A Detailed Comparison of File Integrity Monitoring Software Solutions
VerifiedAdded on 2023/06/10
|5
|698
|430
Report
AI Summary
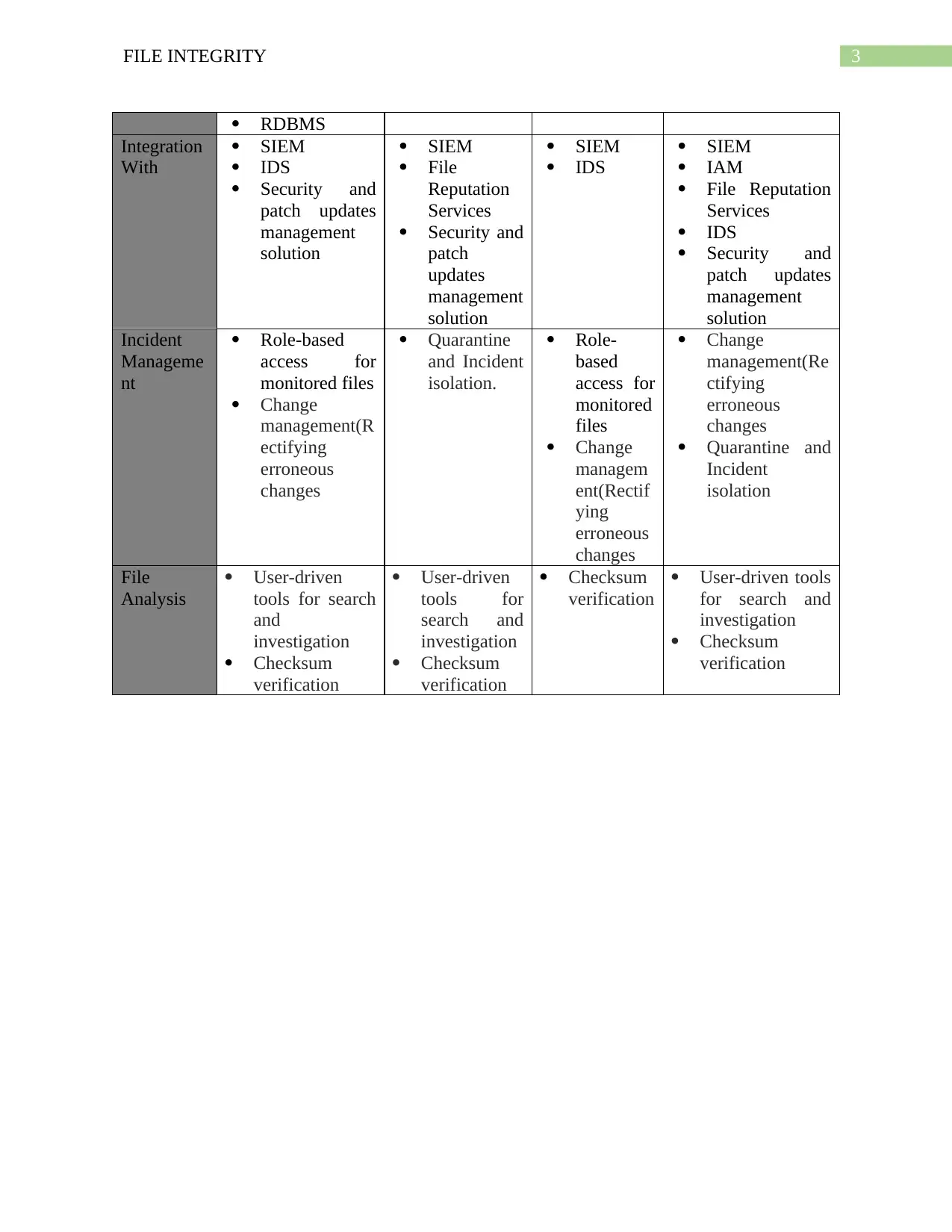
This report provides a comparative analysis of file integrity monitoring (FIM) software, which is a process used to validate the integrity of application software files and operating systems. It examines several popular FIM solutions, including Tripwire, Trustwave Endpoint Protection, ADAudit Plus, and Solarwinds Event and Log Manager. The report details the key features of each software, such as real-time change detection, threat and vulnerability management, active directory change tracking, and network performance monitoring. It also compares the platforms supported by each solution, their integration capabilities with incident management systems, and features like file analysis, checksum verification, and security updates. The report references external sources to support its analysis and provide a comprehensive overview of the FIM landscape.
1 out of 5







![[object Object]](/_next/static/media/star-bottom.7253800d.svg)