Ethical Hacking & Countermeasures Report 2022
Added on 2022-10-12
25 Pages3747 Words46 Views
Running head: ETHICAL HACKING & COUNTERMEASURES
Assessment 011 - Penetration test case study & Discussion Forum
Contributions
Name of the Student
Name of the University
Author’s Note
Assessment 011 - Penetration test case study & Discussion Forum
Contributions
Name of the Student
Name of the University
Author’s Note

1
ETHICAL HACKING & COUNTERMEASURES
Executive Summary
The company Dead Duck Publishing Ltd has approached Network security Pvt. Limited to
conduct a penetration test of two servers associated with the data center of the company and
these data centers are hosted by the company Dead Duck Publishing Ltd itself.
This report is the penetration report of the second quarter and the penetration testing described in
this report was executed during 05/08/2019. The report has detailed each of the activities
considered in executing the testing of the server for identifying the vulnerabilities of the network
and its associated servers. It will provide a comprehensive overview of the penetration testing of
the servers.
Scope:
The penetration has only considered the following IP address and any other IP address that are
not mentioned in this context are not included in the scope of the penetration testing.
(192.168.9235.0/24)
ETHICAL HACKING & COUNTERMEASURES
Executive Summary
The company Dead Duck Publishing Ltd has approached Network security Pvt. Limited to
conduct a penetration test of two servers associated with the data center of the company and
these data centers are hosted by the company Dead Duck Publishing Ltd itself.
This report is the penetration report of the second quarter and the penetration testing described in
this report was executed during 05/08/2019. The report has detailed each of the activities
considered in executing the testing of the server for identifying the vulnerabilities of the network
and its associated servers. It will provide a comprehensive overview of the penetration testing of
the servers.
Scope:
The penetration has only considered the following IP address and any other IP address that are
not mentioned in this context are not included in the scope of the penetration testing.
(192.168.9235.0/24)

2
ETHICAL HACKING & COUNTERMEASURES
Table of Contents
Foot printing....................................................................................................................................3
Vulnerability Analysis.....................................................................................................................9
Open port on the network:...........................................................................................................9
HTTP service on open port:.....................................................................................................9
Password cracking:..................................................................................................................9
Cross-site scripting:...............................................................................................................10
SQL injection:........................................................................................................................10
Identify scenarios for exploitation:............................................................................................10
Verification....................................................................................................................................11
Open port scanning:...................................................................................................................11
HTTP service exploitation:........................................................................................................12
Password cracking:....................................................................................................................12
Cross-site scripting:...................................................................................................................13
SQL injection:............................................................................................................................13
Risk Analysis & Mitigation...........................................................................................................20
Risk Mitigation..............................................................................................................................21
Conclusion.....................................................................................................................................22
Bibliography..................................................................................................................................24
ETHICAL HACKING & COUNTERMEASURES
Table of Contents
Foot printing....................................................................................................................................3
Vulnerability Analysis.....................................................................................................................9
Open port on the network:...........................................................................................................9
HTTP service on open port:.....................................................................................................9
Password cracking:..................................................................................................................9
Cross-site scripting:...............................................................................................................10
SQL injection:........................................................................................................................10
Identify scenarios for exploitation:............................................................................................10
Verification....................................................................................................................................11
Open port scanning:...................................................................................................................11
HTTP service exploitation:........................................................................................................12
Password cracking:....................................................................................................................12
Cross-site scripting:...................................................................................................................13
SQL injection:............................................................................................................................13
Risk Analysis & Mitigation...........................................................................................................20
Risk Mitigation..............................................................................................................................21
Conclusion.....................................................................................................................................22
Bibliography..................................................................................................................................24

3
ETHICAL HACKING & COUNTERMEASURES
Foot printing
Develop a plan of attack (POA):
Open port scanning: proper port-scanning tool will deployed which provides a faster
scanning result and then identify what are port that are open and easier to access. These
ports are then considered for exploiting the network and gain access to the overall
network
Password cracking: for cracking the password root access to the system will be
established and if this access is gained then the files containing the password hash will be
accessed or the existing password will be modified
HTTP service exploitation: first the port which host the HTTP service will be analyzed
and if any open port is found on which the HTTP service is hosted, then malicious code
will be sent to exploit the network over the internet along with exploitation of the
machine which executes these HTTP service
Cross-site scripting: virtual machine will be scanned through web scanner and it will
provide context for identifying online servers and identify vulnerability to exploit the
machine and establish access to server to modify the data that is stored in the database of
the sever
SQL injection: information regarding the network is gathered with details regarding the
target host and with that information, information regarding the running services, IP
addresses as well as the version details is determined for fetching details regarding the
customer tables and scope regarding the vulnerability for executing the SQL injection for
exploiting the network
ETHICAL HACKING & COUNTERMEASURES
Foot printing
Develop a plan of attack (POA):
Open port scanning: proper port-scanning tool will deployed which provides a faster
scanning result and then identify what are port that are open and easier to access. These
ports are then considered for exploiting the network and gain access to the overall
network
Password cracking: for cracking the password root access to the system will be
established and if this access is gained then the files containing the password hash will be
accessed or the existing password will be modified
HTTP service exploitation: first the port which host the HTTP service will be analyzed
and if any open port is found on which the HTTP service is hosted, then malicious code
will be sent to exploit the network over the internet along with exploitation of the
machine which executes these HTTP service
Cross-site scripting: virtual machine will be scanned through web scanner and it will
provide context for identifying online servers and identify vulnerability to exploit the
machine and establish access to server to modify the data that is stored in the database of
the sever
SQL injection: information regarding the network is gathered with details regarding the
target host and with that information, information regarding the running services, IP
addresses as well as the version details is determined for fetching details regarding the
customer tables and scope regarding the vulnerability for executing the SQL injection for
exploiting the network

4
ETHICAL HACKING & COUNTERMEASURES
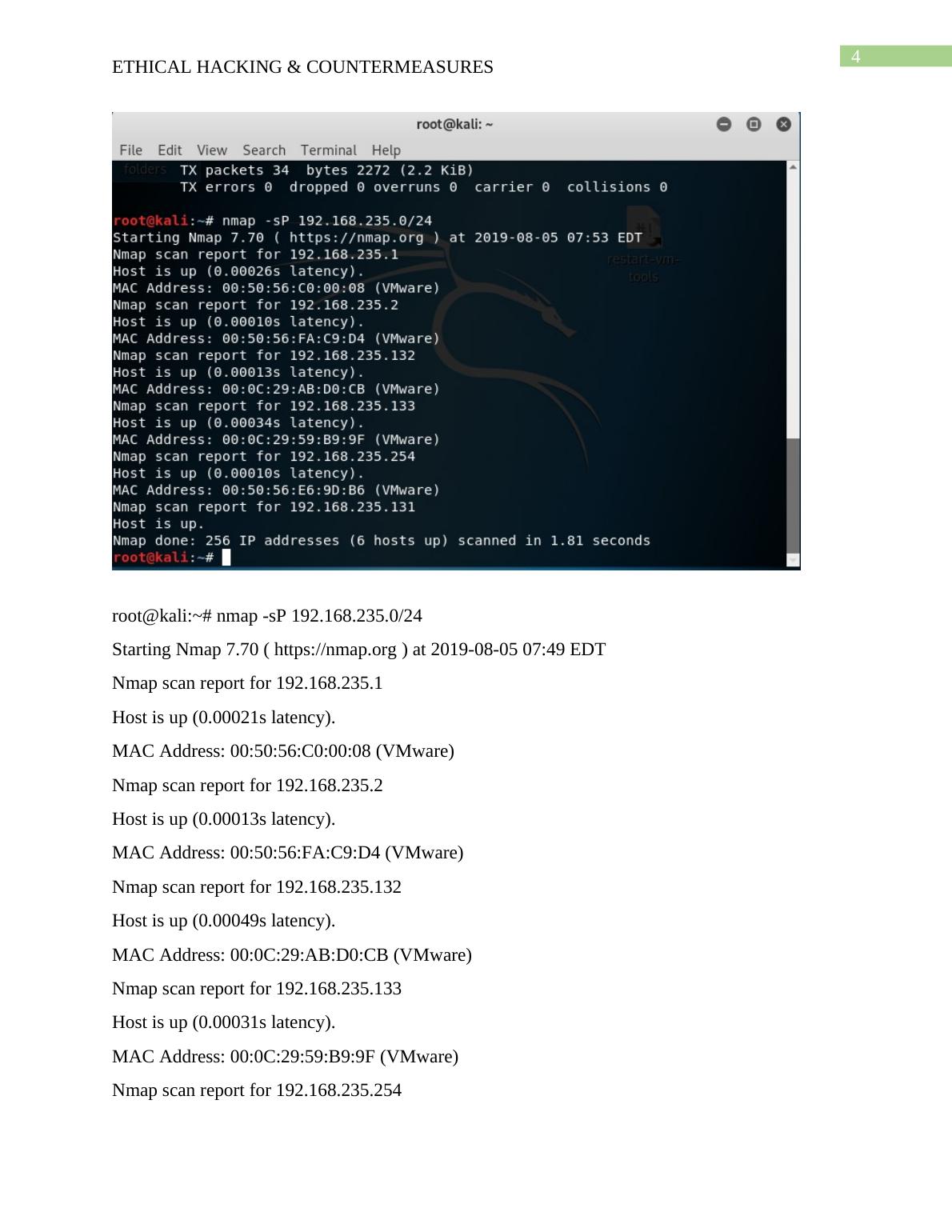
root@kali:~# nmap -sP 192.168.235.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-05 07:49 EDT
Nmap scan report for 192.168.235.1
Host is up (0.00021s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.235.2
Host is up (0.00013s latency).
MAC Address: 00:50:56:FA:C9:D4 (VMware)
Nmap scan report for 192.168.235.132
Host is up (0.00049s latency).
MAC Address: 00:0C:29:AB:D0:CB (VMware)
Nmap scan report for 192.168.235.133
Host is up (0.00031s latency).
MAC Address: 00:0C:29:59:B9:9F (VMware)
Nmap scan report for 192.168.235.254
ETHICAL HACKING & COUNTERMEASURES
root@kali:~# nmap -sP 192.168.235.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-05 07:49 EDT
Nmap scan report for 192.168.235.1
Host is up (0.00021s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.235.2
Host is up (0.00013s latency).
MAC Address: 00:50:56:FA:C9:D4 (VMware)
Nmap scan report for 192.168.235.132
Host is up (0.00049s latency).
MAC Address: 00:0C:29:AB:D0:CB (VMware)
Nmap scan report for 192.168.235.133
Host is up (0.00031s latency).
MAC Address: 00:0C:29:59:B9:9F (VMware)
Nmap scan report for 192.168.235.254
5
ETHICAL HACKING & COUNTERMEASURES
Host is up (0.00012s latency).
MAC Address: 00:50:56:E6:9D:B6 (VMware)
Nmap scan report for 192.168.235.131
Host is up.
Nmap done: 256 IP addresses (6 hosts up) scanned in 1.76 seconds
root@kali:~#
For Live Server E
A scan is performed on the targeted system for identification of the open ports and is given
below:
PORT SCAN -
ETHICAL HACKING & COUNTERMEASURES
Host is up (0.00012s latency).
MAC Address: 00:50:56:E6:9D:B6 (VMware)
Nmap scan report for 192.168.235.131
Host is up.
Nmap done: 256 IP addresses (6 hosts up) scanned in 1.76 seconds
root@kali:~#
For Live Server E
A scan is performed on the targeted system for identification of the open ports and is given
below:
PORT SCAN -
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Reflective Critical Analysis | Web Application Securitylg...
|5
|1203
|10
TCP Scan On The Webserverlg...
|13
|1284
|26
Network Vulnerability And Cyber Securitylg...
|15
|1453
|15
Cyber Security - Identification of threatslg...
|16
|1865
|20
Analysis of Security Vulnerability of WidgetsInc Virtual Machine Imagelg...
|23
|3636
|97
INFORMATION SYSTEM THREATS, ATTACKS AND DEFENSES.lg...
|29
|1680
|33