Firewalls
VerifiedAdded on 2022/10/06
|17
|1394
|368
AI Summary
This article discusses the importance of firewalls in information security and explores different types of firewalls. It covers the configuration of an external firewall, SSH hardening, and improved network design using a demilitarized zone architecture. The article also discusses the use of internal application-level firewalls to enhance network security.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: FIREWALLS
1
Firewalls
Name
University
Date:
1
Firewalls
Name
University
Date:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

FIREWALLS
2
Introduction
Confidentiality, integrity, and availability of data are some of the fundamental concepts
of information security. Traditional forms of security focused on keeping data away from
unauthorized individuals by locking them away in safe houses under key and lock (Gilman &
Barth, 2017). However, the digitization of data has made such walls inefficient in keeping
intruders from accessing confidential information (Pachghare, 2015). The goal of information
security is to enable an organization maintain high availability of data to authorized persons
while keeping it away from the unauthorized individuals maximally. The use of firewalls is
essential in this regard. There are different types of firewalls. Packet filtering firewalls, stateful
inspection firewalls, application-level gateway, and the next generation firewalls. They all
operate on a software-defined environment. Hardware implementations of firewalls include the
bastion host and the demilitarized zone (DMZ) (Lundgren & Möller, 2017). The bastion host
architecture is demonstrated in this project. Section 3 of this report will detail the design of the
demilitarized zone firewall architecture.
Assumptions
The case scenario has been provided with the network architecture detailed below.
Figure 1: The case scenario for the bastion host implementation
2
Introduction
Confidentiality, integrity, and availability of data are some of the fundamental concepts
of information security. Traditional forms of security focused on keeping data away from
unauthorized individuals by locking them away in safe houses under key and lock (Gilman &
Barth, 2017). However, the digitization of data has made such walls inefficient in keeping
intruders from accessing confidential information (Pachghare, 2015). The goal of information
security is to enable an organization maintain high availability of data to authorized persons
while keeping it away from the unauthorized individuals maximally. The use of firewalls is
essential in this regard. There are different types of firewalls. Packet filtering firewalls, stateful
inspection firewalls, application-level gateway, and the next generation firewalls. They all
operate on a software-defined environment. Hardware implementations of firewalls include the
bastion host and the demilitarized zone (DMZ) (Lundgren & Möller, 2017). The bastion host
architecture is demonstrated in this project. Section 3 of this report will detail the design of the
demilitarized zone firewall architecture.
Assumptions
The case scenario has been provided with the network architecture detailed below.
Figure 1: The case scenario for the bastion host implementation

FIREWALLS
3
The network consists of:
i. SSH Server
ii. Proxy server
iii. File Server
iv. Local area network
v. Layer 2 switch
vi. Firewall
The following assumptions were made in the design of the network:
i. The LAN does not have an internal firewall implementation
ii. An external firewall can be configured sufficiently to protect the file server from
unauthorized access.
iii. No virtual private network configuration has been implemented.
iv. The firewall adopted performs both packet-filtering and DDoS Detection.
External Firewall Configuration
Considering the assumptions of the case scenario stated above, the configuration of the
external firewall connecting the network to the wide area network/Internet will need to be robust
to ward off malicious attacks . The tool to be used in this exercise is the iptools software, which
is packaged in Linux distributions. Ubuntu 18.04 LTS distribution was utilized for this exercise.
Adding rules to the IP table
Find the virtual network server computer IP address using command prompt ifconfig command
3
The network consists of:
i. SSH Server
ii. Proxy server
iii. File Server
iv. Local area network
v. Layer 2 switch
vi. Firewall
The following assumptions were made in the design of the network:
i. The LAN does not have an internal firewall implementation
ii. An external firewall can be configured sufficiently to protect the file server from
unauthorized access.
iii. No virtual private network configuration has been implemented.
iv. The firewall adopted performs both packet-filtering and DDoS Detection.
External Firewall Configuration
Considering the assumptions of the case scenario stated above, the configuration of the
external firewall connecting the network to the wide area network/Internet will need to be robust
to ward off malicious attacks . The tool to be used in this exercise is the iptools software, which
is packaged in Linux distributions. Ubuntu 18.04 LTS distribution was utilized for this exercise.
Adding rules to the IP table
Find the virtual network server computer IP address using command prompt ifconfig command
FIREWALLS
4
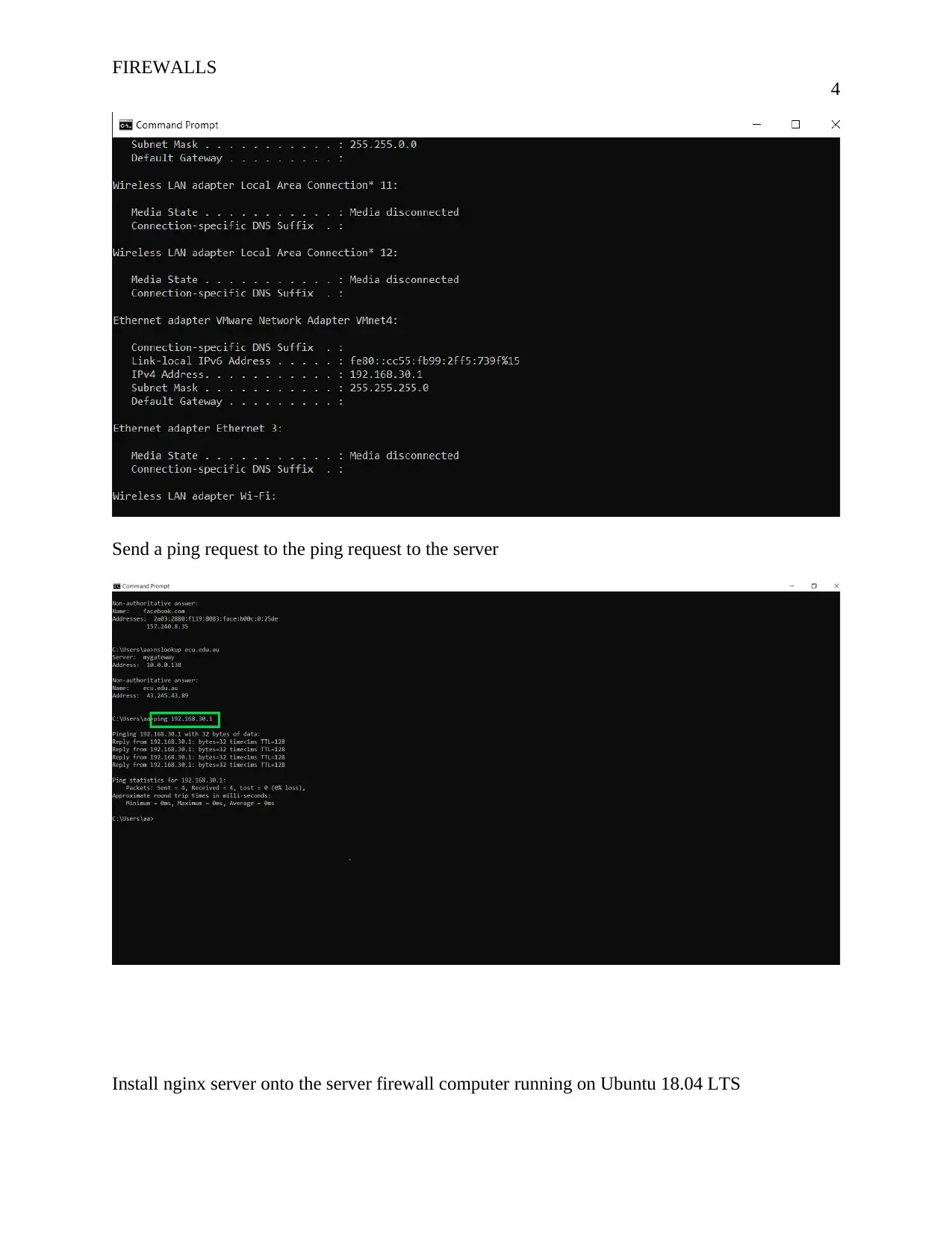
Send a ping request to the ping request to the server
Install nginx server onto the server firewall computer running on Ubuntu 18.04 LTS
4
Send a ping request to the ping request to the server
Install nginx server onto the server firewall computer running on Ubuntu 18.04 LTS
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
FIREWALLS
5
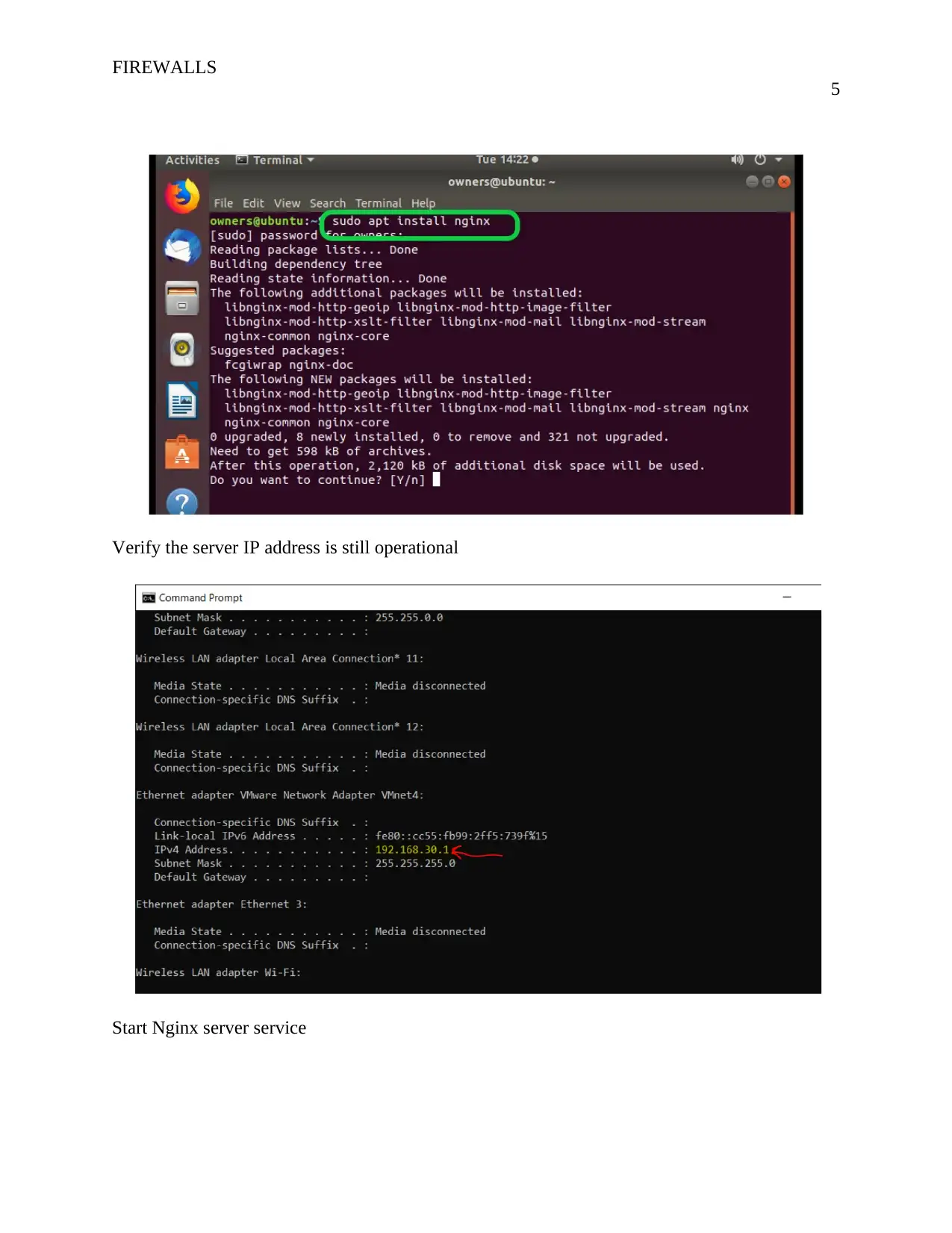
Verify the server IP address is still operational
Start Nginx server service
5
Verify the server IP address is still operational
Start Nginx server service
FIREWALLS
6
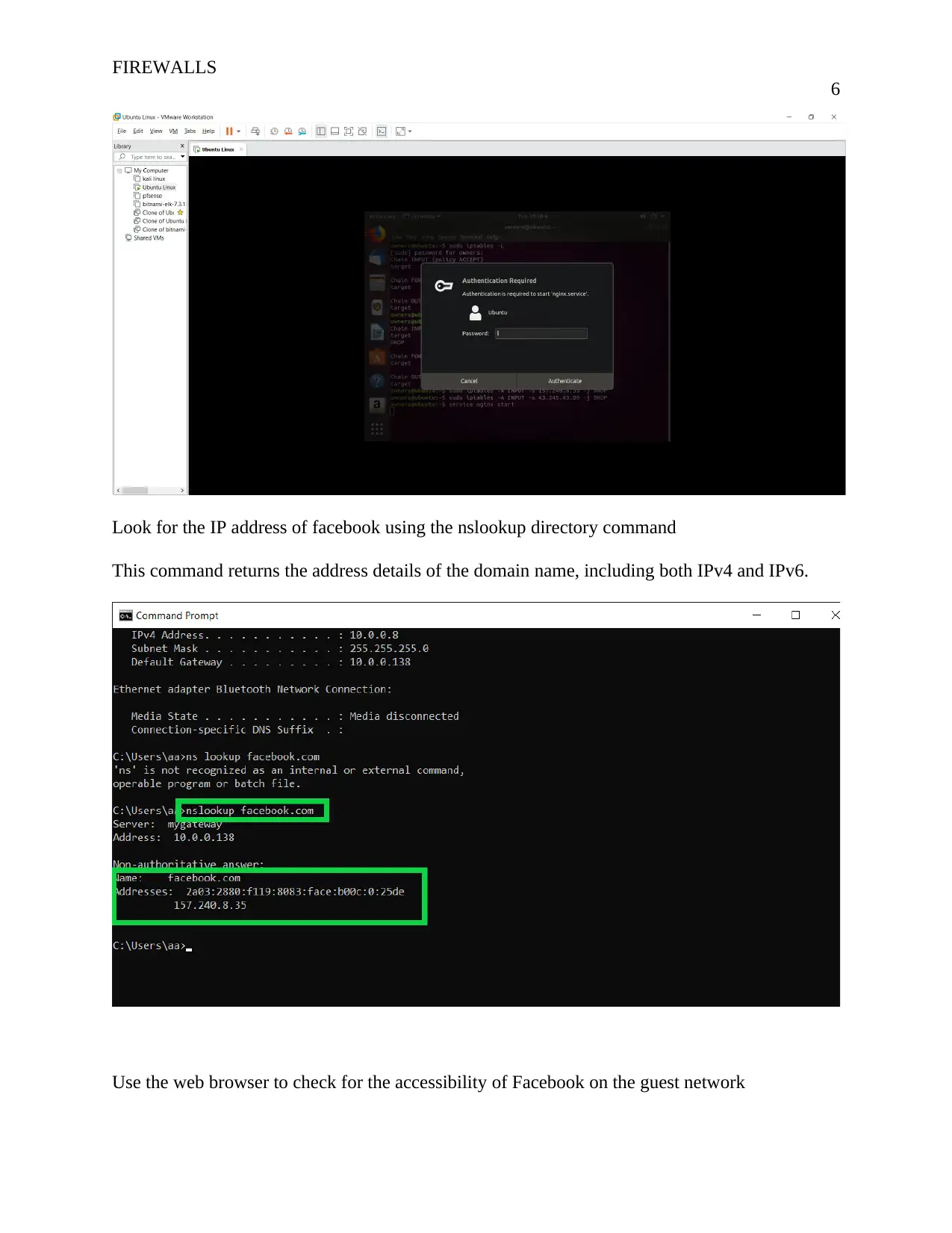
Look for the IP address of facebook using the nslookup directory command
This command returns the address details of the domain name, including both IPv4 and IPv6.
Use the web browser to check for the accessibility of Facebook on the guest network
6
Look for the IP address of facebook using the nslookup directory command
This command returns the address details of the domain name, including both IPv4 and IPv6.
Use the web browser to check for the accessibility of Facebook on the guest network
FIREWALLS
7
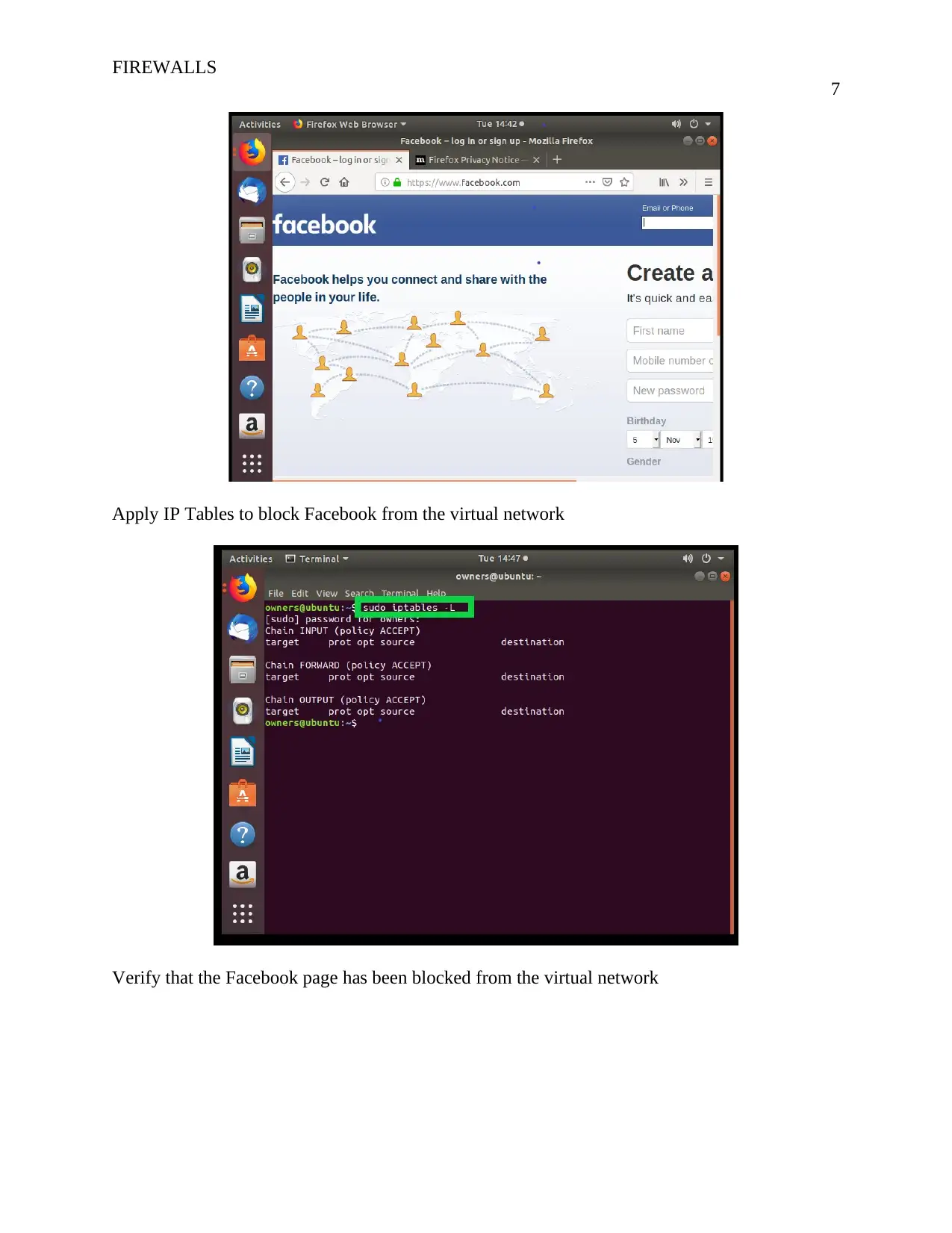
Apply IP Tables to block Facebook from the virtual network
Verify that the Facebook page has been blocked from the virtual network
7
Apply IP Tables to block Facebook from the virtual network
Verify that the Facebook page has been blocked from the virtual network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
FIREWALLS
8
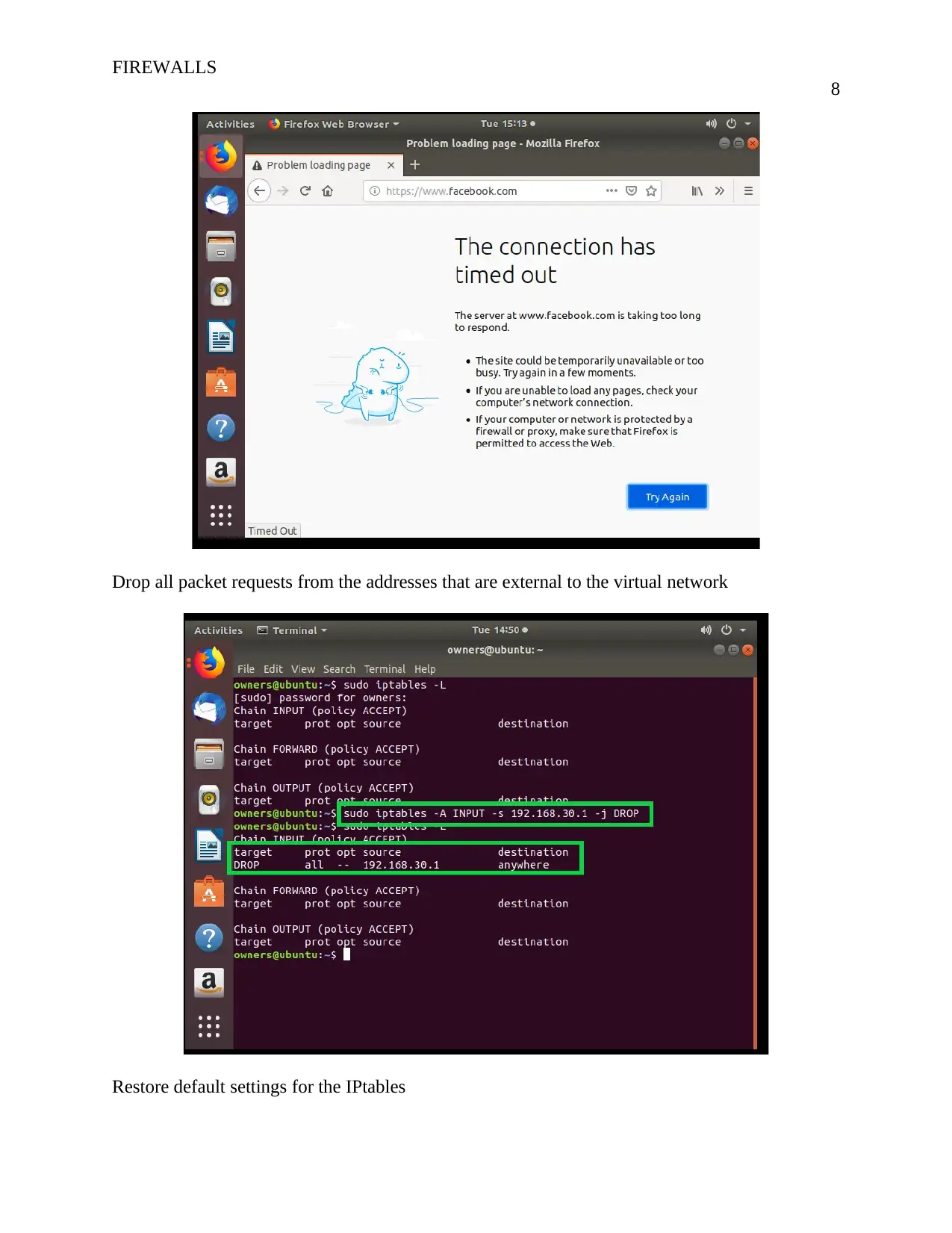
Drop all packet requests from the addresses that are external to the virtual network
Restore default settings for the IPtables
8
Drop all packet requests from the addresses that are external to the virtual network
Restore default settings for the IPtables
FIREWALLS
9
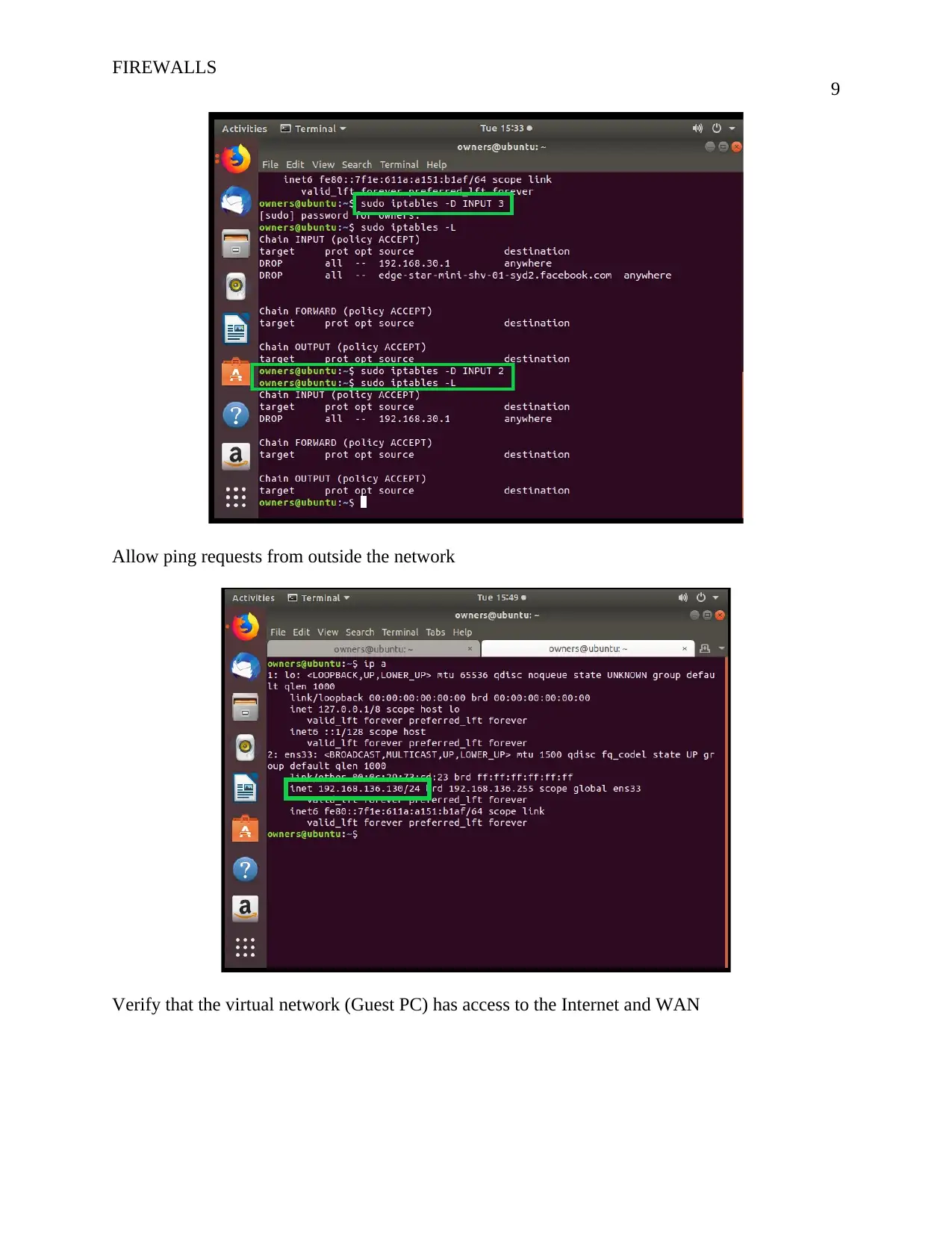
Allow ping requests from outside the network
Verify that the virtual network (Guest PC) has access to the Internet and WAN
9
Allow ping requests from outside the network
Verify that the virtual network (Guest PC) has access to the Internet and WAN
FIREWALLS
10
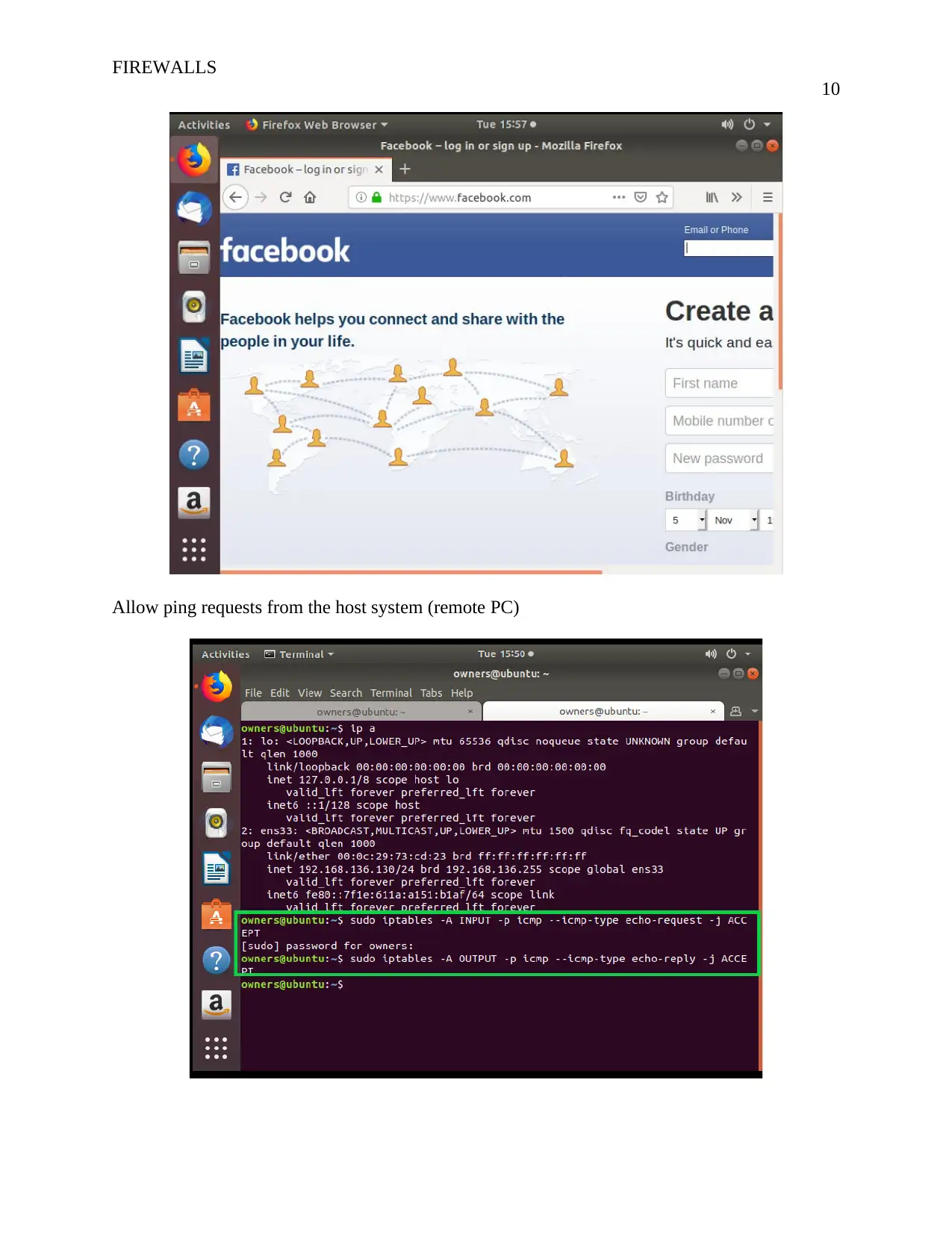
Allow ping requests from the host system (remote PC)
10
Allow ping requests from the host system (remote PC)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
FIREWALLS
11
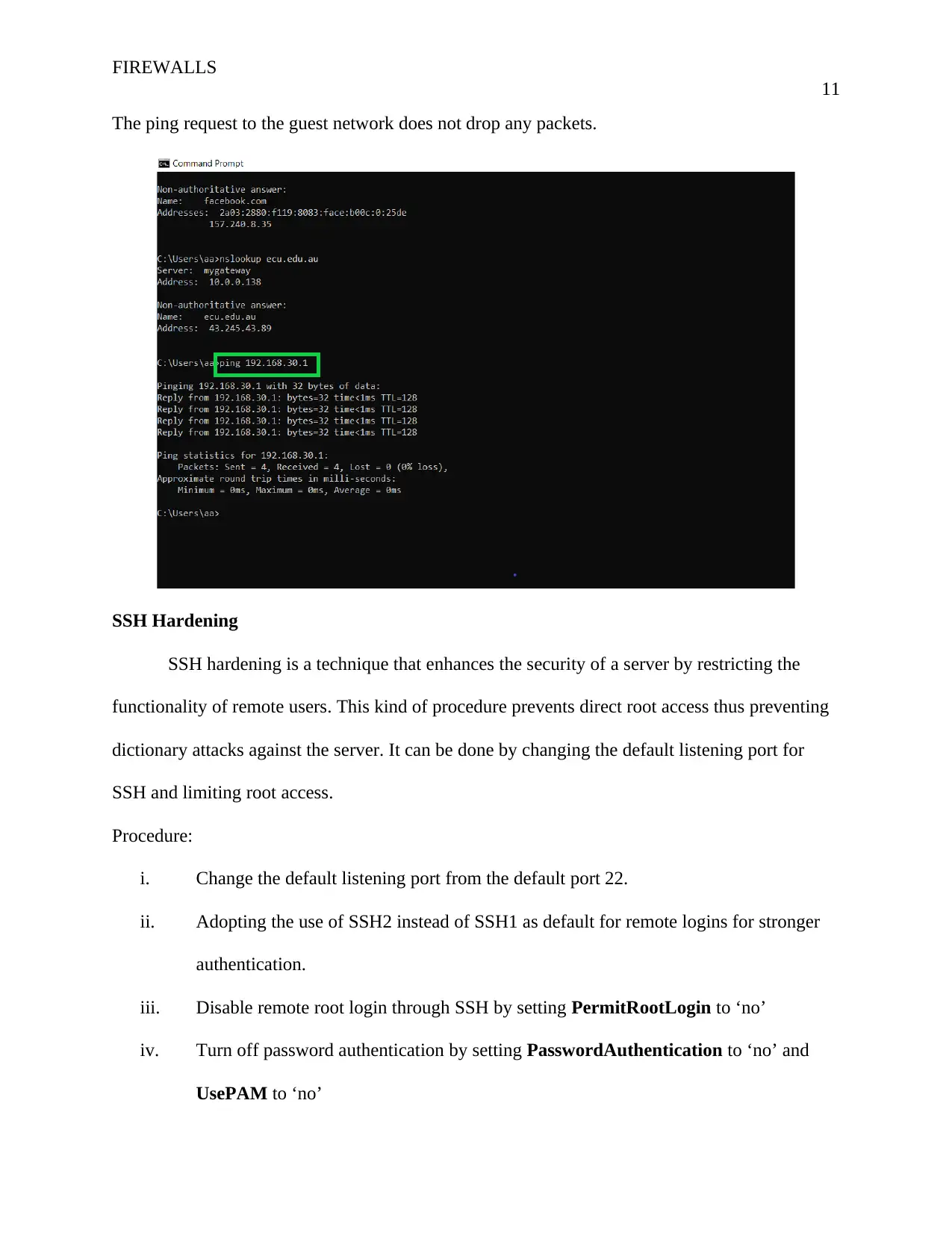
The ping request to the guest network does not drop any packets.
SSH Hardening
SSH hardening is a technique that enhances the security of a server by restricting the
functionality of remote users. This kind of procedure prevents direct root access thus preventing
dictionary attacks against the server. It can be done by changing the default listening port for
SSH and limiting root access.
Procedure:
i. Change the default listening port from the default port 22.
ii. Adopting the use of SSH2 instead of SSH1 as default for remote logins for stronger
authentication.
iii. Disable remote root login through SSH by setting PermitRootLogin to ‘no’
iv. Turn off password authentication by setting PasswordAuthentication to ‘no’ and
UsePAM to ‘no’
11
The ping request to the guest network does not drop any packets.
SSH Hardening
SSH hardening is a technique that enhances the security of a server by restricting the
functionality of remote users. This kind of procedure prevents direct root access thus preventing
dictionary attacks against the server. It can be done by changing the default listening port for
SSH and limiting root access.
Procedure:
i. Change the default listening port from the default port 22.
ii. Adopting the use of SSH2 instead of SSH1 as default for remote logins for stronger
authentication.
iii. Disable remote root login through SSH by setting PermitRootLogin to ‘no’
iv. Turn off password authentication by setting PasswordAuthentication to ‘no’ and
UsePAM to ‘no’

FIREWALLS
12
v. Restrict server to known users e.g. AllowUsers ‘Username’
vi. Restart ssh with systemctl restart sshd
Figure 2: Editing SSH remote login rules
Improved Network Design
The network configuration performed in the previous section implements a bastion host
in which a single layer of abstraction is provided between the trusted and untrusted network.
Even though it is sufficiently secure in most of the cases, this kind of network is not immune
from attacks where an intruder gains physical access to internal devices. In the event of a
successful bypass of the firewall by a malicious individual or program, the LAN devices will be
completely exposed. A better network implements a demilitarized zone architecture, which
features three different zones: The trusted network, demilitarized zone (DMZ), and the untrusted
network, is shown in figure 2 below.
12
v. Restrict server to known users e.g. AllowUsers ‘Username’
vi. Restart ssh with systemctl restart sshd
Figure 2: Editing SSH remote login rules
Improved Network Design
The network configuration performed in the previous section implements a bastion host
in which a single layer of abstraction is provided between the trusted and untrusted network.
Even though it is sufficiently secure in most of the cases, this kind of network is not immune
from attacks where an intruder gains physical access to internal devices. In the event of a
successful bypass of the firewall by a malicious individual or program, the LAN devices will be
completely exposed. A better network implements a demilitarized zone architecture, which
features three different zones: The trusted network, demilitarized zone (DMZ), and the untrusted
network, is shown in figure 2 below.

FIREWALLS
13
Figure 3: Demilitarized zone (DMZ) firewall architecture
The DMZ, also known as the screened subnet, is partially exposed to the untrusted
network. It is protected by the external firewall. If a hacker manages to bypass the first firewall,
this subnet shields any possible attacks by serving as alternate targets. The internal firewall will
still prevent unauthorized access or further manipulation of the network, thus providing extra
protection.
Internal firewall configuration using OPNsense
OPNsense makes a web organization hostile to lockout rule and a "permit all" rule for
IPv4 and IPv6 for the LAN interface when you set up your LAN/WAN endless supply of
OPNsense (Carey, & Oyeniyi, 2018). These principles prevent you from locking yourself out of
the web organization pages on your switch just as permit unlimited Internet access for your
system. The default firewall setup is supposed to enable your OPNsense switch to act as a run of
the mill purchaser grade switch (Linden, Huang, Hsu, & Lee, 2015). Fitting gadgets
straightforwardly into the switch (or into a change associated with the switch), and they will
13
Figure 3: Demilitarized zone (DMZ) firewall architecture
The DMZ, also known as the screened subnet, is partially exposed to the untrusted
network. It is protected by the external firewall. If a hacker manages to bypass the first firewall,
this subnet shields any possible attacks by serving as alternate targets. The internal firewall will
still prevent unauthorized access or further manipulation of the network, thus providing extra
protection.
Internal firewall configuration using OPNsense
OPNsense makes a web organization hostile to lockout rule and a "permit all" rule for
IPv4 and IPv6 for the LAN interface when you set up your LAN/WAN endless supply of
OPNsense (Carey, & Oyeniyi, 2018). These principles prevent you from locking yourself out of
the web organization pages on your switch just as permit unlimited Internet access for your
system. The default firewall setup is supposed to enable your OPNsense switch to act as a run of
the mill purchaser grade switch (Linden, Huang, Hsu, & Lee, 2015). Fitting gadgets
straightforwardly into the switch (or into a change associated with the switch), and they will
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
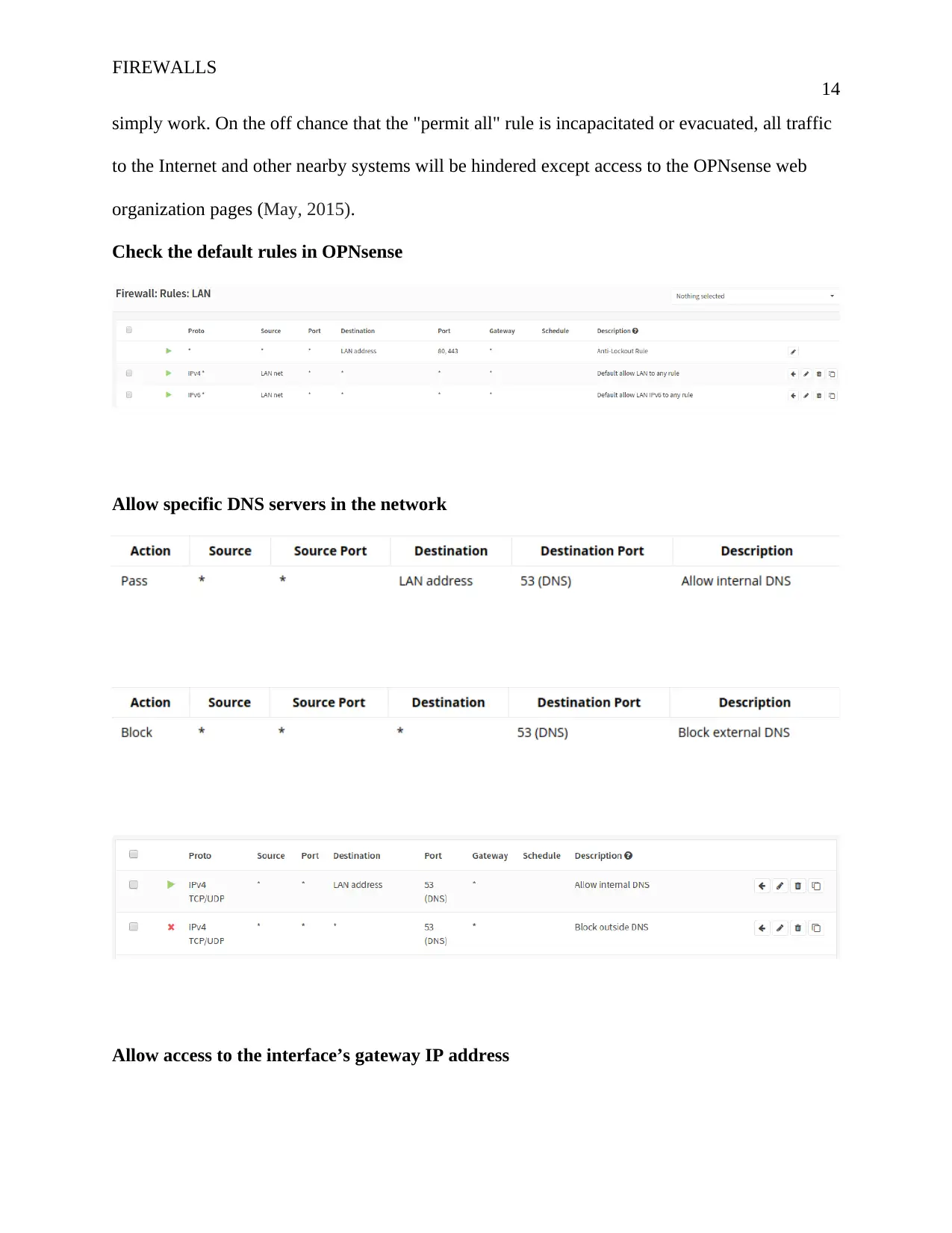
FIREWALLS
14
simply work. On the off chance that the "permit all" rule is incapacitated or evacuated, all traffic
to the Internet and other nearby systems will be hindered except access to the OPNsense web
organization pages (May, 2015).
Check the default rules in OPNsense
Allow specific DNS servers in the network
Allow access to the interface’s gateway IP address
14
simply work. On the off chance that the "permit all" rule is incapacitated or evacuated, all traffic
to the Internet and other nearby systems will be hindered except access to the OPNsense web
organization pages (May, 2015).
Check the default rules in OPNsense
Allow specific DNS servers in the network
Allow access to the interface’s gateway IP address

FIREWALLS
15
Allow Local Services across VLANs/Interfaces
Block Access to Other VLANs
Conclusion
The strengthening of network security is an important step towards keeping information
private and confidential. The use of cryptographic mechanisms enables quick access of this
information to authorized individuals while restricting access to unauthorized entities. Firewalls
serve as the first line of defense against unwanted access by performing packet and address
filtering and dropping/blocking functions. They enable the reduction of replay attacks, DDoS
attacks, and even spoofing attempts that may be tried by hackers. A bastion host, as has been
discussed, does not provide ultimate security. The use of a DMZ enhances the safety of a
network. However, the addition of internal application-level firewalls reduces the chances of
unauthorized access, thus keeping information secure.
15
Allow Local Services across VLANs/Interfaces
Block Access to Other VLANs
Conclusion
The strengthening of network security is an important step towards keeping information
private and confidential. The use of cryptographic mechanisms enables quick access of this
information to authorized individuals while restricting access to unauthorized entities. Firewalls
serve as the first line of defense against unwanted access by performing packet and address
filtering and dropping/blocking functions. They enable the reduction of replay attacks, DDoS
attacks, and even spoofing attempts that may be tried by hackers. A bastion host, as has been
discussed, does not provide ultimate security. The use of a DMZ enhances the safety of a
network. However, the addition of internal application-level firewalls reduces the chances of
unauthorized access, thus keeping information secure.

FIREWALLS
16
16
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

FIREWALLS
17
References
Carey, M. J., & Oyeniyi, T. (2018). U.S. Patent Application No. 15/653,293.
Gilman, E., & Barth, D. (2017). Zero Trust Networks: Building Secure Systems in Untrusted
Networks. O'Reilly Media, Inc.
Linden, T., Huang, J., Hsu, J., & Lee, M. J. (2015). U.S. Patent No. 9,203,865. Washington, DC:
U.S. Patent and Trademark Office.
Lundgren, B., & Möller, N. (2017). Defining Information Security. Science Engineering and
Ethics, 25(2), 419-441. doi:10.1007/s11948-017-9992-1
May, R. A. (2015). U.S. Patent No. 9,065,802. Washington, DC: U.S. Patent and Trademark
Office.
Pachghare, V. (2015). CRYPTOGRAPHY AND INFORMATION SECURITY. PHI Learning Pvt.
Ltd.
17
References
Carey, M. J., & Oyeniyi, T. (2018). U.S. Patent Application No. 15/653,293.
Gilman, E., & Barth, D. (2017). Zero Trust Networks: Building Secure Systems in Untrusted
Networks. O'Reilly Media, Inc.
Linden, T., Huang, J., Hsu, J., & Lee, M. J. (2015). U.S. Patent No. 9,203,865. Washington, DC:
U.S. Patent and Trademark Office.
Lundgren, B., & Möller, N. (2017). Defining Information Security. Science Engineering and
Ethics, 25(2), 419-441. doi:10.1007/s11948-017-9992-1
May, R. A. (2015). U.S. Patent No. 9,065,802. Washington, DC: U.S. Patent and Trademark
Office.
Pachghare, V. (2015). CRYPTOGRAPHY AND INFORMATION SECURITY. PHI Learning Pvt.
Ltd.
1 out of 17
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.

