Faculty of Engineering and Environment
VerifiedAdded on 2022/08/20
|13
|2659
|12
Assignment
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Faculty of Engineering and Environment
KF7028 Research and Project Management
Assignment: Research Proposal
Project Title: Cloud Security and its utilization in IT industry
Module: KF7028 – Research and Project Management
Module tutor: Shelagh Keogh
Supervisor/Tutor name:
Assignment title: MSc Research Proposal
Student name and your university identifier: (always underline the surname/family name by
which you are recorded in the university systems)
Programme or course of study:
Confirmation that you have completed the draft of your ethical approval process:
Word Count:
1
KF7028 Research and Project Management
Assignment: Research Proposal
Project Title: Cloud Security and its utilization in IT industry
Module: KF7028 – Research and Project Management
Module tutor: Shelagh Keogh
Supervisor/Tutor name:
Assignment title: MSc Research Proposal
Student name and your university identifier: (always underline the surname/family name by
which you are recorded in the university systems)
Programme or course of study:
Confirmation that you have completed the draft of your ethical approval process:
Word Count:
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1. Background
Cloud Computing had become one of the most integral part of computing programs
nowadays utilised in almost every organisation. Since its Inception in the year 2007 cloud
computing one of the most interesting field in the information technology industry. It is
mostly based on the research areas with virtualizations, grid computing, SOA and utility
computing. It is a type of computing which mostly relies on the sharing of integral computer
resources like processes, memory and application. This stored computing resource is shared
through request by organisations over the internet with the help of applications [1]. Thus for
sharing and storing of data, instead of physical devices, applications are being used. The
introduction of cloud computing had updated the needs of application and downgraded the
uses of hard drives or other physical storage. Storing of information with the utilisation of
applications reduce the cost of having hardware storage systems. This was easier to
implement because of the economic satisfaction that an organisation would have can also
utilise the resources saved instead of having a physical storage device. The remote services
are also available where with the help of cloud computing a user can access the stored data
through the help of an application without a physical device. The accessing and manipulation
of the stored data can happen over the internet with the help of applications, which means it
can also be done remotely [2]. However the amount of data breach an unauthorised access
with the help of valid user accounts that has been reported so far also provides information
about the cloud services being vulnerable to the unauthorised access of the malicious
attackers.
The research paper would that find about the data breach an unauthorised access that has
been ensuing upon the use of cloud computing causing organizations to go through financial
debacles and loss of important resources. This would clear out the security issues that IT
industry has been facing with the implementation of cloud services so that in future they
would be able to figure out a better way mitigating the issues that cloud services have.
2. Aim/Research question
The primary aim of this research is to find about the security issues that persist with cloud
computing and how Cloud Security is utilised in the IT industry.
Research questions for this paper can be framed as below:
What is Cloud Security?
How cloud computing security issues can be classified?
What effects do the cloud computing security issues have on the industries?
How the IT industry is affected by the cloud security issues?
How is the situation in the IT industry about the utilisation of Cloud Security?
2
Cloud Computing had become one of the most integral part of computing programs
nowadays utilised in almost every organisation. Since its Inception in the year 2007 cloud
computing one of the most interesting field in the information technology industry. It is
mostly based on the research areas with virtualizations, grid computing, SOA and utility
computing. It is a type of computing which mostly relies on the sharing of integral computer
resources like processes, memory and application. This stored computing resource is shared
through request by organisations over the internet with the help of applications [1]. Thus for
sharing and storing of data, instead of physical devices, applications are being used. The
introduction of cloud computing had updated the needs of application and downgraded the
uses of hard drives or other physical storage. Storing of information with the utilisation of
applications reduce the cost of having hardware storage systems. This was easier to
implement because of the economic satisfaction that an organisation would have can also
utilise the resources saved instead of having a physical storage device. The remote services
are also available where with the help of cloud computing a user can access the stored data
through the help of an application without a physical device. The accessing and manipulation
of the stored data can happen over the internet with the help of applications, which means it
can also be done remotely [2]. However the amount of data breach an unauthorised access
with the help of valid user accounts that has been reported so far also provides information
about the cloud services being vulnerable to the unauthorised access of the malicious
attackers.
The research paper would that find about the data breach an unauthorised access that has
been ensuing upon the use of cloud computing causing organizations to go through financial
debacles and loss of important resources. This would clear out the security issues that IT
industry has been facing with the implementation of cloud services so that in future they
would be able to figure out a better way mitigating the issues that cloud services have.
2. Aim/Research question
The primary aim of this research is to find about the security issues that persist with cloud
computing and how Cloud Security is utilised in the IT industry.
Research questions for this paper can be framed as below:
What is Cloud Security?
How cloud computing security issues can be classified?
What effects do the cloud computing security issues have on the industries?
How the IT industry is affected by the cloud security issues?
How is the situation in the IT industry about the utilisation of Cloud Security?
2

3. Background, Motivation and Relevance
The world of computation has changed and become much for centralised in the last few
decades where distributed systems as seen a virtual centralisation through cloud computing.
Where location identification and data processing has different realms of computing, on the
other hand there has been full control of data and it’s processing for user in their own
computer. Therefore it is extremely important to maintain the data provided by a vendor into
the computer of a client for a customer. The issue arises in this case is that the Client or the
customer is not aware from where the data and its processing is being available in the
computer provided by a vendor and how the services are making it possible to access the data
[3]. They do not even have an idea about how the data is stored. Logically, client does not
have a control over the stored data. Client do not have any control over the data stored in a
cloud and therefore Cloud Computing uses this connections as their communication media. It
is a known fact that the vendor might be using some assurances about the service level
agreements to convince the customers about the security issues. How the organisations that
are using Cloud Computing as their service infrastructure would be much more aware of the
facts and they how they would like to critically examine the confidential or secure data
transfer or storing through cloud architecture for their business sensitive data and applications
is one of the most important factor in the latest IT industry scenario. Organisations have a
much better and deeper look out at the security of the corporate data that is transferred to the
cloud. It cannot be said that the organisation do not find it difficult to have all their business
sensitive data stored over the cloud but different services and platforms are available for them
to use as their infrastructure. This can mostly be classified into three separate services. They
are, Software as a Service or SaaS, Infrastructure as a Service or IaaS and Platform as a
Service or PaaS [4].
There have been several reports detected from different parts of the world related to the IT
industry that has presented the evidences of security breaches in cloud computing. In the year
2019, there have been numerous reports about data breaches alone for the IT industries. As
per reports, because of a failure in the system for Verifications.io, a 150 GB MongoDB
database containing over 808 million to 2 billion records worldwide was found potentially
vulnerable to data breach because it was not password protected [5]. The unauthorized
authentication made the file discoverable by Security Discovery researchers, after which the
site was taken offline. Similar to this, there have been many other potential security breaches
or even attacks on the cloud security in IT organizations reported after the businesses started
to infiltrate the utilization of cloud services. Therefore, how the businesses in the IT
industries have taken up these security threat reports and implied mitigations strategies for
securing the cloud services must be researched about.
In the context of the latest security threats in the cloud services, especially for the IT
industries, this research is extremely relevant and necessary to continue with.
3
The world of computation has changed and become much for centralised in the last few
decades where distributed systems as seen a virtual centralisation through cloud computing.
Where location identification and data processing has different realms of computing, on the
other hand there has been full control of data and it’s processing for user in their own
computer. Therefore it is extremely important to maintain the data provided by a vendor into
the computer of a client for a customer. The issue arises in this case is that the Client or the
customer is not aware from where the data and its processing is being available in the
computer provided by a vendor and how the services are making it possible to access the data
[3]. They do not even have an idea about how the data is stored. Logically, client does not
have a control over the stored data. Client do not have any control over the data stored in a
cloud and therefore Cloud Computing uses this connections as their communication media. It
is a known fact that the vendor might be using some assurances about the service level
agreements to convince the customers about the security issues. How the organisations that
are using Cloud Computing as their service infrastructure would be much more aware of the
facts and they how they would like to critically examine the confidential or secure data
transfer or storing through cloud architecture for their business sensitive data and applications
is one of the most important factor in the latest IT industry scenario. Organisations have a
much better and deeper look out at the security of the corporate data that is transferred to the
cloud. It cannot be said that the organisation do not find it difficult to have all their business
sensitive data stored over the cloud but different services and platforms are available for them
to use as their infrastructure. This can mostly be classified into three separate services. They
are, Software as a Service or SaaS, Infrastructure as a Service or IaaS and Platform as a
Service or PaaS [4].
There have been several reports detected from different parts of the world related to the IT
industry that has presented the evidences of security breaches in cloud computing. In the year
2019, there have been numerous reports about data breaches alone for the IT industries. As
per reports, because of a failure in the system for Verifications.io, a 150 GB MongoDB
database containing over 808 million to 2 billion records worldwide was found potentially
vulnerable to data breach because it was not password protected [5]. The unauthorized
authentication made the file discoverable by Security Discovery researchers, after which the
site was taken offline. Similar to this, there have been many other potential security breaches
or even attacks on the cloud security in IT organizations reported after the businesses started
to infiltrate the utilization of cloud services. Therefore, how the businesses in the IT
industries have taken up these security threat reports and implied mitigations strategies for
securing the cloud services must be researched about.
In the context of the latest security threats in the cloud services, especially for the IT
industries, this research is extremely relevant and necessary to continue with.
3
4. Scope, Objectives and Risk
The scope of the project is extremely vast as this is a very relevant topic on which the
research is about to be conducted. IT industry has faced several issues regarding the Cloud
Security mostly when it comes to the new systems which are technologically advanced [6].
Every time the organisations start to think of implementing a new cloud Service the security
system has to be given a thought before the implementation. Therefore if a research could
focus on how the organisations could gather IT security, the research would have much better
scope of experimenting the results further.
Following will be a detailed numbered steps that would outline how the objective of the
deliverables would be gathered with the help of SMART objectives. This would be listed as
below:
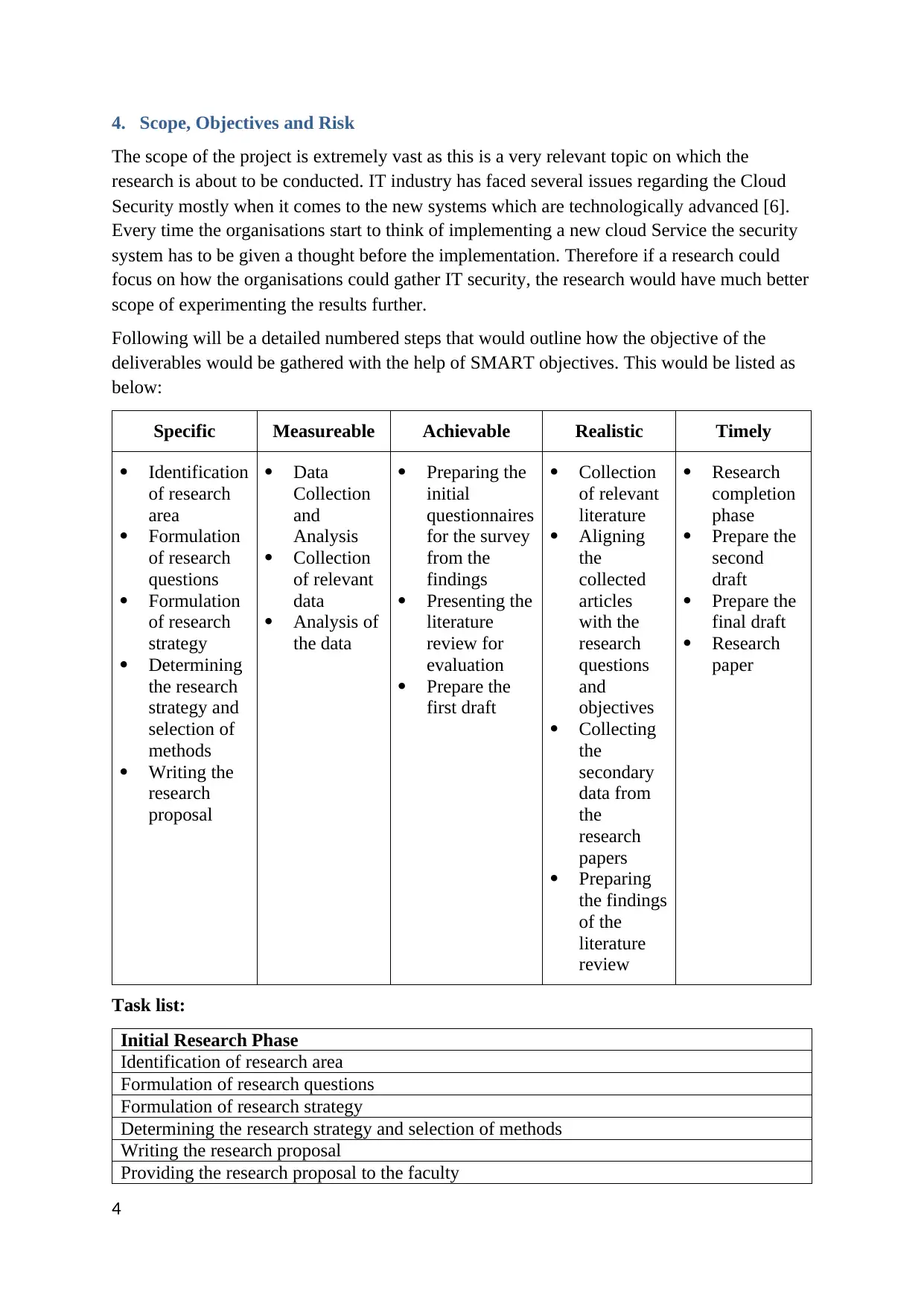
Specific Measureable Achievable Realistic Timely
Identification
of research
area
Formulation
of research
questions
Formulation
of research
strategy
Determining
the research
strategy and
selection of
methods
Writing the
research
proposal
Data
Collection
and
Analysis
Collection
of relevant
data
Analysis of
the data
Preparing the
initial
questionnaires
for the survey
from the
findings
Presenting the
literature
review for
evaluation
Prepare the
first draft
Collection
of relevant
literature
Aligning
the
collected
articles
with the
research
questions
and
objectives
Collecting
the
secondary
data from
the
research
papers
Preparing
the findings
of the
literature
review
Research
completion
phase
Prepare the
second
draft
Prepare the
final draft
Research
paper
Task list:
Initial Research Phase
Identification of research area
Formulation of research questions
Formulation of research strategy
Determining the research strategy and selection of methods
Writing the research proposal
Providing the research proposal to the faculty
4
The scope of the project is extremely vast as this is a very relevant topic on which the
research is about to be conducted. IT industry has faced several issues regarding the Cloud
Security mostly when it comes to the new systems which are technologically advanced [6].
Every time the organisations start to think of implementing a new cloud Service the security
system has to be given a thought before the implementation. Therefore if a research could
focus on how the organisations could gather IT security, the research would have much better
scope of experimenting the results further.
Following will be a detailed numbered steps that would outline how the objective of the
deliverables would be gathered with the help of SMART objectives. This would be listed as
below:
Specific Measureable Achievable Realistic Timely
Identification
of research
area
Formulation
of research
questions
Formulation
of research
strategy
Determining
the research
strategy and
selection of
methods
Writing the
research
proposal
Data
Collection
and
Analysis
Collection
of relevant
data
Analysis of
the data
Preparing the
initial
questionnaires
for the survey
from the
findings
Presenting the
literature
review for
evaluation
Prepare the
first draft
Collection
of relevant
literature
Aligning
the
collected
articles
with the
research
questions
and
objectives
Collecting
the
secondary
data from
the
research
papers
Preparing
the findings
of the
literature
review
Research
completion
phase
Prepare the
second
draft
Prepare the
final draft
Research
paper
Task list:
Initial Research Phase
Identification of research area
Formulation of research questions
Formulation of research strategy
Determining the research strategy and selection of methods
Writing the research proposal
Providing the research proposal to the faculty
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Literature Review
Collection of relevant literature
Aligning the collected articles with the research questions and objectives
Collecting the secondary data from the research papers
Preparing the findings of the literature review
Preparing the initial questionnaires for the survey from the findings
Presenting the literature review for evaluation
Data Collection and Analysis
Collection of relevant data
Analyse the data
Prepare the first draft
Research completion phase
Prepare the second draft
Prepare the final draft
Submitting the Research paper
5
Collection of relevant literature
Aligning the collected articles with the research questions and objectives
Collecting the secondary data from the research papers
Preparing the findings of the literature review
Preparing the initial questionnaires for the survey from the findings
Presenting the literature review for evaluation
Data Collection and Analysis
Collection of relevant data
Analyse the data
Prepare the first draft
Research completion phase
Prepare the second draft
Prepare the final draft
Submitting the Research paper
5
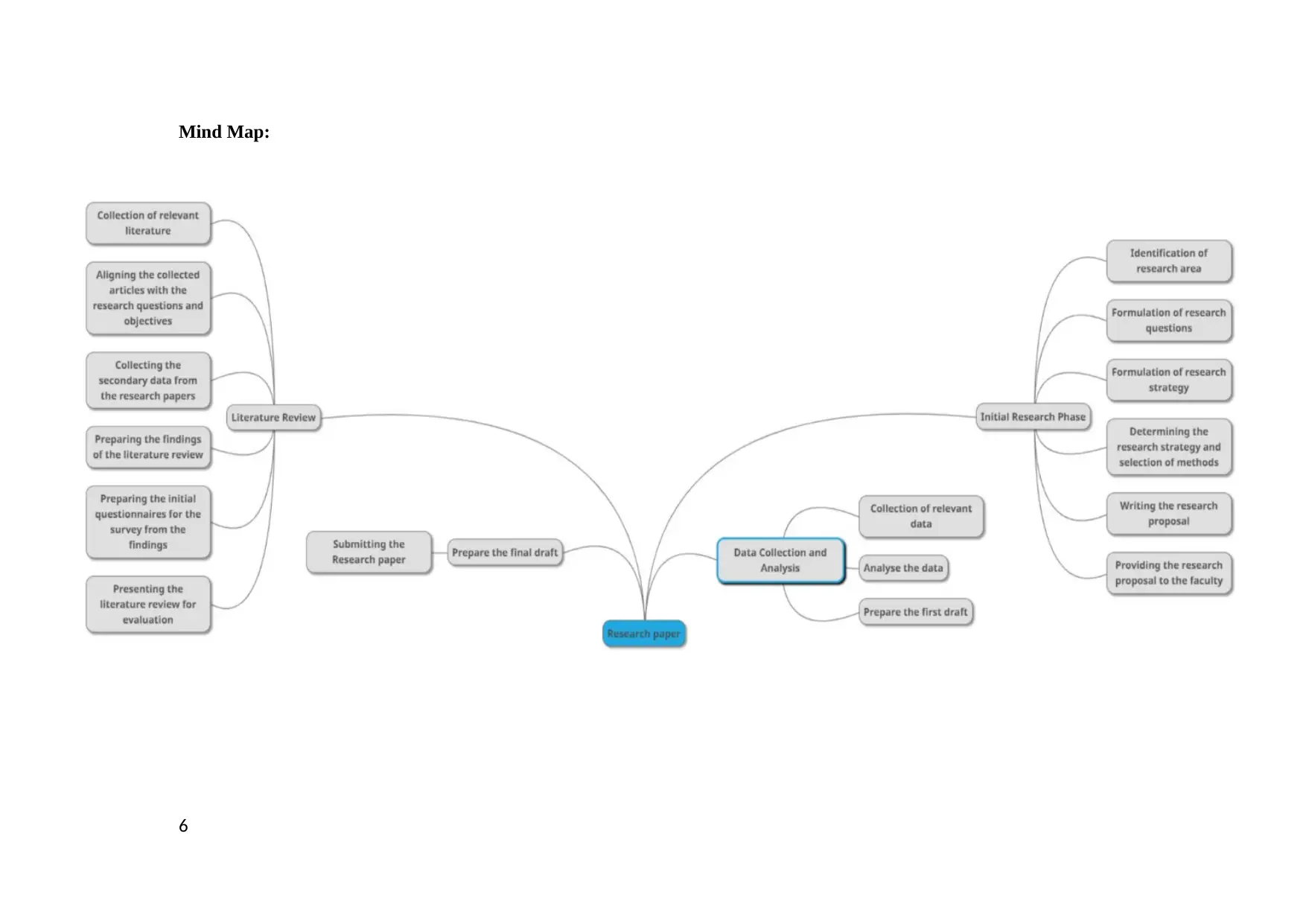
Mind Map:
6
6

7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5. Ethics, Legal, Social, Security and Professional Issues
Every project has several ethical issues attached to its associated with every part of the
project to consider the research area and also the security issues related to the conduction of
the research process [7]. The collection of data is the primary area in this research that clearly
represents why the conduction of a research paper has several ethical issues and how research
can be conducted following all the ethical standardizations.
5.1. Ethics Issues
There are several ethical issues that are associated with the standardization involving the
religion, philosophical faradism, model responsibilities, society beliefs, cultural
representation, rules and regulation in a profession. There are several codes of ethics
associated with the development of a research paper as well. While conducting a survey, no
data collected from a respondent can be manipulated in any way it can be counted as an
ethical issue [8]. Even while conducting a literature review for collecting secondary data from
the research papers presented by different authors, it is to be kept in mind that all credible
sources have to be deferred with in text citation and also where the direct quotations are used,
the sources need to be referred. On the other hand there should be no direct plagiarized
writing while representing the findings from the secondary sources.
Other than that there are several issues in computer science papers that are associated with
the conduction of an ethical research.
5.2. Social Issues
There are several social issues associated with information technology. Mostly these are the
communication breakdown that bars socializing with the family unit and also it ensures
cohesion within the group [9]. Other than that there are deformation of characters, identity
theft, addiction to gaming problematic situations in education, data privacy, and even
confidential data violation and vulnerability to unauthorised hackers.
5.3. Security Issues
Security issues are common when it comes to the preparation of an IT security system
especially with the cloud system applications. Since there are just an application,
infrastructure or web service, it becomes easier to find vulnerabilities in the system. There is
no physical data evidence and all of them are digitally recorded, stored and shared. For this
reason security reasons prevail in this case as well.
5.4. Professional Issues
Professional issues would not be applicable in this area as it is expected within a particular
professional body. Since the research is about various Cloud Security system and its
implementation in the IT industry therefore by no means there can be e a professional issue
described in this research paper [10]. This is because, first and foremost inclusion of the
8
Every project has several ethical issues attached to its associated with every part of the
project to consider the research area and also the security issues related to the conduction of
the research process [7]. The collection of data is the primary area in this research that clearly
represents why the conduction of a research paper has several ethical issues and how research
can be conducted following all the ethical standardizations.
5.1. Ethics Issues
There are several ethical issues that are associated with the standardization involving the
religion, philosophical faradism, model responsibilities, society beliefs, cultural
representation, rules and regulation in a profession. There are several codes of ethics
associated with the development of a research paper as well. While conducting a survey, no
data collected from a respondent can be manipulated in any way it can be counted as an
ethical issue [8]. Even while conducting a literature review for collecting secondary data from
the research papers presented by different authors, it is to be kept in mind that all credible
sources have to be deferred with in text citation and also where the direct quotations are used,
the sources need to be referred. On the other hand there should be no direct plagiarized
writing while representing the findings from the secondary sources.
Other than that there are several issues in computer science papers that are associated with
the conduction of an ethical research.
5.2. Social Issues
There are several social issues associated with information technology. Mostly these are the
communication breakdown that bars socializing with the family unit and also it ensures
cohesion within the group [9]. Other than that there are deformation of characters, identity
theft, addiction to gaming problematic situations in education, data privacy, and even
confidential data violation and vulnerability to unauthorised hackers.
5.3. Security Issues
Security issues are common when it comes to the preparation of an IT security system
especially with the cloud system applications. Since there are just an application,
infrastructure or web service, it becomes easier to find vulnerabilities in the system. There is
no physical data evidence and all of them are digitally recorded, stored and shared. For this
reason security reasons prevail in this case as well.
5.4. Professional Issues
Professional issues would not be applicable in this area as it is expected within a particular
professional body. Since the research is about various Cloud Security system and its
implementation in the IT industry therefore by no means there can be e a professional issue
described in this research paper [10]. This is because, first and foremost inclusion of the
8
detailed information about cloud security systems might not always be related to professional
issues. The development of the research paper would be based entirely upon technological
mismanagement and vulnerability caused due to lack of training, lesson understanding of the
technological world or even due to miscommunications.
6. Schedule of Activities
Task Name Duration Start Finish Predecessors
Formulation of research strategy 15 days Sat 22-
02-20
Wed 11-
03-20
Determining the research strategy and
selection of methods 2 days Sat 22-
02-20
Mon 24-
02-20
Writing the research proposal 3 days Tue 25-
02-20
Thu 27-
02-20 2
Providing the research proposal to the
faculty 0 days Thu 27-
02-20
Thu 27-
02-20 3
Literature Review 10 days Fri 28-
02-20
Wed 11-
03-20
Collection of relevant literature 16 days Thu 12-
03-20
Fri 27-03-
20 5
Aligning the collected articles with the
research questions and objectives 4 days Thu 12-
03-20
Sun 15-
03-20
Collecting the secondary data from the
research papers 2 days Mon 16-
03-20
Tue 17-
03-20 7
Preparing the findings of the literature
review 3 days Wed 18-
03-20
Fri 20-03-
20 8
Preparing the initial questionnaires for the
survey from the findings 1 day Sat 21-
03-20
Sat 21-03-
20 9
Presenting the literature review for
evaluation 0 days Sat 21-
03-20
Sat 21-03-
20 10
Data Collection and Analysis 5 days Sun 15-
03-20
Thu 19-
03-20
Collection of relevant data 2 days Sun 22-
03-20
Mon 23-
03-20 11
Analyse the data 3 days Fri 20-03-
20
Sun 22-
03-20 12
Prepare the first draft 0 days Mon 23-
03-20
Mon 23-
03-20 13
Research completion phase 5 days Sat 21-
03-20
Wed 25-
03-20
Prepare the second draft 2 days Tue 24-
03-20
Wed 25-
03-20 15
Prepare the final draft 2 days Thu 26-
03-20
Fri 27-03-
20 17
Submitting the Research paper 0 days Fri 27-03- Fri 27-03- 18
9
issues. The development of the research paper would be based entirely upon technological
mismanagement and vulnerability caused due to lack of training, lesson understanding of the
technological world or even due to miscommunications.
6. Schedule of Activities
Task Name Duration Start Finish Predecessors
Formulation of research strategy 15 days Sat 22-
02-20
Wed 11-
03-20
Determining the research strategy and
selection of methods 2 days Sat 22-
02-20
Mon 24-
02-20
Writing the research proposal 3 days Tue 25-
02-20
Thu 27-
02-20 2
Providing the research proposal to the
faculty 0 days Thu 27-
02-20
Thu 27-
02-20 3
Literature Review 10 days Fri 28-
02-20
Wed 11-
03-20
Collection of relevant literature 16 days Thu 12-
03-20
Fri 27-03-
20 5
Aligning the collected articles with the
research questions and objectives 4 days Thu 12-
03-20
Sun 15-
03-20
Collecting the secondary data from the
research papers 2 days Mon 16-
03-20
Tue 17-
03-20 7
Preparing the findings of the literature
review 3 days Wed 18-
03-20
Fri 20-03-
20 8
Preparing the initial questionnaires for the
survey from the findings 1 day Sat 21-
03-20
Sat 21-03-
20 9
Presenting the literature review for
evaluation 0 days Sat 21-
03-20
Sat 21-03-
20 10
Data Collection and Analysis 5 days Sun 15-
03-20
Thu 19-
03-20
Collection of relevant data 2 days Sun 22-
03-20
Mon 23-
03-20 11
Analyse the data 3 days Fri 20-03-
20
Sun 22-
03-20 12
Prepare the first draft 0 days Mon 23-
03-20
Mon 23-
03-20 13
Research completion phase 5 days Sat 21-
03-20
Wed 25-
03-20
Prepare the second draft 2 days Tue 24-
03-20
Wed 25-
03-20 15
Prepare the final draft 2 days Thu 26-
03-20
Fri 27-03-
20 17
Submitting the Research paper 0 days Fri 27-03- Fri 27-03- 18
9
20 20
Table 1: Schedule of Activities
(Source: Created by the Author)
Figure 1: Gantt Chart
(Source: Created by the Author)
10
ID Task
Mode
Task Name Duration Start Finish Predecessors Resource Names
1 Formulation of
research strategy
15 days Sat
22-02-20
Wed
11-03-20
2 Determining the
research strategy
and selection of
methods
2 days Sat
22-02-20
Mon
24-02-20
3 Writing the
research proposal
3 days Tue
25-02-20
Thu
27-02-20
2
4 Providing the
research proposal
to the faculty
0 days Thu
27-02-20
Thu
27-02-20
3
5 Literature
Review
10 days Fri
28-02-20
Wed
11-03-20
6 Collection of relevant
literature
16 days Thu
12-03-20
Fri
27-03-20
5
7 Aligning the
collected articles
with the research
questions and
objectives
4 days Thu
12-03-20
Sun
15-03-20
8 Collecting the
secondary data
from the research
papers
2 days Mon
16-03-20
Tue
17-03-20
7
9 Preparing the
findings of the
literature review
3 days Wed
18-03-20
Fri
20-03-20
8
10 Preparing the initial questionnaires for the survey from the findings1 day Sat 21-03-20Sat 21-03-209
11 Presenting the literature review for evaluation0 days Sat 21-03-20Sat 21-03-2010
12 Data Collection and Analysis5 days Sun 15-03-20Thu 19-03-20
13 Collection of relevant data2 days Sun 22-03-20Mon 23-03-2011
14 Analyse the data 3 days Fri 20-03-20Sun 22-03-2012
15 Prepare the first draft0 days Mon 23-03-20Mon 23-03-2013
16 Research completion phase5 days Sat 21-03-20Wed 25-03-20
17 Prepare the second draft2 days Tue 24-03-20Wed 25-03-2015
18 Prepare the final draft2 days Thu 26-03-20Fri 27-03-2017
19 Submitting the Research paper0 days Fri 27-03-20Fri 27-03-2018
27-02
21-03
23-03
27-03
02-02 09-02 16-02 23-02 01-03 08-03 15-03 22-03 29-03
February March April
Table 1: Schedule of Activities
(Source: Created by the Author)
Figure 1: Gantt Chart
(Source: Created by the Author)
10
ID Task
Mode
Task Name Duration Start Finish Predecessors Resource Names
1 Formulation of
research strategy
15 days Sat
22-02-20
Wed
11-03-20
2 Determining the
research strategy
and selection of
methods
2 days Sat
22-02-20
Mon
24-02-20
3 Writing the
research proposal
3 days Tue
25-02-20
Thu
27-02-20
2
4 Providing the
research proposal
to the faculty
0 days Thu
27-02-20
Thu
27-02-20
3
5 Literature
Review
10 days Fri
28-02-20
Wed
11-03-20
6 Collection of relevant
literature
16 days Thu
12-03-20
Fri
27-03-20
5
7 Aligning the
collected articles
with the research
questions and
objectives
4 days Thu
12-03-20
Sun
15-03-20
8 Collecting the
secondary data
from the research
papers
2 days Mon
16-03-20
Tue
17-03-20
7
9 Preparing the
findings of the
literature review
3 days Wed
18-03-20
Fri
20-03-20
8
10 Preparing the initial questionnaires for the survey from the findings1 day Sat 21-03-20Sat 21-03-209
11 Presenting the literature review for evaluation0 days Sat 21-03-20Sat 21-03-2010
12 Data Collection and Analysis5 days Sun 15-03-20Thu 19-03-20
13 Collection of relevant data2 days Sun 22-03-20Mon 23-03-2011
14 Analyse the data 3 days Fri 20-03-20Sun 22-03-2012
15 Prepare the first draft0 days Mon 23-03-20Mon 23-03-2013
16 Research completion phase5 days Sat 21-03-20Wed 25-03-20
17 Prepare the second draft2 days Tue 24-03-20Wed 25-03-2015
18 Prepare the final draft2 days Thu 26-03-20Fri 27-03-2017
19 Submitting the Research paper0 days Fri 27-03-20Fri 27-03-2018
27-02
21-03
23-03
27-03
02-02 09-02 16-02 23-02 01-03 08-03 15-03 22-03 29-03
February March April
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

7. Reference List
[1] M.S., Donovan, Innovation and Induction Corridors: A Proposal for Integrating Research,
Development, and Teacher Professional Preparation. Strategic Education Research Partnership,
2017.
[2] K.M., Shuman, Grant Proposal Preparation Readiness: A Glimpse at the Education Level of
Higher Education Faculty. Journal of Research Administration, 50(1), 2019, pp.89-107.
[3] S.A., Aljawarneh, A., Alawneh, and R., Jaradat, Cloud security engineering: Early stages of
SDLC. Future Generation Computer Systems, 74, 2017, pp.385-392.
[4] K., El Makkaoui, A., Ezzati, A. Beni-Hssane, and C., Motamed, Cloud security and privacy model
for providing secure cloud services. In 2016 2nd international conference on cloud computing
technologies and applications (CloudTech) 2016, May, (pp. 81-86). IEEE.
[5] F., Imran, Y.Yunfei and M., Ikram, CLOUD COMPUTING SECURITY ISSUES AND
THREATSINBUSINESSENVIRONMENT. GSJ, 7(7). 2019.
[6] D. Alsmadi, and V. Prybutok, Sharing and storage behavior via cloud computing: Security and
privacy in research and practice. Computers in Human Behavior, 85, 2018, pp.218-226.
[7] N.S., Kumar, M., Uvaneshwari, M. Viswanathan and K. Amsavalli, One-Tier Cache System
Applied to Data Mining Techniques to Enhance the Information Security in the
Cloud. Technology, 8(10), 2017, pp.1709-1717.
[8] N. Khan, and A. Al-Yasiri, Identifying cloud security threats to strengthen cloud computing
adoption framework. Procedia Computer Science, 94, 2016, pp.485-490.
[9] S., Khatal, A., Kadhane, R., Moon and I.,Tamboli, A secure mutual authentication protocol for
cloud computing using secret sharing and Image steganography. Development, 4(5), 2017.
[10] S.M., Altowaijri, An Architecture to Improve the Security of Cloud Computing in the Healthcare
Sector. In Smart Infrastructure and Applications (pp. 249-266). Springer, Cham, 2020.
11
[1] M.S., Donovan, Innovation and Induction Corridors: A Proposal for Integrating Research,
Development, and Teacher Professional Preparation. Strategic Education Research Partnership,
2017.
[2] K.M., Shuman, Grant Proposal Preparation Readiness: A Glimpse at the Education Level of
Higher Education Faculty. Journal of Research Administration, 50(1), 2019, pp.89-107.
[3] S.A., Aljawarneh, A., Alawneh, and R., Jaradat, Cloud security engineering: Early stages of
SDLC. Future Generation Computer Systems, 74, 2017, pp.385-392.
[4] K., El Makkaoui, A., Ezzati, A. Beni-Hssane, and C., Motamed, Cloud security and privacy model
for providing secure cloud services. In 2016 2nd international conference on cloud computing
technologies and applications (CloudTech) 2016, May, (pp. 81-86). IEEE.
[5] F., Imran, Y.Yunfei and M., Ikram, CLOUD COMPUTING SECURITY ISSUES AND
THREATSINBUSINESSENVIRONMENT. GSJ, 7(7). 2019.
[6] D. Alsmadi, and V. Prybutok, Sharing and storage behavior via cloud computing: Security and
privacy in research and practice. Computers in Human Behavior, 85, 2018, pp.218-226.
[7] N.S., Kumar, M., Uvaneshwari, M. Viswanathan and K. Amsavalli, One-Tier Cache System
Applied to Data Mining Techniques to Enhance the Information Security in the
Cloud. Technology, 8(10), 2017, pp.1709-1717.
[8] N. Khan, and A. Al-Yasiri, Identifying cloud security threats to strengthen cloud computing
adoption framework. Procedia Computer Science, 94, 2016, pp.485-490.
[9] S., Khatal, A., Kadhane, R., Moon and I.,Tamboli, A secure mutual authentication protocol for
cloud computing using secret sharing and Image steganography. Development, 4(5), 2017.
[10] S.M., Altowaijri, An Architecture to Improve the Security of Cloud Computing in the Healthcare
Sector. In Smart Infrastructure and Applications (pp. 249-266). Springer, Cham, 2020.
11

8. Appendix A
12
Name__________________________________________Department________________________
___________
Email address: __________________________________Phone number:
_______________________________
Mailing address:
_____________________________________________________________________________
This is an application for approval of: (please tick as many as apply)
Research project involving human participants
Course/Paper which involves student projects that collect data from human participants
Undergraduate student project which involves data collection from human participants
Master's degree research
PhD research
PhD research proposal to move from Conditional to Full enrolment
Supervisor’s name: (if applicable)
_____________________________________________________________
Supervisor’s approval (signature)
____________________________________________________________
Project Title:
________________________________________________________________________________
-
_________________________________________________________________________________
__________
Is this research associated with an external grant or funding? ⃞ Yes ⃞ No
Please specify:
________________________________________________________________________
I request approval for this research or related activity and attach all relevant
documentation necessary for evaluation under the Ethical Conduct in Human Research
and Related Activities Regulations.
I am applying under section 10 of the Ethical Conduct in Human Research and Related
Activities Regulations Large Random Sample Surveys and Similar Research Methodology
and consequently there is no consent form in this application.
I am applying under section 11 of the Ethical Conduct in Human Research and Related
Activities Regulations Field Research and consequently there is no consent form in this
application.
I have read and complied with the Ethical Conduct in Human Research and Related
Activities Regulations.
Principal Investigator’s signature :
_____________________________________________________________
Ethics Committee Action
12
Name__________________________________________Department________________________
___________
Email address: __________________________________Phone number:
_______________________________
Mailing address:
_____________________________________________________________________________
This is an application for approval of: (please tick as many as apply)
Research project involving human participants
Course/Paper which involves student projects that collect data from human participants
Undergraduate student project which involves data collection from human participants
Master's degree research
PhD research
PhD research proposal to move from Conditional to Full enrolment
Supervisor’s name: (if applicable)
_____________________________________________________________
Supervisor’s approval (signature)
____________________________________________________________
Project Title:
________________________________________________________________________________
-
_________________________________________________________________________________
__________
Is this research associated with an external grant or funding? ⃞ Yes ⃞ No
Please specify:
________________________________________________________________________
I request approval for this research or related activity and attach all relevant
documentation necessary for evaluation under the Ethical Conduct in Human Research
and Related Activities Regulations.
I am applying under section 10 of the Ethical Conduct in Human Research and Related
Activities Regulations Large Random Sample Surveys and Similar Research Methodology
and consequently there is no consent form in this application.
I am applying under section 11 of the Ethical Conduct in Human Research and Related
Activities Regulations Field Research and consequently there is no consent form in this
application.
I have read and complied with the Ethical Conduct in Human Research and Related
Activities Regulations.
Principal Investigator’s signature :
_____________________________________________________________
Ethics Committee Action

13
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




