Analysis of Fingerprint Authentication Methods and Performance Metrics
VerifiedAdded on 2023/06/04
|13
|967
|462
Report
AI Summary
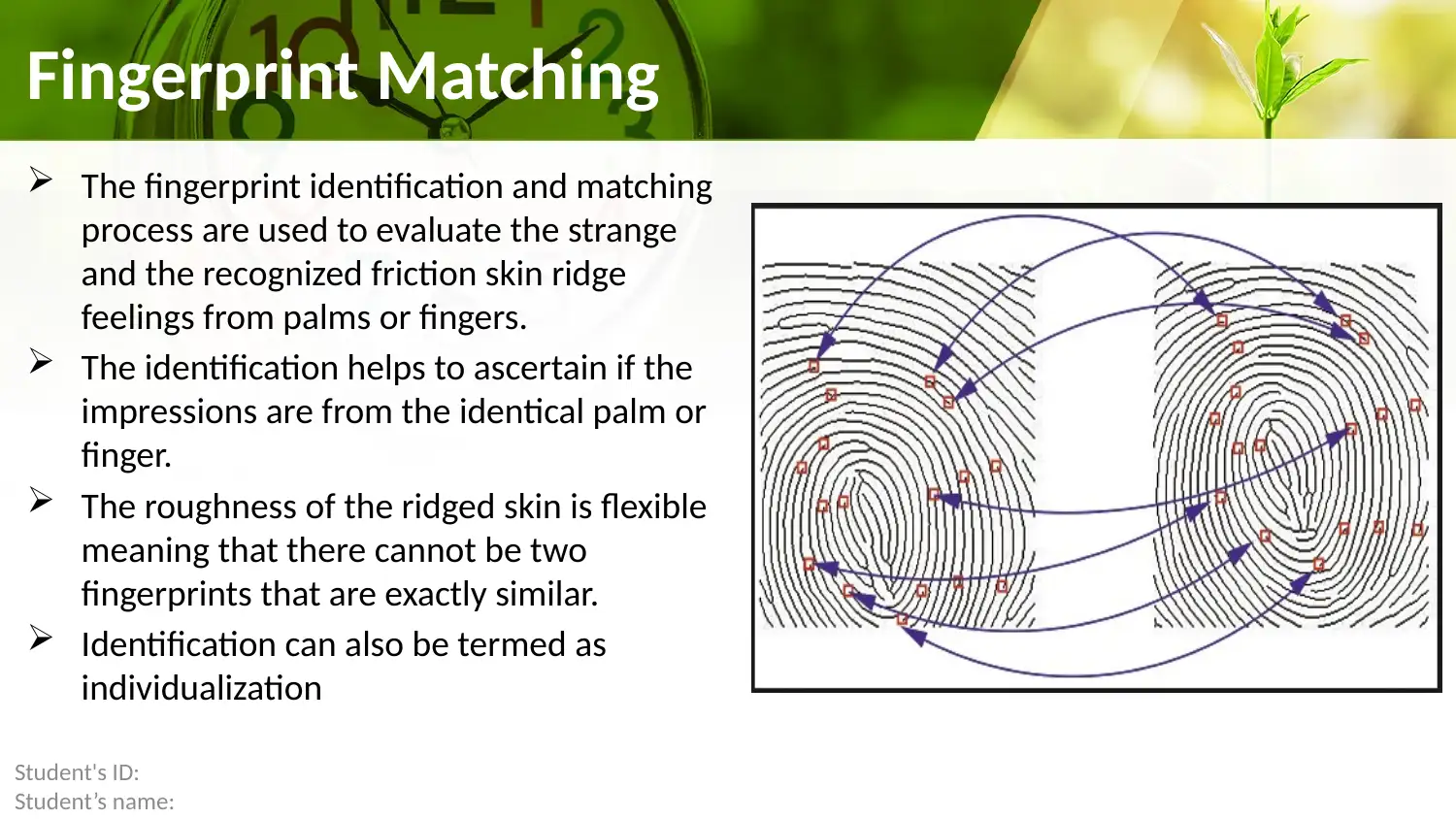
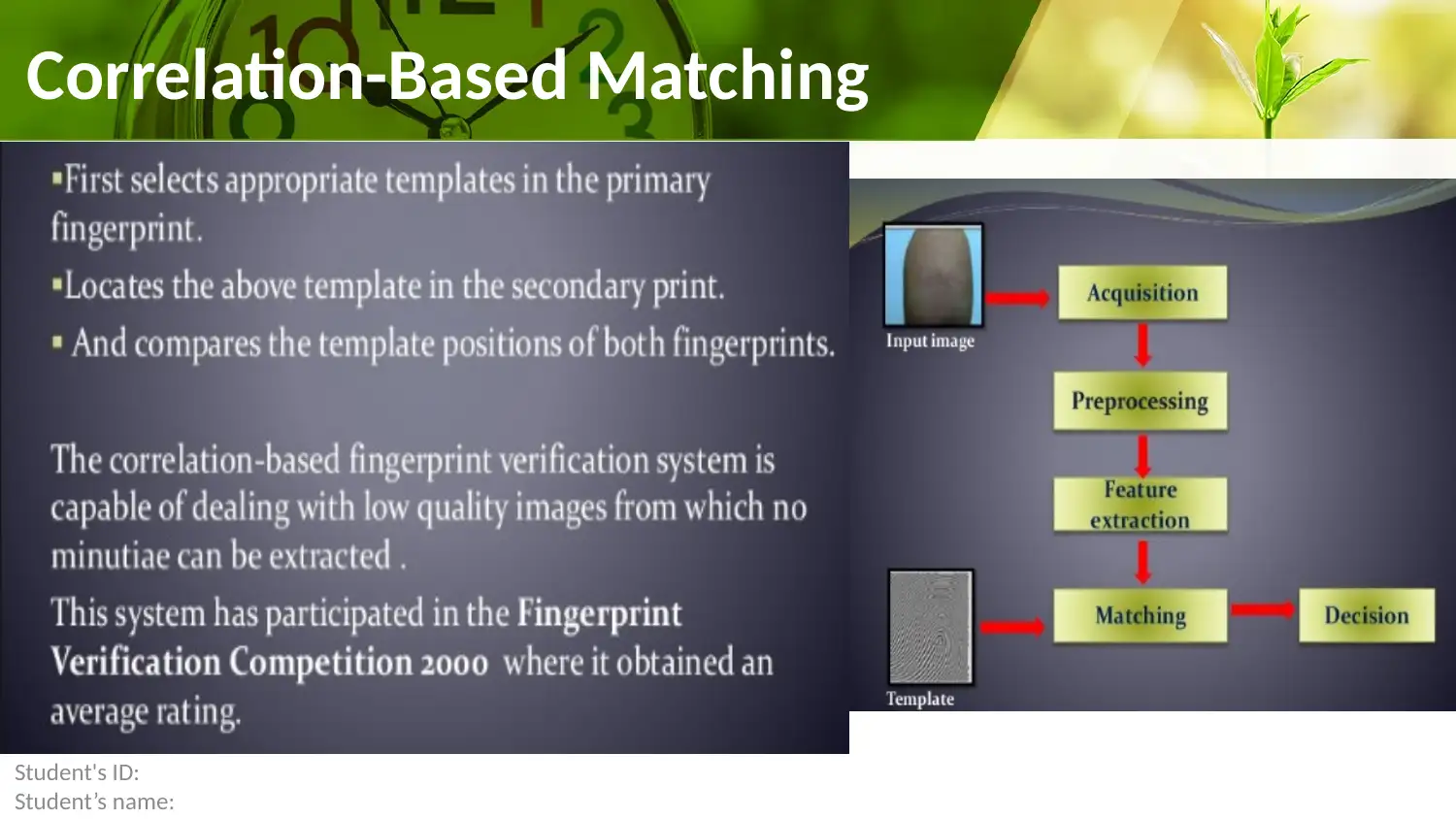
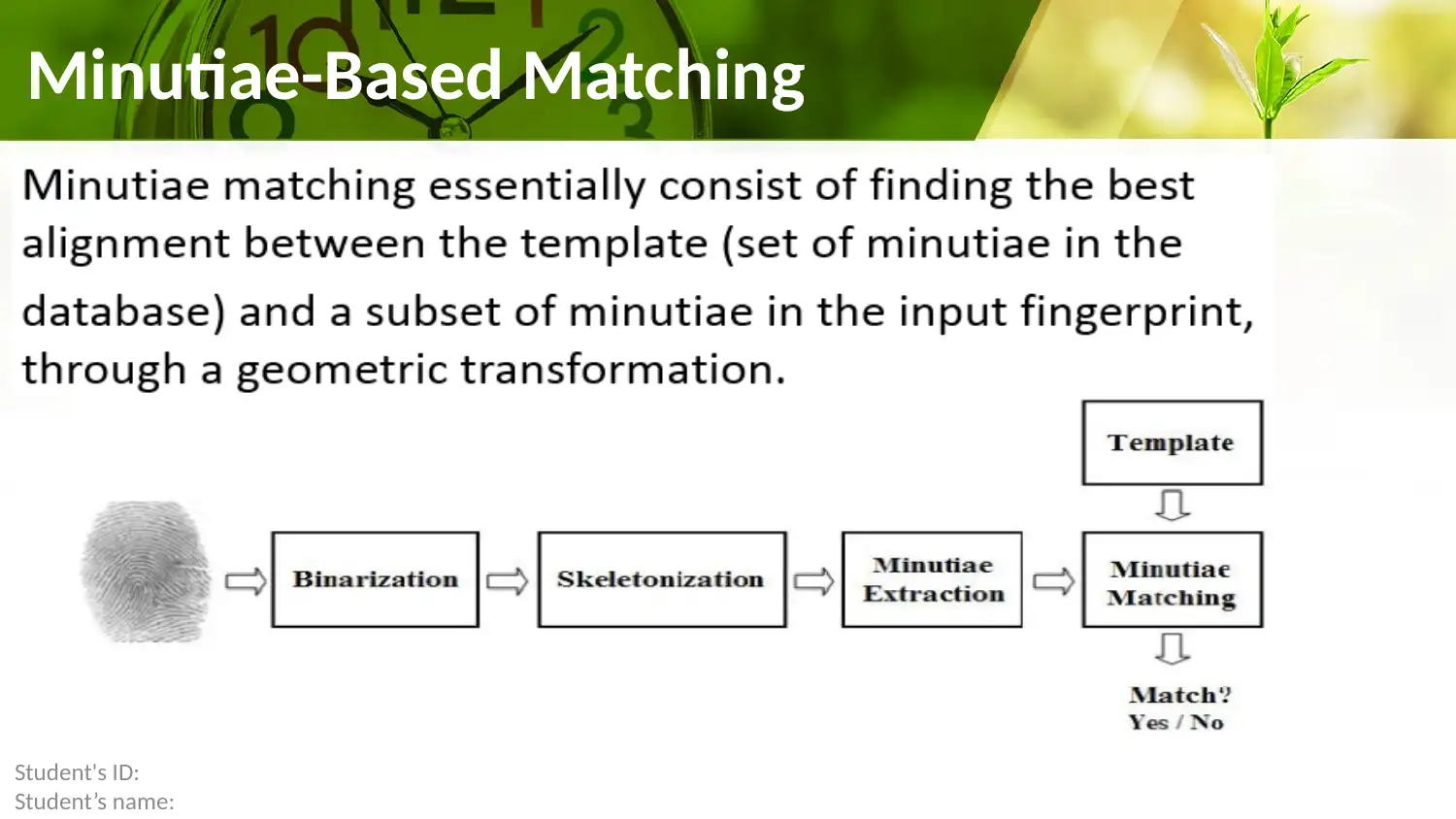
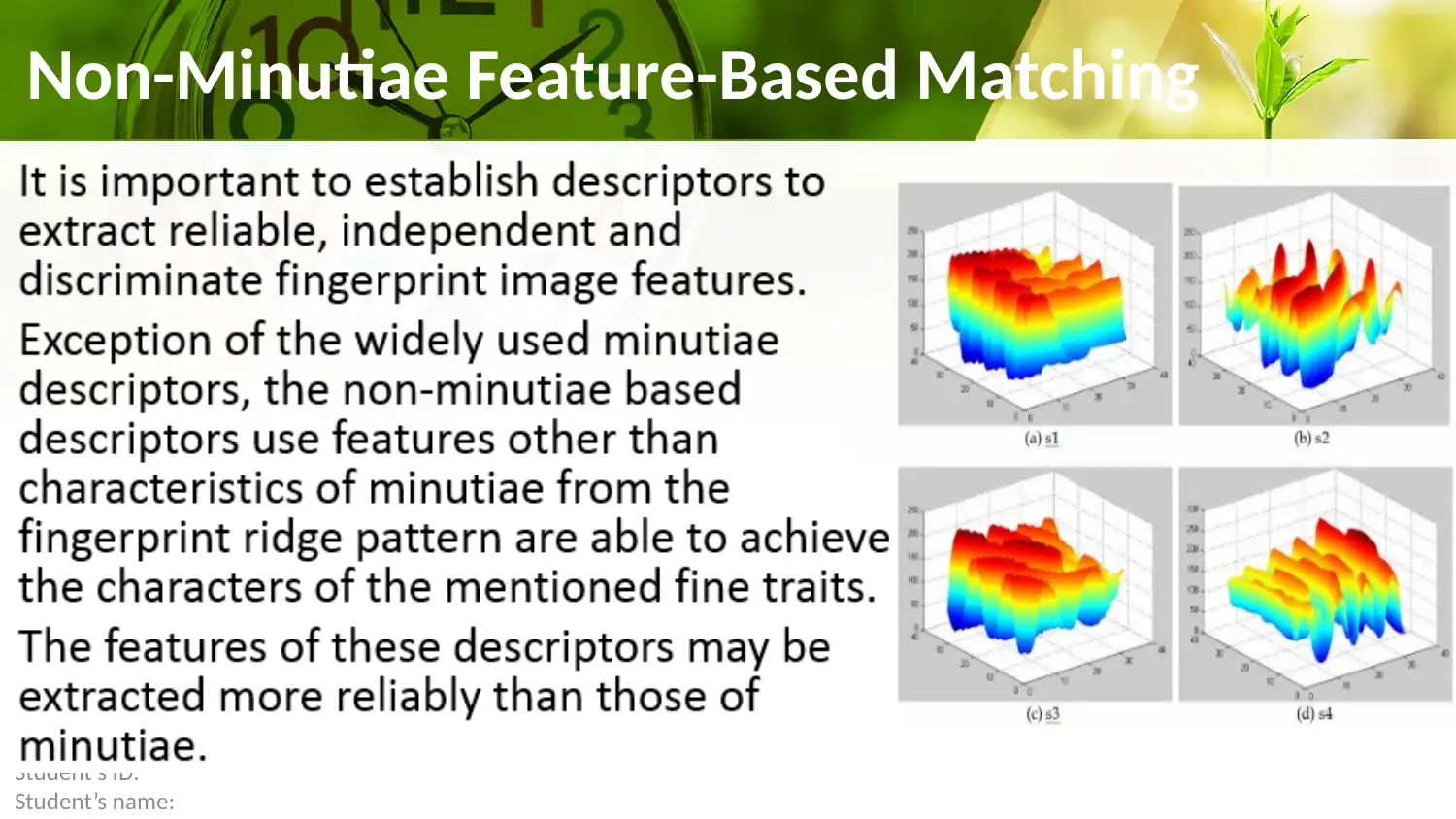
This report provides a comprehensive overview of fingerprint authentication methods, focusing on correlation-based, minutiae-based, and non-minutiae feature-based matching techniques. It delves into the fingerprint identification process, highlighting its use in evaluating friction skin ridge details from palms or fingers. The report also addresses various types of fingerprinting errors, including False Rejection Rate, False Acceptance Rate, and Equal Error Rate, while examining the transformation and integration of biometric capabilities. Furthermore, it discusses the factors influencing fingerprint integration and the importance of combining fingerprint biometrics with other security measures. The conclusion emphasizes the critical role of fingerprint biometric technology in tackling security challenges, while advocating for well-informed decisions and cost-benefit analysis before implementation. Desklib offers a wide range of resources, including past papers and solved assignments, to aid students in their understanding of this subject.
1 out of 13












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)