Face Detection and IoT Security
VerifiedAdded on 2022/12/30
|14
|3846
|91
AI Summary
This study explores the enhancement of face detection technology in the context of IoT security. It includes a literature review, research questions, methodologies, experimental set-up, and project planning.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: FACE DETECTION AND IOT SECURITY
Face Detection and IOT Security
Name of the student:
Name of the university:
Author Note
Face Detection and IOT Security
Name of the student:
Name of the university:
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1FACE DETECTION AND IOT SECURITY
Executive summary
The following study is a research proposal that is performed o understand face detection technology.
This identification is intended to be done under the security of the Internet of Things or IoT. To
conduct the research, at first various literature are reviewed. Then, in this proposal, the research
questions are evaluated along with discussing the methodologies. Furthermore, the analysis
investigates various experimental set-ups to be done. Then the results are examined along with a
demonstration of the project planning for the current research.
Executive summary
The following study is a research proposal that is performed o understand face detection technology.
This identification is intended to be done under the security of the Internet of Things or IoT. To
conduct the research, at first various literature are reviewed. Then, in this proposal, the research
questions are evaluated along with discussing the methodologies. Furthermore, the analysis
investigates various experimental set-ups to be done. Then the results are examined along with a
demonstration of the project planning for the current research.

2FACE DETECTION AND IOT SECURITY
Table of Contents
1. Introduction:......................................................................................................................................3
2. Literature review:...............................................................................................................................3
3. Research questions, aims and sub-goals:...........................................................................................4
3.1. Research questions:....................................................................................................................4
3.2. Discussion on aims:....................................................................................................................5
3.3. Analyzing sub-goals:..................................................................................................................5
4. Analyzing theoretical content:...........................................................................................................6
5. Discussion on experimental set-up:...................................................................................................7
6. Evaluating the results, outcome and relevance:.................................................................................7
6.1. Discussing the results:................................................................................................................7
6.2. Analyzing the outcomes:............................................................................................................8
6.3. The relevance of the results:.......................................................................................................8
7. Project Planning and Gantt Charts:....................................................................................................9
8. Conclusion:......................................................................................................................................10
10. References:....................................................................................................................................11
Table of Contents
1. Introduction:......................................................................................................................................3
2. Literature review:...............................................................................................................................3
3. Research questions, aims and sub-goals:...........................................................................................4
3.1. Research questions:....................................................................................................................4
3.2. Discussion on aims:....................................................................................................................5
3.3. Analyzing sub-goals:..................................................................................................................5
4. Analyzing theoretical content:...........................................................................................................6
5. Discussion on experimental set-up:...................................................................................................7
6. Evaluating the results, outcome and relevance:.................................................................................7
6.1. Discussing the results:................................................................................................................7
6.2. Analyzing the outcomes:............................................................................................................8
6.3. The relevance of the results:.......................................................................................................8
7. Project Planning and Gantt Charts:....................................................................................................9
8. Conclusion:......................................................................................................................................10
10. References:....................................................................................................................................11

3FACE DETECTION AND IOT SECURITY
1. Introduction:
IoT is a rising field. In this way the face recognitions is deployed. The standard Picamera that
has been capturing the image for determining the identity of the person. This is the prototype
identifying the visitors. For instance, as the door identifies the visitors, the doors get unlocked and
opened. As they are never determined the door gets locked firmly. In the system has been
performing the recognition and detection quickly at real time. In this way the project uses the
primary Pi cam, there is the online connection for creating the door unlocking that through facial
identification.
The following research proposal is made on face detection enhancement included under IoT
security. Further, literature reviews are conducted with research questions, methodologies.
Moreover, the study evaluates the experimental set-us, outcomes and project planning.
2. Literature review:
Sarigiannidis, Karapistoli and Economides (2015) highlights within IoT, all the gadgets have
been behaving like a small art of the Internet node. Here, all the nodes have been interacting and
making communications. Next, security cameras have been used for developing security places,
cities and homes. Apart from this, the technology has been requiring individuals detecting the issue
taken from the camera. Conti et al. (2017) analyzes the IoT assimilated with the computer vision.
This is to find out individual faces. For executing the system, the authors have mentioned about the
credit card computers using the distinct camera broad for security system. Here, the Rasberry Pi 3 is
mentioned. Again, Motlagh, Bagaa and Taleb (2017) argues that likewise PIR or Passive Infrared
Sensor can be mounted on that Rasberry PI to detect movements. Thus, it helps to monitor and
receives notifications while the motion is determined. Apart from this the image can be captured and
find the faces. It helps in sending images to Smartphones by using various applications of telegrams.
1. Introduction:
IoT is a rising field. In this way the face recognitions is deployed. The standard Picamera that
has been capturing the image for determining the identity of the person. This is the prototype
identifying the visitors. For instance, as the door identifies the visitors, the doors get unlocked and
opened. As they are never determined the door gets locked firmly. In the system has been
performing the recognition and detection quickly at real time. In this way the project uses the
primary Pi cam, there is the online connection for creating the door unlocking that through facial
identification.
The following research proposal is made on face detection enhancement included under IoT
security. Further, literature reviews are conducted with research questions, methodologies.
Moreover, the study evaluates the experimental set-us, outcomes and project planning.
2. Literature review:
Sarigiannidis, Karapistoli and Economides (2015) highlights within IoT, all the gadgets have
been behaving like a small art of the Internet node. Here, all the nodes have been interacting and
making communications. Next, security cameras have been used for developing security places,
cities and homes. Apart from this, the technology has been requiring individuals detecting the issue
taken from the camera. Conti et al. (2017) analyzes the IoT assimilated with the computer vision.
This is to find out individual faces. For executing the system, the authors have mentioned about the
credit card computers using the distinct camera broad for security system. Here, the Rasberry Pi 3 is
mentioned. Again, Motlagh, Bagaa and Taleb (2017) argues that likewise PIR or Passive Infrared
Sensor can be mounted on that Rasberry PI to detect movements. Thus, it helps to monitor and
receives notifications while the motion is determined. Apart from this the image can be captured and
find the faces. It helps in sending images to Smartphones by using various applications of telegrams.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4FACE DETECTION AND IOT SECURITY
Moreover, the IoT is based on the applications of telegrams that is utilized for seeing the tasks and
receive notices as the movements is found.
García et al. (2017) mentions that resberry pi is an efficient board providing the environment
of programming. Its camera Moduleit comprises of 5 mega pixel of a camera module that is
compatible with the Rasberry Pi. Apart from this, Hu et al. (2017) servo motor consists of the motor
with the rotational angle within 0 to 180 degrees. This is helpful to use that at the latch of the door. It
is useful to open the door while any specific face gets determined. Again, the DTMF Module or the
“Dual Tone Multiple Frequency Based Module” has been using IC MT8870. It can be utilized for
controlling remotely the door locking. Again, it has been providing a smart interface to control the
projects to get remotely controlled. Then, there are software requirements that comprise the Opencv.
It is a python based vision library of computers aiding image processing. Again, Chen et al. (2016)
mentions about the Raspbian Jeeielt which is an operating system that is Linux Based. It is to be
installed within Resberry pi 3. It is regarded as the successor of the raspbian of Wizzy. Besides, it
has been delivering the scenario of programming for different language. At last, Othman and Aydin
(2017) discusses database which is a file that contains various faces. Here, the faces are been stored
according to expressions like happiness, sad and many more. Here, the image of a person with
glasses is also stored here.
3. Research questions, aims and sub-goals:
3.1. Research questions:
How to enhance face detection technology?
How IoT security is influenced through developing face detection technology?
Moreover, the IoT is based on the applications of telegrams that is utilized for seeing the tasks and
receive notices as the movements is found.
García et al. (2017) mentions that resberry pi is an efficient board providing the environment
of programming. Its camera Moduleit comprises of 5 mega pixel of a camera module that is
compatible with the Rasberry Pi. Apart from this, Hu et al. (2017) servo motor consists of the motor
with the rotational angle within 0 to 180 degrees. This is helpful to use that at the latch of the door. It
is useful to open the door while any specific face gets determined. Again, the DTMF Module or the
“Dual Tone Multiple Frequency Based Module” has been using IC MT8870. It can be utilized for
controlling remotely the door locking. Again, it has been providing a smart interface to control the
projects to get remotely controlled. Then, there are software requirements that comprise the Opencv.
It is a python based vision library of computers aiding image processing. Again, Chen et al. (2016)
mentions about the Raspbian Jeeielt which is an operating system that is Linux Based. It is to be
installed within Resberry pi 3. It is regarded as the successor of the raspbian of Wizzy. Besides, it
has been delivering the scenario of programming for different language. At last, Othman and Aydin
(2017) discusses database which is a file that contains various faces. Here, the faces are been stored
according to expressions like happiness, sad and many more. Here, the image of a person with
glasses is also stored here.
3. Research questions, aims and sub-goals:
3.1. Research questions:
How to enhance face detection technology?
How IoT security is influenced through developing face detection technology?

5FACE DETECTION AND IOT SECURITY
3.2. Discussion on aims:
At the present days, the security has turned into the primary concern at the society. It is found
that nobody’s home has been secured. Again, the technologies that are developed regarding security
has been easily tackled from the side of different intruders. Hence, the research proposal makes an
attempt to develop the system home security through IoT. The study aims the following
To create an IoT based system of automated door lock through face recognition.
Apart from this a development of new face recognition algorithm is also intended that can
take over various cons of algorithms such as linear discriminant analysis or LDA or principle
component analysis or PCA.
In this way the development of the system at IoT has been making notable changes in the current
security technologies. Using a micro-controller board has been helpful to deploy the simplicity with
flexibility under the system. Again, IoT usage has been aiding to monitor and control the system
distantly.
3.3. Analyzing sub-goals:
To develop the system on the basis on Rasberry-pi3, for making the house accessible as the
face is identified. This must be done through algorithms from the library of Open CV.
To allow the individuals by house owners for monitoring the entrance distantly.
To get the system less likely deceived as the owner is able to check every visitor under the
remote console.
To get identified by camera properly as how to never works.
To include the passcode functions regarding entrance that is corrupted by face recognition.
3.2. Discussion on aims:
At the present days, the security has turned into the primary concern at the society. It is found
that nobody’s home has been secured. Again, the technologies that are developed regarding security
has been easily tackled from the side of different intruders. Hence, the research proposal makes an
attempt to develop the system home security through IoT. The study aims the following
To create an IoT based system of automated door lock through face recognition.
Apart from this a development of new face recognition algorithm is also intended that can
take over various cons of algorithms such as linear discriminant analysis or LDA or principle
component analysis or PCA.
In this way the development of the system at IoT has been making notable changes in the current
security technologies. Using a micro-controller board has been helpful to deploy the simplicity with
flexibility under the system. Again, IoT usage has been aiding to monitor and control the system
distantly.
3.3. Analyzing sub-goals:
To develop the system on the basis on Rasberry-pi3, for making the house accessible as the
face is identified. This must be done through algorithms from the library of Open CV.
To allow the individuals by house owners for monitoring the entrance distantly.
To get the system less likely deceived as the owner is able to check every visitor under the
remote console.
To get identified by camera properly as how to never works.
To include the passcode functions regarding entrance that is corrupted by face recognition.

6FACE DETECTION AND IOT SECURITY
4. Analyzing theoretical content:
It is expected for the current experiment on face recognition technology that IoT can enable
the communication, actuating and sensing the system. This system can be automated easily. Hence,
one can move on to develop a smart home. This can be done by extending the system of security
(Davies et al. 2016). For developing that the Rasberry Pi micro-controller board regarding the
system is developing. This must also include the module of the pi camera to determine face and
programmable motors for opening the lock of the doors. Here, the suitable raspberry pi operating
system can be installed over the board of raspberry pi microcontroller (Gou et al. 2013).
As far as the door unlocking system is considered, servo motor at the latch of the door is to
be placed. Here, the motor can be programmed with the way that the system has been authentications
can be done on the person who is staying in the front of the camera. Moreover, it is intended that the
motor would be rotating o open the latch. For the experiment image processing technology can be
used for authenticating the individual for entering the home (Morabito et al. 2018). Again, for
processing the image, the pi camera module can be used. This is been attached to the camera module
of the Pi. It has been aiding for storing the different faces at the databases. As anyone needs to
access the home, he must stand in front of the camera. The device would identify the face. Then it
will be comparing the faces that are been stored within the database of LFW. Hence, as the face
matches the door can be unlocked automatically (Aydin and Othman 2017). However, as it never
happens a call of warning must be sent to the house owner.
4. Analyzing theoretical content:
It is expected for the current experiment on face recognition technology that IoT can enable
the communication, actuating and sensing the system. This system can be automated easily. Hence,
one can move on to develop a smart home. This can be done by extending the system of security
(Davies et al. 2016). For developing that the Rasberry Pi micro-controller board regarding the
system is developing. This must also include the module of the pi camera to determine face and
programmable motors for opening the lock of the doors. Here, the suitable raspberry pi operating
system can be installed over the board of raspberry pi microcontroller (Gou et al. 2013).
As far as the door unlocking system is considered, servo motor at the latch of the door is to
be placed. Here, the motor can be programmed with the way that the system has been authentications
can be done on the person who is staying in the front of the camera. Moreover, it is intended that the
motor would be rotating o open the latch. For the experiment image processing technology can be
used for authenticating the individual for entering the home (Morabito et al. 2018). Again, for
processing the image, the pi camera module can be used. This is been attached to the camera module
of the Pi. It has been aiding for storing the different faces at the databases. As anyone needs to
access the home, he must stand in front of the camera. The device would identify the face. Then it
will be comparing the faces that are been stored within the database of LFW. Hence, as the face
matches the door can be unlocked automatically (Aydin and Othman 2017). However, as it never
happens a call of warning must be sent to the house owner.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7FACE DETECTION AND IOT SECURITY
5. Discussion on experimental set-up:
Architectural setup:
In the experiment, the faces are to be stored at the database of Yale's face. Here, the faces are
to be stored within a specific system of nomenclatures. For instance, as the face to be stored in in sad
mood, the face can be stored as the name “subject.sad”. Again, as the individual wear spectacles, the
face can be stored as the name “subject.glasses”. Nevertheless, as the face becomes impossible to get
identified, an email can be sent to the house owner with an image of the human standing under the
camera (Pacheco and Hariri 2016). Similarly, as the call gets transferred to the house owners, the
owner can be notified about the person in front of that camera. As the owner understands the person,
they can simply open the door distantly through the DTMF module.
Software and Algorithm set-up:
Firstly, the OpenCV is a software library of open source computer vision. Moreover, the
library comprises of lots of optimized algorithms. These can be utilized by various IoT related areas
that involve face recognition and detection. Then, the image processing can be considered as the
operation that is mathematically intensive (Alam 2018). This is one of the greatest sectors of
research for the area of big data. At last, there is the haar cascade classifier algorithm. It is the
classifier that can be utilized for finding the object for which that has been trained and from that
source.
5. Discussion on experimental set-up:
Architectural setup:
In the experiment, the faces are to be stored at the database of Yale's face. Here, the faces are
to be stored within a specific system of nomenclatures. For instance, as the face to be stored in in sad
mood, the face can be stored as the name “subject.sad”. Again, as the individual wear spectacles, the
face can be stored as the name “subject.glasses”. Nevertheless, as the face becomes impossible to get
identified, an email can be sent to the house owner with an image of the human standing under the
camera (Pacheco and Hariri 2016). Similarly, as the call gets transferred to the house owners, the
owner can be notified about the person in front of that camera. As the owner understands the person,
they can simply open the door distantly through the DTMF module.
Software and Algorithm set-up:
Firstly, the OpenCV is a software library of open source computer vision. Moreover, the
library comprises of lots of optimized algorithms. These can be utilized by various IoT related areas
that involve face recognition and detection. Then, the image processing can be considered as the
operation that is mathematically intensive (Alam 2018). This is one of the greatest sectors of
research for the area of big data. At last, there is the haar cascade classifier algorithm. It is the
classifier that can be utilized for finding the object for which that has been trained and from that
source.

8FACE DETECTION AND IOT SECURITY
6. Evaluating the results, outcome and relevance:
6.1. Discussing the results:
It is understood that the security system suggested has been of low expense. It has also
included the lesser power consuming system. It has been easily providing a greater level of security
since it has assimilated the current technologies all-together. This includes IoT and face-recognition.
Besides, there are fast growing technologies on which the scientists and industries must conduct
their research. This is how the two innovations have been able to put notable effects on developing
security systems. Because of this, security has been double. Again, remote monitoring and
controlling has been possible due to the usage of IoT and identifying face to make that almost
impossible for hacking. Thus, the door lock system of face recognition is successfully finished as
planned. Apart from thus, face recognition and passcode have been worked well. Moreover, high
accuracy has been there to identify the faces f house owners and identify the way of sending the
image of matched faces to another raspberry pi within time. Further, due to this a smart output is
provided. This has taken smart time to determine that. Thus the experiment has been satisfactory to
build on that.
6.2. Analyzing the outcomes:
It has brought low costs. It has been helpful for remote monitoring. It has been flexible and
scalable. Besides, it has included less consumption of power. Further, it is understood that the new
embedded innovations can be simply included for that development because of the usage of
Rasberry Pi. Ultimately it is also evaluated that along with the Internet, the system can also work in
the offline mode also.
6. Evaluating the results, outcome and relevance:
6.1. Discussing the results:
It is understood that the security system suggested has been of low expense. It has also
included the lesser power consuming system. It has been easily providing a greater level of security
since it has assimilated the current technologies all-together. This includes IoT and face-recognition.
Besides, there are fast growing technologies on which the scientists and industries must conduct
their research. This is how the two innovations have been able to put notable effects on developing
security systems. Because of this, security has been double. Again, remote monitoring and
controlling has been possible due to the usage of IoT and identifying face to make that almost
impossible for hacking. Thus, the door lock system of face recognition is successfully finished as
planned. Apart from thus, face recognition and passcode have been worked well. Moreover, high
accuracy has been there to identify the faces f house owners and identify the way of sending the
image of matched faces to another raspberry pi within time. Further, due to this a smart output is
provided. This has taken smart time to determine that. Thus the experiment has been satisfactory to
build on that.
6.2. Analyzing the outcomes:
It has brought low costs. It has been helpful for remote monitoring. It has been flexible and
scalable. Besides, it has included less consumption of power. Further, it is understood that the new
embedded innovations can be simply included for that development because of the usage of
Rasberry Pi. Ultimately it is also evaluated that along with the Internet, the system can also work in
the offline mode also.

9FACE DETECTION AND IOT SECURITY
6.3. The relevance of the results:
Here, the security system has been the assimilation of the IoT and face recognition system.
Thus the technologies have been involving the rise in technologies. With that, most of the
developments can be performed. Thus, there are various algorithms of face identifications to be
developed till date. However, there has been none who are proper and thus everyone has its
individual drawbacks. Thus, for making a suitable design for the future, the algorithm of face
identification can be performed. Here, the new algorithms can also be introduced. In this way
technology has been scalable. Thus the latest changes can be done. Besides, the latest hardware can
be attached with ease. In this way, the idea of a smart home can be deployed. Here, everything at
home is intended to be effective. This refers to the fact that there is no necessity to provide a
command to the hardware all the time. Again, the hardware itself has been knowing what to do and
not to do.
7. Project Planning and Gantt Charts:
During the implementation of the project is must be reminded that whether the project has
been on course. It must be viewed till the ultimate activity at the Gantt Chart. Then, it must be
reviewed that any activity has been overshooting the deadline. Next, the links between the tasks
needed are to be determined. Through unlinking the activities one never rely on others. Here, the
available slack time can be used. Thus the flexibility can be maximized. However, as some tasks are
overlapping each other, the overall duration can be reduced for the projects. As it occurs, suitable
lead times can be assigned using lag and lead time in the Gantt Chart. Next, it must be checked
whether the constraints working are checked. It must also be checked that the tasks have proper
constraints. It can be developed inadvertently and can result in trouble. Further, as the constraints
have been commonly overriding the links, schedule conflicts can be introduced.
6.3. The relevance of the results:
Here, the security system has been the assimilation of the IoT and face recognition system.
Thus the technologies have been involving the rise in technologies. With that, most of the
developments can be performed. Thus, there are various algorithms of face identifications to be
developed till date. However, there has been none who are proper and thus everyone has its
individual drawbacks. Thus, for making a suitable design for the future, the algorithm of face
identification can be performed. Here, the new algorithms can also be introduced. In this way
technology has been scalable. Thus the latest changes can be done. Besides, the latest hardware can
be attached with ease. In this way, the idea of a smart home can be deployed. Here, everything at
home is intended to be effective. This refers to the fact that there is no necessity to provide a
command to the hardware all the time. Again, the hardware itself has been knowing what to do and
not to do.
7. Project Planning and Gantt Charts:
During the implementation of the project is must be reminded that whether the project has
been on course. It must be viewed till the ultimate activity at the Gantt Chart. Then, it must be
reviewed that any activity has been overshooting the deadline. Next, the links between the tasks
needed are to be determined. Through unlinking the activities one never rely on others. Here, the
available slack time can be used. Thus the flexibility can be maximized. However, as some tasks are
overlapping each other, the overall duration can be reduced for the projects. As it occurs, suitable
lead times can be assigned using lag and lead time in the Gantt Chart. Next, it must be checked
whether the constraints working are checked. It must also be checked that the tasks have proper
constraints. It can be developed inadvertently and can result in trouble. Further, as the constraints
have been commonly overriding the links, schedule conflicts can be introduced.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
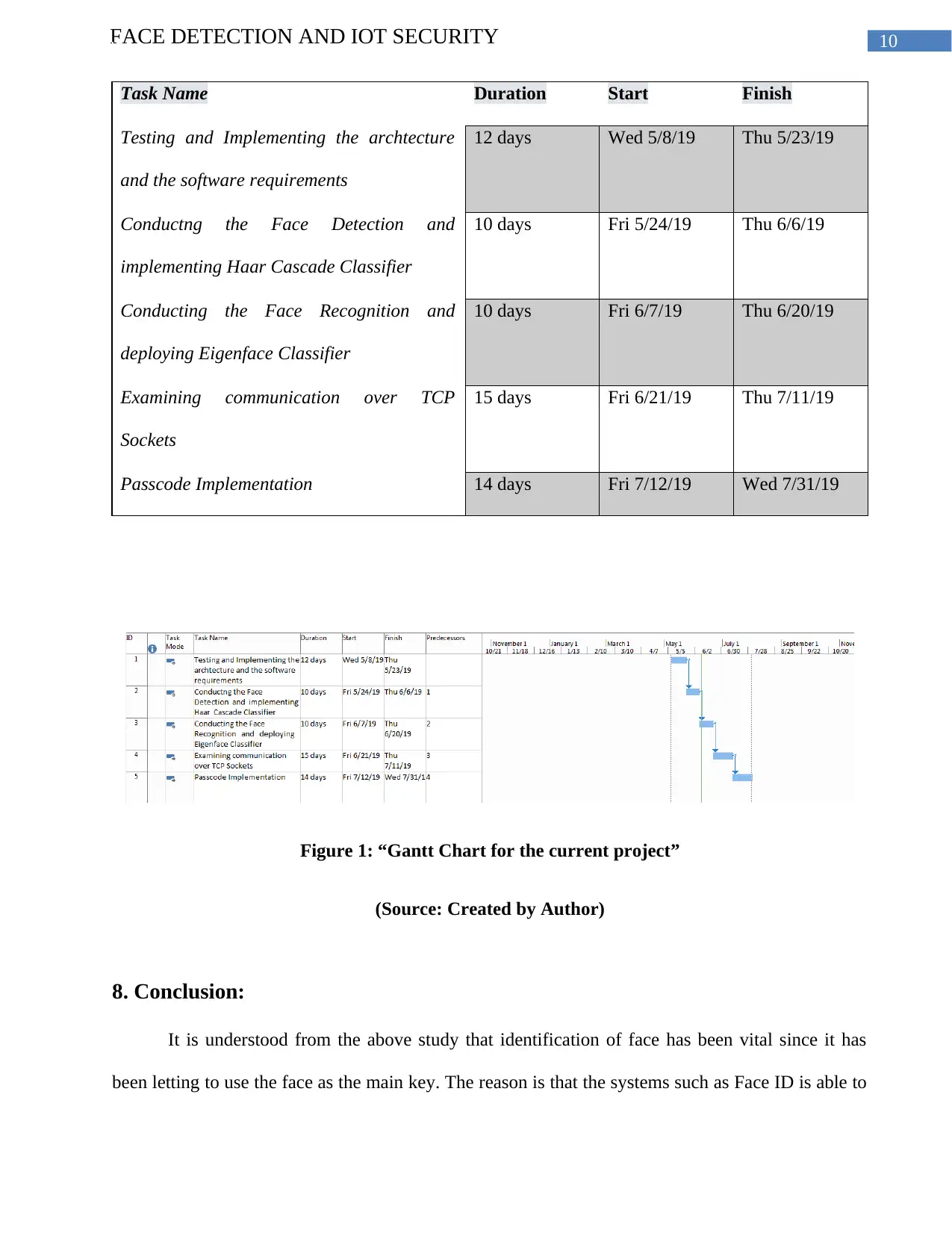
10FACE DETECTION AND IOT SECURITY
Task Name Duration Start Finish
Testing and Implementing the archtecture
and the software requirements
12 days Wed 5/8/19 Thu 5/23/19
Conductng the Face Detection and
implementing Haar Cascade Classifier
10 days Fri 5/24/19 Thu 6/6/19
Conducting the Face Recognition and
deploying Eigenface Classifier
10 days Fri 6/7/19 Thu 6/20/19
Examining communication over TCP
Sockets
15 days Fri 6/21/19 Thu 7/11/19
Passcode Implementation 14 days Fri 7/12/19 Wed 7/31/19
Figure 1: “Gantt Chart for the current project”
(Source: Created by Author)
8. Conclusion:
It is understood from the above study that identification of face has been vital since it has
been letting to use the face as the main key. The reason is that the systems such as Face ID is able to
Task Name Duration Start Finish
Testing and Implementing the archtecture
and the software requirements
12 days Wed 5/8/19 Thu 5/23/19
Conductng the Face Detection and
implementing Haar Cascade Classifier
10 days Fri 5/24/19 Thu 6/6/19
Conducting the Face Recognition and
deploying Eigenface Classifier
10 days Fri 6/7/19 Thu 6/20/19
Examining communication over TCP
Sockets
15 days Fri 6/21/19 Thu 7/11/19
Passcode Implementation 14 days Fri 7/12/19 Wed 7/31/19
Figure 1: “Gantt Chart for the current project”
(Source: Created by Author)
8. Conclusion:
It is understood from the above study that identification of face has been vital since it has
been letting to use the face as the main key. The reason is that the systems such as Face ID is able to

11FACE DETECTION AND IOT SECURITY
read the expressions at real time. In this way it is meant that it the time to move to devices that can
be managed through facial gestures. Under the space of IoT, it has indicated the appliances to be
operated rather than conventional security control. Moreover, it is also seen that there is a rise in
demands to make the IoT systems to function easily and efficiently. Here, they have been also
requiring the systems to get personal. For instance, it can be imagined that Amazon Echo and
Google Home could determine the face and bring the user up the setting of users despite the person
needing any announcement of the identity. In this way the wearables have been getting high benefits
from this type of system. Further, none has required to input the passcode on the smartwatch or
additional wearable device. Here, the facial identification of the user has been great. Controlling the
gesture has been also helpful here that the IoT. Again, the individuals have needed the wearable to
remain fashionable, functional and seamless. Nonetheless, this has been slightly much acceptable
and operate gadgets with the method of eye tracking. Besides, the telecommunications, the eye-
tracking has the end-all-be-all ofseamless monitoring. Here, it must be reminded that gesture
controlling is the initial step over the road. This one can be one to the few of considering the step.
10. References:
Alam, T., 2018. A Reliable Communication Framework and Its Use in Internet of Things (IoT).
International Journal of Scientific Research in Computer Science, Engi-neering and Information
Technology (IJSRCSEIT), ISSN, pp.2456-3307.
Amin, A.H.M., Ahmad, N.M. and Ali, A.M.M., 2016, May. Decentralized face recognition scheme
for distributed video surveillance in IoT-cloud infrastructure. In 2016 IEEE Region 10 Symposium
(TENSYMP) (pp. 119-124). IEEE.
read the expressions at real time. In this way it is meant that it the time to move to devices that can
be managed through facial gestures. Under the space of IoT, it has indicated the appliances to be
operated rather than conventional security control. Moreover, it is also seen that there is a rise in
demands to make the IoT systems to function easily and efficiently. Here, they have been also
requiring the systems to get personal. For instance, it can be imagined that Amazon Echo and
Google Home could determine the face and bring the user up the setting of users despite the person
needing any announcement of the identity. In this way the wearables have been getting high benefits
from this type of system. Further, none has required to input the passcode on the smartwatch or
additional wearable device. Here, the facial identification of the user has been great. Controlling the
gesture has been also helpful here that the IoT. Again, the individuals have needed the wearable to
remain fashionable, functional and seamless. Nonetheless, this has been slightly much acceptable
and operate gadgets with the method of eye tracking. Besides, the telecommunications, the eye-
tracking has the end-all-be-all ofseamless monitoring. Here, it must be reminded that gesture
controlling is the initial step over the road. This one can be one to the few of considering the step.
10. References:
Alam, T., 2018. A Reliable Communication Framework and Its Use in Internet of Things (IoT).
International Journal of Scientific Research in Computer Science, Engi-neering and Information
Technology (IJSRCSEIT), ISSN, pp.2456-3307.
Amin, A.H.M., Ahmad, N.M. and Ali, A.M.M., 2016, May. Decentralized face recognition scheme
for distributed video surveillance in IoT-cloud infrastructure. In 2016 IEEE Region 10 Symposium
(TENSYMP) (pp. 119-124). IEEE.

12FACE DETECTION AND IOT SECURITY
Aydin, I. and Othman, N.A., 2017, September. A new IoT combined face detection of people by
using computer vision for security application. In 2017 International Artificial Intelligence and Data
Processing Symposium (IDAP) (pp. 1-6). IEEE.
Chen, D., Cong, J., Gurumani, S., Hwu, W.M., Rupnow, K. and Zhang, Z., 2016. Platform choices
and design demands for IoT platforms: cost, power, and performance tradeoffs. IET Cyber-Physical
Systems: Theory & Applications, 1(1), pp.70-77.
Conti, F., Schilling, R., Schiavone, P.D., Pullini, A., Rossi, D., Gürkaynak, F.K., Muehlberghuber,
M., Gautschi, M., Loi, I., Haugou, G. and Mangard, S., 2017. An IoT endpoint system-on-chip for
secure and energy-efficient near-sensor analytics. IEEE Transactions on Circuits and Systems I:
Regular Papers, 64(9), pp.2481-2494.
Davies, N., Taft, N., Satyanarayanan, M., Clinch, S. and Amos, B., 2016, February. Privacy
mediators: Helping IoT cross the chasm. In Proceedings of the 17th International Workshop on
Mobile Computing Systems and Applications (pp. 39-44). ACM.
García, C.G., Meana-Llorián, D., G-Bustelo, B.C.P., Lovelle, J.M.C. and Garcia-Fernandez, N.,
2017. Midgar: Detection of people through computer vision in the Internet of Things scenarios to
improve the security in Smart Cities, Smart Towns, and Smart Homes. Future Generation Computer
Systems, 76, pp.301-313.
Gou, Q., Yan, L., Liu, Y. and Li, Y., 2013, August. Construction and strategies in IoT security
system. In 2013 IEEE international conference on green computing and communications and IEEE
internet of things and IEEE cyber, physical and social computing (pp. 1129-1132). IEEE.
Aydin, I. and Othman, N.A., 2017, September. A new IoT combined face detection of people by
using computer vision for security application. In 2017 International Artificial Intelligence and Data
Processing Symposium (IDAP) (pp. 1-6). IEEE.
Chen, D., Cong, J., Gurumani, S., Hwu, W.M., Rupnow, K. and Zhang, Z., 2016. Platform choices
and design demands for IoT platforms: cost, power, and performance tradeoffs. IET Cyber-Physical
Systems: Theory & Applications, 1(1), pp.70-77.
Conti, F., Schilling, R., Schiavone, P.D., Pullini, A., Rossi, D., Gürkaynak, F.K., Muehlberghuber,
M., Gautschi, M., Loi, I., Haugou, G. and Mangard, S., 2017. An IoT endpoint system-on-chip for
secure and energy-efficient near-sensor analytics. IEEE Transactions on Circuits and Systems I:
Regular Papers, 64(9), pp.2481-2494.
Davies, N., Taft, N., Satyanarayanan, M., Clinch, S. and Amos, B., 2016, February. Privacy
mediators: Helping IoT cross the chasm. In Proceedings of the 17th International Workshop on
Mobile Computing Systems and Applications (pp. 39-44). ACM.
García, C.G., Meana-Llorián, D., G-Bustelo, B.C.P., Lovelle, J.M.C. and Garcia-Fernandez, N.,
2017. Midgar: Detection of people through computer vision in the Internet of Things scenarios to
improve the security in Smart Cities, Smart Towns, and Smart Homes. Future Generation Computer
Systems, 76, pp.301-313.
Gou, Q., Yan, L., Liu, Y. and Li, Y., 2013, August. Construction and strategies in IoT security
system. In 2013 IEEE international conference on green computing and communications and IEEE
internet of things and IEEE cyber, physical and social computing (pp. 1129-1132). IEEE.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13FACE DETECTION AND IOT SECURITY
Hu, P., Ning, H., Qiu, T., Song, H., Wang, Y. and Yao, X., 2017. Security and privacy preservation
scheme of face identification and resolution framework using fog computing in internet of things.
IEEE Internet of Things Journal, 4(5), pp.1143-1155.
Morabito, R., Cozzolino, V., Ding, A.Y., Beijar, N. and Ott, J., 2018. Consolidate IoT edge
computing with lightweight virtualization. IEEE Network, 32(1), pp.102-111.
Motlagh, N.H., Bagaa, M. and Taleb, T., 2017. UAV-based IoT platform: A crowd surveillance use
case. IEEE Communications Magazine, 55(2), pp.128-134.
Ning, H., Liu, H. and Yang, L.T., 2013. Cyberentity security in the internet of things. Computer,
46(4), pp.46-53.
Othman, N.A. and Aydin, I., 2017, September. A new IoT combined body detection of people by
using computer vision for security application. In 2017 9th International Conference on
Computational Intelligence and Communication Networks (CICN) (pp. 108-112). IEEE.
Pacheco, J. and Hariri, S., 2016, September. IoT security framework for smart cyber infrastructures.
In 2016 IEEE 1st International Workshops on Foundations and Applications of Self* Systems (FAS*
W) (pp. 242-247). IEEE.
Sarigiannidis, P., Karapistoli, E. and Economides, A.A., 2015, June. Visiot: A threat visualisation
tool for iot systems security. In 2015 IEEE International Conference on Communication Workshop
(ICCW) (pp. 2633-2638). IEEE.
Wang, T., Yang, J., Lei, Z., Liao, S. and Li, S.Z., 2013, June. Face liveness detection using 3D
structure recovered from a single camera. In 2013 International Conference on Biometrics (ICB)
(pp. 1-6). IEEE.
Hu, P., Ning, H., Qiu, T., Song, H., Wang, Y. and Yao, X., 2017. Security and privacy preservation
scheme of face identification and resolution framework using fog computing in internet of things.
IEEE Internet of Things Journal, 4(5), pp.1143-1155.
Morabito, R., Cozzolino, V., Ding, A.Y., Beijar, N. and Ott, J., 2018. Consolidate IoT edge
computing with lightweight virtualization. IEEE Network, 32(1), pp.102-111.
Motlagh, N.H., Bagaa, M. and Taleb, T., 2017. UAV-based IoT platform: A crowd surveillance use
case. IEEE Communications Magazine, 55(2), pp.128-134.
Ning, H., Liu, H. and Yang, L.T., 2013. Cyberentity security in the internet of things. Computer,
46(4), pp.46-53.
Othman, N.A. and Aydin, I., 2017, September. A new IoT combined body detection of people by
using computer vision for security application. In 2017 9th International Conference on
Computational Intelligence and Communication Networks (CICN) (pp. 108-112). IEEE.
Pacheco, J. and Hariri, S., 2016, September. IoT security framework for smart cyber infrastructures.
In 2016 IEEE 1st International Workshops on Foundations and Applications of Self* Systems (FAS*
W) (pp. 242-247). IEEE.
Sarigiannidis, P., Karapistoli, E. and Economides, A.A., 2015, June. Visiot: A threat visualisation
tool for iot systems security. In 2015 IEEE International Conference on Communication Workshop
(ICCW) (pp. 2633-2638). IEEE.
Wang, T., Yang, J., Lei, Z., Liao, S. and Li, S.Z., 2013, June. Face liveness detection using 3D
structure recovered from a single camera. In 2013 International Conference on Biometrics (ICB)
(pp. 1-6). IEEE.
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





