Case Study: Ethical Considerations and Data Privacy in Data Analytics
VerifiedAdded on 2023/06/09
|9
|2902
|321
Case Study
AI Summary
This case study delves into the ethical and privacy considerations within data analytics, presenting two distinct scenarios. The first scenario addresses a conflict between a CTO, an IT Manager, and Chelsea regarding the implementation of a new security system, evaluating the impact of their decisions on data privacy and ethical standards as outlined in the Australia Privacy Act and ACS Code of Professional Conduct and Ethics. It further explores whether Chelsea should agree or refuse the proposed solution and provides recommendations for handling the conflict, including a k-anonymity evaluation. The second scenario evaluates the benefits of using big data in loan systems for financial institutions, the harms faced by individuals like Josh and Hannah due to loan application denials, and the major societal harms resulting from lengthy loan application processes. It concludes by explaining three major lessons for preventing these harms, along with justifications and challenges for incorporating these measures, such as improving human understanding, institutional and economic efficiency, and predictive accuracy and personalization. The document provides insight into ethical frameworks and risk management, emphasizing the need for understanding the interaction between data practices and potential damages.

Assignment 3 Ethics
and Privacy in Data
Analytics
and Privacy in Data
Analytics
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
INTRODUCTION...........................................................................................................................3
MAIN BODY..................................................................................................................................3
TASK A...........................................................................................................................................3
A) Discuss and review how the decision taken by the CTO and IT Manager impacted the data
privacy and ethical considerations specified in the Australia Privacy Act and ACS Code of
Professional Conduct and Ethics:................................................................................................3
B Should Chelsea agree or refuse to implement the proposed solution? Provide your
recommendations and suggestions with appropriate references to handle the conflict:..............4
C Suppose you are a member of Chelsea’s IT security team. She has asked you to perform a k-
anonymity evaluation for the below dataset. The quasi-identifiers are {Sex, Age, Postcode}
and the sensitive attribute is Income:...........................................................................................4
TASK2.............................................................................................................................................5
a. In order to evaluate loan system what are the significant benefits from financial institution
using big data:..............................................................................................................................5
b. What harms faced by Josh and Hannah for denial of loan application and provide three
significant harms which are important for life interest:...............................................................5
c Explanation on major harm to society due to lengthy loan application process:......................6
d. Explanation on three major lesson for prevention on those harms along with justification
and challenges to incorporate these measures:............................................................................6
CONCLUSION................................................................................................................................7
REFERENCES................................................................................................................................9
INTRODUCTION...........................................................................................................................3
MAIN BODY..................................................................................................................................3
TASK A...........................................................................................................................................3
A) Discuss and review how the decision taken by the CTO and IT Manager impacted the data
privacy and ethical considerations specified in the Australia Privacy Act and ACS Code of
Professional Conduct and Ethics:................................................................................................3
B Should Chelsea agree or refuse to implement the proposed solution? Provide your
recommendations and suggestions with appropriate references to handle the conflict:..............4
C Suppose you are a member of Chelsea’s IT security team. She has asked you to perform a k-
anonymity evaluation for the below dataset. The quasi-identifiers are {Sex, Age, Postcode}
and the sensitive attribute is Income:...........................................................................................4
TASK2.............................................................................................................................................5
a. In order to evaluate loan system what are the significant benefits from financial institution
using big data:..............................................................................................................................5
b. What harms faced by Josh and Hannah for denial of loan application and provide three
significant harms which are important for life interest:...............................................................5
c Explanation on major harm to society due to lengthy loan application process:......................6
d. Explanation on three major lesson for prevention on those harms along with justification
and challenges to incorporate these measures:............................................................................6
CONCLUSION................................................................................................................................7
REFERENCES................................................................................................................................9

INTRODUCTION
Data security plays the vital role in the success and failure of the organisation. In today’s
worlds the transaction has been taken place mostly with the use of online system or portal.
Therefore, it is necessary for the organisation to secure their system with the use of advanced
technology so that data breech from the external hacker could be avoided. Sensitive information
could be in the form of salary details of the employees, major contracts entered by the
organisations, details relating to proposed contracts they are entered into and so on. Security of
the information plays the vital role in corporate and all the organisation are facing the security
breech in today’s time. In this statement security breaches and their solution in two different case
scenario has been discussed in the detailed manner along with providing solutions for the same
(Hermann, 2022).
MAIN BODY
TASK A
A) Discuss and review how the decision taken by the CTO and IT Manager impacted the data
privacy and ethical considerations specified in the Australia Privacy Act and ACS Code of
Professional Conduct and Ethics:
The CTO and IT manager of the view that current system is capable enough to avoid the
security breaches as installation of the new system takes time and it also increases the cost of the
company as well. On the other hand, Chelsea of the view that old system must be replaced with
the new system as she fees that the data that has been stored is very sensitive and it requires extra
protection. Such information may be related to salaries of the employees, annual performance
evaluation, customer information such as credit card details and so on. The ACS code of
professional ethics laid down six different principles which must be complied by all of its
member accordingly:
The primacy of the public interest:
The main focus is that to give important consideration to the public interest while
performing the duties over the personal, private and sectional interest and so on. The
public could include public health, safety and the environment. In accordance with the
value identify those whose work has been potentially impacted and consider their interest
on prima facie basis. Provide regular advice to the stakeholders as soon as conflicts of
Data security plays the vital role in the success and failure of the organisation. In today’s
worlds the transaction has been taken place mostly with the use of online system or portal.
Therefore, it is necessary for the organisation to secure their system with the use of advanced
technology so that data breech from the external hacker could be avoided. Sensitive information
could be in the form of salary details of the employees, major contracts entered by the
organisations, details relating to proposed contracts they are entered into and so on. Security of
the information plays the vital role in corporate and all the organisation are facing the security
breech in today’s time. In this statement security breaches and their solution in two different case
scenario has been discussed in the detailed manner along with providing solutions for the same
(Hermann, 2022).
MAIN BODY
TASK A
A) Discuss and review how the decision taken by the CTO and IT Manager impacted the data
privacy and ethical considerations specified in the Australia Privacy Act and ACS Code of
Professional Conduct and Ethics:
The CTO and IT manager of the view that current system is capable enough to avoid the
security breaches as installation of the new system takes time and it also increases the cost of the
company as well. On the other hand, Chelsea of the view that old system must be replaced with
the new system as she fees that the data that has been stored is very sensitive and it requires extra
protection. Such information may be related to salaries of the employees, annual performance
evaluation, customer information such as credit card details and so on. The ACS code of
professional ethics laid down six different principles which must be complied by all of its
member accordingly:
The primacy of the public interest:
The main focus is that to give important consideration to the public interest while
performing the duties over the personal, private and sectional interest and so on. The
public could include public health, safety and the environment. In accordance with the
value identify those whose work has been potentially impacted and consider their interest
on prima facie basis. Provide regular advice to the stakeholders as soon as conflicts of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

interest arises. It is necessary to endeavour to preserve the confidentiality and privacy of
the information of others (Hossain, Akter and Yanamandram, 2020).
The enhancement of the quality of life:
With the help of data security, the quality of life has been improved of the users and their
connected persons also. It is necessary for the business to promote and protect the safety
of those individual that are being affected by the entity.
Honesty:
It is necessary for the organisation as not to break the trust of general public and the
specific trust that has been made by stakeholders on the corporation. It is essential for the
corporate along with its employees to ensure the honesty must be carried upon while
performing the task as it creates trust amongst the management in each other and work
will carry out smoothly (Klugman and et.al., 2018).
Competence:
Only those work should be accepted which is competent enough to deal will so that their
capability will be utilised in an effective manner. It is necessary for the organisation to
bring those people on line who are competent and capable to work with in different case
scenario so that their ability will improve and enhance and ultimately is beneficial for the
organisations growth as well.
B Should Chelsea agree or refuse to implement the proposed solution? Provide your
recommendations and suggestions with appropriate references to handle the conflict:
She should refuse to accept the suggestion given by the CTO and the IT manger being if
her suggestion is not considering then there will be the higher chances for the data breech in the
system. It is essential for her to recommend her view to the top management and not only
restricted to the views given by CTO and IT manager. If the board of director, consider that her
view is important then may be new system has been implemented in the given situation or time.
C Suppose you are a member of Chelsea’s IT security team. She has asked you to perform a k-
anonymity evaluation for the below dataset. The quasi-identifiers are {Sex, Age, Postcode}
and the sensitive attribute is Income:
ID Age Postcode Sex Income ($)
1 20-25 308* male 95000
2 20-25 318* male 80000
the information of others (Hossain, Akter and Yanamandram, 2020).
The enhancement of the quality of life:
With the help of data security, the quality of life has been improved of the users and their
connected persons also. It is necessary for the business to promote and protect the safety
of those individual that are being affected by the entity.
Honesty:
It is necessary for the organisation as not to break the trust of general public and the
specific trust that has been made by stakeholders on the corporation. It is essential for the
corporate along with its employees to ensure the honesty must be carried upon while
performing the task as it creates trust amongst the management in each other and work
will carry out smoothly (Klugman and et.al., 2018).
Competence:
Only those work should be accepted which is competent enough to deal will so that their
capability will be utilised in an effective manner. It is necessary for the organisation to
bring those people on line who are competent and capable to work with in different case
scenario so that their ability will improve and enhance and ultimately is beneficial for the
organisations growth as well.
B Should Chelsea agree or refuse to implement the proposed solution? Provide your
recommendations and suggestions with appropriate references to handle the conflict:
She should refuse to accept the suggestion given by the CTO and the IT manger being if
her suggestion is not considering then there will be the higher chances for the data breech in the
system. It is essential for her to recommend her view to the top management and not only
restricted to the views given by CTO and IT manager. If the board of director, consider that her
view is important then may be new system has been implemented in the given situation or time.
C Suppose you are a member of Chelsea’s IT security team. She has asked you to perform a k-
anonymity evaluation for the below dataset. The quasi-identifiers are {Sex, Age, Postcode}
and the sensitive attribute is Income:
ID Age Postcode Sex Income ($)
1 20-25 308* male 95000
2 20-25 318* male 80000
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
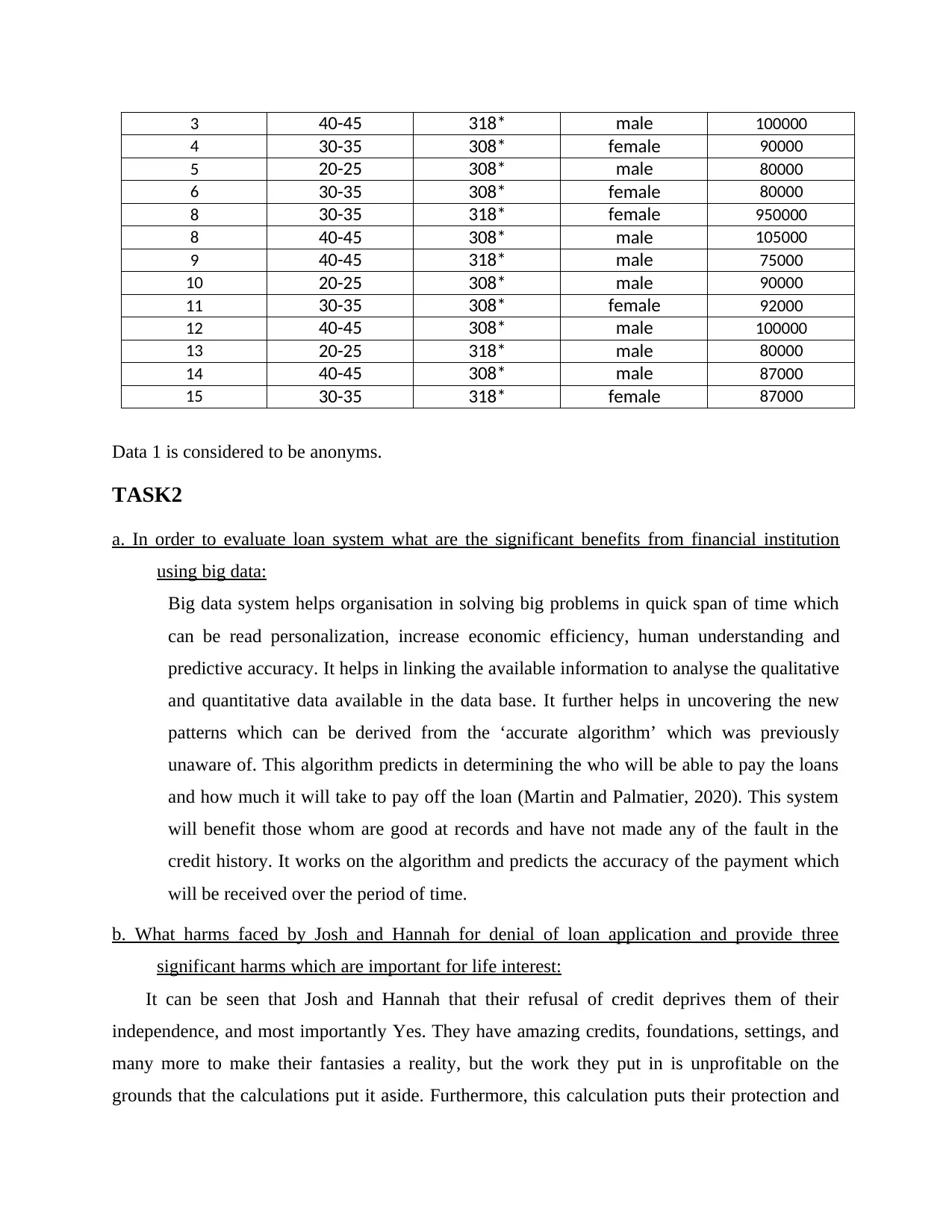
3 40-45 318* male 100000
4 30-35 308* female 90000
5 20-25 308* male 80000
6 30-35 308* female 80000
8 30-35 318* female 950000
8 40-45 308* male 105000
9 40-45 318* male 75000
10 20-25 308* male 90000
11 30-35 308* female 92000
12 40-45 308* male 100000
13 20-25 318* male 80000
14 40-45 308* male 87000
15 30-35 318* female 87000
Data 1 is considered to be anonyms.
TASK2
a. In order to evaluate loan system what are the significant benefits from financial institution
using big data:
Big data system helps organisation in solving big problems in quick span of time which
can be read personalization, increase economic efficiency, human understanding and
predictive accuracy. It helps in linking the available information to analyse the qualitative
and quantitative data available in the data base. It further helps in uncovering the new
patterns which can be derived from the ‘accurate algorithm’ which was previously
unaware of. This algorithm predicts in determining the who will be able to pay the loans
and how much it will take to pay off the loan (Martin and Palmatier, 2020). This system
will benefit those whom are good at records and have not made any of the fault in the
credit history. It works on the algorithm and predicts the accuracy of the payment which
will be received over the period of time.
b. What harms faced by Josh and Hannah for denial of loan application and provide three
significant harms which are important for life interest:
It can be seen that Josh and Hannah that their refusal of credit deprives them of their
independence, and most importantly Yes. They have amazing credits, foundations, settings, and
many more to make their fantasies a reality, but the work they put in is unprofitable on the
grounds that the calculations put it aside. Furthermore, this calculation puts their protection and
4 30-35 308* female 90000
5 20-25 308* male 80000
6 30-35 308* female 80000
8 30-35 318* female 950000
8 40-45 308* male 105000
9 40-45 318* male 75000
10 20-25 308* male 90000
11 30-35 308* female 92000
12 40-45 308* male 100000
13 20-25 318* male 80000
14 40-45 308* male 87000
15 30-35 318* female 87000
Data 1 is considered to be anonyms.
TASK2
a. In order to evaluate loan system what are the significant benefits from financial institution
using big data:
Big data system helps organisation in solving big problems in quick span of time which
can be read personalization, increase economic efficiency, human understanding and
predictive accuracy. It helps in linking the available information to analyse the qualitative
and quantitative data available in the data base. It further helps in uncovering the new
patterns which can be derived from the ‘accurate algorithm’ which was previously
unaware of. This algorithm predicts in determining the who will be able to pay the loans
and how much it will take to pay off the loan (Martin and Palmatier, 2020). This system
will benefit those whom are good at records and have not made any of the fault in the
credit history. It works on the algorithm and predicts the accuracy of the payment which
will be received over the period of time.
b. What harms faced by Josh and Hannah for denial of loan application and provide three
significant harms which are important for life interest:
It can be seen that Josh and Hannah that their refusal of credit deprives them of their
independence, and most importantly Yes. They have amazing credits, foundations, settings, and
many more to make their fantasies a reality, but the work they put in is unprofitable on the
grounds that the calculations put it aside. Furthermore, this calculation puts their protection and

safety at risk by pulling the endlessly obtrusive realities of their lives away from the realities they
have not been educated or agreed to share. This also raises an immediate and legitimate ethical
question, as no one, working with Josh and Hannah, can share ideas on where computing is
going or whether its considerations are fair (Passos, Mwangi and Kapczinski, 2019).
Damage to privacy and security: Due to the breadth of personal information, people are
being created today (or, to use a better example, various lakes, springs and streams personal
information aggregated and streamed in advanced scenarios), most of us do not Acknowledging
how our lives are or may be revealed through normal information rehearsal.
Damage to Equity and Justice: Huge Life Interests to be judged and treated decently,
whether including how we are treated by policing Criminal and ordinary court frameworks, how
our bosses and educators assess us, the nature of healthcare and the different governing bodies
we get, or how money foundations and safety net providers treat us.
Impairment to Transparency and Autonomy: In this unique case, forthrightness is a
precondition for the ability to understand how a particular social framework or institution
functions, and to optionally ask about life-affecting choices made within that framework or
foundation. This way, if your bank rejects your application for housing credit, for example, you
can get direct access to data on the exact reason you were denied an advance payment and who
was denied it.
c Explanation on major harm to society due to lengthy loan application process:
Beyond their impact on Josh and Hannah, these framings can also do real harm to society,
such as class slack, entrenched prejudice, entrenched sexism, and ability discrimination. If these
frameworks strictly adhere to the decision to label individuals with a specific racial basis
/gender/ disorder / clinical history / category as "high risk", then, by then, these gatherings will
end up in the public domain because despite their extraordinary accounts and traits, but they
won't be able to break through bias-based barriers and gain cash or its status (Sedkaoui, 2018).
d. Explanation on three major lesson for prevention on those harms along with justification and
challenges to incorporate these measures:
The most well-known advantages of information are often more obvious and expected than
possible damages, so we'll get through these quickly:
Human understanding: Information available and its uncovered associated practices
unnoticed connections is an examples on Earth in advance, information advances our
have not been educated or agreed to share. This also raises an immediate and legitimate ethical
question, as no one, working with Josh and Hannah, can share ideas on where computing is
going or whether its considerations are fair (Passos, Mwangi and Kapczinski, 2019).
Damage to privacy and security: Due to the breadth of personal information, people are
being created today (or, to use a better example, various lakes, springs and streams personal
information aggregated and streamed in advanced scenarios), most of us do not Acknowledging
how our lives are or may be revealed through normal information rehearsal.
Damage to Equity and Justice: Huge Life Interests to be judged and treated decently,
whether including how we are treated by policing Criminal and ordinary court frameworks, how
our bosses and educators assess us, the nature of healthcare and the different governing bodies
we get, or how money foundations and safety net providers treat us.
Impairment to Transparency and Autonomy: In this unique case, forthrightness is a
precondition for the ability to understand how a particular social framework or institution
functions, and to optionally ask about life-affecting choices made within that framework or
foundation. This way, if your bank rejects your application for housing credit, for example, you
can get direct access to data on the exact reason you were denied an advance payment and who
was denied it.
c Explanation on major harm to society due to lengthy loan application process:
Beyond their impact on Josh and Hannah, these framings can also do real harm to society,
such as class slack, entrenched prejudice, entrenched sexism, and ability discrimination. If these
frameworks strictly adhere to the decision to label individuals with a specific racial basis
/gender/ disorder / clinical history / category as "high risk", then, by then, these gatherings will
end up in the public domain because despite their extraordinary accounts and traits, but they
won't be able to break through bias-based barriers and gain cash or its status (Sedkaoui, 2018).
d. Explanation on three major lesson for prevention on those harms along with justification and
challenges to incorporate these measures:
The most well-known advantages of information are often more obvious and expected than
possible damages, so we'll get through these quickly:
Human understanding: Information available and its uncovered associated practices
unnoticed connections is an examples on Earth in advance, information advances our
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

understanding of key ethical connections— in our own lives, society and in nature. Knowning
the world has done more or itself, but in addition, the more we understand about the world and
how it works, the wiser we can act in it. Information helps in understanding the better because it
has complied in sequential manner: from huge frameworks such as climate, environment,
markets, transport and communication organizations, to the human body, a specific biological
specialty or a specific political region, to A framework for overseeing matter and energy at the
atomic level. Information practices can likewise reveal new insights into damages, needs, and
dangers that were previously hidden or left unattended (Shayganmehr and et.al., 2021).
Institutional, Economic Efficiency and Social: it helps in providing better information and
accurate understanding of how the world works, we can plan or mediate within its framework to
work. This reduces wasted effort and assets and facilitates alignment between the social
framework or foundation's strategy/process and our goals. For instance, a wealth of information
can help us make better framing models, such as provincial traffic flows and through these
models, we can more effectively identify specific changes that may ease congestion and reduce
pollution and fuel use—ethically A crucial supplement that can improve our satisfaction and
climate. Information used to more easily show voting behaviour in specific districts could allow
us to differentiate the transmission of measurement station areas and times that best support voter
turnout, thereby improving morally critical qualities such as resident commitment.
Predictive Accuracy and Personalization: extensive rehearsals of information can not only
help make social frameworks work more proficiently, but they can also be used to more precisely
tailor activities for explicit People achieve excellent results, parties and conditions, and are more
receptive to constant input from customers in (around). Clearly, the most significant examples of
this informational advantage may include customized search and ad serving. The architects of
web search tools, web-based advocacy stages, and related tools need them to convey to you what
is best for you right now. Information review enables them to more accurately anticipate your
tendencies and requirements (Shayganmehr and et.al., 2021).
CONCLUSION
From the above report it has been concluded that it is very important for the business
organisation to analyse the various aspects in order to be effective and efficient. The business
analytics is defined as the process of taking consideration of the historical data in order to make
the right decision for the growth of the business enterprise. It is very essential for the business
the world has done more or itself, but in addition, the more we understand about the world and
how it works, the wiser we can act in it. Information helps in understanding the better because it
has complied in sequential manner: from huge frameworks such as climate, environment,
markets, transport and communication organizations, to the human body, a specific biological
specialty or a specific political region, to A framework for overseeing matter and energy at the
atomic level. Information practices can likewise reveal new insights into damages, needs, and
dangers that were previously hidden or left unattended (Shayganmehr and et.al., 2021).
Institutional, Economic Efficiency and Social: it helps in providing better information and
accurate understanding of how the world works, we can plan or mediate within its framework to
work. This reduces wasted effort and assets and facilitates alignment between the social
framework or foundation's strategy/process and our goals. For instance, a wealth of information
can help us make better framing models, such as provincial traffic flows and through these
models, we can more effectively identify specific changes that may ease congestion and reduce
pollution and fuel use—ethically A crucial supplement that can improve our satisfaction and
climate. Information used to more easily show voting behaviour in specific districts could allow
us to differentiate the transmission of measurement station areas and times that best support voter
turnout, thereby improving morally critical qualities such as resident commitment.
Predictive Accuracy and Personalization: extensive rehearsals of information can not only
help make social frameworks work more proficiently, but they can also be used to more precisely
tailor activities for explicit People achieve excellent results, parties and conditions, and are more
receptive to constant input from customers in (around). Clearly, the most significant examples of
this informational advantage may include customized search and ad serving. The architects of
web search tools, web-based advocacy stages, and related tools need them to convey to you what
is best for you right now. Information review enables them to more accurately anticipate your
tendencies and requirements (Shayganmehr and et.al., 2021).
CONCLUSION
From the above report it has been concluded that it is very important for the business
organisation to analyse the various aspects in order to be effective and efficient. The business
analytics is defined as the process of taking consideration of the historical data in order to make
the right decision for the growth of the business enterprise. It is very essential for the business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

organisations to maintain their data and gather information so that they can make changes and
acquire the right set of strategies within the business operations. It is important for the managers
to analyse the patters and the root causes within the company. It is also analysed that maintaining
privacy is the big issues now a day because of the new technologies. The privacy of the
organisation and its information need to be secured by the company in order to have an effective
functioning. This plays a major role in the working of the organisation. The big data which is
collected by the organizations in order to be effective where the companies need to be aware of
the several risk which is involved within the maintaining security. It is very important for the
organisation to practices the ethical ways in order to build the brand image.
acquire the right set of strategies within the business operations. It is important for the managers
to analyse the patters and the root causes within the company. It is also analysed that maintaining
privacy is the big issues now a day because of the new technologies. The privacy of the
organisation and its information need to be secured by the company in order to have an effective
functioning. This plays a major role in the working of the organisation. The big data which is
collected by the organizations in order to be effective where the companies need to be aware of
the several risk which is involved within the maintaining security. It is very important for the
organisation to practices the ethical ways in order to build the brand image.

REFERENCES
Books and Journals
Hermann, E., 2022. Artificial intelligence and mass personalization of communication content—
An ethical and literacy perspective. New Media & Society, 24(5), pp.1258-1277.
Hossain, M.A., Akter, S. and Yanamandram, V., 2020. Revisiting customer analytics capability
for data-driven retailing. Journal of Retailing and Consumer Services, 56, p.102187.
Klugman, C.M. and et.al., 2018. The ethics of smart pills and self-acting devices: autonomy,
truth-telling, and trust at the dawn of digital medicine. The American journal of
bioethics, 18(9), pp.38-47.
Martin, K.D. and Palmatier, R.W., 2020. Data privacy in retail: Navigating tensions and
directing future research. Journal of Retailing, 96(4), pp.449-457.
Passos, I.C., Mwangi, B. and Kapczinski, F. eds., 2019. Personalized psychiatry: Big data
analytics in mental health. Springer International Publishing.
Sedkaoui, S. ed., 2018. Big data analytics for entrepreneurial success. IGI Global.
Shayganmehr, M. and et.al., 2021. Industry 4.0 enablers for a cleaner production and circular
economy within the context of business ethics: A study in a developing country. Journal
of Cleaner Production, 281, p.125280.
Shayganmehr, M. and et.al., 2021. Industry 4.0 enablers for a cleaner production and circular
economy within the context of business ethics: A study in a developing country. Journal
of Cleaner Production, 281, p.125280.
Shrivastava, G. and et.al., 2018. Handbook of research on network forensics and analysis
techniques. IGI Global.
Thite, M., 2022. Digital human resource development: where are we? Where should we go and
how do we go there?. Human Resource Development International, 25(1), pp.87-103.
Uskov, V.L. and et.al., 2019, April. Machine learning-based predictive analytics of student
academic performance in STEM education. In 2019 IEEE Global Engineering
Education Conference (EDUCON) (pp. 1370-1376). IEEE.
Waheed, H. and et.al., 2018. A bibliometric perspective of learning analytics research
landscape. Behaviour & Information Technology, 37(10-11), pp.941-957.
Books and Journals
Hermann, E., 2022. Artificial intelligence and mass personalization of communication content—
An ethical and literacy perspective. New Media & Society, 24(5), pp.1258-1277.
Hossain, M.A., Akter, S. and Yanamandram, V., 2020. Revisiting customer analytics capability
for data-driven retailing. Journal of Retailing and Consumer Services, 56, p.102187.
Klugman, C.M. and et.al., 2018. The ethics of smart pills and self-acting devices: autonomy,
truth-telling, and trust at the dawn of digital medicine. The American journal of
bioethics, 18(9), pp.38-47.
Martin, K.D. and Palmatier, R.W., 2020. Data privacy in retail: Navigating tensions and
directing future research. Journal of Retailing, 96(4), pp.449-457.
Passos, I.C., Mwangi, B. and Kapczinski, F. eds., 2019. Personalized psychiatry: Big data
analytics in mental health. Springer International Publishing.
Sedkaoui, S. ed., 2018. Big data analytics for entrepreneurial success. IGI Global.
Shayganmehr, M. and et.al., 2021. Industry 4.0 enablers for a cleaner production and circular
economy within the context of business ethics: A study in a developing country. Journal
of Cleaner Production, 281, p.125280.
Shayganmehr, M. and et.al., 2021. Industry 4.0 enablers for a cleaner production and circular
economy within the context of business ethics: A study in a developing country. Journal
of Cleaner Production, 281, p.125280.
Shrivastava, G. and et.al., 2018. Handbook of research on network forensics and analysis
techniques. IGI Global.
Thite, M., 2022. Digital human resource development: where are we? Where should we go and
how do we go there?. Human Resource Development International, 25(1), pp.87-103.
Uskov, V.L. and et.al., 2019, April. Machine learning-based predictive analytics of student
academic performance in STEM education. In 2019 IEEE Global Engineering
Education Conference (EDUCON) (pp. 1370-1376). IEEE.
Waheed, H. and et.al., 2018. A bibliometric perspective of learning analytics research
landscape. Behaviour & Information Technology, 37(10-11), pp.941-957.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
