Superiority of Fingerprint Recognition Over Face Recognition: A Report
VerifiedAdded on 2020/05/28
|27
|7463
|220
Report
AI Summary
This report provides a detailed comparison between fingerprint recognition and face recognition as biometric authentication mechanisms. It begins with an introduction to biometrics, emphasizing their increasing use in various industries and governmental sectors. The report then delves into the processes of both fingerprint and face recognition, including feature extraction and matching techniques. It analyzes the advantages and disadvantages of each method, discussing factors such as accuracy, usability, and security, while also addressing limitations like physical changes and costs. The report highlights the superiority of fingerprint recognition due to its unique and unchanging nature, as well as its higher accuracy and reliability. The report also examines real-world examples and the next generation of authentication, such as Apple Face ID, before concluding with a comparative analysis of the two technologies, emphasizing the strengths of fingerprint recognition in providing a more secure and reliable biometric authentication system. The report also provides a detailed analysis of the fingerprint and face recognition processes, highlighting the strengths and weaknesses of each method.

Running head: FINGERPRINTING VS FACE RECOGNITION
Fingerprinting is superior to face recognition as a biometric authentication mechanism
Name of the Student:
Name of the University:
Fingerprinting is superior to face recognition as a biometric authentication mechanism
Name of the Student:
Name of the University:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1FINGERPRINTING VS FACE RECOGNITION
Table of Contents
1.0 Introduction................................................................................................................................2
1.1 Background of the study........................................................................................................3
2.0 Fingerprint recognition vs Face recognition as biometric authentication mechanism..............3
2.1 Is Fingerprint recognition better............................................................................................3
2.2 Is Face recognition better.......................................................................................................4
2.3 Fingerprint identification process..........................................................................................5
2.4 Face recognition process........................................................................................................6
2.5 Advantages and disadvantages of Fingerprint recognition....................................................7
2.6 Advantages and disadvantages of Face recognition............................................................10
2.7 Examples of fingerprint recognition and face recognition..................................................11
2.8 Next generation of authentication- Apple Face ID..............................................................15
2.9 Compare fingerprint recognition and face recognition........................................................16
3.0 Conclusion...............................................................................................................................20
References......................................................................................................................................22
Table of Contents
1.0 Introduction................................................................................................................................2
1.1 Background of the study........................................................................................................3
2.0 Fingerprint recognition vs Face recognition as biometric authentication mechanism..............3
2.1 Is Fingerprint recognition better............................................................................................3
2.2 Is Face recognition better.......................................................................................................4
2.3 Fingerprint identification process..........................................................................................5
2.4 Face recognition process........................................................................................................6
2.5 Advantages and disadvantages of Fingerprint recognition....................................................7
2.6 Advantages and disadvantages of Face recognition............................................................10
2.7 Examples of fingerprint recognition and face recognition..................................................11
2.8 Next generation of authentication- Apple Face ID..............................................................15
2.9 Compare fingerprint recognition and face recognition........................................................16
3.0 Conclusion...............................................................................................................................20
References......................................................................................................................................22

2FINGERPRINTING VS FACE RECOGNITION
1.0 Introduction
The report is based on “Fingerprinting is superior to face recognition as a biometric
authentication mechanism.” Biometric applications are used in various industries and
governmental sector. Biometric identification refers to identify the individual based on people’s
distinguishing characteristics. It is the method to recognize the human based on physical and
behavioural traits (Galbally, Marcel and Fierrez 2014). Automated identification and verification
of the individuals is based on unique behavioural characteristics like fingerprints, face
recognition, iris and others. From thousands of years, fingerprint biometric authentication is
existed. In the year 1970s, biometric appeared as automated technology (Larrain et al. 2017).
There are three basic components of biometric system: automated mechanism which scans and
captures digital image, mechanism process and store the data and third component interfaces
with application system.
The report provides a debate on fingerprint and face recognition as biometric
authentication mechanism. Most of the industries are using biometrics to control physical access
to the buildings. Due to advancement of technology, this trend is begun to grow. Increasing need
of biometric authentication reduces the fraud and provides a secure environment to public. Most
of the biometric control system follows of simple model to process and store the data. The way
to access the system is to enrol the system. Enrolment is needed to generate of reference
template. As per the device, the enrolment method varies and involves of scanning to achieve of
accurate measurements (Berini et al. 2016). The template provides reference for comparing when
access to attempt is to be made. It stores and misuses the template which creates most concerns
for the users.
1.0 Introduction
The report is based on “Fingerprinting is superior to face recognition as a biometric
authentication mechanism.” Biometric applications are used in various industries and
governmental sector. Biometric identification refers to identify the individual based on people’s
distinguishing characteristics. It is the method to recognize the human based on physical and
behavioural traits (Galbally, Marcel and Fierrez 2014). Automated identification and verification
of the individuals is based on unique behavioural characteristics like fingerprints, face
recognition, iris and others. From thousands of years, fingerprint biometric authentication is
existed. In the year 1970s, biometric appeared as automated technology (Larrain et al. 2017).
There are three basic components of biometric system: automated mechanism which scans and
captures digital image, mechanism process and store the data and third component interfaces
with application system.
The report provides a debate on fingerprint and face recognition as biometric
authentication mechanism. Most of the industries are using biometrics to control physical access
to the buildings. Due to advancement of technology, this trend is begun to grow. Increasing need
of biometric authentication reduces the fraud and provides a secure environment to public. Most
of the biometric control system follows of simple model to process and store the data. The way
to access the system is to enrol the system. Enrolment is needed to generate of reference
template. As per the device, the enrolment method varies and involves of scanning to achieve of
accurate measurements (Berini et al. 2016). The template provides reference for comparing when
access to attempt is to be made. It stores and misuses the template which creates most concerns
for the users.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3FINGERPRINTING VS FACE RECOGNITION
1.1 Background of the study
Galbally, Marcel and Fierrez (2014) stated that biometric are gaining of popularity as
authentication method in various organizations. Wang et al. (2015) argued that it is a type of
access control system based on biological qualities of user. There are various types of biometrics
authentication methods such as face recognition, fingerprint, iris recognition and others. Best-
Rowden and Jain (2018) mentioned that the advantage of using biometrics is that it offers of
extra security. As fingerprints are unique, therefore it is unrepeatable for the users and for each
person. Its level of security is maximum, as compared to other biometric methods. Its
maintenance cost is also low and after completion of installation, there is minimum cost
associated with maintenance (Liu, Zhang and Shen 2015). There is no such requirement of
additional devices for the entry. By means of fingerprint access control, there are no requirement
to use of traditional keys and switches. Jain et al. (2017) argued that behind the benefits, there
are also limitations of this method. It is less convenient in case of the users change. The cost of
installation is higher as compared to other access control system.
2.0 Fingerprint recognition vs Face recognition as biometric authentication
mechanism
2.1 Is Fingerprint recognition better
Fingerprint recognition refers to the automated method to verify match the human
fingerprints. The fingerprint of human is scanned electronically and there is creation of reference
template. This type of template is created by pattern of fingerprint and image of the fingerprint. It
is considered as the best biometric authentication mechanism as it is distinctive for individual
person (Bowyer and Burge 2016). It is better than any other biometric authorization mechanism
1.1 Background of the study
Galbally, Marcel and Fierrez (2014) stated that biometric are gaining of popularity as
authentication method in various organizations. Wang et al. (2015) argued that it is a type of
access control system based on biological qualities of user. There are various types of biometrics
authentication methods such as face recognition, fingerprint, iris recognition and others. Best-
Rowden and Jain (2018) mentioned that the advantage of using biometrics is that it offers of
extra security. As fingerprints are unique, therefore it is unrepeatable for the users and for each
person. Its level of security is maximum, as compared to other biometric methods. Its
maintenance cost is also low and after completion of installation, there is minimum cost
associated with maintenance (Liu, Zhang and Shen 2015). There is no such requirement of
additional devices for the entry. By means of fingerprint access control, there are no requirement
to use of traditional keys and switches. Jain et al. (2017) argued that behind the benefits, there
are also limitations of this method. It is less convenient in case of the users change. The cost of
installation is higher as compared to other access control system.
2.0 Fingerprint recognition vs Face recognition as biometric authentication
mechanism
2.1 Is Fingerprint recognition better
Fingerprint recognition refers to the automated method to verify match the human
fingerprints. The fingerprint of human is scanned electronically and there is creation of reference
template. This type of template is created by pattern of fingerprint and image of the fingerprint. It
is considered as the best biometric authentication mechanism as it is distinctive for individual
person (Bowyer and Burge 2016). It is better than any other biometric authorization mechanism
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4FINGERPRINTING VS FACE RECOGNITION
as over 140 years, no two of the fingerprints are seen as alike, not the fingerprints of identical
twins. The system requires clean hand to take the fingerprint of people. The examples of its
application include of mobile phones, car doors, military applications and others (Ghiass et al.
2014). Fingerprint is made up of ridges, furrows where its uniqueness is being determined by
patterns made by ridges and furrows. The ridge of fingerprint will never changed in the entire
life of individual.
The images of fingerprint are acquired by use of various sensors. Examples are such
capacitive sensor which gets pixel value based on characteristics of fingerprint. The
characteristics of fingerprint are finger ridge (Jain et al. 2015). In same way, optical sensors are
used of prisms in order to detect changes into reflectance of light by characteristics. The thermal
scanners into the system are used to measure differences into the temperature over time for
creating digital images.
2.2 Is Face recognition better
Like fingerprint recognition, face recognition technology measures and equals with
distinctive characteristics of the identification and biometric authentication purposes. The
biometric can detect the face into images and equivalent them against accumulated templates
into the database (Shekhar et al. 2014). The system analyzes precise characteristics which are
common to everyone’s face. It analyzes the distance between eyes, width of nose, chin, place of
cheekbones and jaw line. Those quantities are combined into single code which is used to
identify the person. The system measures distance between the human and digital camera and
then the data are stored into database (Yuan, Sun and Lv 2016). It captures huge images in quite
a second, compare the image with the stored data and then the results are produced.
as over 140 years, no two of the fingerprints are seen as alike, not the fingerprints of identical
twins. The system requires clean hand to take the fingerprint of people. The examples of its
application include of mobile phones, car doors, military applications and others (Ghiass et al.
2014). Fingerprint is made up of ridges, furrows where its uniqueness is being determined by
patterns made by ridges and furrows. The ridge of fingerprint will never changed in the entire
life of individual.
The images of fingerprint are acquired by use of various sensors. Examples are such
capacitive sensor which gets pixel value based on characteristics of fingerprint. The
characteristics of fingerprint are finger ridge (Jain et al. 2015). In same way, optical sensors are
used of prisms in order to detect changes into reflectance of light by characteristics. The thermal
scanners into the system are used to measure differences into the temperature over time for
creating digital images.
2.2 Is Face recognition better
Like fingerprint recognition, face recognition technology measures and equals with
distinctive characteristics of the identification and biometric authentication purposes. The
biometric can detect the face into images and equivalent them against accumulated templates
into the database (Shekhar et al. 2014). The system analyzes precise characteristics which are
common to everyone’s face. It analyzes the distance between eyes, width of nose, chin, place of
cheekbones and jaw line. Those quantities are combined into single code which is used to
identify the person. The system measures distance between the human and digital camera and
then the data are stored into database (Yuan, Sun and Lv 2016). It captures huge images in quite
a second, compare the image with the stored data and then the results are produced.

5FINGERPRINTING VS FACE RECOGNITION
2.3 Fingerprint identification process
Acquire biometric sample: The person steps the finger on the biometric device either
thumb or any other finger. Once the device captures the information, it creates electronic
representation of the person which is used later on the verification process. The device captures
the fingerprint by use of various sensors such as optical scanner (Gudavalli, Kumar and Raju
2015). The scanner is consisted of charge coupled device that contains of light sensitive diodes.
It provides electric signals at elimination. The tiny dots represented the light which hits the spot.
Those spots are recorded as pixels and that array of pixels form image.
Feature extraction: The person presents the fingerprint on the biometric device such that
the device can capture the image of unique finger (Ding and Tao 2016). The system extracts the
details from the processed image and then compared it with the stored image into the system.
Matching: After capturing of the image, the device matches the fingerprint image with its
database data. When the image is matched, then it pulls template from the database from where it
stress and grants access if it matches (Paone et al. 2014). If it is not matched, then it denies
entering the person due to unrecognized fingerprint.
2.3 Fingerprint identification process
Acquire biometric sample: The person steps the finger on the biometric device either
thumb or any other finger. Once the device captures the information, it creates electronic
representation of the person which is used later on the verification process. The device captures
the fingerprint by use of various sensors such as optical scanner (Gudavalli, Kumar and Raju
2015). The scanner is consisted of charge coupled device that contains of light sensitive diodes.
It provides electric signals at elimination. The tiny dots represented the light which hits the spot.
Those spots are recorded as pixels and that array of pixels form image.
Feature extraction: The person presents the fingerprint on the biometric device such that
the device can capture the image of unique finger (Ding and Tao 2016). The system extracts the
details from the processed image and then compared it with the stored image into the system.
Matching: After capturing of the image, the device matches the fingerprint image with its
database data. When the image is matched, then it pulls template from the database from where it
stress and grants access if it matches (Paone et al. 2014). If it is not matched, then it denies
entering the person due to unrecognized fingerprint.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6FINGERPRINTING VS FACE RECOGNITION
Figure 1: Physiological modalities: fingerprint recognition vs. facial recognition
(Source: Jain, Cao and Arora 2014, pp-7)
2.4 Face recognition process
There are four stages of the face recognition process such as:
Capture: A physical sample is being captured by the face recognition system at the time
of enrollment (Marasco and Ross 2015).
Face Extraction: From the sample, unique data are being extracted and a template is
being created.
Comparison: With the new sample, a template is compared.
Matching: The system decides if the features which are extracted from new sample are
matching or not matching (Vipparthi et al. 2016).
Figure 1: Physiological modalities: fingerprint recognition vs. facial recognition
(Source: Jain, Cao and Arora 2014, pp-7)
2.4 Face recognition process
There are four stages of the face recognition process such as:
Capture: A physical sample is being captured by the face recognition system at the time
of enrollment (Marasco and Ross 2015).
Face Extraction: From the sample, unique data are being extracted and a template is
being created.
Comparison: With the new sample, a template is compared.
Matching: The system decides if the features which are extracted from new sample are
matching or not matching (Vipparthi et al. 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
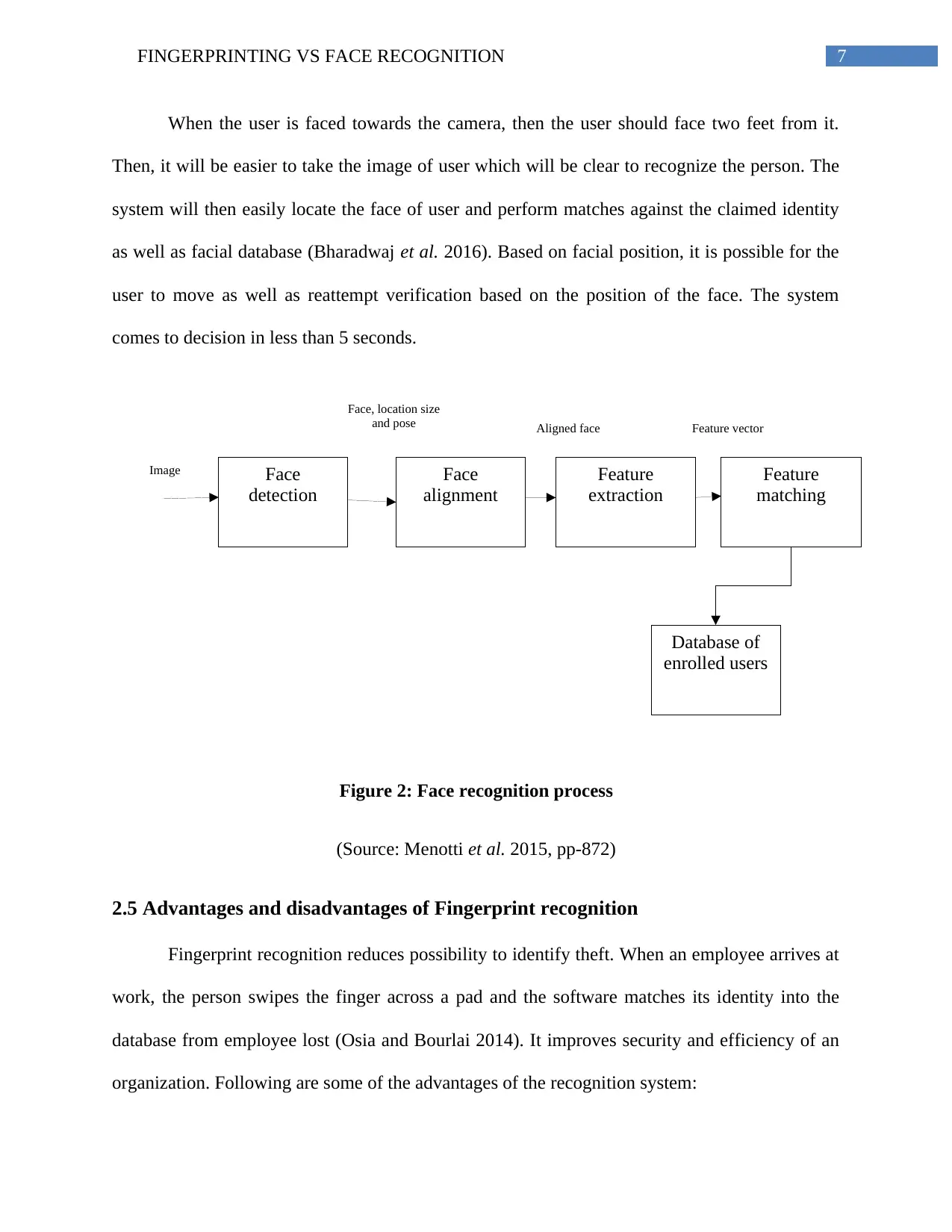
7FINGERPRINTING VS FACE RECOGNITION
Face
detection
Face
alignment
Feature
extraction
Feature
matching
Database of
enrolled users
Feature vector
Face, location size
and pose Aligned face
Image
When the user is faced towards the camera, then the user should face two feet from it.
Then, it will be easier to take the image of user which will be clear to recognize the person. The
system will then easily locate the face of user and perform matches against the claimed identity
as well as facial database (Bharadwaj et al. 2016). Based on facial position, it is possible for the
user to move as well as reattempt verification based on the position of the face. The system
comes to decision in less than 5 seconds.
Figure 2: Face recognition process
(Source: Menotti et al. 2015, pp-872)
2.5 Advantages and disadvantages of Fingerprint recognition
Fingerprint recognition reduces possibility to identify theft. When an employee arrives at
work, the person swipes the finger across a pad and the software matches its identity into the
database from employee lost (Osia and Bourlai 2014). It improves security and efficiency of an
organization. Following are some of the advantages of the recognition system:
Face
detection
Face
alignment
Feature
extraction
Feature
matching
Database of
enrolled users
Feature vector
Face, location size
and pose Aligned face
Image
When the user is faced towards the camera, then the user should face two feet from it.
Then, it will be easier to take the image of user which will be clear to recognize the person. The
system will then easily locate the face of user and perform matches against the claimed identity
as well as facial database (Bharadwaj et al. 2016). Based on facial position, it is possible for the
user to move as well as reattempt verification based on the position of the face. The system
comes to decision in less than 5 seconds.
Figure 2: Face recognition process
(Source: Menotti et al. 2015, pp-872)
2.5 Advantages and disadvantages of Fingerprint recognition
Fingerprint recognition reduces possibility to identify theft. When an employee arrives at
work, the person swipes the finger across a pad and the software matches its identity into the
database from employee lost (Osia and Bourlai 2014). It improves security and efficiency of an
organization. Following are some of the advantages of the recognition system:

8FINGERPRINTING VS FACE RECOGNITION
Access and timekeeping: The scanner verifies the identity of person to make sure that the
person has permission to access particular working environment. The organization is used of this
system to confirm when the employee arrives and leaves the office. Time theft costs the
company a huge amount of money (Minaee and Wang 2015). Therefore, the system tracks the
attendance of employee which results into proper time logs.
Accuracy: Fingerprint recognition has higher accuracy rate. The fingerprint pattern is
unique as it provides of distinguish fingerprints of each individuals. None of the person have
alike fingerprint even they are twins (Galbally and Satta 2016). Tests are done and it is resulted
that this biometric authentication mechanism is better as compared to other mechanism as it
provides high quality images and are performed under controlled situations.
Usability: Fingerprints is successfully installed in most of the applications for security
purposes. It is integrated into existing applications by means of low learning curve. Users can
easily use the system as it is spontaneous (Evans et al. 2015). It is cheaper and reliable sensor
makes the rate of usability raises.
Reliability: The system provides a reliable way to track the employees where no extra
data are stored into the system. The system only uses of fingerprint based system; therefore the
employees are not worried to keep cards and passwords secured (Soldera, Behaine and
Scharcanski 2015). The system provides capability to detect the individual out of millions of
persons. Small storage space is required for biometric template in this recognition system. It
reduces the database memory size when needed. It is also a standardized technique.
Highly secure: The fingerprint scanners are highly secured. It is used to lock and unlock
any devices along with applications need to remember the passwords. It is also easier and
Access and timekeeping: The scanner verifies the identity of person to make sure that the
person has permission to access particular working environment. The organization is used of this
system to confirm when the employee arrives and leaves the office. Time theft costs the
company a huge amount of money (Minaee and Wang 2015). Therefore, the system tracks the
attendance of employee which results into proper time logs.
Accuracy: Fingerprint recognition has higher accuracy rate. The fingerprint pattern is
unique as it provides of distinguish fingerprints of each individuals. None of the person have
alike fingerprint even they are twins (Galbally and Satta 2016). Tests are done and it is resulted
that this biometric authentication mechanism is better as compared to other mechanism as it
provides high quality images and are performed under controlled situations.
Usability: Fingerprints is successfully installed in most of the applications for security
purposes. It is integrated into existing applications by means of low learning curve. Users can
easily use the system as it is spontaneous (Evans et al. 2015). It is cheaper and reliable sensor
makes the rate of usability raises.
Reliability: The system provides a reliable way to track the employees where no extra
data are stored into the system. The system only uses of fingerprint based system; therefore the
employees are not worried to keep cards and passwords secured (Soldera, Behaine and
Scharcanski 2015). The system provides capability to detect the individual out of millions of
persons. Small storage space is required for biometric template in this recognition system. It
reduces the database memory size when needed. It is also a standardized technique.
Highly secure: The fingerprint scanners are highly secured. It is used to lock and unlock
any devices along with applications need to remember the passwords. It is also easier and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9FINGERPRINTING VS FACE RECOGNITION
cheaper system. The online transactions become convenient when tap screen with the finger
within fraction of seconds secure the entire process (Azeem et al. 2014). The fingerprint speeds
the transaction process secured.
Fingerprint biometric technology consists of various benefits, but it has various limiting
factors. The fingerprint devices not only capture of the image of finger, but also capture the dirt
and contamination which are found into the finger of users. Those are chances which are rejected
by the system as the worker are not mark the contaminants on the finger. The disadvantage of
this system is that there is damage to the devices (Blanco-Gonzalo et al. 2015). Apart from
disadvantages, the fingerprint recognition has some disadvantages such as:
Not considered for physical changes person: When a person is physically changes, then
the size and pattern of the fingers are also changed over time. Therefore, the scanner is not taken
into consideration (Saini and Rana 2014). When changes occur into the individuals, then it is
difficult for the system to identify and gain access. It is difficult to take accurate image of
fingerprint.
Expensive: The cost of the hardware and software equipments is expensive. As
fingerprint is high security system, therefore expensive computer equipments are required.
False rejection and acceptance: The biometric system is not always read the fingerprint
image properly. Then, the employee is refused to access. It is also possible when the employee
does not out the finger at the right place (Melin and Castillo 2014). When the system is used for
punching, then it is possible that it identifies punch made from one employee as another, then
there is false acceptance of employee and therefore results into wrong access to the unauthorized
employee.
cheaper system. The online transactions become convenient when tap screen with the finger
within fraction of seconds secure the entire process (Azeem et al. 2014). The fingerprint speeds
the transaction process secured.
Fingerprint biometric technology consists of various benefits, but it has various limiting
factors. The fingerprint devices not only capture of the image of finger, but also capture the dirt
and contamination which are found into the finger of users. Those are chances which are rejected
by the system as the worker are not mark the contaminants on the finger. The disadvantage of
this system is that there is damage to the devices (Blanco-Gonzalo et al. 2015). Apart from
disadvantages, the fingerprint recognition has some disadvantages such as:
Not considered for physical changes person: When a person is physically changes, then
the size and pattern of the fingers are also changed over time. Therefore, the scanner is not taken
into consideration (Saini and Rana 2014). When changes occur into the individuals, then it is
difficult for the system to identify and gain access. It is difficult to take accurate image of
fingerprint.
Expensive: The cost of the hardware and software equipments is expensive. As
fingerprint is high security system, therefore expensive computer equipments are required.
False rejection and acceptance: The biometric system is not always read the fingerprint
image properly. Then, the employee is refused to access. It is also possible when the employee
does not out the finger at the right place (Melin and Castillo 2014). When the system is used for
punching, then it is possible that it identifies punch made from one employee as another, then
there is false acceptance of employee and therefore results into wrong access to the unauthorized
employee.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10FINGERPRINTING VS FACE RECOGNITION
2.6 Advantages and disadvantages of Face recognition
Biometric technology becomes popular due to face recognition technology. The system is
used of biometric identification based on the facial characteristics of the person. The system
identifies the person from a distance through use of digital camera, consult of 2D images and use
of 3D recognition for identifying the facial features (Chingovska et al. 2016). Following are the
advantages of face recognition:
Reliable matching: By means of face recognition system, matching of reliable face are
offered. The face recognition software is integrated into different types of video monitoring
system and it also supports of video as well as graphic formats (Chingovska et al. 2016).
Fast and proper results: The system provides fast as well as accurate results. The users
are able to benefit from higher recognition rates and short processing times, which makes the
system more efficient as well as effective.
Easier integration: An integrated biometric system is easier to program into the
organizational computer system (Yang et al. 2014). It works with existing software that the
organization has to place.
Disadvantages of facial recognition system are as follows:
Quality of image: The quality of image affects the facial recognition of a person. The
quality of facial image is low compared with digital camera. It is requirement of high definition
video of 1080p, but it provides an image quality of 720p.
2.6 Advantages and disadvantages of Face recognition
Biometric technology becomes popular due to face recognition technology. The system is
used of biometric identification based on the facial characteristics of the person. The system
identifies the person from a distance through use of digital camera, consult of 2D images and use
of 3D recognition for identifying the facial features (Chingovska et al. 2016). Following are the
advantages of face recognition:
Reliable matching: By means of face recognition system, matching of reliable face are
offered. The face recognition software is integrated into different types of video monitoring
system and it also supports of video as well as graphic formats (Chingovska et al. 2016).
Fast and proper results: The system provides fast as well as accurate results. The users
are able to benefit from higher recognition rates and short processing times, which makes the
system more efficient as well as effective.
Easier integration: An integrated biometric system is easier to program into the
organizational computer system (Yang et al. 2014). It works with existing software that the
organization has to place.
Disadvantages of facial recognition system are as follows:
Quality of image: The quality of image affects the facial recognition of a person. The
quality of facial image is low compared with digital camera. It is requirement of high definition
video of 1080p, but it provides an image quality of 720p.

11FINGERPRINTING VS FACE RECOGNITION
Size of image: Sometimes, the system takes a small size of face which is difficult to
recognize the person (Wei, Chen and Wang 2014). Small image of person coupled with target
distant from camera, means there is only 100 to 200 pixels on the side.
Processing and storage: In case of face recognition system, it is seen that high definition
video is low; even it occupies a larger amount of disk spaces Gudavalli, Kumar and Raju 2015).
Processing of each frame of the video is vital to undertake, therefore only fraction of 10-25
percent is run throughout the system.
Change in style and facial expressions: There is problem with false rejection when
people have changed the hair style, bread and wear of glasses. There is also change into
variations into skin color under various lightning conditions which is an issue to detect the face
(Gragnaniello et al. 2015). There are various face angles with respect to the digital camera; it
raises issue when the camera is not able to detect the user. There are various facial expressions
such as varies into level of smile will be issue as the camera is not able to detect the face
correctly.
2.7 Examples of fingerprint recognition and face recognition
Finger readers are widely used biometric technology in the world to provide a secure
environment to any organizations. From both client’s and business owner’s perspectives,
fingerprint scanning approach are widely used and the examples of this approach are as follows:
Identity access management: Fingerprint based access is a more convenient and
effective way than the traditional identity card using approach. However, the fingerprint
scanning mechanism is referred to as a superior technology than face recognition in case of
biometric authentication (Berini et al. 2016). From the latest version of Android, significant
Size of image: Sometimes, the system takes a small size of face which is difficult to
recognize the person (Wei, Chen and Wang 2014). Small image of person coupled with target
distant from camera, means there is only 100 to 200 pixels on the side.
Processing and storage: In case of face recognition system, it is seen that high definition
video is low; even it occupies a larger amount of disk spaces Gudavalli, Kumar and Raju 2015).
Processing of each frame of the video is vital to undertake, therefore only fraction of 10-25
percent is run throughout the system.
Change in style and facial expressions: There is problem with false rejection when
people have changed the hair style, bread and wear of glasses. There is also change into
variations into skin color under various lightning conditions which is an issue to detect the face
(Gragnaniello et al. 2015). There are various face angles with respect to the digital camera; it
raises issue when the camera is not able to detect the user. There are various facial expressions
such as varies into level of smile will be issue as the camera is not able to detect the face
correctly.
2.7 Examples of fingerprint recognition and face recognition
Finger readers are widely used biometric technology in the world to provide a secure
environment to any organizations. From both client’s and business owner’s perspectives,
fingerprint scanning approach are widely used and the examples of this approach are as follows:
Identity access management: Fingerprint based access is a more convenient and
effective way than the traditional identity card using approach. However, the fingerprint
scanning mechanism is referred to as a superior technology than face recognition in case of
biometric authentication (Berini et al. 2016). From the latest version of Android, significant
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





