).
For this research, our hypothesis will be “ethical hacking is ethical”
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Research proposal on ethical hacking 11
And from the hypothesis, an analysis and evaluation will be carried out basing on the
outcome of the research reports.
Research methodology
In our research the methodology used to get data was qualitative research methodology
based on both primary secondary research which is the analysis of the available literature and
collecting of firsthand information through online respectively. Secondary research is the
collection of data that was gathered earlier by other researchers, institutions, and Non-
government organization, extra. In our research, data was undertaken with care and diligence to
provide a cost-effective way of gaining a broad understanding of our research questions. This
research methodology provided a baseline in which we came to compare our collection results
which were got depending obviously on the focus of our study topic (Foulger et al. 2009, p.10). We
used this methodology to collect data from the following sources;
Scholarly journals; these contains of reports of original research and experimentation
written by experts in different fields. Articles undergo a peer review where other experts in the
same field review the same article for relevance and originality. Therefore by second hand
analysis, we will manage to review some articles in some of the scholarly journals written by
experts which are related to our topic of study (Logan and Clarkson 2005, p.157).
Reference books; by the above method of data collection, we referred to different books
in order to get a summary of the answer to our research questions for example handbooks,
manuals, encyclopedias, and dictionaries, plus other technical reports (Pike 2013, p.4).
And from the hypothesis, an analysis and evaluation will be carried out basing on the
outcome of the research reports.
Research methodology
In our research the methodology used to get data was qualitative research methodology
based on both primary secondary research which is the analysis of the available literature and
collecting of firsthand information through online respectively. Secondary research is the
collection of data that was gathered earlier by other researchers, institutions, and Non-
government organization, extra. In our research, data was undertaken with care and diligence to
provide a cost-effective way of gaining a broad understanding of our research questions. This
research methodology provided a baseline in which we came to compare our collection results
which were got depending obviously on the focus of our study topic (Foulger et al. 2009, p.10). We
used this methodology to collect data from the following sources;
Scholarly journals; these contains of reports of original research and experimentation
written by experts in different fields. Articles undergo a peer review where other experts in the
same field review the same article for relevance and originality. Therefore by second hand
analysis, we will manage to review some articles in some of the scholarly journals written by
experts which are related to our topic of study (Logan and Clarkson 2005, p.157).
Reference books; by the above method of data collection, we referred to different books
in order to get a summary of the answer to our research questions for example handbooks,
manuals, encyclopedias, and dictionaries, plus other technical reports (Pike 2013, p.4).

Research proposal on ethical hacking 12
Research constraints
During our research, we expect to acknowledge some limitations which would try to
hinder our data collection. These will give us an opportunity to demonstrate that we thought
critically about our research problem and that we understood the relevant literature published
about it. Limitations also show that we properly assessed the methods chosen for studying the
problem because the aim of the research is not only discovering new knowledge but also to
explore what we don’t know. Here among others are the challenges that we came across and how
they affected our work (Johnson 2017).
Lack of available and reliable data; we did not have enough reliable resources where we
could get firsthand information such as journals, articles, among other references. This limited
effective data collection since the scope of our study was based on a large size. By this we lacked
prior research studies on our topic and limited us to easily understand the research problem that
we were investigating on.
Access; since the study was secondary research, we were denied to access some of the
resources due to different reasons such as use of complicated languages by some of the authors,
access costs extra which hindered us from understanding the language to solve our research
problem. Exercise of selectivity; since our research topic covers a large sample area, and needs
consultation to many resources, reviewing of the information became overwhelmed by the large
volume of the sources available (Reddy et al. 2010). If the selection is not well done would lead us
to getting wrong information, it was also often difficult to determine the quality of some of the
data in question. More so, since in our sources the data was not collected for the same purpose as
Research constraints
During our research, we expect to acknowledge some limitations which would try to
hinder our data collection. These will give us an opportunity to demonstrate that we thought
critically about our research problem and that we understood the relevant literature published
about it. Limitations also show that we properly assessed the methods chosen for studying the
problem because the aim of the research is not only discovering new knowledge but also to
explore what we don’t know. Here among others are the challenges that we came across and how
they affected our work (Johnson 2017).
Lack of available and reliable data; we did not have enough reliable resources where we
could get firsthand information such as journals, articles, among other references. This limited
effective data collection since the scope of our study was based on a large size. By this we lacked
prior research studies on our topic and limited us to easily understand the research problem that
we were investigating on.
Access; since the study was secondary research, we were denied to access some of the
resources due to different reasons such as use of complicated languages by some of the authors,
access costs extra which hindered us from understanding the language to solve our research
problem. Exercise of selectivity; since our research topic covers a large sample area, and needs
consultation to many resources, reviewing of the information became overwhelmed by the large
volume of the sources available (Reddy et al. 2010). If the selection is not well done would lead us
to getting wrong information, it was also often difficult to determine the quality of some of the
data in question. More so, since in our sources the data was not collected for the same purpose as

Research proposal on ethical hacking 13
the original researcher had his or her own goals, the purpose of the original researcher’s
potentially biased our research.
Costs; the research is quite costly and involves some expenditures such as payments to
Access to possible instruments to search on some of the research questions like computers for
internet, Transport for each person to visit libraries where there are reliable resources such as
journals, Subsistence costs for each person such as food and drinks to enable each person to have
energy of carrying out the research, Special activities cost such as paying for expert to train some
of our group members to know how to carry out secondary research, Monitoring and evaluating
costs which involves cost of meeting and end of the research conference, Costs of consultancy
services such as asking other people on suitable resources to get firsthand information, among
some other small costs. These limited us to access some resources in the period where we had
unlimited funds (Khan 2010, p.11).
Measure used to collect data; in the process of the collection of data, sometimes by
interpreting the findings, you may discover that the way used to collect the data inhibited the
ability to conduct a thorough analysis of the results for example regretting of not including a
specific question or including an irrelevant one which could have helped to address a specific
area that emerged later in the study. By acknowledging this, we state a need for future
researchers to revise a specific method suitable for gathering data (Krutz and Vines 2007).
Research time table
Secondary research involves a systematic process that being objective and gathering
multitude information for analysis so that a researcher can come to the final resolution. Therefore
the original researcher had his or her own goals, the purpose of the original researcher’s
potentially biased our research.
Costs; the research is quite costly and involves some expenditures such as payments to
Access to possible instruments to search on some of the research questions like computers for
internet, Transport for each person to visit libraries where there are reliable resources such as
journals, Subsistence costs for each person such as food and drinks to enable each person to have
energy of carrying out the research, Special activities cost such as paying for expert to train some
of our group members to know how to carry out secondary research, Monitoring and evaluating
costs which involves cost of meeting and end of the research conference, Costs of consultancy
services such as asking other people on suitable resources to get firsthand information, among
some other small costs. These limited us to access some resources in the period where we had
unlimited funds (Khan 2010, p.11).
Measure used to collect data; in the process of the collection of data, sometimes by
interpreting the findings, you may discover that the way used to collect the data inhibited the
ability to conduct a thorough analysis of the results for example regretting of not including a
specific question or including an irrelevant one which could have helped to address a specific
area that emerged later in the study. By acknowledging this, we state a need for future
researchers to revise a specific method suitable for gathering data (Krutz and Vines 2007).
Research time table
Secondary research involves a systematic process that being objective and gathering
multitude information for analysis so that a researcher can come to the final resolution. Therefore
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
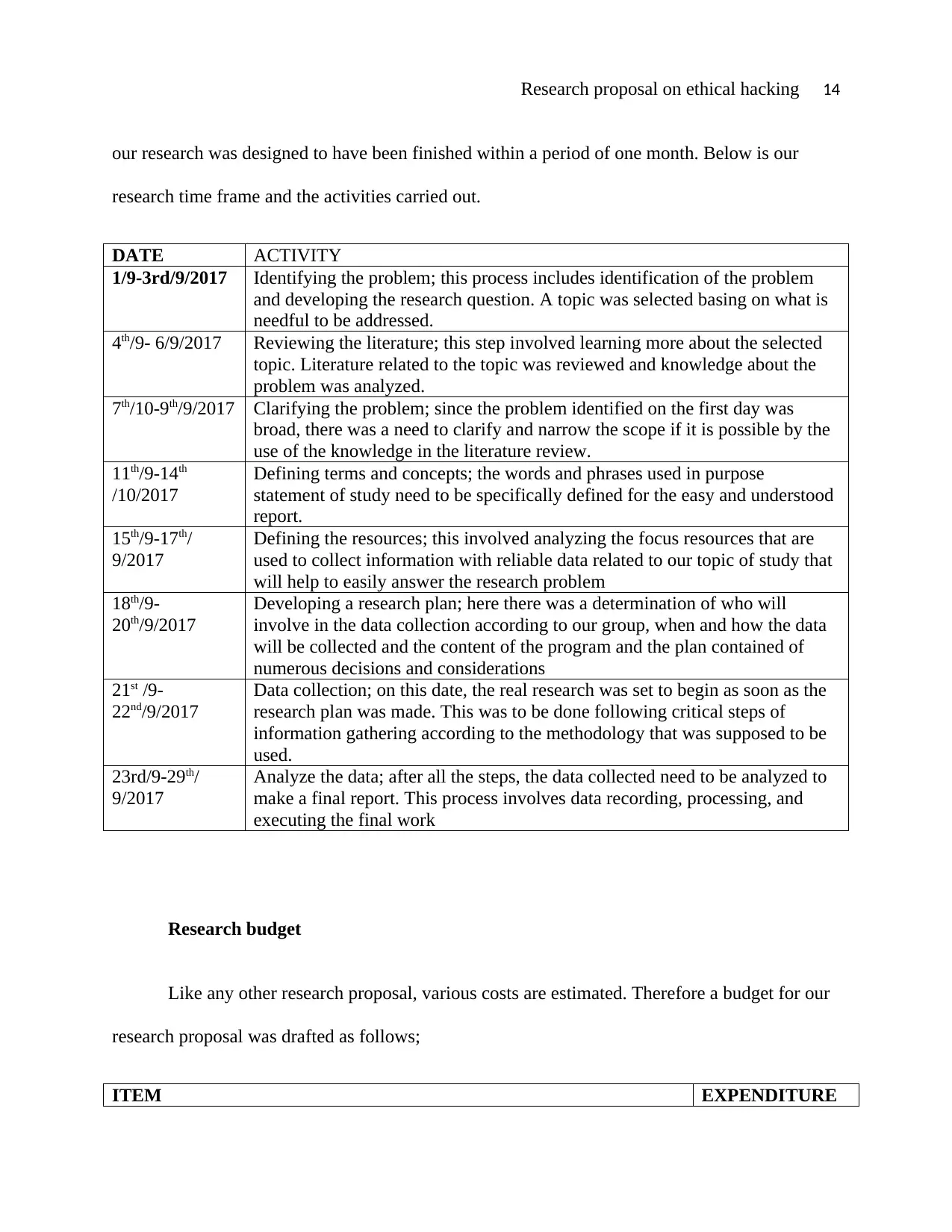
Research proposal on ethical hacking 14
our research was designed to have been finished within a period of one month. Below is our
research time frame and the activities carried out.
DATE ACTIVITY
1/9-3rd/9/2017 Identifying the problem; this process includes identification of the problem
and developing the research question. A topic was selected basing on what is
needful to be addressed.
4th/9- 6/9/2017 Reviewing the literature; this step involved learning more about the selected
topic. Literature related to the topic was reviewed and knowledge about the
problem was analyzed.
7th/10-9th/9/2017 Clarifying the problem; since the problem identified on the first day was
broad, there was a need to clarify and narrow the scope if it is possible by the
use of the knowledge in the literature review.
11th/9-14th
/10/2017
Defining terms and concepts; the words and phrases used in purpose
statement of study need to be specifically defined for the easy and understood
report.
15th/9-17th/
9/2017
Defining the resources; this involved analyzing the focus resources that are
used to collect information with reliable data related to our topic of study that
will help to easily answer the research problem
18th/9-
20th/9/2017
Developing a research plan; here there was a determination of who will
involve in the data collection according to our group, when and how the data
will be collected and the content of the program and the plan contained of
numerous decisions and considerations
21st /9-
22nd/9/2017
Data collection; on this date, the real research was set to begin as soon as the
research plan was made. This was to be done following critical steps of
information gathering according to the methodology that was supposed to be
used.
23rd/9-29th/
9/2017
Analyze the data; after all the steps, the data collected need to be analyzed to
make a final report. This process involves data recording, processing, and
executing the final work
Research budget
Like any other research proposal, various costs are estimated. Therefore a budget for our
research proposal was drafted as follows;
ITEM EXPENDITURE
our research was designed to have been finished within a period of one month. Below is our
research time frame and the activities carried out.
DATE ACTIVITY
1/9-3rd/9/2017 Identifying the problem; this process includes identification of the problem
and developing the research question. A topic was selected basing on what is
needful to be addressed.
4th/9- 6/9/2017 Reviewing the literature; this step involved learning more about the selected
topic. Literature related to the topic was reviewed and knowledge about the
problem was analyzed.
7th/10-9th/9/2017 Clarifying the problem; since the problem identified on the first day was
broad, there was a need to clarify and narrow the scope if it is possible by the
use of the knowledge in the literature review.
11th/9-14th
/10/2017
Defining terms and concepts; the words and phrases used in purpose
statement of study need to be specifically defined for the easy and understood
report.
15th/9-17th/
9/2017
Defining the resources; this involved analyzing the focus resources that are
used to collect information with reliable data related to our topic of study that
will help to easily answer the research problem
18th/9-
20th/9/2017
Developing a research plan; here there was a determination of who will
involve in the data collection according to our group, when and how the data
will be collected and the content of the program and the plan contained of
numerous decisions and considerations
21st /9-
22nd/9/2017
Data collection; on this date, the real research was set to begin as soon as the
research plan was made. This was to be done following critical steps of
information gathering according to the methodology that was supposed to be
used.
23rd/9-29th/
9/2017
Analyze the data; after all the steps, the data collected need to be analyzed to
make a final report. This process involves data recording, processing, and
executing the final work
Research budget
Like any other research proposal, various costs are estimated. Therefore a budget for our
research proposal was drafted as follows;
ITEM EXPENDITURE
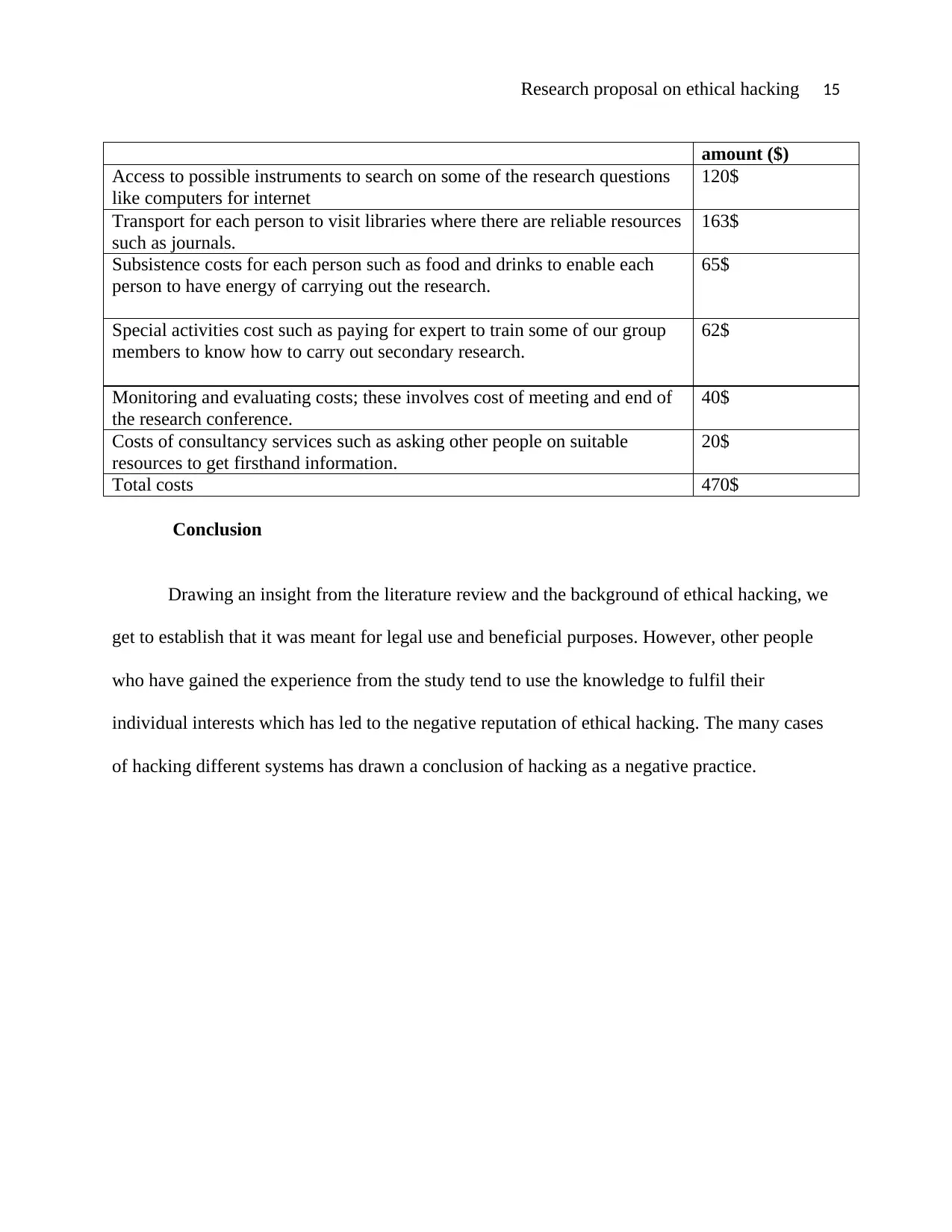
Research proposal on ethical hacking 15
amount ($)
Access to possible instruments to search on some of the research questions
like computers for internet
120$
Transport for each person to visit libraries where there are reliable resources
such as journals.
163$
Subsistence costs for each person such as food and drinks to enable each
person to have energy of carrying out the research.
65$
Special activities cost such as paying for expert to train some of our group
members to know how to carry out secondary research.
62$
Monitoring and evaluating costs; these involves cost of meeting and end of
the research conference.
40$
Costs of consultancy services such as asking other people on suitable
resources to get firsthand information.
20$
Total costs 470$
Conclusion
Drawing an insight from the literature review and the background of ethical hacking, we
get to establish that it was meant for legal use and beneficial purposes. However, other people
who have gained the experience from the study tend to use the knowledge to fulfil their
individual interests which has led to the negative reputation of ethical hacking. The many cases
of hacking different systems has drawn a conclusion of hacking as a negative practice.
amount ($)
Access to possible instruments to search on some of the research questions
like computers for internet
120$
Transport for each person to visit libraries where there are reliable resources
such as journals.
163$
Subsistence costs for each person such as food and drinks to enable each
person to have energy of carrying out the research.
65$
Special activities cost such as paying for expert to train some of our group
members to know how to carry out secondary research.
62$
Monitoring and evaluating costs; these involves cost of meeting and end of
the research conference.
40$
Costs of consultancy services such as asking other people on suitable
resources to get firsthand information.
20$
Total costs 470$
Conclusion
Drawing an insight from the literature review and the background of ethical hacking, we
get to establish that it was meant for legal use and beneficial purposes. However, other people
who have gained the experience from the study tend to use the knowledge to fulfil their
individual interests which has led to the negative reputation of ethical hacking. The many cases
of hacking different systems has drawn a conclusion of hacking as a negative practice.

Research proposal on ethical hacking 16
References
Chatzidakis, A. and Mitussis, D., 2007. Computer ethics and consumer ethics: the impact of the
internet on consumers' ethical decision‐making process. Journal of Consumer Behaviour, 6(5),
pp.305-320.
Coleman, E.G., 2013. Coding freedom: The ethics and aesthetics of hacking. Princeton
University Press.
Crosbie, M., 2012. Hack the cloud: Ethical hacking and cloud forensics. Cybercrime and Cloud
Forensics: Applications for Investigation, Processes, pp.42-58.
Engebretson, P., 2013. The basics of hacking and penetration testing: ethical hacking and
penetration testing made easy. Elsevier.
Farsole, A.A., Kashikar, A.G. and Zunzunwala, A., 2010. Ethical hacking. International Journal
of Computer Applications (IJCA), 1(10), pp.14-20.
Foulger, T.S., Ewbank, A.D., Kay, A., Popp, S.O. and Carter, H.L., 2009. Moral spaces in
MySpace: Preservice teachers’ perspectives about ethical issues in social networking. Journal of
Research on Technology in Education, 42(1), pp.1-28.
References
Chatzidakis, A. and Mitussis, D., 2007. Computer ethics and consumer ethics: the impact of the
internet on consumers' ethical decision‐making process. Journal of Consumer Behaviour, 6(5),
pp.305-320.
Coleman, E.G., 2013. Coding freedom: The ethics and aesthetics of hacking. Princeton
University Press.
Crosbie, M., 2012. Hack the cloud: Ethical hacking and cloud forensics. Cybercrime and Cloud
Forensics: Applications for Investigation, Processes, pp.42-58.
Engebretson, P., 2013. The basics of hacking and penetration testing: ethical hacking and
penetration testing made easy. Elsevier.
Farsole, A.A., Kashikar, A.G. and Zunzunwala, A., 2010. Ethical hacking. International Journal
of Computer Applications (IJCA), 1(10), pp.14-20.
Foulger, T.S., Ewbank, A.D., Kay, A., Popp, S.O. and Carter, H.L., 2009. Moral spaces in
MySpace: Preservice teachers’ perspectives about ethical issues in social networking. Journal of
Research on Technology in Education, 42(1), pp.1-28.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Research proposal on ethical hacking 17
Graves, K., 2007. CEH: Official Certified Ethical Hacker Review Guide: Exam 312-50. John
Wiley & Sons.
Graves, K., 2010. CEH certified ethical hacker study guide. John Wiley & Sons.
Hafele, D.M., 2004. Three Different Shades of Ethical Hacking: Black, White and Gray.
Harper, A., Harris, S., Ness, J., Eagle, C., Lenkey, G. and Williams, T., 2011. Gray hat hacking
the ethical hackers handbook. McGraw-Hill Osborne Media.
Harvey, B., 2004. Computer hacking and ethics. University of California, Berkeley. Retrieved
July23.
Jamil, D.A.N.I.S.H. and Khan, M.N.A., 2011. Is ethical hacking ethical?. International Journal
of Engineering Science and Technology (IJEST), ISSN, pp.0975-5462.
Johnson, C.E., 2017. Meeting the ethical challenges of leadership: Casting light or shadow. Sage
Publications.
Kaupins, G. and Park, S., 2011. Legal and ethical implications of corporate social
networks. Employee Responsibilities and Rights Journal, 23(2), pp.83-99.
Khan, M.E., 2010. Different forms of software testing techniques for finding errors.
International journal of computer science issues, 7(3), pp.11-16.
Krutz, R.L. and Vines, R.D., 2007. THE CEH PREP GUIDE, THE COMPREHENSIVE GUIDE
TO CERTIFIED ETHICAL HACKING (With CD). John Wiley & Sons.
Graves, K., 2007. CEH: Official Certified Ethical Hacker Review Guide: Exam 312-50. John
Wiley & Sons.
Graves, K., 2010. CEH certified ethical hacker study guide. John Wiley & Sons.
Hafele, D.M., 2004. Three Different Shades of Ethical Hacking: Black, White and Gray.
Harper, A., Harris, S., Ness, J., Eagle, C., Lenkey, G. and Williams, T., 2011. Gray hat hacking
the ethical hackers handbook. McGraw-Hill Osborne Media.
Harvey, B., 2004. Computer hacking and ethics. University of California, Berkeley. Retrieved
July23.
Jamil, D.A.N.I.S.H. and Khan, M.N.A., 2011. Is ethical hacking ethical?. International Journal
of Engineering Science and Technology (IJEST), ISSN, pp.0975-5462.
Johnson, C.E., 2017. Meeting the ethical challenges of leadership: Casting light or shadow. Sage
Publications.
Kaupins, G. and Park, S., 2011. Legal and ethical implications of corporate social
networks. Employee Responsibilities and Rights Journal, 23(2), pp.83-99.
Khan, M.E., 2010. Different forms of software testing techniques for finding errors.
International journal of computer science issues, 7(3), pp.11-16.
Krutz, R.L. and Vines, R.D., 2007. THE CEH PREP GUIDE, THE COMPREHENSIVE GUIDE
TO CERTIFIED ETHICAL HACKING (With CD). John Wiley & Sons.

Research proposal on ethical hacking 18
Logan, P.Y. and Clarkson, A., 2005, February. Teaching students to hack: curriculum issues in
information security. In ACM SIGCSE Bulletin (Vol. 37, No. 1, pp. 157-161). ACM.
Nelson, B., 2014. Computer science: Hacking into the cyberworld. Nature, 506(7489), pp.517-
519.
Palmer, C.C., 2001. Ethical hacking. IBM Systems Journal, 40(3), pp.769-780.
Pike, R.E., 2013. The “ethics” of teaching ethical hacking. Journal of International Technology
and Information Management, 22(4), p.4.
Reddy, S.V., Ramani, K.S., Rijutha, K., Ali, S.M. and Reddy, C.P., 2010, June. Wireless
hacking-a WiFi hack by cracking WEP. In Education Technology and Computer (Vol. 1, pp. V1-
189). IEEE.
Reddy, S.V., Ramani, K.S., Rijutha, K., Ali, S.M. and Reddy, C.P., 2010, June. Wireless
hacking-a WiFi hack by cracking WEP. In Education Technology and Computer (Vol. 1, pp.
V1-189). IEEE.
Regalado, D., Harris, S., Harper, A., Eagle, C., Ness, J., Spasojevic, B., Linn, R. and Sims, S.,
2015. Gray Hat Hacking the Ethical Hacker's Handbook. McGraw-Hill Education Group
Tavani, H.T., 2011. Ethics and technology: Controversies, questions, and strategies for ethical
computing. John Wiley & Sons.
Tiller, J.S., 2004. The ethical hack: a framework for business value penetration testing. CRC
Press.
Logan, P.Y. and Clarkson, A., 2005, February. Teaching students to hack: curriculum issues in
information security. In ACM SIGCSE Bulletin (Vol. 37, No. 1, pp. 157-161). ACM.
Nelson, B., 2014. Computer science: Hacking into the cyberworld. Nature, 506(7489), pp.517-
519.
Palmer, C.C., 2001. Ethical hacking. IBM Systems Journal, 40(3), pp.769-780.
Pike, R.E., 2013. The “ethics” of teaching ethical hacking. Journal of International Technology
and Information Management, 22(4), p.4.
Reddy, S.V., Ramani, K.S., Rijutha, K., Ali, S.M. and Reddy, C.P., 2010, June. Wireless
hacking-a WiFi hack by cracking WEP. In Education Technology and Computer (Vol. 1, pp. V1-
189). IEEE.
Reddy, S.V., Ramani, K.S., Rijutha, K., Ali, S.M. and Reddy, C.P., 2010, June. Wireless
hacking-a WiFi hack by cracking WEP. In Education Technology and Computer (Vol. 1, pp.
V1-189). IEEE.
Regalado, D., Harris, S., Harper, A., Eagle, C., Ness, J., Spasojevic, B., Linn, R. and Sims, S.,
2015. Gray Hat Hacking the Ethical Hacker's Handbook. McGraw-Hill Education Group
Tavani, H.T., 2011. Ethics and technology: Controversies, questions, and strategies for ethical
computing. John Wiley & Sons.
Tiller, J.S., 2004. The ethical hack: a framework for business value penetration testing. CRC
Press.

Research proposal on ethical hacking 19
Venter, H.S. and Eloff, J.H.P., 2000. Network security: Important issues. Network
Security, 2000(6), pp.12-16.
Veruggio, G., Operto, F. and Bekey, G., 2016. Roboethics: Social and ethical implications.
In Springer handbook of robotics (pp. 2135-2160). Springer International Publishing.
Wilhelm, T., 2009. Professional penetration testing: creating and operating a formal hacking
lab. Syngress Publishing.
Yang, M.H., Lin, B., Chandlrees, N. and Chao, H.Y., 2009. The effect of perceived ethical
performance of shopping websites on consumer trust. Journal of computer information
systems, 50(1), pp.15-24.
Venter, H.S. and Eloff, J.H.P., 2000. Network security: Important issues. Network
Security, 2000(6), pp.12-16.
Veruggio, G., Operto, F. and Bekey, G., 2016. Roboethics: Social and ethical implications.
In Springer handbook of robotics (pp. 2135-2160). Springer International Publishing.
Wilhelm, T., 2009. Professional penetration testing: creating and operating a formal hacking
lab. Syngress Publishing.
Yang, M.H., Lin, B., Chandlrees, N. and Chao, H.Y., 2009. The effect of perceived ethical
performance of shopping websites on consumer trust. Journal of computer information
systems, 50(1), pp.15-24.
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




