MET CS690: Configuring Firewall Rules to Support Business Functions
VerifiedAdded on 2023/06/11
|10
|922
|63
Homework Assignment
AI Summary
This document provides solutions for configuring firewall rules to address various network security scenarios within an enterprise environment, as part of a MET CS690 assignment. The scenarios covered include enabling remote network access via SSH, mitigating virus attacks using firewall and cloud-based tools like Wildfire, permitting VPN access to the corporate network, securing sensitive information within VLANs, connecting to jump servers using SSH in DMZ1, restricting VLAN access to the internet using ACLs, and blocking RFC 1918 addresses. Each solution includes specific firewall rules and configurations, aiming to balance business needs with robust security measures, such as using IP objects, access lists, and aliases. The document references security principles and practices to ensure the overall security posture of the network is maintained.

FIREWALL RULES
Name
Date of Submission
Subject
Name
Date of Submission
Subject
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
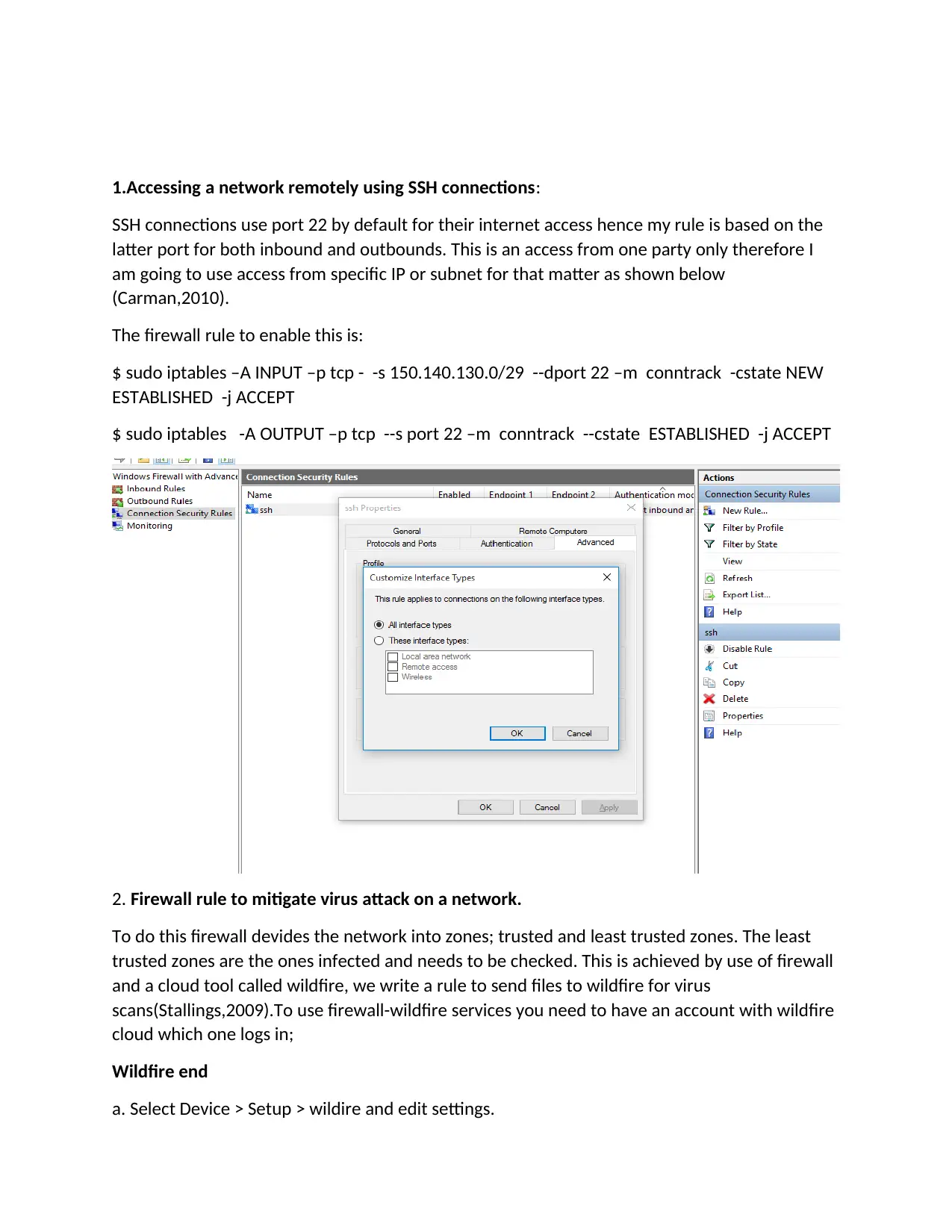
1.Accessing a network remotely using SSH connections:
SSH connections use port 22 by default for their internet access hence my rule is based on the
latter port for both inbound and outbounds. This is an access from one party only therefore I
am going to use access from specific IP or subnet for that matter as shown below
(Carman,2010).
The firewall rule to enable this is:
$ sudo iptables –A INPUT –p tcp - -s 150.140.130.0/29 --dport 22 –m conntrack -cstate NEW
ESTABLISHED -j ACCEPT
$ sudo iptables -A OUTPUT –p tcp --s port 22 –m conntrack --cstate ESTABLISHED -j ACCEPT
2. Firewall rule to mitigate virus attack on a network.
To do this firewall devides the network into zones; trusted and least trusted zones. The least
trusted zones are the ones infected and needs to be checked. This is achieved by use of firewall
and a cloud tool called wildfire, we write a rule to send files to wildfire for virus
scans(Stallings,2009).To use firewall-wildfire services you need to have an account with wildfire
cloud which one logs in;
Wildfire end
a. Select Device > Setup > wildire and edit settings.
SSH connections use port 22 by default for their internet access hence my rule is based on the
latter port for both inbound and outbounds. This is an access from one party only therefore I
am going to use access from specific IP or subnet for that matter as shown below
(Carman,2010).
The firewall rule to enable this is:
$ sudo iptables –A INPUT –p tcp - -s 150.140.130.0/29 --dport 22 –m conntrack -cstate NEW
ESTABLISHED -j ACCEPT
$ sudo iptables -A OUTPUT –p tcp --s port 22 –m conntrack --cstate ESTABLISHED -j ACCEPT
2. Firewall rule to mitigate virus attack on a network.
To do this firewall devides the network into zones; trusted and least trusted zones. The least
trusted zones are the ones infected and needs to be checked. This is achieved by use of firewall
and a cloud tool called wildfire, we write a rule to send files to wildfire for virus
scans(Stallings,2009).To use firewall-wildfire services you need to have an account with wildfire
cloud which one logs in;
Wildfire end
a. Select Device > Setup > wildire and edit settings.

b.Use the private wildfire services, define file size for the files the firewall forwards
c. Save.
Firewall end
Enabling firewall to get wildfire signatures;
a. Select Device > Updates:
Enable wildfire-500 appliance.
Then attach the virus profile for scan
Rules;
Test security –policy-match source subnet/IP destination subnet/IP application dns protocol 53
“Network Infrastructure”} from users:43224
Source:any
IP/subnet destination
Router IP application
Source-region-none;
To Data_Center;
Destination any;
Destination-region-none;
User-any;
Category any;
Application/service dns/any/any/any;
Action allow;
Icmp –unreachable: no terminal yes;}
3. Firewall rules to permit VPN access to cooperate network.
On cooperate network (Tankard,2009);
Creating IP object;
c. Save.
Firewall end
Enabling firewall to get wildfire signatures;
a. Select Device > Updates:
Enable wildfire-500 appliance.
Then attach the virus profile for scan
Rules;
Test security –policy-match source subnet/IP destination subnet/IP application dns protocol 53
“Network Infrastructure”} from users:43224
Source:any
IP/subnet destination
Router IP application
Source-region-none;
To Data_Center;
Destination any;
Destination-region-none;
User-any;
Category any;
Application/service dns/any/any/any;
Action allow;
Icmp –unreachable: no terminal yes;}
3. Firewall rules to permit VPN access to cooperate network.
On cooperate network (Tankard,2009);
Creating IP object;
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

On object settings>>IP object
Enter name of the object
Select “WAN/DMZ/RT/VPN” interface
Select type as “single”
Enter server name
Save.
On employee’s network
Click available index to create IP object
Enter name
Select “LAN? DMZ/RT/VPN” as the interface
Select the employee network subnet.
Save.
Firewall>>filter setup>>default data filter page;
Create a rule now to pass packets to the cooperate network’s servers.
Direction WAN? DMZ/RT/VPN-LAN/DMZ/RT/VPN
4. Accessing sensitive information within VLAN;
For this to happen we enable ports in the inbound; ports 137,135 and UDP 500
Firewall {
All-ping enable
Broadcast-ping disable
Group{
Address-group SIP_IP_Range{
Address 162.250.60.0/22
Address 199.36.248.0/22
199.87.120.0/22
Enter name of the object
Select “WAN/DMZ/RT/VPN” interface
Select type as “single”
Enter server name
Save.
On employee’s network
Click available index to create IP object
Enter name
Select “LAN? DMZ/RT/VPN” as the interface
Select the employee network subnet.
Save.
Firewall>>filter setup>>default data filter page;
Create a rule now to pass packets to the cooperate network’s servers.
Direction WAN? DMZ/RT/VPN-LAN/DMZ/RT/VPN
4. Accessing sensitive information within VLAN;
For this to happen we enable ports in the inbound; ports 137,135 and UDP 500
Firewall {
All-ping enable
Broadcast-ping disable
Group{
Address-group SIP_IP_Range{
Address 162.250.60.0/22
Address 199.36.248.0/22
199.87.120.0/22
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Description “jive IP BLOCK 3,BLOCK2,BLOCK 1”
}
Address-group home.yyyyyyy.io_Network{
Address 10.10.1.0/24
Description “”
}
Network-group LAN_NETWORKS{
Description “”
Network 10.10.1.0/24
}
Ipv6-receive-redirects disable
Ipv6-src-route disable
Log-martians enable
Name VLAN50_IN{
Default-action accept
Description “”
ruleA{
action accept
description “Accept Established/Related”
log disable
protocol all
state{established enable
invalid disable
related enable
}
}
ruleB{
}
Address-group home.yyyyyyy.io_Network{
Address 10.10.1.0/24
Description “”
}
Network-group LAN_NETWORKS{
Description “”
Network 10.10.1.0/24
}
Ipv6-receive-redirects disable
Ipv6-src-route disable
Log-martians enable
Name VLAN50_IN{
Default-action accept
Description “”
ruleA{
action accept
description “Accept Established/Related”
log disable
protocol all
state{established enable
invalid disable
related enable
}
}
ruleB{

Action drop
Description”Drop LAN_Networks”
Destination{
Group{
Network-group LAN_Networks
}
}
Log disable
Protocol all
}
}
Name VLAN50_LOCAL{
Default-action drop
Description “”
ruleA{
action accept
description “accept DNS”
destination {
port 137
}log disable
Protocol udp
}
ruleB{
action accept
description “accept DHCP”
destination {
port 67-68
Description”Drop LAN_Networks”
Destination{
Group{
Network-group LAN_Networks
}
}
Log disable
Protocol all
}
}
Name VLAN50_LOCAL{
Default-action drop
Description “”
ruleA{
action accept
description “accept DNS”
destination {
port 137
}log disable
Protocol udp
}
ruleB{
action accept
description “accept DHCP”
destination {
port 67-68
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

}log disable
Protocall udp
}
}
}
}
Protocall udp
}
}
}
}
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5. Connecting to jump server using SSH in DMZ1
This can be achieved in three steps below.
On the origin server we run the command;
a. Origin>ssh –R*:192.168.60.7:target:22 username@jumpserver .This rule creates ssh session
on the jumpserver
b. Origin> ssh jumphost IP 10.10.100.53 creates session on the old robot
c.Firewall;
In the sshd_config:AllowTcpForwarding yes
GatewayPorts yes
6. Restricting VLANs access to the internet in the ACL;
Rule;
Ip access-list extended “break “ deny ip 192.168.100.124 0 0.0.0 72.163.4.161 0.0.0.0 pemit ip
any
Interface fastethernet1 service-acl input “break”
The rule is placed on the ACL’s ASA.
7. Blocking RFC 1918 on a network;
In achieving this we use the firewall aliases, we create an alias for RFC 1918 with a network
range and give it a name
Create alias for network range named private_networks by default
Add ranges 10.0.0.0/8
172.16.0.0/12
169.254.0.0/16
127.0.0.0/8
Create floating firewall rule under Firewal>Rules
Action –Reject
Quick –Checked
This can be achieved in three steps below.
On the origin server we run the command;
a. Origin>ssh –R*:192.168.60.7:target:22 username@jumpserver .This rule creates ssh session
on the jumpserver
b. Origin> ssh jumphost IP 10.10.100.53 creates session on the old robot
c.Firewall;
In the sshd_config:AllowTcpForwarding yes
GatewayPorts yes
6. Restricting VLANs access to the internet in the ACL;
Rule;
Ip access-list extended “break “ deny ip 192.168.100.124 0 0.0.0 72.163.4.161 0.0.0.0 pemit ip
any
Interface fastethernet1 service-acl input “break”
The rule is placed on the ACL’s ASA.
7. Blocking RFC 1918 on a network;
In achieving this we use the firewall aliases, we create an alias for RFC 1918 with a network
range and give it a name
Create alias for network range named private_networks by default
Add ranges 10.0.0.0/8
172.16.0.0/12
169.254.0.0/16
127.0.0.0/8
Create floating firewall rule under Firewal>Rules
Action –Reject
Quick –Checked

Interface –WAN
Direction -out
TCP/IP version –ipv4
Protocol –any
Destination Single host/Alias:
Private networks
Log –optional
Direction -out
TCP/IP version –ipv4
Protocol –any
Destination Single host/Alias:
Private networks
Log –optional
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
References
Carman, D. W., Kruus, P. S., & Matt, B. J. (2010). Constraints and approaches for distributed sensor
network security (final). DARPA Project report,(Cryptographic Technologies Group, Trusted
Information System, NAI Labs), 1(1).
Stallings, W. (2009). Network and internetwork security: principles and practice (Vol. 1). Englewood Cliffs:
Prentice Hall.
Tankard, C. (2011). Advanced persistent threats and how to monitor and deter them. Network
security, 2011(8), 16-19.
Carman, D. W., Kruus, P. S., & Matt, B. J. (2010). Constraints and approaches for distributed sensor
network security (final). DARPA Project report,(Cryptographic Technologies Group, Trusted
Information System, NAI Labs), 1(1).
Stallings, W. (2009). Network and internetwork security: principles and practice (Vol. 1). Englewood Cliffs:
Prentice Hall.
Tankard, C. (2011). Advanced persistent threats and how to monitor and deter them. Network
security, 2011(8), 16-19.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





